60 Victimology Topics & Examples
For your paper on crime prevention, penology, or violence in any form, take a look at our victimology research topics. Get a critical title from the collection prepared by our team .

🏆 Best Victimology Topics & Essay Examples
📌 interesting victimology research paper topics, ❓ victimology research questions.
- Victimology: Definition, Theory and History Victimology is a science that dedicates itself to the study of the connection between the victim and the offender. The police use victimology in order to discover a correlation between the victims and the offenders, […]
- Victimology and Domestic Violence In this situation there are many victims; Anne is a victim of domestic violence and the children are also victims of the same as well as the tragic death of their father.
- The Green Victimology: Saving Non-Human Victims Consequently, a multidisciplinary study of green victimology is required to create solutions to protect victims and mitigate the detrimental effects of environmental crime.
- Career in Victimology But criminal victimologists continue to investigate the problems of victim-offender interactions, individual characteristics of victims within and outside of the context of a committed crime, relation of victims to latent criminality, etc.
- Victimology and Victimization The concept of the sideshow freak is a term inextricably linked to the various circuses and carnivals in the U.S.during the mid 19th to mid 20th century.
- The Victimology Project by Ellisha Shelsta The case revealed victims of the crime, described the behavioral pattern of the offender and provided insights into the relationship between the perpetrator and the injured party.
- Comparing Positivist and Radical Victimology Perspective
- Contribution to Victimology and Marginalisation
- Crime, Victimology and Victimization
- Female Victims of Assault Crimes Dealing With Victimology
- Feminism, Positivism, and Radical Victimology
- Historical Background of Victimology
- History of Victimology and Its Impact on Society
- Justice System and the Impact of Victimology
- Law Enforcement and the Study of Victimology
- Merton’s Strain Theory and Victimology Theories
- Similarities Between Criminology and Victimology
- The Politics of Victimization: Victims, Victimology, and Human Rights
- The Role of Victimology in Law Enforcement
- Victimology and Alternatives to the Traditional Criminal Justice System
- Victimology and Criminal Justice System
- Victimology and How to Avoid Becoming a Victim of a Crime
- Victimology and Its Effect on the Justice System
- Victimology and Restorative Justice
- Parallels Between Criminology and Victimology
- Victimology: Crime and Criminal Victimization
- Victimology: Criminology and Victim
- Victimology: The Cause of Domestic Violence
- Victimology: The Role of Victims When Influencing Crime
- What Is Victimology Criminology?
- Why Is the Victimology Perspective Important in Understanding Serial Murder?
- What Are the Contributions of the Different Personalities in Studying Victimology?
- What Is the Difference Between Victimology and Victimologists?
- What Is the Interrelationship Between Criminology, Penology, and Victimology?
- How Does Criminal Psychology Relate to Victimology?
- What Is the Definition of the Term Human Behavior and Victimology?
- What Degrees in Psychology Specialise in Criminal Victimology?
- What Is the Effect of Victimology in Society?
- What Is the Worst Classical School Theory in Explaining Victimology?
- What Are the Advantages of Victimology in the Philippines?
- Why Do We Need to Study Human Behavior and Victimology?
- What Victimology Says About Child Abuse?
- How Is Victimology Different From Sociology?
- What Are the Recent Areas of Research in Victimology?
- What Is Victimology and Why Is It Important?
- What Is Victimology in Human Behavior?
- What Role Does Victimology Play in the Study of Criminology and Criminal Justice?
- What Is the Difference Between Victimology and Psychology?
- Do You Think “White Victimology” Is a Valid Concept?
- In What Ways Can the State Be Considered a Perpetrator in Victimology?
- What Did Heidegger Think About Victimology?
- What Is the Summary of Hans von Hentig’s Victimology?
- What Are Similarities Among the Three Basic Theories of Victimology?
- What Is the Historical Overview of Victimology?
- Who Was the Father of Victimology?
- What Are the Different Types of Victimology?
- How Do You Determine Victimology?
- How Is Penology and Victimology Related?
- How Is Victimology Relevant in Law Enforcement?
- Human Trafficking Titles
- Cryptography Paper Topics
- Prostitution Topics
- Cyber Security Topics
- Sex Trafficking Research Ideas
- Rape Essay Titles
- Serial Killer Paper Topics
- Cyber Bullying Essay Ideas
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, March 1). 60 Victimology Topics & Examples. https://ivypanda.com/essays/topic/victimology-essay-topics/
"60 Victimology Topics & Examples." IvyPanda , 1 Mar. 2024, ivypanda.com/essays/topic/victimology-essay-topics/.
IvyPanda . (2024) '60 Victimology Topics & Examples'. 1 March.
IvyPanda . 2024. "60 Victimology Topics & Examples." March 1, 2024. https://ivypanda.com/essays/topic/victimology-essay-topics/.
1. IvyPanda . "60 Victimology Topics & Examples." March 1, 2024. https://ivypanda.com/essays/topic/victimology-essay-topics/.
Bibliography
IvyPanda . "60 Victimology Topics & Examples." March 1, 2024. https://ivypanda.com/essays/topic/victimology-essay-topics/.
- Skip to main content
- Skip to primary sidebar
Criminal Justice
IResearchNet
Academic Writing Services
Domestic violence research topics.
The list of domestic violence research paper topics below will show that domestic violence takes on many forms. Through recent scientific study, it is now known that domestic violence occurs within different types of households. The purpose of creating this list is for students to have available a comprehensive, state-of-the-research, easy-to-read compilation of a wide variety of domestic violence topics and provide research paper examples on those topics.
Domestic violence research paper topics can be divided into seven categories:
- Victims of domestic violence,
- Theoretical perspectives and correlates to domestic violence,
- Cross-cultural and religious perspectives,
- Understudied areas within domestic violence research,
- Domestic violence and the law,
- Child abuse and elder abuse, and
- Special topics in domestic violence.
100+ Domestic Violence Research Topics
Victims of domestic violence.
Initial research recognized wives as victims of domestic violence. Thereafter, it was acknowledged that unmarried women were also falling victim to violence at the hands of their boyfriends. Subsequently, the term ‘‘battered women’’ became synonymous with ‘‘battered wives.’’ Legitimizing female victimization served as the catalyst in introducing other types of intimate partner violence.
- Battered Husbands
- Battered Wives
- Battered Women: Held in Captivity
- Battered Women Who Kill: An Examination
- Cohabiting Violence
- Dating Violence
- Domestic Violence in Workplace
- Intimate Partner Homicide
- Intimate Partner Violence, Forms of
- Marital Rape
- Mutual Battering
- Spousal Prostitution
Read more about victims of domestic violence .
Part 2: Research Paper Topics on
Theoretical Perspectives and Correlates to Domestic Violence
There is no single causal factor related to domestic violence. Rather, scholars have concluded that there are numerous factors that contribute to domestic violence. Feminists found that women were beaten at the hands of their partners. Drawing on feminist theory, they helped explain the relationship between patriarchy and domestic violence. Researchers have examined other theoretical perspectives such as attachment theory, exchange theory, identity theory, the cycle of violence, social learning theory, and victim-blaming theory in explaining domestic violence. However, factors exist that may not fall into a single theoretical perspective. Correlates have shown that certain factors such as pregnancy, social class, level of education, animal abuse, and substance abuse may influence the likelihood for victimization.
- Animal Abuse: The Link to Family Violence
- Assessing Risk in Domestic Violence Cases
- Attachment Theory and Domestic Violence
- Battered Woman Syndrome
- Batterer Typology
- Bullying and the Family
- Coercive Control
- Control Balance Theory and Domestic Violence
- Cycle of Violence
- Depression and Domestic Violence
- Education as a Risk Factor for Domestic Violence
- Exchange Theory
- Feminist Theory
- Identity Theory and Domestic Violence
- Intergenerational Transfer of Intimate Partner Violence
- Popular Culture and Domestic Violence
- Post-Incest Syndrome
- Pregnancy-Related Violence
- Social Class and Domestic Violence
- Social Learning Theory and Family Violence
- Stockholm Syndrome in Battered Women
- Substance Use/Abuse and Intimate Partner Violence
- The Impact of Homelessness on Family Violence
- Victim-Blaming Theory
Read more about domestic violence theories .
Part 3: Research Paper Topics on
Cross-Cultural and Religious Perspectives on Domestic Violence
It was essential to acknowledge that domestic violence crosses cultural boundaries and religious affiliations. There is no one particular society or religious group exempt from victimization. A variety of developed and developing countries were examined in understanding the prevalence of domestic violence within their societies as well as their coping strategies in handling these volatile issues. It is often misunderstood that one religious group is more tolerant of family violence than another. As Christianity, Islam, and Judaism represent the three major religions of the world, their ideologies were explored in relation to the acceptance and prevalence of domestic violence.
- Africa: Domestic Violence and the Law
- Africa: The Criminal Justice System and the Problem of Domestic Violence in West Africa
- Asian Americans and Domestic Violence: Cultural Dimensions
- Child Abuse: A Global Perspective
- Christianity and Domestic Violence
- Cross-Cultural Examination of Domestic Violence in China and Pakistan
- Cross-Cultural Examination of Domestic Violence in Latin America
- Cross-Cultural Perspectives on Domestic Violence
- Cross-Cultural Perspectives on How to Deal with Batterers
- Dating Violence among African American Couples
- Domestic Violence among Native Americans
- Domestic Violence in African American Community
- Domestic Violence in Greece
- Domestic Violence in Rural Communities
- Domestic Violence in South Africa
- Domestic Violence in Spain
- Domestic Violence in Trinidad and Tobago
- Domestic Violence within the Jewish Community
- Human Rights, Refugee Laws, and Asylum Protection for People Fleeing Domestic Violence
- Introduction to Minorities and Families in America
- Medical Neglect Related to Religion and Culture
- Multicultural Programs for Domestic Batterers
- Qur’anic Perspectives on Wife Abuse
- Religious Attitudes toward Corporal Punishment
- Rule of Thumb
- Same-Sex Domestic Violence: Comparing Venezuela and the United States
- Worldwide Sociolegal Precedents Supporting Domestic Violence from Ancient to Modern Times
Part 4: Research Paper Topics on
Understudied Areas within Domestic Violence Research
Domestic violence has typically examined traditional relationships, such as husband–wife, boyfriend–girlfriend, and parent–child. Consequently, scholars have historically ignored non-traditional relationships. In fact, certain entries have limited cross-references based on the fact that there were limited, if any, scholarly publications on that topic. Only since the 1990s have scholars admitted that violence exists among lesbians and gay males. There are other ignored populations that are addressed within this encyclopedia including violence within military and police families, violence within pseudo-family environments, and violence against women and children with disabilities.
- Caregiver Violence against People with Disabilities
- Community Response to Gay and Lesbian Domestic Violence
- Compassionate Homicide and Spousal Violence
- Domestic Violence against Women with Disabilities
- Domestic Violence by Law Enforcement Officers
- Domestic Violence within Military Families
- Factors Influencing Reporting Behavior by Male Domestic Violence Victims
- Gay and Bisexual Male Domestic Violence
- Gender Socialization and Gay Male Domestic Violence
- Inmate Mothers: Treatment and Policy Implications
- Intimate Partner Violence and Mental Retardation
- Intimate Partner Violence in Queer, Transgender, and Bisexual Communities
- Lesbian Battering
- Male Victims of Domestic Violence and Reasons They Stay with Their Abusers
- Medicalization of Domestic Violence
- Police Attitudes and Behaviors toward Gay Domestic Violence
- Pseudo-Family Abuse
- Sexual Aggression Perpetrated by Females
- Sexual Orientation and Gender Identity: The Need for Education in Servicing Victims of Trauma
Part 5: Research Paper Topics on
Domestic Violence and the Law
The Violence against Women Act (VAWA) of 1994 helped pave domestic violence concerns into legislative matters. Historically, family violence was handled through informal measures often resulting in mishandling of cases. Through VAWA, victims were given the opportunity to have their cases legally remedied. This legitimized the separation of specialized domestic and family violence courts from criminal courts. The law has recognized that victims of domestic violence deserve recognition and resolution. Law enforcement agencies may be held civilly accountable for their actions in domestic violence incidents. Mandatory arrest policies have been initiated helping reduce discretionary power of police officers. Courts have also begun to focus on the offenders of domestic violence. Currently, there are batterer intervention programs and mediation programs available for offenders within certain jurisdictions. Its goals are to reduce the rate of recidivism among batterers.
- Battered Woman Syndrome as a Legal Defense in Cases of Spousal Homicide
- Batterer Intervention Programs
- Clemency for Battered Women
- Divorce, Child Custody, and Domestic Violence
- Domestic Violence Courts
- Electronic Monitoring of Abusers
- Expert Testimony in Domestic Violence Cases
- Judicial Perspectives on Domestic Violence
- Lautenberg Law
- Legal Issues for Battered Women
- Mandatory Arrest Policies
- Mediation in Domestic Violence
- Police Civil Liability in Domestic Violence Incidents
- Police Decision-Making Factors in Domestic Violence Cases
- Police Response to Domestic Violence Incidents
- Prosecution of Child Abuse and Neglect
- Protective and Restraining Orders
- Shelter Movement
- Training Practices for Law Enforcement in Domestic Violence Cases
- Violence against Women Act
Read more about Domestic Violence Law .
Part 6: Research Paper Topics on
Child Abuse and Elder Abuse
Scholars began to address child abuse over the last third of the twentieth century. It is now recognized that child abuse falls within a wide spectrum. In the past, it was based on visible bruises and scars. Today, researchers have acknowledged that psychological abuse, where there are no visible injuries, is just as damaging as its counterpart. One of the greatest controversies in child abuse literature is that of Munchausen by Proxy. Some scholars have recognized that it is a syndrome while others would deny a syndrome exists. Regardless of the term ‘‘syndrome,’’ Munchausen by Proxy does exist and needs to be further examined. Another form of violence that needs to be further examined is elder abuse. Elder abuse literature typically focused on abuse perpetrated by children and caregivers. With increased life expectancies, it is now understood that there is greater probability for violence among elderly intimate couples. Shelters and hospitals need to better understand this unique population in order to better serve its victims.
- Assessing the Risks of Elder Abuse
- Child Abuse and Juvenile Delinquency
- Child Abuse and Neglect in the United States: An Overview
- Child Maltreatment, Interviewing Suspected Victims of
- Child Neglect
- Child Sexual Abuse
- Children Witnessing Parental Violence
- Consequences of Elder Abuse
- Elder Abuse and Neglect: Training Issues for Professionals
- Elder Abuse by Intimate Partners
- Elder Abuse Perpetrated by Adult Children
- Filicide and Children with Disabilities
- Mothers Who Kill
- Munchausen by Proxy Syndrome
- Parental Abduction
- Postpartum Depression, Psychosis, and Infanticide
- Ritual Abuse–Torture in Families
- Shaken Baby Syndrome
- Sibling Abuse
Part 7: Research Paper Topics on
Special Topics in Domestic Violence
Within this list, there are topics that may not fit clearly into one of the aforementioned categories. Therefore, they are be listed in a separate special topics designation. Analyzing Incidents of Domestic Violence: The National Incident-Based Reporting System
- Community Response to Domestic Violence
- Conflict Tactics Scales
- Dissociation in Domestic Violence, The Role of
- Domestic Homicide in Urban Centers: New York City
- Fatality Reviews in Cases of Adult Domestic Homicide and Suicide
- Female Suicide and Domestic Violence
- Healthcare Professionals’ Roles in Identifying and Responding to Domestic Violence
- Measuring Domestic Violence
- Neurological and Physiological Impact of Abuse
- Social, Economic, and Psychological Costs of Violence
- Stages of Leaving Abusive Relationships
- The Physical and Psychological Impact of Spousal Abuse
Domestic violence remains a relatively new field of study among social scientists but it is already a popular research paper subject within college and university students. Only within the past 4 decades have scholars recognized domestic violence as a social problem. Initially, domestic violence research focused on child abuse. Thereafter, researchers focused on wife abuse and used this concept interchangeably with domestic violence. Within the past 20 years, researchers have acknowledged that other forms of violent relationships exist, including dating violence, battered males, and gay domestic violence. Moreover, academicians have recognized a subcategory within the field of criminal justice: victimology (the scientific study of victims). Throughout the United States, colleges and universities have been creating victimology courses, and even more specifically, family violence and interpersonal violence courses.
The media have informed us that domestic violence is so commonplace that the public has unfortunately grown accustomed to reading and hearing about husbands killing their wives, mothers killing their children, or parents neglecting their children. While it is understood that these offenses take place, the explanations as to what factors contributed to them remain unclear. In order to prevent future violence, it is imperative to understand its roots. There is no one causal explanation for domestic violence; however, there are numerous factors which may help explain these unjustified acts of violence. Highly publicized cases such as the O.J. Simpson and Scott Peterson trials have shown the world that alleged murderers may not resemble the deranged sociopath depicted in horror films. Rather, they can be handsome, charming, and well-liked by society. In addition, court-centered programming on television continuously publicizes cases of violence within the home informing the public that we are potentially at risk by our caregivers and other loved ones. There is the case of the au pair Elizabeth Woodward convicted of shaking and killing Matthew Eappen, the child entrusted to her care. Some of the most highly publicized cases have also focused on mothers who kill. America was stunned as it heard the cases of Susan Smith and Andrea Yates. Both women were convicted of brutally killing their own children. Many asked how loving mothers could turn into cold-blooded killers.
Browse other criminal justice research topics .
Sorry - This site requires JavaScript to be enabled to work properly.
View all open access research ., learn with the library.
Visit our library blog for search tips on victim services topics, highlights from our free collection, and tutorials on creating alerts, reading research papers, and respecting copyright.

May 14, 2024
Center for victim research youtube channel.
Have you checked out the Center for Victim Research YouTube Channel yet? You will find a video archive of all of CVR’s webinars, including Evidence Hours and Ask-a-Researcher, as well […]
READ POST »

April 24, 2024
Visit our collections.
The Justice Information Center houses the Center for Victim Research Community, which contains three collections of resources for victim service providers and researchers. The Open Access Instruments Collection includes tools […]

April 1, 2022
Research-to-practice inspiration in the cvr library, part 2.
In a 2020 survey of Texas victim service providers, respondents said that hearing from others who have partnered with researchers would help with their own efforts to work with a […]
Library How-To Video Tutorial
Some quick tips for searching our Library.
ASK A LIBRARIAN

Have a question about searching the collection, setting up customized alerts, or sharing a resource? Look for your question in our FAQs, or contact the Research Librarian!
OUR PARTNER LIBRARIES
For resources beyond research, visit CVR’s partner libraries.
LEARN MORE »
FEATURED TAGS
- Bibliographies
- Journal Club
- Keeping Up With Research
- Search Tips
HELPFUL LINKS
- Newsletter Sign Up
- Sign In/Register

Privacy Policy | Accessibility Statement
- Partner Libraries
- Research Syntheses
- National Census of Victim Service Providers
- Collaborations Supported by CVR
- Research Basics
- Program Evaluation
- Victim Protection
- Screening & Assessment
- Needs Assessment
- Collecting Data
- Working Together
- Find a Partner

An official website of the United States government, Department of Justice.
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
NCJRS Virtual Library
Victimology handbook: research findings, treatment, and public policy, additional details.
Vance Allen , 19 Union Square , West Floor 8 , New York , NY 10003-3304 , United States
No download available
Availability, related topics.
Advertisement
Research trends in cybercrime victimization during 2010–2020: a bibliometric analysis
- Review Paper
- Published: 06 January 2022
- Volume 2 , article number 4 , ( 2022 )
Cite this article

- Huong Thi Ngoc Ho 1 &
- Hai Thanh Luong ORCID: orcid.org/0000-0003-2421-9149 2
11k Accesses
12 Citations
1 Altmetric
Explore all metrics
Research on cybercrime victimization is relatively diversified; however, no bibliometric study has been found to introduce the panorama of this subject. The current study aims to address this research gap by performing a bibliometric analysis of 387 Social Science Citation Index articles relevant to cybercrime victimization from Web of Science database during the period of 2010–2020. The purpose of the article is to examine the research trend and distribution of publications by five main fields, including time, productive authors, prominent sources, active institutions, and leading countries/regions. Furthermore, this study aims to determine the global collaborations and current gaps in research of cybercrime victimization. Findings indicated the decidedly upward trend of publications in the given period. The USA and its authors and institutions were likely to connect widely and took a crucial position in research of cybercrime victimization. Cyberbullying was identified as the most concerned issue over the years and cyber interpersonal crimes had the large number of research comparing to cyber-dependent crimes. Future research is suggested to concern more about sample of the elder and collect data in different countries which are not only European countries or the USA. Cross-nation research in less popular continents in research map was recommended to be conducted more. This paper contributed an overview of scholarly status of cybercrime victimization through statistical evidence and visual findings; assisted researchers to optimize their own research direction; and supported authors and institutions to build strategies for research collaboration.
Similar content being viewed by others

Research synthesis of cybercrime laws and COVID-19 in Indonesia: lessons for developed and developing countries

The Nuts and Bolts of the India-Abusive Fake Government of Telangana: Cyberpolicing Against Online Sedition

Cybercrime in the Russian Federation: Criminological and Criminal Law Analysis
Explore related subjects.
- Artificial Intelligence
Avoid common mistakes on your manuscript.
Introduction
To date, the debate of cybercrime definition has been controversial which is considered as one of the five areas of cyber criminology (Ngo and Jaishankar 2017 ; Drew 2020 ). Footnote 1 Several terms are used to illustrate ‘cybercrime’, such as ‘high-tech crime’ (Insa 2007 ), ‘computer crime’ (Choi 2008 ; Skinner and Fream 1997 ), ‘digital crime’ (Gogolin 2010 ), or ‘virtual crime’ (Brenner 2001 ). ‘Cybercrime’, however, has been the most popular in the public parlance (Wall 2004 ). A propensity considers crime directly against computer as cybercrime, while other tendency asserts that any crime committed via internet or related to a computer is cybercrime (Marsh and Melville 2008 ; Wall 2004 ). Hence, there is a distinction between ‘true cybercrime’ or ‘high-tech’ cybercrime and ‘low-tech’ cybercrime (Wagen and Pieters 2020 ). Council of Europe defines ‘any criminal offense committed against or with the help of a computer network’ as cybercrime (Abdullah and Jahan 2020 , p. 90). Despite different approaches, cybercrime generally includes not only new types of crimes which have just occurred after the invention of computer and internet (Holt and Bossler 2014 ; Drew 2020 ) but also traditional types of crimes which took the advantages of information communication technology (ICT) as vehicle for illegal behaviors (Luong 2021 ; Nguyen and Luong 2020 ; Luong et al. 2019 ). Two main cybercrime categories identified, respectively, are cyber-dependent crime (hacking, malware, denial of service attacks) and cyber-enable crime (phishing, identity theft, cyber romance scam, online shopping fraud). Nevertheless, there are several different classifications of cybercrime such as cybercrime against certain individuals, groups of individuals, computer networks, computer users, critical infrastructures, virtual entities (Wagen and Pieters 2020 ); cyber-trespass, cyber-deceptions, cyber-pornography, and cyber-violence (Wall 2001 ).
Due to the common prevalence of cybercrime, the increasing threats of cybercrime victimization are obviously serious. Cybercrime victimization has become a crucial research subfield in recent years (Wagen and Pieters 2020 ). It is difficult to differ “forms of online victimization” and “acts that actually constitute a crime”, then it is usual for researchers to focus less on perspective of criminal law and consider any negative experiences online as cybercrime (Näsi et al. 2015 , p. 2). It was likely to lead to practical gaps between theory and practice in terms of investigating the nexus of offender and victims on cyberspace. In the light of literature review, numerous specific aspects of cybercrime victimization were investigated by questionnaire surveys or interview survey such as the prevalence of cybercrime victimization (Näsi et al. 2015 ; Whitty and Buchanan 2012 ); causes and predictors of cybercrime victimization (Abdullah and Jahan 2020 ; Algarni et al. 2017 ; Ilievski 2016 ; Jahankhani 2013 ; Kirwan et al. 2018 ; Näsi et al. 2015 ; Reyns et al. 2019 ; Saad et al. 2018 ); and the relationship between social networking sites (SNS) and cybercrime victimization (Das and Sahoo 2011 ; Algarni et al. 2017 ; Benson et al. 2015 ; Seng et al. 2018 ). To some extent, therefore, the current study examines cybercrime victimization in the large scale, referring to any negative experiences on cyberspace or computer systems. Nevertheless, no bibliometric analysis was found to show the research trend and general landscape of this domain.
Bibliometric is a kind of statistical analysis which uses information in a database to provide the depth insight into the development of a specified area (Leung et al. 2017 ). The present study aims to address this research gap by providing a bibliometric review of the relevant SSCI articles in WoS database during the period of 2010–2020. The pattern of publications, the productivity of main elements (authors, journals, institutions, and countries/regions), statistic of citations, classification of key terms, research gaps, and other collaborations will be presented and discussed in section four and five after reviewing literatures and presenting our methods conducted. This article contributes an overview of research achievements pertaining to cybercrime victimization in the given period through statistical evidence and visual findings; assists researchers to perceive clearly about the key positions in research maps of this field, and obtain more suggestions to develop their own research direction.
Literature review
- Cybercrime victimization
Cybercrime victimization may exist in two levels including institutional and individual level (Näsi et al. 2015 ). For the former, victim is governments, institutions, or corporations, whereas for the latter, victim is a specific individual (Näsi et al. 2015 ). A wide range of previous studies concerned about individual level of victim and applied Lifestyle Exposure Theory (LET), Routine Activity Theory (RAT) and General Theory of Crime to explain cybercrime victimization (Choi 2008 ; Holt and Bossler 2009 ; Ngo and Paternoster 2011 ). Basing on these theories, situational and individual factors were supposed to play an important role in understanding cybercrime victimization (Choi 2008 ; Van Wilsem 2013 ). However, there was another argument that situational and individual factors did not predict cybercrime victimization (Ngo and Paternoster 2011 ; Wagen and Pieters 2020 ). Overall, most of those studies just focused only one distinctive kind of cybercrime such as computer viruses, malware infection, phishing, cyberbullying, online harassment, online defamation, identity theft, cyberstalking, online sexual solicitation, cyber romance scams or online consumer fraud. Referring to results of the prior research, some supported for the applicability of mentioned theories but other did not share the same viewpoint (Leukfeldt and Yar 2016 ). It was hard to evaluate the effect of LET or RAT for explanation of cybercrime victimization because the nature of examined cybercrime were different (Leukfeldt and Holt 2020 ; Leukfeldt and Yar 2016 ).
Previous research determined that cybercrime victimization was more common in younger group compared to older group because the young is the most active online user (Näsi et al. 2015 ; Oksanen and Keipi 2013 ) and males tended to become victims of cybercrime more than females in general (Näsi et al. 2015 ). However, findings might be different in research which concerned specific types of cybercrime. Women were more likely to be victims of the online romance scam (Whitty and Buchanan 2012 ) and sexual harassment (Näsi et al. 2015 ), while men recorded higher rate of victimization of cyber-violence and defamation. Other demographic factors were also examined such as living areas (Näsi et al. 2015 ), education (Oksanen and Keipi 2013 ; Saad et al. 2018 ) and economic status (Oksanen and Keipi 2013 ; Saad et al. 2018 ). Furthermore, several prior studies focus on the association of psychological factors and cybercrime victimization, including awareness and perception (Ariola et al. 2018 ; Saridakis et al. 2016 ), personality (Kirwan et al. 2018 ; Orchard et al. 2014 ; Parrish et al. 2009 ), self-control (Ilievski 2016 ; Ngo and Paternoster 2011 ; Reyns et al. 2019 ), fear of cybercrime (Lee et al. 2019 ), online behaviors (Al-Nemrat and Benzaïd 2015 ; Saridakis et al. 2016 ). Psychological factors were assumed to have effects on cybercrime victimization at distinctive levels.
Another perspective which was much concerned by researchers was the relationship between cybercrime victimization and SNS. SNS has been a fertile land for cybercriminals due to the plenty of personal information shared, lack of guard, the availability of communication channels (Seng et al. 2018 ), and the networked nature of social media (Vishwanath 2015 ). When users disclosed their personal information, they turned themselves into prey for predators in cyberspace. Seng et al. ( 2018 ) did research to understand impact factors on user’s decision to react and click on suspicious posts or links on Facebook. The findings indicated that participants’ interactions with shared contents on SNS were affected by their relationship with author of those contents; they often ignored the location of shared posts; several warning signals of suspicious posts were not concerned. Additionally, Vishwanath ( 2015 ) indicated factors that led users to fall victims on the SNS; Algarni et al. ( 2017 ) investigated users’ susceptibility to social engineering victimization on Facebook; and Kirwan et al. ( 2018 ) determined risk factors resulting in falling victims of SNS scam.
Bibliometric of cybercrime victimization
“Bibliometric” is a term which was coined by Pritchard in 1969 and a useful method which structures, quantifies bibliometric information to indicate the factors constituting the scientific research within a specific field (Serafin et al. 2019 ). Bibliometric method relies on some basic types of analysis, namely co-authorship, co-occurrence, citation, co-citation, and bibliographic coupling. This method was employed to various research domains such as criminology (Alalehto and Persson 2013 ), criminal law (Jamshed et al. 2020 ), marketing communication (Kim et al. 2019 ), social media (Chen et al. 2019 ; Gan and Wang 2014 ; Leung et al. 2017 ; Li et al. 2017 ; You et al. 2014 ; Zyoud et al. 2018 ), communication (Feeley 2008 ), advertising (Pasadeos 1985 ), education (Martí-Parreño et al. 2016 ).
Also, there are more and more scholars preferring to use bibliometric analysis on cyberspace-related subject such as: cyber behaviors (Serafin et al. 2019 ), cybersecurity (Cojocaru and Cojocaru 2019 ), cyber parental control (Altarturi et al. 2020 ). Serafin et al. ( 2019 ) accessed the Scopus database to perform a bibliometric analysis of cyber behavior. All documents were published by four journals: Cyberpsychology, Behavior and Social Networking (ISSN: 21522723), Cyberpsychology and Behavior (ISSN: 10949313) , Computers in Human Behavior (ISSN: 07475632) and Human–Computer Interaction (ISSN: 07370024), in duration of 2000–2018. Findings indicated the use of Facebook and other social media was the most common in research during this period, while psychological matters were less concerned (Serafin et al. 2019 ). Cojocaru and Cojocaru ( 2019 ) examined the research status of cybersecurity in the Republic of Moldavo, then made a comparison with the Eastern Europe countries’ status. This study employed bibliometric analysis of publications from three data sources: National Bibliometric Instrument (database from Republic of Moldavo), Scopus Elsevier and WoS. The Republic of Moldavo had the moderate number of scientific publications on cybersecurity; Russian Federation, Poland, Romania, Czech Republic, and Ukraine were the leading countries in Eastern Europe area (Cojocaru and Cojocaru 2019 ). Altarturi et al. ( 2020 ) was interested in bibliometric analysis of cyber parental control, basing on publications between 2000 and 2019 in Scopus and WoS. This research identified some most used keywords including ‘cyberbullying’, ‘bullying’, ‘adolescents’ and ‘adolescence’, showing their crucial position in the domain of cyber parental control (Altarturi et al. 2020 ). ‘Cyber victimization’ and ‘victimization’ were also mentioned as the common keywords by Altarturi et al. ( 2020 ). Prior research much focus on how to protect children from cyberbullying. Besides, four online threats for children were determined: content, contact, conduct and commercial threats (Altarturi et al. 2020 ).
Generally, it has been recorded several published bibliometric analyses of cyber-related issues but remained a lack of bibliometric research targeting cybercrime victimization. Thus, the present study attempts to fill this gap, reviewing the achievements of existed publications as well as updating the research trend in this field.
In detail, our current study aims to address four research questions (RQs):
What is overall distribution of publication based on year, institutions and countries, sources, and authors in cybercrime victimization?
Which are the topmost cited publications in terms of cybercrime victimization?
Who are the top co-authorships among authors, institutions, and countries in research cybercrime victimization?
What are top keywords, co-occurrences and research gaps in the field of cybercrime victimization?
Data collection procedure
Currently, among specific approaches in cybercrime’s fileds, WoS is “one of the largest and comprehensive bibliographic data covering multidisciplinary areas” (Zyoud et al. 2018 , p. 2). This paper retrieved data from the SSCI by searching publications of cybercrime victimization on WoS database to examine the growth of publication; top keywords; popular topics; research gaps; and top influential authors, institutions, countries, and journals in the academic community.
This paper employed Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) for data collection procedure. For timeline, we preferred to search between 2010 and 2020 on the WoS system with two main reasons. First, when the official update of the 2009 PRISMA Statement had ready upgraded with the specific guidelines and stable techniques, we consider beginning since 2010 that is timely to test. Secondly, although there are several publications from the early of 2021 to collect by the WoS, its updated articles will be continued until the end of the year. Therefore, we only searched until the end of 2020 to ensure the full updates.
To identify publications on cybercrime victimization, the study accessed WoS and used two keywords for searching: ‘cybercrime victimization’ or ‘cyber victimization’ after testing and looking for some terminology-related topics. Accordingly, the paper applied a combination of many other searching terms besides two selected words such as “online victimization”, “victim of cybercrime”, “phishing victimization”, “online romance victimization”, “cyberstalking victim”, “interpersonal cybercrime victimization”, or “sexting victimization”, the results, however, were not really appropriate. A lot of papers did not contain search keywords in their titles, abstracts, keywords and were not relavant to study topic. After searching with many different terms and comparing the results, the current study selected the two search terms for the most appropriate articles. The query result consisted of 962 documents. Basing on the result from preliminary searching, retrieved publications were refined automatically on WoS by criteria of timespan, document types, language, research areas, and WoS Index as presented in Table 1 . Accordingly, the criteria for automatic filter process were basic information of an articles and classified clearly in WoS system so the results reached high accuracy. The refined results are 473 articles.
After automatic filters, file of data was converted to Microsoft Excel 2016 for screening. The present study examined titles and abstracts of 473 articles to assess the eligibility of each publication according to the relevance with given topic. There are 387 articles are eligible,while 86 irrelevant publications were excluded.
Data analysis
Prior to data analysis, the raw data were cleaned in Microsoft Excel 2016. Different forms of the same author’s name were corrected for consistency, for example “Zhou, Zong-Kui” and “Zhou Zongkui”, “Van Cleemput, Katrien” and “Van Cleemput, K.”, “Williams, Matthew L.” and “Williams, Matthew”. Similarly, different keywords (single/plural or synonyms) used for the same concept were identified and standardized such as “victimization” and “victimisation”; “adolescent” and “adolescents”; “cyber bullying”, “cyber-bullying” and “cyberbullying”; “routine activity theory” and “routine activities theory”.
The data were processed by Microsoft Excel 2016 and VOS Viewer version 1.6.16; then it was analyzed according to three main aspects. First, descriptive statistic provided evidence for yearly distribution and growth trend of publications, frequency counts of citations, the influential authors, the predominant journals, the top institutions and countries/territories, most-cited publications. Second, co-authorship and co-occurrence analysis were constructed and visualized by VOS Viewer version 1.6.16 to explore the network collaborations. Finally, the current study also investigated research topics through content analysis of keywords. The authors’ keywords were classified into 15 themes, including: #1 cybercrime; #2 sample and demographic factors; #3 location; #4 theory; #5 methodology; #6 technology, platforms and related others; #7 psychology and mental health; #8 physical health; #9 family; #10 school; #11 society; #12 crimes and deviant behaviors; #13 victim; #14 prevention and intervention; and #15 others. Besides, the study also added other keywords from titles and abstracts basing on these themes, then indicated aspects examined in previous research.
In this section, all findings corresponding with four research questions identified at the ouset of this study would be illustrated (Fig. 1 ).
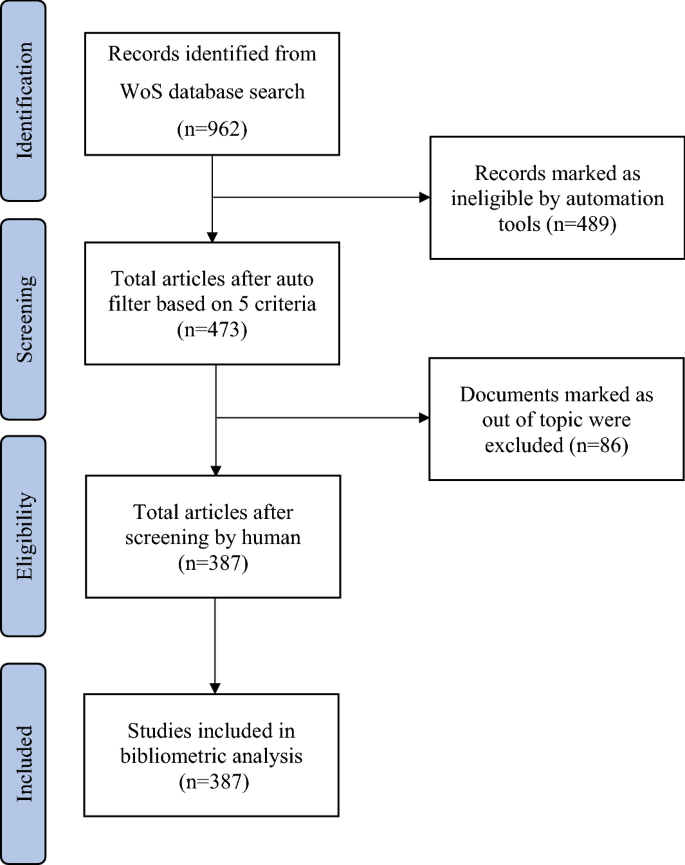
PRISMA diagram depicts data collection from WoS database
Distribution of publication
Distribution by year, institutions and countries.
Basing on retrieved data, it was witnessed an increasing trend of articles relevant to cybercrime victimization in SSCI list during the time of 2010–2020 but it had slight fluctuations in each year as shown in Fig. 2 . The total number of articles over this time was 387 items, which were broken into two sub-periods: 2010–2014 and 2015–2020. It is evident that the latter period demonstrated the superiority of the rate of articles (79.33%) compared to the previous period (20.67%). The yearly quantity of publications in this research subject was fewer than forty before 2015. Research of cybercrime victimization reached a noticeable development in 2016 with over fifty publications, remained the large number of publications in the following years and peaked at 60 items in 2018.
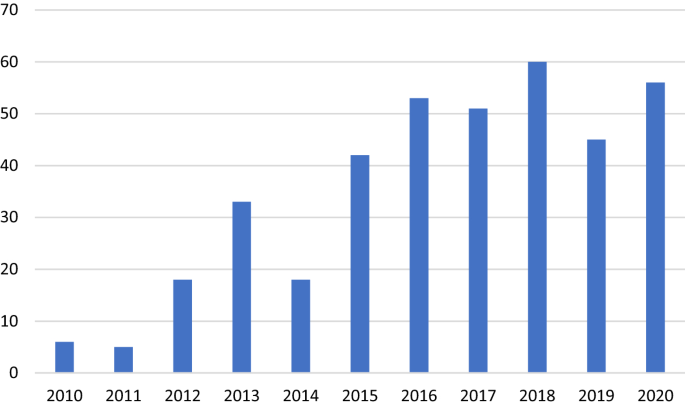
Annual distribution of publications
Distribution by institutions and countries
Table 2 shows the top contributing institutions according to the quantity of publications related to cybercrime victimization. Of the top institutions, four universities were from the USA, two ones were from Spain, two institutions were from Australia and the rest ones were from Czech Republic, Belgium, Greece, and Austria. Specifically, Masaryk University (17 documents) became the most productive publishing institution, closely followed by Michigan State University (16 documents). The third and fourth places were University of Antwerp (13 documents) and Weber State University (10 documents). Accordingly, the institutions from The USA and Europe occupied the vast majority.
In Table 2 , University of Seville (total citations: 495, average citations: 70.71) ranked first and University of Cordoba (total citations: 484, average citations: 60.50) stayed at the second place in both total citations and average citations.
Referring to distribution of publications by countries, there were 45 countries in database contributing to the literature of cybercrime victimization. The USA recorded the highest quantity of papers, creating an overwhelming difference from other countries (159 documents) as illustrated in Fig. 3 . Of the top productive countries, eight European countries which achieved total of 173 publications were England (39 documents), Spain (34 documents), Germany (22 documents), Netherlands (18 documents), Italy (17 documents) and Czech Republic (17 documents), Belgium (14 documents), Greece (12 documents). Australia ranked the fourth point (32 documents), followed by Canada (30 documents). One Asian country which came out seventh place, at the same position with Netherlands was China (18 documents).
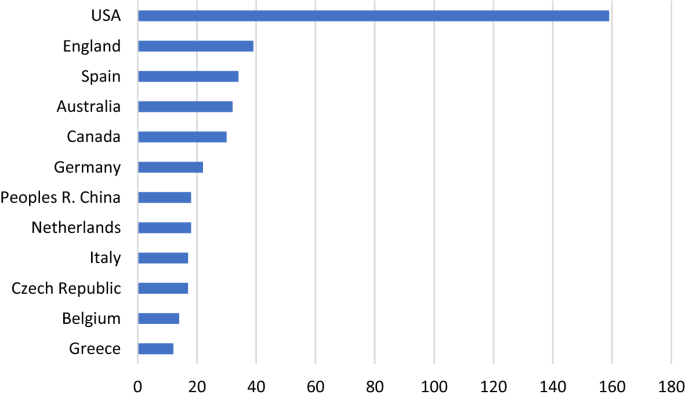
Top productive countries based on the number of publications
Distribution by sources
Table 3 enumerates the top leading journals in the number of publications relevant to cybercrime victimization. The total publications of the first ranking journal— Computers in Human Behavior were 56, over twice as higher as the second raking journal— Cyberpsychology, Behavior and Social Networking (24 articles). Most of these journals have had long publishing history, starting their publications before 2000. Only three journals launched after 2000, consisting of Journal of School Violence (2002), Cyberpsychology: Journal of Psychosocial Research on Cyberspace (2007) and Frontiers in Psychology (2010). Besides, it is remarked that one third of the top journals focuses on youth related issues: Journal of Youth and Adolescence , Journal of Adolescence, School Psychology International and Journal of School Violence .
In Table 3 , relating to total citations, Computers in Human Behavior remained the first position with 2055 citations. Journal of Youth and Adolescence had total 1285 citations, ranked second and followed by Aggressive Behavior with 661 citations. In terms of average citations per documents, an article of Journal of Youth and Adolescence was cited 67.63 times in average, much higher than average citations of one in Computers in Human Behavior (36.70 times). The other journals which achieved the high number of average citations per document were School Psychology International (59.00 times), Journal of Adolescence (44.83 times) and Aggressive Behavior (44.07 times).
Distribution by authors
Table 4 displays ten productive authors based on article count; total citations of each author and their average citations per document are also included. Michelle F. Wright from Pennsylvania State University ranked first with twenty publications, twice as higher as the second positions, Thomas J. Holt (10 articles) from Michigan State University and Bradford W. Reyns (10 articles) from Weber State University. Rosario Ortega-Ruiz from University of Cordoba stayed at the third place in terms of total publications but the first place in aspect of total citations (483 citations) and the average citations (60.38 times).
Of the most productive authors based on total publications, there were three authors from universities in the USA; one from the university in Canada (Brett Holfeld); the others were from institutions in Euro, including Spain (Rosario Ortega-Ruiz), Greece (Constantinos M. Kokkinos) and Belgium (Heidi Vandebosch), Netherlands (Rutger Leukfeldt) and Austria (Takuya Yanagida and Christiane Spiel).
Most-cited publications
The most-cited literature items are displayed in Table 5 . The article which recorded the highest number of citations was ‘Psychological, Physical, and Academic Correlates of Cyberbullying and Traditional Bullying’ (442 citations) by Robin M. Kowalski et al. published in Journal of Adolescent Health , 2013. Seven of ten most-cited articles were about cyberbullying; focused on youth population; made comparisons between cyberbullying and traditional bullying; analyzed the impact of several factors such as psychological, physical, academic factors or use of Internet; discussed on preventing strategies. The other publications studied victimization of cyberstalking and cyber dating abuse. All most-cited articles were from 2015 and earlier.
Of the top productive authors, only Bradford W. Reyns had an article appeared in the group of most-cited publications. His article ‘Being Pursued Online: Applying Cyberlifestyle-Routine Activities Theory to Cyberstalking Victimization’ (2011) was cited 172 times.
- Co-authorship analysis
“Scientific collaboration is a complex social phenomenon in research” (Glänzel and Schubert 2006 , p. 257) and becomes the increasing trend in individual, institutional and national levels. In bibliometric analysis, it is common to assess the productivity and international collaboration of research; identify key leading researchers, institutions, or countries (E Fonseca et al. 2016 ) as well as potential collaborators in a specific scientific area (Romero and Portillo-Salido 2019 ) by co-authorship analysis which constructs networks of authors and countries (Eck and Waltman 2020 ).
This section analyses international collaboration relevant to research of cybercrime victimization among authors, institutions, and countries during 2010–2020 through visualization of VOS Viewer software.
Collaboration between authors
Referring to the threshold of choose in this analysis, minimum number of documents of author is three and there were 80 authors for final results. Figure 4 illustrates the relationships between 80 scientists who study in subject of cybercrime victimization during 2010–2020. It shows several big groups of researchers (Wright’s group, Vandebosch’s group, or Holt’s group), while numerous authors had limited or no connections to others (Sheri Bauman, Michelle K. Demaray or Jennifer D. Shapka).
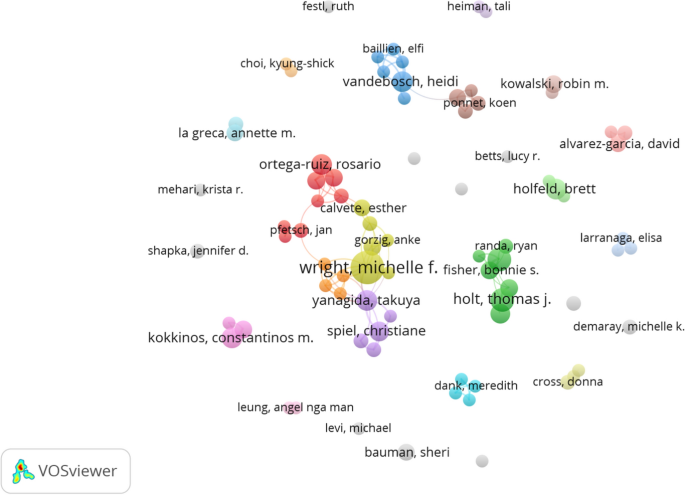
Collaboration among authors via network visualization (threshold three articles for an author, displayed 80 authors)
Figure 5 displayed a significant network containing 23 authors who were active in collaboration in detail. The displayed items in Fig. 5 are divided into five clusters coded with distinctive colors, including red, green, blue, yellow, and purple. Each author item was represented by their label and a circle; the size of label and circle are depended on the weight of the item, measured by the total publications (Eck and Waltman 2020 ). The thickness of lines depends on the strength of collaboration (Eck and Waltman 2020 ).
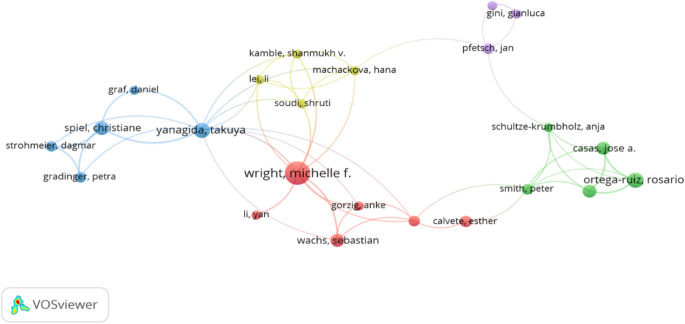
Collaboration among authors via network visualization (threshold three articles for an author, displayed 23 authors)
The most significant cluster was red one which is comprised of six researchers: Michelle F. Wright, Sebastian Wachs, Yan Li, Anke Gorzig, Manuel Gamez-Guadix and Esther Calvete. The remarked author for the red cluster was Michelle F. Wright whose value of total link strength is 24. She had the strongest links with Sebastian Wachs; closely link with Yan Li, Anke Gorzig, Manuel Gamez-Guadix and collaborated with authors of yellow cluster, including Shanmukh V. Kamble, Li Lei, Hana Machackova, Shruti Soudi as well as Takuya Yanagida of blue cluster. Michelle F. Wright who obtained the largest number of published articles based on criteria of this study made various connections with other scholars who were from many different institutions in the world. This is also an effective way to achieve more publications.
Takuya Yanagida was the biggest node for the blue cluster including Petra Gradinger, Daniel Graf, Christiane Spiel, Dagmar Strohmeier. Total link strength for Takuya Yanagida was 28; twelve connections. It is observed that Takuya Yanagida’ s research collaboration is definitely active. Besides, other research groups showed limited collaborations comparing with the red and blue ones.
Collaboration between institutions
The connections among 156 institutions which published at least two documents per one are shown in Fig. 6 . Interestingly, there is obvious connections among several distinctive clusters which were coded in color of light steel blue, orange, purple, steel blue, green, red, yellow, light red, dark turquoise, light blue, brown and light green. These clusters created a big chain of connected institutions and were in the center of the figure, while other smaller clusters or unlinked bubbles (gray color) were distributed in two sides. The biggest chain consisted of most of productive institutions such as Masaryk University, Michigan State University, University of Antwerp, Weber State University, University of Cordoba, Edith Cowan University, University of Cincinnati, University of Victoria, University of Vienna, and University of Seville.
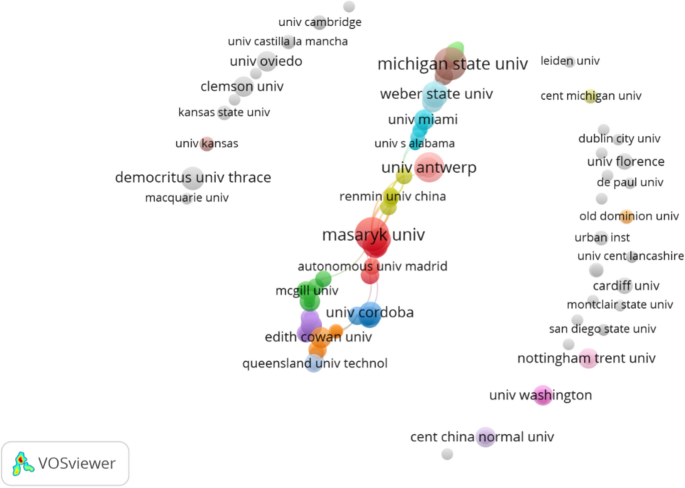
Collaboration among institutions via network visualization (threshold two articles for an institution, 156 institutions were displayed)
Light steel blue and orange clusters presented connections among organizations from Australia. Light green included institutions from Netherland, while turquoise and light blue consisted of institutions from the USA. Yellow cluster was remarked by the various collaborations among institutions from China and Hong Kong Special Administrative Region (Renmin University of China and South China Normal University, University of Hong Kong, the Hong Kong Polytechnic University and the Chinese University of Hong Kong), the USA (University of Virginia), Cyprus (Eastern Mediterranean University), Japan (Shizuoka University), India (Karnataka University) and Austria (University Applied Sciences Upper Austria). Central China Normal University is another Chinese institution which appeared in Fig. 5 , linking with Ministry of Education of the People’s Republic of China, Suny Stony Brook and University of Memphis from the USA.
Masaryk University and Michigan State University demonstrated their productivity in both the quantity of publications and the collaboration network. They were active in research collaboration, reaching twelve and eleven links, respectively, with different institutions, but focused much on networking with institutions in the USA and Europe.
Collaboration between countries
The collaboration among 45 countries which published at least one SSCI documents of cybercrime victimization during the given period was examined in VOS Viewer but just 42 items were displayed via overlay visualization. Figure 7 depicts the international collaborations among significant countries. The USA is the biggest bubble due to its biggest number of documents and shows connections with 26 countries/regions in Euro, Asia, Australia, Middle East. Excepting European countries, England collaborate with the USA, Australia, South Korea, Japan, Thailand, Singapore, Sri Lanka, and Colombia. Spain and Germany almost focus on research network within Euro. China has the strongest tie with the USA, link with Australia, Germany, Czech Republic, Austria, Cyprus and Turkey, Japan, Indian, Vietnam.
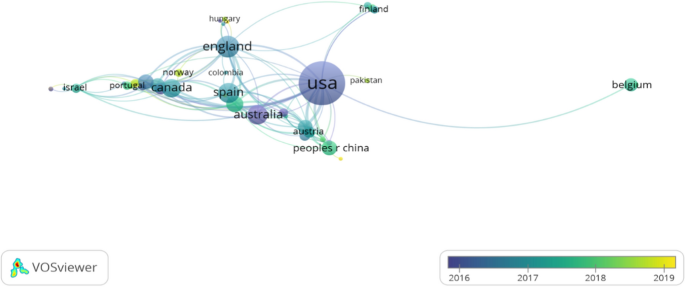
Collaboration among countries via overlay visualization
Color bar in Fig. 7 is determined by the average publication year of each country and the color of circles based on it. It is unsurprised that the USA, Australia, England, or Spain shows much research experience in this field and maintain the large number of publications steadily. Interestingly, although the average publication year of South Korea or Cyprus was earlier than other countries (purple color), their quantities of documents were moderate. The new nodes (yellow circles) in the map included Vietnam, Norway, Pakistan, Ireland, Scotland, Switzerland.
Keywords and co-occurrence
The present paper examined the related themes and contents in research of cybercrime victimization during 2010–2020 through collecting author keywords, adding several keywords from tiles and abstracts. Besides, this study also conducted co-occurrence analysis of author keywords to show the relationships among these keywords.
The keywords were collected and categorized into 15 themes in Table 6 , including cybercrime; sample and demographic factors; location; theory; methodology; technology, platform, and related others; psychology and mental health; physical health; family; school; society; crimes and other deviant behaviors; victim; prevention and intervention; and others.
In the theme of cybercrime, there were numerous types of cybercrimes such as cyberbullying, cyber aggression, cyberstalking, cyber harassment, sextortion and other cyber dating crimes, cyber fraud, identity theft, phishing, hacking, malware, or ransomware. Generally, the frequency of interpersonal cybercrimes or cyber-enable crimes was much higher than cyber-dependent crimes. Cyberbullying was the most common cybercrime in research.
Relating to sample and demographic factors, there were sample of children, adolescent, adults, and the elder who were divided into more detail levels in each research; however, adolescent was the most significant sample. Besides, demographic factor of gender received a remarked concern from scholars.
It is usual that most of the research were carried out in one country, in popular it was the USA, Spain, Germany, England, Australia, Canada or Netherland but sometimes the new ones were published such as Chile, Vietnam, Thailand or Singapore. It was witnessed that some studies showed data collected from a group of countries such as two countries (Canada and the United State), three countries (Israel, Litva, Luxembourg), four countries (the USA, the UK, Germany, and Finland), or six Europe countries (Spain, Germany, Italy, Poland, the United Kingdom and Greece).
A wide range of theories were applied in this research focusing on criminological and psychological theories such as Routine Activities Theory, Lifestyle—Routine Activities Theory, General Strain Theory, the Theory of Reasoned Action or Self-control Theory.
Table 6 indicated a lot of different research methods covering various perspective of cybercrime victimization: systematic review, questionnaire survey, interview, experiment, mix method, longitudinal study, or cross-national research; many kinds of analysis such as meta-analysis, social network analysis, latent class analysis, confirmatory factor analysis; and a wide range of measurement scales which were appropriate for each variable.
Topic of cybercrime victimization had connections with some main aspects of technology (information and communication technologies, internet, social media or technology related activities), psychology (self-esteem, fear, attitude, personality, psychological problems, empathy, perceptions or emotion), physical health, family (parents), school (peers, school climate), society (norms, culture, social bonds), victim, other crimes (violence, substance use), prevention and intervention.
Co-occurrence analysis was performed with keywords suggested by authors and the minimum number of occurrences per word is seven. The result showed 36 frequent keywords which clustered into five clusters as illustrated in Fig. 8 .
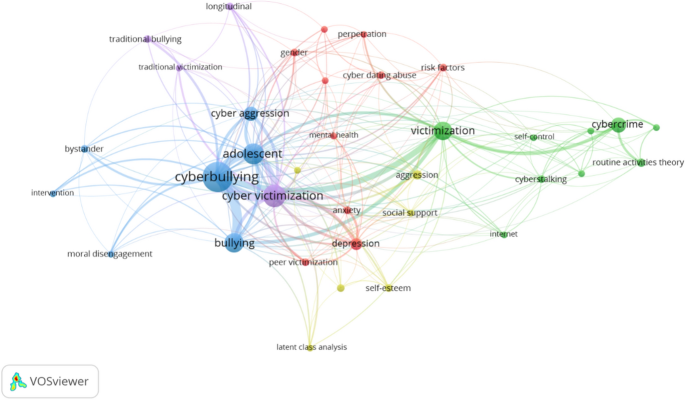
Co-occurrence between author keywords via network visualization (the minimum number of occurrences per word is seven, 36 keywords were displayed)
Figure 8 illustrates some main issues which were concerned in subject of cybercrime victimization, as well as the relationship among them. Fifteen most frequent keywords were presented by big bubbles, including: ‘cyberbullying’ (174 times), ‘cyber victimization’ (90 times), ‘adolescent’ (79 times), ‘bullying’ (66 times), ‘victimization’ (56 times), ‘cybercrime’ (40 times), ‘cyber aggression’ (37 times), ‘depression’ (23 times), ‘aggression’ (14 times), ‘routine activities theory’ (13 times), ‘cyberstalking’ (11 times), ‘gender’ (11 times), ‘longitudinal’ (10 times), ‘peer victimization’ (10 times) and ‘self-esteem’ (10 times).
‘Cyberbullying’ linked with many other keywords, demonstrating the various perspectives in research of this topic. The thick lines which linked ‘cyberbullying’ and ‘bullying’, ‘adolescent’, ‘cyber victimization’, ‘victimization’ showed the strong connections between them; there were close relationship between ‘cyber aggression’, ‘bystander”, ‘self-esteem’ or ‘moral disengagement’ and ‘cyberbullying’.
‘Cybercrime’ had strong links with ‘victimization’, ‘routine activities theory’. In Fig. 8 , the types of cybercrime which occurred at least seven times were: cyberbullying, cyber aggression, hacking, cyberstalking, and cyber dating abuse.
The increasing trend over the years reveals the increasing concern of scholarly community on this field, especially in the boom of information technology and other communication devices and the upward trend in research of cyberspace-related issues (Altarturi et al. 2020 ; Leung et al. 2017 ; Serafin et al. 2019 ). It predicts the growth of cybercrime victimization research in future.
Psychology was the more popular research areas in database, defeating criminology penology. As part of the ‘human factors of cybercrime’, human decision-making based on their psychological perspectives plays as a hot topic in cyber criminology (Leukfeldt and Holt 2020 ). Then, it is observed that journals in psychology field was more prevalent in top of productive sources. Besides, journal Computers in Human Behavior ranked first in total publications, but Journal of Youth and Adolescence ranked higher place in the average citations per document. Generally, top ten journals having highest number of publications on cybercrime victimization are highly qualified ones and at least 10 years in publishing industry.
The USA demonstrated its leading position in the studied domain in terms of total publications as well as the various collaborations with other countries. The publications of the USA occupied much higher than the second and third countries: England and Spain. It is not difficult to explain for this fact due to the impressive productivity of institutions and authors from the USA. A third of top twelve productive institutions were from the USA. Three leading positions of top ten productive authors based on document count were from institutions of the USA, number one was Michelle F. Wright; others were Thomas J. Holt and Bradford W. Reyns.
Furthermore, these authors also participated in significant research groups and become the important nodes in those clusters. The most noticeable authors in co-authors network were Michelle F. Wright. The US institutions also had strong links in research network. The USA was likely to be open in collaboration with numerous countries from different continents in the world. It was assessed to be a crucial partner for others in the international co-publication network (Glänzel and Schubert 2006 ).
As opposed to the USA, most of European countries prefer developing research network within Europe and had a limited collaboration with other areas. Australia, the USA, or Japan was in a small group of countries which had connections with European ones. Nevertheless, European countries still showed great contributions for research of cybercrime victimization and remained stable links in international collaboration. The prominent authors from Euro are Rosario Ortega-Ruiz, Constantinos M. Kokkinos or Rutger Leukfeldt.
It is obvious that the limited number of publications from Asia, Middle East, Africa, or other areas resulted in the uncomprehensive picture of studied subject. For example, in the Southeast Asia, Malaysia and Vietnam lacked the leading authors with their empirical studies to review and examine the nature of cybercrimes, though they are facing to practical challenges and potential threats in the cyberspace (Lusthaus 2020a , b ). The present study indicated that Vietnam, Ireland, or Norway was the new nodes and links in research network.
Several nations which had a small number of publications such as Vietnam, Thailand, Sri Lanka, or Chile started their journey of international publications. It is undeniable that globalization and the context of global village (McLuhan 1992 ) requires more understanding about the whole nations and areas. Conversely, each country or area also desires to engage in international publications. Therefore, new nodes and clusters are expected to increase and expand.
The findings indicated that cyberbullying was the most popular topic on research of cybercrime victimization over the given period. Over a half of most-cited publications was focus on cyberbullying. Additionally, ‘cyberbullying’ was the most frequent author keyword which co-occurred widely with distinctive keywords such as ‘victimization’, ‘adolescents’, ‘bullying’, ‘social media’, ‘internet’, ‘peer victimization’ or ‘anxiety’.
By reviewing keywords, several research gaps were indicated. Research samples were lack of population of the children and elders, while adolescent and youth were frequent samples of numerous studies. Although young people are most active in cyberspace, it is still necessary to understand other populations. Meanwhile, the elderly was assumed to use information and communication technologies to improve their quality of life (Tsai et al. 2015 ), their vulnerability to the risk of cybercrime victimization did not reduce. Those older women were most vulnerable to phishing attacks (Lin et al. 2019 ; Oliveira et al. 2017 ). Similarly, the population of children with distinctive attributes has become a suitable target for cybercriminals, particularly given the context of increasing online learning due to Covid-19 pandemic impacts. These practical gaps should be prioritized to focus on research for looking the suitable solutions in the future. Besides, a vast majority of research were conducted in the scope of one country; some studies collected cross-national data, but the number of these studies were moderate and focused much on developed countries. There are rooms for studies to cover several countries in Southeast Asia or South Africa.
Furthermore, although victims may be both individuals and organizations, most of research concentrated much more on individuals rather than organizations or companies. Wagen and Pieters ( 2020 ) indicated that victims include both human and non-human. They conducted research covering cases of ransomware victimization, Bonet victimization and high-tech virtual theft victimization and applying Actor-Network Theory to provide new aspect which did not aim to individual victims. The number of this kind of research, however, was very limited. Additionally, excepting cyberbullying and cyber aggression were occupied the outstanding quantity of research, other types of cybercrime, especially, e-whoring, or social media-related cybercrime should still be studied more in the future.
Another interesting topic is the impact of family on cybercrime victimization. By reviewing keyword, it is clear that the previous studies aimed to sample of adolescent, hence, there are many keywords linking with parents such as ‘parent-adolescent communication’, ‘parent-adolescent information sharing’, ‘parental mediation’, ‘parental monitoring of cyber behavior’, ‘parental style’. As mentioned above, it is necessary to research more on sample of the elder, then, it is also essential to find out how family members affect the elder’s cybercrime victimization.
It is a big challenge to deal with problems of cybercrime victimization because cybercrime forms become different daily (Näsi et al. 2015 ). Numerous researchers engage in understanding this phenomenon from various angles. The current bibliometric study assessed the scholarly status on cybercrime victimization during 2010–2020 by retrieving SSCI articles from WoS database. There is no study that applied bibliometric method to research on the examined subject. Hence, this paper firstly contributed statistical evidence and visualized findings to literature of cybercrime victimization.
Statistical description was applied to measure the productive authors, institutions, countries/regions, sources, and most-cited documents, mainly based on publication and citation count. The international collaborations among authors, institutions, and countries were assessed by co-authors, while the network of author keywords was created by co-occurrence analysis. The overall scholarly status of cybercrime victimization research was drawn clearly and objectively. The research trend, popular issues and current gaps were reviewed, providing numerous suggestions for policymakers, scholars, and practitioners about cyber-related victimization (Pickering and Byrne 2014 ). Accordingly, the paper indicated the most prevalent authors, most-cited papers but also made summary of contributions of previous research as well as identified research gaps. First, this article supports for PhD candidates or early-career researchers concerning about cybercrime victimization. Identifying the leading authors, remarked journals, or influencing articles, gaps related to a specific research topic is important and useful task for new researchers to start their academic journey. Although this information is relatively simple, it takes time and is not easy for newcomers to find out, especially for ones in poor or developing areas which have limited conditions and opportunities to access international academic sources. Thus, the findings in the current paper provided for them basic but necessary answers to conduct the first step in research. Secondly, by indicating research gaps in relevance to sample, narrow topics or scope of country, the paper suggests future study fulfilling them to complete the field of cybercrime victimization, especial calling for publications from countries which has had a modest position in global research map. Science requires the balance and diversity, not just focusing on a few developed countries or areas. Finally, the present study assists researchers and institutions to determined strategy and potential partners for their development of research collaborations. It not only improve productivity of publication but also create an open and dynamic environment for the development of academic field.
Despite mentioned contributions, this study still has unavoidable limitations. The present paper just focused on SSCI articles from WoS database during 2010–2020. It did not cover other sources of databases that are known such as Scopus, ScienceDirect, or Springer; other types of documents; the whole time; or articles in other languages excepting English. Hence it may not cover all data of examined subject in fact. Moreover, this bibliometric study just performed co-authorship and co-occurrence analysis. The rest of analysis such as citation, co-citation and bibliographic coupling have not been conducted. Research in the future is recommended to perform these kinds of assessment to fill this gap. To visualize the collaboration among authors, institutions, countries, or network of keywords, this study used VOS Viewer software and saved the screenshots as illustrations. Therefore, not all items were displayed in the screenshot figures.
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
In the ‘commemorating a decade in existence of the International Journal of Cyber Criminoogy’, Ngo and Jaishankar ( 2017 ) called for further research with focusing on five main areas in the Cyber Criminiology, including (1) defining and classifying cybercrime, (2) assessing the prevalence, nature, and trends of cybercrime, (3) advancing the field of cyber criminology, (4) documenting best practices in combating and preventing cybercrime, and (5) cybercrime and privacy issues.
Abdullah ATM, Jahan I (2020) Causes of cybercrime victimization: a systematic literature review. Int J Res Rev 7(5):89–98
Google Scholar
Al-Nemrat A, Benzaïd C (2015) Cybercrime profiling: Decision-tree induction, examining perceptions of internet risk and cybercrime victimisation. In: Proceedings—14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, TrustCom 2015, vol 1, pp 1380–1385. https://doi.org/10.1109/Trustcom.2015.534
Alalehto TI, Persson O (2013) The Sutherland tradition in criminology: a bibliometric story. Crim Justice Stud 26(1):1–18
Article Google Scholar
Algarni A, Xu Y, Chan T (2017) An empirical study on the susceptibility to social engineering in social networking sites: the case of Facebook. Eur J Inf Syst 26(6):661–687
Altarturi HHM, Saadoon M, Anuar NB (2020) Cyber parental control: a bibliometric study. Child Youth Serv Rev. https://doi.org/10.1016/j.childyouth.2020.105134
Ariola B, Laure ERF, Perol ML, Talines PJ (2018) Cybercrime awareness and perception among Students of Saint Michael College of Caraga. SMCC Higher Educ Res J 1(1):1. https://doi.org/10.18868/cje.01.060119.03
Benson V, Saridakis G, Tennakoon H (2015) Purpose of social networking use and victimisation: are there any differences between university students and those not in HE? Comput Hum Behav 51:867–872
Brenner SW (2001) Is there such a thing as “rough”? Calif Crim Law Rev 4(1):348–349. https://doi.org/10.3109/09637487909143344
Chen X, Wang S, Tang Y, Hao T (2019) A bibliometric analysis of event detection in social media. Online Inf Rev 43(1):29–52. https://doi.org/10.1108/OIR-03-2018-0068
Choi K (2008) Computer Crime Victimization and Integrated Theory: an empirical assessment. Int J Cyber Criminol 2(1):308–333
Cojocaru I, Cojocaru I (2019) A bibliomentric analysis of cybersecurity research papers in Eastern Europe: case study from the Republic of Moldova. In: Central and Eastern European E|Dem and E|Gov Days, pp 151–161
Das B, Sahoo JS (2011) Social networking sites—a critical analysis of its impact on personal and social life. Int J Bus Soc Sci 2(14):222–228
Drew JM (2020) A study of cybercrime victimisation and prevention: exploring the use of online crime prevention behaviours and strategies. J Criminol Res Policy Pract 6(1):17–33. https://doi.org/10.1108/JCRPP-12-2019-0070
E Fonseca B, Sampaio, de Araújo Fonseca MV, Zicker F (2016). Co-authorship network analysis in health research: method and potential use. Health Res Policy Syst 14(1):1–10. https://doi.org/10.1186/s12961-016-0104-5
Feeley TH (2008) A bibliometric analysis of communication journals from 2002 to 2005. Hum Commun Res 34:505–520
Gan C, Wang W (2014) A bibliometric analysis of social media research from the perspective of library and information science. IFIP Adv Inf Commun Technol 445:23–32. https://doi.org/10.1007/978-3-662-45526-5_3
Glänzel W, Schubert A (2006) Analysing scientific networks through co-authorship. Handb Quant Sci Technol Res. https://doi.org/10.1007/1-4020-2755-9_12
Gogolin G (2010) The digital crime tsunami. Digit Investig 7(1–2):3–8. https://doi.org/10.1016/j.diin.2010.07.001
Holt TJ, Bossler AM (2009) Examining the applicability of lifestyle-routine activities theory for cybercrime victimization. Deviant Behav 30(1):1–25. https://doi.org/10.1080/01639620701876577
Holt TJ, Bossler AM (2014) An assessment of the current state of cybercrime scholarship. Deviant Behav 35(1):20–40. https://doi.org/10.1080/01639625.2013.822209
Ilievski A (2016) An explanation of the cybercrime victimisation: self-control and lifestile/routine activity theory. Innov Issues Approaches Soc Sci 9(1):30–47. https://doi.org/10.12959/issn.1855-0541.iiass-2016-no1-art02
Insa F (2007) The Admissibility of Electronic Evidence in Court (A.E.E.C.): Fighting against high-tech crime—results of a European study. J Digital Forensic Pract 1(4):285–289. https://doi.org/10.1080/15567280701418049
Jahankhani H (2013) Developing a model to reduce and/or prevent cybercrime victimization among the user individuals. Strategic Intell Manag. https://doi.org/10.1016/b978-0-12-407191-9.00021-1
Jamshed J, Naeem S, Ahmad K (2020) Analysis of Criminal Law Literature: a bibliometric study from 2010–2019. Library Philos Pract
Kim J, Kang S, Lee KH (2019) Evolution of digital marketing communication: Bibliometric analysis and networs visualization from key articles. J Bus Res
Kirwan GH, Fullwood C, Rooney B (2018) Risk factors for social networking site scam victimization among Malaysian students. Cyberpsychol Behav Soc Netw 21(2):123–128. https://doi.org/10.1089/cyber.2016.0714
Lee S-S, Choi KS, Choi S, Englander E (2019) A test of structural model for fear of crime in social networking sites A test of structural model for fear of crime in social networking sites. Int J Cybersecur Intell Cybercrime 2(2):5–22
Leukfeldt R, Holt T (eds) (2020) The human factor of cybercrime. Routledge, New York
Leukfeldt ER, Yar M (2016) Applying routine activity theory to cybercrime: a theoretical and empirical analysis. Deviant Behav 37(3):263–280. https://doi.org/10.1080/01639625.2015.1012409
Leung XY, Sun J, Bai B (2017) Bibliometrics of social media research: a co-citation and co-word analysis. Int J Hosp Manag 66:35–45. https://doi.org/10.1016/j.ijhm.2017.06.012
Li Q, Wei W, Xiong N, Feng D, Ye X, Jiang Y (2017) Social media research, human behavior, and sustainable society. Sustainability 9(3):384. https://doi.org/10.3390/su9030384
Lin T, Capecci DE, Ellis DM, Rocha HA, Dommaraju S, Oliveira DS, Ebner NC (2019) Susceptibility to spear-phishing emails: effects of internet user demographics and email content. ACM Trans Comput-Hum Interact 26(5):1–28. https://doi.org/10.1145/3336141
Luong TH (2021) Prevent and combat sexual assault and exploitation of children on cyberspace in Vietnam: situations, challenges, and responses. In: Elshenraki H (ed) Combating the exploitation of children in cyberspace: emerging research and opportunities. IGI Global, Hershey, pp 68–94
Chapter Google Scholar
Luong HT, Phan HD, Van Chu D, Nguyen VQ, Le KT, Hoang LT (2019) Understanding cybercrimes in Vietnam: from leading-point provisions to legislative system and law enforcement. Int J Cyber Criminol 13(2):290–308. https://doi.org/10.5281/zenodo.3700724
Lusthaus J (2020a) Cybercrime in Southeast Asia: Combating a Global Threat Locally. Retrieved from Canberra, Australia: https://s3-ap-southeast-2.amazonaws.com/ad-aspi/202005/Cybercrime%20in%20Southeast%20Asia.pdf?naTsKQp2jtSPYsWpSo4YmE1sVBNv_exJ
Lusthaus J (2020b) Modelling cybercrime development: the case of Vietnam. In: Leukfeldt R, Holt T (eds) The human factor of cybercrime. Routledge, New York, pp 240–257
Marsh I, Melville G (2008) Crime justice and the media. Crime Justice Med. https://doi.org/10.4324/9780203894781
Martí-Parreño J, Méndez-Ibáñezt E, Alonso-Arroyo A (2016) The use of gamification in education: a bibliometric and text mining analysis. J Comput Assist Learn
McLuhan M (1992) The Global Village: Transformations in World Life and Media in the 21st Century (Communication and Society). Oxford University Press, Oxford
Näsi M, Oksanen A, Keipi T, Räsänen P (2015) Cybercrime victimization among young people: a multi-nation study. J Scand Stud Criminol Crime Prev. https://doi.org/10.1080/14043858.2015.1046640
Ngo F, Jaishankar K (2017) Commemorating a decade in existence of the international journal of cyber criminology: a research agenda to advance the scholarship on cyber crime. Int J Cyber Criminol 11(1):1–9
Ngo F, Paternoster R (2011) Cybercrime victimization: an examination of individual and situational level factors. Int J Cyber Criminol 5(1):773
Nguyen VT, Luong TH (2020) The structure of cybercrime networks: transnational computer fraud in Vietnam. J Crime Justice. https://doi.org/10.1080/0735648X.2020.1818605
Oksanen A, Keipi T (2013) Young people as victims of crime on the internet: a population-based study in Finland. Vulnerable Child Youth Stud 8(4):298–309
Oliveira D, Rocha H, Yang H, Ellis D, Dommaraju S, Muradoglu M, Weir D, Soliman A, Lin T, Ebner N (2017) Dissecting spear phishing emails for older vs young adults: on the interplay of weapons of influence and life domains in predicting susceptibility to phishing. In: Conference on Human Factors in Computing Systems—Proceedings, 2017-May, 6412–6424. https://doi.org/10.1145/3025453.3025831
Orchard LJ, Fullwood C, Galbraith N, Morris N (2014) Individual differences as predictors of social networking. J Comput-Mediat Commun 19(3):388–402. https://doi.org/10.1111/jcc4.12068
Parrish JL Jr, Bailey JL, Courtney JF (2009) A personality based model for determining susceptibility to phishing attacks. University of Arkansas, Little Rock, pp 285–296
Pasadeos Y (1985) A bibliometric study of advertising citations. J Advert 14(4):52–59
Pickering C, Byrne J (2014) The benefits of publishing systematic quantitative literature reviews for PhD candidates and other early-career researchers. Higher Educ Res Devel ISSN 33(3):534–548
Reyns BW, Fisher BS, Bossler AM, Holt TJ (2019) Opportunity and Self-control: do they predict multiple forms of online victimization? Am J Crim Justice 44(1):63–82. https://doi.org/10.1007/s12103-018-9447-5
Romero L, Portillo-Salido E (2019) Trends in sigma-1 receptor research: a 25-year bibliometric analysis. Front Pharmacol. https://doi.org/10.3389/fphar.2019.00564
Saad ME, Huda Sheikh Abdullah SN, Murah MZ (2018) Cyber romance scam victimization analysis using Routine Activity Theory versus apriori algorithm. Int J Adv Comput Sci Appl 9(12):479–485. https://doi.org/10.14569/IJACSA.2018.091267
Saridakis G, Benson V, Ezingeard JN, Tennakoon H (2016) Individual information security, user behaviour and cyber victimisation: an empirical study of social networking users. Technol Forecast Soc Change 102:320–330. https://doi.org/10.1016/j.techfore.2015.08.012
Seng S, Wright M, Al-Ameen MN (2018) Understanding users’ decision of clicking on posts in facebook with implications for phishing. Workshop on Technology and Consumer Protection (ConPro 18), May, 1–6
Serafin MJ, Garcia-Vargas GR, García-Chivita MDP, Caicedo MI, Correra JC (2019) Cyberbehavior: a bibliometric analysis. Annu Rev Cyber Ther Telemed 17:17–24. https://doi.org/10.31234/osf.io/prfcw
Skinner WF, Fream AM (1997) A social learning theory analysis of computer crime among college students. J Res Crime Delinq 34(4):495–518. https://doi.org/10.1177/0022427897034004005
Tsai H, Yi S, Shillair R, Cotten SR, Winstead V, Yost E (2015) Getting grandma online: are tablets the answer for increasing digital inclusion for older adults in the US? Educ Gerontol 41(10):695–709. https://doi.org/10.1080/03601277.2015.1048165
van Eck NJ, Waltman L (2020) Manual for VOSviewer version 1.6.16
Van Wilsem J (2013) “Bought it, but never got it” assessing risk factors for online consumer fraud victimization. Eur Sociol Rev 29(2):168–178. https://doi.org/10.1093/esr/jcr053
van der Wagen W, Pieters W (2020) The hybrid victim: re-conceptualizing high-tech cyber victimization through actor-network theory. Eur J Criminol 17(4):480–497. https://doi.org/10.1177/1477370818812016
Vishwanath A (2015) Habitual Facebook use and its impact on getting deceived on social media. J Comput-Mediat Commun 20(1):83–98. https://doi.org/10.1111/jcc4.12100
Wall D (2001) Crime and the Internet: Cybercrime and cyberfears, 1st edn. Routledge, London
Wall D (2004) What are cybercrimes? Crim Justice Matters 58(1):20–21
Whitty MT, Buchanan T (2012) The online romance scam: a serious cybercrime. Cyberpsychol Behav Soc Netw 15(3):181–183. https://doi.org/10.1089/cyber.2011.0352
You GR, Sun X, Sun M, Wang JM, Chen YW (2014) Bibliometric and social network analysis of the SoS field. In: Proceedings of the 9th International Conference on System of Systems Engineering: The Socio-Technical Perspective, SoSE 2014, 13–18. https://doi.org/10.1109/SYSOSE.2014.6892456
Zyoud SH, Sweileh WM, Awang R, Al-Jabi SW (2018) Global trends in research related to social media in psychology: Mapping and bibliometric analysis. Int J Ment Health Syst 12(1):1–8. https://doi.org/10.1186/s13033-018-0182-6
Download references
Author information
Authors and affiliations.
School of Journalism and Communication, Huazhong University of Science and Technology, Wuhan, Hubei, China
Huong Thi Ngoc Ho
School of Global, Urban and Social Studies, RMIT University, Melbourne, Australia
Hai Thanh Luong
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Hai Thanh Luong .
Ethics declarations
Conflict of interest.
The authors declare that they have no competing interest.
Rights and permissions
Reprints and permissions
About this article
Ho, H.T.N., Luong, H.T. Research trends in cybercrime victimization during 2010–2020: a bibliometric analysis. SN Soc Sci 2 , 4 (2022). https://doi.org/10.1007/s43545-021-00305-4
Download citation
Received : 13 September 2021
Accepted : 15 December 2021
Published : 06 January 2022
DOI : https://doi.org/10.1007/s43545-021-00305-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Bibliometric analysis
- Web of science
- Co-occurrence analysis
- Find a journal
- Publish with us
- Track your research
Current Status and Challenges of Protection and Support for Victims in India
Korean Journal of Victimology, 2022 Vol.30 No. 1
5 Pages Posted: 11 Oct 2022
G. S. Bajpai
National Law University Delhi
Date Written: August 9, 2022
Until 1970s the victims of crime were not considered as an essential part of the criminal justice system. This attitude started to change after the formation of the standalone discipline of victimology and research in the field of victimology. From the past few decades, the field of victimology has witnessed a huge growth and also created revolution in many countries to deal with victims of crime. All over the world, countries have started recognizing the need for victim’ s services to help them in criminal justice system, to overcome the effects of crime victimization and to provide justice. But in India, still victims are not recognized as victims and there is no significant improvement of victim’ s position in the criminal justice system.
Suggested Citation: Suggested Citation
G. S. Bajpai (Contact Author)
National law university delhi ( email ).
Sector-14 Dwarka New Delhi, New Delhi 110078 India
Do you have a job opening that you would like to promote on SSRN?
Paper statistics, related ejournals, law & society: public law - crime, criminal law, & punishment ejournal.
Subscribe to this fee journal for more curated articles on this topic
India Law eJournal
Criminology ejournal.
- Skip to main content
- Skip to primary sidebar
IResearchNet
Victimization Topics
Victimization can be defined as the act or process of someone being injured or damaged by another person. The resulting damage may be physical (e.g., bruises, broken bones) or psychological (e.g., posttraumatic stress disorder [PTSD], depression). Victimization is a frequent event that occurs within an interpersonal context, often involving an abuse of power, such as a parent who abuses a child; an adult child who abuses a frail, elderly parent; or a teacher who sexually abuses a student. Although past research on victimization has tended to be compartmentalized, a more integrative approach is needed not only because of the frequent comorbidity among the different types of victimization, but also because of the shared psychological issues. Read more about Victimization .
Victimization Research Topics
- Battered Woman Syndrome
- Child Maltreatment
- Child Sexual Abuse
- Intimate Partner Violence
- Mild Traumatic Brain Injury
- Posttraumatic Stress Disorder
- Psychological Autopsy
- Rape Trauma Syndrome
- Reporting Crimes and Victimization
- Sexual Assault Victims Coping
- Sexual Harassment
- Victim Participation in Criminal Justice
To understand victimization, several core themes need to be acknowledged. Contrary to a layperson’s perspective, victimization is not a rare event that occurs only in a stranger-on-stranger context. On the contrary, victimization is an extraordinarily frequent event that most often occurs in, and adheres to, the ordinary roles of human life. Although stereotyped conceptions of victimization do occur (e.g., a woman raped by a stranger walking down a street at night) and are damaging and need to be addressed, these types of victimization are not the norm outside the context of a war. Rather, the most significant sources of victimization are those that arise out of our ordinary day-to-day roles, such as those of spouse, parent, child, and friend. Thus, victimization must be understood as an inherent part of human relationships.
Browse other Forensic Psychology Research Topics .
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- v.5(3); 2019 Mar

Cyberbullying and its influence on academic, social, and emotional development of undergraduate students
This study investigated the influence of cyberbullying on the academic, social, and emotional development of undergraduate students. It's objective is to provides additional data and understanding of the influence of cyberbullying on various variables affecting undergraduate students. The survey sample consisted of 638 Israeli undergraduate students. The data were collected using the Revised Cyber Bullying Survey, which evaluates the frequency and media used to perpetrate cyberbullying, and the College Adjustment Scales, which evaluate three aspects of development in college students. It was found that 57% of the students had experienced cyberbullying at least once or twice through different types of media. Three variables were found to have significant influences on the research variables: gender, religion and sexual preferences. Correlation analyses were conducted and confirmed significant relationships between cyberbullying, mainly through instant messaging, and the academic, social and emotional development of undergraduate students. Instant messaging (IM) was found to be the most common means of cyberbullying among the students.
The main conclusions are that although cyberbullying existence has been proven, studies of cyberbullying among undergraduate students have not been fully developed. This particular population needs special attention in future research. The results of this study indicate that cyberbullying has an influence on the academic, social, and emotional development of undergraduate students. Additional Implications of the findings are discussed.
1. Introduction
Cyberbullying is defined as the electronic posting of mean-spirited messages about a person (such as a student) often done anonymously ( Merriam-Webster, 2017 ). Most of the investigations of cyberbullying have been conducted with students in elementary, middle and high school who were between 9 and 18 years old. Those studies focused on examining the prevalence and frequency of cyberbullying. Using “cyberbullying” and “higher-education” as key words in Google scholar (January, 2019) (all in title) yields only twenty one articles. In 2009, 2012 and 2013 one article appeared each year, since 2014 each year there were few publications. Of these articles only seven relates to effect of cyberbullying on the students, thus a gap in the literature exists in that it only minimally reports on studies involving undergraduate students. Given their relationship and access to technology, it is likely that cyberbullying occurs frequently among undergraduates. The purpose of this study is to examine the frequency and media used to perpetrate cyberbullying, as well as the relationship that it has with the academic, social and emotional development of undergraduate students.
Undergraduate students use the Internet for a wide variety of purposes. Those purposes include recreation, such as communicating in online groups or playing games; academics, such as doing assignments, researching scholarships or completing online applications; and practical, such as preparing for job interviews by researching companies. Students also use the Internet for social communication with increasing frequency.
The literature suggests that cyberbullied victims generally manifest psychological problems such as depression, loneliness, low self-esteem, school phobias and social anxiety ( Grene, 2003 ; Juvonen et al., 2003 ; Akcil, 2018 ). Moreover, research findings have shown that cyberbullying causes emotional and physiological damage to defenseless victims ( Akbulut and Eristi, 2011 ) as well as psychosocial difficulties including behavior problems ( Ybarra and Mitchell, 2007 ), drinking alcohol ( Selkie et al., 2015 ), smoking, depression, and low commitment to academics ( Ybarra and Mitchell, 2007 ).
Under great emotional stress, victims of cyberbullying are unable to concentrate on their studies, and thus their academic progress is adversely affected ( Akcil, 2018 ). Since the victims are often hurt psychologically, the depressive effect of cyberbullying prevents students from excelling in their studies ( Faryadi, 2011 ). The overall presence of cyberbullying victimization among undergraduate college students was found to be significantly related to the experience of anxiety, depression, substance abuse, low self-esteem, interpersonal problems, family tensions and academic underperformance ( Beebe, 2010 ).
1.1. Cyberbullying and internet
The Internet has been the most useful technology of modern times, which has enabled entirely new forms of social interaction, activities, and organizing. This has been possible thanks to its basic features such as widespread usability and access. However, it also causes undesirable behaviors that are offensive or threatening to others, such as cyberbullying. This is a relatively new phenomenon.
According to Belsey (2006, p.1) , “Cyberbullying involves the use of information and communication technologies such as e-mail, cell-phone and pager text messages, instant messaging, defamatory personal web sites, blogs, online games and defamatory online personal polling web sites, to support deliberate, repeated, and hostile behavior by an individual or group that is intended to harm others.” Characteristics like anonymity, accessibility to electronic communication, and rapid audience spread, result in a limitless number of individuals that can be affected by cyberbullying.
Different studies suggest that undergraduate students' use of the Internet is more significant and frequent than any other demographic group. A 2014 survey of 1006 participants in the U.S. conducted by the Pew Research Center revealed that 97% of young adults aged from 18 to 29 years use the Internet, email, or access the Internet via a mobile device. Among them, 91% were college students.
1.2. Mediums to perpetrate cyberbullying
The most frequent and common media within which cyberbullying can occur are:
Electronic mail (email): a method of exchanging digital messages from an author to one or more recipients.
Instant messaging: a type of online chat that offers real-time text transmission between two parties.
Chat rooms: a real-time online interaction with strangers with a shared interest or other similar connection.
Text messaging (SMS): the act of composing and sending a brief electronic message between two or more mobile phones.
Social networking sites: a platform to build social networks or social relations among people who share interests, activities, backgrounds or real-life connections.
Web sites : a platform that provides service for personal, commercial, or government purpose.
Studies indicate that undergraduate students are cyberbullied most frequently through email, and least often in chat rooms ( Beebe, 2010 ). Other studies suggest that instant messaging is the most common electronic medium used to perpetrate cyberbullying ( Kowalski et al., 2018 ).
1.3. Types of cyberbullying
Watts et al. (2017) Describe 7 types of cyberbullying: flaming, online harassment, cyberstalking, denigration, masquerading, trickery and outing, and exclusion. Flaming involves sending angry, rude, or vulgar messages via text or email about a person either to that person privately or to an online group.
Harassment involves repeatedly sending offensive messages, and cyberstalking moves harassment online, with the offender sending threatening messages to his or her victim. Denigration occurs when the cyberbully sends untrue or hurtful messages about a person to others. Masquerading takes elements of harassment and denigration where the cyberbully pretends to be someone else and sends or posts threatening or harmful information about one person to other people. Trickery and outing occur when the cyberbully tricks an individual into providing embarrassing, private, or sensitive information and posts or sends the information for others to view. Exclusion is deliberately leaving individuals out of an online group, thereby automatically stigmatizing the excluded individuals.
Additional types of cyberbullying are: Fraping - where a person accesses the victim's social media account and impersonates them in an attempt to be funny or to ruin their reputation. Dissing - share or post cruel information online to ruin one's reputation or friendships with others. Trolling - is insulting an individual online to provoke them enough to get a response. Catfishing - steals one's online identity to re-creates social networking profiles for deceptive purposes. Such as signing up for services in the victim's name so that the victim receives emails or other offers for potentially embarrassing things such as gay-rights newsletters or incontinence treatment. Phishing - a tactic that requires tricking, persuading or manipulating the target into revealing personal and/or financial information about themselves and/or their loved ones. Stalking – Online stalking when a person shares her personal information publicly through social networking websites. With this information, stalkers can send them personal messages, send mysterious gifts to someone's home address and more. Blackmail – Anonymous e-mails, phone-calls and private messages are often done to a person who bear secrets. Photographs & video - Threaten to share them publicly unless the victim complies with a particular demand; Distribute them via text or email, making it impossible for the victim to control who sees the picture; Publish the pictures on the Internet for anyone to view. Shunning - persistently avoid, ignore, or reject someone mainly from participating in social networks. Sexting - send sexually explicit photographs or messages via mobile phone.
1.4. Prevalence of cyberbullying
Previous studies have found that cyberbullying incidents among college students can range from 9% to 34% ( Baldasare et al., 2012 ).
Beebe (2010) conducted a study with 202 college students in United States. Results indicated that 50.7% of the undergraduate students represented in the sample reported experiencing cyberbullying victimization once or twice during their time in college. Additionally, 36.3% reported cyberbullying victimization on a monthly basis while in college. According to Dılmaç (2009) , 22.5% of 666 students at Selcuk University in Turkey reported cyberbullying another person at least once and 55.35% reported being a victim of cyberbullying at least once in their lifetimes. In a study of 131 students from seven undergraduate classes in United States, 11% of the respondents indicated having experienced cyberbullying at the university ( Walker et al., 2011 ). Of those, Facebook (64%), cell phones (43%) and instant messaging (43%) were the most frequent technologies used. Students indicated that 50% of the cyberbullies were classmates, 57% were individuals outside of the university, and 43% did not know who was cyberbullying them.
Data from the last two years (2017–18) is similar to the above. A research, of 187 undergraduate students matriculated at a large U.S. Northeastern metropolitan Roman Catholic university ( Webber and Ovedovitz, 2018 ), found that 4.3% indicated that they were victims of cyberbullying at the university level and a total of 7.5% students acknowledged having participated in bullying at that level while A survey (N = 338) at a large midwestern university conducted by Varghese and Pistole (2017) , showed that frequency counts indicated that 15.1% undergraduate students were cyberbully victims during college, and 8.0% were cyberbully offenders during college.
A study of 201 students from sixteen different colleges across the United States found a prevalence rate of 85.2% for college students who reported being victims of cyberbullying out of the total 201 responses recorded. This ranged from only occasional incidents to almost daily experiences with cyberbullying victimization ( Poole, 2017 ).
In A research of international students, 20.7% reported that they have been cyberbullied in the last 30 days once to many times ( Akcil, 2018 ).
1.5. Psychological impact of cyberbullying
Cyberbullying literature suggests that victims generally manifest psychological problems such as depression, anxiety, loneliness, low self-esteem, social exclusion, school phobias and poor academic performance ( DeHue et al., 2008 ; Juvonen and Gross, 2008 ; Kowalski and Limber, 2007 ; Grene, 2003 ; Juvonen et al., 2003 ; Rivituso, 2012 ; Varghese and Pistole, 2017 ; Na, 2014 ; Akcil, 2018 ), low self-esteem, family problems, school violence and delinquent behavior ( Webber and Ovedovitz, 2018 ), which brings them to experience suicidal thoughts as a means of escaping the torture ( Ghadampour et al., 2017 ).
Moreover, research findings have shown that cyberbullying causes emotional and physiological damage to defenseless victims ( Faryadi, 2011 ) as well as psychosocial problems including inappropriate behaviors, drinking alcohol, smoking, depression and low commitment to academics ( Walker et al., 2011 ).
The victims of cyberbullying, under great emotional stress, are unable to concentrate on their studies, and thus their academic progress is adversely affected ( Faryadi, 2011 ). Since the victims are often hurt psychologically, the depressive effect of cyberbullying prevents students from excelling in their studies ( Faryadi, 2011 ).
In a Malaysian university study with 365 first year students, the majority of the participants (85%) interviewed indicated that cyberbullying affected their academic performance, specifically their grades ( Faryadi, 2011 ). Also, 85% of the respondents agreed that bullying caused a devastating impact on students' emotions and equally caused unimaginable psychological problems among the victims. Heiman and Olenik-Shemesh (2018) report that for students with learning disabilities, predictors of cybervictimization were low social support, low self-perception, and being female, whereas for students without learning disabilities, the predictors were low social support, low well-being, and low body perception.
1.6. Academic, social, and emotional development of undergraduate students
The transition to academic institutions is marked by complex challenges in emotional, social, and academic adjustment ( Gerdes and Mallinckrodt, 1994 ; Parker et al., 2004 ).
The adaptation to a new environment is an important factor in academic performance and future achievement. Undergraduate students are not only developing academically and intellectually, they are also establishing and maintaining personal relationships, developing an identity, deciding about a career and lifestyle, and maintaining personal health and wellness. Many students are interacting with people from diverse backgrounds who hold different values and making new friends. Some are also adapting to living away from home for the very first time ( Inkelas et al., 2007 ).
The concept of academic development involves not only academic abilities, but motivational factors, and institutional commitment. Motivation to learn, taking actions to meet academic demands, a clear sense of purpose, and general satisfaction with the academic environment are also important components of the academic field ( Lau, 2003 ).
A second dimension, the social field, may be as important as academic factors. Writers have emphasized integration into the social environment as a crucial element in commitment to a particular academic institution ( Tinto, 1975 ). Becoming integrated into the social life of college, forming a support network, and managing new social freedoms are some important elements of social development. Crises in the social field include conflict in a living situation, starting or maintaining relationships, interpersonal conflicts, family issues, and financial issues ( McGrath, 2005 ), which are manifested as feelings of loneliness ( Clark et al., 2015 ).
In the emotional field, students commonly question their relationships, direction in life, and self-worth ( Rey et al., 2011 ). A balanced personality is one which is emotionally adjusted. Emotional adjustment is essential for creating a sound personality. physical, intellectual mental and esthetical adjustments are possible when emotional adjustment is made ( Ziapour et al., 2018 ). Inner disorders may result from questions about identity and can sometimes lead to personal crises ( Gerdes and Mallinckrodt, 1994 ). Emotional problems may be manifested as global psychological distress, somatic distress, anxiety, low self-esteem, or depression. Impediments to success in emotional development include depression and anxiety, stress, substance abuse, and relationship problems ( Beebe, 2010 ).
The current study is designed to address two research questions: (1) does cyberbullying affect college students' emotional state, as measured by the nine factors of the College Adjustment Scales ( Anton and Reed, 1991 ); (2) which mode of cyberbullying most affects students' emotional state?
2.1. Research settings and participants
The present study is set in Israeli higher education colleges. These, function as: (1) institutions offering undergraduate programs in a limited number of disciplinary fields (mainly the social sciences), (2) centers for training studies (i.e.: teacher training curricula), as well as (3) as creators of access to higher education. The general student population is heterogeneous, coming from the Western Galilee. In this study, 638 Israeli undergraduate students participated. The sample is a representative of the population of the Western galilee in Israel. The sample was 76% female, 70% single, 51% Jewish, 27% Arabs, 7% Druze, and 15% other ethnicity. On the dimension of religiosity, 47% were secular, 37% traditional, 12% religious, 0.5% very religious, and 3.5% other. On the dimension of sexual orientation, 71% were straight women, 23.5% straight men, 4% bisexual, 1% lesbians, and 0.5% gay males (note: according to the Williams Institute, approximately 4% of the population in the US are LGBT, [ Gates, 2011 ], while 6% of the EU population are LGBT, [ Dalia, 2016 ]).
2.2. Instrumentation
Two instruments were used to collect data: The Revised Cyber Bullying Survey (RCBS), with a Cronbach's alpha ranging from .74 to .91 ( Kowalski and Limber, 2007 ), designed to measure incidence, frequency and medium used to perpetrate cyberbullying. The survey is a 32-item questionnaire. The frequency was investigated using a 5-item scale with anchors ranging from ‘it has never happened to me’ to ‘several times a week’. Five different media were explored: email, instant messaging, chat room, text messaging, and social networking sites. Each medium was examined with the same six questions related to cases of cyberbullying (see Table 1 ).
Description of the Revised Cyber Bullying Survey (RCBS) variables.
| Means of cyberbullying | N | Minimum | Maximum | Mean | SD | Reliability |
|---|---|---|---|---|---|---|
| Chat | 610 | .00 | 24 | .48 | 1.64 | 0.87 |
| Social networking | 635 | .00 | 20 | .95 | 1.93 | 0.85 |
| SMS | 631 | .00 | 12 | .78 | 1.53 | 0.80 |
| Instant messages | 634 | .00 | 13 | .96 | 1.81 | 0.81 |
| 637 | .00 | 11 | .41 | 1.05 | 0.68 | |
| Valid N (listwise) | 608 |
Note: the theoretical range is between zero to twenty-four.
Table 1 shows the five variables that composed the RCBS questionnaire (all of the variables are composed of 6 statements). The results indicate that the levels of all the variables is very low, which means that the respondents experienced cyberbullying once or twice. The internal consistency reliability estimate based on the current sample suggested that most of the variables have an adequate to high level of reliability, with a Cronbach's alpha of 0.68–0.87.
The College Adjustment Scales (CAS) ( Anton and Reed, 1991 ), evaluated the academic, social, and emotional development of college students. Values were standardized and validated for use with college students. The validity for each subscale ranged from .64 to .80, noting high correlations among scales. Reliability of the scales ranged from .80 to .92, with a mean of .86. The instrument included 128 items, divided into 10 scales: anxiety, depression, suicidal ideation, substance abuse, self-esteem problems, interpersonal problems, family problems, academic problems, career problems, and regular activities (see Table 2 ). Students responded to each item using a four-point scale.
Description of CAS variables.
| Variables | N | Minimum | Maximum | Mean | SD | Reliability |
|---|---|---|---|---|---|---|
| Academic problems | 634 | 28 | 73 | 47.87 | 8.87 | 0.77 |
| Anxiety | 633 | 30 | 78 | 51.17 | 9.57 | 0.88 |
| Career problems | 632 | 36 | 80 | 55.47 | 8.63 | 0.87 |
| Depression | 633 | 27 | 78 | 53.27 | 9.14 | 0.81 |
| Family problems | 633 | 32 | 74 | 44.61 | 11.19 | 0.72 |
| Interpersonal problems | 633 | 29 | 77 | 52.51 | 8.38 | 0.72 |
| Regular activities | 624 | 27 | 78 | 57.10 | 8.80 | 0.69 |
| Self-esteem problems | 633 | 22 | 74 | 50.31 | 9.19 | 0.76 |
| Substance abuse | 633 | 39 | 75 | 49.72 | 8.45 | 0.78 |
| Suicidal ideation | 633 | 44 | 76 | 51.92 | 9.63 | 0.87 |
| Valid N (listwise) | 624 |
Anxiety: A measure of clinical anxiety, focusing on common affective, cognitive, and physiological symptoms.
Depression: A measure of clinical depression, focusing on common affective, cognitive, and physiological symptoms.
Suicidal Ideation: A measure of the extent of recent ideation reflecting suicide, including thoughts of suicide, hopelessness, and resignation.
Substance Abuse: A measure of the extent of disruption in interpersonal, social, academic, and vocational functioning as a result of substance use and abuse.
Self-esteem Problems: A measure of global self-esteem which taps negative self-evaluations and dissatisfaction with personal achievement.
Interpersonal Problems: A measure of the extent of problems in relating to others in the campus environment.
Family Problems: A measure of difficulties experienced in relationships with family members.
Academic Problems: A measure of the extent of problems related to academic performance.
Career Problems: A measure of the extent of problems related to career choice.
Participants also responded to a demographic questionnaire that included items on gender, birth year, marital status, ethnicity, and sexual orientation. As sexual orientation is a major cause for bullying ( Pollock, 2006 ; Cahill and Makadon, 2014 ), it was included in the background information.
Convenience sampling and purposive sampling were used for this study. Surveys with written instructions were administered in classrooms, libraries and online via Google Docs at the end of the semester.
The surveys were translated to Hebrew and back translated four times until sufficient translation was achieved. The research was approved by the Western Galilee College Research and Ethic Committee.
A sizeable percentage, 57.4% (366), of the respondents reported being cyber bullied at least once and 3.4% (22) reported being cyber bullied at least once a week. The types of bullies can be seen in Fig. 1 .

Types of bullies.
Three variables were found to have significant influences on the research variables: (1) gender (see Table 3 ); (2) religion (see Table 4 ); and (3) sexual preferences (see Table 5 ).
Results of independent t-tests for research variables by gender.
| M | SD | t | ||
|---|---|---|---|---|
| Depression | Male | 51.82 | 8.08 | 1.99 |
| Female | 53.63 | 9.37 | ||
| Regular activities | Male | 55.66 | 8.82 | 2.05 |
| Female | 57.47 | 8.77 | ||
| Self-esteem problems | Male | 48.79 | 9.19 | 2.08 |
| Female | 50.68 | 9.16 | ||
| Suicidal ideation | Male | 50.10 | 8.91 | 2.48 |
| Female | 52.34 | 9.74 | ||
Note: n male = 127, n female = 510, *p < .05.
Results of independent t-tests for research variables by level of religion.
| M | SD | T | ||
|---|---|---|---|---|
| Depression | Secular | 52.07 | 8.97 | 3.08 |
| Religious | 54.30 | 9.17 | ||
| Family problemýs | Secular | 43.60 | 11.16 | 2.09 |
| Religious | 45.46 | 11.16 | ||
| Interpersonal problems | Secular | 51.77 | 8.80 | 2.04 |
| Religious | 53.14 | 7.97 | ||
| Suicidal ideation | Secular | 50.13 | 8.85 | 4.42 |
| Religious | 53.44 | 10.00 | ||
Note: n religious = 345, n secular = 293, ∗ p < .05, ∗∗ p < .01, ∗∗∗ p < .001.
Results of independent t-tests for research variables by sexual preference.
| M | SD | t | ||
|---|---|---|---|---|
| Anxiety | Heterosexual | 50.92 | 9.63 | 2.41 |
| Other | 54.60 | 8.12 | ||
| Depression | Heterosexual | 52.88 | 8.90 | 4.14 |
| Other | 58.86 | 10.59 | ||
| Family problems | Heterosexual | 44.11 | 10.94 | 4.20 |
| Other | 51.52 | 12.42 | ||
| Interpersonal problems | Heterosexual | 52.26 | 8.31 | 2.80 |
| Other | 56.00 | 8.80 | ||
| Self-esteem problems | Heterosexual | 50.07 | 9.14 | 2.44 |
| Other | 53.64 | 9.28 | ||
| Substance abuse | Heterosexual | 49.34 | 8.19 | 3.48 |
| Other | 54.98 | 10.27 | ||
| Suicidal ideation | Heterosexual | 51.33 | 9.34 | 5.88 |
| Other | 60.14 | 9.89 | ||
Note: n heterosexual = 596, n other = 42, ∗ p < .05, ∗∗ p < .01, ∗∗∗ p < .001.
Independent t-tests between the CAS variables and gender show significant differences between females and males (see Table 3 ).
Independent t-tests between the CAS variables and level of religiosity show significant differences between secular and religious persons, i.e., observant believers (see Table 4 ).
Independent t-tests between the CAS variables and sexual preference show significant differences between heterosexual individuals and others (see Table 5 ).
The research population was divided into three age groups having five year intervals. One respondent who was 14 years old was removed from the population.
For the variable “career problems” it was found that there was a significant difference between the 26–30 year age group [p < .05, F(2,5815) = 3.49, M = 56.55] and the 31–35 (M = 56.07) as well as the 20–25 (M = 54.58) age groups.
For the variable "depression" it was found that there was a significant difference between the 20–25 year age group [p < .05, F(2,5815) = 3.84, M = 54.56] and the 31–35 (M = 51.61) as well as the 26–30 (M = 52.83) age groups.
For the variable “interpersonal problems” it was found that there was a significant difference between the 20–25 year age group [p < .06, F(2,5815) = 3.84, M = 53.85] and the 31–35 (M = 51.29) as well as the 26–30 (M = 52.19) age groups.
For the variable “suicidal ideation” it was found that there was a significant difference between the 20–25 year age group [p < .06, F(2,5815) = 3.84, M = 55.45] and the 31–35 (M = 49.71) as well as the 26–30 (M = 50.13) age groups (see Table 6 ).
Results of one way Anova for research variables by age.
| Age Group | M | SD | F | |
|---|---|---|---|---|
| Career problems | 20–25 | 54.58 | 7.97 | 3.49 |
| 26–30 | 56.55 | 8.36 | ||
| 31–35 | 56.07 | 9.29 | ||
| Depression | 20–25 | 54.56 | 10.08 | 3.84 |
| 26–30 | 52.83 | 8.62 | ||
| 31–35 | 51.61 | 8.14 | ||
| Interpersonal problems | 20–25 | 53.58 | 8.23 | 2.87 |
| 26–30 | 52.19 | 8.42 | ||
| 31–35 | 51.29 | 8.06 | ||
| Suicidal ideation | 20–25 | 55.45 | 10.48 | 22.79 |
| 26–30 | 50.13 | 8.67 | ||
| 31–35 | 49.71 | 8.58 |
Note: n 20-25 = 216, n 26-30 = 287, n 31-35 = 82, ∗ p < .05, ∗∗ p < .01, ∗∗∗ p < .001.
To confirm that there was no effect among the independent variables, a Pearson correlation analysis of cyberbullying with CAS variables was run. As the correlations between the independent variables are weak, no multicollinearity between them was noted (see Table 7 ).
Pearson correlation of cyberbullying with CAS variables.
| CAS Variables | Cyberbullying | ||||
|---|---|---|---|---|---|
| IM | Chat | SMS | Social Network | ||
| Academic problems | 0.018 | 0.196*** | 0.079 | 0.141*** | 0.189*** |
| Anxiety | 0.042 | 0.216*** | 0.080* | 0.159*** | 0.194*** |
| Career problems | -0.007 | 0.089 | -0.08 | 0.079 | 0.057 |
| Depression | 0.064 | 0.210*** | 0.122** | 0.102* | 0.172*** |
| Family problems | 0.142*** | 0.227*** | 0.081* | 0.132** | 0.156*** |
| Interpersonal problems | 0.054 | 0.150*** | 0.094 | 0.040 | 0.110** |
| Regular activities | -0.121** | -0.014 | 0.005- | -0.015 | 0.003 |
| Self-esteem | 0.041 | 0.229*** | 0.124** | 0.171*** | 0.208*** |
| Substance abuse | 0.150*** | 0.235*** | 0.184*** | 0.161*** | 0.174*** |
| Suicidal ideation | 0.130** | 0.230*** | 0.148*** | 0.093* | 0.130** |
Note: n = 638, ∼ p < .06, ∗ p < .05, ∗∗ p < .01, ∗∗∗ p < .001.
Regression analyses on the effect of the cyberbullying variables on the CAS variables (see Fig. 2 ) show that an increase in cyberbullying by social networking and IM increases the academic problems variable. The model explained 6.1% of the variance (F (13,585) = 2.94, p < .001) and shows an increase in the suicidal ideation variable. There is also a marginal effect of cyberbullying by SMS on suicidal ideation, revealing that an increase in cyberbullying by SMS causes a decrease in suicidal ideation. The explained variance of the model is 24.8% (F (11,584) = 14.80, p < .001). Higher cyberbullying by social networking results in an increase in the anxiety variable. The explained variance of the model is 8.8% (F (13,584) = 4.32, p < .001). An increase in cyberbullying by chat and IM shows an increase in the substance abuse variable. The model explains 13% of the variance (F (13,584) = 6.71, p < .001). Increasing cyberbullying by social networking and IM increases the self-esteem problems variable. The explained variance of the model is 9% (F (13,584) = 4.43, p < .001). An increase of cyberbullying by email increases the problems students have with regular activities. The explained variance of the model is 5.2% (F (13,575) = 2.44, p < .01). Heightened cyberbullying by social networking and IM increases students' interpersonal problems. There is also an effect of cyberbullying by IM on suicidal ideation, such that an increase in cyberbullying by IM causes a decrease in interpersonal problems. The explained variance of the model is 8% (F (13,584) = 3.89, p < .001). An increase in cyberbullying by SMS decreases the family problems variable. The explained variance of the model is 11.4% (F (13,584) = 5.76, p < .001). And finally, heightened cyberbullying by IM and social networking decreases the depression variable. The variance explained by the model is 11.9% (F (13,584) = 6.04, p < .001).

The influence of academic cyberbullying variables on the CAS variables.
4. Discussion
The objective of this study was to fill an existing gap in the literature regarding the influence of cyberbullying on the academic, social, and emotional development of undergraduate students.
As has been presented, cyberbullying continues to be a disturbing trend not only among adolescents but also undergraduate students. Cyberbullying exists in colleges and universities, and it has an influence on the development of students. Fifty seven percent of the undergraduate students who participated in this study had experienced cyberbullying at least once during their time in college. As previous studies have found that cyberbullying incidents among college students can range from 9% to 50% ( Baldasare et al., 2012 ; Beebe, 2010 ) it seems that 57% is high. Considering the effect of smartphone abundance on one hand and on the other the increasing use of online services and activities by young-adults can explain that percentage.
Considering the effect of such an encounter on the academic, social and emotional development of undergraduate students, policy makers face a formidable task to address the relevant issues and to take corrective action as Myers and Cowie (2017) point out that due to the fact that universities are in the business of education, it is a fine balancing act between addressing the problem, in this case cyberbullying, and maintaining a duty of care to both the victim and the perpetrator to ensure they get their degrees. There is a clear tension for university authorities between acknowledging that university students are independent young adults, each responsible for his or her own actions, on one hand, and providing supervision and monitoring to ensure students' safety in educational and leisure contexts.
Although there are increasing reports on connections between cyberbullying and social-networks (see: Gahagan et al., 2016 ), sending SMS or MMS messages through Internet gateways ensures anonymity, thus indirectly supporting cyberbullying. A lot of websites require only login or a phone number that can also be made up ( Gálik et al., 2018 ) which can explain the fact that instant-messaging (IM) was found to be the most common means of cyberbullying among undergraduate students with a negative influence on academic, family, and emotional development (depression, anxiety, and suicidal ideation). A possible interpretation of the higher frequency of cyberbullying through IM may be that young adults have a need to be connected.
This medium allows for being online in ‘real time’ with many peers or groups. With the possibility of remaining anonymous (by creating an avatar – a fake profile) and the possibility of exposing private information that remains recorded, students who use instant messaging become easy targets for cyberbullying. IM apps such as WhatsApp are extremely popular as they allow messages, photos, videos, and recordings to be shared and spread widely and in real time.
Students use the Internet as a medium and use it with great frequency in their everyday lives. As more aspects of students' lives and daily affairs are conducted online, coupled with the fact that excessive use may have consequences, it is important for researchers and academic policy makers to study the phenomenon of cyberbullying more deeply.
Sexual orientation is also a significant factor that increases the risk of victimization. Similarly, Rivers (2016) documented the rising incidence of homophobic and transphobic bullying at university and argues strongly for universities to be more active in promoting tolerance and inclusion on campus. It is worth noting that relationships and sexual orientation probably play a huge role in bullying among university students due to their age and the fact that the majority of students are away from home and experiencing different forms of relationships for the first time. Faucher et al. (2014) actually found that same sex cyberbullying was more common at university level than at school. Nonetheless, the research is just not there yet to make firm conclusions.
Finally, cyberbullying is not only an adolescent issue. Although its existence has been proven, studies of cyberbullying among undergraduate students have not been fully developed. This particular population needs special attention in future research.
The results of this study indicate that cyberbullying has an influence on the academic, social, and emotional development of undergraduate students.
In the academic field, findings revealed a statistically significant correlation between cyberbullying perpetrated by email and academic problems. Relationships between academic problems and cyberbullying perpetrated by other media were not found. This suggests that cyberbullying through instant messaging, chat room, text messaging, and social networking sites, have not influenced academic abilities, motivation to learn, and general satisfaction with the academic environment. However, cyberbullying perpetrated by email has an influence on academics, perhaps because of the high use of this medium among undergraduate students.
With regard to career problems, correlations with cyberbullying were not found. This indicates that cyberbullying has no influence on career problems, perhaps because these kinds of problems are related to future career inspirations, and not to the day-to-day aspects of a student's life.
In the social field, it was found that interpersonal problems such as integration into the social environment, forming a support network, and managing new social freedoms, were related to cyberbullying via social networking sites. This finding is consistent with the high use of social networking sites, the purpose of the medium, and the reported episodes of cyberbullying in that medium.
Family problems were also related to cyberbullying perpetrated by all kinds of media. This may indicate that as cyberbullying through the use of email, instant messaging, chat rooms, text messaging, and social networking sites increases, so do family problems. This could be due to the strong influence that cyberbullying generates in all the frameworks of students, including their families.
Finally, in the emotional field, correlations between cyberbullying perpetrated by all kinds of media and substance abuse were found. This may indicate that as cyberbullying through the use of email, instant messaging, chat rooms, text messaging, and social networking sites increases, so does substance abuse. This is important because cyberbullying may be another risk factor for increasing the probability of substance abuse.
Depression and suicidal ideation were significantly related to the same media – email instant messaging and chat cyberbullying – suggesting that depression may lead to a decision of suicide as a solution to the problem. Previous findings support the above that being an undergraduate student – a victim of cyberbullying emerges as an additional risk factor for the development of depressive symptoms ( Myers and Cowie, 2017 ). Also Selkie et al. (2015) reported among 265 female college students, being engaged in cyberbullying as bullies, victims, or both led to higher rates of depression and alcohol use.
Relationships between anxiety and cyberbullying, through all the media, were not found although Schenk and Fremouw (2012) found that college student victims of cyberbullying scored higher than matched controls on measures of depression, anxiety, phobic anxiety, and paranoia. This may be because it was demonstrated that anxiety is one of the most common reported mental health problems in all undergraduate students, cyberbullied or not.
Self-esteem problems were significantly related to cyberbullying via instant messaging, social networking sites, and text messaging. This may suggest that as cyberbullying through instant messaging, social networking sites, and text messaging increases, so do self-esteem problems. This is an important finding, given that these were the media with more reported episodes of cyberbullying.
5. Conclusions
This findings of this study revealed that cyberbullying exists in colleges and universities, and it has an influence on the academic, social, and emotional development of undergraduate students.
It was shown that cyberbullying is perpetrated through multiple electronic media such as email, instant messaging, chat rooms, text messaging, and social networking sites. Also, it was demonstrated that students exposed to cyberbullying experience academic problems, interpersonal problems, family problems, depression, substance abuse, suicidal ideation, and self-esteem problems.
Students have exhibited clear preferences towards using the Internet as a medium and utilize it with great frequency in their everyday lives. As more and more aspects of students' lives are conducted online, and with the knowledge that excessive use may have consequences for them, it is important to study the phenomenon of cyberbullying more deeply.
Because college students are preparing to enter the workforce, and several studies have indicated a trend of cyberbullying behavior and victimization throughout a person's lifetime ( Watts et al., 2017 ), the concern is these young adults are bringing these attitudes into the workplace.
Finally, cyberbullying is not only an adolescent issue. Given that studies of cyberbullying among undergraduate students are not fully developed, although existence of the phenomenon is proven, we conclude that the college and university population needs special attention in future areas of research. As it has been indicated by Peled et al. (2012) that firm policy in regard to academic cheating reduces its occurrence, colleges should draw clear guidelines to deal with the problem of cyberbullying, part of it should be a safe and if needed anonymous report system as well as clear punishing policy for perpetrators.
As there's very little research on the effect of cyberbullying on undergraduates students, especially in light of the availability of hand held devices (mainly smartphones) and the dependence on the internet for basically every and any activity, the additional data provided in this research adds to the understanding of the effect of cyberbullying on the welfare of undergraduate students.
Declarations
Author contribution statement.
Yehuda Peled: Conceived and designed the experiments; Performed the experiments; Analyzed and interpreted the data; Contributed reagents, materials, analysis tools or data; Wrote the paper.
Funding statement
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Competing interest statement
The authors declare no conflict of interest.
Additional information
No additional information is available for this paper.
- Akbulut Y., Eristi B. Cyberbullying and victimization among Turkish university students. Australas. J. Educ. Technol. 2011; 27 (7):1155–1170. [ Google Scholar ]
- Akcil S. Kent State University; 2018. Cyberbullying-Victimization, Acculturative Stress, and Depression Among International College Students. Doctoral dissertation. [ Google Scholar ]
- Anton D.W., Reed R.J. Psychological Assessment Resources, Inc; 1991. College Adjustment Scales. [ Google Scholar ]
- Baldasare A., Bauman S., Goldman L., Robie A. Cyberbullying: voices of college students. Cutting Edge Technol. Higher Educ. 2012; 5 :127–155. https://studentaffairs.arizona.edu/assessment/documents/CyberbullyChapterFinal.pdf Retrieved from. [ Google Scholar ]
- Beebe J.E. University of Northern Colorado; 2010. The Prevalence of Cyber Bullying Victimization and its Relationship to Academic, Social, and Emotional Adjustment Among College Students. https://eric.ed.gov/?id=ED517400 ProQuest LLC, Ph.D. Dissertation. [ Google Scholar ]
- Belsey B. 2006. Cyber Bullying: an Emerging Threat to “Always on” Generation. http://www.cyberbullying.ca/pdf/Cyberbullying_Article_by_Bill_Belsey.pdf From. [ Google Scholar ]
- Cahill S., Makadon H. Sexual orientation and gender identity data collection in clinical settings and in electronic health records: a key to ending LGBT health disparities. LGBT Health. 2014; 1 (1):34–41. [ PubMed ] [ Google Scholar ]
- Clark D.M.T., Loxton N.J., Tobin S.J. Declining loneliness over time: evidence from American colleges and high schools. Pers. Soc. Psychol. Bull. 2015; 41 (1):78–89. [ PubMed ] [ Google Scholar ]
- Dalia–Global consumer understanding . 2016. Counting the LGBT Population: 6% of Europeans Identify as LGBT. https://daliaresearch.com/counting-the-lgbt-population-6-of-europeans-identify-as-lgbt/ [ Google Scholar ]
- DeHue F., Bolman C., Völlink T. Cyberbullying: youngsters' experiences and parental perception. Cyberpsychol. Behav. 2008; 11 (2):217–223. [ PubMed ] [ Google Scholar ]
- Dılmaç B. Psychological needs as a predictor of cyber bullying: a preliminary report on college students. Educ. Sci. Theor. Pract. 2009; 9 (3):1307–1325. [ Google Scholar ]
- Faryadi Q. Cyber bullying and academic performance. Int. J. Comput. Eng. Res. 2011; 1 (1):2250–3005. [ Google Scholar ]
- Faucher C., Jackson M., Cassidy W. Cyberbullying among university students: gendered experiences, impacts, and perspectives. Educ. Res. Int. 2014 [ Google Scholar ]
- Gálik S., Hladíková V., Pavlák L. Cyberbullying and opportunities for its prevention. Media Lit. Acad. Res. 2018; 1 (1):6–17. [ Google Scholar ]
- Gahagan K., Vaterlaus J.M., Frost L.R. College student cyberbullying on social networking sites: conceptualization, prevalence, and perceived bystander responsibility. Comput. Hum. Behav. 2016; 55 :1097–1105. [ Google Scholar ]
- Gates G.J. The Williams Institute, UCLA School of Law; 2011. How many People Are Lesbian, Gay, Bisexual and Transgender? https://escholarship.org/uc/item/09h684x2 [ Google Scholar ]
- Gerdes H., Mallinckrodt B. Emotional, social, and academic adjustment of college students: a longitudinal study of retention. J. Couns. Dev. 1994; 72 (3):281–288. [ Google Scholar ]
- Ghadampour F., Shafiei M., Heidarirad H. Relationships among cyberbullying, psychological vulnerability and suicidal thoughts in female and male students. J. Res. Psychol. Health. 2017; 11 :28–40. [ Google Scholar ]
- Grene M.B. Counselling and climate change as treatment modalities for bullying in school. Int. J. Adv. Couns. 2003; 25 (4):293–302. [ Google Scholar ]
- Heiman T., Olenik Shemesh D. Predictors of cyber-victimization of higher-education students with and without learning disabilities. J. Youth Stud. 2018:1–18. [ Google Scholar ]
- Inkelas K.K., Daver Z.E., Vogt K.E., Leonard J.B. Living–learning programs and first-generation college students’ academic and social transition to college. Res. High. Educ. 2007; 48 (4):403–434. [ Google Scholar ]
- Juvonen J., Graham S., Shuster M.A. Bullying among young adolescents: the strong, the weak, and the troubled. Paediatrics. 2003; 112 (6):1231–1237. [ PubMed ] [ Google Scholar ]
- Juvonen J., Gross E.F. Extending the school grounds?—bullying experiences in cyberspace. J. Sch. Health. 2008; 78 (9):496–505. [ PubMed ] [ Google Scholar ]
- Kowalski R.M., Limber S.P. Electronic bullying among middle school children. J. Adolesc. Health. 2007; 41 :S22–S30. [ PubMed ] [ Google Scholar ]
- Kowalski R., Limber S.P., McCord A. A developmental approach to cyberbullying: prevalence and protective factors. Aggress. Violent Behav. 2018 [ Google Scholar ]
- Lau L.K. Institutional factors affecting student retention. Education. 2003; 124 (1):126–137. [ Google Scholar ]
- McGrath S. 2005. The Multiple Contexts of Vocational Education and Training in Southern Africa. Vocational Education and Training in Southern Africa: a Comparative Study; pp. 1–8. http://hdl.handle.net/20.500.11910/7250 URI: [ Google Scholar ]
- Merriam-Webster . 2017. On-line Dictionary. https://www.merriam-webster.com/dictionary/cyberbullying [ Google Scholar ]
- Myers C.A., Cowie H. Bullying at university: the social and legal contexts of cyberbullying among university students. J. Cross Cult. Psychol. 2017; 48 (8):1172–1182. [ Google Scholar ]
- Na H. 2014. The Effects of Cyberbullying Victimization on Psychological Adjustments Among College Students. https://dspace-prod.lib.uic.edu/bitstream/handle/10027/11288/Na_Hyunjoo.pdf?sequence=1&isAllowed=y Doctoral dissertation. [ Google Scholar ]
- Parker J.D., Summerfeldt L.J., Hogan M.J., Majeski S.A. Emotional intelligence and academic success: examining the transition from high school to university. Pers. Indiv. Differ. 2004; 36 (1):163–172. [ Google Scholar ]
- Peled Y., Barczyk C., Sarid M. Institutional Characteristics and faculty perceptions of academic dishonesty. Educ. Pract. Theor. 2012; 34 (2):61–79. [ Google Scholar ]
- Pollock S.L. Counsellor roles in dealing with bullies and their LGBT victims. Middle Sch. J. 2006; 38 (2):29–36. [ Google Scholar ]
- Poole S.P. Vol. 115. 2017. The Experience of Victimization as the Result of Cyberbullying Among College Students: A Study of Demographics, Self-Esteem, and Locus of Control. http://scholarworks.sfasu.edu/etds/115 Electronic Theses and Dissertations. [ Google Scholar ]
- Rey L., Extremera N., Pena M. Perceived emotional intelligence, self-esteem and life satisfaction in adolescents. Psychosoc. Interv. 2011; 20 (2) [ Google Scholar ]
- Rivers I. Homophobic and transphobic bullying in universities. In: Cowie H., Myers C.-A., editors. Bullying Among university Students. Routledge; London, England: 2016. pp. 48–60. [ Google Scholar ]
- Rivituso G. 2012. Cyberbullying: an Exploration of the Lived Experiences and the Psychological Impact of Victimization Among College Students an Interpretive Phenomenological Analysis. Education Doctoral Theses. Paper 21. [ Google Scholar ]
- Selkie E.M., Kota R., Chan Y.F., Moreno M. Cyberbullying, depression, and problem alcohol use in female college students: a multisite study. Cyberpsychol. Behav. Soc. Netw. 2015; 18 (2):79–86. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Schenk A.M., Fremouw W.J. Prevalence, psychological impact, and coping of cyberbully victims among college students. J. Sch. Violence. 2012; 11 :21–37. [ Google Scholar ]
- Tinto V. Dropout from higher education: a theoretical synthesis of recent research. Rev. Educ. Res. 1975; 45 (1):89–125. [ Google Scholar ]
- Varghese M.E., Pistole M.C. College student cyberbullying: self-esteem, depression, loneliness, and attachment. J. Coll. Couns. 2017; 20 (1):7–21. [ Google Scholar ]
- Walker C.M., Sockman B.J., Koehn S. An exploratory study of cyberbullying with undergraduate university students. TechTrends. 2011; 55 (2):31–38. [ Google Scholar ]
- Watts L.K., Wagner J., Velasquez B., Behrens P.I. Cyberbullying in higher education: a literature review. Comput. Hum. Behav. 2017; 69 :268–274. [ Google Scholar ]
- Webber M.A., Ovedovitz A.C. Cyberbullying among college students: a look at its prevalence at a U.S. Catholic University. Int. J. Educ. Methodol. 2018; 4 (2):101–107. [ Google Scholar ]
- Ybarra M.L., Mitchell K.J. Prevalence and frequency of internet harassment instigation: implications for adolescent health. J. Adolesc. Health. 2007; 41 :189–195. [ PubMed ] [ Google Scholar ]
- Ziapour A., Khatony A., Jafari F., Kianipour N. Correlation of personality traits with happiness among university students. J. Clin. Diagn. Res. 2018; 12 (4) [ Google Scholar ]
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Sustainability
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering

Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Study reveals the benefits and downside of fasting
Press contact :, media download.

*Terms of Use:
Images for download on the MIT News office website are made available to non-commercial entities, press and the general public under a Creative Commons Attribution Non-Commercial No Derivatives license . You may not alter the images provided, other than to crop them to size. A credit line must be used when reproducing images; if one is not provided below, credit the images to "MIT."

Previous image Next image
Low-calorie diets and intermittent fasting have been shown to have numerous health benefits: They can delay the onset of some age-related diseases and lengthen lifespan, not only in humans but many other organisms.
Many complex mechanisms underlie this phenomenon. Previous work from MIT has shown that one way fasting exerts its beneficial effects is by boosting the regenerative abilities of intestinal stem cells, which helps the intestine recover from injuries or inflammation.
In a study of mice, MIT researchers have now identified the pathway that enables this enhanced regeneration, which is activated once the mice begin “refeeding” after the fast. They also found a downside to this regeneration: When cancerous mutations occurred during the regenerative period, the mice were more likely to develop early-stage intestinal tumors.
“Having more stem cell activity is good for regeneration, but too much of a good thing over time can have less favorable consequences,” says Omer Yilmaz, an MIT associate professor of biology, a member of MIT’s Koch Institute for Integrative Cancer Research, and the senior author of the new study.
Yilmaz adds that further studies are needed before forming any conclusion as to whether fasting has a similar effect in humans.
“We still have a lot to learn, but it is interesting that being in either the state of fasting or refeeding when exposure to mutagen occurs can have a profound impact on the likelihood of developing a cancer in these well-defined mouse models,” he says.
MIT postdocs Shinya Imada and Saleh Khawaled are the lead authors of the paper, which appears today in Nature .
Driving regeneration
For several years, Yilmaz’s lab has been investigating how fasting and low-calorie diets affect intestinal health. In a 2018 study , his team reported that during a fast, intestinal stem cells begin to use lipids as an energy source, instead of carbohydrates. They also showed that fasting led to a significant boost in stem cells’ regenerative ability.
However, unanswered questions remained: How does fasting trigger this boost in regenerative ability, and when does the regeneration begin?
“Since that paper, we’ve really been focused on understanding what is it about fasting that drives regeneration,” Yilmaz says. “Is it fasting itself that’s driving regeneration, or eating after the fast?”
In their new study, the researchers found that stem cell regeneration is suppressed during fasting but then surges during the refeeding period. The researchers followed three groups of mice — one that fasted for 24 hours, another one that fasted for 24 hours and then was allowed to eat whatever they wanted during a 24-hour refeeding period, and a control group that ate whatever they wanted throughout the experiment.
The researchers analyzed intestinal stem cells’ ability to proliferate at different time points and found that the stem cells showed the highest levels of proliferation at the end of the 24-hour refeeding period. These cells were also more proliferative than intestinal stem cells from mice that had not fasted at all.
“We think that fasting and refeeding represent two distinct states,” Imada says. “In the fasted state, the ability of cells to use lipids and fatty acids as an energy source enables them to survive when nutrients are low. And then it’s the postfast refeeding state that really drives the regeneration. When nutrients become available, these stem cells and progenitor cells activate programs that enable them to build cellular mass and repopulate the intestinal lining.”
Further studies revealed that these cells activate a cellular signaling pathway known as mTOR, which is involved in cell growth and metabolism. One of mTOR’s roles is to regulate the translation of messenger RNA into protein, so when it’s activated, cells produce more protein. This protein synthesis is essential for stem cells to proliferate.
The researchers showed that mTOR activation in these stem cells also led to production of large quantities of polyamines — small molecules that help cells to grow and divide.
“In the refed state, you’ve got more proliferation, and you need to build cellular mass. That requires more protein, to build new cells, and those stem cells go on to build more differentiated cells or specialized intestinal cell types that line the intestine,” Khawaled says.
Too much of a good thing
The researchers also found that when stem cells are in this highly regenerative state, they are more prone to become cancerous. Intestinal stem cells are among the most actively dividing cells in the body, as they help the lining of the intestine completely turn over every five to 10 days. Because they divide so frequently, these stem cells are the most common source of precancerous cells in the intestine.
In this study, the researchers discovered that if they turned on a cancer-causing gene in the mice during the refeeding stage, they were much more likely to develop precancerous polyps than if the gene was turned on during the fasting state. Cancer-linked mutations that occurred during the refeeding state were also much more likely to produce polyps than mutations that occurred in mice that did not undergo the cycle of fasting and refeeding.
“I want to emphasize that this was all done in mice, using very well-defined cancer mutations. In humans it’s going to be a much more complex state,” Yilmaz says. “But it does lead us to the following notion: Fasting is very healthy, but if you’re unlucky and you’re refeeding after a fasting, and you get exposed to a mutagen, like a charred steak or something, you might actually be increasing your chances of developing a lesion that can go on to give rise to cancer.”
Yilmaz also noted that the regenerative benefits of fasting could be significant for people who undergo radiation treatment, which can damage the intestinal lining, or other types of intestinal injury. His lab is now studying whether polyamine supplements could help to stimulate this kind of regeneration, without the need to fast.
“This fascinating study provides insights into the complex interplay between food consumption, stem cell biology, and cancer risk,” says Ophir Klein, a professor of medicine at the University of California at San Francisco and Cedars-Sinai Medical Center, who was not involved in the study. “Their work lays a foundation for testing polyamines as compounds that may augment intestinal repair after injuries, and it suggests that careful consideration is needed when planning diet-based strategies for regeneration to avoid increasing cancer risk.”
The research was funded, in part, by Pew-Stewart Scholars Program for Cancer Research award, the MIT Stem Cell Initiative, the Koch Institute Frontier Research Program via the Kathy and Curt Marble Cancer Research Fund, and the Bridge Project, a partnership between the Koch Institute for Integrative Cancer Research at MIT and the Dana-Farber/Harvard Cancer Center.
Share this news article on:
Press mentions, medical news today.
A new study led by researchers at MIT suggests that fasting and then refeeding stimulates cell regeneration in the intestines, reports Katharine Lang for Medical News Today . However, notes Lang, researchers also found that fasting “carries the risk of stimulating the formation of intestinal tumors.”
Prof. Ömer Yilmaz and his colleagues have discovered the potential health benefits and consequences of fasting, reports Max Kozlov for Nature . “There is so much emphasis on fasting and how long to be fasting that we’ve kind of overlooked this whole other side of the equation: what is going on in the refed state,” says Yilmaz.
MIT researchers have discovered how fasting impacts the regenerative abilities of intestinal stem cells, reports Ed Cara for Gizmodo . “The major finding of our current study is that refeeding after fasting is a distinct state from fasting itself,” explain Prof. Ömer Yilmaz and postdocs Shinya Imada and Saleh Khawaled. “Post-fasting refeeding augments the ability of intestinal stem cells to, for example, repair the intestine after injury.”
Previous item Next item
Related Links
- Omer Yilmaz
- Koch Institute
- Department of Biology
Related Topics
Related articles.

How early-stage cancer cells hide from the immune system

Study links certain metabolites to stem cell function in the intestine

Fasting boosts stem cells’ regenerative capacity

How diet influences colon cancer
More mit news.

How MIT’s online resources provide a “highly motivating, even transformative experience”
Read full story →

Students learn theater design through the power of play

A framework for solving parabolic partial differential equations

Designing better delivery for medical therapies

Making a measurable economic impact

Faces of MIT: Jessica Tam
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
After losing a $1.6 million inheritance, Harriet Spring says banks need to do more to protect customers from fraud
Topic: Scams and Fraud
Harriet Spring deposited $1.6 million into a Westpac account, and never saw the money again. ( ABC News: Mark Moore )
Harriet Spring was "groomed" by a man claiming to be from ING Bank, then handed over $1.6 million of her mother's money. She says change to the banking system is needed now.
Federal Financial Services Minister Stephen Jones says banks, social media giants and telcos all need to work together.
What's next?
Bolstered codes of practice for all three industries are set to come into place by the end of the year.
Harriet Spring's mother Elaine died 10 days ago, but the $1.6 million she accumulated over her 95-year life is nowhere to be seen.
"What she thought she had produced in her lifetime won't go to her family," said Ms Spring.
In February, Harriet Spring helped her mother sell her home that had been in the family for three generations.
After the sale, she was called by a man claiming to be from ING Bank, who had what Ms Spring described as a "posh" English accent.
"He told me he was from the ING term deposit section, and coincidentally, I was looking for a term deposit for my mother's money."
After months of regular phone calls from the scammer, a process Ms Spring saw as a form of "grooming", Ms Spring deposited her mother's $1.6 million into a Westpac account.
She never saw the money again.
"The money was stolen," she said.
"People are going to say boohoo, we lost our intergenerational wealth, but this money isn't going to good deeds or a charity.
"The fact is, it doesn't belong to anyone else other than my mother. And it's gone."
Ms Spring has confirmed the money, which was set to be distributed amongst 15 family members, has not been recouped.
"It's the difference of people getting businesses off the ground, buying first homes, I myself will have to work for another 10 years beyond what I had hoped to work.
"My mother was an Order of Australia medallist for services to charity. This isn't the legacy she deserved."
Dispute over scam stats: are they going down?
Australians made more than 600,000 scam reports last year, reporting losses of $2.7 billion overall.
Despite the number of reported scams increasing, the amount lost in 2023 was down compared to 2022, when Australians lost a record $3.1 billion.
The federal government has claimed this as a win, saying this is the first time in six years that scam losses have decreased year-on-year.
But there is disagreement about whether the federal government's strategy is placing enough responsibility on the banking sector to stamp out scams.
Consumer groups and victims have called on the Australian government to follow the UK, where a new scheme is set to force banks to compensate scam victims.
It is a cause Harriet Spring supports wholeheartedly — she thinks if she was scammed in the UK, she would probably have been able to recoup some of the money she lost.
Harriet Spring helped her mother sell her home that had been in the family for three generations. ( ABC News: Mark Moore )
At the National Press Club this week, Minister for Financial Services Stephen Jones was asked multiple times why he was pursuing a code of conduct system to stamp out scams, instead of a UK-style compensation model.
He said he was not convinced the UK model would be more effective, and argued it also was not fair.
"There are many players within the scam ecosystem, telecommunications companies, social media platforms and banks.
"Some of them are some of the biggest companies in the world — our big four banks are wealthy and they make a lot of profit and they should make a contribution to uplifting the standards and compensating victims."
"But if you look at the market capitalisation of some of the players in the social media area, who are publishing the scams, taking advertising revenue from the scams, have some of the best IT available in the world, and you are saying it's a fairer, better and more effective system that we hold someone like the Broken Hill credit union accountable for a scam which propagated and published on a social media platform, [and] they have made money out of, but, it's not the responsibility of the social media platform to do anything about it? I'm sorry, I just don't agree."
Banks 'pile on the injustice' to their customers, says consumer advocate
But figures from consumer watchdog the ACCC suggest only 6 per cent of reported scams in 2023 began on social media.
Stephanie Tonkin, chief executive of advocacy group the Consumer Action Law Centre, says banks "pile on the injustice" facing scammed customers by denying responsibility for refunds.
"Instead of accepting responsibility … [they] blame their customers who pay them to keep their money safe from increasingly sophisticated crimes and deception," she said.
"The onus continues to be on the customer to avoid being scammed against malignant forces over which they have no control and it's exasperating banks offer little help."
Mr Jones's approach has the support of banking lobby groups.
Anna Bligh, chief executive of the Australian Banking Association, which represents banks including Australia's four largest, said: "Winning the war against scammers can only be achieved through a collective effort across the economy, including from government, banks, telecommunications companies and social media platforms.
"Focusing liability on one industry, such as banks, risks undermining the success of an entire scams chain approach."
Ms Bligh said Australian banks had scam protection measures that were "among the best in the world" and noted scams were reducing at a faster rate in Australia than in the UK.
"There is a good reason why no other country in the world has adopted a UK-style reimbursement model."
Mr Jones told the press club there were a number of reforms slated for the banking system, including a "payee confirmation" reform that will add another layer of security to transactions.
This measure was recommended by the ACCC in 2022, and is set to be in place by the end of 2025 provided legislation passes parliament.
It's not the only measure the federal government is taking.
It's also spending $86 million on a national effort to prevent scams, and has created a national centre to report scams and distribute information to banks, law enforcement and vulnerable communities.
But for Harriet Spring, who points out it's the banks that ultimately facilitate the transfer of funds, that's not good enough.
"I mean, after all, what are the banks there for, if not to keep your money secure?" she said.
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Research: How to Build Consensus Around a New Idea
- Devon Proudfoot
- Wayne Johnson

Strategies for overcoming the disagreements that can stymie innovation.
Previous research has found that new ideas are seen as risky and are often rejected. New research suggests that this rejection can be due to people’s lack of shared criteria or reference points when evaluating a potential innovation’s value. In a new paper, the authors find that the more novel the idea, the more people differ on their perception of its value. They also found that disagreement itself can make people view ideas as risky and make them less likely to support them, regardless of how novel the idea is. To help teams get on the same page when it comes to new ideas, they suggest gathering information about evaluator’s reference points and developing criteria that can lead to more focused discussions.
Picture yourself in a meeting where a new idea has just been pitched, representing a major departure from your company’s standard practices. The presenter is confident about moving forward, but their voice is quickly overtaken by a cacophony of opinions from firm opposition to enthusiastic support. How can you make sense of the noise? What weight do you give each of these opinions? And what does this disagreement say about the idea?
- DP Devon Proudfoot is an Associate Professor of Human Resource Studies at Cornell’s ILR School. She studies topics related to diversity and creativity at work.
- Wayne Johnson is a researcher at the Utah Eccles School of Business. He focuses on evaluations and decisions about new information, including persuasion regarding creative ideas and belief change.
Partner Center
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Key things to know about U.S. election polling in 2024

Confidence in U.S. public opinion polling was shaken by errors in 2016 and 2020. In both years’ general elections, many polls underestimated the strength of Republican candidates, including Donald Trump. These errors laid bare some real limitations of polling.
In the midterms that followed those elections, polling performed better . But many Americans remain skeptical that it can paint an accurate portrait of the public’s political preferences.
Restoring people’s confidence in polling is an important goal, because robust and independent public polling has a critical role to play in a democratic society. It gathers and publishes information about the well-being of the public and about citizens’ views on major issues. And it provides an important counterweight to people in power, or those seeking power, when they make claims about “what the people want.”
The challenges facing polling are undeniable. In addition to the longstanding issues of rising nonresponse and cost, summer 2024 brought extraordinary events that transformed the presidential race . The good news is that people with deep knowledge of polling are working hard to fix the problems exposed in 2016 and 2020, experimenting with more data sources and interview approaches than ever before. Still, polls are more useful to the public if people have realistic expectations about what surveys can do well – and what they cannot.
With that in mind, here are some key points to know about polling heading into this year’s presidential election.
Probability sampling (or “random sampling”). This refers to a polling method in which survey participants are recruited using random sampling from a database or list that includes nearly everyone in the population. The pollster selects the sample. The survey is not open for anyone who wants to sign up.
Online opt-in polling (or “nonprobability sampling”). These polls are recruited using a variety of methods that are sometimes referred to as “convenience sampling.” Respondents come from a variety of online sources such as ads on social media or search engines, websites offering rewards in exchange for survey participation, or self-enrollment. Unlike surveys with probability samples, people can volunteer to participate in opt-in surveys.
Nonresponse and nonresponse bias. Nonresponse is when someone sampled for a survey does not participate. Nonresponse bias occurs when the pattern of nonresponse leads to error in a poll estimate. For example, college graduates are more likely than those without a degree to participate in surveys, leading to the potential that the share of college graduates in the resulting sample will be too high.
Mode of interview. This refers to the format in which respondents are presented with and respond to survey questions. The most common modes are online, live telephone, text message and paper. Some polls use more than one mode.
Weighting. This is a statistical procedure pollsters perform to make their survey align with the broader population on key characteristics like age, race, etc. For example, if a survey has too many college graduates compared with their share in the population, people without a college degree are “weighted up” to match the proper share.
How are election polls being conducted?
Pollsters are making changes in response to the problems in previous elections. As a result, polling is different today than in 2016. Most U.S. polling organizations that conducted and publicly released national surveys in both 2016 and 2022 (61%) used methods in 2022 that differed from what they used in 2016 . And change has continued since 2022.
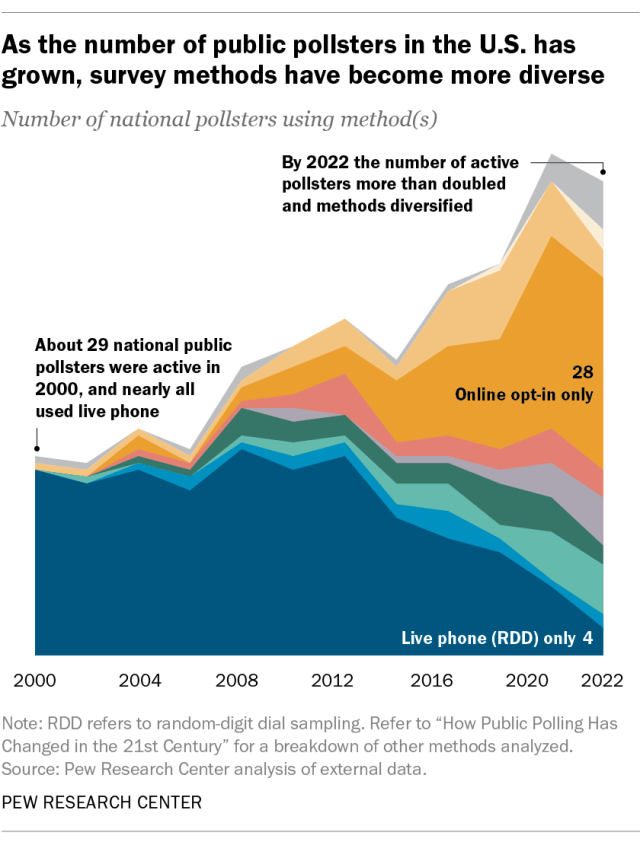
One change is that the number of active polling organizations has grown significantly, indicating that there are fewer barriers to entry into the polling field. The number of organizations that conduct national election polls more than doubled between 2000 and 2022.
This growth has been driven largely by pollsters using inexpensive opt-in sampling methods. But previous Pew Research Center analyses have demonstrated how surveys that use nonprobability sampling may have errors twice as large , on average, as those that use probability sampling.
The second change is that many of the more prominent polling organizations that use probability sampling – including Pew Research Center – have shifted from conducting polls primarily by telephone to using online methods, or some combination of online, mail and telephone. The result is that polling methodologies are far more diverse now than in the past.
(For more about how public opinion polling works, including a chapter on election polls, read our short online course on public opinion polling basics .)
All good polling relies on statistical adjustment called “weighting,” which makes sure that the survey sample aligns with the broader population on key characteristics. Historically, public opinion researchers have adjusted their data using a core set of demographic variables to correct imbalances between the survey sample and the population.
But there is a growing realization among survey researchers that weighting a poll on just a few variables like age, race and gender is insufficient for getting accurate results. Some groups of people – such as older adults and college graduates – are more likely to take surveys, which can lead to errors that are too sizable for a simple three- or four-variable adjustment to work well. Adjusting on more variables produces more accurate results, according to Center studies in 2016 and 2018 .
A number of pollsters have taken this lesson to heart. For example, recent high-quality polls by Gallup and The New York Times/Siena College adjusted on eight and 12 variables, respectively. Our own polls typically adjust on 12 variables . In a perfect world, it wouldn’t be necessary to have that much intervention by the pollster. But the real world of survey research is not perfect.
Predicting who will vote is critical – and difficult. Preelection polls face one crucial challenge that routine opinion polls do not: determining who of the people surveyed will actually cast a ballot.
Roughly a third of eligible Americans do not vote in presidential elections , despite the enormous attention paid to these contests. Determining who will abstain is difficult because people can’t perfectly predict their future behavior – and because many people feel social pressure to say they’ll vote even if it’s unlikely.
No one knows the profile of voters ahead of Election Day. We can’t know for sure whether young people will turn out in greater numbers than usual, or whether key racial or ethnic groups will do so. This means pollsters are left to make educated guesses about turnout, often using a mix of historical data and current measures of voting enthusiasm. This is very different from routine opinion polls, which mostly do not ask about people’s future intentions.
When major news breaks, a poll’s timing can matter. Public opinion on most issues is remarkably stable, so you don’t necessarily need a recent poll about an issue to get a sense of what people think about it. But dramatic events can and do change public opinion , especially when people are first learning about a new topic. For example, polls this summer saw notable changes in voter attitudes following Joe Biden’s withdrawal from the presidential race. Polls taken immediately after a major event may pick up a shift in public opinion, but those shifts are sometimes short-lived. Polls fielded weeks or months later are what allow us to see whether an event has had a long-term impact on the public’s psyche.
How accurate are polls?
The answer to this question depends on what you want polls to do. Polls are used for all kinds of purposes in addition to showing who’s ahead and who’s behind in a campaign. Fair or not, however, the accuracy of election polling is usually judged by how closely the polls matched the outcome of the election.
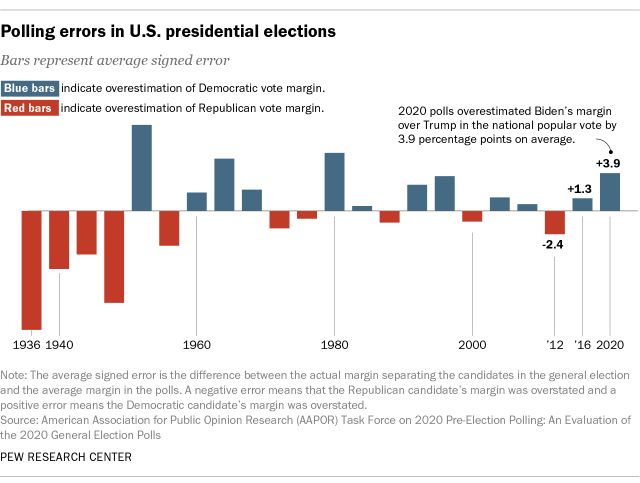
By this standard, polling in 2016 and 2020 performed poorly. In both years, state polling was characterized by serious errors. National polling did reasonably well in 2016 but faltered in 2020.
In 2020, a post-election review of polling by the American Association for Public Opinion Research (AAPOR) found that “the 2020 polls featured polling error of an unusual magnitude: It was the highest in 40 years for the national popular vote and the highest in at least 20 years for state-level estimates of the vote in presidential, senatorial, and gubernatorial contests.”
How big were the errors? Polls conducted in the last two weeks before the election suggested that Biden’s margin over Trump was nearly twice as large as it ended up being in the final national vote tally.
Errors of this size make it difficult to be confident about who is leading if the election is closely contested, as many U.S. elections are .
Pollsters are rightly working to improve the accuracy of their polls. But even an error of 4 or 5 percentage points isn’t too concerning if the purpose of the poll is to describe whether the public has favorable or unfavorable opinions about candidates , or to show which issues matter to which voters. And on questions that gauge where people stand on issues, we usually want to know broadly where the public stands. We don’t necessarily need to know the precise share of Americans who say, for example, that climate change is mostly caused by human activity. Even judged by its performance in recent elections, polling can still provide a faithful picture of public sentiment on the important issues of the day.
The 2022 midterms saw generally accurate polling, despite a wave of partisan polls predicting a broad Republican victory. In fact, FiveThirtyEight found that “polls were more accurate in 2022 than in any cycle since at least 1998, with almost no bias toward either party.” Moreover, a handful of contrarian polls that predicted a 2022 “red wave” largely washed out when the votes were tallied. In sum, if we focus on polling in the most recent national election, there’s plenty of reason to be encouraged.
Compared with other elections in the past 20 years, polls have been less accurate when Donald Trump is on the ballot. Preelection surveys suffered from large errors – especially at the state level – in 2016 and 2020, when Trump was standing for election. But they performed reasonably well in the 2018 and 2022 midterms, when he was not.
During the 2016 campaign, observers speculated about the possibility that Trump supporters might be less willing to express their support to a pollster – a phenomenon sometimes described as the “shy Trump effect.” But a committee of polling experts evaluated five different tests of the “shy Trump” theory and turned up little to no evidence for each one . Later, Pew Research Center and, in a separate test, a researcher from Yale also found little to no evidence in support of the claim.
Instead, two other explanations are more likely. One is about the difficulty of estimating who will turn out to vote. Research has found that Trump is popular among people who tend to sit out midterms but turn out for him in presidential election years. Since pollsters often use past turnout to predict who will vote, it can be difficult to anticipate when irregular voters will actually show up.
The other explanation is that Republicans in the Trump era have become a little less likely than Democrats to participate in polls . Pollsters call this “partisan nonresponse bias.” Surprisingly, polls historically have not shown any particular pattern of favoring one side or the other. The errors that favored Democratic candidates in the past eight years may be a result of the growth of political polarization, along with declining trust among conservatives in news organizations and other institutions that conduct polls.
Whatever the cause, the fact that Trump is again the nominee of the Republican Party means that pollsters must be especially careful to make sure all segments of the population are properly represented in surveys.
The real margin of error is often about double the one reported. A typical election poll sample of about 1,000 people has a margin of sampling error that’s about plus or minus 3 percentage points. That number expresses the uncertainty that results from taking a sample of the population rather than interviewing everyone . Random samples are likely to differ a little from the population just by chance, in the same way that the quality of your hand in a card game varies from one deal to the next.
The problem is that sampling error is not the only kind of error that affects a poll. Those other kinds of error, in fact, can be as large or larger than sampling error. Consequently, the reported margin of error can lead people to think that polls are more accurate than they really are.
There are three other, equally important sources of error in polling: noncoverage error , where not all the target population has a chance of being sampled; nonresponse error, where certain groups of people may be less likely to participate; and measurement error, where people may not properly understand the questions or misreport their opinions. Not only does the margin of error fail to account for those other sources of potential error, putting a number only on sampling error implies to the public that other kinds of error do not exist.
Several recent studies show that the average total error in a poll estimate may be closer to twice as large as that implied by a typical margin of sampling error. This hidden error underscores the fact that polls may not be precise enough to call the winner in a close election.
Other important things to remember
Transparency in how a poll was conducted is associated with better accuracy . The polling industry has several platforms and initiatives aimed at promoting transparency in survey methodology. These include AAPOR’s transparency initiative and the Roper Center archive . Polling organizations that participate in these organizations have less error, on average, than those that don’t participate, an analysis by FiveThirtyEight found .
Participation in these transparency efforts does not guarantee that a poll is rigorous, but it is undoubtedly a positive signal. Transparency in polling means disclosing essential information, including the poll’s sponsor, the data collection firm, where and how participants were selected, modes of interview, field dates, sample size, question wording, and weighting procedures.
There is evidence that when the public is told that a candidate is extremely likely to win, some people may be less likely to vote . Following the 2016 election, many people wondered whether the pervasive forecasts that seemed to all but guarantee a Hillary Clinton victory – two modelers put her chances at 99% – led some would-be voters to conclude that the race was effectively over and that their vote would not make a difference. There is scientific research to back up that claim: A team of researchers found experimental evidence that when people have high confidence that one candidate will win, they are less likely to vote. This helps explain why some polling analysts say elections should be covered using traditional polling estimates and margins of error rather than speculative win probabilities (also known as “probabilistic forecasts”).
National polls tell us what the entire public thinks about the presidential candidates, but the outcome of the election is determined state by state in the Electoral College . The 2000 and 2016 presidential elections demonstrated a difficult truth: The candidate with the largest share of support among all voters in the United States sometimes loses the election. In those two elections, the national popular vote winners (Al Gore and Hillary Clinton) lost the election in the Electoral College (to George W. Bush and Donald Trump). In recent years, analysts have shown that Republican candidates do somewhat better in the Electoral College than in the popular vote because every state gets three electoral votes regardless of population – and many less-populated states are rural and more Republican.
For some, this raises the question: What is the use of national polls if they don’t tell us who is likely to win the presidency? In fact, national polls try to gauge the opinions of all Americans, regardless of whether they live in a battleground state like Pennsylvania, a reliably red state like Idaho or a reliably blue state like Rhode Island. In short, national polls tell us what the entire citizenry is thinking. Polls that focus only on the competitive states run the risk of giving too little attention to the needs and views of the vast majority of Americans who live in uncompetitive states – about 80%.
Fortunately, this is not how most pollsters view the world . As the noted political scientist Sidney Verba explained, “Surveys produce just what democracy is supposed to produce – equal representation of all citizens.”
- Survey Methods
- Trust, Facts & Democracy
- Voter Files

Scott Keeter is a senior survey advisor at Pew Research Center .

Courtney Kennedy is Vice President of Methods and Innovation at Pew Research Center .
How do people in the U.S. take Pew Research Center surveys, anyway?
How public polling has changed in the 21st century, what 2020’s election poll errors tell us about the accuracy of issue polling, a field guide to polling: election 2020 edition, methods 101: how is polling done around the world, most popular.
901 E St. NW, Suite 300 Washington, DC 20004 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
© 2024 Pew Research Center

- News & Stories
Q&A: Understanding and Preventing Youth Firearm Violence
Jessika Bottiani discusses her research on the significant disparities in youth firearm violence and how understanding those gaps can help future prevention efforts.
Leslie Booren
August 26, 2024
This summer the United States Surgeon General Dr. Vivek Murthy released a landmark advisory on firearm violence , declaring it a public health crisis. According to the advisory, gun violence reaches across the lifespan and is currently the leading cause of death for children and adolescents in America.
Researchers at Youth-Nex, the UVA Center to Promote Effective Youth Development, have been examining some of the root causes of youth firearm violence disparities to better understand this crisis and how future prevention efforts may work.
Recently, the Society for Research on Adolescence (SRA) recognized Dr. Jessika Bottiani, an associate research professor at the UVA School of Education and Human Development and faculty affiliate at Youth-Nex, and her co-authors with the 2024 Social Policy Publication Award for a paper on the prevention of youth firearm violence disparities . SRA highlighted this review as work that should be read by all policymakers.
We sat down with Bottiani to learn more about this research review.
Q: Your paper examined research on youth firearm violence and firearm risk. What did you find?
A: Our review and synthesis of data demonstrated striking differences in firearm risk across intersectional identities. We separated out different types of firearm violence (e.g., homicide, suicide, injury), which revealed distinctions in risk across different demographic groups–most saliently gun homicide among Black boys and young men in urban settings.

A staggering degree of inequity in firearm fatalities is shouldered by Black boys and young men in this country, where the rate of firearm homicide is more than 20 times higher among Black boys and young men ages 15-24 than for white boys and young men in the same age groups. We also saw higher rates of gun suicide among white and Indigenous American boys and young men in rural areas of the United States.
When we examined rates by geography, we identified intersectional differences in risk that are important for policymakers to understand. For example, we saw that higher rates of firearm homicide among Black boys and young men were most salient in urban areas of the Midwest and south of the United States. Overlaying data onto maps demonstrated how young male suicide by firearm is also clustered geographically, for example, in rural counties in the Midwest and west for Indigenous young males, and in in rural counties in the west for White male youth (who have the second highest rate of suicide by firearm after Indigenous young males).
Q: Why was a review of the research specifically focused on disparities in youth firearm violence needed?
A: A lot of systematic and scoping reviews on firearm violence had come out in the literature around this time, but none of them focused on understanding why Black boys and young men in urban areas were so disproportionately affected, or why we were also seeing gaps affecting rural White boys and young men. This paper presented data that revealed the degree of these disparities and tried to understand the root causes.
We don’t pay enough attention to the role of racist historical policies and regulations that have calcified into today’s racially segregated geographies and poverty. With this paper, we wanted to reveal the way in which youth gun violence is inextricably bound to the history of race, place, and culture in the United States. The paper also delves into cultural norms around guns and masculinity. We feel insights on these aspects of context are vital for understanding how to address youth firearm violence.
Q: What future prevention efforts do you suggest in your paper?
A: We put forth a number of evidence-based solutions for settings ranging from emergency rooms to schools to address firearm violence at the individual level. Yet perhaps more importantly, we also provide suggestions for tackling the structural and sociocultural factors that underlie firearm violence.
At the community level, our recommendations range from violence interrupters to programs and policies that seek to disrupt racial segregation and redress housing inequities. We also note the potential for media campaigns addressing sociocultural norms to be a tool for prevention.
We provided a review of gun restriction and safety policies, and their potential effectiveness in addressing youth firearm violence (while also acknowledging the political climate wherein such policies have been increasingly challenged). We point out that some recent firearm related policies, purportedly race neutral in their language, had harmful impacts specifically on communities and people of color.
Individual level interventions or policies that seek to address only one piece of the puzzle are bound to be ineffective at scale. Rather, what is required are multisector, place-based initiatives that address structural factors related to poverty and the built environment in under-resourced segregated neighborhoods.
News Information
Media contact.
Audrey Breen
[email protected]
Research Center or Department
Featured faculty.
- Jessika H. Bottiani
Thought Leadership
News Topics
- Health & Wellness
Related News
Learning Mindset Could Be Key to Addressing Medical Students’ Alarming Burnout
Too Much Treadmill? Outdoor Training Could Help Your Shin Splints
How Summer Mindfulness Practices Can Help Mitigate School-year Stress
Summer Fun Can Help Students Find Belonging
- Alzheimer's disease & dementia
- Arthritis & Rheumatism
- Attention deficit disorders
- Autism spectrum disorders
- Biomedical technology
- Diseases, Conditions, Syndromes
- Endocrinology & Metabolism
- Gastroenterology
- Gerontology & Geriatrics
- Health informatics
- Inflammatory disorders
- Medical economics
- Medical research
- Medications
- Neuroscience
- Obstetrics & gynaecology
- Oncology & Cancer
- Ophthalmology
- Overweight & Obesity
- Parkinson's & Movement disorders
- Psychology & Psychiatry
- Radiology & Imaging
- Sleep disorders
- Sports medicine & Kinesiology
- Vaccination
- Breast cancer
- Cardiovascular disease
- Chronic obstructive pulmonary disease
- Colon cancer
- Coronary artery disease
- Heart attack
- Heart disease
- High blood pressure
- Kidney disease
- Lung cancer
- Multiple sclerosis
- Myocardial infarction
- Ovarian cancer
- Post traumatic stress disorder
- Rheumatoid arthritis
- Schizophrenia
- Skin cancer
- Type 2 diabetes
- Full List »
share this!
August 27, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
trusted source
Ohio study reveals high risk of overdose deaths among those using drugs when they're alone
by Case Western Reserve University

In Cuyahoga County, the stark reality of the opioid crisis is that most drug overdose victims die alone, with no one nearby to help. A recent study , done in partnership with Case Western Reserve University and Cuyahoga County, highlights the critical need for "targeted harm-reduction strategies" in Northeast Ohio, where the opioid epidemic continues to claim lives at nearly twice the national average. The paper is published in the journal Substance Use & Misuse .
Those strategies include the distribution of Naloxone (an opioid antagonist that can reverse the effects of an overdose ), and increasing the availability of medication-assisted treatment options and fentanyl test strips.
The research, using data from the Cuyahoga County Medical Examiner's Office, examined overdose deaths between 2016 and 2020, focusing on people using drugs when they were alone.
The study revealed that a staggering 75% of overdose victims were using drugs alone, a behavior strongly associated with increased mortality. Key findings indicate that individuals using drugs alone were more likely to be at home and less likely to receive life-saving interventions like naloxone, said Daniel Flannery, the Dr. Semi J. and Ruth Begun Professor and director of the Begun Center for Violence Prevention Research and Education at CWRU's Jack, Joseph and Morton Mandel School of Applied Social Sciences.
"Being informed is crucial—knowledge equips you to take action," Flannery said. "It's about reviving someone in need, and if that's not possible, contacting emergency services immediately. The chances of a fatal outcome significantly increase when there's no one around to help."
New policies and community efforts must prioritize reaching individuals at risk of using alone to curb the devastating impact of the opioid crisis, said Vaishali Deo, research associate at the Begun Center and co-principal investigator in the research.
"Our findings underscore the urgent need for innovative harm-reduction strategies aimed at those most vulnerable—those using drugs alone," Deo said. "Interventions must focus on reducing isolation and improving access to emergency medical care to prevent further loss of life."
Additional insights include:
- In Cuyahoga County, from 2016 through 2020, there were 2,944 unintentional overdose deaths for those over 18 years old. That's 54 deaths per 100,000 residents. The national average is 28 overdose deaths per 100,000 residents.
- The study further details the demographics and circumstances surrounding overdose deaths in Cuyahoga County from 2016 to 2020. Most were non-Hispanic (94.9%), white (72.2%) and male (71.3%), with a significant portion 35 to 64 years old. Most lived in the City of Cleveland. Over half attained at least a high school diploma.
- Toxicology reports revealed that synthetic opioids, specifically illicitly manufactured fentanyl, was present in 72.7% of the deaths. Cocaine and heroin were also significant contributors, found in 41.6% and 29.6% of cases, respectively. Nearly 80% of overdose deaths involved the use of multiple substances.
- Despite the presence of bystanders in more than half the cases, most victims (74.9%) were using drugs alone at the time of their fatal overdose, mainly at home. Emergency medical services responded to most of the incidents, yet over 60% of victims were pronounced dead at the scene—highlighting the critical timing needed for interventions like naloxone, which was administered in just 28.6% of the cases.
Deo and Flannery were joined in the research by Sarah Fulton, a research associate at the Begun Center, and Manreet K. Bhullar, a senior forensic epidemiologist at the Cuyahoga County Medical Examiner's Office, and Thomas P. Gilson, chief medical examiner of Cuyahoga County.
"These findings paint a stark picture of the opioid crisis in our community," Gilson said. "The tragic reality is that too many people are dying alone, and we must act swiftly to implement lifesaving measures that can prevent these unnecessary deaths."
Explore further
Feedback to editors

Managing early stages of abortion care at home after 12 weeks is safe and reduces time spent in hospital, study finds
4 hours ago

Billions worldwide consume inadequate levels of micronutrients critical to human health, new study finds

Blocking the longevity gene S6K1 extends lifespan in mice by reducing inflammation
6 hours ago

Machine learning predicts which patients will continue taking opioids after hand surgery

Study describes a new molecular pathway involved in the control of reproduction

Machine learning helps identify rheumatoid arthritis subtypes
7 hours ago

Immune protection against tuberculosis reinfection driven by cells that dampen lung inflammation, shows study

Girls with mental health conditions have lower HPV vaccination coverage

Mankai plant found to reduce post-meal sugar levels in diabetics
8 hours ago

Unique chicken line advances research on autoimmune disease that affects humans
Related stories.

Preventing fatal overdoses in the local community
Sep 15, 2023

Researchers warn of next 'wave' of opioid overdose deaths
Nov 30, 2021

Naloxone, witnessed overdoses could reduce opioid-related deaths
Jun 27, 2024

At least 9 dead, dozens treated in Texas capital after unusual spike in overdoses
May 2, 2024

Analysis finds racial inequities in naloxone administration during fatal overdoses
May 29, 2024

Biden administration calls for greater access to overdose antidote
Mar 13, 2024
Recommended for you

Mechanisms of how morphine relieves pain mapped out
9 hours ago

Access to opioid agonist treatment in prisons saves lives, researchers say
13 hours ago

Researchers find e-cigarette use disrupts the nasal microbiome
Aug 26, 2024

Frequent cannabis users miss more workdays, research shows

A compound in rosemary extract can reduce cocaine sensitivity
Aug 20, 2024
Let us know if there is a problem with our content
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Medical Xpress in any form.
Newsletter sign up
Get weekly and/or daily updates delivered to your inbox. You can unsubscribe at any time and we'll never share your details to third parties.
More information Privacy policy
Donate and enjoy an ad-free experience
We keep our content available to everyone. Consider supporting Science X's mission by getting a premium account.
E-mail newsletter
Economics JIW - Tips for Choosing a Topic: Home
Choosing a topic.
Choosing a topic that can answer an economic research question is challenging. Some tips:
- Ripped from the headlines rarely makes a good economic paper. You will be using data to determine causation or correlation. Sometimes a similar event can be used. Topics such as artificial intelligence may make a good policy paper but not a good economic one due to lack of data.
- Literature Review: Your JIW should use primarily scholarly sources. Start with Econlit (the database of the American Economic Association). Econlit indexes major journals, working papers, conference proceedings, dissertations, and chapters in critical books. It takes a long time for scholarly literature to appear. Preprints are called working papers in economics and major ones are indexed in Econlit. Y ou are your own research team and have limited time. Many articles are written over a couple of years and involve many people gathering and cleaning the data. Some starting places: see https://libguides.princeton.edu/econliterature/gettingstarted
- Outside of finance and some macroeconomic data, most data will not have many points in time. Data determines the methods used . While a linear regression can be great for time series data, it is likely not what you will use for survey data.
- Longitudinal or panel study : same group of individuals is interviewed at intervals over a period of time. This can be very useful to observe changes over time. Keep in mind when using a long running longitudinal dataset that the panel generally is not adding new participants so may not reflect today’s demographics.
- Cross-sectional study : data from particular subjects are obtained only once. While you are studying different individuals each time, you are looking at individuals with similar demographic characteristics. Demography is typically rebalanced to reflect the population.
- Summary statistics : aggregated counts of survey or administrative data.
- Typically around a 2 year time lag from the time the survey data is collected to the time of release. The Economic Census and Census of Agriculture take about 4 years for all data to be released. Many surveys never release the microdata.
- Very little subnational data is available and is often restricted when available. State level macro data for the United States is more prevalent. City level data is often a case study or only available for very large cities.
- Many micro-level datasets are restricted. It is not uncommon to wait a year before getting permission or denial to use the data. Each organization has its own rules.
- Historical data in electronic format prior to 1950 is rare. Most governmental links provide current data only.
- What is measured changes over time . Do not assume modern concepts were tracked in the past. Definitions of indicators often change over time.
- Data cannot be made more frequent. Many items are collected annually or even once a decade. Major macroeconomic indicators such as GDP tend to be quarterly but some countries may only estimate annually.
- What exists for one country may not exist for another country. Data is generally inconsistent across borders .
- Documentation is typically in the native language .
- Always look at the methodology. The methodology section is one of the most important parts of the paper. Someone should be able to replicate your work. Describe the dataset and its population. Describe how the data was subset, any filters used, and any adjustment methods. While you are likely not trying to publish in American Economic Review or Journal of Finance , these are the gold standards. See how they layout the articles and in particular the methodology and data sections.
- The basic question to ask when looking for economic data is " who cares about what i am studying ?" Unfortunately, the answer may be no one. Ideally, look for an organization that is concerned with your research as part of its mission. Examples include the International Labor Organization or the Bureau of Labor Statistics focusing on labor research; the International Monetary Fund or the Board of Governors of the Federal Reserve System focusing on monetary and fiscal concerns; the World Bank focusing on development; and the World Health Organization focusing on health. This does not mean these organizations collect data on all topics related to that field.
- Find a topic for which there is literature and data but allows room to add a contribution. Topics such as sports and music are popular due to personal interests but may not make good research topics due to lack of data and overuse.
More tips:
- Data is typically not adjusted for inflation. It is usually presented in current (nominal) currency. This means the numbers as they originally appeared. When data has been adjusted for inflation (constant or real), a base year such as 2020 or 1990 will be shown. If a base year is not provided, then data is current and therefore not adjusted for inflation. If given a choice, choose current dollars. Data is often derived from different datasets and many will use different base years. Adjust everything at the end. It is easier than doing reverse math!
- While most datasets are consistent within the dataset for currency used such as all in US Dollars or Euro or Japanese Yen or each item in local currency, some will mix and match. LCU is a common abbreviation meaning local currency units. Consider looking at percent changes rather than actual values. If adjusting use the exchange rate for each period of time, not the latest one.
- Economic indicators may be either seasonally adjusted or not seasonally adjusted. This is very common for employment and retail sales. Unless something says it is seasonally adjusted, it is not. Be consistent and note in methodology.
Librarians are here to help! Librarians can help to devise a feasible topic, assist with the literature search, and choose appropriate data. Your data may fall into multiple categories. Think of the primary aspect of your topic in terms of first contact. Do not email librarians individually. If unsure who to contact either put all that apply on same email or email just one. If that person is not the best, they will refer you.
Bobray Bordelon Economics, Finance, & Data Librarian [email protected]
Charissa Jefferson
Labor Librarian [email protected]
Mary Carter Finance and Operations Research Librarian [email protected]
Data workshops
- Environmental and energy data (Bordelon), 9/23/2024 - 7:30-8:50 pm
- Health, Crime and other Socioeconomic Data (Bordelon), 9/23/2024 and 10/02/2024 - 3-4:20 pm
- Macroeconomics and trade data (Bordelon), 9/25/2024 and 9/30/2024 - 3-4:20 pm
- Finance data (Carter), 9/23/2024 and 9/25/2024 - 3-4:20 pm
- Labor and education data (Jefferson), 9/23/2024 and 9/25/2024 - 3-4:20 pm
Workshops listed twice have the same content and are done as an opportunity to fit your schedule. While you must attend at least one data workshop, it is wise to attend more than one. If in a certificate program, with the exception of political economy which has to be incorporated into your JIW, other programs have different requirements which are typically for your senior year. As an example, if in finance, if you choose not to explore a finance topic this year you will still need to incorporate in your senior theses so try and attend a finance workshop in addition to your topical workshop for your JIW since these are intended to help you for your time at Princeton and both the JIW but also the senior thesis.
- Last Updated: Aug 28, 2024 9:32 AM
- URL: https://libguides.princeton.edu/ECOJIWTopics
The Causes and Consequences of U.S. Teacher Strikes
The U.S. has witnessed a resurgence of labor activism, with teachers at the forefront. We examine how teacher strikes affect compensation, working conditions, and productivity with an original dataset of 772 teacher strikes generating 48 million student days idle between 2007 and 2023. Using an event study framework, we find that, on average, strikes increase compensation by 8% and lower pupil-teacher ratios by 0.5 students, driven by new state revenues. We find little evidence of sizable impacts on student achievement up to five years post-strike, though strikes lasting 10 or more days decrease math achievement in the short-term.
Correspondence regarding the manuscript can be sent to Melissa Arnold Lyon: Rockefeller College of Public Affairs and Policy, University at Albany, 135 Western Avenue, Albany, NY 12222 ([email protected]). We are very grateful for research assistance from Zoe Beckman, Eunice Chong, Summer Dai, Stephanie Tu, Sarah Newberger, Hyesang Noh, Adam Shephardson, and Natalie Truong. This research also benefited immensely from the helpful feedback of Jesse Bruhn, Jake Rosenfeld, Sarah Anzia, and the seminar participants at Michigan State University, the 2023 APSA Comparative Labor Politics Workshop, and the 2023 APSA and 2022 AEFP Annual Meetings. This research was supported by a NAEd/Spencer Postdoctoral Fellowship awarded to Lyon. This research was completed before Matthew Kraft joined the Council of Economic Advisers as a senior economist in July of 2024. The views expressed herein are those of the authors and do not necessarily reflect the views of the National Bureau of Economic Research.
MARC RIS BibTeΧ
Download Citation Data
More from NBER
In addition to working papers , the NBER disseminates affiliates’ latest findings through a range of free periodicals — the NBER Reporter , the NBER Digest , the Bulletin on Retirement and Disability , the Bulletin on Health , and the Bulletin on Entrepreneurship — as well as online conference reports , video lectures , and interviews .


IMAGES
VIDEO
COMMENTS
60 Victimology Topics & Examples. Updated: Mar 1st, 2024. 3 min. For your paper on crime prevention, penology, or violence in any form, take a look at our victimology research topics. Get a critical title from the collection prepared by our team.
A systematic review conducted in 2012 found that victims of all. crime types express a range of needs - emotiona l or psychological, information, concerning the criminal proceedings, practical ...
Journal of Victimology and Victim Justice, a peer-reviewed journal focuses on both critical leadership and practical development representing victimological perspectives from a broad range of disciplines and contribute to a greater understanding of victims, victimization, victim- offender relations, institutional functioning and allied issues. View full journal description
Victim participation is essential to a functioning system of criminal justice. Whether for domestic or international criminal justice, victims participate by reporting the victimisation to authorities, providing statements, giving information, supplying evidence, appearing for questions, giving witness testimony, responding to cross-examination, making submissions for various purposes, and ...
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on VICTIMOLOGY. Find methods information, sources, references or conduct a literature review on VICTIMOLOGY
Part 1: Research Paper Topics on. Victims of Domestic Violence. Initial research recognized wives as victims of domestic violence. Thereafter, it was acknowledged that unmarried women were also falling victim to violence at the hands of their boyfriends. Subsequently, the term ''battered women'' became synonymous with ''battered ...
The International Review of Victimology is the leading international peer-reviewed journal for victimological research, focusing on traditional areas of research and broader concerns, such as political and human rights issues. It includes the victim-offender relationship, the effects of victimization, victims in the criminal justice system, reparation and restitution by offenders, crime ...
The articles included in this issue reflect three broad areas of cybercrime research: cybercrime victimization, cybercrime perpetration, and techniques and facilitators of cybercrime. While there is some overlap, the issue includes three papers focused on each of these three areas. The first area covered in the special issue focuses on ...
This book explores what victimology, as both an academic discipline and an activist movement, has achieved since its initial conception in the 1940s, from a variety of experts' perspectives. Focussing on nine, dynamic and contemporary case studies covering topics like violence against women and girls, bereaved family activism, and ...
Abstract. Sexual assault (SA) is a common and deleterious form of trauma. Over 40 years of research on its impact has suggested that SA has particularly severe effects on a variety of forms of psychopathology, and has highlighted unique aspects of SA as a form of trauma that contribute to these outcomes. The goal of this meta-analytic review ...
Research Syntheses. CVR's syntheses summarize the state of the field for multiple victimization types. Results are translated into fact sheets, reports, webinars, podcasts, and conference presentations. Because victim research is an emerging field, CVR's researchers gathered evidence from the best available research, practice, and ...
The current bibliometric study assessed the scholarly status on cybercrime victimization during 2010-2020 by retrieving SSCI articles from WoS database. There is no study that applied bibliometric method to research on the examined subject. Hence, this paper firstly contributed statistical evidence and visualized findings to literature of ...
Research focusing on victimization has become a well-established subarea in criminology, and it continues to grow in terms of its breadth and depth of focus. The field of victimology is the scientific study of the harms that people suffer as a result of such activities.
Research-to-practice inspiration in the CVR Library, part 2. In a 2020 survey of Texas victim service providers, respondents said that hearing from others who have partnered with researchers would help with their own efforts to work with a […] The CVR Library contains open access research about victims, victim services, trauma, resilience ...
Christine Bryce. 51175195227243259275 283PrefaceCurrent Issues in Victimology Research focuses on topics of concern for those who study victims of cri. , or what we refer to as victimology. There is a myriad of topics that we could have included in this third edition, and thus it was.
Abstract. Fourteen papers on victim research findings address the immediate and long-term effects of criminal victimization and the response to the victim by various professionals. Under an expanded concept of victimization, a number of papers address research on the victimizing impact of natural and environmental disasters.
Research on cybercrime victimization is relatively diversified; however, no bibliometric study has been found to introduce the panorama of this subject. The current study aims to address this research gap by performing a bibliometric analysis of 387 Social Science Citation Index articles relevant to cybercrime victimization from Web of Science database during the period of 2010-2020. The ...
Until 1970s the victims of crime were not considered as an essential part of the criminal justice system. ... This attitude started to change after the formation of the standalone discipline of victimology and research in the field of victimology. ... Subscribe to this fee journal for more curated articles on this topic FOLLOWERS. 855. PAPERS ...
Stephanie Fohring is a Lecturer in Criminology at Edinburgh Napier University. Her research interests cover victims and victim identity and labelling, crime surveys and the psychological impact of crime, particularly in relation to crime reporting and the criminal justice system.
Victimization can be defined as the act or process of someone being injured or damaged by another person. The resulting damage may be physical (e.g., bruises, broken bones) or psychological (e.g., posttraumatic stress disorder [PTSD], depression). Victimization is a frequent event that occurs within an interpersonal context, often involving an ...
A research, of 187 undergraduate students matriculated at a large U.S. Northeastern metropolitan Roman Catholic university (Webber and Ovedovitz, 2018), found that 4.3% indicated that they were victims of cyberbullying at the university level and a total of 7.5% students acknowledged having participated in bullying at that level while A survey ...
MIT researchers have discovered how fasting impacts the regenerative abilities of intestinal stem cells, reports Ed Cara for Gizmodo.. "The major finding of our current study is that refeeding after fasting is a distinct state from fasting itself," explain Prof. Ömer Yilmaz and postdocs Shinya Imada and Saleh Khawaled.
Australians lost more than $3.1 billion to scams in 2022, a new record and an 80 per cent increase from 2021, according to a new report. After months of regular phone calls from the scammer, a ...
New research suggests that this rejection can be due to people's lack of shared criteria or reference points when evaluating a potential innovation's value. In a new paper, the authors find ...
Confidence in U.S. public opinion polling was shaken by errors in 2016 and 2020. In both years' general elections, many polls underestimated the strength of Republican candidates, including Donald Trump. These errors laid bare some real limitations of polling. In the midterms that followed those ...
Recently, the Society for Research on Adolescence (SRA) recognized Dr. Jessika Bottiani, an associate research professor at the UVA School of Education and Human Development and faculty affiliate at Youth-Nex, and her co-authors with the 2024 Social Policy Publication Award for a paper on the prevention of youth firearm violence disparities ...
The paper is published in the journal Substance Use & Misuse. In Cuyahoga County, the stark reality of the opioid crisis is that most drug overdose victims die alone, with no one nearby to help.
Given the nature of the research, a purposive sampling strategy was adopted. This involved specifically selecting participants based on their relevance to the research topic (Silverman, 2010). The inclusion criteria required participants to perceive themselves to have been in a relationship with a narcissist and also be above 18 years old.
Choosing a topic that can answer an economic research question is challenging. Some tips: Ripped from the headlines rarely makes a good economic paper. You will be using data to determine causation or correlation. Sometimes a similar event can be used. Topics such as artificial intelligence may make a good policy paper but not a good economic ...
The U.S. has witnessed a resurgence of labor activism, with teachers at the forefront. We examine how teacher strikes affect compensation, working conditions, and productivity with an original dataset of 772 teacher strikes generating 48 million student days idle between 2007 and 2023.