Griffith University
Popular sites
Home > Using Learning at Griffith > Staff Using Learning@Griffith > Assessment for staff > Turnitin > Creating and Configuring
Creating and Configuring Turnitin Assignments
- Using Learning@Griffith
- Getting started
- Assessment tools
- Communication and Collaboration
- Lecture capture
- Organisations
- Preparing a course site
- Content tools
- Administration tools

A-Z of tools
On this page, how to manually create a turnitin assignment, what to do before performing a turnitin recycle, how to perform a turnitin recycle, what to do after a turnitin recycle, how to configure a turnitin assignment for draft submissions, how to configure a turnitin assignment for final submissions, the start date, due date and post date do not appear on the modify page. how do i change these settings, learning@griffith help in canvas.
We have a brand-new help website for the new LMS Canvas, with access to further support from 24/7 call and chat lines.
Learning@Griffith Help
Creating Turnitin assignments
Turnitin assignments can be manually created within your course site. To create a Turnitin assignment:
- Navigate to the content folder you would like the assignment to appear in
- Hover over the Assignments tab toward the top of the area, then click Turnitin Direct Assignment
This will open the assignment creation page where you can configure the settings as desired.
How to set up Turnitin assignments after a course copy
If you have performed a course copy and the source (old) course site contained Turnitin assignments, copies of those assignments should be present in the destination (new) course site, provided the correct course copy settings were used. However, these new assignments will not be functional or accessible until a Turnitin recycle process is performed. The Turnitin recycle process establishes a connection between your Learning@Griffith course site and the Turnitin system and separates the new course site from the old one.
Before performing a Turnitin recycle, please note that the process should:
- If you are able to access and edit Turnitin submission points, a recycle may not be required
- If a recycle is performed in the old course site it will sever the link between the course site and Turnitin and it can be very difficult to recover student work.
- Students may not be able to access a submission point to upload their paper if a recycle has not been performed after a copy.
- If a recycle is performed after students have been able to make submissions in your course site, it will sever the link between the course site and Turnitin and it can be very difficult to recover student work.
To perform a Turnitin recycle:
- Navigate to the current/new course site in Learning@Griffith
- Confirm you are in the correct course and not an older offering or the wrong course
- In the left-hand course menu, expand Course Tools , then click Turnitin Direct Tools
- Click the Recycle Turnitin Direct Assignments link or icon
- Click the blue Recycle Turnitin Direct Assignments button
- Wait for the page to reload
If you have any concerns about performing a recycle, please contact the IT Service Centre for assistance.
After you have performed a recycle, we strongly recommend you edit each assignment and ensure the settings align with those recommended for Draft submissions or Final submissions . Keep in mind that some important settings, such as the Due Date and Post Date, cannot be checked or changed from the Modify page and must be checked via the Edit Parts area .
Configuring Turnitin assignments
Turnitin assignments can be configured on the assignment creation page or the Modify page. The assignment creation page is shown immediately after you manually create an assignment , while the Modify page can be accessed by clicking the chevron to the right of the assignment title in the assessment folder, then clicking Edit .
Draft submission points are optional and provide students the opportunity to check their similarity score prior to submitting the final version of their paper for marking. The following settings are recommended for all Turnitin assignments set up for Draft submissions, with bold text referencing the most important settings to review.
Assignment Details part 1
- This will show to students just above the View Assignment link in the content folder
- You may want to include 'DRAFT' somewhere in the title. For example, 'DRAFT Lab Report Submission'.
- This will show to students in the expandable description box just after they click View Assignment
- The character limit of this field is 1000
- Set Submission Method to File Upload
- There is no need to set this above zero because draft submissions are not marked
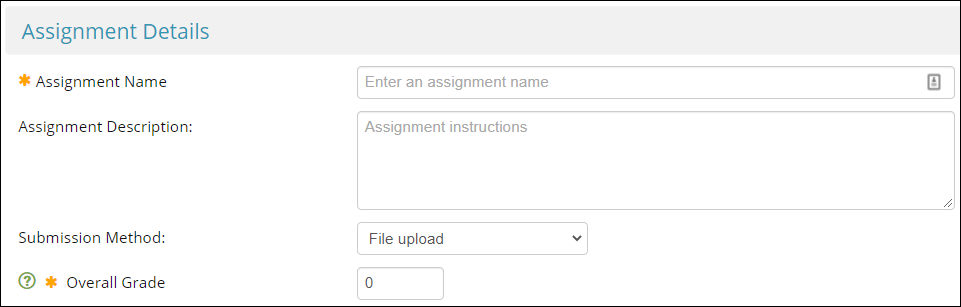
Assignment Details part 2
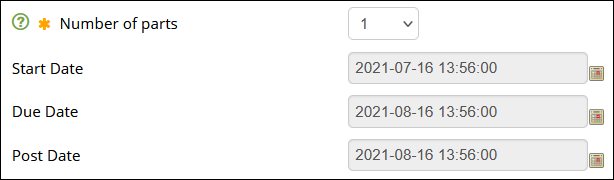
Please note that these settings are only available on the assignment creation page and not on the Modify page. If you need to change these settings after the assignment has been created, see editing Turnitin assignments .
- Leave Number of Parts set to 1
- Leave the Start Date as the default
- Click the calendar icon and extend the Due Date far enough into the future to allow students with extensions to make draft submissions
- Leave the Post Date as the default
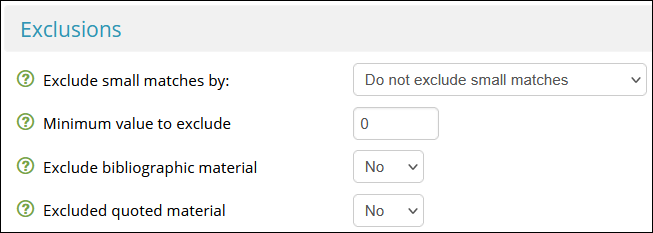
- Set Exclude small Matches by to Do not exclude small matches
- Set Minimum value to exclude to zero
- Set Exclude bibliographic material to No
- Set Exclude quoted material to No
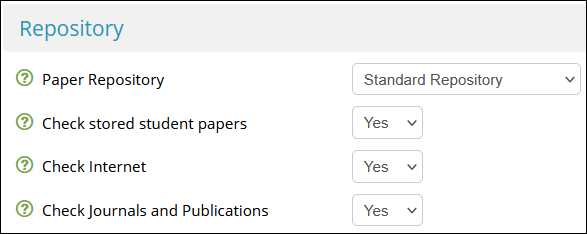
Account Specific
- Set Enable e-rater grammar check to No
- Set Use GradeMark to Yes
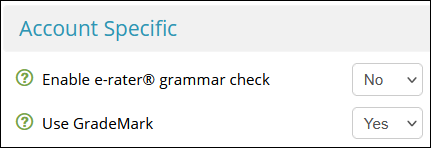
- This ensures papers uploaded to the draft submission point are not added to the repository against which future submissions are checked for similarity. As such, it mitigates the risk of papers submitted to a final submission point matching with the student's own draft submission.
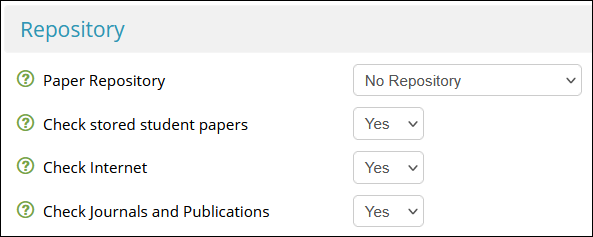
- Set Check stored student papers to Yes
- Set Check Internet to Yes
- Set Journals and Publications to Yes
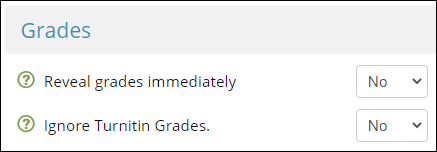
- Set Reveal Grades Immediately to No
- Set Ignore Turnitin Grades to No
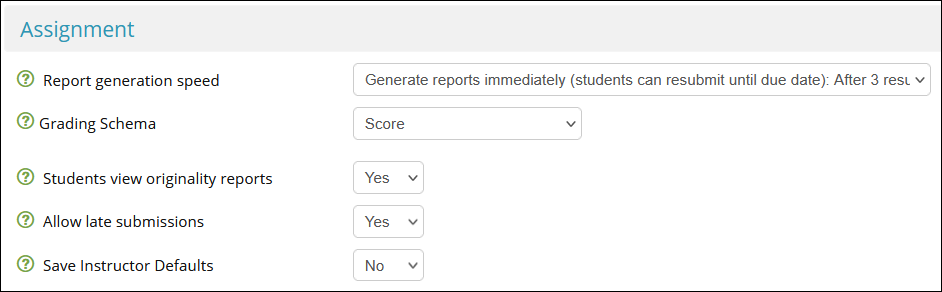
- This reduces the risk of originality reports being stuck in 'Pending' and requiring the vendor to take action
- Set Grading Schema to Score
- If this is set to No , students will not be able to view their similarity report
- This reduces the risk of students with extensions being unable to make draft submissions
- Set Save Instructor Defaults to No
Finishing up
When you are ready to create or save the assignment, click the blue Create Assignment or Update Assignment button to save the settings.
Final submission points provide students a place to submit the final version of their assignment for marking. The following settings are recommended for all Turnitin assignments set up for Final submissions, with bold text referencing the most important settings to review.
- You may want to include 'FINAL' somewhere in the title. For example, 'FINAL Lab Report Submission'.
- This will ensure your Mark Centre is configured correctly for assessment mapping during the Grade Management process.
- Click the calendar icon and set the Due Date according to the due date of the assignment
- The Post Date controls the release of marks and feedback to students. Setting this well into the future will mitigate the risk of marks and feedback being released to students prematurely. Marks and feedback can then be released by changing the Post Date once marking and moderation are complete.
- This ensures submissions are added to the repository against which future submissions are checked for similarity.
- This option allows students unlimited submissions up until the Due Date set further up the page. This setting can reduce workload on instructors as students can make resubmissions without needing to contact a member of the teaching team for assistance up until the listed Due Date. Students would still need to contact a member of the teaching team for assistance after the listed due date passes.
- This option means students only get one attempt to make a submission, regardless of whether the due date has passed or not. If a student submits the wrong file or requires a resubmission for any other reason, they would need to contact a member of the teaching team, even before the due date.
- This will ensure that marks are passed through to the Mark Centre as numbers and not ticks or letters
- This will allow students to view similarity reports for their final submissions
- This will prevent students from viewing similarity reports for their final submissions
- This will ensure students who are submitting late, either with or without an approved extension, can still submit.
- Late submissions are easily identifiable when marking because the timestamp text will be red as opposed to black for on-time submissions
- If you are creating separate submission points for on-time and late submissions, you will most likely want to set this to No for the on-time submission point and Yes for the late submission point.
Editing Turnitin assignments
Once a Turnitin assignment has been created, you can check and change its settings at any time by accessing the Modify page:
- Navigate to the folder in your course site that contains the assignment
- Click the chevron to the right of the assignment title, then click Edit
The settings can then be amended to match our recommended configuration for Draft submissions or recommended configuration for Final submissions .
Editing FAQs
Settings in assignment details part 2 (including the Start Date, Due Date and Post Date) cannot be edited from the Modify page. Instead, they can accessed and amended from the Edit Parts area:
- Click the View Assignment link below the assignment title
- Click the blue Edit Parts button
- Make any required changes
- Click the blue Update Parts button
Using Learning@Griffith site navigation
- Creating, Configuring and Editing Turnitin Assignments
- Managing Turnitin Submissions
- Turnitin Similarity Report, Marks and Feedback
Your answer may be in our list of tools . Make sure you've clicked around this website to see if your question or issue has already been addressed.
Request assistance
- You can log a Service Request with us online, using the IT support form
- Or, you can phone or email us via the IT Service Centre
Learning@Griffith specialist technical support is available Monday to Friday, 9am - 5pm. At other times, IT Service Centre staff may be able to assist you.
The Learning@Griffith Support Team provide technical support for the Learning@Griffith system. Learning Futures works in partnership with Academic and Administrative elements across Griffith to support the attainment of our Learning and Teaching goals. Visit our Training page for more information on accessing services provided by Learning Futures.
IT Service Centre
IT support chat
IT support form
Service Catalogue
Service status (availability)
(07) 3735 5555 Brisbane
(07) 5552 5555 Gold Coast
Common questions
More answers
Griffith University
Popular sites
Home > Library > Study and assignment skills > Write assignments > Assignment types
- Assignment types
Write assignments
- About the library
- Resources and borrowing
- Study and assignment skills
- Research and publishing
- Visit our libraries
- Study spaces
- Student orientation
- Staff orientation
- Corporate information
- Course resources
- Library guides
- Borrowing and my account
- Interlibrary loan
- Library catalogue help
- Library apps
- Resolve access issues
- Manage your time
- Read effectively
- Think critically
- Make effective notes
- Work in groups
- Prepare for exams
- Assess your skills
- Record and edit video
- Social media
- Effective email communication
- Understand your assessment
- Prepare to search
- Search for information
- Evaluate your sources
- Structure assignments
- Write with academic style
- Edit and proofread
- Use feedback
- AGPS Harvard
- Chicago 17 Notes and Bibliography
- Chicago 17 Author-date
- Academic integrity matters
- Manage and plan
- Find and reuse
- Create and capture
- Process and analyse
- Share and archive
- Research metrics
- Researcher profiles
- Before you publish
- Develop a publishing strategy
- Promote your research
- Engage with open research
- Make research open
- Discover open research
- Read and publish agreements
- Academic writing for researchers
- Search and find research literature
- Organise your research literature
- Literature management software
- Systematic-style reviews
- Research repository
- Guide for students
- Staff setup guide
- Add resources
- Structure reading lists
- Request digitisations
- Resources for teaching
- Workshops and eLearning
- Academic skills model
- Support for individual students
- Contact the library
Check your assignment task sheet to see the writing format required. View the various formats typically required at university.
Essays are an assessment item that can indicate your understanding of a topic. They can demonstrate how well you search for information, put ideas together in a logical sequence and write academically.
An essay can be analytical, argumentative or persuasive. You may be asked to discuss, analyse, explain, investigate, explore or review a topic. Your essay must show evidence of research, using a wide range of quality, peer reviewed academic sources.
Steps for writing an essay
Essays require a specific structure . The introduction, body and conclusion have a specific function within the writing. Check with your lecturer or tutor if you are unsure how to approach your essay.
Use the assessment task question to work out what you are required to do, and guide you with the essay format.
Do you have to compare and contrast, evaluate or discuss? These directive verbs indicate the type of essay you need to write and how to structure it.
Identify the keywords and phrases to use when searching for information around your topic.
Use the marking criteria sheet to help you decide the most important elements of the essay.
A thesis is the central argument or position around which your essay flows.
The thesis statement is placed in your essay's introduction. Each paragraph is used as evidence to support or refute the claim, and it is reiterated in the conclusion.
Edit your essay, ask yourself:
- Have I clearly introduced my thesis in the introduction?
- Have I used the body of the essay to support my thesis statement?
- Does the conclusion show how I have proven my thesis?
Use the essay paragraphs to develop your argument.
The paragraphs should:
- have a logical flow of ideas to sequentially build on the points you are making
- use evidence and examples to support your argument.
Academic arguments require balance and counterarguments. The relationships between your reasons are important to consider. A good essay should be easy to follow as it presents your thoughts in a logical manner.
Make sure that the essay answers the question, and your writing supports your thesis. Demonstrate how each piece of information included in the paragraphs is relevant. This should be easy for the reader to figure out.
Keep the question and marking criteria open while writing your essay so that you remain focused on the task. The conclusion should include a summarised answer to the question, reiterating your thesis.
Report writing is an essential skill in many disciplines. You should develop effective report writing skills because it’s highly likely you’ll be writing reports in the workplace.
A report is a formal written document used to provide concise information on a specific subject. It can be used to communicate the results of an experiment, inform on the progress of a project or to make recommendations.
An effective report is an accurate presentation of information. It should be objective, concise and structured to guide the reader through the main points.
The task instructions usually specify what sections need to be included in your report. However, a report often has the following sections:
- Title page and acknowledgements—include the title of the report, who commissioned it (or for assessment include your lecturer, course code, and student number) and the date.
- Executive summary or abstract—provide a summary of the report's main points. It briefly covers the aims, objectives, research methods and the findings. It identifies what action is required. Although the abstract is located at the beginning of the report, it is usually written last as it is a summary of the whole report.
- Table of contents—outline the structure of the report.
- Introduction—state the aims and objectives of the report, the problem or situation that prompted the report and identify what the report intends to achieve. Include definitions, research methods and background history (if relevant).
- Methodology—explain what you did and how you did it. For instance, the materials used in an experiment, the subjects involved in a survey or the steps you took in a project.
- Results or findings—detail the findings from the experiment, survey or research project.
- Discussion—present and discuss the facts or evidence.
- Conclusions—provide implications from the content of the report.
- Recommendations—describe a clear course of action. Demonstrate your professional competence in a specific situation that clearly aligns with the conclusions.
- References—acknowledge all the sources used in the report. Learn more about referencing .
- Appendices—contains additional graphical, statistical or other supplementary material. Each item should be clearly labelled (for example, Appendix 1) and referred to in the report.
A case study gives you the opportunity to apply what you are learning to a real life or fictitious case. It requires you to do further research to show how the theory applies to the practical situation.
Steps for responding to a case study
- Get a clear understanding of the case study by reading it several times.
- Make notes and consider how it relates to what you have learnt.
- Reflect on how to show your learning through your understanding of the case study.
- Identify the questions that need to be answered to address the case.
- Determine if the answers will come from the case, the literature or a combination of both.
- Research to find the answers to the questions.
- Take notes to show evidence (such as theory) to support your thinking.
- Compare your notes—from the research and case—against the marking criteria, have you addressed the required content?
- Use evidence and examples from the literature and case to support your argument in the body of the assignment.
- Avoid summarising the whole case as you will use too much of the word count.
- See how to structure your assignment to help guide you in organising your work.
Reflective writing
You may be asked to think about, or reflect upon, a situation or event that has occurred and document your feelings and reactions. For example, you may be asked to write a reflective essay on a work placement experience.
Reflective writing requires you to make a link between your experience and the course content. It’s a way of clarifying the relationship between theory and practice.
Taking time to reflect allows you to become more aware of your own values and belief system and any assumptions you may hold to support those.
Steps for reflective writing
Document the facts, what happened, when did it happen and how did it happen?
For example if writing a reflective essay on a work placement experience, include:
- tasks you completed and when
- processes or steps involved to complete the task
- why the task needed to be done
- how long it took to complete
- the challenges involved.
Record all the relevant details.
Describe what you think about the event or experience, dig deep and get in touch with your feelings.
- What emotions did you experience?
- Do you have any new insights?
- Can you make a connection with other things you know or concepts in the course?
- What were the strengths and weaknesses of the concept, process, event or procedure?
Identify what you have learnt from the experience.
- Did it change your thinking or shift your values, assumptions or opinions about the event?
- What else could you have done in the situation or event?
- Are there any actions that could have helped
- What hindered the situation?
- How will you use this information in the future?
Literature review
You may be required to write a literature review as part of your university studies.
Literature reviews can be used alone or in research projects, reports, articles and theses.
They are a way of bringing together, analysing and evaluating a range of sources in relation to a particular topic or research question.
Steps for writing a literature review
If you have a research topic, problem or question to analyse, it is important to take time to clarify what is expected before you start researching and writing.
When developing your own research topic and question, try to:
- define the general topic area
- identify the particular problem or issue you are interested in investigating
- turn the problem into questions. For example, why does this happen? How can we solve this problem? What are the main features of this issue?
- brainstorm ideas and key points.
As you get started, it is important to formulate key questions to focus your research.
To find relevant research you will need a search strategy. A search strategy is a structured organisation of terms used to search an online research tool, such as the library catalogue or databases. The search strategy shows how these terms combine in order to retrieve the best results.
Online research tools work in different ways so you need to adapt your search strategy for each one.
To develop a search strategy:
- Identify the keywords in your assessment topic.
- Identify any related words (use a dictionary, encyclopaedia or provided readings).
- Combine your keywords and related words into a search strategy using the terms AND, OR and NOT.
Enter your search strategy in the Library catalogue to find relevant literature. Identify other research tools such as library databases to find highly specialised information.
In a literature review, you are not simply recounting what each author says about a topic. You need to critically evaluate and discuss the literature to convince the reader of its relevance to your work.
Critically evaluate by questioning each item you read to assess its:
- reliability—are the facts accurate?
- credibility—is the author an authority?
- perspective—is there bias or opinion?
- purpose—does the information inform, explain or persuade?
- evidence—does the author use facts, examples, statistics, expert testimony?
There are many ways to sort and classify the literature that you are reading, including:
- thesis chapters (if applicable)
- your own categories
- theoretical perspective (for example, ‘Marxist’, ‘behaviourist’ or ‘post-modernist’)
- discipline categories
- whether it supports, or conflicts with, your thesis or central argument
- reliability.
How your review is organised depends on what information is gathered and how your discipline structures them. This is one way to organise it:
- Introduction—include your topic, aim, main ideas, overall plan, limits and scope.
- Body—include your research (where applicable), discussion of evidence, theories, concepts and relationships between different literature.
- Conclusion—bring together the key issues, trends, common threads, major gaps and agreements/disagreements in the literature.
Annotated bibliography
Writing an annotated bibliography is the first step in collecting information about a topic of interest, or to find the scope of an issue. It helps establish what current research exists, and the value or quality of that research. It allows you to gain a clearer perspective and develop critical appraisal skills.
Structure your annotated bibliography
An annotated bibliography looks like an extended reference list, it has three parts—a reference, main summary and critique.
Provide the full bibliographic details of the text—including, title, author and year—in the required referencing style.
Learn more about referencing
Each annotation is one paragraph. It retells the main points, identifying the theoretical perspectives, research findings, methods and conclusions.
Critique the text by considering the research's findings, relevancy and limitations. Give an evaluative comment about the usefulness of the research for your own work. For example:
- Is there any bias?
- Are the findings relevant to certain populations or groups?
- Does it look at an issue from a broad or narrow perspective?
- What ideas does it support or oppose?
- Is it useful in practical situations?
- How does it inform your understanding of the topic?
It is important to be concise. Limit to about 100-300 words per annotation—consult your task sheet for guidance on word length.
Eakin, E., Reeves M., Winkler E., Lawler S., & Owen, N. (2010). Maintenance of physical activity and dietary change following a telephone-delivered intervention. Health Psychology , 29 , 566-573. http://dx.doi.org/10.1037/a0021359
A randomised controlled trial was conducted and 434 patients with Type 2 diabetes or hypertension were recruited from ten primary care practices in a disadvantaged community. Five practices were randomised to a telephone-counselling intervention (n = 228) and five practices to usual care (n= 206). The aim was to examine the maintenance of behavioural changes six months after a telephone-delivered physical activity and diet intervention. Participants received 18 phone calls, a workbook with information on physical activity and healthy eating that followed the 5 A’s approach, and a pedometer. The usual care group received brief feedback on their assessment and health related brochures. The main outcome measures included the use of validated, self-report measures of physical activity and diet. Data was collected at baseline, twelve months, and 18 months (months post intervention). The findings showed both interventions were found to show significantly improved behaviour changes particularly in those who adhered to the study. The research is relevant for managing people with type 2 diabetes and hypertension living in disadvantaged communities. The researchers concluded that telephone-delivered interventions promoted maintenance of health behaviour change but studies with longer term follow-up are needed to determine how intervention duration and intensity might enhance maintenance .

Presentations—video, in-person, online
You may be asked to deliver a presentation individually, in partnership or as part of a group.
Consider the following to help inform your style, language and delivery.
- Who is the presentation targeted at or intended for?
- What do they already know on the subject?
- Why are they there?
- What would they like to know?
For example, a Business course presentation may be targeted at stakeholders, or be a pitch for potential investors.
The intention of the presentation influences the type of language, rhetorical features and tone used.
Are you pitching:
- a new service
- an idea or product
- to enlighten and inform your audience?
For example, a persuasive presentation may use more emotive language, rhetorical questions and repetition. Whereas, this approach may not be suitable for a formal report.
When, where and how will your presentation be delivered? Will it be delivered live, online or pre-recorded?
This will influence your preparations for organising the visual, environmental and technical elements, to ensure a successful presentation.
Do you need to record and edit video for your presentation?
Create an effective and engaging presentation
Regardless of the type of presentation and how it is delivered a successful presentation should take into account the following:
- Matter—does the subject and content address the task and marking criteria?
- Manner—practise the verbal (volume, pace, pause) and non-verbal (eye contact, gestures) delivery elements.
- Method—have it structured in a logical way (introduction, body, conclusion) with support of visual aids.
Visual elements
You may be asked to support your presentation with visual aids, such as PowerPoint or an infographic. Visual aids, used appropriately, can enhance your presentation and engage your audience.
Ensure your visual aids support your presentation in purpose and style and reinforce your message.
Communicate your message effectively using a simple and strategic design.
- Limit the text quantity, use three to five bullet points per slide.
- Use high resolution images and pictures.
- Limit animation and flashy transitions.
- Use contrasting colours for readability.
- Maintain continuity in text font, images and colour.
Finally, your choices should reflect the audience, purpose and context.
Practice makes perfect
Practise frequently to ensure a smooth, successful and confident presentation delivery.
- aloud—consider recording yourself to identify areas for improvement
- in front of peers and/or family
- with the technology and visuals that will be used on the day
- with your partner or group members, if relevant, to ensure smooth transition between presenters.
Academic integrity
Understand your academic integrity obligations and responsibilities to act in an honest and ethical manner.
Check out our resources
Ask the library
Common questions.
More answers
We are here to help!
Find us in the libraries or contact us by phone or online.
Request form
(07) 3735 5555
We offer online workshops on researching, referencing, structuring assignments and exam preparation. Come along and improve your skills!
Peer assisted study sessions
Attend a student facilitated group study session.
Griffith mentors study support
Get study support by connecting with a Griffith student mentor.
- myGriffith |
- Staff Portal |
Ask Us > Current student
Current students
How do i apply for an extension on an assessment (e.g. assignment).
An extension of time applies to assessment items undertaken and submitted outside of scheduled class time (e.g. an assignment).
If you are applying for an assignment extension, your application must be submitted using the online application form by the due date.
For individual assessment items, supporting documentation is not required for extensions up to and including three calendar days, unless you are enrolled in a course through Open Universities Australia (OUA)*. For group assessment, all OUA assessment and extensions greater than three calendar days your application must include appropriate documentation to support the grounds on which you are requesting your extension.
Students registered with Student Disability and Accessibility can apply for an extension on disability grounds for up to and including 10 calendar days without the requirement to provide supporting documentation.
* For students not registered with Student Disability and Accessibility, accumulation of more than three approved extensions for individual assignments of three or less calendar days will trigger the supporting documentation requirement for the remainder of the trimester, after which the count will be reset.
You can make a request for an extension of time on one of the following grounds:
- bereavement
- personal safety grounds
- other personal, professional or exceptional circumstances (e.g. family or personal circumstances, employment-related circumstances, unavoidable commitments).
- Navigate to the Assessment Application Landing page in myGriffith.
- Make the appropriate selection for your circumstances.
- Complete the application form.
- If required, attach appropriate documentary evidence to support your application. Supporting documentation may include a medical certificate, statutory declaration, bereavement notice, letter from employer or a copy of an accident report. You can find other forms of appropriate supporting documentation at Assessment Applications .
- Track your application after submitting.
Important : If you require a further extension on an already approved Assignment Extension Application, you can now do this via the online application. Further documentation to support an additional extension is required and you cannot exceed the maximum allowable extension period for the reason selected.
*If you've forgotten your login details see: I've forgotten my student ID number andor password. What do I do?

Was this answer helpful?
Answers others found helpful.
- Can I get an extension to submit my assignment (assessment) after the due date?
- How do I apply for a deferred assessment (e.g. deferred exam)?
- I missed my exam. What should I do?
- Is there a penalty if I submit my assessment (assignment) late?
- What is the difference between deferred assessment, an assignment extension and special consideration?
Answer ID: 3444
- Ask a question
- Privacy policy |
- Copyright matters |
- CRICOS Provider - 00233E
Gold Coast • Logan • Brisbane | Australia
Library Connect
Supporting your study – Assignment help
- by The Library
- posted November 21, 2023

It’s week 3 and you may have already started working on assignments, or you might be planning to start soon. If you need assistance with an assignment the Library is here to help! Here’s some tips to help you work through the different stages of completing an assignment:
Getting started
- Think about how you are going to manage your time to complete your assignments by their due dates.
- Understand your assessment by checking the course profile, task information and marking criteria.
- Break the task into questions and as you read you can take notes to answer these questions.
Researching
- Identify search terms from your topic and use search techniques to help you find the best results with these terms. You can join search terms together to create a search statement .
- Use your search statement in the Library catalogue , databases and Google Scholar .
- Check out the Library guides to find resources and databases relevant to your topic.
- Take time to evaluate your sources to ensure they are suitable to use.
Writing and referencing
- The assignment type will determine how the assignment is written and presented.
- Ensure you write with academic style and structure the assignment correctly.
- Use references in your writing and follow the formats and examples in the Referencing guides for your in-text references and reference list or bibliography.
Editing and proofreading
- Edit your work when you finish your draft and make sure you proofread your work before submitting .
If you need help at any point, you can register for a Library workshop , attend a Griffith Mentor Study Support drop-in or contact the library .

Subscribe to Library Connect via Email
Enter your email address to subscribe to this blog and receive notifications of new posts by email.
Email Address
Show posts about:
Or search via keyword:.
Privacy plan Copyright matters CRICOS Provider - 00233E TEQSA – PRV12076
Gold Coast Logan Brisbane – Australia
First Peoples of Australia
Assignment presentation formatting guidelines
To remain consistent with APA 7 th Edition conventions, ALL undergraduate written essay/report style assignments (for courses in Griffith Health programs) should be formatted using the following rules. To download a copy of these formatting guidelines and/or access an exemplar which demonstrates how your manuscript should look when following these guidelines, click on the buttons below.
Margins : 2.54 left, right, top and bottom (this is the pre-set default margin setting).
Font Type: ‘Times New Roman’.
Font Size: 12 point font only with no larger fonts used for headings (if used).
Line Spacing : Double line spacing should be used throughout the assignment and on the reference list with no additional spaces between paragraphs, assignment ‘sections’ or listed references. New paragraphs or sections are indicated by indenting of the first line of each new paragraph (see presentation formatting exemplar ).
Indenting: Each new paragraph should be indented 5-7 spaces (or one Tab space).
Justification: No justification of text on the right hand margin. Justify the left side of text in the body of essay/report against the left hand margin except for indents required for the first lines of each new paragraph (see presentation formatting exemplar ).
Page Numbers: Page numbers should be inserted in the upper right-hand side of the page header flush against the margin. Page numbers should start on the Title Page (starting at 1) and should be formatted with just the page number (see presentation formatting exemplar ).
Assignment Title: Devise a suitably descriptive assignment title to include on the title page.
Footer: Your student number is to be inserted into the footer of the document (to assist with identification of lost pages if submission errors occur).
Title Page: Include a title page with the following information only (also see presentation formatting exemplar ).
Student Name:
Essay/Report title:
Word count: (excluding title page, reference list/bibliography and appendices).
Note : Your title page will also have a page number in the header (starting at ‘1’) and your student number in the footer (see presentation formatting exemplar ).
Word Count: Word counts will comprise all text material contained within the body of the written assignment. This will include in-text citations, quotations, and any headings (if used). This will also include any information presented in tables or figures which are included within the body of the assignment in addition to your Abstract or Executive Summary (if you are required to include one). Information included outside of the main body of the assignment (e.g. university cover page, title page, reference list/bibliography, appendices) will NOT contribute to the word count.
You must adhere to the stipulated word count for your assignment. Assignments which go over this stated limit will be penalised, with the marker ceasing to read your paper once the word count has been reached.
Headings: Headings are generally used more in research reports than in essays. The following rules should be followed to format headings if used (see table below).
The above table has been adapted from the APA Style Guide to Electronic References (2012).
Note : In general, if you are using headings in an essay , you will format them using Level 2 heading guidelines. Headings in a research report will be mainly formatted as Level 1, 2, and 3 headings, however all five levels of headings can be used in research reports (depending on the size of your report and the nature of information you need to discuss in particular sections).
When using Level 1 and 2 headings, your paragraph text will commence on the next line, indented by one tab space. When using Levels 3, 4 and 5, your paragraph text will commence two spaces after the full stop at the end of the heading (i.e. continuing on the same line as the heading). See the APA Annotated Exemplars (Essay and Research Report versions) in the APA Referencing Guidelines section for examples of how to format different levels of headings and associated paragraph text.
Important Tip: When writing research reports, do not include the heading 'Introduction' at the start of your report. The heading at the start of your Introduction should be the title of the report that you have included on your title page. It should be formatted as a Level 1 heading ( see table above).
Serial Comma : APA conventions require the use of a comma between elements in a series of three or more items. This is known as a ‘serial comma’. For example:
Examining height, width, and depth indicated that ....
Use of numbers in assignment text:
· Numbers between zero and nine should be represented in words. For example:
o There were five experimental groups in the trial.
· Numbers ten and above should be represented in numerical format. For example:
o A total of 47 participants took part in the pilot test.
Privacy policy | Copyright matters | CRICOS Provider - 00233E
- myGriffith |
- Staff Portal |
Ask Us > Future student
Future students
Can i get an extension to submit my assignment (assessment) after the due date.
No, you need to:
- complete an application for an assignment extension by the due time on the due date for the assessment item (emailed requests will not be considered)
- if required, submit appropriate documentation to support your application.
Once approved, you may need to download and attach your Assessment Extension Approved Items coversheet to your assignment. This coversheet can be generated via your Assessment Application Status page.
Important: There are penalties if you have not received approval for an extension .
See also: How do I apply for an extension on an assessment (e.g.: assignment)? How do I apply for an extension on an assessment (e.g. assignment )?
Was this answer helpful?
Published answers.
- How do I apply for an extension of my higher degree by research (HDR) candidature?
- How do I apply for a late enrolment into a course (after the last date to add a course has passed)?
- My thesis was not submitted by my maximum submission date and my higher degree by research (HDR) candidature has lapsed. What can I do to complete?
- I am an international student. What happens after I submit my application to study at Griffith University?
- Will I still be able to pursue a research higher degree after completing a new Honours degree?
Answer ID: 2122
- Ask a question
- Privacy policy |
- Copyright matters |
- CRICOS Provider - 00233E
Gold Coast • Logan • Brisbane | Australia
Due: Sat May 25 11:59 pm Late submissions accepted until Sun May 26 11:59 pm
Assignment by Michael Chang & Julie Zelenski idea originated by Randal Bryant & David O'Hallaron (CMU). Modifications by Nick Troccoli, Brynne Hurst, Kathleen Creel and Jonathan Kula.
Learning Goals
This assignment focuses on understanding assembly code representations of programs. You will be building your skills with:
- reading and tracing assembly code
- understanding how data access, control structures, and function calls translate between C and assembly
- reverse-engineering
- understanding the challenges of writing secure and robust systems
- understanding privacy, trust, and the role of the ethical penetration tester
- mastering the gdb debugger!
You have been hired as a security expert for Stanford Bank (a fictional on-campus bank). They need you to investigate reports of infiltration and security issues and replicate the issues so that they can fix them.
There are three parts to this assignment, each of which can be completed independently:
- an ATM withdrawal program containing some vulnerabilities - you'll need to use your C and assembly skills to find and demonstrate how to exploit these vulnerabilities.
- A dataset that you will use to deanonymize bank users.
- The SecureVault program, a new product designed by the bank to provide increased security to the master vault. You'll be given an executable of the SecureVault program (no C code provided!) to show that it is possible to reverse engineer this program and break into the master vault without being told the passwords.
These problems are like C/assembly "puzzles" to solve, and we hope you enjoy solving them and exploring this material as much as we enjoyed creating them!
Note: check out our assignment overview video on Canvas ; it goes over the different parts of the assignment, what to expect, and tips and tricks! Note the overview video is from this quarter last year, but the assignment is the same (save for the fact that questions 2 and 3 are exchanged).
Spring 2024: Lecture 22 (Mon 5/20) is necessary to work on questions 3 and 4 in part 2 of this assignment.
A few reminders:
- The working on assignments page contains info about the assignment process.
- The collaboration policy page outlines permitted assignment collaboration, emphasizing that you are to do your own independent thinking, design, writing, and debugging. Even without any code being submitted, you should not be doing any joint debugging/development, sharing or copying written answers, sharing specific details about SecureVault behavior, etc. If you are having trouble completing the assignment on your own, please reach out to the course staff; we are here to help!
To get started on this assignment, clone the starter project using the command
View Full Starter File List
- vault : Your SecureVault executable program, custom-generated for each student.
- custom_tests : The file where you will add custom tests to reproduce vulnerabilities in the provided ATM withdrawal program.
- input.txt : A blank text file where you should add the passwords for each SecureVault level, one per line. See the section on SecureVault for more information.
- readme.txt : A file where you should add answers to short written questions for all three parts of the assignment.
- .gdbinit : A gdb configuration file you can optionally use to run certain gdb commands each time gdb launches. See the section on using GDB in SecureVault for more information.
- samples : A symbolic link to the shared directory for this assignment. It contains:
- atm : The executable ATM program, which you will explore for vulnerabilities.
- atm.c : The C source code for the ATM program, which you will explore for vulnerabilities. Note that you're not able to edit or recompile this code/executable.
- checkins.csv : A file containing public social media location check-in data for various locations on Stanford campus over the past three months.
- search_checkins : An executable program to search the check-in data.
- bank : a folder containing the following:
- customers.db : A file with the list of all users and balances for the ATM program.
- transactions.csv : A file with ATM transaction information from the past three months at the Stanford campus ATM.
- SANITY.INI and sanity.py : Files to configure and run sanity check. You can ignore these files.
- wordlist : A list of dictionary words used for SecureVault.
- tools : Contains symbolic links to the sanitycheck and submit programs for testing and submitting your work. ( codecheck is not needed on this assignment)
You will be using gdb frequently on this assignment. Here are essential resources as you work - note that you should make sure you have downloaded the CS107 GDB configuration file mentioned in the Getting Started Guide if you didn't previously do so.
Open Getting Started Guide Open GDB Guide Open Lab5 GDB Tips Open Lab6 GDB Tips
1. ATM Security
Stanford Bank recently updated the ATM software to a version with some additional features. The IT team reviewed the new code and thought it all looked good, but having now installed it in production, they are observing some suspicious activity. The bank has called you because your superior C and assembly skills are just what's needed to investigate and resolve these problems!
In the samples folder, they have provided you the code ( atm.c ) and compiled executable ( atm ), which you can examine/run but cannot recompile or edit (since they want to ensure you work with the same executable installed on the ATMs themselves). The ATM program is invoked with an amount and the credentials for a particular account. If the credential is authorized and the account has sufficient funds, the amount is withdrawn and dispersed in cash. Accounts must maintain a minimum balance of $50, and the ATM is supposed to maintain bank security by rejecting unauthorized access. Every time you run the program, it will print out information to the terminal about the transaction that took place, or the error that occurred, if any. For example, if you ask to withdraw $100 from your account balance of $107, it should be denied with an error message because that would bring your current $107 balance below the required minimum of $50. If you try to sneak cash from another account or use a fake name, your credential should get rejected as unauthorized.
Here are a few examples - try it out yourself! Note that $USER automatically acts as your SUNET ID, and every account balance is set to be $107. Also, each time you run the program anew, all balances return to their original starting levels. No money actually changes hands in this ATM, which is a blessing given its security flaws.
Expand ATM Sample Runs
The bank has identified three anomalies in the ATM program behavior that they need your help investigating. For each of the anomalies (a), (b), and (c) below, you will need to do the following:
- include a test case in your custom_tests file to showcase how to reproduce the vulnerability. Note that there may be more than one way to trigger a vulnerability.
- A concise description of the underlying defect in the code.
- An explanation of exactly how you constructed your test case to exploit it.
- Your recommendation for fixing it. The bank is not looking for a major rewrite/redesign, so in your proposed changes you should directly address the vulnerability with minimal other disruption. Note that there may be more than one possible remedy for fixing each issue. Also make sure you do not remove intended functionality of the bank program, and account for any potential additional security issues introduced by your proposed fix .
NOTE: when running your own custom tests, make sure to inspect the output to ensure your tests are causing the behavior you expect! The sanitycheck tool itself does not verify that the tests cause the specified exploits.
As you work through your investigation, you will need to review the source code for the atm program. The program is roughly 175 lines of C code of similar complexity to what you have been writing this quarter, and is decomposed and fairly readable, though sorely lacking in comments. You should find that the program's approach seems reasonable and the code is sincere in its attempt to operate correctly. As you're reading, take a minute to reflect on how far your awesome C skills have come to let you read through this provided program!
NOTE: when running the ATM program under GDB, make sure you are in the samples folder first before running gdb atm .
a) Negative Balances
A prior version of the ATM program restricted a withdrawal to be at most the full account balance, allowing the customer to drain their account to $0, but no further. The current version has changed the withdraw function to require a non-zero minimum balance. The expected behavior should be that all account balances stay above this minimum. However, the bank saw an (otherwise ordinary) withdrawal transaction that not only caused an account to go below the minimum, but also overdrew so far as to end up with a negative balance. Oops, that's definitely not supposed to happen! Review the C code for the withdraw function, specifically the changes from the old version. It seems to work in many cases, but apparently not all. Read carefully through this function to try and discover the flaw - your understanding of signed and unsigned integers will be useful here! Once you have found the vulnerability, determine a command to make a withdrawal as yourself that withdraws more money than is present in your account . Put this command in custom_tests , and answer the specified readme questions.
b) Unauthorized Account Access
The bank has also received a customer complaint about an unauthorized withdrawal from their account. It seems that another user with different credentials was able to successfully withdraw money from the aggrieved customer's account. Moreover, the credential used appears to be entirely fake - no such user exists in the database! A user should not be able to access a different customer's account and especially not by supplying a bogus credential! Review the C code for the find_account function that is responsible for matching the provided username to their account number. It seems to work properly when the username matches an existing account, but not when the username doesn't match an existing account. Trace through line by line how the function executes when called with an invalid username that is not in the database. What lines are executed? Once you do this, you'll find that the function appears to behave unpredictably. Your next task is to examine the generated assembly to determine precisely how the function will behave - your understanding of the %rax / %eax register will be useful here! Once you have found the vulnerability, determine a command with a designed bogus name credential to withdraw $40 from one of the CS107 staff member's accounts. Put this command in custom_tests , and answer the specified readme questions. (The samples/bank/customers.db file contains information about all valid users and their balances, and the first 15 users in the database are staff accounts.)
c) Accessing The Master Vault
The most worrisome issue is repeated illicit withdrawals from the master vault account, account number 0. The name on the master account is not an actual user, so this account cannot be accessed using the simple username-based credential. Instead, the user must specify two account arguments, the account's number and its secret passcode, as a form of heightened security, like this:
At first the bank thought the vault passcode had been leaked, but changing the passcode did nothing to thwart the attack. In a fit of desperation, the bank removed the vault passcode file altogether, figuring this would disable all access to the vault, yet the rogue user continues to make withdrawals from it! It seems that the high-security passcode authentication may have its own security flaw! The code that handles this authentication is in the lookup_by_number and read_secret_passcode functions. These functions work correctly in many situations, but fail in certain edge cases. Remember that it seems that in certain cases supplied credentials are accepted despite the lack of a saved passcode file . The vulnerability is subtle in the C code, so you should also use GDB to examine the code at the assembly level and diagram out the memory on the stack for these functions . This problem is similar to the stack diagramming/exploit problem from lab6 - revisit that problem if you need a refresher! Your exploit should not involve reading from any file. Once you have found the vulnerability, determine a command to withdraw $300 from the bank vault despite its disabled passcode . Put this command in custom_tests , and answer the specified readme questions.
2. Dataset Aggregation
Separate from the faulty ATM software, Stanford Bank believes that someone was able to gain access to their account logs and get a list of ATM transaction information for their Stanford campus ATM. The company believes that this poses little threat because the transaction logs have limited recorded data. However, you are concerned that this data can be combined with other available data in dangerous ways, such as to learn private information. For instance, knowing someone's history of large (or small) transactions might tell you about their financial situation; knowing memberships in clubs or organizations might tell you about social relationships and webs of networks. Your task is to combine this data with another dataset you have found of public location check-ins to show the harms of a potential data breach. To aid in investigating your concerns, the bank has made the ATM transaction data available to you in the samples/bank/transactions.csv file. This file has one account transaction per line, and each transaction occurred at the Stanford campus ATM. Each line has the following format:
For example, here is one line from the file that represents a withdrawal of $15 on 2/15/21 at 4:54PM:
Transactions with the same account identifier are guaranteed to be for the same bank account, but the identifier doesn't give any information about whose account it is (intentionally done by the bank to obfuscate the data).
You have already downloaded a publicly-available location checkins dataset from an online social network, in the file samples/checkins.csv . It is too large to read through manually, so you also already created a program search_checkins that displays that checkin data and lets you search through it more easily. Run the program ( samples/search_checkins ) for instructions on how to use it.
Show the risks of dataset aggregation and express your concerns to the bank managers by answering the following questions in your readme.txt . Note that you are not expected to create any additional programs to parse or otherwise process these datasets with code - the intent is for you to skim the transactions.csv file by hand and use it along with the search_checkins program to answer the following questions.
- a) The likely user who made multiple large transactions?
- b) Two (there may be more, but you must identify only two) likely members of the Stanford SecurityStars Club, which has a club meeting on the 15th of each month where people must bring $15 to pay their membership dues? (Assume they are procrastinators in withdrawing the money)
- How were you able to de-anonymize the transactions data?
- Beyond encrypting the data, what recommendations would you give to Stanford Bank to further anonymize or obfuscate the account data in the case of accidental data breaches?
- Use one or more of the four models of privacy discussed in lecture to explain why disclosure of the information that can be aggregated here is (or is not) a violation of privacy.
3. SecureVault
Stanford Bank is rolling out a new tool, SecureVault, to provide increased security at the master vault at each of their branches. Employees must enter four secret passwords into this program to gain access to the master vault. For extra security, the bank creates a different SecureVault program for each branch with different expected passwords; the bank headquarters does not give the source code to any of the branches; and the program triggers an alarm that notifies the central system each time an incorrect password is entered. They are confident that this means only someone who is told the password can get access, and any potential intruders will be detected by the alarm system. They have hired you to test this. Your task is to show that you can reverse engineer the program to gain access to the bank vault without being told the password, and without alerting central security.
Do not start by running SecureVault and entering passwords to "see what will happen" . You will quickly learn that what happens is the alarm goes off and it deducts points :-) When started, SecureVault waits for input and when you enter the wrong password, it will raise the alarm and notify the central system, deducting points. Thoroughly read the SecureVault information below before attempting to enter any passwords! There is a lot of information below, but it is included to help provide useful tips for you to work through this part of the assignment.
Without the original source code, all you know is that SecureVault has four "levels" of security, each with a different password. If the user enters the correct password, it deactivates the level and the program proceeds on. But given the wrong input, SecureVault raises an alarm by printing a message, alerting central security and terminating. To reach the master vault, one needs to successfully disarm each of its levels.
This is where the bank needs your help. Each of you is assigned a different generated SecureVault executable unique to you, generated just as they would be for each bank branch. Your mission is to apply your best assembly detective skills to reverse engineer the SecureVault executable to work out the input required to pass each level and reach the master vault, thus proving the insecurity of the bank's approach.
Specifically, you must fill in your input.txt file with the passwords to defuse each level in order, 1 per line, for each level you have solved. You must also answer the following questions in your readme.txt file. Make sure to verify your input.txt file (with appropriate protections!) to ensure proper formatting and that all lines are entered correctly before submitting! We will test by running ./vault input.txt on your submission, using the original SecureVault program generated for you. Here are the readme questions to work through as you go:
- What tactics did you use to suppress/avoid/disable alarms?
- level_1 contains an instruction near the start of the form mov $<multi-digit-hex-value>,%edi . Explain how this instruction fits into the operation of level_1 . What is this hex value and for what purpose is it being moved? Why can this instruction reference %edi instead of the full %rdi register?
- level_2 contains a jg that is not immediately preceded by a cmp or test instruction. Explain how a branch instruction operates when not immediately preceded by a cmp or test . Under what conditions is this particular jg branch taken?
- Explain how the loop in the winky function of level_3 is exited.
- Explain how the mycmp function is used in level_4 . What type of data is being compared and what ordering does it apply?
- How would you describe Stanford Bank’s trust model? (In other words: who among the bank headquarters, the bank branches, and you was trusted?) Justify your answer.
SecureVault Information
From the SecureVault assembly, you will work backwards to construct a picture of the original C source in a process known as reverse-engineering . Note that you don't necessarily need to recreate the entire C source; your goal is to work out a correct input to pass the level. This requires a fairly complete exploration of the code path you follow to deactivate the level, but any code outside that path can be investigated on a need-to-know basis. Once you understand what makes your SecureVault program "tick", you can supply each level with the password it requires to disarm it. The levels get progressively more complex, but the expertise you gain as you move up from each level increases as well. One confounding factor is that SecureVault raises an alarm whenever it is given invalid input. Each time the alarm goes off (except for a free pass the first time), it notifies central security (the CS107 staff) and points are deducted from your score. Thus, there are consequences to setting off the alarm -- you must be careful!
The bank has confirmed to you a few things about how the SecureVault programs operate:
- If you start SecureVault with no command-line argument, it reads input typed at the console.
If you give an argument to SecureVault, such as input.txt :
SecureVault will read all lines from that file and then switch over to reading from the console. This feature allows you to store inputs for solved levels in input.txt and avoid retyping them each time.
Alarms can be triggered when executing at the shell or within gdb. However, gdb offers you tools you can use to intercept the alarms, so your safest choice is to work under gdb and employ preventive measures.
- It is not possible to know for sure whether the central system (course staff) is notified about an alarm. You must use your investigative skills and best defensive measures!
- The central system will give you a free pass (no point deduction) the first time they are notified about an alarm.
- The SecureVault program in your repository was lovingly created just for you and is unique to your id. It is said that it can detect if an impostor attempts to run it and won't play along.
- The SecureVault program is designed for the myth computers (running on the console or logged in remotely). There is a rumor that it will refuse to run anywhere else.
- It seems as though the function names were left visible in the object code, with no effort to disguise them. Thus, a function name of initialize_vault or read_five_numbers can be a clue. Similarly, it seems to use the standard C library functions, so if you encounter a call to qsort or sscanf , it is the real deal.
- There is one important restriction: Do not use brute force! You could write a program to try every possible input to find a solution. But this is trouble because a) you lose points on each incorrect guess which raises an alarm, b) trying all possible inputs will take an eternity and risk saturating the network, and c) part of your submission requires answering questions that show you understanding of the assembly code, which guessing will not provide :)
Using tools such as gdb , objdump and new tools nm and strings is critical to effectively investigating and disarming each level. Once you are familiar with the tools at your disposal, first work to reliably prevent alarms from triggering , then proceed with disarming each of the levels .
Step 1: Familiarity with Tools
Here are some helpful tools to gather general information:
- nm : use the nm utility ( nm vault ) to print what's called the "symbol table" of the executable, which contains the names of functions and global variables and their addresses. The names may give you a sense of the structure of the SecureVault program.
- strings : use the strings utility ( strings vault ) to print all the printable strings contained in the executable, including string constants. See if any of these strings seem relevant in determining the passwords.
- gdb lets you single-step by assembly instruction, examine (and change!) memory and registers, view the runtime stack, disassemble the object code, set breakpoints, and more. Live experimentation on the executing SecureVault program is the most direct way to become familiar in what's happening at the assembly level.
- Compiler Explorer : pull up tools like the Compiler Explorer interactive website from lab, or gcc on myth , to compile and explore the assembly translation of any code you'd like. For example, if you're unsure how to a particular C construct translates to assembly, how to access a certain kind of data, how break works in assembly, or how a function pointer is invoked by qsort , write a C program with the code in question and trace through its disassembly. Since you yourself wrote the test program, you also don't have to fear it setting off any alarms :-) You can compile directly on myth using a copy of a Makefile from any CS107 assignment/lab as a starting point, and then use gdb or objdump to poke around.
GDB Suggestions
GDB is absolutely invaluable on this assignment. Here are some suggestions on how to maximize your use of gdb in addition to the tips in lab5 and lab6 :
- Expand your gdb repertoire. The labs have introduced you to handy commands such as break , x , print , info , disassemble , display , watch , and stepi/nexti . Here are some additional commands that you might find similarly useful: jump , kill , and return . Within gdb, you can use help name-of-command to get more details about any gdb command. See the quick gdb reference card for a summary of many other neat gdb features.
Get fancy with your breakpoints. You can breakpoints by function name, source line, or address of a specific instruction. Use commands to specify a list of commands to be automatically executed whenever a given breakpoint is hit. These commands might print a variable, dump the stack, jump to a different instruction, change values in memory, return early from a function, and so on. Breakpoint commands are particularly useful for installing actions you intend to be automatically and infallibly completed when arriving at a certain place in the code. (hint!)
gdb kill workaround : gdb 9.2 (current version on myth as of 04/2021) has a bug when attempting to use kill in the commands sequence for a breakpoint that creates a cascade of problems --can cause gdb itself to crash or hang. The gdb command signal SIGKILL can be used as an alternate means to kill a program from a commands sequence that doesn't trip this bug.
Use a .gdbinit file . The provided file named .gdbinit in the assignment folder can be used to set a startup sequence for gdb. In this text file, you enter a sequence of commands exactly as you would type them to the gdb command prompt. Upon starting, gdb will automatically execute the commands from it. This will be a convenient place to put gdb commands to execute every time you start the debugger. Hint: wouldn't this be useful for creating breakpoints with commands that you want to be sure are always in place when running the SecureVault program? The .gdbinit file we give you in the starter repo has only one command to echo Successfully executing commands from .gdbinit in current directory . If you see this message when you start gdb, it confirms the .gdbinit file has been loaded. If you see an error message about auto-loading .gdbinit being declined when starting gdb, this means you haven't installed the CS107 GDB configuration file - see the top of this page for instructions.
- Custom gdb commands . Use define to add your own gdb "macros" for often-repeated command sequences. You can add defines to your .gdbinit file so you have access to them in subsequent gdb sessions as well.
- Fire up tui mode (maybe...). The command layout asm followed by layout reg will give you a split window showing disassembly and register values. This layout will display current values for all registers in the upper pane, the sequence of assembly instructions in the middle pane, and your gdb command line at the bottom. As you single-step with si , the register values will update automatically (those values that changed are highlighted) and the middle pane will follow instruction control flow. This is a super-convenient view of what is happening at the machine level, but sadly, you have to endure a number of quirks and bugs to use it. The tui mode can occasionally crash gdb itself, killing off gdb and possibly the SecureVault program while it's at it. Even when tui is seemingly working, the display has a habit of turning wonky, often fixable by the refresh command (use this early and often!) but not always. A garbled display could cause you to misunderstand the program state, misidentify where your SecureVault is currently executing, or accidentally execute a gdb command you didn't intend. Any alarm suppression mechanism that requires you, the fallible human, to take the right action at a critical time could easily be waylaid by interference, so don't attempt tui before you have invincible automatic protection against alarms. Selective use of auto-display expressions (introduced in lab6) is a great alternative with less disruption. You can exit tui using ctrl-x a and re-enter it again (this doesn't require leaving gdb and losing all your state).
Step 2: General Investigation and Preventing Alarms
Once you are familiar with the tools at your disposal, your next step is to gather general information about how the SecureVault program works to figure out how to reliably prevent alarms from triggering . There are simple manual blocks that give some measure of protection, but it is best to go further to develop an invincible guard. Feel free to use any technique at your disposal, such as leveraging gdb features, tweaking the global program state, modifying your setup, tricking the SecureVault program into running in a safe manner, etc. Avoiding the alarm entirely is one straightforward approach to ensure that we won't hear about it, but there are ways to selectively disable just the transmission portion to the central system (course staff) . Once you figure how to set up appropriate protection against alarms, you will then be free to experiment with the levels without worry. Note that the program can only trigger an alarm when it is "live", i.e., executing in shell or running with gdb .
Step 3: Disarming Levels
Your next task is to approach each level individually to figure out a password that disarms it. There may be more than one password for each level; your task is to enter your 4 passwords, one per line, starting with level 1, into your input.txt file. Here are key tips for how to approach your reverse engineering exploration:
- Run the program live in GDB (with appropriate alarm protections!) and step through to better understand its behavior. Reading and diagramming the assembly by hand is useful to an extent, but quickly becomes infeasible with larger programs.
- Break the assembly into chunks. For instance, if it calls any functions, that's a good stopping point to orient yourself and understand the assembly just up to that point.
- Use gdb to verify your hypotheses. Verify key assumptions you make about the vault behavior to ensure you're on the right track. One helpful trick is you can change register contents while running gdb. E.g. if you think "I believe if %rdi stored this, it would do that", then try it! You can do p $rdi = val to change register contents mid-program. Or if you think something is a char * , cast and print it out, e.g. p (char *)$rdi .
- Document your knowns and unknowns. If you run into a situation where you are stuck due to seemingly-conflicting assumptions, document them and re-verify them. If you have multiple conflicting assumptions, at least one must not be the case.
- Use compiler explorer to see what code looks like in assembly. If you think you happened upon e.g. a loop, if statement, etc. try using compiler explorer to type in some code quickly and see what that code looks like in assembly. If it resembles the assembly you're seeing, perhaps that can help you better understand its structure.
- Use library functions to your advantage. If you spot a call to what looks like a library function, it's the real deal. Use the man page for that function to learn about what parameters it takes in, what it does, and what it returns. This can give you key information about the types of data in different registers - e.g. if you see a call to strlen , then the value put into %rdi must be of type char * , and what's stored in %rax afterwards must be a size_t string length.
- When tracing an unknown function, before dissecting its behavior first learn about the input/output of the function and what role it plays. Does it return anything? What parameters does it take in? If it has a return value, is it checked to be something in particular? Going into a function with an idea of what must be returned for you to continue with the vault can help you focus on understanding how to achieve that.
Sanity Check
The default sanitycheck test cases are ATM inputs and one test case that reports the line count of your input.txt file. This sanitycheck is configured to only allow test cases for ATM in your custom_tests file. The SecureVault executable is not run by sanitycheck.
Once you are finished working and have saved all your changes, check out the guide to working on assignments for how to submit your work. We recommend you do a trial submit in advance of the deadline to allow time to work through any snags. You may submit as many times as you would like; we will grade the latest submission. Submitting a stable but unpolished/unfinished version is like an insurance policy. If the unexpected happens and you miss the deadline to submit your final version, this previous submit will earn points. Without a submission, we cannot grade your work.
We would also appreciate if you filled out this homework survey to tell us what you think once you submit. We appreciate your feedback!
For this assignment, here is a tentative point breakdown (out of 119):
- custom_tests (24 points) Each successful attack test case earns 8 points. We will test by running tools/sanitycheck custom_tests on your submission. Your custom_tests should contain 3 test cases, one for each ATM attack.
- readme.txt (55 points) The written questions will be graded on the understanding of the issues demonstrated by your answers and the thoroughness and correctness of your conclusions.
- Input.txt (40 points) Each SecureVault level you have solved earns 10 points. We will test by running ./vault input.txt on your submission. The input.txt file in your submission should contain one line for each level you have solved, starting from level 1. Malformed entries in your input.txt or wrong line-endings will cause grading failures. To avoid surprises, be sure that you have verified your input.txt in the same way we will in grading (i.e., ./vault input.txt ).
- SecureVault alarms triggered (up to 6 points deducted) Each alarm notification (beyond the first one) that reaches the staff results in a 1 point deduction, capped at 6 points total.
Post-Assignment Check-in
How did the assignment go for you? We encourage you to take a moment to reflect on how far you've come and what new knowledge and skills you have to take forward. Once you finish this assignment, your assembly skills will be unstoppable, and you will have a better understanding of trust, privacy and security! You successfully found vulnerabilities in a program using its source and assembly, and reverse engineered a complex program without having access to its source at all. Rock on!
To help you gauge your progress, for each assignment/lab, we identify some of its takeaways and offer a few thought questions you can use as a self-check on your post-task understanding. If you find the responses don't come easily, it may be a sign a little extra review is warranted. These questions are not to be handed in or graded. You're encouraged to freely discuss these with your peers and course staff to solidify any gaps in you understanding before moving on from a task.
- What are some of the gdb commands that allow re-routing control in an executing program?
- What is the main indication that an assembly passage contains a loop?
- What makes someone a trustworthy fiduciary or guardian of personal data? How and why should an institution like a bank protect the privacy of its customers?
- Explain the difference between a function's return value and its return address.
- Consider the mechanics of function pointer work at the assembly level. How is a call through a function pointer the same/different when compared to an ordinary function call?
- For performance reasons, the compiler prefers storing local variables in registers whenever possible. What are some reasons that force the compiler to store a local variable on the stack instead?
- For the instruction sequence below, what must be true about values of op1 and op2 for the branch to be taken? What changes if ja is substituted for jg ? cmp op1,op2 jg target
- International
- Today’s Paper
- Premium Stories
- ⏪ Election Rewind
- Express Shorts
- Health & Wellness
- Brand Solutions
IGNOU June 2024 TEE: Assignment submission deadline extended till May 31
Ignou assignment's last date 2024 has been extended for odl and online programmes for the june tee session. the university will now accept assignments (both hard copy and soft copy) till may 31, 2024..
IGNOU TEE assignment submission 2024: The Indira Gandhi National Open University (IGNOU) has extended the assignment submission last date for ODL and online courses. Now, students can submit their assignments both in soft and hard copies by May 31.
Candidates enrolled in ODL, online programmes, GOAL, and EVBB for the June 2024 TEE can submit their projects, dissertations, practical files, and internship reports online at the official website – ignou.ac.in, the open university said in an official notification.

However, students are suggested to submit the assignment before the last date to avoid last minute rush. Students must note that the IGNOU assignment submission last date 2024 is common for all programmes irrespective of admission year, mode or programme.
Candidates are required to attach a copy of the fee receipt with the project report at the time of submission of hardcopy or by uploading it to the online portal.
IGNOU June TEE 2024: Steps for assignment submission
Step 1: Go to the official website – ignou.ac.in

Step 2: Navigate to the assignment submission link available on the homepage
Step 3: Login using the necessary credentials in the designated field
Step 4: Upload the scanned assignment with the respective code
Step 5: Submit the assignment
Step 6: Students are advised to take a screenshot of the assignment submission receipt for further reference
“With the approval of the competent authority, the last date for submission of assignments (both in hard copy and soft copy) for term end examination, June 2024 for both ODL and online programmes, GOAL and EVBB has been extended up to May 31,” read the notification.
The IGNOU has stared the fresh admission cycle for undergraduate, postgraduate, and other programmes for the July 24 academic year. The last date to apply for the various programmes at IGNOU is June 30. The university offers certificates, diplomas, advanced diplomas, postgraduate diplomas, and degrees. The University is offering more than 290 UG, PG, PG diploma, diploma, certificate and awareness programmes through ODL and online mode.
Sponsored | Sharpen Your CTO Edge: Master Strategy, Leadership, and Innovation at ISB Executive Education's CTO Programme

Coconut water, derived from young coconuts, is a trendy option for hydration and wellness. With high levels of electrolytes, it's an ideal post-workout beverage. It may also aid in managing blood pressure, enhancing heart health, and supplying antioxidants. While diabetics should be cautious, pregnant women can reap its advantages.
- Maharashtra Board SSC HSC Result 2024 Live Updates: Results soon? Here's what official website says 9 hours ago
- Lok Sabha Election 2024 Phase 4 Voting Highlights: Over 62% polling recorded till 8 pm today; with over 35%, Srinagar witnesses highest turnout in 2 decades 9 hours ago
- Lok Sabha Election 2024 Live Updates: 'Bengal CM, under pressure from Muslim fundamentalists, is defaming, abusing our saints to get votes,' says PM Modi 10 hours ago
- RBSE 10th, 12th Result 2024 Live Updates: RBSE Science, Commerce and Arts result tomorrow at 12:15 10 hours ago
Best of Express

Buzzing Now

May 19: Latest News
- 01 Search on for boy who drowned in Poicha
- 02 Communal, personal attacks indicate mandate going against BJP: Sharad Pawar
- 03 Manthan at Cannes – Amul model is India’s gift to the world: GCMMF MD Jayen Mehta
- 04 ‘Ice cream man of India’ Raghunandan Kamath dies at 70
- 05 Thailand Open: Satwik-Chirag banking on ‘a special bond’ with Bangkok as they reach yet another final
- Elections 2024
- Political Pulse
- Entertainment
- Movie Review
- Newsletters
- Web Stories

IMAGES
VIDEO
COMMENTS
Select a submission type, e.g. Upload to upload a file from your computer (either via selecting the Choose a file to upload or dragging and dropping the file from your computer). Once uploaded, your file will be saved as an assignment submission draft. When you are ready to submit your assignment, click the Submit Assignment button.
To provide a resubmission for an individual assignment: Navigate to Mark Centre. Click the chevron (down arrow) in the cell corresponding to the student's submission. Click View Mark Details. Click the grey Ignore Attempt button on the right-hand side for the relevant attempt. This will allow a new submission to be made while retaining a record ...
To apply. Review the Assessment Applications page for the application requirements. Navigate to the Assessment Application Landing page in myGriffith. Make the appropriate selection for your circumstances. Complete the application form. If required, attach appropriate documentary evidence to support your application.
Final submission points provide students a place to submit the final version of their assignment for marking. The following settings are recommended for all Turnitin assignments set up for Final submissions, with bold text referencing the most important settings to review. Assignment Details part 1. Enter an Assignment Name in the box provided
Essay. Essays are an assessment item that can indicate your understanding of a topic. They can demonstrate how well you search for information, put ideas together in a logical sequence and write academically. An essay can be analytical, argumentative or persuasive. You may be asked to discuss, analyse, explain, investigate, explore or review a ...
Track your application after submitting. Important: If you require a further extension on an already approved Assignment Extension Application, you can now do this via the online application. Further documentation to support an additional extension is required and you cannot exceed the maximum allowable extension period for the reason selected.
In particular keep an eye out for the assignment type. Break the assignment down into manageable pieces: Make time for researching, writing and editing your assignment. Breaking your assignment into manageable pieces and setting deadlines for each element helps you feel a sense of accomplishment and keeps you motivated to keep going.
The assignment type will determine how the assignment is written and presented. Ensure you write with academic style and structure the assignment correctly. Use references in your writing and follow the formats and examples in the Referencing guides for your in-text references and reference list or bibliography. Editing and proofreading
To remain consistent with APA 7 th Edition conventions, ALL undergraduate written essay/report style assignments (for courses in Griffith Health programs) should be formatted using the following rules. To download a copy of these formatting guidelines and/or access an exemplar which demonstrates how your manuscript should look when following these guidelines, click on the buttons below.
complete an application for an assignment extension by the due time on the due date for the assessment item (emailed requests will not be considered) if required, submit appropriate documentation to support your application.
A few reminders: The working on assignments page contains info about the assignment process.; The collaboration policy page outlines permitted assignment collaboration, emphasizing that you are to do your own independent thinking, design, writing, and debugging. Even without any code being submitted, you should not be doing any joint debugging/development, sharing or copying written answers ...
IGNOU TEE assignment submission 2024: The Indira Gandhi National Open University (IGNOU) has extended the assignment submission last date for ODL and online courses. Now, students can submit their assignments both in soft and hard copies by May 31. Candidates enrolled in ODL, online programmes, GOAL, and EVBB for the June 2024 TEE can submit their projects, dissertations, practical files, and ...
Stephanie Griffith of CNN Opinion curated the thoughts of seven people who are still on the job, including the 101-year-old Dr. Howard Tucker, a neurologist who teaches medical students in Cleveland.