Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals

Environmental studies articles from across Nature Portfolio
Latest research and reviews.
Developing countries can adapt to climate change effectively using nature-based solutions
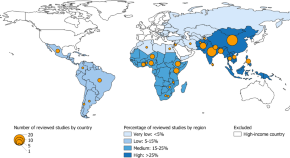
Nature-based solutions can reduce the immediate risks and impacts of climate change in coastal areas and increase adaptive capacity in the agricultural sector in low- and middle-income countries, according to a systematic review of 363 empirical studies.
- Sergio Villamayor-Tomas
- Alexander Bisaro
- Martin Noltze
Balancing protection and production in ocean conservation
- John N. Kittinger
- Randi D. Rotjan
- Constance Rambourg
Floating photovoltaics may reduce the risk of hydro-dominated energy development in Africa
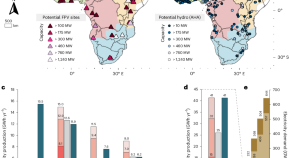
A new study finds that strategically integrating floating solar panels on reservoirs could substitute 20–100% of Africa’s planned hydropower by 2050. For the Zambezi watercourse, this approach generates a more stable electricity supply compared with hydro-dominated development.
- Wyatt Arnold
- Matteo Giuliani
- Andrea Castelletti
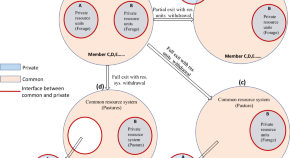
Between commons and anticommons: a nested common-private interface framework
- Carol Kerven
The development, shortcomings and future improvement of punitive damages for environmental torts in China—a reflection and comparative research
- Rongzhao Zhang
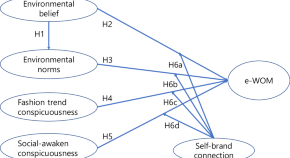
Environmentally sustainable fashion and conspicuous behavior
- Sae Eun Lee
- Kyu-Hye Lee
News and Comment
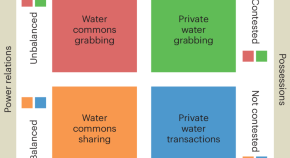
Water commons grabbing and (in)justice
Water commons are water resources collectively managed and utilized by communities as common property to support their food security, traditions, and livelihoods. Water commons are under increasing pressure of acquisition, privatization, and grabbing. This Comment analytically defines the water commons, examines their vulnerability to grabbing, and discusses the associated water justice and environmental implications.
- Paolo D’Odorico
- Jampel Dell’Angelo
- Maria Cristina Rulli

When will the BBNJ Agreement deliver results?
A new international agreement on the conservation and sustainable use of marine biodiversity of areas beyond national jurisdiction (BBNJ) was adopted and subsequently opened for signature in September 2023. Yet on average, recent multilateral environmental agreements (MEAs) have taken over four years to move from signature to entry into force, while ocean-focused MEAs have taken nearly twice as long. Rapid ratification of the BBNJ Agreement is crucial for multiple reasons, not least to achieve the Kunming-Montreal Biodiversity Framework target for 30% of the marine environment to be protected by 2030. It is also vital to fulfill the Agreement’s stated ambition to contribute to a just and equitable future for humankind, considering today’s unprecedented expansion of commercial activities into the ocean.
- Robert Blasiak
- Jean-Baptiste Jouffray

Restoration as a meaningful aid to ecological recovery of coral reefs
Restoration supports the recovery of ecological attributes such as cover, complexity, and diversity to slow the areal decline of natural ecosystems. Restoration activity is intensifying worldwide to combat persistent stressors that are driving global declines to the extent and resilience of coral reefs. However, restoration is disputed as a meaningful aid to reef ecological recovery, often as an expensive distraction to addressing the root causes of reef loss. We contend this dispute partly stems from inferences drawn from small-scale experimental restoration outcomes amplified by misconceptions around cost-based reasoning. Alongside aggressive emissions reductions, we advocate urgent investment in coral reef ecosystem restoration as part of the management toolbox to combat the destruction of reefs as we know them within decades.
- David J. Suggett
- James Guest
The Global Biodiversity Framework’s ecosystem restoration target requires more clarity and careful legal interpretation
- Justine Bell-James
- Rose Foster
- James A. Fitzsimons
Cities committed to climate action despite COVID-19
How did the COVID-19 pandemic affect urban climate actions worldwide? A study now finds that although the climate commitments of most cities persisted, low engagement in green recovery interventions can hamper long-term goals.
- Daniel Lindvall

Particulate matter sampling to assess air pollution
Lisbett Materano highlights how urban dust samples can be used to identify environmental and health risks from air pollution.
- Lisbett Susana Materano-Escalona
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
News and views for the UB community
- Stories >
UB chemist studying environmental pollutants receives national awards
Your colleagues

Emanuela Gionfriddo (center) with her students, from left, Aghogho A. Olomukoro, Charutha Dassanayake, Héctor Martínez-Pérez-Cejuela, and Madison Williams. Photo: Meredith Forrest Kulwicki
By JACKIE HAUSLER
Published April 25, 2024
Emanuela Gionfriddo, associate professor in the Department of Chemistry, has been recognized for her scientific accomplishments with two national awards: the Rising Star in Measurement Science from the American Chemical Society (ACS) and the Young Investigation Award (YIA) from the Chinese American Chromatography Association (C.A.C.A.)
Gionfriddo’s research centers on analytical chemistry, which focuses on measuring chemicals and developing new methodologies to increase the precision of measurements. Her research is largely funded by the National Science Foundation (NSF); over the course of her brief career, she already has published more than 60 articles in peer-reviewed publications, and holds a patent.
Her team works to develop miniaturized separation technologies that use minimal amounts of toxic chemicals and produce limited laboratory waste, promoting “green” and environmentally friendly analytical chemistry practices that are critical for resource conservation and minimizing the impact on the environment.
“We focus on developing methods to separate and identify different substances in complex chemical mixtures,” says Gionfriddo, who joined UB in January as part of the university’s historic “Advancing Top 25: Faculty Hiring” initiative. “Then, we use our methods to measure and understand how emerging pollutants spread in the environment, how they reach living organisms and how they distribute in the body. By applying our methodologies to biological tissues and biofluids, we aim to elucidate the chemical relationship between environmental exposure and disease.”
The ACS recognizes early-career scientists from across the globe who are “making significant contributions to the field of measurement science.” Gionfriddo’s work was included in a special issue of ACS Measurement Science Au that also highlights 19 other outstanding researchers from across the globe, selected from a pool of more than 300, showing the diversity in the field of measurement science. Her research featured in the journal is titled, “Enhancing Quantitative Analysis of Xenobiotics in Blood Plasma through Cross-Matrix Calibration and Bayesian Hierarchical Modeling.”
Similarly, C.A.C.A.’s Young Investigation Awards are “selected annually to recognize outstanding scientists who have contributed exceptionally to the development of separation science and its applications.” This is the inaugural award for the category.
“These awards recognize the effort of my research group at the national and international levels, and this makes me very proud of the team of scientists I am mentoring,” says Gionfriddo. “Our research necessitates high levels of precision, which is not always straightforward to obtain,” she adds. “These awards definitely pay off for the hard work that went into publishing our findings.”
Gionfriddo is no stranger to such recognition. She received the 2023 LCGC Emerging Leader in Chromatography Award; the 2023 Eastern Analytical Symposium Young Investigator Award; and the 2022 ACS Analytical Division Satinder Ahuja Award for Young Investigators in Separation Science.
She is also one of the founding members of the Nina McClelland Laboratory for Water Chemistry and Environmental Analysis at the University of Toledo and was appointed to the Ohio Attorney General’s Environmental Council of Advisors. She serves as chair-elect of the ACS Analytical Chemistry Subdivision on Chromatography and Separation Chemistry.
In addition to her research and accomplishments in the field, her team is active in outreach activities aimed at promoting participation of young women and underrepresented minorities in STEM fields.
Last year she founded “Girls in STEM, Together we CHEM,” “where we provide young women with exposure to STEM opportunities,” says Gionfriddo. “Witnessing individuals like themselves achieve success in STEM fields, as well as opportunities to have hands-on experience in a scientific setting, can profoundly influence young women’s aspirations, empowering them to challenge damaging stereotypes and overcome anxieties.” She hopes to resume this program at UB this summer.
Gionfriddo earned a bachelor’s degree, master’s degree and PhD in chemistry from the University of Calabria in Italy. She then joined the University of Waterloo (Ontario, Canada) as a postdoctoral fellow and manager of the Gas-Chromatography section of the Industrially Focused Analytical Research Laboratory (InFAReL). She joined the UB faculty in January 2024.
share this!
April 23, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
trusted source
written by researcher(s)
Ecosystems are deeply interconnected—environmental research, policy and management should be too
by Rebecca Gladstone-Gallagher, Conrad Pilditch and Simon Francis Thrush, The Conversation
Why are we crossing ecological boundaries that affect Earth's fundamental life-supporting capacity? Is it because we don't have enough information about how ecosystems respond to change? Or are we unable, even unwilling, to use that information better?
We have a lot to learn still, but as we show in our research , using current ecological knowledge more effectively could deliver substantial environmental gains.
Our work focuses on improving links between research and ecosystem management to identify key trigger points for action in a framework that joins land, freshwater and sea ecosystems.
Specifically, we investigate solutions to environmental and societal problems that stem from the disparities between scientific research , policy and management responses to environmental issues.
We need managers and policy makers to consider ecological tipping points and how they can cascade though ecosystems from land into rivers and lakes and, ultimately, the ocean.
Our work's standing among global research aimed at stopping ecosystem collapse has been recognized as one of 23 national champions in this year's Frontiers Planet Prize .
More holistic solutions
This issue came into focus when New Zealand set up research collaborations known as national science challenges a decade ago to solve "wicked" social and ecological problems.
The challenges focused on environmental issues were deliberately created to concentrate on separate ecosystem and management domains (marine, freshwater and land). But all included research groups addressing ecological tipping points.
This was our inspirational spark. Our research highlights the consequences of managing land, freshwater and sea ecosystems in socially constructed bubbles. We focus on solutions where social and ecological connections are at the forefront of environmental management practices and decisions.
An example is the movement of pollutants such as microplastics from the land to the sea. Most of the microplastics found along coasts and in harbors are blown or washed off the land. While this pollution is a well recognized environmental threat to the marine environment , we have not yet focused on strategies to reduce the load.
Our work points to the ignored but critical issue that people's impacts on land accumulate in the sea, but land management and consequent actions are not informed by these far-field effects.
This leads to lags in decision making which create undesirable environmental outcomes that are difficult to return from. But if we act on these connections, the environmental gains could be substantial.
Cyclones as a real-world example
As a result of massive soil erosion on the east coast of the North Island during Cyclone Bola in 1988, steep hillsides were retired from grazing and converted to pine plantations to help stabilize the land.
Fast forward three decades and a large proportion of the forest reached harvest at the same time. The exposed soil associated with clear felling was left draped in woody debris to protect it from rain.
However, Cyclone Gabrielle hit in February last year, with extreme rainfall washing both soil and woody debris into streams.
This destroyed habitats, transported vast amounts of silt and wrecked lowland farms, orchards and critical infrastructure. The debris also clogged harbors and coastal beaches, smothered seafloor habitats, destroyed fisheries and affected cultural and recreational values.
This real-world example demonstrates the severe consequences of lags in information flow and management responses. If land-use management decisions had considered the effects on other connected ecosystems and the potential for climate change to intensify those connections, the outcomes could have been different.
We could have implemented more diverse strategies in land use and put emphasis on restoring native forest and coastal wetlands.
Living with nature, not off it
Our vision is one where social and ecological connections across ecosystem domains are at the forefront of moving to a more sustainable future.
Living within planetary boundaries requires a paradigm shift in behaviors, including the way we link science and management to on-the-ground action. Crucially, we need to increase the speed at which new research is taken up and rapidly transition this into action that improves environmental outcomes at local scales.
This behavioral shift underpins the way to a more integrated, broad-scale ability to act and stay within planetary boundaries.
Our research shows we can, with trust and open minds, transcend the disciplinary silos to support new forms of research organization. The challenge now is to extend holistic approaches into new practices.
This means identifying opportunities where connected research can alter behaviors across society, from individuals to global finance and governance. Central to this transition is recognizing we are part of complex social and ecological systems and our actions have indirect effects and long-term consequences.
We need new research to provide this evidence. It will inevitably lead to new questions about fundamental ecological and integrated Earth processes.
We believe these holistic approaches will allow science to be more readily incorporated into decision making and ensure environmental perspectives are captured. This will lead to relevant, locally appropriate, integrated and robust environmental management actions.
Provided by The Conversation
Explore further
Feedback to editors

How much trust do people have in different types of scientists?

Scientists say voluntary corporate emissions targets not enough to create real climate action

Barley plants fine-tune their root microbial communities through sugary secretions

A shortcut for drug discovery: Novel method predicts on a large scale how small molecules interact with proteins

Yeast study offers possible answer to why some species are generalists and others specialists

Cichlid fishes' curiosity promotes biodiversity: How exploratory behavior aids in ecological adaptation

Climate change could become the main driver of biodiversity decline by mid-century, analysis suggests

First-of-its-kind study shows that conservation actions are effective at halting and reversing biodiversity loss

Deer are expanding north, and that's not good for caribou: Scientists evaluate the reasons why

Warming Arctic reduces dust levels in parts of the planet, study finds
2 hours ago
Relevant PhysicsForums posts
Large eruption at ruang volcano, indonesia.
Apr 23, 2024
Unlocking the Secrets of Prof. Verschure's Rosetta Stones
Apr 22, 2024
Tidal friction and global warming
Apr 20, 2024
Iceland warming up again - quakes swarming
Apr 18, 2024
M 4.8 - Whitehouse Station, New Jersey, US
Apr 6, 2024
Major Earthquakes - 7.4 (7.2) Mag and 6.4 Mag near Hualien, Taiwan
Apr 5, 2024
More from Earth Sciences
Related Stories

A new framework for customized marine conservation in local contexts
Aug 31, 2023

Planning at multiple scales for healthy corals and communities
Study shows impacts of invasive species transcend ecosystem boundaries
Apr 4, 2024

New Zealand government wants to fast-track approvals of large infrastructure projects. That's bad news for biodiversity
Mar 19, 2024
Assessment of China's protected areas needs refining, study finds
Feb 23, 2024

Our oceans are in deep trouble—a 'mountains to sea' approach could make a real difference
Jun 7, 2023
Recommended for you

Study says it's likely a warmer world made deadly Dubai downpours heavier
3 hours ago

Cocaine is an emerging contaminant of concern in the Bay of Santos (Brazil), says researcher
Study shows the longer spilled oil lingers in freshwater, the more persistent compounds it produces

New research confirms plastic production is directly linked to plastic pollution
Apr 24, 2024
Let us know if there is a problem with our content
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Phys.org in any form.

Newsletter sign up
Get weekly and/or daily updates delivered to your inbox. You can unsubscribe at any time and we'll never share your details to third parties.
More information Privacy policy
Donate and enjoy an ad-free experience
We keep our content available to everyone. Consider supporting Science X's mission by getting a premium account.
E-mail newsletter
Climate and environmental justice have left us better off. This Earth Day, let’s celebrate that success.
Subscribe to planet policy, manann donoghoe manann donoghoe senior research associate - brookings metro @manannanad.
April 22, 2024
When researchers, policymakers, and activists talk about climate, they are increasingly using terms such as “justice” and “equity.” These terms are now pervasive enough to appear in documents from groups as diverse as Extinction Rebellion , the United Nations , and Deloitte . But recent polling has found that relatively few Americans know what “climate justice” actually is.
With increasing claims of “greenwashing” directed at corporate America—and some state leaders fighting federal actions to advance climate justice—this Earth Day, it’s worth taking a closer look at climate and environmental justice (CEJ). When deployed in public policy and civic action, CEJ concepts can reveal the links between placed-based social injustices, climate impacts, and pollution, as well as offer pathways to inclusive and ultimately effective climate policy.
What is climate and environmental justice?
According to organizations such as the Intergovernmental Panel on Climate Change and Environmental Protection Agency (EPA) , climate and environmental justice is about ensuring that all people and communities are provided the support, resources, and opportunities they need to thrive under an unstable climate. It means that individuals—regardless of race, ethnicity, income, gender, age, sexuality, ability, or location—can share in the benefits and opportunities created by climate and environmental policies, such as community investment, green jobs, and access to renewable energy. It also means that the unequal burdens of climate impacts and pollutants are minimized.
CEJ is closely related to the environmental justice movement, which Robert D. Bullard and others founded in the late 1980s and early 1990s after documenting highly unequal distributions of toxic pollutants across racial groups in the U.S. South. It’s deeply connected to concepts such as environmental racism and sacrifice zones , which attempt to identify how harmful developments are unfairly concentrated in majority-Black and other historically marginalized communities. It is also associated with movements such as that for climate reparations , which combine climate justice with racial justice, reparations, and decolonization movements.
In the most basic sense, CEJ is about the equitable distribution of costs and benefits between demographic groups, regions, occupations, and sectors. But achieving that equitable distribution often requires addressing the lingering legacies of policies rooted in structural racism, such as residential segregation. This means asking questions such as: Which groups are included in decisionmaking processes that affect local land use? Who’s at the table when the plans for a new development are drawn up? How have historic policies shaped the flow of capital and resources across groups and regions? Who has a stake in the ownership of public assets like electricity utilities?
These are important questions to ask, because the current pattern of climate impacts and vulnerabilities within the U.S. is highly inequitable. That’s not a moral claim, but a statement of fact. A plethora of studies demonstrate that communities of color are more likely to be located in areas with a lack of green space and parklands, hotter heat waves , less affordable electricity , and lower rates of compensation after climate-related disasters. These disparities mean that as the impacts of climate change intensify, they’re likely to drive a wedge in health, wealth, and well-being between demographic groups, thus worsening the existing gaps in these areas.
Climate and environmental justice gains in 2023 are shaping policy
After decades of pressure by activists and civic organizations, Americans are seeing the benefits of CEJ. Below are just a handful of highlights from 2023 that demonstrate how government agencies and civic organizations have applied CEJ approaches to advance more effective and equitable climate and environmental policy, from the local to international level.
Human- and civil-rights-based arguments have gained traction in litigation
In 2023, coalitions of activists, citizens, and academics used human- and civil-rights-based arguments to win environmental protections for some states and communities. These successes set precedents that can inform future litigation strategies. In August, a coalition of young Montanans sued their state, arguing that it had contravened their constitution by favoring the fossil fuel sector over the health of residents and the environment. While the U.S. has the highest rate of climate litigation internationally, few of these cases make it to trial. This was the first time a U.S. court declared that laws barring state agencies from considering the links between climate change and fossil fuel projects were unconstitutional.
In another U.S. first, the UN declared that the DuPont and Chemours factories in Fayetteville, N.C. violated international human rights by knowingly polluting the lower Cape Fear River Basin for decades with the “forever chemical” PFAS . The declaration came after a local citizens group—Clean Cape Fear, with the assistance of the University of California, Berkeley Environmental Law Clinic— filed a complaint with the UN accusing the companies of withholding toxicity data that clearly demonstrated disparate impacts on residents.
In the past, litigators have not been able to successfully use rights-based arguments; for example, the EPA has been burdened under legal challenges when they’ve attempted to enforce civil rights . Yet the above successes demonstrate a growing momentum around linking environmental injustices to human and civil rights.
The Biden administration’s CEJ policies are taking effect
Justice and equity have been a pillar of the Biden administration’s approach to climate and environment policies. Over 2023, these policies started to take effect in tangible ways. The Greenhouse Gas Reduction Fund , designed to enable low-income and historically marginalized communities to benefit from climate investments, has mobilized $14 billion to establish national clean financing institutions that provide affordable financing for energy projects in marginalized communities; issued $6 billion for technical assistance hubs that build capacity in communities for more effective climate infrastructure projects; and solicited notices of intent for $7 billion in solar investments in low-income and disadvantaged communities. Moreover, the EPA set stronger standards for local air quality, including soot pollution and methane emissions from the oil and gas sector, which are likely to directly improve the health of residents living alongside high-emitting industrial facilities.
The administration has also taken steps to embed CEJ across functions of government by releasing the National Climate Resilience Framework and establishing a White House Environmental Justice Advisory Council and Environmental Justice Interagency Council .
Disaster relief got an overhaul
After years of research showing failures in the ways that the Federal Emergency Management Agency (FEMA) distributes disaster relief (including our own research on the subject ), the agency made extensive changes to their processes.
Many of these changes are likely to directly make disaster relief more equitable. One of the most notable—increasing the flexibility of individual assistance—will get relief to people sooner, provide displacement assistance, and automatically provide $750 for basic needs. Other changes, such as expanding eligibility for assistance and simplifying the notoriously complicated individual assistance application process, will reduce the barriers to accessing relief and get funds to more families quicker.
Chicago launched a bold plan to advance environmental justice
Chicago’s EJ Action Plan Report , released in December 2023, is perhaps the most comprehensive city plan yet in attempting to remedy historic environmental injustices. The report details a plan to target resources toward newly designated “environmental justice neighborhoods” identified in the city’s Cumulative Impact Assessment . These neighborhoods—representing roughly 30% of census tracts across the city—rank high in cancer-causing pollutants and diesel emissions, are proximate to industrial facilities, and have demographic factors associated with vulnerability, such as high asthma and heart disease rates, low incomes, high housing stress, and a high proportion of non-white residents.
The action plan’s proposals are far-ranging and practical, including updating zoning regulations to offer greater protections to over-polluted and marginalized communities; placing air quality monitors in these neighborhoods to improve the enforcement of pollution standards; and creating a fund to invest in amenities that improve residents’ long-term health and well-being. The city’s next step will be to enshrine the action plan into city ordinances later this year. This is no small task, and Chicago’s progress may set a new standard for municipal environmental justice policies.
The international community has moved closer to phasing out fossil fuels
While many in the CEJ community were rightly disappointed at the outcomes of COP28—the largest global forum to negotiate national commitments to take climate action—the final agreement was the first to agree to “transition” away from fossil fuels. The U.S. also pledged to support “largely” phasing out fossil fuels, signaling the administration’s movement toward formally adopting this stance.
Committing to phase out fossil fuels in the U.S. would not only help to mitigate climate impacts, but it would also directly benefit those living amid the industry’s local pollutants. A 2022 study estimated that nearly 14 million Americans across 236 counties lived in areas with an increased cancer risk because of air pollution emitted by oil and gas extraction. And even more Americans live alongside refineries and other industrial processes that are further down the oil and gas supply chain.
The decision to include the phrase “transition away from fossil fuels” in the COP28 agreement comes after sustained pressure on the international community from civic organizations and nations facing pronounced or existential climate threats. One example is the fossil fuel non-proliferation treaty —somewhat of a parallel to the nuclear non-proliferation treaty of 1970—which continues to gain influence. Several countries have agreed signed the treaty, including Colombia and Vanuatu, as have cities and subnational and civil society organizations. In the U.S., cities and states including California, Maine, and Austin, Texas have signed the treaty.
The CEJ movement has been focused on prevention—now it needs to shift toward building
In 2022, 71% of Americans said their community had experienced an extreme weather event. In this sense, climate impacts are an equalizer, with a unifying quality that crosses ideological, class, and racial divides. Yet current policy gaps and a history of unaddressed inequities mean that the threshold for a disaster is a lot lower for some households than others. These disparities turn climate change into a dividing force.
The actions and policies above show how CEJ can overcome these divisions by building new and more equitable policy structures. Pioneers of the CEJ movement developed its focus around prevention issues such as stopping high-polluting industrial developments in low-income neighborhoods. While prevention is still an important goal, the movement now needs to reorient toward building—creating new policies that embed justice and equity as measurable targets. This would include, for example, where and how governments distribute public funds to finance and build climate-resilient infrastructure.
By embracing this new approach, on future Earth Days the CEJ community might not only reflect on the environmental damage prevented, but also on the advancements made toward a more equitable future.
Related Content
Joseph B. Keller, Manann Donoghoe, Andre M. Perry
January 29, 2024
Manann Donoghoe, Andre M. Perry, Samantha Gross, Ede Ijjasz-Vasquez, Joseph B. Keller, John W. McArthur, Sanjay Patnaik, Barry G. Rabe, Sophie Roehse, Kemal Kirişci, Landry Signé, David G. Victor
December 14, 2023
Manann Donoghoe, Justin Lall, Andre M. Perry
December 13, 2023
Brookings Metro
Brookings Initiative on Climate Research and Action Promoting equitable and effective climate action in every community
Carlos Martín, Carolyn Kousky, Karina French, Manann Donoghoe
April 23, 2024
The Brookings Institution, Washington DC
4:00 pm - 5:15 pm EDT
Abraão Vicente
March 22, 2024

Kristy Ferraro, '24 PhD
Unique Research on Calving Impacts on Nutrient Cycle Earns 2024 Bormann Prize
A study led by YSE doctoral candidate Kristy Ferraro demonstrates how plant-fungal associations in ecosystems can mitigate the impact of calving animals in nitrogen cycling.
Listen to Article
In the expanding field of zoogeochemistry, which examines how animals interact with nutrient cycles, Kristy Ferraro had a novel idea. The Yale School of the Environment doctoral candidate developed a field experiment that would look at how plant-fungal ecology interacted with the nutrients introduced by calving animals — white tail deer — during spring green-up.
“Animals interact with ecosystems in so many different ways. They are constantly impacting, and are impacted by, the environments they live in,” Ferraro said. “Untangling the ways in which animals are supporting ecosystems or contributing to ecosystem function is important because it helps us understand their role. While we know that carcasses and waste can accelerate nutrient cycles and create nutrient hotspots, for large mammals, there hasn’t been much work on the role of placenta and natal fluid in ecosystem functions. There also hasn’t been any work on the interactive effects of animal inputs and the underlying plant-fungal associations. The research really extends beyond the question of how animals impact ecosystems to how ecosystems are modulating that impact.”
This groundbreaking interdisciplinary research, which was published in 2023 in the Journal of Animal Ecology, earned Ferraro the 2024 F. Herbert Bormann Prize. The award honors a YSE doctoral student whose work best exemplifies the legacy of Bormann, a plant ecologist who taught at YSE from 1966-1993 and whose research called the world’s attention to the threat of acid rain. Ferraro received the award at the 40th annual Research Day held at YSE April 12.
For the study, Ferraro and a team of YSE researchers placed animal placentas and simulated natal fluid at Yale-Myers Forest in plots dominated by one of two different plant-fungal associations common in northern forests — ericoid mycorrhizal (ErM) or ectomycorrhizal (EcM). They returned to the sites three months later to record nutrient concentrations in the vegetation in the plots, as well as the cycling of nutrients in the soil. They found that the calving materials act as fertilizers and create nutrient hotspots that ultimately create more nutritious plants for animals to eat. They also discovered that while the nutrients introduced by the calving did accelerate nitrogen cycling, in some cases the underlying plant-fungal associations mitigated the effects by slowing it down.
“Our study highlights one newly discovered piece of an infinite feedback loop between animals and ecosystems … Specifically, the underlying plant-fungal association can mediate the impacts of calving inputs,” Ferraro said.
The study was co-authored by Oswald Schmitz, Oastler Professor of Population and Community Ecology; Mark Bradford, professor of soils and ecosystem ecology; Les Welker ’22,’24 MESc; and Eli Ward ’18 MFS, ’23 PhD.
Ferraro said she was thrilled to receive the Bormann prize for the research.

From left: Les Welker ’22, ’24 MESc; Eli Ward '18 MFS, ’23 PhD; and Kristy Ferraro ’24 PhD conduct field research at Yale-Myers Forest examining how calving animals impact the nutrient cycle and how those impacts can be modulated by plant-fungal associations.
“What is special about the Bormann prize is the legacy it represents. Professor Bormann not only did interdisciplinary work, but he also did impactful work … and that’s the sort of work I want to do. I want to do work that not only brings disciplines together and helps us better understand conservation and ecology, but also makes us do better conservation and ecology,” she said.
Ferraro first had set her sights on studying caribou in Canada, but when the COVID-19 pandemic hit, she restructured her research and worked with Ward, a forest ecologist at the Connecticut Agricultural Experiment Station, to add the component of investigating plant-fungal interactions with zoogeochemistry at a site closer to home.
It wasn’t easy getting the materials for the study, Ferraro noted. Instead of white-tail deer placenta and natal fluid, the team substituted lamb placentas because it was easier to obtain. To get those, she had to call farmers around the state and ask them to freeze the placentas so she could obtain them and place them at the forest sites.
“We called about 50 sheep farmers around Connecticut to ask them to keep the materials, and we got a lot of varied responses. Some were like, ‘Absolutely not. That’s weird.’ But we ultimately found three really wonderful farmers who were super interested in the research and were really engaged,” she said.

After picking up the placentas from the farmers, sometimes out of buckets, the team then placed the placenta and simulated natal fluid in crab traps at the Yale-Myers plots that had the two different fungal associations (ErM and EcM).
“Not everyone has the stomach for it. I barely had the stomach for it. So that was the first hurdle,” Ferraro said.
They also set up camera traps to record animal interactions. The cameras revealed that some placentas were stolen by animals to nourish themselves.
“Turns out possums are really good at sticking their little hands into the cages,” Ferraro said, adding that racoons, coyotes, and turkeys also helped themselves to the placentas.
Despite the scavenging by animals, they found that the natal fluid itself had enough of an impact to bump up nutrient cycling and create nutrition hotspots in the surrounding plant material, but the impact was mediated by both plant-fungal associations, with ErM plant-fungal associations having a slower nutrient cycle compared to EcM.
The findings have important implications. As shrubs move north and spread due to climate change, the ErM plant-fungal associations that are underlyng shrub communities could mute the nutrient hotspots animals create as they did at Yale-Myers Forest, Ferraro said.
“Kristy’s research fits well with the spirit of the Bormann Award. Herb Bormann pioneered the use of experiments at scale to evaluate how human impacts, such as forest harvesting, leads to alterations of biogeochemical cycling across the landscape. Kristy also reports on an experiment, at scale, to evaluate effects of another human impact — forest management that supports deer populations — in boosting biogeochemical cycling. The work gives holistic insight into an animal species’ impact on biogeochemical processes in ecosystems,” Schmitz said.
Other Research Day award winners include doctoral students Destiny Treloar, who earned the Schmitz Prize for best oral presentation for her research on “Exploring the Relationship Between Sociodemographic Characteristics, Food Access, and Food Assistance Participation During the COVID-19 Pandemic in a Predominantly Hispanic/Latino City: Hialeah, Florida; Lachlan Byrnes, for Best Poster on “Contrasting patterns of mortality in an Amazon-Cerrado forest edge during exceptional drought”; and Ananya Rao ’25 MESc, who received the Master’s Student Oral Presentation Prize for her research on “Leveraging Community Forest Resources Rights to augment NTFP-based livelihoods in Central India.”
- Kristy Ferraro
- Oswald Schmitz
- Mark Bradford
- Doctoral Program
Media Contact
Paige stein.
Chief Communications and Marketing Officer
Research in the News

Climate Change Threatens Resilience of Sri Lankan Rainforests

An Inside Look at Beech Leaf Disease

Achieving Sustainable Urban Growth on a Global Scale
Connect with us.
- Request Information
- Register for Events
ESG Rulemaker to Research Biodiversity and Workforce Disclosures
By Michael Kapoor

A global rulemaker decided Tuesday to research just two of four proposed topics for new standard setting—biodiversity and workforce skills—as it concentrates on helping companies use existing reporting rules.
All 14 International Sustainability Standards Board members voted in favor of researching a new standard on biodiversity, ecosystems and ecosystem services reporting. Thirteen supported looking into the knowledge and experience of a company’s staff, known as human capital.
The board decided not to look into another two possible topics listed as priorities in a May 2023 consultation document: human rights and integrating sustainability and financial reporting. The votes came as the ...
Learn more about Bloomberg Law or Log In to keep reading:
Learn about bloomberg law.
AI-powered legal analytics, workflow tools and premium legal & business news.
Already a subscriber?
Log in to keep reading or access research tools.
An official website of the United States government
The .gov means it's official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you're on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
- Browse Titles
NCBI Bookshelf. A service of the National Library of Medicine, National Institutes of Health.
Dusetzina SB, Tyree S, Meyer AM, et al. Linking Data for Health Services Research: A Framework and Instructional Guide [Internet]. Rockville (MD): Agency for Healthcare Research and Quality (US); 2014 Sep.

Linking Data for Health Services Research: A Framework and Instructional Guide [Internet].
- Hardcopy Version at Agency for Healthcare Research and Quality
2 Research Environment
A foundational element of any research project is the research program environment. In the context of comparative effectiveness research (CER) using linked data, a secure and well-performing environment is important for several reasons, including that it helps build and assure trust between researchers and the providers of sensitive data, be they patients, registry administrators, insurance claim administrators, or others. If data providers are confident that a research partner has strong administrative and technical security systems and takes data security seriously at a programmatic level, they will be more confident in providing sensitive data to the researchers, including data with unique identifiers. As we describe in Chapters 4 and 5 of this report, linkage quality is typically much stronger when unique identifiers are available. Therefore, a secure research environment and capable information technology support can directly influence the quality of the research data obtained and, by extension, research results. With faith in the integrity and security of the research environment, data providers may also be more likely to provide other unique data that can be important to driving truly innovative research.
A secure and well-performing environment is also important in that system performance and security controls can directly influence the scope of the research project, including the size and complexity of the data that can be managed and linked to support the project. Often, as the scope and complexity of research projects increase and the data volume grows, computing environments are challenged to scale up to ensure seamless operations.
This chapter describes key considerations concerning the research environment, including the technical platform and security considerations, to guide researchers as they seek to develop or optimize their systems for CER projects using large volumes of data such as linked registry and administrative claims data.
- Computing Systems and the Balance Between Security and Usability
As shown in Figure 2.1 , security and usability often stand on opposite ends of a spectrum. The tradeoff for having a highly secure system is decreased accessibility and practical usability, whereas systems that are highly accessible often face greater challenges in assuring data security. Understanding the scope of the research project and the needs of the researcher or research team is important to specifying a system configuration that meets the needs of the project and balances security with usability. For example, a single researcher with a small research project of limited scope will likely have different needs for a computing environment compared with a large decentralized research team undertaking a multiyear research study using national data.
Security versus usability.
We present three different computing system scenarios to help researchers identify where on the spectrum their program may fall. While this discussion does not take into account the number of users, it is important to note that the cost of large systems varies greatly depending on existing infrastructures and purchasing prices of solutions offered by various vendors.
Desktop Computer: High Security, Low Usability, Low Cost
In this environment, the user accesses all data on a dedicated desktop computer located in a dedicated and constantly locked office with limited network access.
- Security : The risks of theft and network attacks are reduced to a minimum.
- Usability : Multiple users will never be able to access the data concurrently.
Central Server: Medium Security, Medium Usability, Moderate Cost
This environment allows multiple users to connect remotely through a secure command line (e.g., through a secure protocol such as SSH) to a central computing server housing all the data and tools.
- Security : The risk increases while gaining access to information over a network. Controlling individual users’ access to information creates new administrative challenges.
- Usability : Multiple users can collaborate on a central system. Computing jobs can be submitted in the background and the progress can be checked from remote locations.
Virtual Remote Desktops: High Security, High Usability, High Cost
This environment allows multiple users to connect remotely to virtualized desktops over the Internet from laptops or desktop computers to access shared data and tools.
- Security : Since the accessing computers supply only monitor, keyboard, and mouse, the data never leave the server environment. Even secure printing to dedicated printers is possible to control paper output.
- Usability : Each user connects to a virtual computer in the central environment. All tools are housed on the server but accessed through existing desktops.
- Building the Technical Platform
Regardless of the selected technologies, the number of users, or security requirements, the technical platform can be disassembled into various components ( Figure 2.2 ). Defining the requirements for the individual components creates a meaningful information technology plan.
Component architecture.
Securing the Platform
Most regulatory security frameworks, such as the Health Information Portability and Accountability Act (HIPAA) and Federal Information Security Management Act (FISMA), focus on controlling the confidentiality, integrity, and availability of information. The efforts to implement administrative, physical, and technical safeguards tend to scale up as the system complexity increases. Regulatory requirements and risk assessments will strongly affect the technical implementations.
Users Accessing Platform
To support a wide range of innovative research on complex linked data resources, the experience and focus of team members narrow and deepen. Work is divided among individuals to cover areas such as data management, data linking, cohort discovery, advanced modeling, and more. Complex research projects depend on the seamless integration and collaboration of the various users and the use of their preferred tools. By defining the user profiles and job responsibilities, the main usability properties of the expected environment are established. Examples of typical roles within complex project teams include the following.
Role: Data Manager . The data manager takes care of the data. This might include importing new data, conversion of file formats, preparation and receipt of data carriers (storage devices), archiving obsolete data, and granting access to data.
Role: Data Linking . The linking expert is responsible for linking data sources. This might include cleaning linking variables, building linking methods, and cohort discovery (e.g., selection of patients meeting specific study-inclusion criteria), resulting in datasets for various research projects.
Role: Analyst/Statistician . The statistician is responsible for all modeling aspects of a research study. These might include creating analytic cohorts for study questions (using previously linked deidentified data), preparing data for modeling, and analyzing data to meet project objectives.
Gaining Access to Platform
Access management controls how users gain access to the system and data. An existing organization might have a central user-management process that establishes authentication with a simple username/password combination. More advanced two-factor authentication methods ensure that a compromised password alone does not convey access to the system. Biometric authentication (e.g., fingerprint reader) verifies the identity of the intended user. Examples of commonly used authentication methods and their pros and cons are provided in Appendix 2.1 .
Processing Power of Platform
The processing power of the computing system directly affects the time it takes to manipulate the data. As linking processes touch the same information repeatedly, tuning parameters to optimize the performance of hardware and software will reduce the run times. For considerations for hardware performance, see Appendix 2.1 .
It is important to understand that the researcher’s network has an impact on data flow. The network can quickly become the bottleneck for moving data, resulting in an exceptionally slow response. In an optimized setup, the connection between data and processing components is a dedicated Gigabit (1,000Mbps) network or even fiber optics. Any components between the processing and storage, such as firewalls, network switches, or routers, will reduce information flow. In a setup in which the data are stored on hard drives directly attached to the processing system, network performance will have a limited impact on data flow.
Data Storage Platform
The storage performance directly affects the time it takes to perform data tasks. For example, tasks such as cleaning and standardizing data, combining data sources, or performing exploratory analyses of linked data sources are storage-intensive activities. The main technical characteristics of the storage platform are size and speed. A storage device is attached using a specific technology, such as Serial Advance Technology Attachment (SATA), Serial Attached Small Computer System Interface (Serial SCSI or SAS), Universal Serial Bus (USB), or Storage Area Network (SAN). Various vendors sell enterprise storage solutions encapsulating multiple storage devices in a single appliance.
Storage Size . When purchasing data carriers, it is important to understand that physical data size and actual available data size will greatly vary depending on the installation. Methods used to prevent data loss, such as Redundant Array of Independent Disks (RAID), might require as much as twice the amount of physical space as required for storing the physical data. The file system used to store data also affects available data size. A data carrier is divided into blocks like a blank book with many pages. The size of the data block is fixed for the entire file system. As an example, if the block size is 1,024 characters (or bytes) and a file of 1,500 characters is saved, it will consume 2,048 physical bytes on the data carrier. Since the partially used blocks cannot be used for other files, these bytes are “lost.”
Storage Speed. Storage devices have two speed-related properties: (1) the time it takes to find the data on the carrier (referred to as seek time and measured in milliseconds) and (2) the continuous read/write performance. The seek time depends mainly on how fast the disk is spinning. Common rotation speeds are 5,400, 7,200, 10,000, and 15,000 revolutions per minute (RPM). In the case of a solid state disk (SSD), the seek time will be extremely low, as there are no moving parts. The continuous read/write performance depends not only on how fast the disk is spinning, but also on how the disk is attached to the processing system.
A well-performing storage system can read/write information at rates of 100MB/s or more. A disk spinning at 5,400 or 7,200 RPM, as delivered in standard laptops or desktops, generally cannot achieve this. In comparison, an SSD attached over SATA can easily reach read/write rates of 500MB/s or more. To optimize cost, a computing system can be outfitted with slower/cheaper storage for archiving in combination with fast analytic storage to support powerful processing.
- Securing the Research Environment
Federal and State laws have mandated several sets of regulations, each intended to address one or more of the following objectives:
- Confidentiality : Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information
- Integrity : Guarding against improper information modification or destruction; includes ensuring information nonrepudiation and authenticity
- Availability : Ensuring reliable and timely access to information
Regulatory Requirements
The research environment must comply with applicable laws to protect the hosted information. Because HIPAA governs health information collected by covered entities mainly during health encounters, alternative research datasets might require compliance with other contractual requirements or State regulations. Researchers should consult with a regulatory expert as early as possible to ensure that they understand the scope of all applicable laws.
Regulatory requirements generally describe what must be controlled and leave it up to the research team to define how to reach the required controls by implementing adequate policies and procedures. Some State-level privacy laws may govern even self-collected information. In the following sections, we describe a sample of regulatory requirements that might be applicable to researchers working with sensitive health information.
Federal Information Security Management Act of 2002 . FISMA defines a mandatory framework for managing information security for all information systems used or operated by a U.S. Federal Government agency or by a contractor or other organization on behalf of a Federal agency. It requires the development, documentation, and implementation of an information security program. The National Institute for Standards and Technology (NIST) standards and guidelines (Special Publications 800 series) and Federal Information Processing Standards (FIPS) publications further define the framework of the program.
Health Information Portability and Accountability Act . The U.S. Congress created HIPAA in 1996. Security standards establishing requirements to safeguard Protected Health Information (PHI), both paper and electronic (ePHI), were issued as part of HIPAA in April 2003. The security requirements specifically address administrative, physical, and technical safeguards meant to ensure that patient health records and Personally Identifiable Information (PII) remain as secure as possible.
State Security-Breach Laws . Forty-six States, the District of Columbia, and multiple U.S. territories (Guam, Puerto Rico, and the Virgin Islands) have enacted privacy-breach notification laws. While these laws can vary from State to State, they generally follow a similar framework. This framework defines “sensitive data,” sets out requirements for triggering the breach-notification process, identifies actors and roles in the notification process, defines to whom the law applies, and describes those cases under which certain parties and/or information may be exempt from notification requirements ( www.fas.org/sgp/crs/misc/R42475.pdf ). Researchers are responsible for understanding their responsibilities under the relevant State breach-notification legislation and should consult legislative resources such as the National Conference of State Legislatures for regulatory text ( www.ncsl.org ).
Identifying Sensitive Data
Sensitive data are the information protected by regulatory requirements. The definition of sensitive data varies widely between laws. In some cases, the scope of a Data Use Agreement (DUA) could even require aggregation or define minimum cell sizes. In the following section, we provide a summary of regulatory definitions per FISMA, HIPAA, and State security-breach laws.
Personally Identifiable Information, FISMA . As used in information security, PII is any information maintained by an agency that can be linked to an individual. This includes (1) any information (e.g., name, Social Security Number, date and place of birth, mother’s maiden name, or biometric records) that can be used to distinguish or trace an individual’s identity and (2) any other information (e.g., medical, educational, financial, and employment information) that is linked or linkable to an individual. Examples of PII include, but are not limited to—
- Name, such as full name, maiden name, mother’s maiden name, or alias
- Personal identification number, such as Social Security Number, passport number, driver’s license number, taxpayer identification number, or financial account or credit card number
- Address information, such as street address or email address
- Personal characteristics, including photographic image (especially of face or other identifying characteristic), fingerprints, handwriting, or other biometric data (e.g., retina scan, voice signature, facial geometry)
Protected Health Information, HIPAA . The HIPAA Privacy Rule protects all “individually identifiable health information” held or transmitted by a covered entity or its business associate in any form or media, whether electronic, paper, or oral. The Privacy Rule calls this information Protected Health Information , or PHI.
Under HIPAA, individually identifiable health information is information, including demographic data, that relates to any of the following:
- The individual’s past, present, or future physical or mental health condition
- The provision of health care to the individual
- The past, present, or future payment for the provision of health care to the individual
- Information that identifies the individual or for which there is a reasonable basis to believe it can be used to identify the individual
Individually identifiable health information includes many common identifiers (e.g., name, address, birth date, Social Security Number). The Privacy Rule excludes from PHI employment records that a covered entity maintains in its capacity as an employer, and educational and certain other records subject to or defined in the Family Educational Rights and Privacy Act, 20 U.S.C. §1232g.
Electronic Protected Health Information, HIPAA . The HIPAA Security Rule protects a subset of information covered by the Privacy Rule, which is all individually identifiable health information a covered entity creates, receives, maintains, or transmits in electronic form. The Security Rule calls this information electronic Protected Health Information , or ePHI. The Security Rule does not apply to PHI transmitted orally or in writing.
Limited Datasets, HIPAA . HIPAA also has a provision for Limited Datasets (LDSs) from which most but not all potentially identifying information has been removed. Elements in an LDS are often necessary for research; however, Direct Identifiers , a subset of PHI defined by HIPAA §164.514(e)(2), must be removed. The Direct Identifiers include—
- Postal address information other than town or city, State, and ZIP Code
- Telephone numbers
- Fax numbers
- Electronic mail addresses
- Social Security Numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Device identifiers and serial numbers
- Web Universal Resource Locators (URLs)
- Internet Protocol (IP) addresses
- Biometric identifiers, including finger and voice prints
- Full-face photographic images and any comparable images
LDSs can include the following PHI:
- Date of birth
- Date of death
- Dates of service
- Town or city
Personal Information, State Security-Breach Laws . Researchers should review applicable State legislation for definitions of Personal Information. Generally, these definitions do not vary substantially from State to State and are very similar to Federal definitions. For example, the North Carolina State Security-Breach Laws (North Carolina General Statute §75-65) define Personal Information as a person’s first name or first initial and last name in combination with any of the following identifying information:
- Social Security Number or employer taxpayer identification numbers
- Driver’s license, State identification card, or passport numbers
- Checking account numbers
- Savings account numbers
- Credit card numbers
- Debit card numbers
- Personal Identification Number (PIN)
- Electronic identification numbers, electronic mail names or addresses, Internet account numbers, or Internet identification names
- Digital signatures
- Any other numbers or information that can be used to access a person’s financial resources
- Biometric data
- Fingerprints
- Parent’s legal surname before marriage
Summary of Protected Information
The research team may find it useful to summarize in matrix form the protected information types identified by applicable regulatory requirements. This matrix will help the research team identify information in datasets and assess the policies and procedures that might apply to a specific work task. Table 2.1 shows an example of one such matrix.
Example of matrix summarizing protected information types.
Building and Implementing a Security Plan
Meeting applicable regulatory requirements requires thoughtful planning and management. While it is tempting to think of information security in terms of technological controls, successful security management requires people, processes, and technology in equal proportion. An overarching security management plan addresses how people, processes, and technology will be leveraged to maintain the confidentiality, integrity, and availability of sensitive data within the bounds set by applicable regulatory requirements.
While development of the security management plan is an iterative process, with sections added or refined as planning activities proceed, the document will ultimately address the following:
- Security laws and regulations describe those regulatory requirements applicable to the research team, as discussed previously.
- Major functions list those functions the security plan is intended to accomplish.
- Scope lists those sensitive data types the security program is intended to address.
- Roles and responsibilities describe roles that will be held by members of the organization and their responsibilities vis-à-vis information security.
- Management commitment represents an official statement on the part of the applicable management body in support of the processes and procedures documented within the security plan.
- FISMA security categorization and impact level define the FISMA category assigned to the data and information systems covered by the security plan. This section is applicable only to those systems subject to FISMA.
- Compliance and entity coordination describe which roles are responsible for ensuring organizational compliance with the security plan and which roles are responsible for coordinating security activities among relevant entities external to the research team (e.g., data centers, overarching security offices).
Security documentation control
Risk management (described in further detail below)
Workforce security
Access management
Security training
Incident reporting
Contingency planning
Security assessment
Facility access
Workstation access
Devices and removable media
Data integrity
Authentication
Network security
System activity review/audit
At the outset of security planning, the research team should be able to define the security laws and regulations, major functions, and scope sections. Roles and responsibilities, management commitment, entity coordination, and FISMA categorization (if applicable) can be defined further through stakeholder meetings. The processes and procedures documented in the subplans will be developed as part of the risk-management process described below.
Workforce Training
A training plan defines working procedures, emergency and incident management, sanction policies, policies and procedures on how to inform members of the workforce about their roles and responsibilities, and other relevant procedures. Many large research environments might be able to leverage existing training modules. These might include training on HIPAA, research ethics, basic computer and network use, and basic human resources policies. Keeping the retraining on an annual basis is advisable.
- Managing Risks
Research teams must first understand regulatory requirements, then select and implement adequate security controls to meet these requirements and to mitigate risks posed to the security of the organization’s information systems and data. Often, discussions of information security mistakenly emphasize specific technical safeguards. An emphasis on risk management, however, properly defines technical solutions as the means by which organizational risks are controlled. Risk management, therefore, drives information security planning. A comprehensive risk-management program not only allows data custodians to identify risks posed to their data, but also provides a framework for selection of functional and technical security controls.
Data custodians subject to FISMA requirements should consult NIST guidance for implementing a FISMA-compliant life-cycle program, which includes detailed volumes of guidance and controls. We illustrate a more general risk-management framework in Figure 2.3 . This framework envisions risk management as a continuous cycle of assessing, addressing, and monitoring organizational risk to ensure the confidentiality, integrity, and availability of information systems.
Risk-management cycle.
Identifying and Assessing Risk
Risk identification is conducted on any technology, process, and procedure within the scope of the environment. Risk identification is, simply put, the process of identifying and documenting potential threats to the research team’s information and information systems. Risk identification can be conducted in a variety of ways, including brainstorming sessions, documentation reviews, assumptions analysis, cause and effect diagramming, strengths/weaknesses/opportunities/threats (SWOT) analysis, and expert consultation. Inclusion of an independent third party, be it an outside consultant or even representatives from a separate group within the research team, will provide an external point of view invaluable in fully defining the spectrum of potential adverse events. Regardless of the method used, this process must clearly identify and document the source of the risk and the impact of the risk should it be realized.
Assess identified risks along two primary dimensions: probability of occurrence and criticality of impact. Actions and mitigations planned in the next phase of the risk-management cycle will be based largely on each risk’s score as assessed during this phase.
Risk scores evaluate the combination of the probability and impact of a security breach/incident. Higher scores represent higher security risks. Lower scores represent reduced security risks. Table 2.2 provides an example of how to plot and assess the severity of a security breach/incident (criticality of impact) and the likelihood of occurrence of an event.
Example of risk scores.
Tracking Risks
The risk register is the collection of all identified risks, their assessed impact and probability, and possible actions/mitigations. Both HIPAA and FISMA mandate the analysis of risk and a record thereof. Table 2.3 is an example of a generic risk register.
Example of generic risk register.
Planning Risk Responses
Once risks have been identified, assessed, and documented in the risk register, data custodians and other stakeholders can plan appropriate methods of dealing with each risk. Risk responses can be divided into four categories: avoidance, acceptance, transfer, and mitigation.
- Risk avoidance occurs when a research team takes the necessary actions to reduce the likelihood of risk realization to close to (if not exactly) zero. Generally, risk avoidance is the most desirable method of dealing with risks; however, it is often cost prohibitive or simply infeasible to avoid all risks.
- Risk acceptance occurs when a research team chooses to accept the consequences of a risk should it be realized. Risk acceptance is generally recommended when the impact of a risk is small or when the probability of occurrence is significantly lower than the cost to avoid, transfer, or mitigate. Each research team must define its own criteria for what constitutes an “acceptable” risk.
- Risk transfer occurs when a research team passes the impact of risk realization on to another party. The most common form of risk transfer is insurance. Risk transfer is feasible only when the impact can be clearly measured and addressed by the third party.
- Risk mitigation occurs when a research team takes steps to reduce the probability or impact of risk realization. Risks that cannot be avoided, accepted, or transferred must be mitigated.
After a research team decides whether to avoid, accept, transfer, or mitigate a risk, it must determine the necessary steps to do so. At this juncture, the research team will identify the necessary and appropriate technical controls to either avoid or mitigate certain risks. Actions identified in this phase must also be documented in the risk register.
Implementing Risk Responses
During the implementation phase, the research team develops and deploys the technical controls identified in the planning phase. Just as importantly, the research team must also document the controls selected, develop all necessary records, and train stakeholders accordingly. Users must understand not only how to use any security controls implemented but also the “rules of behavior” for maintaining a secure environment. Technical controls alone are not sufficient to create a fully secure environment; users and other stakeholders must foster and maintain a culture of security.
Monitoring Risks
Risk management is an ongoing cyclical process. The research team must periodically reassess the environment for new or changing risks, which in turn must be identified, assessed, and addressed through planning and action. Thoughtful and frequent monitoring of risk allows a research team to adapt more easily to changes, both expected and unexpected, without compromising information security.
- Conclusions
A research environment incorporating a secure and well-performing computing platform represents the operational backbone for conducting innovative research using complex linked data sources. Securing and safeguarding the information not only meets legal and regulatory requirements, but also builds needed trust among stakeholders. Data providers will be more open to providing access to their information, researchers will be confident in accessing sensitive data, and programmers and analysts will operate effectively in a standardized environment with consistent application of technologies and tools. The technical implementation, combining performance and storage, will enable complex data management, as described in Chapter 3 . Supported by the leadership, successfully implemented security policies and procedures fit seamlessly into daily workflows, reducing and mitigating potential risks. The environment is now ready to support research and to receive even the most sensitive data.
Appendix 2.1. Procedures and Processes To Enhance Data Security
Moving sensitive data using cds or dvds.
Perform the following steps to create and transport sensitive data using CDs or DVDs. This procedure can be adapted for electronic transfer using a protocol such as the secure file transfer protocol (SFTP).
- Create a new media number and add it to a data carrier list tracking all movable media containing sensitive data.
- Create a local folder with the media number as the name.
- Assemble all the data in the created folder.
- Generate an encryption key using a GUID (globally unique identifier) tool such as that found at www.guidgenerator.com/ and print it on a document along with the media number.
- Create an archive using a PGP ( http://en.wikipedia.org/wiki/Pretty_Good_Privacy ) encryption tool with all the contents of the folder, using the GUID as the encryption key.
- After testing the self-extracting archive, use a file-shredding tool ( www.fileshredder.org/ ) to remove the folder with the data.
- Burn the archive onto a data CD or DVD labeled with the media number.
- You can now mail the data carrier, and fax or email the encryption key separately to the receiving party.
Guidelines for Storage and Destruction of Movable Media
- Store movable media in a safe, separated from the encryption keys.
- Destroy damaged and/or retired media, including hard disks, by shredding.
- Update movable media records for every media item that is disposed of or destroyed.
- Shred any printed material at location or use a secure document disposal service.
Decoupling and Mapping Data
Figure 2.4 describes a process for adding data sources to the research data environment, removing direct identifiers, and creating a merged dataset with elements regarding the individuals’ health status or health services utilization. In the context described below, we retain Protected Health Information (PHI) within the original data files but limit access (a process known as decoupling). When PHI is destroyed following the data linkage, this is known as deidentification. We use the terms deidentified and decoupled interchangeably in this report as we discuss data security and staging, but readers should understand the differences represented by the terminology.
Process for creating a merged dataset.
Data file : This file contains raw data such as claims, diagnoses, and treatment. Individuals cannot be directly identified in these data.
Finder file : The finder files contain direct identifiers of individuals.
Mapping process : Using a mapping method, the individuals in the finder files are matched.
Crosswalk : The crosswalk identifies matching records for each individual and possible duplicates. A new unique identifier (ID) is assigned for each true identified research subject.
Removal of direct identifiers : Using the crosswalk and the data file, a new file is generated by replacing the source identifiers with the new IDs.
Merged dataset : Information about an individual can now be accessed across data sources and deidentified datasets using the new IDs.
Physical Separation of Data Using Storage Architecture
In the computing environment, data are separated physically into the three storage areas, as shown in Figure 2.5 .
Physical storage areas.
Direct identifier storage : Raw data including direct identifiers are secured in a highly restricted part of the system. The direct identifier space is accessible only through very restrictive access-management controls. All work on data linking and removal of direct identifiers is performed in this environment. Only a limited set of specifically trained, authorized individuals work in this environment.
Deidentified storage : The deidentified space contains deidentified master datasets from each source. This storage might be accessible to authorized users in read-only mode. Research datasets are extracted, or “cut,” from these master files.
Project storage : Individual programmers access this space for projects. Institutional Review Boards and Data Use Agreements control the access to master datasets and datasets for projects.
Examples of Common Authentication Methods
Simple User Account . A user authenticates with username and password.
- Pros : This is a quick and simple way to access a system.
- Cons : Once the username and password are known, any individual can gain access.
Two-Factor Authentication . A user authenticates with username, password, and Personal Identification Number (PIN) (e.g., RSA secure ID).
- Pros : A changing PIN provides a second factor in addition to logging in with the username and password. An authentication is not possible without the device.
- Cons : The PIN verification is costly and, depending on the implementation, requires that the computing environment have access to the system verifying the PIN.
Biometric Authentication . A user authenticates with username, password, and (for example) a fingerprint.
- Pros : The additional biometric verification requires the account holder to be present at the time of authentication.
- Cons : Managing biometric information requires custom software installations on the client system.
Performance Considerations for Computer Hardware
Fine-tuning the three hardware components of memory, central processing unit (CPU), and bus speed is essential for the actual processing power. Random access memory (RAM) can be added after a purchase, but changes to the CPU or bus speeds are complicated and impractical. The bus speed represents how fast information can be moved between the CPU and the memory, and from and to the attached storage. When purchasing a system, you should purchase the highest affordable CPU/bus speed combination while leaving space to add memory later.
Central Processing Unit . Performance of a CPU is affected by (a) sockets (i.e., actual number of CPUs); (b) cores and threads (i.e., how instructions can be processed in parallel); and (c) clock (i.e., a number in GHz representing how many instructions are processed per second).
Random Access Memory . Selecting memory is dependent on the supported architecture of the motherboard. Manufacturers generally advise on what type of memory is supported and best for optimized performance. The product description of memory often includes physical and performance parameters. For example “240-Pin DDR3 1600” represents memory that has 240 pins connecting it to the motherboard and supports a 1600MHz clock.
Bus Speed . Depending on the architecture, there are multiple bus speeds affecting data throughput between storage, memory, and CPU. For example: a hard disk might be attached using SATA3 or “SATA 6Gb/s,” representing a bus speed of 6Gb/s. Bus speeds on the CPU/motherboard (chipset layout) are more complicated and fine-tuned by the vendor. Components with fancy names such as North Bridge, South Bridge, and Front Side Bus (FSB) ( http://en.wikipedia.org/wiki/Front-side_bus ) are part of this architecture. Vendors typically offer systems with high-performance options where these speeds are optimized and enhanced compared with home use products.
- Cite this Page Dusetzina SB, Tyree S, Meyer AM, et al. Linking Data for Health Services Research: A Framework and Instructional Guide [Internet]. Rockville (MD): Agency for Healthcare Research and Quality (US); 2014 Sep. 2, Research Environment.
- PDF version of this title (1.0M)
In this Page
- Procedures and Processes To Enhance Data Security
Other titles in these collections
- AHRQ Methods for Effective Health Care
- Health Services/Technology Assessment Texts (HSTAT)
Recent Activity
- Research Environment - Linking Data for Health Services Research Research Environment - Linking Data for Health Services Research
Your browsing activity is empty.
Activity recording is turned off.
Turn recording back on
Connect with NLM
National Library of Medicine 8600 Rockville Pike Bethesda, MD 20894
Web Policies FOIA HHS Vulnerability Disclosure
Help Accessibility Careers

COMMENTS
A new study finds that strategically integrating floating solar panels on reservoirs could substitute 20–100% of Africa’s planned hydropower by 2050. For the Zambezi watercourse, this approach ...
When it comes to sustainability and environmental impact, this Northeastern Ph.D. grad is at the ‘forefront of innovation’. Looking at doctorate programs, Abhijeet Parvatker found a perfect match in Northeastern and Matthew Eckelman, a professor of civil, environmental and chemical engineering. by Alena Kuzub. April 24, 2024.
Her research is largely funded by the National Science Foundation (NSF); over the course of her brief career, she already has published more than 60 articles in peer-reviewed publications, and holds a patent. ... friendly analytical chemistry practices that are critical for resource conservation and minimizing the impact on the environment.
Our research highlights the consequences of managing land, freshwater and sea ecosystems in socially constructed bubbles. We focus on solutions where social and ecological connections are at the ...
After years of research showing failures in the ways that the Federal Emergency Management Agency (FEMA) distributes disaster relief (including our own research on the subject), the agency made ...
Supporting and encouraging a diversity of students in the research environment begin with recruitment and selection that goes beyond traditional passive strategies such as waiting for email requests or asking laboratory members to suggest candidates. Active recruitment requires good advertising. Advertisements should be accessible and ...
The research really extends beyond the question of how animals impact ecosystems to how ecosystems are modulating that impact.” This groundbreaking interdisciplinary research, which was published in 2023 in the Journal of Animal Ecology, earned Ferraro the 2024 F. Herbert Bormann Prize. The award honors a YSE doctoral student whose work best ...
More than 130 million Americans are exposed to unhealthy levels of air pollution, according to the American Lung Association’s (ALA) 2024 “State of the Air” report. The annual report ...
April 23, 2024, 3:19 PM UTC. ESG Rulemaker to Research Biodiversity and Workforce Disclosures. By Michael Kapoor. Michael Kapoor. Freelance Correspondent. International board will focus on two of four potential topics. Proposals on human rights, integrated reporting dropped. A global rulemaker decided Tuesday to research just two of four ...
A foundational element of any research project is the research program environment. In the context of comparative effectiveness research (CER) using linked data, a secure and well-performing environment is important for several reasons, including that it helps build and assure trust between researchers and the providers of sensitive data, be they patients, registry administrators, insurance ...