- Architecture and Design
- Asian and Pacific Studies
- Business and Economics
- Classical and Ancient Near Eastern Studies
- Computer Sciences
- Cultural Studies
- Engineering
- General Interest
- Geosciences
- Industrial Chemistry
- Islamic and Middle Eastern Studies
- Jewish Studies
- Library and Information Science, Book Studies
- Life Sciences
- Linguistics and Semiotics
- Literary Studies
- Materials Sciences
- Mathematics
- Social Sciences
- Sports and Recreation
- Theology and Religion
- Publish your article
- The role of authors
- Promoting your article
- Abstracting & indexing
- Publishing Ethics
- Why publish with De Gruyter
- How to publish with De Gruyter
- Our book series
- Our subject areas
- Your digital product at De Gruyter
- Contribute to our reference works
- Product information
- Tools & resources
- Product Information
- Promotional Materials
- Orders and Inquiries
- FAQ for Library Suppliers and Book Sellers
- Repository Policy
- Free access policy
- Open Access agreements
- Database portals
- For Authors
- Customer service
- People + Culture
- Journal Management
- How to join us
- Working at De Gruyter
- Mission & Vision
- De Gruyter Foundation
- De Gruyter Ebound
- Our Responsibility
- Partner publishers

Your purchase has been completed. Your documents are now available to view.

Digital image steganography and steganalysis: A journey of the past three decades
Steganography is the science and art of covert communication. Conversely, steganalysis is the study of uncovering the steganographic process. The evolution of steganography has been paralleled by the development of steganalysis. In this game of hide and seek, the two player’s steganography and steganalysis always want to break the other down. Over the past three decades, research has produced a plethora of remarkable image steganography techniques (ISTs). The major challenge for most of these ISTs is to achieve a fair balance between the metrics such as high hiding capacity (HC), better imperceptibility, and improved security. This study aims to present an exhaustive scrutiny of various ISTs from the classical to recent developments in the spatial domain, with respect to various image steganographic metrics. Further, the current status, recent developments, open challenges, and promising directions in this field are also highlighted.
[1] Martin A., Sapiro G., Seroussi G., Is image steganography natural?, IEEE Transactions on Image processing, 2005, 14(12), 2040-2050 10.1109/TIP.2005.859370 Search in Google Scholar
[2] Kadhim I. J., Premaratne P., Vial P. J., Halloran B., Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research, Neurocomputing, 2019, 335, 299-326 10.1016/j.neucom.2018.06.075 Search in Google Scholar
[3] Cheddad A., Condell J., Curran K., Mc-Kevitt P., Digital image steganography: Survey and analysis of current methods, Signal processing, 2010, 90(3), 727-752 10.1016/j.sigpro.2009.08.010 Search in Google Scholar
[4] Johnson N. F., Jajodia S., Exploring steganography: Seeing the unseen, Computer, 1998, 31(2), 26-34 10.1109/MC.1998.4655281 Search in Google Scholar
[5] Hussain M., Wahab A. W. A., Idris Y. I. B., Ho A. T., Jung K. H., Image steganography in spatial domain: A survey, Signal Processing: Image Communication, 2018, 65, 46-66 10.1016/j.image.2018.03.012 Search in Google Scholar
[6] Atawneh S., Almomani A., Sumari P., Steganography in digital images: Common approaches and tools, IETE Technical Review, 2013, 30(4), 344-358 10.4103/0256-4602.116724 Search in Google Scholar
[7] Nisha C. D., Monoth T., Analysis of Spatial Domain Image Steganography Based on Pixel-Value Differencing Method, In Soft Computing for Problem Solving, Springer, Singapore, 2020, 385-397. https://doi.org/10.1007/978-981-15-0184-5_34 10.1007/978-981-15-0184-5_34 Search in Google Scholar
[8] Karampidis K., Kavallieratou E., Papadourakis G., A review of image steganalysis techniques for digital forensics, Journal of information security and applications, 2018, 40, 217-235 10.1016/j.jisa.2018.04.005 Search in Google Scholar
[9] Nissar A. Mir A. H., Classification of steganalysis techniques: A study, Digital Signal Processing, 2010, 20(6), 1758-1770 10.1016/j.dsp.2010.02.003 Search in Google Scholar
[10] Singh L. Singh A. K. Singh P. K., Secure data hiding techniques: a survey, Multimedia Tools and Applications, 2018, 1-21. https://doi.org/10.1007/s11042-018-6407-5s Search in Google Scholar
[11] Subhedar M. S., Mankar V. H., Current status and key issues in image steganography: A survey, Computer science review, 2014, 13, 95-113 10.1016/j.cosrev.2014.09.001 Search in Google Scholar
[12] Hussain M., Wahab A. W. A., Anuar N. B., Salleh R., Noor R. M., Pixel value differencing steganography techniques: Analysis and open challenge, In IEEE International Conference on Consumer Electronics-Taiwan, 2015, 21-22 10.1109/ICCE-TW.2015.7216859 Search in Google Scholar
[13] Sahu A. K., Swain G., A review on LSB substitution and PVD based image steganography techniques, Indonesian Journal of Electrical Engineering and Computer Science, 2016, 2(3), 712-719 10.11591/ijeecs.v2.i3.pp712-719 Search in Google Scholar
[14] Kharrazi M., Sencar H. T., Memon N. D., Performance study of common image steganography and steganalysis techniques, Journal of Electronic Imaging, 2006, 15(4), 041104 10.1117/1.2400672 Search in Google Scholar
[15] Li B., He, J., Huang J., Shi Y. Q., A survey on image steganography and steganalysis, Journal of Information Hiding and Multimedia Signal Processing, 2011, 2(2), 142-172 Search in Google Scholar
[16] Judge J. C., Steganography: past, present, future (No. UCRL-ID-151879), Lawrence Livermore National Lab., CA (US), 2001 10.2172/15006450 Search in Google Scholar
[17] Amirtharajan R., Qin J., Rayappan J. B. B., Random image steganography and steganalysis: Present status and future directions, Information Technology Journal, 2012, 11, 566-576 10.3923/itj.2012.566.576 Search in Google Scholar
[18] Kahn D., The history of steganography, In International Workshop on Information Hiding, Springer, Berlin, Heidelberg, 1996, 1-5 10.1007/3-540-61996-8_27 Search in Google Scholar
[19] Mishra M., Mishra P., Adhikary M. C., Digital image data hiding techniques: A comparative study, arXiv preprint arXiv:1408.3564, 2014 Search in Google Scholar
[20] Provos N., Honeyman P., Hide and seek: An introduction to steganography, IEEE security & privacy, 2003, 1(3), 32-44 10.1109/MSECP.2003.1203220 Search in Google Scholar
[21] Petitcolas F. A., Anderson R. J., Kuhn M. G., Information hiding-a survey, Proceedings of the IEEE, 1999, 87(7), 1062-1078 10.1109/5.771065 Search in Google Scholar
[22] Vinodhini R. E., Malathi P., Kumar T. G., A survey on DNA and image steganography, In 4th International Conference on Advanced Computing and Communication Systems (ICACCS), 2017, 1-7 10.1109/ICACCS.2017.8014670 Search in Google Scholar
[23] Wang H., Wang S., Cyber warfare: steganography vs. steganalysis, Communications of the ACM, 2004, 47(10), 76-82 10.1145/1022594.1022597 Search in Google Scholar
[24] Altaay A. A. J., Sahib S. B., Zamani M., An introduction to image steganography techniques, In International Conference on Advanced Computer Science Applications and Technologies (ACSAT), 2012, 122-126 10.1109/ACSAT.2012.25 Search in Google Scholar
[25] Abraham A., Paprzycki M., Significance of steganography on data security, In International Conference on Information Technology: Coding and Computing, 2004. Proceedings, ITCC 2004, 2004(2), 347-351 Search in Google Scholar
[26] Amirtharajan R., Rayappan J. B. B., Steganography-time to time: A review, Research Journal of Information Technology, 2013, 5(2), 53-66 10.3923/rjit.2013.53.66 Search in Google Scholar
[27] Pradhan A., Sahu A. K., Swain G., Sekhar K. R., Performance evaluation parameters of image steganography techniques, In International Conference on Research Advances in Integrated Navigation Systems (RAINS), 2016, 1-8 10.1109/RAINS.2016.7764399 Search in Google Scholar
[28] Meng R., Cui Q., Yuan C., A survey of image information hiding algorithms based on deep learning, Computer Modeling in Engineering & Sciences, 2018, 117(3), 425-454 10.31614/cmes.2018.04765 Search in Google Scholar
[29] Girdhar A., Kumar V., Comprehensive survey of 3D image steganography techniques, IET Image Processing, 2017, 12(1), 1-10 10.1049/iet-ipr.2017.0162 Search in Google Scholar
[30] Artz D., Digital steganography: hiding data within data, IEEE Internet computing, 2001, 5(3), 75-80 10.1109/4236.935180 Search in Google Scholar
[31] Trivedi M. C., Sharma S., Yadav V. K., Analysis of several image steganography techniques in spatial domain: A survey, In Proceedings of the Second International Conference on Information and Communication Technology for Competitive Strategies, 2016, 84 10.1145/2905055.2905294 Search in Google Scholar
[32] Jung K. H., A survey of reversible data hiding methods in dual images, IETE Technical Review, 2016, 33(4), 441-452 10.1080/02564602.2015.1102099 Search in Google Scholar
[33] Shi Y. Q., Li X., Zhang X., Wu H. T., Ma, B., Reversible data hiding: advances in the past two decades, IEEE Access, 2016, 4, 3210-3237 10.1109/ACCESS.2016.2573308 Search in Google Scholar
[34] Westfeld A., Pfitzmann A., Attacks on steganographic systems, In International workshop on information hiding, Springer, Berlin, Heidelberg, 1999, 61-76 10.1007/10719724_5 Search in Google Scholar
[35] Mousavi S.M., Naghsh A., Manaf A. A., Abu-Bakar S. A. R., A robust medical image watermarking against salt and pepper noise for brain MRI images, Multimedia Tools and Applications, 2017, 76(7), 10313–10342 10.1007/s11042-016-3622-9 Search in Google Scholar
[36] Wang Z., Bovik A. C., A universal image quality index, IEEE signal processing letters, 2002, 9(3), 81-84 10.1109/97.995823 Search in Google Scholar
[37] Bagnall R. J., Reversing the steganography myth in terrorist operations: The asymmetrical threat of simple intelligence dissemination techniques using common tools, SANS Information Security Reading Room, 2002, 19 Search in Google Scholar
[38] Tirkel A. Z., Rankin G. A., Van-Schyndel R. M., Ho W. J., Mee N. R. A., Osborne, C. F., Electronic watermark, Digital Image Computing, Technology and Applications (DICTA’93), 1993, 666-673 Search in Google Scholar
[39] Simmons G. J., The prisoners’ problem and the subliminal channel, In Advances in Cryptology, Springer, Boston, MA, 1984, 51-67 10.1007/978-1-4684-4730-9_5 Search in Google Scholar
[40] Fridrich J., Goljan M., Practical steganalysis of digital images: State of the art, Security and Watermarking of Multimedia Contents IV, International Society for Optics and Photonics, 2002, 4675, 1–14 10.1117/12.465263 Search in Google Scholar
[41] Zhang T., Ping X., A new approach to reliable detection of LSB steganography in natural images, Signal processing, 2003, 83(10), 2085-2093 10.1016/S0165-1684(03)00169-5 Search in Google Scholar
[42] Xia Z., Wang X., Sun X., Liu Q., Xiong N., Steganalysis of LSB matching using differences between nonadjacent pixels, Multimedia Tools and Applications, 2016, 75(4), 1947-1962 10.1007/s11042-014-2381-8 Search in Google Scholar
[43] Zhang J., Xiong F., Zhang D., Steganalysis for LSB Matching Based on the Dependences Between Neighboring Pixels, Journal of multimedia, 2012, 7(5), https://doi.org/10.1002/sec.864 10.1002/sec.864 Search in Google Scholar
[44] Fridrich J., Goljan M., Du R., Reliable detection of LSB steganography in color and grayscale images, In Proceedings of the work-shop on Multimedia and security: new challenges, 2001, 27-30 10.1145/1232454.1232466 Search in Google Scholar
[45] Ker A. D., Steganalysis of LSB matching in grayscale images, IEEE signal processing letters, 2005, 12(6), 441-444 10.1109/LSP.2005.847889 Search in Google Scholar
[46] Fridrich J., Goljan M., Du R., Detecting LSB steganography in color, and gray-scale images, IEEE multimedia, 2001, 8(4), 22-28 10.1109/93.959097 Search in Google Scholar
[47] Ker A. D., Improved detection of LSB steganography in grayscale images, In International workshop on information hiding, Springer, Berlin, Heidelberg, 2004, 97-115 10.1007/978-3-540-30114-1_8 Search in Google Scholar
[48] Pevný T., Filler T., Bas P., Using high-dimensional image models to perform highly undetectable steganography, In International Workshop on Information Hiding, Springer, Berlin, Heidelberg, 2010, 161-177 10.1007/978-3-642-16435-4_13 Search in Google Scholar
[49] Pevny T., Bas P., Fridrich J., Steganalysis by subtractive pixel adjacency matrix, IEEE Transactions on information Forensics and Security, 2010, 5(2), 215-224 10.1109/TIFS.2010.2045842 Search in Google Scholar
[50] Zhang H., Ping X., Xu M., Wang R., Steganalysis by subtractive pixel adjacency matrix and dimensionality reduction, Science China Information Sciences, 2014, 57(4), 1-7 10.1007/s11432-013-4793-x Search in Google Scholar
[51] Kurak C., Mc-Hugh J., A cautionary note on image downgrading, Proceedings Eighth Annual Computer Security Application Conference, 1992, 153-159 Search in Google Scholar
[52] Wang R. Z., Lin C. F., Lin J. C., Hiding data in images by optimal moderately-significant-bit replacement, Electronics Letters, 2000, 36(25), 2069-2070 10.1049/el:20001429 Search in Google Scholar
[53] Chan C. K., Cheng L. M., Improved hiding data in images by optimal moderately-significant-bit replacement, Electronics Letters, 2001, 37(16), 1017-1018 10.1049/el:20010714 Search in Google Scholar
[54] Wang R. Z., Lin C. F., Lin J. C., Image hiding by optimal LSB substitution and genetic algorithm, Pattern recognition, 2001, 34(3), 671-683 10.1016/S0031-3203(00)00015-7 Search in Google Scholar
[55] Chan C. K., Cheng L. M., Hiding data in images by simple LSB substitution, Pattern recognition, 2004, 37(3), 469-474 10.1016/j.patcog.2003.08.007 Search in Google Scholar
[56] Chang C. C., Lin M. H., Hu Y. C., A fast and secure image hiding scheme based on LSB substitution, International journal of pattern recognition and artificial intelligence, 2002, 16(04), 399-416 10.1142/S0218001402001770 Search in Google Scholar
[57] Zakaria A., Hussain M., Wahab A., Idris M., Abdullah N., Jung K. H., High-capacity image steganography with minimum modified bits based on data mapping and LSB substitution, Applied Sciences, 2018, 8(11), 2199 10.3390/app8112199 Search in Google Scholar
[58] Yang H., Sun X., Sun G., A high-capacity image data hiding scheme using adaptive LSB substitution, Radioengineering, 2009, 18(4), 509-516 Search in Google Scholar
[59] Cheng-Hsing Y., Chi-Yao W., Shiuh-Jeng W., Hung-Min S., Adaptive data hiding in edge areas of images with spatial LSB domain systems, IEEE Transactions on Information Forensics and Security, 2008, 3(3), 488-497 10.1109/TIFS.2008.926097 Search in Google Scholar
[60] Gupta S., Goyal A., Bhushan B., Information hiding using least significant bit steganography and cryptography, International Journal of Modern Education and Computer Science, 2012, 4(6), 27-34 10.5815/ijmecs.2012.06.04 Search in Google Scholar
[61] Khan S., Ahmad N., Wahid M., Varying index varying bits substitution algorithm for the implementation of VLSB steganography, Journal of the Chinese Institute of Engineers, 2016, 39(1), 101-109 10.1080/02533839.2015.1082933 Search in Google Scholar
[62] Wu N. I., Hwang M. S., A novel LSB data hiding scheme with the lowest distortion, The Imaging Science Journal, 2017, 65(6), 371-378 10.1080/13682199.2017.1355089 Search in Google Scholar
[63] Sahu A. K., Swain G., A novel n-rightmost bit replacement image steganography technique, 3D Research, 2019, 10(1), 2 10.1007/s13319-018-0211-x Search in Google Scholar
[64] Hussain M., Abdul W. A., Javed N., Jung K. H., Hybrid data hiding scheme using right-most digit replacement and adaptive least significant bit for digital images, Symmetry, 2016, 8(6), 41 10.3390/sym8060041 Search in Google Scholar
[65] Sahu A. K., Swain G., A novel multi stego-image based data hiding method for gray scale image, Pertanika Journal of Science and Technology, 2019, 29(2), 753-768. Search in Google Scholar
[66] Sahu A. K., Swain G., Babu E. S., Digital image steganography using bit flipping, Cybernetics and Information Technologies, 2018, 18(1), 69-80 10.2478/cait-2018-0006 Search in Google Scholar
[67] Shreelekshmi R., Wilscy M., Madhavan C. V., Undetectable least significant bit replacement steganography, Multimedia Tools and Applications, 2019, 78(8), 10565-10582 10.1007/s11042-018-6541-0 Search in Google Scholar
[68] Kim C., Shin D., Kim B. G., Yang C. N., Secure medical images based on data hiding using a hybrid scheme with the Hamming code, LSB, and OPAP, Journal of Real-Time Image Processing, 2018, 14(1), 115-126 10.1007/s11554-017-0674-7 Search in Google Scholar
[69] Zhou R. G., Luo J., Liu X., Zhu C., Wei L., Zhang X., A novel quantum image steganography scheme based on LSB, International Journal of Theoretical Physics, 2018, 57(6), 1848-1863 10.1007/s10773-018-3710-x Search in Google Scholar
[70] Sahu A. K., Swain G., Information hiding using group of bits substitution, International Journal on Communications Antenna and Propagation, 2017, 7(2), 162-167 10.15866/irecap.v7i2.11675 Search in Google Scholar
[71] Swain G., Digital image steganography using variable length group of bits substitution, Procedia Computer Science, 2016, 85, 31-38 10.1016/j.procs.2016.05.173 Search in Google Scholar
[72] Jung K. H., Data hiding of digital images based on bit position and parity bit, The Imaging Science Journal, 2012, 60(6), 329-337 10.1179/174313112X13522089179550 Search in Google Scholar
[73] Laskar S. A., Hemachandran K., High Capacity data hiding using LSB Steganography and Encryption, International Journal of Database Management Systems, 2012, 4(6), 57 10.5121/ijdms.2012.4605 Search in Google Scholar
[74] Elmasry W., New LSB-based colour image steganography method to enhance the eflciency in payload capacity, security and integrity check, Sadhana, 2018, 43(5), 68 10.1007/s12046-018-0848-4 Search in Google Scholar
[75] Chakraborty S., Jalal A. S., Bhatnagar C., LSB based non blind predictive edge adaptive image steganography, Multimedia Tools and Applications, 2017, 76(6), 7973-7987 10.1007/s11042-016-3449-4 Search in Google Scholar
[76] Sharp T., An implementation of key-based digital signal steganography, In International Workshop on Information Hiding, Springer, Berlin, Heidelberg, 2001, 13-26 10.1007/3-540-45496-9_2 Search in Google Scholar
[77] Mielikainen J., LSB matching revisited, IEEE signal processing letters, 2006, 13(5), 285-287 10.1109/LSP.2006.870357 Search in Google Scholar
[78] Sahu A. K., Swain G., An improved data hiding technique using bit differencing and LSB matching, Internetworking Indonesia Journal, 2018, 10(1), 17-21 Search in Google Scholar
[79] Sabeti V., Samavi S., Shirani S., An adaptive LSB matching steganography based on octonary complexity measure, Multimedia tools and applications, 2013, 64(3), 777-793 10.1007/s11042-011-0975-y Search in Google Scholar
[80] Juneja M., Sandhu P. S., Designing of robust image steganography technique based on LSB insertion and encryption, In International Conference on Advances in Recent Technologies in Communication and Computing, 2009, 302-305 10.1109/ARTCom.2009.228 Search in Google Scholar
[81] Swain G., Lenka S. K., A novel steganography technique by mapping words with LSB array, International Journal of Signal and Imaging Systems Engineering, 2015, 8(1-2), 115-122 10.1504/IJSISE.2015.067052 Search in Google Scholar
[82] Swain G., Lenka, S. K., LSB array based image steganography technique by exploring the four least significant bits, In International Conference on Computing and Communication Systems, Springer, Berlin, Heidelberg, 2011, 479-488 10.1007/978-3-642-29216-3_52 Search in Google Scholar
[83] Alshayeji M. H., Al-Roomi S. A., Abed S. E., A high-capacity and secure least significant bit embedding approach based on word and letter frequencies, Security and Communication Networks, 2016, 9(18), 5764-5788 10.1002/sec.1735 Search in Google Scholar
[84] Jung K. H., Yoo K. Y., Steganographic method based on interpolation and LSB substitution of digital images, Multimedia Tools and Applications, 2015, 74(6), 2143-2155 10.1007/s11042-013-1832-y Search in Google Scholar
[85] Lee Y. K., Chen L. H., High capacity image steganographic model, IEE Proceedings-Vision, Image and Signal Processing, 2000, 147(3), 288-294 10.1049/ip-vis:20000341 Search in Google Scholar
[86] Rengarajan A., K., Infant A. K., Rayappan J. B. B., High performance pixel indicator for colour image steganography, Information Technology, 2013, 5(3), 277-290 10.3923/rjit.2013.277.290 Search in Google Scholar
[87] Laimeche L., Meraoumia A., Bendjenna H., Enhancing LSB embedding schemes using chaotic maps systems, Neural Computing and Applications, 2019, 1-19. https://doi.org/10.1007/s00521-019-04523-z (in press) 10.1007/s00521-019-04523-z Search in Google Scholar
[88] Tavares J. R. C., Junior F. M. B., Word-Hunt: A LSB steganography method with low expected number of modifications per pixel, IEEE Latin America Transactions, 2016, 14(2), 1058-1064 10.1109/TLA.2016.7437258 Search in Google Scholar
[89] Sarreshtedari S., Akhaee M. A., One-third probability embedding: a new±1 histogram compensating image least significant bit steganography scheme, IET image processing, 2013, 8(2), 78-89 10.1049/iet-ipr.2013.0109 Search in Google Scholar
[90] Muhammad K., Ahmad J., Rehman N. U., Jan Z., Sajjad M., CISSKALSB: color image steganography using stego key-directed adaptive LSB substitution method, Multimedia Tools and Applications, 2017, 76(6), 8597-8626 10.1007/s11042-016-3383-5 Search in Google Scholar
[91] Wang Z. H., Chang C. C., Li M. C., Optimizing least-significant-bit substitution using cat swarm optimization strategy, Information Sciences, 2012, 192, 98-108. 10.1016/j.ins.2010.07.011 Search in Google Scholar
[92] Qazanfari K., Safabakhsh R., A new steganography method which preserves histogram: Generalization of LSB++, Information Sciences, 2014, 277, 90-101 10.1016/j.ins.2014.02.007 Search in Google Scholar
[93] Parvez M. T., Gutub A. A. A., RGB intensity based variable-bits image steganography, In IEEE Asia-Pacific Services Computing Conference, 2008, 1322-1327 10.1109/APSCC.2008.105 Search in Google Scholar
[94] Wu D. C., Tsai W. H., A steganographic method for images by pixel-value differencing. Pattern Recognition Letters, 2003, 24(9-10), 1613-1626 10.1016/S0167-8655(02)00402-6 Search in Google Scholar
[95] Yang C. H., Weng C. Y., Tso H. K., Wang S. J., A data hiding scheme using the varieties of pixel-value differencing in multimedia images, Journal of Systems and Software, 2011, 84(4), 669-678 10.1016/j.jss.2010.11.889 Search in Google Scholar
[96] Chang K. C., Chang C. P., Huang P. S., Tu T. M., A Novel Image Steganographic Method Using Tri-way Pixel-Value Differencing, Journal of multimedia, 2008, 3(2), 37-44 10.4304/jmm.3.2.37-44 Search in Google Scholar
[97] Hussain M., Wahab A. W. A., Ho A. T., Javed N., Jung K. H., A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement, Signal Processing: Image Communication, 2017, 50, 44-57 10.1016/j.image.2016.10.005 Search in Google Scholar
[98] Tseng H. W., Leng H. S., A steganographic method based on pixel-value differencing and the perfect square number, Journal of Applied Mathematics, 2013, Article ID 189706, 1-8, http://doi.org/10.1155/2013/189706 10.1155/2013/189706 Search in Google Scholar
[99] Swain G., Adaptive pixel value differencing steganography using both vertical and horizontal edges, Multimedia Tools and Applications, 2016, 75(21), 13541-13556 10.1007/s11042-015-2937-2 Search in Google Scholar
[100] Hong W., Chen T. S., Luo C. W., Data embedding using pixel value differencing and diamond encoding with multiple-base notational system, Journal of Systems and Software, 2012, 85(5), 1166-1175 10.1016/j.jss.2011.12.045 Search in Google Scholar
[101] Lee Y. P., Lee J. C., Chen W. K., Chang K. C., Su J., Chang C. P., High-payload image hiding with quality recovery using tri-way pixel-value differencing, Information Sciences, 2012, 191, 214-225 10.1016/j.ins.2012.01.002 Search in Google Scholar
[102] Chang C. C., Chuang J. C., Hu, Y. C., Spatial domain image hiding scheme using pixel-values differencing, Fundamenta Informaticae, 2006, 70(3), 171-184 Search in Google Scholar
[103] Luo W., Huang F., Huang J., A more secure steganography based on adaptive pixel-value differencing scheme, Multimedia tools and applications, 2011, 52(2-3), 407-430 10.1007/s11042-009-0440-3 Search in Google Scholar
[104] Balasubramanian C., Selvakumar S., Geetha S., High payload image steganography with reduced distortion using octonary pixel pairing scheme, Multimedia tools and applications, 2014, 73(3), 2223-2245 10.1007/s11042-013-1640-4 Search in Google Scholar
[105] Swain G., Adaptive and non-adaptive PVD steganography using overlapped pixel blocks, Arabian Journal for Science and Engineering, 2018, 43(12), 7549-7562 10.1007/s13369-018-3163-9 Search in Google Scholar
[106] Hameed M. A., Aly S., Hassaballah M., An eflcient data hiding method based on adaptive directional pixel value differencing (ADPVD), Multimedia Tools and Applications, 2018, 77(12), 14705-14723 10.1007/s11042-017-5056-4 Search in Google Scholar
[107] Grajeda-Marin I. R., Montes-Venegas H. A., Marcial-Romero J. R., Hernandez-Servin J. A., De-Ita G., An optimization approach to the TWPVD method for digital image steganography, In Mexican Conference on Pattern Recognition, Springer, Cham, 2016, 125-134 10.1007/978-3-319-39393-3_13 Search in Google Scholar
[108] Hosam O., Ben Halima N., Adaptive block-based pixel value differencing steganography, Security and Communication Networks, 2016, 9(18), 5036-5050 10.1002/sec.1676 Search in Google Scholar
[109] Prasad S., Pal A. K., An RGB colour image steganography scheme using overlapping block-based pixel-value differencing, Royal Society Open Science, 2017, 4(4), 161066 10.1098/rsos.161066 Search in Google Scholar
[110] Jung K. H., Yoo K. Y., High-capacity index based data hiding method, Multimedia Tools and Applications, 2015, 74(6), 2179-2193. 10.1007/s11042-014-2081-4 Search in Google Scholar
[111] Lu H. C., Chu Y. P., Hwang M. S., New steganographic method of pixel value differencing. Journal of Imaging Science and Technology, 2006, 50(5), 424-426 10.2352/J.ImagingSci.Technol.(2006)50:5(424) Search in Google Scholar
[112] Liu H. H., Lin Y. C., Lee C. M., A digital data hiding scheme based on pixel-value differencing and side match method, Multimedia Tools and Applications, 2019, 78(9), 12157-12181 10.1007/s11042-018-6766-y Search in Google Scholar
[113] Grajeda-Marín I. R., Montes-Venegas H. A., Marcial-Romero J. R., Hernández-Servín J. A., Muñoz-Jiménez V., Luna G. D. I., A New Optimization Strategy for Solving the Fall-Off Boundary Value Problem in Pixel-Value Differencing Steganography, International Journal of Pattern Recognition and Artificial Intelligence, 2018, 32(01), 1860010 10.1142/S0218001418600108 Search in Google Scholar
[114] Mandal J., Das D., Steganography using adaptive pixel value differencing (APVD) of gray images through exclusion of overflow/underflow, In Second international conference on computer science, engineering and applications (CCSEA), 2012, 93–102 10.5121/csit.2012.2211 Search in Google Scholar
[115] Kim P. H., Yoon E. J., Ryu K. W., Jung K. H., Data-Hiding Scheme Using Multidirectional Pixel-Value Differencing on Colour Images, Security and Communication Networks, 2019, https://doi.org/10.1155/2019/9038650 (in press) 10.1155/2019/9038650 Search in Google Scholar
[116] Zhang X., Wang S., Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security, Pattern Recognition Letters, 2004, 25(3), 331-339 10.1016/j.patrec.2003.10.014 Search in Google Scholar
[117] Wu H. C., Wu N. I., Tsai C. S., Hwang M. S., Image steganographic scheme based on pixel-value differencing and LSB replacement methods, IEE Proceedings-Vision, Image and Signal Processing, 2005, 152(5), 611-615 10.1049/ip-vis:20059022 Search in Google Scholar
[118] Yang C. H., Weng C. Y., Wang S. J., Sun H. M., Varied PVD+ LSB evading detection programs to spatial domain in data embedding systems, Journal of Systems and Software, 2010, 83(10), 1635-1643 10.1016/j.jss.2010.03.081 Search in Google Scholar
[119] Gulve A. K., Joshi M. S., A high capacity secured image steganography method with five pixel pair differencing and LSB substitution, International Journal of Image, Graphics and Signal Processing, 2015, 7(5), 66-74 10.5815/ijigsp.2015.05.08 Search in Google Scholar
[120] Swain G., Digital image steganography using nine-pixel differ-encing and modified LSB substitution, Indian Journal of Science and Technology, 2014, 7(9), 1444-1450 10.17485/ijst/2014/v7i9.27 Search in Google Scholar
[121] Darabkh K. A., Al-Dhamari A. K., Jafar I. F., A new steganographic algorithm based on multi directional PVD and modified LSB, Information Technology and Control, 2017, 46(1), 16-36 10.5755/j01.itc.46.1.15253 Search in Google Scholar
[122] Khodaei M., Faez K., New adaptive steganographic method using least-significant-bit substitution and pixel-value differencing., IET Image processing, 2012, 6(6), 677-686 10.1049/iet-ipr.2011.0059 Search in Google Scholar
[123] Hussain M., Wahab A. W. A., Javed N., Jung K. H., Recursive information hiding scheme through LSB, PVD shift, and MPE, IETE Technical Review, 2018, 35(1), 53-63 10.1080/02564602.2016.1244496 Search in Google Scholar
[124] Shukla A. K., Singh A., Singh B., Kumar A., A secure and high-capacity data-hiding method using compression, encryption and optimized pixel value differencing, IEEE Access, 2018, 6, 51130-51139 10.1109/ACCESS.2018.2868192 Search in Google Scholar
[125] Jung K. H., Data hiding scheme improving embedding capacity using mixed PVD and LSB on bit plane, Journal of Real-Time Image Processing, 2018, 14(1), 127-136 10.1007/s11554-017-0719-y Search in Google Scholar
[126] Khodaei M., Sadeghi B. B., Faez K., Adaptive data hiding, using pixel-value-differencing and LSB substitution, Cybernetics and Systems, 2016, 47(8), 617-628 10.1080/01969722.2016.1214459 Search in Google Scholar
[127] Liao X., Wen Q. Y., Zhang J., A steganographic method for digital images with four-pixel differencing and modified LSB substitution, Journal of Visual Communication and Image Representation, 2011, 22(1), 1-8 10.1016/j.jvcir.2010.08.007 Search in Google Scholar
[128] Yang C. H., Weng C. Y., Wang S. J., Sun H. M., Adaptive data hiding in edge areas of images with spatial LSB domain systems, IEEE Transactions on Information Forensics and Security, 2008, 3(3), 488-497 10.1109/TIFS.2008.926097 Search in Google Scholar
[129] Kalita M., Tuithung T., Majumder S., An adaptive color image steganography method using adjacent pixel value differencing and LSB substitution technique, Cryptologia, 2019, 1-24, https://doi.org/10.1080/01611194.2019.1579122 (in press) 10.1080/01611194.2019.1579122 Search in Google Scholar
[130] Jung K. H., Ha K. J., Yoo K. Y., Image data hiding method based on multi-pixel differencing and LSB substitution methods, In International Conference on Convergence and Hybrid Information Technology, 2008, 355-358 10.1109/ICHIT.2008.279 Search in Google Scholar
[131] Gulve A. K., Joshi M. S., An Image Steganography Method Resistive to fall off Boundary Value Problem with Five Pixel Pair Differ-encing, Journal of Mathematics and Computer Science, 2015, 5, 240-251 10.22436/jmcs.015.03.08 Search in Google Scholar
[132] Sahu A. K., Swain G., Data hiding using adaptive LSB and PVD technique resisting PDH and RS analysis, International Journal of Electronic Security and Digital Forensics, 2019, 11(4), 458-476 10.1504/IJESDF.2019.102567 Search in Google Scholar
[133] Halder T., Karforma S., Mandal R., A Block-Based Adaptive Data Hiding Approach Using Pixel Value Difference and LSB Substitution to Secure E-Governance Documents, Journal of Information Processing Systems, 2019, 15(2), 1-8 Search in Google Scholar
[134] Wang C. M., Wu N. I., Tsai C. S., Hwang M. S., A high quality steganographic method with pixel-value differencing and modulus function, Journal of Systems and Software, 2008, 81(1), 150-158 10.1016/j.jss.2007.01.049 Search in Google Scholar
[135] Joo J. C., Lee H. Y., Lee H. K., Improved steganographic method preserving pixel-value differencing histogram with modulus function, EURASIP Journal on Advances in Signal Processing, 2010, 2010(1), 249826 10.1155/2010/249826 Search in Google Scholar
[136] Xu W. L., Chang C. C., Chen T. S., Wang L. M., An improved least-significant-bit substitution method using the modulo three strategy, Displays, 2016, 42, 36-42 10.1016/j.displa.2016.03.002 Search in Google Scholar
[137] Li Z., He Y., Steganography with pixel-value differencing and modulus function based on PSO, Journal of information security and applications, 2018, 43, 47-52 10.1016/j.jisa.2018.10.006 Search in Google Scholar
[138] Swain G., A data hiding technique by mixing MFPVD and LSB substitution in a pixel, Information Technology and Control, 2018, 47(4), 714-727 10.5755/j01.itc.47.4.19593 Search in Google Scholar
[139] Swain G., Two new steganography techniques based on quotient value differencing with addition-subtraction logic and PVD with modulus function, Optik, 2019, 180, 807-823 10.1016/j.ijleo.2018.11.015 Search in Google Scholar
[140] Swain G., Very high capacity image steganography technique using quotient value differencing and LSB substitution, Arabian Journal for Science and Engineering, 2019, 44(4), 2995-3004 10.1007/s13369-018-3372-2 Search in Google Scholar
[141] Liao X., Wen Q., Zhang J., Improving the adaptive stegano-graphic methods based on modulus function, IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2013, 96(12), 2731-2734 10.1587/transfun.E96.A.2731 Search in Google Scholar
[142] Al-Dhamari A. K., Darabkh K. A., Block-based steganographic algorithm using modulus function and pixel-value differencing, Journal of Software Engineering and Applications, 2017, 10(1), 1-12. 10.4236/jsea.2017.101004 Search in Google Scholar
[143] Sairam T. D., Boopathybagan K., An improved high capacity data hiding scheme using pixel value adjustment and modulus operation, Multimedia Tools and Applications, 2019, 1-11, https://doi.org/10.1007/s11042-019-7557-9 (in press) 10.1007/s11042-019-7557-9 Search in Google Scholar
[144] Shen S., Huang L., Tian Q., A novel data hiding for color images based on pixel value difference and modulus function, Multimedia Tools and Applications, 2015, 74(3), 707-728 10.1007/s11042-014-2016-0 Search in Google Scholar
[145] Lee C. F., Chen H. L., A novel data hiding scheme based on modulus function, Journal of Systems and Software, 2010, 83(5), 832-843 10.1016/j.jss.2009.12.018 Search in Google Scholar
[146] Maleki N., Jalali M., Jahan M. V., Adaptive and non-adaptive data hiding methods for grayscale images based on modulus function, Egyptian Informatics Journal, 2014, 15(2), 115-127 10.1016/j.eij.2014.06.001 Search in Google Scholar
[147] Zhao W., Jie Z., Xin L., Qiaoyan W., Data embedding based on pixel value differencing and modulus function using indeterminate equation, The Journal of China Universities of Posts and Telecommunications, 2015, 22(1), 95-100 10.1016/S1005-8885(15)60631-8 Search in Google Scholar
[148] Nagaraj V., Vijayalakshmi V., Zayaraz G., Color image steganography based on pixel value modification method using modulus function, IERI Procedia, 2013, 4, 17-24 10.1016/j.ieri.2013.11.004 Search in Google Scholar
[149] Sahu A. K., Swain G., An Optimal Information Hiding Approach Based on Pixel Value Differencing and Modulus Function, Wireless Personal Communications, 2019, 108(1). 159-174 10.1007/s11277-019-06393-z Search in Google Scholar
[150] Sahu A. K., Swain G., Pixel overlapping image steganography using PVD and modulus function, 3D Research, 2018, 9(3), 40 10.1007/s13319-018-0188-5 Search in Google Scholar
[151] Sahu A. K., Swain G., Digital Image Steganography using PVD and Modulo Operation, Internetworking Indonesian Journal, 2019, 10(2), 3-13 Search in Google Scholar
[152] Maniriho P., Ahmad T., Information hiding scheme for digital images using difference expansion and modulus function, Journal of King Saud University-Computer and Information Sciences, 2019, 31(3), 335-347 10.1016/j.jksuci.2018.01.011 Search in Google Scholar
[153] Kuo W. C., Secure Modulus Data Hiding Scheme, KSII Transactions on Internet & Information Systems, 2013, 7(3), 600-612 10.3837/tiis.2013.03.011 Search in Google Scholar
[154] Pan F., Li J., Yang X., Image steganography method based on PVD and modulus function, In International Conference on Electronics, Communications and Control (ICECC), 2011, 282-284 10.1109/ICECC.2011.6067590 Search in Google Scholar
[155] Liao X., Wen Q. Y., Zhao Z. L., Zhang J., A novel steganographic method with four-pixel differencing and modulus function, Fundamenta Informaticae, 2012, 118(3), 281-289 10.3233/FI-2012-714 Search in Google Scholar
[156] Liao X., Wen Q., Zhang J., Improving the adaptive stegano-graphic methods based on modulus function, IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2013, 96(12), 2731-2734 10.1587/transfun.E96.A.2731 Search in Google Scholar
[157] Sun S., A novel edge based image steganography with 2k correction and Huffman encoding, Information Processing Letters, 2016, 116(2), 93-99 10.1016/j.ipl.2015.09.016 Search in Google Scholar
[158] Ioannidou A., Halkidis S. T., Stephanides G., A novel technique for image steganography based on a high payload method and edge detection, Expert systems with applications, 2012, 39(14), 11517-11524 10.1016/j.eswa.2012.02.106 Search in Google Scholar
[159] Karakis R., Guler İ., Capraz I., Bilir E., A novel fuzzy logic-based image steganography method to ensure medical data security, Computers in biology and medicine, 2015, 67, 172-183 10.1016/j.compbiomed.2015.10.011 Search in Google Scholar PubMed
[160] Dadgostar H., Afsari F., Image steganography based on interval-valued intuitionistic fuzzy edge detection and modified LSB, Journal of information security and applications, 2016, 30, 94-104 10.1016/j.jisa.2016.07.001 Search in Google Scholar
[161] Li L., Luo B., Li Q., Fang X., A color Images steganography method by multiple embedding strategy based on Sobel operator, In IEEE International Conference on Multimedia Information Networking and Security, 2009, 2, 118-121 10.1109/MINES.2009.187 Search in Google Scholar
[162] Kumar S., Singh A., Kumar M. Information hiding with adaptive steganography based on novel fuzzy edge identification. Defence Technology, 2019, 15(2), 162-169 10.1016/j.dt.2018.08.003 Search in Google Scholar
[163] Lee C. F., Chang C. C., Xie X., Mao K., Shi R. H., An adaptive high-fidelity steganographic scheme using edge detection and hybrid hamming codes, Displays, 2018, 53, 30-39 10.1016/j.displa.2018.06.001 Search in Google Scholar
[164] Bai J., Chang, C. C., Nguyen T. S., Zhu C., Liu Y., A high pay-load steganographic algorithm based on edge detection, Displays, 2017, 46, 42-51 10.1016/j.displa.2016.12.004 Search in Google Scholar
[165] Tseng H. W., Leng H. S., High-payload block-based data hiding scheme using hybrid edge detector with minimal distortion, IET Image Processing, 2014, 8(11), 647-654 10.1049/iet-ipr.2013.0584 Search in Google Scholar
[166] Roy R., Sarkar A., Changder S., Chaos based edge adaptive image steganography, Procedia Technology, 2013, 10, 138-146 10.1016/j.protcy.2013.12.346 Search in Google Scholar
[167] Modi M. R., Islam S., Gupta P., Edge based steganography on colored images, In International Conference on Intelligent Computing, Springer, Berlin, Heidelberg, 2013, 593-600 10.1007/978-3-642-39479-9_69 Search in Google Scholar
[168] Luo W., Huang F., Huang J., Edge adaptive image steganography based on LSB matching revisited, IEEE Transactions on Information Forensics and Security, 2010, 5(2), 201-214 10.1109/TIFS.2010.2041812 Search in Google Scholar
[169] Bassil Y., Image steganography based on a parameterized canny edge detection algorithm, arXiv preprint arXiv:1212.6259, 2012 10.5120/9682-4112 Search in Google Scholar
[170] Islam S., Modi M. R., Gupta P., Edge-based image steganography, EURASIP Journal on Information Security, 2014, 2014(1), 8 10.1186/1687-417X-2014-8 Search in Google Scholar
[171] Chan C. S., Chang C. Y., Hiding data in parity check bit. In Proceedings of the 4th International Conference on Uniquitous Information Management and Communication, 2010, 52 10.1145/2108616.2108679 Search in Google Scholar
[172] Afsari F., Eslami E., Eslami P., Interval-valued intuitionistic fuzzy generators: Application to edge detection, Journal of Intelligent & Fuzzy Systems, 2014, 27(3), 1309-1324 10.3233/IFS-131099 Search in Google Scholar
[173] Al-Dmour H., Al-Ani A., A steganography embedding method based on edge identification and XOR coding, Expert systems with Applications, 2016, 46, 293-306 10.1016/j.eswa.2015.10.024 Search in Google Scholar
[174] Chen W. J., Chang C. C., Le T. H. N., High payload steganography mechanism using hybrid edge detector, Expert Systems with applications, 2010, 37(4), 3292-3301 10.1016/j.eswa.2009.09.050 Search in Google Scholar
[175] Jung K. H., Yoo K. Y., Data hiding using edge detector for scalable images, Multimedia tools and applications, 2014, 71(3), 1455-1468 10.1007/s11042-012-1293-8 Search in Google Scholar
[176] Alam S., Ahmad T., Doja M. N., A Novel Edge Based Chaotic Steganography Method Using Neural Network, In Proceedings of the 5th International Conference on Frontiers in Intelligent Computing: Theory and Applications, Springer, Singapore, 2017, 467-475 10.1007/978-981-10-3156-4_48 Search in Google Scholar
[177] Islam S., Gupta P., Robust edge based image steganography through pixel intensity adjustment, In IEEE International Conference on High Performance Computing and Communications, (HPCC, CSS, ICESS), 2014, 771-777 Search in Google Scholar
[178] Hong W., Adaptive image data hiding in edges using patched reference table and pair-wise embedding technique, Information Sciences, 2013, 221, 473-489 10.1016/j.ins.2012.09.013 Search in Google Scholar
[179] Barton J. M., Method and apparatus for embedding authentication information within digital data, U.S. Patent No. 5,646,997, Washington, DC: U.S. Patent and Trademark Oflce,1997 Search in Google Scholar
[180] Tian J., Reversible data embedding using a difference expansion, IEEE transactions on circuits and systems for video technology, 2003, 13(8), 890-896 10.1109/TCSVT.2003.815962 Search in Google Scholar
[181] Alattar A. M., Reversible watermark using the difference expansion of a generalized integer transform, IEEE transactions on image processing, 2004, 13(8), 1147-1156 10.1109/TIP.2004.828418 Search in Google Scholar
[182] Kim H. J., Sachnev V., Shi Y. Q., Nam J., Choo H. G., A novel difference expansion transform for reversible data embedding, IEEE Transactions on Information Forensics and Security, 2008, 3(3), 456-465 10.1109/TIFS.2008.924600 Search in Google Scholar
[183] Jana B., High payload reversible data hiding scheme using weighted matrix, Optik-International Journal for Light and Electron Optics, 2016, 127(6), 3347-3358 10.1016/j.ijleo.2015.12.055 Search in Google Scholar
[184] Qin C., Chang C. C., Hsu T. J., Reversible data hiding scheme based on exploiting modification direction with two stegano-graphic images, Multimedia Tools and Applications, 2015, 74(15), 5861-5872 10.1007/s11042-014-1894-5 Search in Google Scholar
[185] Nguyen T. S., Chang C. C., A reversible data hiding scheme based on the Sudoku technique, Displays, 2015, 39, 109-116 10.1016/j.displa.2015.10.003 Search in Google Scholar
[186] Chang C. C., Nguyen T. S., Lin C. C., Reversible data embedding for indices based on histogram analysis, Journal of Visual Communication and Image Representation, 2014, 25(7), 1704-1716 10.1016/j.jvcir.2014.06.003 Search in Google Scholar
[187] Liu W. L., Leng H. S., Huang C. K., Chen D. C., A block-based division reversible data hiding method in encrypted images, Symmetry, 2017, 9(12), 308 10.3390/sym9120308 Search in Google Scholar
[188] Parah S. A., Ahad F., Sheikh J. A., Loan N. A., Bhat G. M., A New Reversible and high capacity data hiding technique for E-healthcare applications, Multimedia Tools and Applications, 2017, 76(3), 3943-3975 10.1007/s11042-016-4196-2 Search in Google Scholar
[189] Kumar R., Chand S., A novel high capacity reversible data hiding scheme based on pixel intensity segmentation, Multimedia Tools and Applications, 2017, 76(1), 979-996 10.1007/s11042-015-3069-4 Search in Google Scholar
[190] Hu J., Li T., Reversible steganography using extended image interpolation technique, Computers & Electrical Engineering, 2015, 46, 447-455 10.1016/j.compeleceng.2015.04.014 Search in Google Scholar
[191] Tang M., Hu J., Song W., Zeng S., Reversible and adaptive image steganographic method, AEU-International Journal of Electronics and Communications, 2015, 69(12), 1745-1754 10.1016/j.aeue.2015.08.011 Search in Google Scholar
[192] Sahu A. K., Swain G., High fidelity based reversible data hiding using modified LSB matching and pixel difference, Journal of King Saud University-Computer and Information Sciences, 2019, https://doi.org/10.1016/j.jksuci.2019.07.004 (in press) 10.1016/j.jksuci.2019.07.004 Search in Google Scholar
[193] Sahu A. K., Swain G., Dual Stego-imaging based Reversible Data Hiding using Improved LSB Matching, International Journal of Intelligent Engineering and Systems, 2019, 12(5), 2019, 63-73 10.22266/ijies2019.1031.07 Search in Google Scholar
[194] Chang C. C., Lu T. C., A difference expansion oriented data hiding scheme for restoring the original host images, Journal of Systems and Software, 2006, 79(12), 1754-1766 10.1016/j.jss.2006.03.035 Search in Google Scholar
[195] Chang C. C., Kieu T. D., Chou Y. C., Reversible data hiding scheme using two steganographic images, In TENCON, IEEE Region 10 Conference, 2007, 1-4 10.1109/TENCON.2007.4483783 Search in Google Scholar
[196] Wu M. N., Chang C. C., A novel high capacity reversible information hiding scheme based on side-match prediction and shortest spanning path, Circuits, Systems & Signal Processing, 2008, 27(2), 137-153 10.1007/s00034-008-9026-y Search in Google Scholar
[197] Li J. J., Lee C. F., Chang C. C., Lin J. Y., Wu Y. H., Reversible Data Hiding Scheme Based on Quad-Tree and Pixel Value Ordering, IEEE Access, 2019, 7, 142947-142962 10.1109/ACCESS.2019.2941500 Search in Google Scholar
[198] Lin J. Y., Liu Y., Chang C. C., A real-time dual-image-based reversible data hiding scheme using turtle shells, Journal of Real-Time Image Processing, 2019, 16(3), 673-684 10.1007/s11554-019-00863-0 Search in Google Scholar
[199] Lin J. Y., Chen Y., Chang C. C., Hu Y. C., Dual-image-based reversible data hiding scheme with integrity verification using exploiting modification direction, Multimedia Tools and Applications, 2019, 1-18. https://doi.org/10.1007/s11042-019-07783-y (in press) 10.1007/s11042-019-07783-y Search in Google Scholar
[200] Xie X. Z., Chang C. C., Lin C. C., Lin J. L., A Turtle Shell based RDH scheme with two-dimensional histogram shifting, Multimedia Tools and Applications, 2019, 1-24. https://doi.org/10.1007/s11042-018-7098-7 (in press) 10.1007/s11042-018-7098-7 Search in Google Scholar
[201] Lu T. C., Tseng C. Y., Wu J. H., Dual imaging-based reversible hiding technique using LSB matching, Signal Processing, 2015, 108, 77-89 10.1016/j.sigpro.2014.08.022 Search in Google Scholar
[202] Wang W., Ye J., Wang T., Wang W., A high capacity reversible data hiding scheme based on right-left shift, Signal Processing, 2018, 150, 102-115 10.1016/j.sigpro.2018.04.008 Search in Google Scholar
[203] Wang Y. L., Shen J. J., Hwang M. S., An Improved Dual Image-based Reversible Hiding Technique Using LSB Matching, International Journal of Network Security, 2017, 19(5), 858-862 Search in Google Scholar
[204] Ni Z., Shi Y. Q., Ansari N., Su W., (2006). Reversible data hiding, IEEE Transactions on Circuits and Systems for Video Technology, 2006, 16(3), 354-362 Search in Google Scholar
[205] Sahu A.K., Swain, G., Reversible Image Steganography Using Dual-Layer LSB Matching, Sensing and Imaging, 2020, 21:1, https://doi.org/10.1007/s11220-019-0262-y (in press) 10.1007/s11220-019-0262-y Search in Google Scholar
[206] Wang Y., Cai Z., He W., A New High Capacity Separable Reversible Data Hiding in Encrypted Images Based on Block Selection and Block-Level Encryption, IEEE Access, 2019, 7, 175671-175680 10.1109/ACCESS.2019.2957143 Search in Google Scholar
[207] Tai W. L., Yeh C. M., Chang C. C., Reversible data hiding based on histogram modification of pixel differences, IEEE Transactions on Circuits and Systems for video technology, 2009, 19(6), 906-910 10.1109/TCSVT.2009.2017409 Search in Google Scholar
[208] Hsiao J. Y., Chan K. F., Chang J. M., Block-based reversible data embedding, Signal Processing, 2009, 89(4), 556-569 10.1016/j.sigpro.2008.10.018 Search in Google Scholar
[209] Liu Y., Qu X., Xin G., A ROI-based reversible data hiding scheme in encrypted medical images. Journal of Visual Communication and Image Representation, 2016, 39, 51-57 10.1016/j.jvcir.2016.05.008 Search in Google Scholar
[210] Yao H., Mao F., Tang Z., Qin C., High-fidelity dual-image reversible data hiding via prediction-error shift, Signal Processing, 2019, 170, 107447. https://doi.org/10.1016/j.sigpro.2019.107447 (in press) 10.1016/j.sigpro.2019.107447 Search in Google Scholar
[211] Chang C. C., Lin C. C., Chen Y. H., Reversible data-embedding scheme using differences between original and predicted pixel values, IET information security, 2008, 2(2), 35-46 10.1049/iet-ifs:20070004 Search in Google Scholar
[212] Wang W., A reversible data hiding algorithm based on bidirectional difference expansion, Multimedia Tools and Applications, 2019, 1-24. DOI:10.1007/s11042-019-08255-z (in press) 10.1007/s11042-019-08255-z Search in Google Scholar
[213] Jung K. H., High-capacity reversible data hiding method using block expansion in digital images, Journal of Real-Time Image Processing, 2018, 14(1), 159-170 10.1007/s11554-016-0618-7 Search in Google Scholar
[214] Lu T. C., Chang C. C., Huang Y. H., High capacity reversible hiding scheme based on interpolation, difference expansion, and histogram shifting, Multimedia tools and applications, 2014, 72(1), 417-435 10.1007/s11042-013-1369-0 Search in Google Scholar
[215] Duan X., Jia K., Li B., Guo D., Zhang E., Qin C., Reversible image steganography scheme based on a U-Net structure, IEEE Access, 2019, 7, 9314-9323 10.1109/ACCESS.2019.2891247 Search in Google Scholar
[216] Hong W., Chen T. S., Shiu C. W., Reversible data hiding for high quality images using modification of prediction errors, Journal of Systems and Software, 2009, 82(11), 1833-1842 10.1016/j.jss.2009.05.051 Search in Google Scholar
[217] Pan Z., Hu S., Ma X., Wang L., Reversible data hiding based on local histogram shifting with multilayer embedding, Journal of Visual Communication and Image Representation, 2015, 31, 64-74 10.1016/j.jvcir.2015.05.005 Search in Google Scholar
[218] Li X., Zhang W., Gui X., Yang B., A novel reversible data hiding scheme based on two-dimensional difference-histogram modification, IEEE Transactions on Information Forensics and Security, 2013, 8(7), 1091-1100 10.1109/TIFS.2013.2261062 Search in Google Scholar
[219] Di F., Zhang M., Liao X., Liu J., High-fidelity reversible data hiding by Quadtree-based pixel value ordering, Multimedia Tools and Applications, 2019, 78(6), 7125-7141 10.1007/s11042-018-6469-4 Search in Google Scholar
[220] Liao X., Shu C., Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels, Journal of Visual Communication and Image Representation, 2015, 28, 21-27 10.1016/j.jvcir.2014.12.007 Search in Google Scholar
[221] Malik A., Sikka G., Verma H. K., An image interpolation based reversible data hiding scheme using pixel value adjusting feature, Multimedia Tools and Applications, 2017, 76(11), 13025-13046 10.1007/s11042-016-3707-5 Search in Google Scholar
[222] He W., Xiong G., Weng S., Cai Z., Wang Y., Reversible data hiding using multi-pass pixel-value-ordering and pairwise prediction-error expansion, Information Sciences, 2018, 467, 784-799 10.1016/j.ins.2018.04.088 Search in Google Scholar
[223] He W., Zhou K., Cai J., Wang L., Xiong G., Reversible data hiding using multi-pass pixel value ordering and prediction-error expansion, Journal of Visual Communication and Image Representation, 2017, 49, 351-360 10.1016/j.jvcir.2017.10.001 Search in Google Scholar
[224] Tsai Y. Y., Tsai D. S., Liu C. L., Reversible data hiding scheme based on neighboring pixel differences, Digital Signal Processing, 2013, 23(3), 919-927 10.1016/j.dsp.2012.12.014 Search in Google Scholar
[225] Abbasi R., Xu L., Amin F., Luo B., Efficient Lossless Compression Based Reversible Data Hiding Using Multilayered n-Bit Localization, Security and Communication Networks, 2019, https://doi.org/10.1155/2019/8981240 (in press) 10.1155/2019/8981240 Search in Google Scholar
[226] Tsai P., Hu Y. C., Yeh H. L., Reversible image hiding scheme using predictive coding and histogram shifting, Signal Processing, 2009, 89(6), 1129-1143 10.1016/j.sigpro.2008.12.017 Search in Google Scholar
[227] Wang J., Ni J., Zhang X., Shi Y. Q., Rate and distortion optimization for reversible data hiding using multiple histogram shifting, IEEE Transactions on Cybernetics, 2016, 47(2), 315-326 10.1109/TCYB.2015.2514110 Search in Google Scholar PubMed
[228] Xie X. Z., Chang C. C., Lin C. C., A hybrid reversible data hiding for multiple images with high embedding capacity, IEEE Access, 2019, 10.1109/ACCESS.2019.29 61764 (in press) 10.1109/ACCESS.2019.2961764 Search in Google Scholar
[229] Chang C. C., Tseng H. W., A steganographic method for digital images using side match, Pattern Recognition Letters, 2004, 25(12), 1431-1437 10.1016/j.patrec.2004.05.006 Search in Google Scholar
[230] Chang C. C., Wu W. C., A novel data hiding scheme for keeping high stego-image quality, In 12th IEEE International Multi-Media Modelling Conference, 2006, 1-8 Search in Google Scholar
[231] Chang C. C., Chou Y. C., Kieu T. D., An information hiding scheme using Sudoku, In 3 rd IEEE international conference on innovative computing information and control, 2008, 17-27 10.1109/ICICIC.2008.149 Search in Google Scholar
[232] He M., Liu Y., Chang C. C., He M., A Mini-Sudoku Matrix-Based Data Embedding Scheme With High Payload, IEEE Access, 2019, 7, 141414-141425 10.1109/ACCESS.2019.2943616 Search in Google Scholar
[233] Liu Y., Chang C. C., Huang P. C., Security protection using two different image shadows with authentication, Mathematical biosciences and engineering, 2019, 16(4), 1914-1932 10.3934/mbe.2019093 Search in Google Scholar PubMed
[234] Lin C. C., An information hiding scheme with minimal image distortion, Computer Standards & Interfaces, 2011, 33(5), 477-484 10.1016/j.csi.2011.02.003 Search in Google Scholar
[235] Jung K. H., Yoo K. Y., Data hiding method using image interpolation, Computer Standards & Interfaces, 2009, 31(2), 465-470 10.1016/j.csi.2008.06.001 Search in Google Scholar
[236] Xu H., Wang J., Kim H. J., Near-optimal solution to pair-wise LSB matching via an immune programming strategy, Information Sciences, 2010, 180(8), 1201-1217 10.1016/j.ins.2009.12.027 Search in Google Scholar
[237] Xia B. B., Wang A. H., Chang C. C., Liu L., An Image Steganography Scheme Using 3D-Sudoku, Journal of Information Hiding and Multimedia Signal Processing, 2016, 7(4), 836-845 Search in Google Scholar
[238] Kuo W. C., Kuo S. H., Wang C. C., Wuu L. C., High capacity data hiding scheme based on multi-bit encoding function, Optik-International Journal for Light and Electron Optics, 2016, 127(4), 1762-1769 10.1016/j.ijleo.2015.08.056 Search in Google Scholar
[239] Wazirali R., Alasmary W., Mahmoud M. M., Alhindi A., An Optimized Steganography Hiding Capacity and Imperceptibly Using Genetic Algorithms,IEEE Access, 2019, 7, 133496-133508 10.1109/ACCESS.2019.2941440 Search in Google Scholar
[240] Nguyen T. D., Arch-Int S., Arch-Int N., An adaptive multi bit-plane image steganography using block data-hiding, Multimedia tools and applications, 2016, 75(14), 8319-8345 10.1007/s11042-015-2752-9 Search in Google Scholar
[241] Amirtharajan R., Rayappan J. B. B., An intelligent chaotic embedding approach to enhance stego-image quality, Information Sciences, 2012, 193, 115-124 10.1016/j.ins.2012.01.010 Search in Google Scholar
[242] Younus Z. S., Hussain M. K., Image steganography using exploiting modification direction for compressed encrypted data, Journal of King Saud University-Computer and Information Sciences, 2019, https://doi.org/10.1016/j.jksuci.2019.04.008 (in press) 10.1016/j.jksuci.2019.04.008 Search in Google Scholar
[243] Kuo W. C., Li J. J., Wang C. C., Analysis of overflow in data hiding based on extraction function, Journal of Innovative Technology, 2019, 1(2), 21-25 Search in Google Scholar
[244] Kuo W. C., Kuo S. H., Huang Y. C., Data hiding schemes based on the formal improved exploiting modification direction method, Applied Mathematics & Information Sciences Letters, 2013, 1(3), 1-8 Search in Google Scholar
[245] Kuo W. C., Wang C. C., Data hiding based on generalised exploiting modification direction method, The Imaging Science Journal, 2013, 61(6), 484–490 10.1179/1743131X12Y.0000000011 Search in Google Scholar
[246] Kuo W. C., Kao M. C., A steganographic scheme based on formula fully exploiting modification directions, IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2013, 96(11), 2235-2243 10.1587/transfun.E96.A.2235 Search in Google Scholar
[247] Shen S.Y., Huang L.H., A data hiding scheme using pixel value differencing and improving exploiting modification directions, Computers & Security, 2015, 48, 131–141 10.1016/j.cose.2014.07.008 Search in Google Scholar
[248] Liu Y., Yang C., Sun Q., Enhance embedding capacity of generalized exploiting modification directions in data hiding, IEEE Access, 2017, 6, 5374-5378 10.1109/ACCESS.2017.2787803 Search in Google Scholar
[249] Kieu T. D., Chang C. C., A steganographic scheme by fully exploiting modification directions, Expert systems with Applications, 2011, 38(8), 10648-10657 10.1016/j.eswa.2011.02.122 Search in Google Scholar
[250] Biswas R., Mukherjee I., Bandyopadhyay S. K., Image feature based high capacity steganographic algorithm, Multimedia Tools and Applications, 2019, 1-18. https://doi.org/10.1007/s11042-019-7369-y (in press) 10.1007/s11042-019-7369-y Search in Google Scholar
[251] Verma V., Muttoo S. K., Singh V. B., Enhanced payload and trade-off for image steganography via a novel pixel digits alteration, Multimedia Tools and Applications, 2019, 1-20. DOI: 10.1007/s11042-019-08283-9 10.1007/s11042-019-08283-9 Search in Google Scholar
[252] Vanmathi C., Prabu S., Image Steganography Using Fuzzy Logic and Chaotic for Large Payload and High Imperceptibility, International Journal of Fuzzy Systems, 2018, 20(2), 460-473 10.1007/s40815-017-0420-0 Search in Google Scholar
[253] Wu K. S., Liao W. D., Lin C. N., Chen T. S., A high payload hybrid data hiding scheme with LSB, EMD and MPE, The Imaging Science Journal, 2015, 63(3), 174-181 10.1179/1743131X14Y.0000000099 Search in Google Scholar
[254] Yang C. Y., Wang W. F., Block-based colour image steganography using smart pixel-adjustment, In Genetic and Evolutionary Computing, Springer, Cham, 2015, 145-154 10.1007/978-3-319-12286-1_15 Search in Google Scholar
[255] Chen J. A PVD-based data hiding method with histogram preserving using pixel pair matching, Signal Processing: Image Communication, 2014, 29(3), 375-384 10.1016/j.image.2014.01.003 Search in Google Scholar
[256] Muhammad K., Ahmad J., Farman H., Jan Z., A new image steganographic technique using pattern based bits shuffling and magic LSB for grayscale images, 2016, arXiv preprint arXiv:1601.01386 Search in Google Scholar
[257] Thanikaiselvan V., Santosh K., Manikanta D., Amirtharajan R., A new steganography algorithm against chi square attack, Research Journal of Information Technology, 2013, 5, 363-372 10.3923/rjit.2013.363.372 Search in Google Scholar
[258] Bandyopadhyay D., Dasgupta K., Mandal J. K., Dutta P., Ojha V. K., Snášel V., A Framework of Secured and Bio-Inspired Image Steganography Using Chaotic Encryption with Genetic Algorithm Optimization (CEGAO), In Proceedings of the Fifth International Conference on Innovations in Bio-Inspired Computing and Applications IBICA, Springer, Cham, 2014, 271-280 10.1007/978-3-319-08156-4_27 Search in Google Scholar
[259] Sajasi S., Moghadam A. M. E., A high quality image steganography scheme based on fuzzy inference system, In 13th Iranian Conference on Fuzzy Systems (IFSC), 2013, 1-6 10.1109/IFSC.2013.6675666 Search in Google Scholar
[260] Das S., Sharma S., Bakshi S., Mukherjee I., A framework for pixel intensity modulation based image steganography, In Progress in Advanced Computing and Intelligent Engineering, Springer, Singapore, 2018, 3-14 10.1007/978-981-10-6872-0_1 Search in Google Scholar
[261] Niimi M., Noda H., Kawaguchi E., Eason R. O., High capacity and secure digital steganography to palette-based images, In Proceedings. International Conference on Image Processing, 2002, 2, II-II Search in Google Scholar
[262] Banik B. G., Bandyopadhyay S. K., Image Steganography using BitPlane complexity segmentation and hessenberg QR method, In Proceedings of the First International Conference on Intelligent Computing and Communication, Springer, Singapore, 2017, 623-633 10.1007/978-981-10-2035-3_63 Search in Google Scholar
[263] Paul G., Davidson I., Mukherjee I., Ravi, S. S., Keyless steganography in spatial domain using energetic pixels, In International Conference on Information Systems Security, Springer, Berlin, Heidelberg, 2017, 134-148 10.1007/978-3-642-35130-3_10 Search in Google Scholar
[264] Paul G., Davidson I., Mukherjee I., Ravi S. S., Keyless dynamic optimal multi-bit image steganography using energetic pixels, Multimedia Tools and Applications, 2017, 76(5), 7445-7471 10.1007/s11042-016-3319-0 Search in Google Scholar
[265] Muhammad K., Ahmad J., Rho S., Baik S. W., Image steganography for authenticity of visual contents in social networks, Multimedia Tools and Applications, 2017, 76(18), 18985-19004 10.1007/s11042-017-4420-8 Search in Google Scholar
[266] Liao X., Qin Z., Ding L., Data embedding in digital images using critical functions, Signal Processing: Image Communication, 2017, 58, 146-156 10.1016/j.image.2017.07.006 Search in Google Scholar
[267] Yang C. H., Wang S. J., Weng C. Y., Capacity-raising steganography using multi-pixel differencing and pixel-value shifting operations, Fundamenta Informaticae, 2010, 98(2-3), 321-336 10.3233/FI-2010-229 Search in Google Scholar
[268] Liao X., Guo S., Yin J., Wang H., Li X., Sangaiah, A. K., New cubic reference table based image steganography, Multimedia Tools and Applications, 2018, 77(8), 10033-10050 10.1007/s11042-017-4946-9 Search in Google Scholar
[269] Liao X., Yu Y., Li B., Li Z., Qin Z., A new payload partition strategy in color image steganography, IEEE Transactions on Circuits and Systems for Video Technology. 2019, 10.1109/TCSVT.2019.2896270 (in press) 10.1109/TCSVT.2019.2896270 Search in Google Scholar
[270] Liao X., Yin J., Two Embedding Strategies for Payload Distribution in Multiple Images Steganography, In IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2018, 1982-1986 10.1109/ICASSP.2018.8462384 Search in Google Scholar
[271] Liao X., Yin J., Guo S., Li X., Sangaiah A. K., Medical JPEG image steganography based on preserving inter-block dependencies, Computers & Electrical Engineering, 2018, 67, 320-329 10.1016/j.compeleceng.2017.08.020 Search in Google Scholar
[272] Al-Nofaie S. M. A., Gutub A. A. A., Utilizing pseudo-spaces to improve Arabic text steganography for multimedia data communications, Multimedia Tools and Applications, 2019, 1-49. https://doi.org/10.1007/s11042-019-08025-x (in press) 10.1007/s11042-019-08025-x Search in Google Scholar
[273] Al-Nofaie S., Gutub A., Al-Ghamdi M., Enhancing Arabic text steganography for personal usage utilizing pseudo-spaces, Journal of King Saud University-Computer and Information Sciences, 2019, https://doi.org/10.1016/j.jksuci.2019.06 (in press) Search in Google Scholar
[274] Gutub A. A. A., Alaseri K. A., Refining Arabic text stego-techniques for shares memorization of counting-based secret sharing, Journal of King Saud University-Computer and Information Sciences, 2019, https://doi.org/10.1016/j.jksuci.2019.06 . 014 (in press) Search in Google Scholar
[275] Gutub A., Al-Juaid N., Multi-bits stego-system for hiding text in multimedia images based on user security priority, Journal of Computer Hardware Engineering, 2018, 1(2), 1-9 Search in Google Scholar
[276] Liu G., Liu W., Dai Y., Lian S., Adaptive steganography based on block complexity and matrix embedding, Multimedia systems, 2014, 20(2), 227-238 10.1007/s00530-013-0313-5 Search in Google Scholar
[277] Sun H. M., Weng C. Y., Lee C. F., Yang C. H., Anti-forensics with steganographic data embedding in digital images, IEEE Journal on selected areas in Communications, 2011, 29(7), 1392-1403 10.1109/JSAC.2011.110806 Search in Google Scholar
[278] Kuo W. C., Wang C. C., Hou H. C., Signed digit data hiding scheme, Information Processing Letters, 2016, 116(2), 183-191 10.1016/j.ipl.2015.08.003 Search in Google Scholar
[279] Hong W., Chen T. S., A novel data embedding method using adaptive pixel pair matching, IEEE transactions on information forensics and security, 2011, 7(1), 176-184 10.1109/TIFS.2011.2155062 Search in Google Scholar
[280] Muhammad K., Ahmad J., Farman H., Jan Z., Sajjad M., Baik S. W., A Secure Method for Color Image Steganography using Gray-Level Modification and Multi-level Encryption, Transactions on Internet and Information Systems, 2015, 9(5), 1938-1962 10.3837/tiis.2015.05.022 Search in Google Scholar
[281] Kanan H. R., Nazeri B., A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm, Expert Systems with Applications, 2014, 41(14), 6123-6130 10.1016/j.eswa.2014.04.022 Search in Google Scholar
[282] El-Emam N. N., New data-hiding algorithm based on adaptive neural networks with modified particle swarm optimization, Computers & Security, 2015, 55, 21-45 10.1016/j.cose.2015.06.012 Search in Google Scholar
[283] Chakraborty S., Jalal A. S., Bhatnagar C., Secret image sharing using grayscale payload decomposition and irreversible image steganography, Journal of Information Security and Applications, 2013, 18(4), 180-192 10.1016/j.istr.2013.02.006 Search in Google Scholar
[284] Roy, R. Laha, S., Optimization of Stego Image retaining secret information using Genetic Algorithm with 8-connected PSNR, Procedia Computer Science, 2015, 60, 468-477 10.1016/j.procs.2015.08.168 Search in Google Scholar
[285] Chang C. C., Liu Y., Nguyen T. S., A novel turtle shell based scheme for data hiding, In 2014 tenth international conference on intelligent information hiding and multimedia signal processing, 2014, 89-93 10.1109/IIH-MSP.2014.29 Search in Google Scholar
[286] Hamzah A. A., Khattab S., Bayomi H., A linguistic steganography framework using Arabic calligraphy, Journal of King Saud University-Computer and Information Sciences, 2019, https://doi.org/10.1016/j.jksuci.2019.04.015 (in press) 10.1016/j.jksuci.2019.04.015 Search in Google Scholar
[287] Liu X., Lin C. C., Muhammad K., Al-Turjman F., Yuan S. M., Joint Data Hiding and Compression Scheme Based on Modified BTC and Image Inpainting, 2019, IEEE Access, 7, 116027-116037 10.1109/ACCESS.2019.2935907 Search in Google Scholar
[288] Muhammad K., Steganography: A Secure way for Transmission in Wireless Sensor Networks, 2015, arXiv preprint arXiv:1511.08865 Search in Google Scholar
[289] Muhammad K., Ahmad J., Farman H., Zubair M., A novel image steganographic approach for hiding text in color images using HSI color model, 2015, arXiv preprint arXiv:1503.00388 Search in Google Scholar
[290] Pan J. S., Li W., Yang C. S., Yan L. J., Image steganography based on subsampling and compressive sensing, Multimedia Tools and Applications, 2015, 74(21), 9191-9205 10.1007/s11042-014-2076-1 Search in Google Scholar
[291] Liu Y., Zhao H., Liu S., Feng C., Liu S., A robust and improved visual quality data hiding method for HEVC, IEEE Access, 2018, 6, 53984-53997 10.1109/ACCESS.2018.2869148 Search in Google Scholar
[292] Li N., Hu J., Sun R., Wang S., Luo Z., A high-capacity 3d steganography algorithm with adjustable distortion, IEEE Access, 2017, 5, 24457-24466 10.1109/ACCESS.2017.2767072 Search in Google Scholar
[293] Luo J., Zhou R. G., Luo G., Li Y., Liu G., Traceable Quantum Steganography Scheme Based on Pixel Value Differencing, Scientific reports, 2019, 9(1), 1-12. 10.1038/s41598-019-51598-8 Search in Google Scholar PubMed PubMed Central
[294] Liao X., Chen G., Yin J., Content-adaptive steganalysis for color images, Security and Communication Networks, 9(18), 2016, 5756-5763 10.1002/sec.1734 Search in Google Scholar
[295] Liao X., Chen G., Li Q., Liu J., Improved WOW adaptive image steganography method, In International Conference on Algorithms and Architectures for Parallel Processing, Springer, Cham, 2015, 695-702 10.1007/978-3-319-27137-8_50 Search in Google Scholar
[296] Kaur M., Juneja M., Adaptive Block Based Steganographic Model with Dynamic Block Estimation with Fuzzy Rules, In Innovations in Computer Science and Engineering, Springer, Singapore, 2017, 167-176 10.1007/978-981-10-3818-1_19 Search in Google Scholar
[297] Muhammad K., Sajjad M., Mehmood I., Rho S., Baik S. W., A novel magic LSB substitution method (M-LSB-SM) using multi-level encryption and achromatic component of an image, Multimedia Tools and Applications, 2016, 75(22), 14867-14893 10.1007/s11042-015-2671-9 Search in Google Scholar
[298] Zhang X., Wang S., Eflcient Steganographic Embedding by Exploiting Modification direction, IEE Communications Letter, 2006, 10(11), 781–783 10.1109/LCOMM.2006.060863 Search in Google Scholar
[299] Kaw J. A., Loan N. A., Parah S. A., Muhammad K., Sheikh J. A., Bhat G. M., A reversible and secure patient information hiding system for IoT driven e-health, International Journal of Information Management, 2019, 45, 262-275 10.1016/j.ijinfomgt.2018.09.008 Search in Google Scholar
[300] Shafi I., Noman M., Gohar M., Ahmad A., Khan M., Din S., Ahmad J., An adaptive hybrid fuzzy-wavelet approach for image steganography using bit reduction and pixel adjustment, Soft Computing, 2018, 22(5), 1555-1567 10.1007/s00500-017-2944-5 Search in Google Scholar
[301] El-emam N. N., Embedding a large amount of information using high secure neural based steganography algorithm, International Journal of Information and Communication Engineering, 2008, 4(2), 2 Search in Google Scholar
[302] Hameed M. A., Hassaballah M., Aly S., Awad A. I., An Adaptive Image Steganography Method Based on Histogram of Oriented Gradient and PVD-LSB Techniques, IEEE Access, 2019, 7, 185189-185204 10.1109/ACCESS.2019.2960254 Search in Google Scholar
[303] Liu Y., Chang C. C., Nguyen T. S., High capacity turtle shell-based data hiding, IET Image Processing, 2016, 10(2), 130-137 10.1049/iet-ipr.2014.1015 Search in Google Scholar
[304] Liu L., Chang C. C., Wang A., Data hiding based on extended turtle shell matrix construction method, Multimedia Tools and Applications, 2017, 76(10), 12233-12250 10.1007/s11042-016-3624-7 Search in Google Scholar
[305] Xie X. Z., Lin C. C., Chang C. C., Data hiding based on a two-layer turtle shell matrix, Symmetry, 2018, 10(2), 47 10.3390/sym10020047 Search in Google Scholar
[306] Chang C. C., Chou Y. C., Kieu T. D., An information hiding scheme using Sudoku, In 3rd international conference on innovative computing information and control, 2008, 1-5. 10.1109/ICICIC.2008.149 10.1109/ICICIC.2008.149 Search in Google Scholar
[307] Kumar M. S., Mamatha E., Reddy C. S., Mukesh V., Reddy R. D., Data hiding with dual based reversible image using sudoku technique, In 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), 2017, 2166-2172 10.1109/ICACCI.2017.8126166 Search in Google Scholar
[308] Alface P. R., Macq B., From 3D mesh data hiding to 3D shape blind and robust watermarking: A survey, In Transactions on data hiding and multimedia security II, Springer, Berlin, Heidelberg, 2007, 91-115 10.1007/978-3-540-73092-7_5 Search in Google Scholar
[309] Thiyagarajan P., Natarajan V., Aghila G., Venkatesan V. P., Anitha R., Pattern based 3D image Steganography, 3D Research, 2013, 4(1), 1 10.1007/3DRes.01(2013)1 Search in Google Scholar
[310] Cayre F., Macq B., Data hiding on 3-D triangle meshes, IEEE Transactions on signal Processing, 2003, 51(4), 939-949 10.1109/TSP.2003.809380 Search in Google Scholar
[311] Tsai Y. Y., An adaptive steganographic algorithm for 3D polygonal models using vertex decimation. Multimedia Tools and Applications, 2014, 69(3), 859-876 10.1007/s11042-012-1135-8 Search in Google Scholar
[312] Ghamizi S., Cordy M., Papadakis M., Traon Y. L., Adversarial Embedding: A robust and elusive Steganography and Watermarking technique, 2019, arXiv preprint arXiv:1912.01487 Search in Google Scholar
[313] Kim J., Park H., Park J. I., CNN-based image steganalysis using additional data embedding, Multimedia Tools and Applications, 2019, 1-18. https://doi.org/10.1007/s11042-019-08251-3 10.1007/s11042-019-08251-3 Search in Google Scholar
[314] Baluja S., Hiding images in plain sight: Deep steganography, In Advances in Neural Information Processing Systems, 2017, 2069-2079 Search in Google Scholar
[315] Liu, L., Wang A., Chang C. C., Li, Z., A Secret Image Sharing with Deep-steganography and Two-stage Authentication Based on Matrix Encoding, International Journal of Network Security, 2017, 19(3), 327-334 Search in Google Scholar
[316] Zhang R., Dong S., Liu J., Invisible steganography via generative adversarial networks, Multimedia Tools and Applications, 2019, 78(7), 8559-8575 10.1007/s11042-018-6951-z Search in Google Scholar
[317] Duan X., Jia K., Li B., Guo D., Zhang E., Qin C., Reversible image steganography scheme based on a U-Net structure, IEEE Access, 2019, 7, 9314-9323 10.1109/ACCESS.2019.2891247 Search in Google Scholar
[318] Duan X., Song H., Qin C., Khan M. K., Coverless steganography for digital images based on a generative model, Computers, Materials & Continua, 2018, 55(3), 483-493 Search in Google Scholar
[319] Atee H. A., Ahmad R., Noor N. M., Rahma A. M. S., Aljeroudi Y. Extreme learning machine based optimal embedding location finder for image steganography, PloS one, 2017, 12(2), e0170329 10.1371/journal.pone.0170329 Search in Google Scholar PubMed PubMed Central
[320] Hu D., Wang L., Jiang W., Zheng S., Li B., A novel image steganography method via deep convolutional generative adversarial networks, IEEE Access, 2018, 6, 38303-38314 10.1109/ACCESS.2018.2852771 Search in Google Scholar
[321] Wu P., Yang Y., Li X., Stegnet: Mega image steganography capacity with deep convolutional network, Future Internet, 2018, 10(6), 54 10.3390/fi10060054 Search in Google Scholar
[322] Li C., Jiang Y., Cheslyar M., Embedding image through generated intermediate medium using deep convolutional generative adversarial network, Computers, Materials & Continua, 2018, 56(2), 313-324 Search in Google Scholar
[323] Husien S., Badi H., Artificial neural network for steganography, Neural Computing and Applications, 2015, 26(1), 111-116 10.1007/s00521-014-1702-1 Search in Google Scholar
[324] Ghaleb Al-Jbara H. A., Mat-Kiah L. B., Jalab H. A., Increased capacity of image based steganography using artificial neural network, In AIP Conference Proceedings, 2012, 1482(1), 20-25 10.1063/1.4757431 Search in Google Scholar
[325] Zhu J., Kaplan R., Johnson J., Fei-Fei L., Hidden: Hiding data with deep networks, In Proceedings of the European Conference on Computer Vision (ECCV), 2018, 657-672 10.1007/978-3-030-01267-0_40 Search in Google Scholar
[326] Qian Y., Dong J., Wang W., Tan T., Deep learning for steganalysis via convolutional neural networks, In Media Watermarking, Security, and Forensics. International Society for Optics and Photonics, 2015, 9409, 94090J 10.1117/12.2083479 Search in Google Scholar
[327] Fridrich J., Kodovsky J., Rich models for steganalysis of digital images, IEEE Transactions on Information Forensics and Security, 2012, 7(3), 868-882 10.1109/TIFS.2012.2190402 Search in Google Scholar
[328] Ye J., Ni J., Yi Y., Deep learning hierarchical representations for image steganalysis, IEEE Transactions on Information Forensics and Security, 2017, 12(11), 2545-2557 10.1109/TIFS.2017.2710946 Search in Google Scholar
[329] Hayes J., Danezis G., Generating steganographic images via adversarial training, In Advances in Neural Information Processing Systems, 2017, 1954-1963 Search in Google Scholar
[330] Sharma K., Aggarwal A., Singhania T., Gupta D., Khanna A., Hiding Data in Images Using Cryptography and Deep Neural Network, 2019, arXiv preprint arXiv:1912.10413 10.33969/AIS.2019.11009 Search in Google Scholar
[331] Kim D. H., Lee H. Y., Deep Learning-Based Steganalysis Against Spatial Domain Steganography, In European Conference on Electrical Engineering and Computer Science (EECS), 2017, 1-4 10.1109/EECS.2017.9 Search in Google Scholar
[332] Ye J., Ni J., Yi Y., Deep learning hierarchical representations for image steganalysis, IEEE Transactions on Information Forensics and Security, 2017, 12(11), 2545-2557 10.1109/TIFS.2017.2710946 Search in Google Scholar
[333] Ge S., Gao Y., Wang R., Least significant bit steganography detection with machine learning techniques, In Proceedings of the international workshop on Domain driven data mining, 2007, 24-32. https://doi.org/10.1145/1288552.1288556 10.1145/1288552.1288556 Search in Google Scholar
[334] Berg G., Davidson I., Duan M. Y., Paul, G., Searching for Hidden Messages: Automatic Detection of Steganography, In IAAI, 2003, 51-56 Search in Google Scholar
[335] Wu S., Zhong S. H., Liu Y., Steganalysis via deep residual network, In IEEE 22nd International Conference on Parallel and Distributed Systems (ICPADS), 2016, 1233-1236 10.1109/ICPADS.2016.0167 Search in Google Scholar
[336] Wu S., Zhong S., Liu Y., Deep residual learning for image steganalysis, Multimedia tools and applications, 2018, 77(9), 10437-10453 10.1007/s11042-017-4440-4 Search in Google Scholar
[337] Zhang Y., Zhang W., Chen K., Liu J., Liu Y., Yu N., Adversarial examples against deep neural network based steganalysis, In Proceedings of the 6th ACM Workshop on Information Hiding and Multimedia Security, 2018, 67-72 10.1145/3206004.3206012 Search in Google Scholar
[338] Kang S., Park H., Park J. I., CNN-Based Ternary Classification for Image Steganalysis, Electronics, 2019, 8(11), 122 10.3390/electronics8111225 Search in Google Scholar
[339] USC-SIPI Image Database. [Online]. Available: http://sipi.usc.edu/database/database.php?volume=misc Search in Google Scholar
[340] http://homepages.inf.ed.ac.uk/rbf/CVonline/Imagedbase.htm Search in Google Scholar
[341] Pevny T., Bas P., Fridrich J., Steganalysis by subtractive pixel adjacency matrix, IEEE Transactions on information Forensics and Security, 2010, 5(2), 215-224 10.1109/TIFS.2010.2045842 Search in Google Scholar
[342] Fridrich J., Kodovsky J., Rich models for steganalysis of digital images, IEEE Transactions on Information Forensics and Security, 2012, 7(3), 868-882 10.1109/TIFS.2012.2190402 Search in Google Scholar
[343] Gutub A., Al-Ghamdi M., Hiding shares by multimedia image steganography for optimized counting-based secret sharing, Multimedia Tools and Applications, 2020, 1-35. DOI: 10.1007/s11042-019-08427-x (in press) 10.1007/s11042-019-08427-x Search in Google Scholar
[344] Alanazi N., Khan E., Gutub A., Inclusion of Unicode Standard Seamless Characters to Expand Arabic Text Steganography for Secure Individual Uses, Journal of King Saud University-Computer and Information Sciences. 2020, https://doi.org/10.1016/j.jksuci.2020.04.011 (in press) 10.1016/j.jksuci.2020.04.011 Search in Google Scholar
[345] Gutub A., Al-Juaid N., Khan E., Counting-based secret sharing technique for multimedia applications, Multimedia Tools and Applications, 2019, 78(5), 5591-5619 10.1007/s11042-017-5293-6 Search in Google Scholar
[346] Gutub A., Al-Shaarani F., Eflcient Implementation of Multi-image Secret Hiding Based on LSB and DWT Steganography Comparisons, Arabian Journal for Science and Engineering, 2020, 1-14. https://doi.org/10.1007/s13369-020-04413-w (in press) 10.1007/s13369-020-04413-w Search in Google Scholar
[347] Al-Khodaidi T., Gutub A., Trustworthy Target Key Alteration Helping Counting-Based Secret Sharing Applicability, Arabian Journal for Science and Engineering, 2020, https://doi.org/10.1007/s13369-020-04422-9 (in press) 10.1007/s13369-020-04422-9 Search in Google Scholar
[348] Al-Juaid N., Gutub A., Combining RSA and audio steganography on personal computers for enhancing security, SN Applied Sciences, 2019, 1(8), 830-841 10.1007/s42452-019-0875-8 Search in Google Scholar
© 2020 Aditya Kumar Sahu et al., published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
- X / Twitter
Supplementary Materials
Please login or register with De Gruyter to order this product.
Journal and Issue
Articles in the same issue.
Recent Advances of Image Steganography With Generative Adversarial Networks
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Entropy (Basel)

Distributed Steganography in PDF Files—Secrets Hidden in Modified Pages
This paper shows how to diffuse a message and hide it in multiple PDF files. Presented method uses dereferenced objects and secret splitting or sharing algorithms. It is applicable to various types of PDF files, including text documents, presentations, scanned images etc. Because hiding process is based on structure manipulation, the solution may be easily combined with content-dependent steganographic techniques. The hidden pages are not visible in typical application usage, which was tested with seven different programs.
1. Introduction
PDF is one of the most common used document formats nowadays. The main advantages of these files are preserving the appearance when the document is printed and using hyperlinks. On the other hand, PDF is not customizable and has many problems with changing a style, like increasing font size or adjusting contrast. Nevertheless, its popularity is growing together with the number of compatible software, including readers embedded in web browsers.
Not everyone knows that PDF files may hold secrets, too. Concealing data in an inconspicuous way is called steganography [ 1 ] and is mainly used to communicate secretly. This attribute differentiates it from cryptography [ 2 , 3 ]—when information is encrypted, it cannot be read, but everyone knows of its existence. In steganography, the primary goal is undetectability of secret message. This is realized with an ordinary file called carrier or container in which the message is embedded. Virtually any file may play this role, for example an image, video or HTML page [ 4 ].
Sometimes, the steganography is used solely; in other cases, it is combined with other means of information security [ 5 ]. The one example is to disperse the message in the container with steganographic key. Another is distributed steganography in which the secret is split into some shares that are later embedded in multiple carrier files. The files with payload may be saved in remote locations or in a cloud. To reveal the secret, required number of shares should be recovered first. The general scheme of this approach is presented in Figure 1 .

Distributed steganography scheme.
A few examples of steganographic algorithms designed to work on PDF files include: white text on white background, object overlapping or image steganography in existing pictures. These specialized solutions may be sufficient in some situations, but are not appropriate for many documents commonly found in real life applications, like pure text or scans. Presented steganographic method is more universal and may be used in any type of PDF file.
This paper describes how to split a payload and then conceal the shares in PDF files. Section 2 presents technical details of PDF format. Section 3 demonstrates general method of hiding pages in PDF documents with comprehensible example. Specific algorithms of secret splitting are shown in Section 4 . Details of extracting the data from documents may be found in Section 5 . The last section summarizes the entire article.
2. PDF Format
PDF (Portable Document Format) is a popular document format that became open standard in 2008 [ 6 ]. It is text-based, but may (and usually does) contain binary streams. PDFs are consisted of a few parts: header, body, cross-reference table, trailer, xref pointer and end of file marker [ 7 ], as presented in Figure 2 .

An example of simple PDF file and its parts. The lines on the scheme do not belong to the file; they were added for better readability.
The header of PDF starts with a signature—%PDF- followed by version. It may be PDF-1.5 as in presented example, but older or newer version are possible as well. Another information that is optional in header is charset identifier. This is used by software to determine if the file is encoded in ASCII or not. When the identifier is present, it appears in second line of the file as 4 non-ASCII characters in a comment. (The comments in PDF are created with %, so the header itself is a comment!)
The next and most important part of PDF file is body section. Here are stored all contents normally visible in PDF reader. The body is consisted of objects which come in many types: boolean values, numbers, strings, arrays, dictionaries, binary streams and others. They are built in the following manner:
Each object has its own unique identifier (number). Generation of object is usually equal to 0 (unless the file has multiple revisions) and content very often lies between << and >> which is dictionary format.
Crossref (xref) plays a role of table of contents of the file. Its initial line stores two values: offset and number of objects (in our example from Figure 2 it is 0 8 ). After that there is a table in which each row corresponds to a single object and includes its offset and generation. The table has fixed length of 20 characters so that is easy to parse. The important information to note is that the first object is always null.
The objects form tree structure, so the order of elements in xref table does not necessarily correspond to their appearance in the document. Obviously, the initial element needs to be stored somehow to inform the parser where the content starts. This is what trailer is used for—it defines the reference to root object together with its size (count of indirect objects). When the trailer is parsed, it gives the location of root object which then allows to subsequently parse linked objects called kids.
The second to last element of PDF is xref pointer that indicates where xref table is located. It occupies two lines: first with startxref keyword and second with single number denoting the offset to xref.
PDFs end with %%EOF which is end of file marker. The important but easy to miss fact is that the percent character in this line is doubled.
3. Hidden Pages
The whole page(s) of PDF document may be hidden by modifying the tree structure of objects. The one idea is to remove reference to a certain page from its parent and to decrease the counter of pages. The content of the object remains untouched; only the reference is deleted. Let us consider the following example:
This is a fragment from 2-pages PDF created to demonstrate concealing process. Presented object has two references to kids (id 3 and id 11) and the page counter is set to 2. To delete the second page, we need to remove the reference 11 0 R and additionally decrease page counter by 1. The resulting file is smaller than the original by 7 bytes (which is about 0.07% of total size). Here is how the object looks like after such modifications.
The new document was tested to see if it opens correctly and the number of pages was as expected. The tests included PDF readers that parse and show documents directly and also graphical software with ability to import PDF as raster or vector image. They were: Evince, Adobe Acrobat X, Okular, Firefox (web browser that may internally render PDFs)—group 1; GIMP, Inkscape and Draw from LibreOffice—group 2.
It turned out that every program was able to open the file and show total page count equal to 1 as it should. The only incident occurred during closing the document in Acrobat X. The application ask if it should save changes. But of course no changes were made, the file was just opened. Why this happened? Probably Acrobat X assumed that orphaned object was added to document in current session. If so, why a number of other applications processed this file normally and without any warnings? This is because most readers are written to be tolerant to various weirdness that sometimes appear in PDF files. There are even programs that accept malformed documents, for example with some elements missing. In this study Acrobat X was found the most strict software.
Another approach is applicable when pages are removed from the end of the file. This method is even simpler than previous one, as all we need to do is to decrease the page counter. Then the object would look like:
In this case the reference was not cleared, so only 1 byte was modified and the file size did not change at all.
The tests from previous version were repeated on newly created document. Again, the document opened correctly in each program and the number of pages was equal to 1. This time Acrobat X did not show any dialog (as well as remaining applications) and no warnings were found. Lastly, new PDF was checked with command line program pdftk that was asked to extract the second page from the document. It raised the error that the input file has only 1 page—which confirmed correctness of the solution.
To sum up this section, both methods produce PDF documents with correct number of pages. Second technique (without clearing reference) was found more silent. The size of resulting file is identical or almost identical as the source PDF. Also, described algorithm of secret hiding works very efficiently in terms of complexity. No matter how many pages are concealed, counter modification is done in constant time.
3.1. Example of Adding and Hiding a Page in PDF
Presented technique is particularly useful when a new page (to be hidden) is added to preexisting PDF document. It requires two files: one carrier and one PDF with secret content. First the files are combined and then new pages are concealed as described earlier.
A comprehensible example demonstrate the whole process step by step. At the beginning, two files were prepared—simple 2-pages “Hello World” document that served as a carrier and secret document with text next to a picture.
Next, the documents were joined with pdftk (pdftoolkit):
where ex1.pdf and ex2.pdf are input files and ex3.pdf is final document. Other methods of combining are also possible, such as pdfjam or various PDF printers. The resulting file had 3 pages, two from the container and one from secret document.
Later secret content was hidden with decreasing total page counter. Indeed, the final document has only 2 pages, as presented in Figure 3 . The screenshots show files opened in Firefox, but tests conducted with different software gave the same results.

Example of adding and hiding secret page in PDF document.
The intermediate file was somewhat smaller than sum of carrier and secret file. This is because joining is not simple concatenation, but introduction of new objects and modification of crossref table. The final document had exactly the same length as the intermediate one, which was expected regarding hiding process as byte substitution.
Presented technique does not leave visual traces that user may accidentally bump into during normal application usage. This differentiate it from other known techniques, as setting text color identical to background or hiding the text behind another object. Figure 4 presents what happens when the hidden text is selected, either manually or with Ctrl+A. This is common practice if the user wants to copy an excerpt or when there is insufficient contrast and the content is hard to read. Normally both texts are invisible (one on the left is white, one on the right is covered with white rectangle), but with selection they are easy to spot. Such situation does not occur in described method which is based on structure manipulation.

Example of different technique—hiding text by changing color or covering it with a rectangle.
4. Secret Sharing
Secret sharing techniques allow to divide a secret into several parts called shares that can later be joined to recover initial information [ 8 ]. Usually a certain number of shares is required to successfully reconstruct the secret [ 9 ]. This value is called threshold and it may be lower than total number of shares. In such case secret message may be reconstructed even when some parts are missing. It is also possible to create more complex solutions, including hierarchical [ 10 ], expandable [ 11 , 12 ] or multistage systems [ 13 ]. A majority of schemes use numeric secrets, but there are exceptions, for example matrices [ 14 , 15 ] or images [ 16 ].
The most known secret sharing algorithm is based on XOR operation. It provides perfect secrecy (any number of shares below the threshold is unable to find anything about the secret), but all shares are required to reconstruct secret message. For two parts, the first share is random binary data of length equal to secret length; the second share is a result of bitwise XOR operation on random data and the secret. The reconstruction is simply XOR of both shares.
XOR secret sharing is easy to demonstrate with text data that may be represented in ASCII, Unicode or other encoding standard. For example, converting “Hello” to ASCII codes gives 72, 101, 108, 108, 111 . These numbers take part in share generation. Let us assume that we want three shares, so we need to create two sets of random numbers (of length equal to input text length, in this case 5). The values should be limited to range 0–255 as chosen encoding requires. The random sets are 20, 155, 255, 35, 218 and 38, 106, 229, 76, 174 —they serve as share1 and share2. The last share is created as XOR of ASCII codes of “Hello” and two sets of random values, which is equal to 122, 148, 118, 3, 27 . Now, to reconstruct initial text, one need to compute elementwise XOR of all three shares and transform the codes back to characters. This process is not presented here, but everyone is invited to test correctness of the algorithm with own hands.
In XOR method every share is necessary to recover the secret, which may be seen as disadvantage when some shares are missing or destroyed. In such cases schemes with threshold are the best solution. They have two parameters: n —total number of shares and k —number of shares sufficient to reconstruct the secret. An example of threshold system is encoding the secret in a polynomial. With n = 4 and k = 3, we need to create a polynomial of degree 2 and evaluate it at 4 chosen values. For instance, the secret is equal to 10 and our polynomial is p ( x ) = − 4 x 2 + 2 x + 10 (the secret is free term, remaining coefficients are random numbers). We choose 4 points that lie on polynomial: ( 1 , 8 ) , ( 2 , − 2 ) , ( − 1 , 4 ) and ( − 2 , − 10 ) —these are shares. To recover the secret, one need to reconstruct the polynomial from any three points (which is possible even if one of four points is missing) and get free term. Obviously polynomial formula is shredded after share generation and cannot be used to read the secret directly.
Many more secret sharing algorithms are available besides presented above [ 17 , 18 , 19 , 20 , 21 , 22 , 23 , 24 ]. They offer various secret formats, number of shares and other characteristics that may be adjusted to needs.
5. Distributed Steganography on Hidden Pages in PDF
Previous sections explained how to conceal a page in PDF file and how to divide a secret into pieces. In distributed steganography both these operations are used. Each share is embedded in separate document by placing the payload at additional page which is later removed (as presented in Section 3.1 ). In reconstruction phase, shares are combined to form the secret. But in between there is one more thing to discuss: hidden data recovery.
To explain that, a few details of PDF processing will be necessary. The data in PDF files are stored in binary streams that are easy to identify: they lie between stream and endstream keywords. The content of the stream may be additionally encoded (which is optional, but very often used due to compression) or encrypted. An object with stream may declare many encodings which are applied subsequently. In such case, to retrieve final data, multiple decoders need to be used one by one.
When the document is processed, the software is able to identify required decoders because of the property /Filter followed by decoder name. The most common is /FlateDecode (zlib compression), but others like /ASCIIHexDecode are also possible.
5.1. Example of Decoding a Secret from Multiple PDF Files
To show presented ideas in practice, we will go step by step through decoding process. The message is split with XOR technique (described in Section 4 ) and hidden in two documents filled with “Lorem ipsum” text (2 and 5 pages). First we need to locate the removed page and follow the references until reaching the object with binary stream. In first file its content was (non-printing characters are in hex):
The object declared FlateDecode, therefore the next step is to decompress these data with zlib. At this stage the interesting parts are already visible:
From that we can easily obtain pure numbers: 11, 239, 177, 117, 236 .
The same process we may repeated for second file. Here is binary content of the stream:
After zlib decompression:
And just numbers: 67, 138, 221, 25, 131 .
The one final step is needed to decode hidden message. Two arrays should be XORed elementwise and casted to characters. Eventually the secret is revealed: Hello .
6. Detection
It is also important to analyze possible attacks aimed at detecting or destroying hidden data. When the original file is present, an adversary may use diff program to find discrepancies. However, PDF documents contain binary streams, so they are automatically treated as binaries. Normally, when diff compares binaries, it only informs whether the files differ or not, without giving any details or showing interesting fragments. This is why the adversary needs to use --text option to compare PDF documents line by line.
The program deals well with this task, especially in ideal case when only the counter was modified ( Figure 5 ). These are files that were analyzed in Section 5.1 . The output shows how exactly they differ. For example, “287c287” means that line 287 from first file need to be changed (c) to match line 287 from second file. The lines themselves are separated with “ - - - ” and each of them is marked with “ < ” or “ > ” depending of origin.

Output of diff program for modified files in ideal case.
Such laboratory conditions obviously do not apply to real life in which source file is not conveniently available. Then the adversary needs to perform deeper analysis, including tree structure examination. One possibility is to look for orphaned objects (those which cannot be reached from the root). This strategy is eventually able to find objects deleted from Kids references. On the other hand, it is useless when only the counter was decreased and the references are present. So the attacker should also check pages table and counter value. Different approaches, like manual examination of objects, are more probable to fail. In PDF documents numerous objects represent fonts and page elements, so finding actual content may be challenging.
Incidentally, detecting additional objects or other errors in PDF file does not necessarily mean that steganography was used. Sometimes documents are malformed, have some parts missing or present other weirdness. But the software is still able to process those files and display them more or less correctly. The question may arise why invalid documents are accepted, usually without any warning? The answer is simple: if the reader forced precise adjustment to standard, some documents would break and users would switch to another program that supports not-so-correct format (speaking of which, the same problem is present in HTML browsers). A positive side of that mess is the chance to occasionally use steganography in PDF documents.
Another method of steganalysis is file size examination. This technique is efficient in very short files or when payload size is significant in relation to carrier document size. Of course in serious applications such situation is unacceptable—when size of the file changes noticeably, another container should be selected. Nevertheless, the method is mentioned as theoretical mean which may be used against inexperienced steganogaphers.
Presented technique is resistant to attacks targeted at file content (like resampling and replacing an image) because it is structure-based. The resistance to joining PDF documents varies depending on the software used. It was tested with two applications: pdftk and pdfmerge. The interesting thing is that pdftk behaves differently when working on files created with various version of the algorithm. In case of simple counter decrement it leaks share content, but when the references are deleted, the shares are not compromised (they may be removed, though). These observations apply regardless of order of concatenated documents. On the other hand, pdfmerge raises an error when at least one of the input files is modified, but nonetheless creates valid output without revealing hidden shares.
Destroying hidden data is separate type of attack that is aimed to remove the payload, not to detect it. In typical blind usage suspicious file is processed regardless whether it contains secret data or not. This approach may be used when the amount of data is so massive that it exceeds the ability of inspection or when other methods fail. Such attacks give quite good results in image steganography, because human eye is unable to notice slight alterations of pixels. However, the same cannot be said about binary data. Blind modification or deletion of random streams may damage the file, change its appearance or destroy important content. In conclusion, blind attacks to PDF documents usually make those files useless—for this reason are not recommended.
The concept presented in this paper has been shown on some short documents to be easy to understand. But the analysis reached also larger PDF files, including over 300 MB file created from scanned images. Regardless of page dimensions or dominating types of objects, the hiding and recovering processes were successful. This means that different kinds of PDF documents may serve as containers (scanned files, presentations, text documents, etc.), which is a huge advantage of presented method. Also the secret length may vary. The tests proved that it is possible to conceal a secret on single page as well as on multiple pages. So the universality is main factor that distinguishes this technique from others and allows to build upon it for further advancements.
The solution was analyzed with 7 different programs: 4 PDF readers (Evince, Adobe Acrobat X, Okular, Firefox—web browser) and 3 graphical applications with ability to render PDF content (GIMP, Inkscape and Draw from LibreOffice). Created files opened correctly in all of them; the approach of decrement the counter turned out to be better, because the software had not shown any trace of hidden content.
In real world applications the circumstances should also be considered to make detection harder. The recommended way is to use common documents of decent length that may easily blend in normal traffic. Although the capacity of presented method is theoretically unlimited, it is advisable to choose carriers so that the share size does not exceed 1% (cautious variant) to 5% (more risky) of carrier size. It is particularly important when the shares are not textual, but for example in graphical format.
PDF files have been chosen to this study because of their wide use in Internet which make them great steganographic medium. Obtained results encourage to conduct more research in this area. The future projects may concern new methods of distributed steganography in PDF documents, incorporating cryptography and other means of security. Another idea is to extend the study by new types of carriers and develop advanced methods of sharing and concealing secrets. This covers a broad area of research and concerns especially combination of steganography and secret sharing [ 25 , 26 ]. There are still much things to discover and open problems to address in fascinating field of information hiding.
Abbreviations
The following abbreviations are used in this manuscript:
Author Contributions
Methodology, K.K.; software, K.K.; testing, K.K. and M.R.O.; validation, M.R.O.; investigation, K.K.; writing–original draft preparation, K.K.; writing–review and editing, M.R.O.; visualization, K.K.; supervision, M.R.O.; project administration, K.K.; funding acquisition, K.K. and M.R.O. All authors have read and agreed to the published version of the manuscript.
This work has been supported by the AGH University of Science and Technology research Grant No 16.16.120.773.
Conflicts of Interest
The authors declare no conflict of interest.
Help | Advanced Search
Computer Science > Cryptography and Security
Title: steganography of steganographic networks.
Abstract: Steganography is a technique for covert communication between two parties. With the rapid development of deep neural networks (DNN), more and more steganographic networks are proposed recently, which are shown to be promising to achieve good performance. Unlike the traditional handcrafted steganographic tools, a steganographic network is relatively large in size. It raises concerns on how to covertly transmit the steganographic network in public channels, which is a crucial stage in the pipeline of steganography in real world applications. To address such an issue, we propose a novel scheme for steganography of steganographic networks in this paper. Unlike the existing steganographic schemes which focus on the subtle modification of the cover data to accommodate the secrets. We propose to disguise a steganographic network (termed as the secret DNN model) into a stego DNN model which performs an ordinary machine learning task (termed as the stego task). During the model disguising, we select and tune a subset of filters in the secret DNN model to preserve its function on the secret task, where the remaining filters are reactivated according to a partial optimization strategy to disguise the whole secret DNN model into a stego DNN model. The secret DNN model can be recovered from the stego DNN model when needed. Various experiments have been conducted to demonstrate the advantage of our proposed method for covert communication of steganographic networks as well as general DNN models.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
- Business & Technology
FortiGuard Labs Threat Research
- Industry Trends
- Customer Stories
- PSIRT Blogs
- CISO Collective
Byakugan – The Malware Behind a Phishing Attack
Affected Platforms: Microsoft Windows Impacted Users: Microsoft Windows Impact: The stolen information can be used for future attack Severity Level: High
In January 2024, FortiGuard Labs collected a PDF file written in Portuguese that distributes a multi-functional malware known as Byakugan. While investigating this campaign, a report about it was published. Therefore, this report will only provide a brief analysis of the overlap between that attack and this and focus primarily on the details of the infostealer.
Infection Vector

The PDF image shows a blurred table and asks the victim to click the malicious link on the PDF file to see the content. Once the link is clicked, a downloader is downloaded. The downloader drops a copy of itself (require.exe) along with a clean installer to the temp folder. It then downloads a DLL (dynamic link library), which is executed via DLL-hijacking to run require.exe to download the main module (chrome.exe). It executes the downloader's copy (require.exe), not the downloader (Reader_Install_Setup.exe), because when the downloader is named "require.exe" and located in the temp folder, its behavior is different from when it is Reader_Install_Setup.exe.

The downloader downloads Byakugan’s main module from thinkforce[.]com[.]br. This is the C2 server from which Byakugan receives files and commands. However, it may also work as the attacker's control panel. There is a login page on port 8080. We found descriptions of its features from the page's source code.

Byakugan is a node.js-based malware packed into its executable by pkg. In addition to the main script, there are several libraries corresponding to features.

Additionally, Byakugan can download extra files to perform its functions. These are stored in the default base path, % APPDATA%ChromeApplication, which is also used to store data created by Byakugan.
Byakugan has the following features:
- Screen monitor Lib: streamer.js It uses OBS Studio to monitor the victim’s desktop.

In a previous variant (7435f11e41735736ea95e0c8a66e15014ee238c3a746c0f5b3d4faf4d05215af), Byakugan downloaded the software from its domain. But this is not seen in this newer variant.
- Screen capture Lib: api.js Takes screenshots using Windows APIs.

- Miner Lib: miner.js The attacker can decide whether or not to continue mining when the victim is playing highly demanding games, which can impact performance. The attacker can also choose between mining with a CPU or a GPU to prevent the system from overloading. It downloads a variety of famous miners, such as Xmrig, t-rex, and NBMiner, and stores them in a folder named MicrosoftEdge under the base path.

- Keylogger Lib: api.js The keylogger stores its data in the kl folder located under the default path.

- File manipulation Lib: files.js This provides the functions for file uploading and exploring.

- Browser information stealer Lib: Browser.js Byakugan can steal information about cookies, credit cards, downloads, and auto-filled profiles. The data is stored in the bwdat folder under the base path. It can also inject cookies into a specified browser.
In addition, there are some features that help Byakugan live as long as possible:
- Anti-analysis If the file name is not chrome.exe or is not located in the ChromeApplication folder, it will pretend to be a memory manager and close itself.

In addition, it sets the path it uses to the Windows Defender’s exclusion path and allows files in the Windows firewall.
- Persistence It drops a configuration file for the task scheduler into the Defender folder under the base path, which makes it execute automatically when starting up.

There is a growing trend to use both clean and malicious components in malware, and Byakugan is no exception. This approach increases the amount of noise generated during analysis, making accurate detections more difficult. However, the downloaded files provided critical details about how Byakugan works, which helped us analyze the malicious modules. FortiGuard Labs will continue to monitor this malware and provide updates on this variant as they become available.
Fortinet Protections
The malware described in this report is detected and blocked by FortiGuard Antivirus as:
W64/BKGStealer.854C!tr W64/BKGStealer.4C6A!tr W64/BKGStealer.47AF!tr PDF/TrojanDownloader.Agent.BKN!tr
FortiGate, FortiMail, FortiClient, and FortiEDR support the FortiGuard AntiVirus service. The FortiGuard AntiVirus engine is part of each of these solutions. As a result, customers who have these products with up-to-date protections are protected.
The FortiGuard CDR (content disarm and reconstruction) service can disarm the malicious macros in the document.
We also suggest that organizations go through Fortinet’s free NSE training module: NSE 1 – Information Security Awareness. This module is designed to help end users learn how to identify and protect themselves from phishing attacks.
FortiGuard IP Reputation and Anti-Botnet Security Service proactively block these attacks by aggregating malicious source IP data from the Fortinet distributed network of threat sensors, CERTs, MITRE, cooperative competitors, and other global sources that collaborate to provide up-to-date threat intelligence about hostile sources.
If you believe this or any other cybersecurity threat has impacted your organization, please contact our Global FortiGuard Incident Response Team.
Git repository
github[.]com/thomasdev33k github[.]com/fefifojs github[.]com/wonderreader
blamefade.com[.]br thinkforce.com[.]br
c7dbb5e9e65a221a5f78328b5a6141dd46a0459b88248e84de345b2a6e52b1d9 c6fe9169764301cadccb252fbed218a1a997922f0df31d3e813b4fe2a3e6326d c9a27dbae96afb7d083577d30b2947c8ba9d1a6cb7e10e5f259f0929ef107882
9ef9bbfce214ee10a2e563e56fb6486161c2a623cd91bb5be055f5745edd6479 4d8eac070b6b95f61055b96fb6567a477dbc335ef163c10514c864d9913d23cb 30991c9cac5f4c5c4f382f89055c3b5e9bb373c98ce6a5516d06db3f8a478554
malware analysis , phishing
Related Posts
Phishing campaign delivering three fileless malware: avemariarat / bitrat / pandorahvnc – part ii, new variant of qakbot being spread by html file attached to phishing emails, delivery of malware: a look at phishing campaigns in q3 2022, news & articles.
- News Releases
- News Articles
Security Research
- Threat Research
- FortiGuard Labs
- Ransomware Prevention
Connect With Us
- Fortinet Community
- Partner Portal
- Investor Relations
- Product Certifications
- Industry Awards
- Social Responsibility
- CyberGlossary
- Blog Sitemap
- (866) 868-3678
Copyright © 2024 Fortinet, Inc. All Rights Reserved

Double layer security using crypto-stego techniques: a comprehensive review
- Review Paper
- Published: 13 October 2021
- Volume 12 , pages 9–31, ( 2022 )
Cite this article
- Aiman Jan 1 ,
- Shabir A. Parah ORCID: orcid.org/0000-0001-5983-0912 1 ,
- Muzamil Hussan 1 &
- Bilal A. Malik 2
5014 Accesses
8 Citations
Explore all metrics
Recent advancement in the digital technology and internet has facilitated usage of multimedia objects for data communication. However, interchanging information through the internet raises several security concerns and needs to be addressed. Image steganography has gained huge attention from researchers for data security. Image steganography secures the data by imperceptibly embedding data bits into image pixels with a lesser probability of detection. Additionally, the encryption of data before embedding provides double-layer protection from the potential eavesdropper. Several steganography and cryptographic approaches have been developed so far to ensure data safety during transmission over a network. The purpose of this work is to succinctly review recent progress in the area of information security utilizing combination of cryptography and steganography (crypto-stego) methods for ensuring double layer security for covert communication. The paper highlights the pros and cons of the existing image steganography techniques and crypto-stego methods. Further, a detailed description of commonly using evaluations parameters for both steganography and cryptography, are given in this paper. Overall, this work is an attempt to create a better understanding of image steganography and its coupling with the encryption methods for developing state of art double layer security crypto-stego systems.
Similar content being viewed by others

Research Review on Digital Image Steganography Which Resists Against Compression

Coalescing Image Steganography and Cryptography for Information Security

A Study on Integrating Crypto-Stego Techniques to Minimize the Distortion
Avoid common mistakes on your manuscript.
1 Introduction
The increasing bandwidth and data rates of 4G/5G cellular technology and optical fiber communication revolutionized data communication. The exchange of data in form of text, images, audio, and video over the internet has become ubiquitous [ 1 ]. The multimedia data is being exchanged by governments, law enforcement agencies, and for telemedicine by the hospitals [ 2 ]. During the covid-19 worldwide lockdown traffic of information over the internet saw an upsurge. Although internet usage has various advantages, but security and privacy of data still remain a challenge [ 3 ]. Data thefts, modifications, and alterations have become possible due to the availability of various tools in the hands of hackers. Thus, the security of data has become a challenging task of paramount importance for researchers [ 4 ]. Various information protecting mechanisms like, cryptography and data hiding methods as shown in Fig. 1 , have been put forward to address data security issues [ 5 ]. Cryptography scrambles and converts the secret data into an unreadable form for an unauthorized person [ 6 , 7 ]. Cryptography can be performed either with standard encryption techniques or Chaos based encryption techniques [ 8 ]. There are various standard encryption techniques (SET), like Data Encryption Standard (DES), Advanced Encryption Standard (AES), and Rivest Shamir Adleman algorithm (RSA), etc. [ 9 ]. In these approaches, the secret key is used to encrypt the important data before embedding [ 10 ]. However, the bulk of data with key lengths is the main limitation of the SETs which makes them insecure and less reliable for data encryption [ 11 ]. The limitation of SETs has been overcome by the chaos based encryption approaches. Chaos encryption approach uses initial keys for encryption that are sensitive to the changes made [ 12 ]. Thus, the chaos-based encryption approaches are more secure cryptographic method to ensure security to the data [ 13 ]. Cryptography can provide the considerable security to the data by changes the form of the original data through encryption. But, cryptography alone cannot resist security attacks, as its encrypted form attract attacker’s attention and hence can be modified or hacked. However, it is an insufficient method to provide data security as its encrypted form may draw the attention of an eavesdropper [ 14 ]. Hence, data hiding has been used widely by researchers to hide the existence of important data without being noticed by an intruder [ 15 , 16 , 17 ].
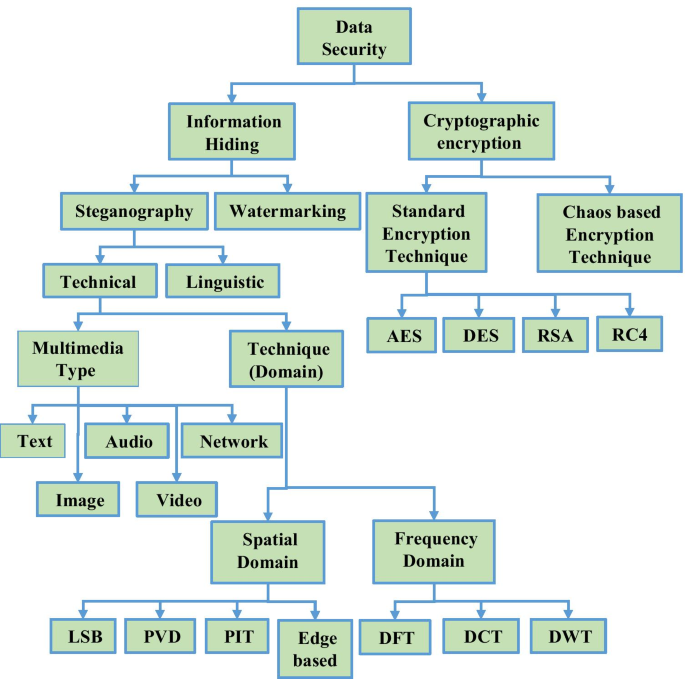
Different Information Protecting Mechanisms
Data hiding can be divided into two methods: steganography and watermarking [ 18 ]. Watermarking is the method of verifying the authenticity of multimedia (image, video, or audio) for copyright protection [ 19 ]. It can be either visible or invisible watermarking to authenticate the ownership. Steganography is the art of hiding important data into any multimedia for secret communication [ 20 ]. It is an invisible process in which detection of data is not easy. Steganography can be separated into two categories: Technical and Linguistic steganography approaches [ 21 ]. Technical steganography can be further subdivided into two sections based on the multimedia used and the technique applied. Steganography technique has various advantages associated with it, the only difficulty of it is to maintain the image quality with a good amount of payload [ 22 ]. Huge secret data size degrades the quality of an image that can suspect the presence of data [ 23 ]. And, if the eavesdropper detects the steganographic method, it can easily recover the data. So, with the concealing approach, data should be preprocessed by including some cryptographic approaches [ 24 ]. Hence, the present trend is of crypto-stego mechanism in which along with steganography, cryptography method is included to provide double layer security to the data as shown in Fig. 2 .
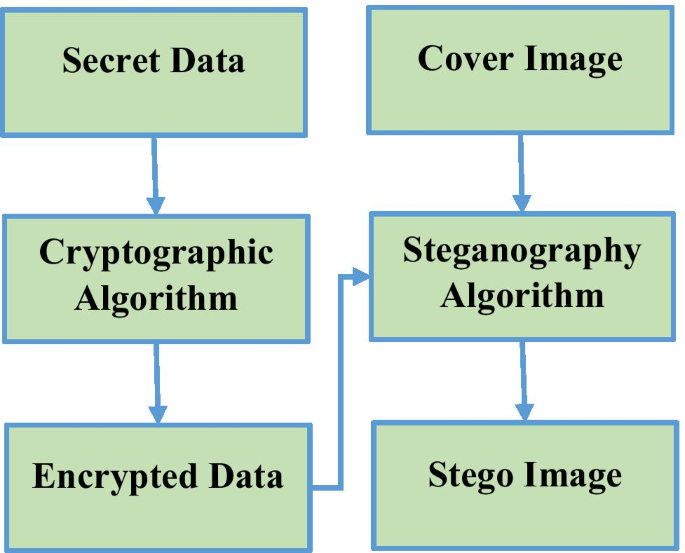
General Steganography approach together with Cryptography (Crypto-Stego)
PSNR value of existing method for 0–2 bpp embedding capacity
PSNR value of exisitng method for 2–6 bpp embedding capacity
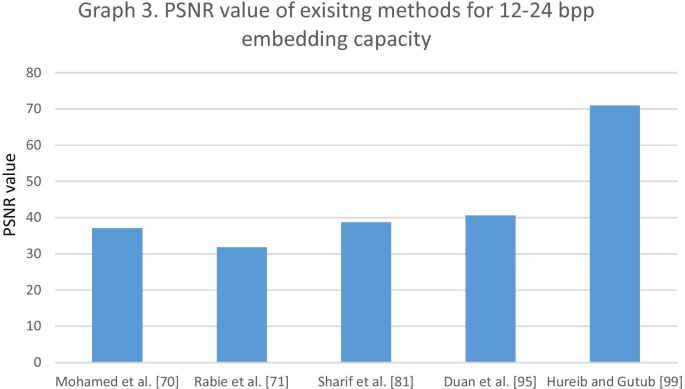
PSNR value of exisitng methods for 12–24 bpp embedding capacity
In this paper, the most recent literature in the area of steganography and crypto-stego has been reviewed to facilitate an exhaustive reference for further research in this area. This paper further discusses the various state-of-art techniques, their limitations, and challenges. The analysis parameters have been also discussed. The main contributions of this paper is:
A comprehensive review of various image crypto-stego methods has been presented.
Various parameters for evaluation of crypto-stego schemes have been presented.
A deep insight into double layer schemes and future research directions have been presented.
The rest of the paper is organized as follows. Section 2 includes the literature survey. Evaluation parameters are discussed in Sect. 3 . Section 4 comprises the directions and future research directions. The paper concludes in Sect. 5 .
2 Literature survey
Steganography is the art of concealing data into any multimedia for covert communication [ 25 ]. Steganography can be divided into many types based on the cover object used to attain security, like text, image, audio, video, and network [ 26 , 27 , 28 , 29 , 30 , 31 ]. Further, the steganography can be divided into two domains based on the techniques used to hide data in any multimedia, i.e., spatial domain technique and frequency domain technique [ 32 ]. Special domain can be further subdivided into various versions, like least significant bit (LSB), pixel value differencing (PVD), pixel indicator technique (PIT), Edge based technique [ 33 ]. Frequency domain can be also subdivided into different types, like discrete fourier transform (DFT), discrete cosine transform (DCT), discrete wavelet transform (DWT) [ 34 ]. In this section, the existing literature on different steganographic techniques and crypto-stego has been discussed. The paper focuses on an analysis of publications in reputed journals from 2016–2021 to be taken into consideration for future work. The various steganography data hiding technique and its coupling with cryptographic approaches have been discussed in the subsequent sections. Incorporating cryptography with the steganographic approach provides better security to the data, therefore using the steganography technique alone is ‘less secure’ compare to the combined approach. As once the steganographic pattern gets revealed to the unintended user, the secret data is prone to hacks and modifications.
2.1 Spatial domain technique
A detailed description of the spatial domain based image steganography techniques has been presented. Table 1 highlights the pros and cons of the reviewed spatial domain techniques.
In 2021, AbdelRaouf [ 35 ] has proposed a novel image steganographic data hiding method. The method has used the adaptive least significant bit (LSB) method for hiding information into every color channel of an image. The method has a huge payload but takes more time for embedding data into an image. Although the technique shows considerable image quality values, however, the proposed method can be improved by introducing an encryption method before embedding to improve security. In 2021, Hussain et al. [ 36 ] have put forth an enhanced adaptive data hiding approach in which the least significant bit (LSB) and pixel value differencing (PVD) methods have been used for increasing hiding space. The method has good imperceptibility and embedding capacity. The proposed approach has focused only on payload and imperceptivity. The technique can be improved in the security domain by incorporating an encryption algorithm. In 2020, Sahu and Swain [ 37 ] have suggested Dual-layer based reversible image steganography using modified least significant bit (LSB) matching. In this approach double layer embedding has been performed to improve image quality. In the first layer, two bits of the secret data are embedded into each pixel using modified LSB matching to develop intermediate pixel pair (IPP). Whereas, in the second layer, four bits of secret information are embedded using IPP. The technique is good enough to provide a good payload with better image imperceptivity. The proposed approach can be enriched by introducing security algorithms to enhance the security of the data embedded in an image. Also, the proposed method can be extended to color images and can be improved to reduce processing time. In 2017, Hussain et al. [ 38 ] have presented a data hiding method to achieve high payload, good visual quality, and maintain security. This method is based on two novel approaches: parity-bit pixel value difference (PBPVT) and improved rightmost digit replacement (iRMDR). In this method, the cover image is separated into two non-overlapping pixel blocks. The embedding algorithm PBPVD (higher level ranges) or iRMDR (lower level ranges) are selected according to the difference value between two pixels in each block. The PBPVD technique increases embedding capacity and iRMDR attains good visual imperceptivity. However, the method can be improved by establishing a security related algorithm to improve the reliability of the method against attacks. Further, the scheme can be extended for color images also.
In 2018, Malik et al. [ 39 ] have come-up with a new data hiding approach using absolute moment block truncation coding (AMBTC) compression. In this method, AMBTC compresses the cover image to embed important data into the compressed pixel values. The method is able to maintain image quality with a good payload. However, security can be improved by incorporating cryptographic approaches. In 2019, Kumar et al. [ 40 ] have proposed an enhanced method of data hiding using absolute moment block truncation coding (AMBTC) using pixel value differencing (PVD) and hamming distance. The cover image is compressed with AMBTC and is divided into three sections: smooth, less-complex, and highly-complex blocks. One bit per pixel is embedded into smooth blocks, 8-bits are embedded into a less-complex block using hamming distance calculation, and more data bits are embedded into a highly-complex block using the PVD technique. The method produces a good embedding space. However, can be extended in the security domain to further increase security to the data.
In 2020, Chakraborty and Jalal [ 41 ] have put forth a novel image hiding method using local binary pattern (LBP). In this scheme, the cover image is separated into 3 × 3 non-overlapping blocks. The reference pixel of each block is encoded using LBP. The encoded image is XORed with the secret image. The image has been shuffled further to embed secret image bits in the LSB of the cover image. The method has strong statistical features against attacks. The presented method can be further extended to embed data by applying payload-specific hand-crafted descriptors. In 2020, Lin et al. [ 42 ] have proposed a new image hiding method for Dynamic GIF (Graphics Interchange Format) images. The presented scheme is based on the Palette sort. In this method, the cover image is decomposed into frames (static GIF image). A new distortion function is applied to all frames. The data is then embedded into these frames to form the stego frames. In this technique, the data is secured by hiding it into an image but with less payload. In 2018, Parah et al. [ 43 ] have presented computationally efficient and reversible data hiding method for secure electronic health record (EHR) communication. In this method, modular arithmetic has been used for embedding EHR into a medical image. Prior to embedding, the cover medical image is scaled up using the pixel reputation method. The proposed scheme has improved image quality with a better amount of payload but takes a good amount of time for embedding data into an image. The security of the method can be improved by implementing some encryption method. The technique can also be extended to color images to increase EHR embedding capacity.
In 2021, Li et al. [ 44 ] have suggested a high capacity image steganography technique. The method has used retracing extended Sudoku (RE-Sudoku) reference matrix for data embedding. The paper has an enhanced payload with good image quality. The method can be improved in security domain to enhance its superiority. Also, the method can be analyzed on color images to show its generality. In 2020, Saha et al. [ 45 ] have come up with a new image hiding method using a hashed-weightage Array. The method is based on extended exploiting modification direction (EMD) that creates less distortion in an image. The presented method has improved payload and reduces distortion of an image than the existing method. The security of proposed scheme can be enhanced by encrypting the secret data. In 2018, Shen et al. [ 46 ] have proposed a new data hiding method based on improved exploiting modification direction (EMD) and interpolation techniques with consideration of human visual system (HVS). In this scheme, the cover image is separated into various 3 × 3 non-overlapping blocks. The presented method hides data into each block by calculating the neighbor mean value and the difference value. The discussed method has improved embedding efficiency and quality than the traditional EMD technique. The presented method takes more time for processing the task. The scheme can be enriched by applying stegna-analysis resist method to improve security. Moreover, the technique can be improved by applying it to color images as well.
In 2016, Bairagi et al. [ 47 ] have put forth an efficient image steganography method for secure communication in the Internet of Things (IoT) infrastructure. This article has presented three information hiding approaches using RGB image steganography. In this method, data has been embedded in an image using a secret key and carrier information. The technique has improved the security of the data than the traditional steganographic techniques. This work can be enhanced by applying encryption approaches for security improvement. In 2020, Rim et al. [ 48 ] have presented a Beta chaotic map based image hiding method. The method used a Beta chaotic map to sort the embedding positions of an image. The simple least significant bit (LSB) technique has been used to embed data into an image. The technique has provided good security to the data than the traditional steganographic approaches. However, the method can be improved to gain more capacity with good image quality. In 2021, Hassan and Gutub [ 49 ] have introduced an efficient image reversible data hiding (RDH) approach. In this method, interpolation optimization has been used to scale up the original image before embedding. The advantage of this method is a good image quality with a huge payload. However, the cryptographic technique can be applied to the secret data before embedding to enhance security.
2.2 Edge based technique
This subsection discusses different edge-based image steganography methods. Table 2 highlights the pros and cons of these techniques after analyzing the surveyed papers.
In 2021, Atta and Ghanbari [ 50 ] have put forth a new data hiding mechanism based on dual tree complex wavelet transform (DT-CWT). In this method, the cover image has been divided into subbands and neutrosophic edge detector (NSED) has been applied on these subbands to attain edge areas. The secret data is embedded into the detected subband edge regions of an image. The method has been able to get good imperceptivity with a good amount of payload. However, needs to secure data by applying some encryption algorithms. In 2019, Dhargupta et al. [ 51 ] have proposed an image steganography approach using Fuzzy edge detection (FED). In this approach, edges of the cover image are detected by FED to embed data into edge areas of an image. Data to be embedded in an edge region depends upon the Euclidean distance and is determined by the Gaussian function. The technique shows good embedding capacity, but with an increase in payload, its quality gets degraded. The method has been applied only on grayscale images. In 2019, Ahmadian and Amirmazlaghani [ 52 ] have suggested a secret image sharing steganography scheme. This method is dependent on fully exploiting modification direction (FEMD) and edge detection technique to embed data into the cover image. The method has been able to improve image quality than the existing methods, but, has less embedding space. In 2018, Kich et al. [ 53 ] have offered an edge detection method based image steganography method. In this approach, secret information has been dissimulated into edge pixels of an image using modified simple linear iterative clustering (M-SLIC) algorithm. The technique has a good payload, robustness, and imperceptivity. However, the scheme can be also upgraded in the security domain. In 2018, He et al. [ 54 ] have suggested a reversible information hiding method using edge information. The method has been proposed for high dynamic range (HDR) color images. The data has been embedded into HDR color images by using edge information. The approach has achieved less visual distortion after embedding secret data into an image. However, the security of the data by preprocessing has not been considered to increase data security. In 2018, Gaurav and Ghanekar [ 55 ] have introduced an edge region detection based image steganography technique. The secret data has been embedded into the least significant bit (LSB) bits of edge pixels. The approach has good image quality with a better payload. However, can be improved to insert a cryptographic approach along with a steganographic method to ensure better security to the data. In 2020, Prasad and Pal [ 56 ] have introduced a new image steganography algorithm, using edge detector and modulus function. For embedding, the modulus function has been used, whereas, edge detector has been used to find edge locations to embed data into edge areas. The method has been tested only on greyscale images. Further, the technique can be improved by introducing an encryption algorithm to increase security.
In 2019, Mukherjee and Sanyal [ 57 ] have presented an edge based image steganography method with a variable threshold. The edges of an image have been detected by the Sobel edge detector with respect to the threshold key. These detected regions are used to hide secret information. The scheme has gained good image quality with considerable hidden data capacity. The suggested method can be further improved by incorporating encryption schemes to the embedding data before hiding. In 2018, Kadhim et al. [ 58 ] have put forth an adaptive image steganography technique. The technique is based on edge detection over dual-tree complex wavelet transform (DT-CWT). Edge regions of an image have been detected using the canny edge detection method. Even though the method has good embedding capacity and image quality, however, can be extended in the security domain to increase data security against attacks. In 2018, Ghosal et al. [ 59 ] have put forth an image steganography technique based on the Laplacian of Gaussian (LoG) edge detector. In this approach, the data has been embedded into all non-edge pair, edge pair and mixed pair of an image. By this technique, the burden of payload into the traditional method of embedding all data into edge areas only has been reduced. The method no doubt has increased payload and image quality. However, the technique can be further enhanced in the security domain. In 2021, Ghosal et al. [ 60 ] have suggested an image hiding approach based on the Kirsch edge detector. In this method, the data has been embedded into both edge and non-edge regions of an image in such a way that image distortion is minimized. The method has improved payload with less image distortion. The proposed method can be improved by applying a cryptographic method to enhance security. In 2019, Banik et al. [ 61 ] have discussed an image steganography method for embedding capacity improvement. The technique has used Kirsch detector to find the edge regions of an image for data hiding. The threshold value has been used as a key to embed data into edge areas of an image. The technique has good image quality with a good payload. The algorithm has been implemented only on greyscale images. Thus, the method can be extended to color images as well. In 2020, Wang et al. [ 62 ] have presented a high capacity hybrid steganography method based on the least significant bit (LSB) and hamming code (HLAH). In this technique, the color cover image is separated into 9 × 9 blocks and the red (R) plane is extracted. The LSB of the R plane is set to ‘0’ and then the canny edge detection technique is used to find the edges of a plane. The method has used the canny edge detection technique to find edges. The data is embedded into the non-edge and edge regions using LSB and (3,1) hamming code. The method has been able to provide a good payload with better image quality than the existing methods. However, the security of the algorithm can be improved by encrypting the secret data prior to embedding.
In 2020. Tripathy and Srivastava [ 63 ] have proposed an edge based data hiding technique using Modulus-3 strategy and comparative analysis. In this method, the data has been changed into ternary data and has been embedded into edge areas of an image using the Modulus-3 strategy. The edge regions have been detected with Sobel, Prewitt, Canny, and Laplacian edge detectors. The method has been able to hide a vast amount of data into an image with good visual image quality. However, the security of the secret data can be further improved by introducing an encryption method along with the proposed algorithm. In 2019, Tuncer and Sonmez [ 64 ] have introduced the image steganography algorithms based on edge detectors and a 2 k correction scheme. The method has used Sobel, Canny, Laplacian of Gaussian (LoG), block based edge detection (BED), and hybrid edge detectors (HED) to find edge pixels of an image. These detected regions have been used to embed data into it using the least significant method (LSB) and 2 k correction method. The technique has the good capacity with good visual quality, but, has not improved much upon security parameter.
2.3 Frequency domain technique
A thorough summary of the techniques reviewed under the frequency domain is given as follows and their pros and cons are pointed out in Table 3 .
In 2021, Abdel-Aziz et al. [ 65 ] have offered an improved data hiding method for securing color images. In this work, the authors have used a hyper chaotic map and left-most significant bit (LMSB) embedding method to embed data into an image. In this approach, the cover image has been first encrypted using a hyper chaotic map to form the encrypted image and is then converted into the YCbCr channels. Of them, the first channel (Y) has been divided into non-overlapping blocks using the DCT technique. The resulted blocks are quantized and secret data has been embedded into frequency coefficients of these quantized discrete cosine transform (DCT) blocks using Huffman coding. The output stego image is further XORed with the remaining two channels (CbCr) to form the encrypted stego image. The scheme has good security and image quality. However, an encrypted form of stego image can suspect the presence of data. Also, the technique can be extended for embedding any type of data into color images. In 2021, Yao et al. [ 66 ] have presented a reversible data hiding (RDH) approach for dual JPEG images. In this method, the cover image is preprocessed to attain DCT coefficients and to ascribe embedding space. Then, secret data has been embedded into obtained frequency coefficients of image pixels using the dual-JPEG RDH scheme. The technique has gained a considerable embedding space with good visual image quality. However, the secret data to be embedded has not been preprocessed to improve data security. In 2018, Liu and Chang [ 67 ] have suggested a reversible data hiding (RDH) technique for JPEG images for hiding a great amount of data. In this approach, the discrete cosine transform (DCT) technique has been used to gain the coefficient values for non-overlapping 8 × 8 blocks. The quantization method has been applied to each block of an image to attain JPEG quantized block. Then, the AC coefficients are scanned in a zigzag direction to embed secret data into non-zero elements. The proposed method has been able to gain good image quality with considerable payload, but, the enhancement of security to the data with preprocessing has not been taken into consideration. In 2018, Attaby et al. [ 68 ] have put forth a novel data hiding approach using discrete cosine transform (DCT) to embed data into JPEG images. The difference value of two DCT coefficients using modulus 3 has been applied to insert two secret data bits into the values of the coefficients of an image. This significantly reduces the image distortion with improvement in image embedding space. However, the data security of the scheme can be improved by applying a cryptography approach to secret information before embedding. In 2016, El-Rahman [ 69 ] has given a new steganographic tool to hide data into the frequency domain of an image using the discrete cosine transform (DCT) method. The technique has hidden the important information about nuclear reactor in the middle frequency. The scheme is able to protect image quality with a high considerable amount of embedding capacity. However, the confidential information of the nuclear reactor needs to be more secure from any thefts. Therefore, encryption of important information before embedding could be more effective for data security. In 2020, Mohamed et al. [ 70 ] have presented an L*a*b* (luminance channel ‘L*’ and chrominance channels ‘a*and b*’) color space image steganography technique using quad-trees. The method has applied the quad-tree of the gray-scaled cover to the RGB of the cover image. The resultant blocks of the quad-tree are transformed to L*a*b* color space using 2dimentional-discrete cosine transform (2D-DCT) to embed data into the largest zero areas of DCT. The method has considerable embedding capacity, good image quality, and secure than the existing spatial and frequency domain steganography methods. However, the technique is complex. In 2018, Rabie et al. [ 71 ] have suggested increased embedding space and image quality data hiding scheme based on transform domain mechanism. The presented scheme uses the quad tree segmentation method to divide the blocks of the cover image. In each block, quantization step and piecewise linear curve fitting are used to hide secret data in the least significant areas of discrete cosine transform (DCT) coefficient areas. The method has tried to gain a better image payload. However, the data is embedded directly without pre-processing that may lead to security issues. In 2017, Saidi et al. [ 72 ] have put forth a new steganographic approach Based on discrete cosine transform (DCT) and chaotic map. The presented approach is used to find coefficients of the cover image. Piecewise linear chaotic map (PWLCM) has been used to scramble embedding positions to improve security to the embedding data. The algorithm has a good payload, however, the technique has poor image imperceptivity. Also, the technique can be improved further to resist any statistical attacks.
In 2018, Nipanikar et al. [ 73 ] have discussed a sparse representation based image steganography technique using particle swarm optimization (PSO) and discrete wavelet transform (DWT) approaches. These approaches have been used to locate the appropriate pixels for embedding speech signal in the cover image. The method is able to achieve good image imperceptibility and payload. However, the algorithm can be extended in the security domain to enhance data security. In 2018, Nevriyanto et al. [ 74 ] have presented an image steganography method using discrete wavelet transform (DWT) and singular value decomposition (SVD) techniques. In this scheme, a text file has been converted into an image to form a watermark for embedding it into an image. The secret watermark has been embedded into the frequency coefficients of an image using the SVD method. The method can be further made secure enough against attacks by incorporating encryption methods on the data and can be also extended to color images. In 2018, Miri and Faez [ 75 ] have introduced an image steganography technique for hiding important data into frequency coefficients of an image. This method has used the integer wavelet transform (IWT) method to obtain the frequency coefficients of an image. The method has been analyzed on greyscale images that can be extended to color images. The security of the data can be further improved by introducing encryption methods to the secret data before embedding. In 2019, Kalita et al. [ 76 ] have proposed a new steganography method using integer wavelet transform (IWT) and the least significant bit (LSB) substitution method. To estimate the embedding capacity, the coefficient value differencing method has been applied. The scheme has good visual quality of an image and considerable embedding capacity. However, the data can be secured from statistical attacks by introducing encryption algorithms. In 2021, Ghosal et al. [ 77 ] have presented exploiting Laguerre transform (LT) based image hiding method. In this scheme, the cover is separated into m-pixel non-overlapping groups. Each pixel of these groups is then transformed into its equivalent coefficients using LT. The secret data is embedded into these coefficients. The resulted pixels are adjected to minimize distortion and have been recomputed by applying inverse LT (ILT). The presented scheme has been able to increase payload with good image quality but takes more time for completing the process. However, the method can be secured by encrypting the data. In 2019, Ma et al. [ 78 ] have come up with a new reversible data hiding (RDH) approach for medical images. The method is based on block classification and code division multiplexing (CDM). In this scheme, the non-overlapping blocks of the medical image are categorized into smooth and texture groups by calculating mean square error (MSE). The secret information has been embedded into transformed frequency coefficients using the integer-to-integer discrete wavelet transform (IDWT) technique of the texture block. The method has large data hiding capacity with good image imperceptibly. Security to the secret data can be further improved by applying cryptography approaches to the secret data prior to embedding. In 2020, Murugan and Subramaniyam [ 79 ] have proposed an image steganography technique to ensure the data security transaction over an insecure network. The data has been embedded into coefficient values of an image using the alpha factor. The image pixels have been transformed with the 2dimentional-Haar discrete wavelet transform (2D-Haar DWT) to gain four sub-bands. The method has good embedding space while preserving image quality than the existing schemes. Also, the proposed method is secure than already existing frequency domain techniques. However, the proposed method is complex.
2.4 Joint Crypto-stego schemes
This subsection includes the reviewed papers of different dual security image steganography techniques. These techniques have encrypted the secret data/ secret image with either standard encryption method or chaotic method before embedding to provide double layer security to the secret data. The pros and cons of different dual security image steganography methods are shown in Table 4 . The following subsections discuss the different combined image steganography and encryption techniques.
Simple domain crypto-stego schemes
The review of different special domain based image steganography and encryption methods are explained below:
In 2021, Maji et al. [ 80 ] have presented a spatial domain based image steganography method in which higher order pixel bits have been used to embed data. To encrypt data, XOR operation has been used to enhance security. Since the method has been implemented on the greyscale image. Thus, the presented approach can be extended to color images to prove its generality. In 2017, Sharif et al. [ 81 ] have presented an image steganography technique based on a 3-dimensional chaotic map. In this method, the pixel position for embedding changes with the change in the cover image. Thus, makes the system secure against any statistical attacks. However, the method can be improved in terms of complexity. In 2020, Gambhir and Mandal [ 82 ] have proposed chaos based least significant bit (CLSB) steganography method. The technique has used logistic map chaotic function to develop random numbers. The scheme shows good security and image quality results. However, can be improved further to increase embedding space to hide huge data into an image. In 2019, Prasad and Pal [ 83 ] have proposed logistic map based image steganography. This method has used the least significant bit (LSB) and pixel value differencing (PVD) techniques to embed data into the cover image. The embedding data is encrypted using a logistic map to improve security to the data. The proposed algorithm has attained better security. The technique can be modified in a different way to achieve better visual image quality and can be extended to color images also. In 2017, Mohammad et al. [ 84 ] have offered image steganography for visual contents authenticity. The method uses color model transformation, three-level encryption algorithm (TLEA), Morton scanning (MS). The data has been embedded with the direct least significant bit (LSB) substitution method using MS. TLEA has been used to encrypt data. The scheme provides the best algorithm for visual content authenticity in social networks. While the technique is complex and has less payload. In 2019, Alotaibi et al. [ 85 ] have proposed a secure framework for safe data transmission in mobile devices using hash, cryptography, and steganography. The proposed method has used a hash function for storing the secret password, cryptography with AES method for encrypting password, and LSB method for hiding encrypted password into an image. The method is able to provide a considerable amount of payload but has low visual quality of an image. In 2021, Mathivanan and Balaji [ 86 ] have suggested a QR code based color image stego-crypto technique. The method uses dynamic bit replacement and logistic map for embedding and encryption respectively. In this approach, the secret data is converted into 2D binary using base64 encoding method and QR code generator and is then embedded into an image using dynamic bit replacement technique. The image is then scrambled using a logistic map. The method is secure against differential attacks but is able to hide a low amount of secret data. In 2021, Abdelwahab et al. [ 87 ] have put forth an efficient image steganography technique to hide data for safe data transmission. In this scheme, plain text is encrypted using the RSA method and is embedded into the YCbCr components of an image using the LSB approach. The resulted stego image is then compressed using Huffman coding, Run Length coding (RLC), or DWT to form compressed stego image. The method has good amount of payload with considerable image quality. However, the scheme is complex.
Edge based crypto-stego techniques
Few edge detections based image steganography techniques along with data encrypting approaches are discussed as under:
In 2021, Parah et al. [ 88 ] have presented efficient security, high payload, and reversible electronic health record (EHR) data hiding approach. In this method, the cover image is scaled up with the pixel reputation method (PRM) and then the boundary conditions are applied to the image. The resulted image is divided into 2 × 2 blocks to embed data first into counter diagonal pixels and then to the main diagonal pixel after checksum computation. The EHR is secured by adding a watermark and applying the RC4 encryption method. The encrypted data is divided into 3-bit chunks and has been then embedded into the pixels after applying the left data mapping (LDM) method. The scheme has increased security to the data and has authenticated its originality. However, with a high payload, the quality of an image can be enhanced by testing the method to color images also. In 2016, Parah et al. [ 89 ] have proposed a new information hiding technique based on a hybrid edge detection method. In this scheme, the color image is separated into three planes (red, green, blue). The data is embedded into edge regions and non-edge regions of green and blue planes by making use of a hybrid edge detector. Whereas, the red plane is used to hold the bit status of green and blue planes. In order to authenticate and detect tempering the data, a fragile watermark is embedded. Before embedding, the secret information is encrypted using the RC4 algorithm. The algorithm is able to increase capacity with good image quality. Further, the security of the method is provided to the data by encrypting it prior to embedding. However, the time complexity of the method can be reduced by reducing the data extraction time. In 2020, Delmi et al. [ 90 ] have discussed the image hiding approach using the edge adaptive method and chaos cryptography technique. In this technique, the data has been encrypted using the Arnold Cat Map function. Whereas, the data has been embedded into the edge region of an image located by a canny edge detector. The technique although has increased security to the data. However, can be enhanced to increase payload with good image quality. In 2021, Sharma et al. [ 91 ] have suggested crypto-stego approach to prevent data from attacks. In this method, Rabin cryptosystem is used to encrypt the secret data, Arnold transform has been used to scramble the data, and the resulted data has been embedded into the edges of multiple images. The framework is able to provide better image quality with a considerable payload. However, the proposed approach is complex.
Frequency domain crypto-stego techniques
Different frequency domain based image steganography together with data encryption surveyed methods have been discussed in this subsection:
In 2016, Kaushik and Sheokand [ 92 ] have put forth a steganography scheme based on chaotic least significant bit (LSB) and discrete wavelet (DWT) approaches. In this method, the data is encrypted using a logistic map. Whereas, the encrypted data is embedded into frequency coefficients of the cover image using DWT by 3–3-2 LSB insertion scheme. The security of the proposed method has been increased by using the chaotic method. The method has good image quality but has less embedding capacity. In 2020, Panday [ 93 ] has suggested a new medical image steganography approach using a bit mask oriented generic algorithm (BMOGA). BMOGA has been used together with cryptographic features to encrypt data. In this approach, data has been embedded in the frequency coefficients of an image. Discrete wavelet transform (DWT) (1-level & 2-level) has been used to find frequency coefficients. The technique is secure and imperceptible, however, can be enhanced to gain a good payload. However, the scheme can be further modified to reduce the complexity of the algorithm. In 2018, Elhoseny et al. [ 94 ] have presented a secure medical data transmission model for internet of things (IoT) based healthcare systems. The method has used 2-D discrete wavelet transform (2D-DWT) to conceal data into both grayscale and color images. The secret information has been encrypted using a hybrid encryption scheme using advanced encryption standard (AES) and Rivest, Shamir, and Adleman (RSA) algorithms. The technique shows good image quality with good data security. However, the technique is complex.
In 2020, Duan et al. [ 95 ] have proposed a high-capacity image hiding scheme. In this method, the data have used encrypted with elliptic curve cryptography (ECC) approach. Discrete cosine transform (DCT) is applied to the secret image prior to encryption. A deep neural network has been used to increase the payload of the cover image. The method has been applied to both gray images as well as a color images. The method shows better security to the data. However, can be improved to reduce algorithm complexity. In 2018, Subhedar and Mankar [ 96 ] have presented image steganography using curvelet transform (CT) to embed secret information in the selected cover image. In order to obtain curvelet coefficients, level 6 CT has been applied to the cover image. Encryption data has been embedded into appropriate blocks by using standard deviation. Whereas, image block has been replaced with secret data block using spread spectrum when the deviation is higher than a threshold. The resulted stego image is obtained by applying inverse CT. In this technique, security has been heightened by encrypting the data using Arnold transform. However, it can be enhanced in payload and quality domain by testing it on the color image also. Further, the method is complex. In 2020, Eyssa et al. [ 97 ] have introduced an efficient image steganography method. In this approach, the data has been encrypted with the Baker map together with a discrete cosine map (DCT). The secret message in the presented method has been embedded into the values of the coefficients of an image. The security of the system has been increased. However, with a good amount of payload the image quality is less that needs to be enhanced. In 2021, Kaur and Singh [ 98 ] have introduced a new data hiding method based on discrete cosine transform (DCT) and coupled chaotic map. The secret data in this approach has been encrypted using coupled chaotic map of logistic and sine map. In this approach, the data has been embedded into the DCT coefficients of an image. The technique has a good payload, but, has been applied only on greyscale images and is complex.
Medical image crypto-stego techniques
The review of various medical image steganography together with data encryption has been discussed in this subsection:
In 2020, Hureib and Gutub [ 99 ] have proposed a combined cryptography and image steganography approach to enhance security in medical health data. In this method, Elliptic curve cryptography has been used to encrypt text before hiding. Then, the encrypted text is embedded into image pixels to hide its presence from the person who is not authorized. The technique has a good payload and image quality, however, it has not been tested for various attacks, like statistical attacks, etc. In 2020, another image steganography technique using elliptic curve cryptography has been presented [ 100 ]. The method has used 1-LSB and 2-LSB image steganography techniques to hide data into an image. The medical data has been embedded in the medical image after encrypting it with cryptography technique to improve data security. The method provides good image quality but has low embedding capacity. In 2019, Samkari and Gutub [ 101 ] have suggested a protecting mechanism for medical records against cybercrimes within the Hajj period. The method has used a 3-layer security system for medical record protection by encrypting data using hybrid cryptography method and hiding encrypted data into an image to produce stego-image for sending through the internet. The presented approach has good image quality and is safe for data transmission, however, the method is complex. In 2021, Denis and Madhubala [ 102 ] have put forth hybrid data encryption and hiding model for medical data security over cloud-based healthcare systems. In this scheme, a hybrid encryption model using AES and RSA algorithms has been used to convert the original data into an encrypted form. Whereas, the 2D-DWT and Adaptive Genetic Algorithm (AGA) based optimal adjustment method to conceal encrypted medical data into an image for safe data transmission. The proposed technique provides good image quality and is secure. However, the approach is complex and has low hiding space. In 2021, Manikandan et al. [ 103 ] have proposed an image steganography technique to secure e-health. In this approach, the secret image is first encrypted with the XOR cipher encryption and is then embedded into the cove image using LSB method. The framework has considerable image quality but provides low embedding capacity. In 2021, Ogundokum et al. [ 104 ] have presented crypto-stego medical information securing model. This technique uses international data encryption algorithm (IDEA) and Matrix-XOR techniques for enhancing security to the internet of medical things (IoMT) for the medical records protection. In this method, secret data has been encrypted using IDEA and is then embedded into carrier image using XOR. The method provides good visual quality of an image and is secure for medical data transmission. However, space for transmitting data in a concealed manner should be increased. In 2021, Prasanalakshmi et al. [ 105 ] have recommended a secure clinical data transmission technique in the internet of things (IoT) using hyperelliptic curve (HECC) and cryptography techniques. This approach has used AES and Blowfish hybrid cryptography for medical data encryption and HECC for embedding encrypted medical data into a medical image. The generated embedded image is then compressed with the 5-level DWT to attain a good payload and better security. The technique provides good image quality with considerable payload, however, the technique is complex.
From the literature, it has been observed that the use of cryptography and steganography together is able to provide double layer security to the data. Cryptography protects data from hacks, and in particular chaos based cryptography can be the better option for encryption because of its ergodicity and dependence on initial condition properties. And, incorporating a steganography approach with cryptography improves data security by concealing it into digital media. Data hiding using chaotic maps to locate and create a random sequence of pixels enhances data security. Also, concealing secret information in edge regions improves payload, can prevent cover image from noticeable distortion, and thus prevents attacks. Moreover, it has been observed that cryptography and steganography have widened their applications almost in all spheres of life, like in e-health, IoT, mobile devices, system login security, cloud, etc.
3 Evaluation parameters
Evaluation parameters are the tools used to check the efficiency, validity, and superiority of an algorithm. Outcomes of the analyzed scheme with various methods whose values lie between expected ranges prove the strength of the technique. The most common characteristics of image steganography and data encryption analysis are explained below in subsections.
3.1 Visual quality analysis
Steganography method alters the image by storing secret information inside pixels that affects the visual quality of an image. However, changes incorporated in an image should not be perceived by the invaders. There are various standard evaluating methods used to confirm the image quality strength, like, mean square error (MSE), peak signal to noise ratio (PSNR), structural similarity index (SSIM), etc. Table 5 summarizes the MSE, PSNR, NCC, NAE, and SSIM values achieved by different image steganography techniques in this study.
Mean square error (MSE):
MSE is the error measurement of the stego image with respect to its original image. It helps in comparing the difference between the pixel values of an original image and stego image. Lesser MSE value provides better quality of an image [ 106 ]. Therefore, the MSE value should be near ‘0’. MSE can be calculated as follows:
where p i and p i ’ respectively represent the pixel values of the original and stego image. And, n represents the image size.
Peak signal to noise ratio (PSNR):
PSNR is the visual quality measuring tool that measures the image alteration in the stego image compared to its original image. It estimates the difference in pixel values of a stego image in relation to its original image. For better image quality, the PSNR value should be more than 39dB [ 107 ]. PSNR values of different existing methods for different payloads are shown in Graphs 1 , 2 , and 3 below. PSNR can be measured as follows:
where MSE can be measured with Eq. 1 .
Normalized cross correlation (NCC):
NCC is the relation determination method of an image. It investigates the relationship between the original image and its corresponding stego image. A better correlation between images indicates better image visual quality. Hence, NCC near ‘1’ is considered as the good steganography algorithm [ 108 ]. NCC can be analyzed as follows:
where O and S respectively denote the original and stego image pixel values.
Normalized absolute error (NAE):
NAE calculates the error between the original image and stego image to measure image quality after embedding. Error between the images should be less (near ‘0’) to retain the image quality [ 88 ]. NAE can be expressed as follows:
where O is the original image pixel value and S is the stego image pixel value.
Structural similarity index (SSIM):
SSIM is the visual quality measuring tool to checks the similarity between the original and stego image. The value of SSIM close to ‘1’ (means 100%) represents the good image quality [ 109 ]. SSIM can be mathematically represented as follows:
where µ i and µ j are the mean intensity, σ i and σ j are the standard deviations, and σ ij is the cross-covariance of images i and j respectively.
3.2 Embedding capacity analysis
Embedding capacity (EC) is another steganographic analysis parameter that calculates the number of secret data bits embedded into a per pixel of an image. The bits per pixel (bpp) should be more while preserving image imperceptivity. EC can be examined as follows:
Here, size of an image is M × N × D, where M and N represents row and column of an image, and D represents the image pixel depth that can be either 1 or 3 depends upon the image selection (gray or color image). Therefore, maximum bpp for a grayscale image will be 8 and for color image it will be 24 (3 × 8 = 24). Embedding capacity for different image steganography techniques is shown in Table 5 .
3.3 Differential analysis
The strength of an algorithm is tested by checking the sensitivity of an encrypted image with its original image and secret key. The strength of an encryption algorithm should be strong enough to resist attacks. The well-known differential analysis is a number of pixel change rate (NPCR) and unified average change intensity (UACI).
Number of pixel change rate (NPCR):
NPCR is the security evaluating method that analysis the single pixel changes in the original image. It checks the sensitivity of the encrypted image compared to its original image and secret key. The acceptable NPCR value is 99.61% and closer to 100% is considered as the best encryption algorithm [ 110 ]. NPCR can be analyzed by the equation as follows:
where m and n are the image measurements. E T is the total number of unequal units. And, I o and I e are the original image and encrypted image respectively.
Unified average change intensity (UACI):
UACI is the other encrypted image strength checking method. It calculates the average intensity of the difference between the original image and encrypted image. More percentage difference in intensities ensures a good UACI value and the lowest acceptable UACI value is 33.44% [ 110 ]. UACI can be calculated by the equation as follows:
where I o and I e are respectively the original and encrypted images. And, m and n are the image measurements.
3.4 Entropy analysis
Entropy is the average information per bit existing in an image. It checks the pixel randomness of an encrypted image. The average range of entropy is between 0 to 8 and close to 8 for 8 bit is considered as the best entropy value [ 111 ]. Entropy can be computed as follows:
where S represents symbol collections, c i ϵ S , P(c i ) represents probability and n is the symbol number.
3.5 Key analysis
The key analysis is the main tool of an encryption algorithm for checking algorithm strength. The algorithm strength depends on key analysis. It can be checked in two ways: key space and key sensitivity analysis. Key space checks the size of the secret key used for encrypting an image. The larger size of the secret key makes the system secure against attacks, as it will be difficult for the unauthorized user to get the exact same key. Key sensitivity checks the sensitivity of the secret key to the changes made. Even a single bit change in the original key results in an altogether different image or unrecoverable image.
3.6 Statistical analysis
Statistical analysis checks the robustness of an encrypted image against attacks. The commonly used statistical analyses are histogram analysis and correlation coefficient for testing its robustness against attacks.
Histogram analysis represents the image by the number of data points within a definite range. The histogram gives the pixel distribution or uncommon forms of an image. Histogram analysis can be checked on stego image or encrypted image in comparison to the original image. In the steganography approach, the histogram deviations of the stego image with respect to its original image can suspect the presence of data in an image. Therefore, for histogram comparison of stego image, the stego image histogram should resemble the original image histogram to avoid statistical attacks. Whereas, the histogram of an encrypted image should be uniform to show its random behavior. Histogram uniformity among pixels claims the robustness of the encryption method. Thus, the histogram of an encrypted image should be uniform to prevent the data from statistical attacks.
Correlation coefficient (CC):
The correlation coefficient (CC) checks the relationship between the original image and the encrypted image. In the original image, the pixels are interconnected with each other in three different directions: horizontal, vertical, and diagonal. However, for encrypted images, the correlation range between the pixels is [1, 1] and near 0 (lesser correlated) is considered as the good encryption technique [ 112 ]. The correlation coefficient can be expressed as follows:
Here, i and j represent image coordinates and C(i, j) represents the covariance between them. σ(i) and σ(j) are the standard deviations of their respective image coordinates. m is the pixel pairs ( i n, j n ) number. And, x(i) and x(j) are the mean deviations of i n and j n respectively.
3.7 Randomness analysis
Randomness analysis checks the pixel haphazardness of an encrypted image. National Institute of Standards and Technology (NIST) [ 113 ] has developed a statistical test suite to find out the algorithm strength by analyzing several tests on an encrypted image. The NIST statistical test suite consists of almost 15 calculable tests. These tests include frequency test, frequency within block test, run test, longest run of ones in a block test, binary matrix rank test, discrete fourier transform (DCT) test, non-overlapping template matching test, overlapping template matching test, etc. This test is helpful in identifying deviations of a binary sequence of an encrypted image.
3.8 Speed analysis
Scheme efficacy is analyzed by the execution time of an algorithm to complete its task [ 114 ]. The execution time of a method depends upon the system configuration and the algorithm complexity. This analysis can be examined for different processing steps of a program, like, embedding process, encryption process, the extraction process, decryption process, etc. The execution time for any of the program steps should be as small as possible to make the method computationally efficient. The embedding and extraction of some image steganography techniques are shown in Table 6 .
3.9 Steganography effect on medical image accuracy analysis
Medical image accuracy analysis checks the accuracy and precision of resulted medical image after treating with the steganography method. The commonly used methods are accuracy, specificity, sensitivity, and precision, [ 115 ] for analyzing the performance and quality contents of an image after steganography.
Accuracy is the medical image quality content and prediction accuracy measuring tool. It is the ratio between all correct predictions (positive or negative) and the entire test set [ 115 , 116 ]. Accuracy can be measured by the Equation as follows:
where TP is true positive, TN is true negative, FP is false positive, and FN is false negative.
Specificity:
Specificity is also called as true negative rate (TNR). It is the ratio between the number of correctly predicted normal people and the total number of normal people [ 115 ]. Specificity can be calculated by the Equation as follows:
where TN is true negative and FP is false positive.
Sensitivity:
Sensitivity is also called true positive rate (TPR) and recall. It is the ratio between the correctly predicted people with a disease and the total number of actual diseased people [ 115 ]. Sensitivity can be computed as follows:
where TP is true positive and FN is false negative.
Precision is also called a positive prediction value (PPV). It is the ratio between the total number of positive predictions people with a disease and the total number of positive predicted people [ 115 ]. Precision can be expressed as follows:
where TP is true positive and FP is false positive.
4 Discussions and future research directions
For secure information transmission, the image steganographic technique is used to restrict intrusion. It embeds the secret data bits into the image pixels to hide the data from unauthorized extraction. Numerous image steganography techniques have been developed by researchers to ensure data security. New trends in image steganography are discussed in this comprehensive review. From the literature, it can be observed that most of the techniques have been able to provide security and safety to the data. The security of data has been enhanced by some of the crypto-stego techniques discussed to provide double layer security to the data. From the survey of the existing image steganography and crypto-stego techniques, it can be noticed that each algorithm has its advantages and disadvantages. A few of the important issues as future directions are highlighted below:
Using smooth regions for hiding data creates more distortion in an image and thus suspects the presence of data. Hiding data into the edge regions not only provides good image quality but increases the embedding capacity of an image. Therefore, edge based image steganography technique could be used to increase the hiding space and visual quality of an image.
Most of the image steganography methods discussed have taken grayscale images as a cover medium. Therefore, there is a need for developing and applying steganography methods also on color images to prove its versatility and to further increase payload.
Hiding data into the frequency coefficients of an image provides security to the data but provides less capacity and is a complex method. Therefore, robust algorithms should be developed in spatial domain to improve data security with less complexity for which the encryption of data together with steganography can be helpful.
Many of the existing image steganography approaches have tried to either improve payload, image quality, or security of the algorithm. Therefore, a good tradeoff between these parameters should be created to improve the overall performance of the method in all dimensions. For this, edge based image steganography and chaos based encryption methods could be used together. Although, the research in this field has been done by the researchers. Though, it is still an underdeveloped field that needs to be explored in various image steganography schemes and different chaotic maps.
A survey of the literature leads us to conclude that computational complexity is still an open area of research in the area of the image steganography method.
Experimental analysis of different reviewed techniques has not used all the evaluation parameters for analyzing the scheme. It can be observed from the survey that image steganography algorithms that encrypt data before embedding have not tested the technique for basic NPCR, UACI, and other security tools. To ensure strong security to the encrypted data. Therefore, every encryption method should be tested for different security tools.
The steganography approach should resist geometrical attacks, signal processing attacks, and noise attacks to ensure its reliability, so development of robust steganographic systems is an open area of research.
Several methods have been tested only on few image formats. Therefore, an effort should be done to create a benchmark dataset to compile the algorithm for different image formats.
5 Conclusion
Technological advancement is increasing exponentially to ease daily activities and for a fast service delivery system. For todays’ efficient communication system, the internet acts as a central pillar and reduces overconsumption of resources like time and cost. However, the internet is an open environment for data thefts, data modifications, etc. Therefore, to protect data/information from getting into the wrong hands, the image steganography method is used for ensuring data security. The purpose of this review paper is to present a comprehensive review of various image steganography and crypto-stego techniques with their pros and cons to help the reader understand different image crypto-stego techniques. This paper also gives insight into the evaluation parameters being used for steganography and cryptography analysis. This review is significantly highlights the grey areas in the area of the image steganography. Most of the existing image steganography approaches still suffer in terms of less security, low payload, poor image quality, and complexity. Therefore, it is a necessity to develop efficient image steganographic schemes along with data encryption to improve image embedding capacity, image imperceptibility, security with less complexity and should be resistant to different attacks.
Jan A, Parah SA, Malik BA, Rashid M. Secure data transmission in IoTs based on CLoG edge detection. Future Generation Computer system. 2021. https://doi.org/10.1016/j.future.2021.03.005 .
Article Google Scholar
Alsaidi A, lehaibi KA, Alzahrani H, Ghamdi MA, Gutub A. Compression multi-level crypto stego security of texts utilizing colored email forwarding. J Comp Sci Computational Math (JCSCM). 2018;8(3). https://doi.org/10.20967/jcscm.2018.03.002 .
Khan WZ, Aalsalem MY, Khan MK, Arshad Q. Data and Privacy: getting consumers to trust products enabled by the Internet of Things. IEEE Consumer Electronics Magazine. 2019;8:35–8. https://doi.org/10.1109/MCE.2018.2880807 .
Singh AK, Kumar B, Singh SK, Ghrera SP, Mohan A. Multiple watermarking technique for securing online social network contents using back propagation neural network. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.023 .
Alanazi N, Alanizy A, Baghoza N, Ghamdi MA, Gutub A. 3-Layer PC text security via combining compression, aes cryptography 2LSB image steganography. J Res Eng Appl Sci. 2018;3(4):118–124. https://doi.org/10.46565/jreas.2018.v03i04.001 .
Parah SA, Sheikh JA, Assad UI, Bhat GM. Hiding in Encrypted Images: A three tier security data hiding technique. Multidim Syst Sign Process. 2017;28(2):549–72.
Al-Roithy BO, Gutub A. Remodeling randomness prioritization to boost-up security of rgb image encryption. Multimed Tools Appl. 2021;80:28521–81. https://doi.org/10.1007/s11042-021-11051-3 .
Jan A, Parah SA, Malik BA. A novel laplacian of gaussian and chaotic encryption based image steganography technique. 2020 Int Conf Emerg Technol (INCET) Belgaum. 2020;1–4. https://doi.org/10.1109/INCET49848.2020.9154173 .
Luo Y, Yu J, Lai W, Liu L. A novel chaotic image encryption algorithm based on improved baker map and logistic map. Multimed Tools Appl. 2019;78:2023–22043. https://doi.org/10.1007/s11042-019-7453-3 .
Jan A, Parah SA, Malik BA. Logistic map-based image steganography using edge detection. Adv Intell Syst Comput. 2021;1189. https://doi.org/10.1007/978-981-15-6067-5_50 .
Patro KAK, Acharya B. A novel multi-dimensional multiple image encryption technique. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-019-08470-8 .
Li C, Feng B, Li S, Kurths J, Chen G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Transaction on Circuits and Systems-I: Regular Papers. 2019;66(6):2322–35. https://doi.org/10.1109/TCSI.2018.2888688 .
Article MathSciNet MATH Google Scholar
Hua Z, Jin F, Xu B, Huang H. 2D Logistic-Sine-Coupling map for image encryption. Elsevier Signal Process. 2018;149:148–61.
Khan M, Sajjad M, Mehmood I, Rho S, Baik SW. image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.029 .
Kim C, Yang CN, Leng L. High-capacity data hiding for ABTC-EQ based compressed image. Electronics. 2020;9(4):644.
Hussan FS, Gutub A. Improving data hiding within colour images using hue component of HSV colour space, CAAI Transactions on Intelligence Technology. IET (IEE). 2021. https://doi.org/10.1049/cit2.12053 .
Hassan FS, Gutub A. Novel embedding secrecy within images utilizing an improved interpolation-based reversible data hiding scheme. J King Saud University - Comp Information Sci. 2020;ISSN:1319–1578. https://doi.org/10.1016/j.jksuci.2020.07.008 .
Hussan M, Parah SA, Gull S, Qureshi GJ. Temper detection and self-recovery of medical imagery for smart health. Arab J Sci Eng. 2021. https://doi.org/10.1007/s13369-020-05135-9 .
Loan NA, Hurrah NN, Parah SA, Lee JW, Sheikh JA, Bhat GM. Secure and robust digital image watermarking using coefficient differencing and Chaotic encryption. IEEE transection. 2018. https://doi.org/10.1109/ACCESS.2018.2808172 .
Biswas R, Mukherjee I, Bandyopadhyay SK. Image feature based high capacity steganographic algorithm. Multimed Tools Appl. 2019. https://doi.org/10.1007/s11042-019-7369-y .
Hussain M, Wahab AWA, Idris YIB, Ho ATS, Jung KH. Image steganography in special domain: A survey. Signal Process Image Commun. 2018;65:46–66. https://doi.org/10.1016/j.image.2018.03.012 .
Wang J, Yang C, Wang P, Song X, Lu J. Payload location for JPEG image steganography based on co-frequency sub-image filtering. International J Distributed Sensor Networks 2020;16(1).
Ayub N, Selwal A. An improved image steganography technique using edge based data hiding in DCT domain. J Int Math. 2020;23(2):357–66.
Google Scholar
Patel SK, Saravanam C. Performance analysis of hybrid edge detector scheme and magic cube based scheme for steganography application. IEEE transection. 2018.
Jiang S, Ye D, Huang J, Shang Y, Zheng Z. SmartSteganography: Light-weight generative audio steganography model for smart embedding applications. J Netw Comput Appl. 2020;165: 102689. https://doi.org/10.1016/j.jnca.2020.102689 .
Prasad S, Pal AK. An RGB colour image steganography scheme using overlapping block-based pixel-value differencing. Royal Soc Open Sci. 2017;4.
Alkhudaydi M, Gutub A. Securing data via cryptography and Arabic text steganography. SN Computer Sci. 2021;2(46). https://doi.org/10.1007/s42979-020-00438-y .
Alkhudaydi MG, Gutub AA. Integrating light-weight cryptography with diacritics Arabic text steganography improved for practical security applications. J Information Security Cybercrimes Res 2020;3(1), 13–30, https://doi.org/10.26735/FMIT1649 .
Gutub A, Al-Ghamdi M. Image based steganography to facilitate improving counting-based secret sharing, 3D Research. 2019;10(6). https://doi.org/10.1007/s13319-019-0216-0 .
Gutub A, Al-Juaid N. Multi-bits stego-system for hiding text in multimedia images based on user security priority. J Comp Hardware Eng. 2018;1(2):1–9. https://doi.org/10.63019/jche.v1i2.513 .
Al-Juaid N, Gutub A. Combining RSA and audio steganography on personal computers for enhancing security. SN Appl Sci. 2019;1:830. https://doi.org/10.1007/s42452-019-0875-8 .
Atty BAE, Iliyasu AM, Alaskar H, Latif AAAE. A Robust Quasi quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms. Sensors. 2020;20:3108. https://doi.org/10.3390/s20113108 .
Parah SA, Sheikh JA, Assad UI, Bhat GM. Realisation and robustness evaluation of a blind spatial domain watermarking technique. Int J Electron. 2017;104(4):659–72.
Pattanaik B, Chitra P, Lakhmi HR, Selvi T, Nagraj V. Contrasting the performance of discrete transformations on digital image steganography using artificial intelligence. Materials Today: Proceedings. 2021. https://doi.org/10.1016/j.matpr.2020.12.076 .
AbdelRaouf A. A new hiding approach for image steganography based on visual color sensitivity. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-020-10224-w .
Hussain M, Riaz Q, Saleem S, Ghafoor A, Jung KH. Enhanced adaptive data hiding method using LSB and pixel value differencing. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-021-10652-2 .
Sahu AK, Swain G. Reversible image steganography using dual-layer LSB matching. Sens Imaging. 2020;21:1. https://doi.org/10.1007/s11220-019-0262-y .
Hussain M, Wahab AWA, Ho ATS, Javed N, Jung KH. A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement. Signal Process Image Commun. 2017. https://doi.org/10.1016/j.image.2016.10.005 .
Malik A, Sikka G, Verma HK. An AMBTC compression based data hiding scheme using pixel value adjusting strategy. Multidim Syst Sign Process. 2018;29(4):1801–18.
Kumar R, Kim DS, Jung KH. Enhanced AMBTC based data hiding method using hamming distance and pixel value differencing. J Inf Secur Appl. 2019;47:94–103.
Chakraborty S, Jalal AS. A novel local binary pattern based feature image steganography. Multimed Tools Appl. 2020;79:19561–74.
Lin J, Qian Z, Wang Z, Zhang X, Feng G. A new steganography method for dynamic GIF images based on palette sort. Wirel Commun Mobile Comput. 2020;2020:8812087.
Parah SA, Sheikh JA, Akhoon JA, Loan NA. Electronic Health Record Hiding in Images for Smart City Applications: A Computationally Efficient and Reversible Information Hiding Technique for Secure Communication. Future Generation Comp Sys. 2018. https://doi.org/10.1016/j.future.2018.02.023 .
Li X, Luo Y, Bian W. Retracing extended sudoku matrix for high-capacity image steganography. Multimed Tools Appl. 2021 https://doi.org/10.1007/s11042-021-10675-9 .
Saha S, Chakraborty A, Chatterjee A, Dhargupta S, Ghosal SK, Sarkar R. Extended exploiting modification direction based steganography using hashed-weightage array. Multimed Tools Appl. 2020;79:20973–93.
Shen SY, Huang LH, Yu SS. A novel adaptive data hiding based on improved EMD and interpolation. Multimed Tools Appl. 2018;77:131–41.
Bairagi AK, Khondoker R, Islam R. An efficient steganographic approach for protecting communication in the Internet of Things (IoT) critical infrastructures. Information Security J: A Global Perspective Taylor & Francis. 25 2016;4(6):197–212. https://doi.org/10.1080/19393555.2016.1206640 .
Rim Z, Afef A, Ridha E, Mourad Z. Beta chaotic map based image steganography. Springer Nature. 2020. https://doi.org/10.1007/978-3-030-20005-3_10 .
Hassan FS, Gutub A. Efficient image reversible data hiding technique based on interpolation optimization. Arab J Sci Eng. 2021. https://doi.org/10.1007/s13369-021-05529-3 .
Atta R, Ghanbari M. 2021 A high payload data hiding scheme based on dual tree complex wavelet transform. Optik. 2021;226. https://doi.org/10.1016/j.ijleo.2020.165786 .
Dhargupta S, Chakraborty A, Ghosal SK, Saha S, Sarkar R. Fuzzy edge detection based steganography using modified Gaussian distribution. Multimed Tools Appl. 2019. https://doi.org/10.1007/s11042-018-7123-x .
Ahmadian AM, Amirmazlaghani M. A novel secret image sharing with steganography scheme utilizing Optimal Asymmetric Encryption Padding and Information Dispersal Algorithms. Signal Process Image Commun. 2019. https://doi.org/10.1016/j.image.2019.01.006 .
Kich I, Ameur EB, Taouil. Image Steganography Based on Edge Detection Algorithm, IEEE transection. 2018.
He X, Zhang W, Zhang H, Ma L, Li Y. Reversible data hiding for high dynamic range images using edge information. Multimed Tools Appl. 2018. https://doi.org/10.1007/s11042-018-6589-x .
Garav K, Ghanekar U. Image steganography algorithm based on edge region detection and hybrid coding. Comput Model Technol. 2018;22(1):40–56.
Prasad S, Pal AK. Stego-key-based image steganography scheme using edge detector and modulus function. Int J Computational Vision and Robotics. 2020;10(3):223–40.
Mukherjee S, Sanyal G. Edge based image steganography with variable threshold. Multimed Tools Appl. 2019;78:16363–88. https://doi.org/10.1007/s11042-018-6975-4 .
Kadhim IJ, Premaratne P, Vial PJ. Adaptive Image Steganography Based on Edge Detection Over Dual-Tree Complex Wavelet Transform Springer Nature International Publishing. 2018;544–550. https://doi.org/10.1007/978-3-319-95957-3_57 .
Ghosal SK, Mandal JK, Sarkar R. High payload image steganography based on Laplacian of Gaussian (LoG) edge detector. Multimed Tools Appl. 2018;77:30403–18.
Ghosal SK, Chatterjee A, Sarkar R. Image steganography based on Kirsch edge detection. Multimed Syst. 2021;27:73–87.
Banik BG, Poddar MK, Bandyopadhyay SK. Image steganography using edge detection by Kirsch operator and flexible replacement technique. Emerg Technol Data Mining Inf Sec Adv Intel Syst Comput. 2019;814:175–87. https://doi.org/10.1007/978-981-13-1501-5_15 .
Wang Y, Tang M, Wang Z. High-capacity adaptive steganography based on LSB and hamming code. Optik. 2020;213. https://doi.org/10.1016/j.ijleo.2020.164685 https://doi.org/10.1016/j.ijleo.2020.164685 .
Tripathy SK, Srivastava R. An Edge-Based Image Steganography Method Using Modulus-3. Strategy and Comparative Analysis Springer Nature. 2020;485–494. https://doi.org/10.1007/978-981-15-4018-9_43 .
Tuncer T, Sonmez Y. A Novel Data Hiding Method based on Edge Detection and 2k Correction with High Payload and High Visual Quality. Balkan J Electrical & Comp Eng. 2019;7(3):311–318. https://doi.org/10.17694/bajece.573514 .
Abdel-Aziz MM, Hosny KM, Lashin NA. Improved data hiding method for security color images. Multimed Tools Appl. 2021;50:12641–70. https://doi.org/10.1007/s11042-020-10217-9 .
Yao H, Fanyu M, Chuan Q, Tang Z. Dual-JPEG-image reversible data hiding. Inf Sci. 2021;563:130–49. https://doi.org/10.1016/j.ins.2021.02.015 .
Article MathSciNet Google Scholar
Liu Y, Chang CC. Reversible data hiding for JPEG images employing all quantized non-zero AC coefficients. Displays. 2018;51:51–6. https://doi.org/10.1016/j.displa.2018.01.004 .
Attaby AA, Ahmed MFMM, Alsammak AK. Data hiding inside JPEG images with high resistance to Steganalysis using a novel technique: DCT-M3. Ain Shams Engineering Journal. 2018;9:1966–74. https://doi.org/10.1016/j.asej.2017.02.003 .
El-Rahman SA. A comparative analysis of image steganography based on DCT algorithm and steganography tool to hide nuclear reactors confidential information. Comput Electr Eng. 2016;1–20. https://doi.org/10.1016/j.compeleceng.2016.09.001 .
Mohamed N, Baziyad M, Rabie T, Kamel I. L*a*b color space high capacity steganography utilizing quad-trees. Multimed Tools Appl. 2020;79:25089–113. https://doi.org/10.1007/s11042-020-09129-5 .
Rabie T, Kamel I, Baziyad M. Maximizing embedding capacity and stego quality: curve-fitting in the transform domain. Multimed Tools Appl. 2018;77:8295–326. https://doi.org/10.1007/s11042-017-4727-5 .
Saidi M, Hermassi H, Rhouma R, Belghith S. A new adaptive image steganography scheme based on DCT and chaotic map. Multimed Tools Appl. 2017;76(11):13493–510. https://doi.org/10.1007/s11042-016-3722-6 .
Nipanikar SI, Deepthi VH, Kulkarni N. A sparse representation based image steganography using particle swarm optimization and wavelet transform. Alex Eng J. 2018;57:2343–56. https://doi.org/10.1016/j.aej.2017.09.005 .
Navriyanto A, Sutarno S, Erwin E, Siswanti SD. Image steganography using combine of discrete wavelet transform and singular value decomposition for more robustness and higher peak signal noise ratio. IEEE Transection. 2018;147–152.
Miri A, Faez K. An image steganography method based on integer wavelet transform. Multimed Tools Appl. 2018;77:13133–44. https://doi.org/10.1007/s11042-017-4935-z .
Kalita M, Tuithung T, Majumdar S. A new steganography method using integer wavelet transform and least significant bit substitution. Comput J. 2019. https://doi.org/10.1093/comjnl/bxz014 .
Ghosal SK, Mukhopadhyay S, Hossain S, Sarkar R. Exploiting Laguerre transform in image steganography. Comput Electr Eng. 2021;89. https://doi.org/10.1016/j.compeleceng.2020.106964 .
Ma B, Li B, Wang XY, Wang CP, Li J, Shi YQ. A code division multiplexing an block classification-based real-time reversible data-hiding algorithm for medical images. J Real-Time Image Proc. 2019. https://doi.org/10.1007/s11554-019-00884-9 .
Murugan GVK, Subramaniyam RU. Performance analysis of image steganography using wavelet transform for safe and secured transaction. Multimed Tools Appl. 2020;79:9101–15. https://doi.org/10.1007/s11042-019-7507-6 .
Maji G, Mandal S, Sen S. Cover independent image steganography in spatial domain using higher order pixel bits. Multimed Tools Appl. 2021;80:15977–6006. https://doi.org/10.1007/s11042-020-10298-6 .
Sharif A, Mollaeefar M, Nzari M. A novel method for digital image steganography based on a new three-dimensional chaotic map. Multimed Tools Appl. 2017;76:7849–67. https://doi.org/10.1007/s11042-016-3398-y .
Gambhir G, Mandal JK. Multicore implementation and performance analysis of a chaos based LSB steganography technique. Microsyst Technol. 2020. https://doi.org/10.1007/s00542-020-04762-4 .
Prasad S, Pal AK. Logistic map-based image steganography scheme using combined LSB and PVD for security Enhancement. Springer Nature Adv Intel Comput. 2019. https://doi.org/10.1007/978-981-13-1501-5_17 .
Mohammad K, Ahamd j, Rho S, Baik SW. Image steganography for authenticity of visual contents in social networks. Multimed Tools Appl. 2017. https://doi.org/10.1007/s11042-017-4420-8 .
Alotaibi M, Al-Hendi D, Alroithy B, Alghamdi M, Gutub A. Secure mobile computing authentication utilizing hash, cryptography and steganography combination. J Inf Sec Cybercrimes Res (JISCR). 2019;2(1):9–20.
Mathivanan P, Balaji GA. QR code base color image stego-crypto technique using dynamic bit replacement and logistic map. Optik. 2021;225: 165838. https://doi.org/10.1016/j.ijleo.2020.165838 .
Abdelwahab OF, Hussein AI, Hamed HFA, Kelash HM, Khalaf AAM. Efficient combination of RSA cryptography, lossy and lossless compression steganography techniques to hide data. Comput Sci. 2021;183:5–12. https://doi.org/10.1016/j.procs.2021.02.002 .
Parah SA, Kaw JA, Bellavista P, Loan NA, Bhat GM, Muhammad K, Victor A. Efficient security and authentication for edge-based Internet of Medical Things. IEEE Internet Things J. 2021. https://doi.org/10.1109/JIOT.2020.3038009 .
Parah SA, Sheikh JA, Akhoon JA, Loan NA, Bhat GM. Information Hiding in Edges: A high capacity information hiding technique using hybrid edge detection. Springer Multimedia Tools Appl. 2016;77(1):185–207.
Delmi A, Suryadi S, Satria Y. Digital image steganography by using edge adaptive based chaos cryptography. J Phys. 2017;1442. https://doi.org/10.1088/1742-6596/1442/1/012041 .
Sharma H, Mishra DC, Sharma RK, Kumar N. Multi-image steganography and authentication using crypto-stego techniques. Multimed Tools Appl. 2021;80:29067–93. https://doi.org/10.1007/s11042-021-11068-8 .
Kaushik N, Sheokand K. A steganography technique based on chaotic LSB and DWT. International J Innov Res Comp Comm Eng. 2016;4(6):10420–10426. https://doi.org/10.15680/IJIRCCE.2016.0405028 .
Panday HM. Secure medical data transmission using a fusion of bit mask oriented genetic algorithm, encryption and steganography. Futur Gener Comput Syst. 2020;111:213–25. https://doi.org/10.1016/j.future.2020.04.034 .
Elhoseny M, Gonzalez GR, Elnasr OMA, Shawkat SA, Arunkumar A, Farouk A. Secure Medical Data Transmission Model for IoT-Based Healthcare Systems. IEEE Transection, Special Section on Information Security Solutions for Telemedicine Applications. 2018;6(2018):20596–608. https://doi.org/10.1109/ACCESS.2018.2817615 .
Duan X, Guo D, Liu N, Li B, Gou M, Qin C. A new high capacity image steganography method combined with image elliptic curve cryptography and deep neural network. IEEE Transection. 2020;8. https://doi.org/10.1109/ACCESS.2020.2971528 .
Subhedar MS, Mankar VH. Curvelet transform and cover selection for secure steganography. Multimed Tools Appl. 2018;77:8115–38. https://doi.org/10.1007/s11042-017-4706-x .
Eyssa AA, Abdelsamie FE, Abdelnaiem AE. An efficient image steganography approach over wireless communication system. Wireless Pers Commun. 2020;110:321–37. https://doi.org/10.1007/s11277-019-06730-2 .
Kaur R, Singh B. A hybrid algorithm for image steganography. Multidimens Syst Signal Process. 2021;32:1–23. https://doi.org/10.1007/s11045-020-00725-0 .
Hureib ESB, Gutub AA. Enhancing medical data security via combining elliptic curve cryptography and image steganography. International J Comp Sci Network Security (IJCSNS). 2020;20(8):1–8. https://doi.org/10.22937/IJCSNS.2020.20.08.1 .
Hureib ESB, Gutub AA. Enhancing medical data security via combining elliptic curve cryptography with 1-LSB and 2-LSB image steganography. International J Comp Sci Network Security (IJCSNS). 2020;20(12):232–241. https://doi.org/10.22937/IJCSNS.2020.20.12.26 .
Samkari H, Gutub A. Protecting medical records against cybercrimes within hajj period by 3-layer security. Recent Trends Inf Technol Appl. 2019;2(3):1–21. https://doi.org/10.5281/zenodo.3543455 .
Denis R, Madhubala P. Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare system. Multimed Tools Appl. 2021;80:21165–202. https://doi.org/10.1007/s11042-021-10723-4 .
Manikandan T, Muruganandham A, Babuji R, Nandalal V, Iqbal JIM. Secure E-Health using image steganography. J Phys. 2021;1917: 012016. https://doi.org/10.1088/1742-6596/1917/1/012016 .
Ogundokun RO, Awotunde JB, Adeniyi EA, Ayo FE. Crypto-stego based model for securing medical information on IOMT platform. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-021-11125-2 .
Prasanalakshmi B, Murugan K, Srinivasan K, Shridevi S, Shamsudheen S, Hu YC. Improved authentication and computation of medical data transmission in the secure IoT using hyperelliptic curve cryptography. J Supercomput. 2021. https://doi.org/10.1007/s11227-021-03861 .
Karakus S, Avci E. A new image steganography method with optimum pixel similarity for data hiding in medical images. Med Hypotheses. 2020;139. https://doi.org/10.1016/j.mehy.2020.109691 .
Sukumar AK, Subramaniyaswamy V, Vijayakumar V, Ravi L. A secure multimedia steganography scheme using hybrid transform and support vector machine for cloud-based storage. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-019-08476-2 .
Gutub A, Al-Shaarani F. Efficient implementation of multi-image secret hiding based on LSB and DWT steganography comparisons. Arab J Sci Eng. 2020. https://doi.org/10.1007/s13369-020-04413-w .
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW. Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.029 .
Khan MF, Ahmed A, Saleem K. A novel cryptographic substitution box design using gaussian distribution. IEEE Access. 2019;7:15999–6007.
Sneha PS, Sankar S, Kumar AS. A chaotic colour image encryption scheme combining Walsh-Hadamard transform and Arnold-Tent maps. J Ambient Intell Humaniz Comput. 2020;11:1289–308. https://doi.org/10.1007/s12652-019-01385-0 .
Shah D, Shah T. Anovel discrete image encryption algorithm based o n finite algebraic structures. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-020-09182-0 .
Cicek I, Pusane AE, Dundar G. An Integrated Dual Entropy Core True Random Number Generator. IEEE Transaction Circuits-II. 2017;64:329–33.
Njitacke ZT, Isaac SD, Nestor T, Kengne J. Window of Multistability and Control in a Simple 3D Hopfield Neural Network: Application to Biomedical Image Encryption. Springer Neural Comput Appl. 2020. https://doi.org/10.1007/s00521-020-05451-z .
Eze P, Parampalli U, Evans R, Liu D. Evaluation of the effect of steganography on medical image classification accuracy. J Bioinforma Comput Biol. 2020;9(4). https://doi.org/10.1007/s11042-021 .
Eze P, Parampalli U, Evans R, Liu D. A new evaluation method for medical image information hiding techniques. IEEE Transection. 2020;6119–6122. https://doi.org/10.1109/EMBC44109.2020.9176066 .
Download references
This work is not supported by any funding.
Author information
Authors and affiliations.
Department of Electronics and Instrumentation Technology, University of Kashmir, Srinagar, India
Aiman Jan, Shabir A. Parah & Muzamil Hussan
Department of Electronics and Communication Engineering, Institute of Technology, University of Kashmir Zakoora, Srinagar, India
Bilal A. Malik
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Shabir A. Parah .
Ethics declarations
Informed consent, research involving human participants and/or animals., conflicts of interest.
The authors do not have any conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Jan, A., Parah, S.A., Hussan, M. et al. Double layer security using crypto-stego techniques: a comprehensive review. Health Technol. 12 , 9–31 (2022). https://doi.org/10.1007/s12553-021-00602-1
Download citation
Received : 03 August 2021
Accepted : 20 September 2021
Published : 13 October 2021
Issue Date : January 2022
DOI : https://doi.org/10.1007/s12553-021-00602-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Steganography
- Cryptography
- Imperceptivity
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
PDF | Steganography is a technique of hiding information in digital media in such a way that no one apart from the intended recipient knows the... | Find, read and cite all the research you need ...
Steganography considers one of the techniques which used to protect the important information. The main goals for this paper, to recognize the researchers for the main fundamentals of steganography. ... Research in information hiding has tremendous increased during the past decade with commercial interests driving the field [5],[7],[8].
Image Steganography is the process of hiding information which can be text, image or video inside a cover image. The secret information is hidden in a way that it not visible to the human eyes. Deep learning technology, which has emerged as a powerful tool in various applications including image steganography, has received increased attention recently. The main goal of this paper is to explore ...
Steganography derives from the Greek word steganos, meaning covered or secret, and graphy (writing or drawing) [1]. Steganography is a technology where modern data ... In Mamta Juneja et. al's [4] research paper a secured robust approach of information security is proposed. It presents two component based LSB ( Least Significant Bit )methods ...
Known steganography attack: The cover media, stego media as well as the steganography tool or algorithm, are known. 4. Conclusion. In this paper, different techniques are discussed for embedding data in text, image, audio/video signals and IP datagram as cover media. All the proposed methods have some limitations.
A number of future directions are presented that can assist researchers in determining the direction of future research in image steganography. With the rapid growth of multimedia technologies, many images are communicated over public channels. Therefore, significant interest has been given to prov ... Download PDF. Sharanpreet Kaur 1,
Fig. 1. Relationship of steganography to related flelds. Unlike information hiding and digital watermarking, the main goal of steganography is to communicate securely in a completely undetectable manner. Although steganography is an ancient art, flrst used against the persian by the romans, it has evolved much trough the years.
Abstract. Steganography is the science that involves encrypting data in a suitable multimedia carrier, such as image, audio, and video files. The main purpose of image steganography is to hide the data in images. This means that it encrypts the text in the form of an icon. Steganography is done when there is communication takes place between ...
Steganography emerged as an effective technology for securing the data over the network. Its specificity of concealing the existence of the secret data supports its application in securing the information in the modern era. The desire of industry and support from various governments motivated the researchers to develop steganography tools. These spatial and transform domain tools implement ...
Steganography is the science and art of covert communication. Conversely, steganalysis is the study of uncovering the steganographic process. The evolution of steganography has been paralleled by the development of steganalysis. In this game of hide and seek, the two player's steganography and steganalysis always want to break the other down. Over the past three decades, research has ...
Abstract: In the past few years, the Generative Adversarial Network (GAN), which proposed in 2014, has achieved great success. There have been increasing research achievements based on GAN in the field of computer vision and natural language processing. Image steganography is an information security technique aiming at hiding secret messages in common digital images for covert communication.
Modern steganography identifies two main classification schemes for the sorting of algorithms. The first distinguishes algorithms based on file type. The second, more widely used scheme categorizes based on embedding method. 3.1 Injection (Insertion), and Generation Classifications.
4 CHAPTER 1 Deep Learning in steganography and steganalysis The Convolutional Neuronal Networks used for steganalysis are mainly built in three parts, which we will call modules: the pre-processing module, the convolution module, and the classi cation module. As an illustration, gure 1.1 schematizes the network proposed by Yedroudj et al. in ...
Most of the research on steganography utilizes cover media, such as videos, images, and sounds. Notably, text steganography is usually not given priority because of the difficulties in identifying redundant bits in a text file. To embed information within a document, its attributes must be changed. ... A new PDF steganography technique was ...
PDF files have been chosen to this study because of their wide use in Internet which make them great steganographic medium. Obtained results encourage to conduct more research in this area. The future projects may concern new methods of distributed steganography in PDF documents, incorporating cryptography and other means of security.
In this research, we propose two new image steganography techniques focusing on increasing image-embedding capacity. The methods will encrypt and hide secret information in the edge area. We utilized two hybrid methods for the edge detection of the images.
The research on steganography can be roughly divided into three stages. Early information hiding technologies were mainly based on non-adaptive hiding strategies, among which the most typical representative is LSB (Least Significant Bit) [ 16 ].
PDF | Steganography is the technique of concealing the covert data in natural and usual looking objects to keep the existence of the information secret.... | Find, read and cite all the research ...
Securing confidential data is imperative in the modern digital era, where the escalating challenges in data security underscore the urgency to provide a secure and efficient approach to confidential text data protection, This paper proposes an innovative three-pronged model integrating encryption, padding, and steganography to robustly protect sensitive text documents. The encryption process ...
View a PDF of the paper titled Steganography of Steganographic Networks, by Guobiao Li and 4 other authors. View PDF Abstract: Steganography is a technique for covert communication between two parties. With the rapid development of deep neural networks (DNN), more and more steganographic networks are proposed recently, which are shown to be ...
Firms. The research revealed a surprising fact: A small number of companies are responsible for a substantial amount of the contact discrimination measured. Who are these firms? In this paper, the authors use the results from their experiment to construct a report card that grades the level of discrimination shown in the experiment by each company.
In January 2024, FortiGuard Labs collected a PDF file written in Portuguese that distributes a multi-functional malware known as Byakugan. While investigating this campaign, a report about it was published. Therefore, this report will only provide a brief analysis of the overlap between that attack and this and focus primarily on the details of ...
VIEW FULL DOCUMENT. Recognizing the Use of Steganography in Forensic Evidence (4e) Digital Forensics, Investigation, and Response, Fourth Edition - Lab 02 Student: Email: Sam Martins [email protected] Time on Task: Progress: 9 hours, 40 minutes 100% Report Generated: Saturday, March 30, 2024 at 7:36 PM Section 1: Hands-On Demonstration Part 1 ...
Steganography is the art of concealing data into any multimedia for covert communication [].Steganography can be divided into many types based on the cover object used to attain security, like text, image, audio, video, and network [26,27,28,29,30,31].Further, the steganography can be divided into two domains based on the techniques used to hide data in any multimedia, i.e., spatial domain ...
Federal Register/Vol. 89, No. 70/Wednesday, April 10, 2024/Notices 25277 DEPARTMENT OF HEALTH AND HUMAN SERVICES National Institutes of Health Center for Scientific Review; Notice of Closed Meeting Pursuant to section 1009 of the
• At least 7 campuses will engage in other innovative research supports around specific societal problems and expand a culture of research on their campus. For example: o SUNY Oswego is using their allocation to support the Great Lakes Institute to conduct research around water quality monitoring, watershed maintenance, meteorological,