Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Published: 15 June 2020

Entanglement-based secure quantum cryptography over 1,120 kilometres
- Juan Yin ORCID: orcid.org/0000-0002-9909-6211 1 , 2 , 3 ,
- Yu-Huai Li 1 , 2 , 3 ,
- Sheng-Kai Liao ORCID: orcid.org/0000-0002-4184-9583 1 , 2 , 3 ,
- Meng Yang 1 , 2 , 3 ,
- Yuan Cao ORCID: orcid.org/0000-0002-0354-2855 1 , 2 , 3 ,
- Liang Zhang 2 , 3 , 4 ,
- Ji-Gang Ren 1 , 2 , 3 ,
- Wen-Qi Cai 1 , 2 , 3 ,
- Wei-Yue Liu 1 , 2 , 3 ,
- Shuang-Lin Li 1 , 2 , 3 ,
- Rong Shu 2 , 3 , 4 ,
- Yong-Mei Huang 5 ,
- Lei Deng 6 ,
- Li Li 1 , 2 , 3 ,
- Qiang Zhang ORCID: orcid.org/0000-0003-3482-3091 1 , 2 , 3 ,
- Nai-Le Liu 1 , 2 , 3 ,
- Yu-Ao Chen ORCID: orcid.org/0000-0002-2309-2281 1 , 2 , 3 ,
- Chao-Yang Lu ORCID: orcid.org/0000-0002-8227-9177 1 , 2 , 3 ,
- Xiang-Bin Wang 2 ,
- Feihu Xu ORCID: orcid.org/0000-0002-1643-225X 1 , 2 , 3 ,
- Jian-Yu Wang 2 , 3 , 4 ,
- Cheng-Zhi Peng ORCID: orcid.org/0000-0002-4753-5243 1 , 2 , 3 ,
- Artur K. Ekert ORCID: orcid.org/0000-0002-1504-5039 7 , 8 &
- Jian-Wei Pan ORCID: orcid.org/0000-0002-6100-5142 1 , 2 , 3
Nature volume 582 , pages 501–505 ( 2020 ) Cite this article
33k Accesses
365 Citations
628 Altmetric
Metrics details
- Quantum information
- Single photons and quantum effects
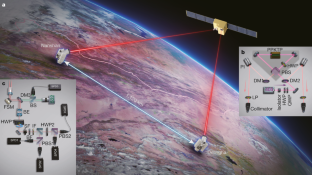
Quantum key distribution (QKD) 1 , 2 , 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 kilometres long 4 , 5 , 6 , 7 . In the field, point-to-point QKD has been achieved from a satellite to a ground station up to 1,200 kilometres away 8 , 9 , 10 . However, real-world QKD-based cryptography targets physically separated users on the Earth, for which the maximum distance has been about 100 kilometres 11 , 12 . The use of trusted relays can extend these distances from across a typical metropolitan area 13 , 14 , 15 , 16 to intercity 17 and even intercontinental distances 18 . However, relays pose security risks, which can be avoided by using entanglement-based QKD, which has inherent source-independent security 19 , 20 . Long-distance entanglement distribution can be realized using quantum repeaters 21 , but the related technology is still immature for practical implementations 22 . The obvious alternative for extending the range of quantum communication without compromising its security is satellite-based QKD, but so far satellite-based entanglement distribution has not been efficient 23 enough to support QKD. Here we demonstrate entanglement-based QKD between two ground stations separated by 1,120 kilometres at a finite secret-key rate of 0.12 bits per second, without the need for trusted relays. Entangled photon pairs were distributed via two bidirectional downlinks from the Micius satellite to two ground observatories in Delingha and Nanshan in China. The development of a high-efficiency telescope and follow-up optics crucially improved the link efficiency. The generated keys are secure for realistic devices, because our ground receivers were carefully designed to guarantee fair sampling and immunity to all known side channels 24 , 25 . Our method not only increases the secure distance on the ground tenfold but also increases the practical security of QKD to an unprecedented level.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
24,99 € / 30 days
cancel any time
Subscribe to this journal
Receive 51 print issues and online access
185,98 € per year
only 3,65 € per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout
Similar content being viewed by others
Entanglement of nanophotonic quantum memory nodes in a telecom network
Creation of memory–memory entanglement in a metropolitan quantum network
Quantum control of a cat qubit with bit-flip times exceeding ten seconds
Data availability.
The data that support the findings of this study are available from the corresponding authors on reasonable request.
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proc. Int. Conf. on Computers, Systems and Signal Processing 175–179 (1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett . 67 , 661 (1991).
ADS MathSciNet CAS PubMed MATH Google Scholar
Bennett, C. H., Brassard, G. & Mermin, N. D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett . 68 , 557 (1992).
Peng, C.-Z. et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett . 98 , 010505 (2007).
ADS PubMed Google Scholar
Rosenberg, D. et al. Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett . 98 , 010503 (2007).
Yin, H.-L. et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett . 117 , 190501 (2016).
Boaron, A. et al. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett . 121 , 190502 (2018).
ADS CAS PubMed Google Scholar
Liao, S.-K. et al. Satellite-to-ground quantum key distribution. Nature 549 , 43 (2017).
Liao, S.-K. et al. Space-to-ground quantum key distribution using a small-sized payload on Tiangong-2 Space Lab. Chin. Phys. Lett . 34 , 090302 (2017).
ADS Google Scholar
Yin, J. et al. Satellite-to-ground entanglement-based quantum key distribution. Phys. Rev. Lett . 119 , 200501 (2017).
Schmitt-Manderbach, T. et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett . 98 , 010504 (2007).
Ursin, R. et al. Entanglement-based quantum communication over 144 km. Nat. Phys . 3 , 481 (2007).
CAS Google Scholar
Elliott, C. et al. Current status of the DARPA quantum network. In Quantum Information and Computation III Vol. 5815, 138–150 (International Society for Optics and Photonics, 2005).
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys . 11 , 075001 (2009).
Chen, T.-Y. et al. Field test of a practical secure communication network with decoy-state quantum cryptography. Opt. Express 17 , 6540 (2009).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19 , 10387–10409 (2011).
Qiu, J. et al. Quantum communications leap out of the lab. Nature 508 , 441 (2014).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett . 120 , 030501 (2018).
Koashi, M. & Preskill, J. Secure quantum key distribution with an uncharacterized source. Phys. Rev. Lett . 90 , 057902 (2003).
Ma, X., Fung, C.-H. F. & Lo, H.-K. Quantum key distribution with entangled photon sources. Phys. Rev. A 76 , 012307 (2007).
Briegel, H.-J., Dur, W., Cirac, J. I. & Zoller, P. Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett . 81 , 5932–5935 (1998).
ADS CAS Google Scholar
Yang, S.-J., Wang, X.-J., Bao, X.-H. & Pan, J.-W. An efficient quantum light–matter interface with sub-second lifetime. Nat. Photon . 10 , 381 (2016).
Yin, J. et al. Satellite-based entanglement distribution over 1200 kilometers. Science 356 , 1140 (2017).
CAS PubMed Google Scholar
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photon . 8 , 595 (2014).
Xu, F., Ma, X., Zhang, Q., Lo, H.-K. & Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys . 92 , 025002 (2020).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photon . 4 , 686 (2010).
Zhao, Y., Fung, C.-H., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78 , 042333 (2008).
Weier, H. et al. Quantum eavesdropping without interception: an attack exploiting the dead time of single-photon detectors. New J. Phys . 13 , 073024 (2011).
Li, H.-W. et al. Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84 , 062308 (2011).
Sajeed, S. et al. Security loophole in free-space quantum key distribution due to spatial-mode detector-efficiency mismatch. Phys. Rev. A 91 , 062301 (2015).
Clauser, J. F., Horne, M. A., Shimony, A. & Holt, R. A. Proposed experiment to test local hidden-variable theories. Phys. Rev. Lett . 23 , 880 (1969).
ADS MATH Google Scholar
Koashi, M. Simple security proof of quantum key distribution based on complementarity. New J. Phys . 11 , 045018 (2009).
ADS MathSciNet Google Scholar
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun . 3 , 634 (2012).
ADS PubMed PubMed Central Google Scholar
Peng, C.-Z. et al. Experimental free-space distribution of entangled photon pairs over 13 km: towards satellite-based global quantum communication. Phys. Rev. Lett . 94 , 150501 (2005).
Cao, Y. et al. Bell test over extremely high-loss channels: towards distributing entangled photon pairs between earth and the moon. Phys. Rev. Lett . 120 , 140405 (2018).
Ladd, T. D. et al. Quantum computers. Nature 464 , 45–53 (2010).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74 , 022313 (2006).
Qi, B., Fung, C.-H.F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Inf. Comput . 7 , 73 (2007).
MathSciNet MATH Google Scholar
Gerhardt, I. et al. Experimentally faking the violation of Bell’s inequalities. Phys. Rev. Lett . 107 , 170404 (2011).
Bugge, A. N. et al. Laser damage helps the eavesdropper in quantum cryptography. Phys. Rev. Lett . 112 , 070503 (2014).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett . 108 , 130503 (2012).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys . 81 , 1301–1350 (2009).
Shor, P. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett . 85 , 441 (2000).
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. Quantum Inf. Comput . 4 , 325 (2004).
Mayers, D. J. Unconditional security in quantum cryptography. J. Assoc. Comput. Mach . 48 , 351–406 (2001).
Lo, H. K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 283 , 2050 (1999).
Ben-Or, M., Horodecki, M., Leung, D. W., Mayers, D. & Oppenheim, J. In Proc. 2nd Int. Conf. on Theory of Cryptography (TCC'05) 386–406 (Springer, 2005).
Renner, R. Security of quantum key distribution. PhD thesis , ETH Zurich (2005); preprint at https://arxiv.org/abs/quant-ph/0512258 .
Tsurumaru, T. Leftover hashing from quantum error correction: unifying the two approaches to the security proof of quantum key distribution. Preprint at https://arxiv.org/abs/1809.05479 (2018).
Serfling, R. J. Probability inequalities for the sum in sampling without replacement. Ann. Stat . 2 , 39–48 (1974).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun . 5 , 3732 (2014).
Fung, C.-H. F., Tamaki, K., Qi, B., Lo, H.-K. & Ma, X. Security proof of quantum key distribution with detection efficiency mismatch. Quantum Inf. Comput . 9 , 131–165 (2009).
Marøy, Ø., Lydersen, L. & Skaar, J. Security of quantum key distribution with arbitrary individual imperfections. Phys. Rev. A 82 , 032337 (2010).
Download references
Acknowledgements
We acknowledge discussions with X. Ma and C. Jiang. We thank colleagues at the National Space Science Center, China Xi’an Satellite Control Center, National Astronomical Observatories, Xinjiang Astronomical Observatory, Purple Mountain Observatory, and Qinghai Station for their management and coordination. We thank G.-B. Li, L.-L. Ma, Z. Wang, Y. Jiang, H.-B. Li, S.-J. Xu, Y.-Y. Yin, W.-C. Sun and Y. Wang for their long-term assistance in observation. This work was supported by the National Key R&D Program of China (grant number 2017YFA0303900), the Shanghai Municipal Science and Technology Major Project (grant number 2019SHZDZX01), the Anhui Initiative in Quantum Information Technologies, Science and Technological Fund of Anhui Province for Outstanding Youth (grant number 1808085J18) and the National Natural Science Foundation of China (grant numbers U1738201, 61625503, 11822409, 11674309, 11654005 and 61771443).
Author information
Authors and affiliations.
Hefei National Laboratory for Physical Sciences at the Microscale and Department of Modern Physics, University of Science and Technology of China, Hefei, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Branch, CAS Center for Excellence in Quantum Information and Quantum Physics, University of Science and Technology of China, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Xiang-Bin Wang, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Research Center for Quantum Science, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Key Laboratory of Space Active Opto-Electronic Technology, Shanghai Institute of Technical Physics, Chinese Academy of Sciences, Shanghai, China
Liang Zhang, Rong Shu & Jian-Yu Wang
The Institute of Optics and Electronics, Chinese Academy of Sciences, Chengdu, China
Yong-Mei Huang
Shanghai Engineering Center for Microsatellites, Shanghai, China
Mathematical Institute, University of Oxford, Oxford, UK
Artur K. Ekert
Centre for Quantum Technologies, National University of Singapore, Singapore, Singapore
You can also search for this author in PubMed Google Scholar
Contributions
C.-Z.P., A.K.E. and J.-W.P. conceived the research. J.Y., C.-Z.P. and J.-W.P. designed the experiments. J.Y., Y.-H.L., S.-K.L., M.Y., Y.C., J.-G.R., S.-L.L., C.-Z.P. and J.-W.P. developed the follow-up optics and monitoring circuit. J.Y., Y.-M.H., C.-Z.P. and J.-W.P. developed the efficiency telescopes. J.Y., S.-K.L., Y.C., L.Z., W.-Q.C., R.S., L.D., J.-Y.W., C.-Z.P. and J.-W.P. designed and developed the satellite and payloads. J.Y., L.Z., W.-Q.C., W.-Y.L. and C.-Z.P. developed the software. F.X., X.-B.W., A.K.E. and J.-W.P. performed the security proof and analysis. L.L., Q.Z., N.-L.L., Y.-A.C., X.-B.W., F.X., C.-Z.P., A.K.E. and J.-W.P. contributed to the theoretical study and implementation against device imperfections. F.X., C.-Y.L., C.-Z.P. and J.-W.P. analysed the data and wrote the manuscript, with input from J.Y., Y.-H.L., M.Y., Y.C. and A.K.E. All authors contributed to the data collection, discussed the results and reviewed the manuscript. J.-W.P. supervised the whole project.
Corresponding authors
Correspondence to Cheng-Zhi Peng or Jian-Wei Pan .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Extended data figures and tables
Extended data fig. 1 satellite-to-delingha link efficiencies under different weather conditions..
a , The data in previous work 23 was taken in different orbits during the period of 7 December 2016 to 22 December 2016. b , The data in current work was taken in different orbits during the period of 6 September 2018 to 22 October 2018. Here the change of link efficiencies on different days was caused by the weather conditions.
Extended Data Fig. 2 Multiple orbits of satellite-to-Delingha link efficiencies under good weather conditions.
Stable and high collection efficiencies were observed during the period of October 2018 to April 2019.
Extended Data Fig. 3 The comparison of satellite-to-Delingha link efficiency under the best-orbit condition.
a , After improving the link efficiency with high-efficiency telescopes and follow-up optics, on average, the current work shows a 3-dB enhancement in the collection efficiency over that of ref. 23 . The lines are linear fits to the data. b , Some representative values.
Extended Data Fig. 4 The finite-key secret key rate R versus the QBER.
For the 3,100 s of data collected in our experiment, a QBER of below about 6.0% is required to produce a positive key. The previous work 23 demonstrated a QBER of 8.1%, which is not sufficient to generate a secret key. In this work, a QBER of 4.5% and a secret key rate of 0.12 bits per second are demonstrated over 1,120 km. If one ignores the important finite-key effect, the QBER in ref. 23 is slightly lower than the well known asymptotic limit of 11% (ref. 43 ).
Extended Data Fig. 5 Schematics of the detection and blinding-attack monitoring circuit.
The biased voltage (HV) is applied to an avalanche photodiode through a passive quenching resistance ( R q = 500 kΩ) and a sampling resistance ( R s = 10 kΩ). The avalanche signals are read out as click or no-click events through a signal-discrimination circuit. The blinding signal monitor is shown in the dot-dash diagram. A resistor-capacitor filter and a voltage follower are used to smooth and minimize the impact on the signals. The outputs of an analogue to digital converter (ADC), at a sampling rate of 250 kHz, are registered by computer data acquisition (PC-DAQ). R1, resistor; C1, capacitor; OA, operational amplifier.
Extended Data Fig. 6
The transmission of the beam splitter within the selected bandwidth of wavelength.
Rights and permissions
Reprints and permissions
About this article
Cite this article.
Yin, J., Li, YH., Liao, SK. et al. Entanglement-based secure quantum cryptography over 1,120 kilometres. Nature 582 , 501–505 (2020). https://doi.org/10.1038/s41586-020-2401-y
Download citation
Received : 15 July 2019
Accepted : 13 May 2020
Published : 15 June 2020
Issue Date : 25 June 2020
DOI : https://doi.org/10.1038/s41586-020-2401-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Verifying the security of a continuous variable quantum communication protocol via quantum metrology.
- Lorcán O. Conlon
- Biveen Shajilal
- Syed M. Assad
npj Quantum Information (2024)
Quantum key distribution over a mimicked dynamic-scattering channel
- Fang-Xiang Wang
- Zheng-Fu Han
Science China Information Sciences (2024)
Quantum-secured time transfer between precise timing facilities: a field trial with simulated satellite links
- Francesco Picciariello
- Francesco Vedovato
- Florian Moll
GPS Solutions (2024)
FSO-QKD protocols under free-space losses and device imperfections: a comparative study
- Mitali Sisodia
- Joyee Ghosh
Quantum Information Processing (2024)
Analysis and protection to user privacy in quantum private query with non-ideal light source
- Yang-Fan Jiao
- Bing-Jie Xu
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
Double layer security using crypto-stego techniques: a comprehensive review
- Review Paper
- Published: 13 October 2021
- Volume 12 , pages 9–31, ( 2022 )
Cite this article

- Aiman Jan 1 ,
- Shabir A. Parah ORCID: orcid.org/0000-0001-5983-0912 1 ,
- Muzamil Hussan 1 &
- Bilal A. Malik 2
5135 Accesses
9 Citations
Explore all metrics
Recent advancement in the digital technology and internet has facilitated usage of multimedia objects for data communication. However, interchanging information through the internet raises several security concerns and needs to be addressed. Image steganography has gained huge attention from researchers for data security. Image steganography secures the data by imperceptibly embedding data bits into image pixels with a lesser probability of detection. Additionally, the encryption of data before embedding provides double-layer protection from the potential eavesdropper. Several steganography and cryptographic approaches have been developed so far to ensure data safety during transmission over a network. The purpose of this work is to succinctly review recent progress in the area of information security utilizing combination of cryptography and steganography (crypto-stego) methods for ensuring double layer security for covert communication. The paper highlights the pros and cons of the existing image steganography techniques and crypto-stego methods. Further, a detailed description of commonly using evaluations parameters for both steganography and cryptography, are given in this paper. Overall, this work is an attempt to create a better understanding of image steganography and its coupling with the encryption methods for developing state of art double layer security crypto-stego systems.
Similar content being viewed by others

Image encryption techniques: A comprehensive review

PSNR vs SSIM: imperceptibility quality assessment for image steganography

Video steganography: recent advances and challenges
Avoid common mistakes on your manuscript.
1 Introduction
The increasing bandwidth and data rates of 4G/5G cellular technology and optical fiber communication revolutionized data communication. The exchange of data in form of text, images, audio, and video over the internet has become ubiquitous [ 1 ]. The multimedia data is being exchanged by governments, law enforcement agencies, and for telemedicine by the hospitals [ 2 ]. During the covid-19 worldwide lockdown traffic of information over the internet saw an upsurge. Although internet usage has various advantages, but security and privacy of data still remain a challenge [ 3 ]. Data thefts, modifications, and alterations have become possible due to the availability of various tools in the hands of hackers. Thus, the security of data has become a challenging task of paramount importance for researchers [ 4 ]. Various information protecting mechanisms like, cryptography and data hiding methods as shown in Fig. 1 , have been put forward to address data security issues [ 5 ]. Cryptography scrambles and converts the secret data into an unreadable form for an unauthorized person [ 6 , 7 ]. Cryptography can be performed either with standard encryption techniques or Chaos based encryption techniques [ 8 ]. There are various standard encryption techniques (SET), like Data Encryption Standard (DES), Advanced Encryption Standard (AES), and Rivest Shamir Adleman algorithm (RSA), etc. [ 9 ]. In these approaches, the secret key is used to encrypt the important data before embedding [ 10 ]. However, the bulk of data with key lengths is the main limitation of the SETs which makes them insecure and less reliable for data encryption [ 11 ]. The limitation of SETs has been overcome by the chaos based encryption approaches. Chaos encryption approach uses initial keys for encryption that are sensitive to the changes made [ 12 ]. Thus, the chaos-based encryption approaches are more secure cryptographic method to ensure security to the data [ 13 ]. Cryptography can provide the considerable security to the data by changes the form of the original data through encryption. But, cryptography alone cannot resist security attacks, as its encrypted form attract attacker’s attention and hence can be modified or hacked. However, it is an insufficient method to provide data security as its encrypted form may draw the attention of an eavesdropper [ 14 ]. Hence, data hiding has been used widely by researchers to hide the existence of important data without being noticed by an intruder [ 15 , 16 , 17 ].
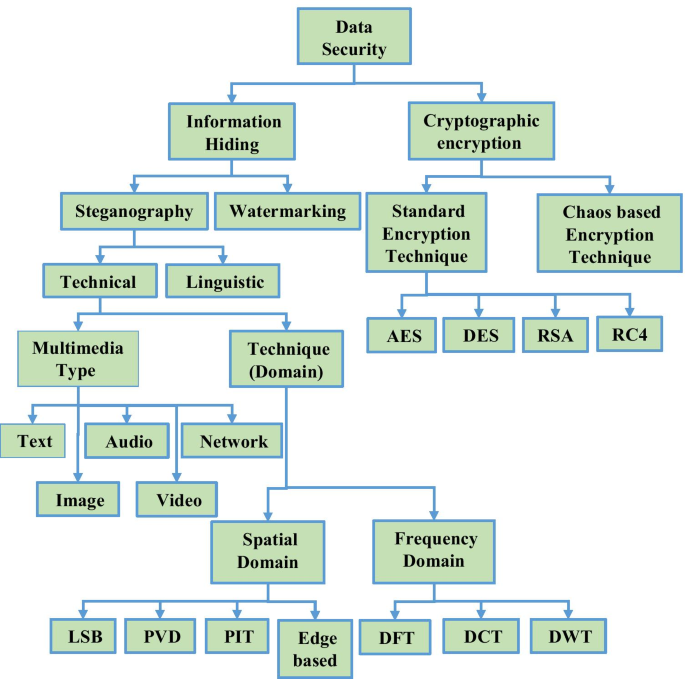
Different Information Protecting Mechanisms
Data hiding can be divided into two methods: steganography and watermarking [ 18 ]. Watermarking is the method of verifying the authenticity of multimedia (image, video, or audio) for copyright protection [ 19 ]. It can be either visible or invisible watermarking to authenticate the ownership. Steganography is the art of hiding important data into any multimedia for secret communication [ 20 ]. It is an invisible process in which detection of data is not easy. Steganography can be separated into two categories: Technical and Linguistic steganography approaches [ 21 ]. Technical steganography can be further subdivided into two sections based on the multimedia used and the technique applied. Steganography technique has various advantages associated with it, the only difficulty of it is to maintain the image quality with a good amount of payload [ 22 ]. Huge secret data size degrades the quality of an image that can suspect the presence of data [ 23 ]. And, if the eavesdropper detects the steganographic method, it can easily recover the data. So, with the concealing approach, data should be preprocessed by including some cryptographic approaches [ 24 ]. Hence, the present trend is of crypto-stego mechanism in which along with steganography, cryptography method is included to provide double layer security to the data as shown in Fig. 2 .
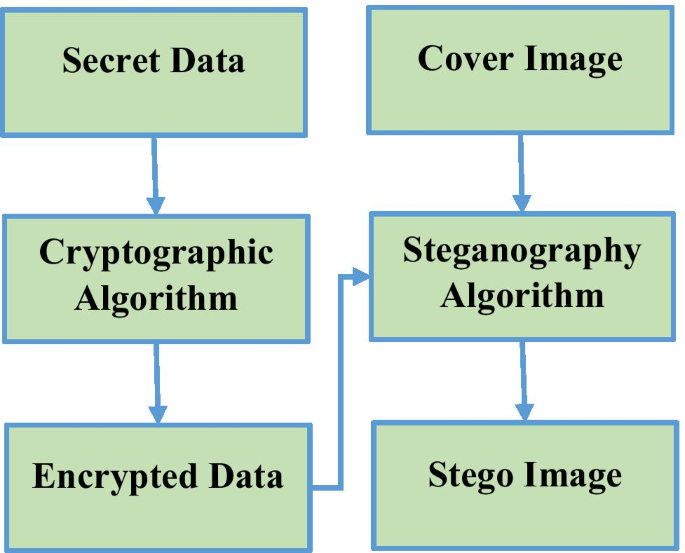
General Steganography approach together with Cryptography (Crypto-Stego)
PSNR value of existing method for 0–2 bpp embedding capacity
PSNR value of exisitng method for 2–6 bpp embedding capacity
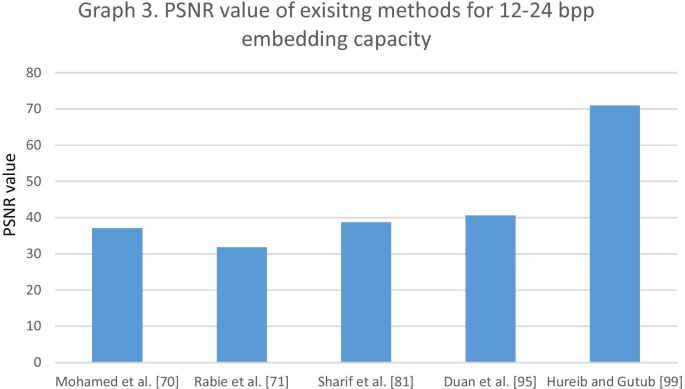
PSNR value of exisitng methods for 12–24 bpp embedding capacity
In this paper, the most recent literature in the area of steganography and crypto-stego has been reviewed to facilitate an exhaustive reference for further research in this area. This paper further discusses the various state-of-art techniques, their limitations, and challenges. The analysis parameters have been also discussed. The main contributions of this paper is:
A comprehensive review of various image crypto-stego methods has been presented.
Various parameters for evaluation of crypto-stego schemes have been presented.
A deep insight into double layer schemes and future research directions have been presented.
The rest of the paper is organized as follows. Section 2 includes the literature survey. Evaluation parameters are discussed in Sect. 3 . Section 4 comprises the directions and future research directions. The paper concludes in Sect. 5 .
2 Literature survey
Steganography is the art of concealing data into any multimedia for covert communication [ 25 ]. Steganography can be divided into many types based on the cover object used to attain security, like text, image, audio, video, and network [ 26 , 27 , 28 , 29 , 30 , 31 ]. Further, the steganography can be divided into two domains based on the techniques used to hide data in any multimedia, i.e., spatial domain technique and frequency domain technique [ 32 ]. Special domain can be further subdivided into various versions, like least significant bit (LSB), pixel value differencing (PVD), pixel indicator technique (PIT), Edge based technique [ 33 ]. Frequency domain can be also subdivided into different types, like discrete fourier transform (DFT), discrete cosine transform (DCT), discrete wavelet transform (DWT) [ 34 ]. In this section, the existing literature on different steganographic techniques and crypto-stego has been discussed. The paper focuses on an analysis of publications in reputed journals from 2016–2021 to be taken into consideration for future work. The various steganography data hiding technique and its coupling with cryptographic approaches have been discussed in the subsequent sections. Incorporating cryptography with the steganographic approach provides better security to the data, therefore using the steganography technique alone is ‘less secure’ compare to the combined approach. As once the steganographic pattern gets revealed to the unintended user, the secret data is prone to hacks and modifications.
2.1 Spatial domain technique
A detailed description of the spatial domain based image steganography techniques has been presented. Table 1 highlights the pros and cons of the reviewed spatial domain techniques.
In 2021, AbdelRaouf [ 35 ] has proposed a novel image steganographic data hiding method. The method has used the adaptive least significant bit (LSB) method for hiding information into every color channel of an image. The method has a huge payload but takes more time for embedding data into an image. Although the technique shows considerable image quality values, however, the proposed method can be improved by introducing an encryption method before embedding to improve security. In 2021, Hussain et al. [ 36 ] have put forth an enhanced adaptive data hiding approach in which the least significant bit (LSB) and pixel value differencing (PVD) methods have been used for increasing hiding space. The method has good imperceptibility and embedding capacity. The proposed approach has focused only on payload and imperceptivity. The technique can be improved in the security domain by incorporating an encryption algorithm. In 2020, Sahu and Swain [ 37 ] have suggested Dual-layer based reversible image steganography using modified least significant bit (LSB) matching. In this approach double layer embedding has been performed to improve image quality. In the first layer, two bits of the secret data are embedded into each pixel using modified LSB matching to develop intermediate pixel pair (IPP). Whereas, in the second layer, four bits of secret information are embedded using IPP. The technique is good enough to provide a good payload with better image imperceptivity. The proposed approach can be enriched by introducing security algorithms to enhance the security of the data embedded in an image. Also, the proposed method can be extended to color images and can be improved to reduce processing time. In 2017, Hussain et al. [ 38 ] have presented a data hiding method to achieve high payload, good visual quality, and maintain security. This method is based on two novel approaches: parity-bit pixel value difference (PBPVT) and improved rightmost digit replacement (iRMDR). In this method, the cover image is separated into two non-overlapping pixel blocks. The embedding algorithm PBPVD (higher level ranges) or iRMDR (lower level ranges) are selected according to the difference value between two pixels in each block. The PBPVD technique increases embedding capacity and iRMDR attains good visual imperceptivity. However, the method can be improved by establishing a security related algorithm to improve the reliability of the method against attacks. Further, the scheme can be extended for color images also.
In 2018, Malik et al. [ 39 ] have come-up with a new data hiding approach using absolute moment block truncation coding (AMBTC) compression. In this method, AMBTC compresses the cover image to embed important data into the compressed pixel values. The method is able to maintain image quality with a good payload. However, security can be improved by incorporating cryptographic approaches. In 2019, Kumar et al. [ 40 ] have proposed an enhanced method of data hiding using absolute moment block truncation coding (AMBTC) using pixel value differencing (PVD) and hamming distance. The cover image is compressed with AMBTC and is divided into three sections: smooth, less-complex, and highly-complex blocks. One bit per pixel is embedded into smooth blocks, 8-bits are embedded into a less-complex block using hamming distance calculation, and more data bits are embedded into a highly-complex block using the PVD technique. The method produces a good embedding space. However, can be extended in the security domain to further increase security to the data.
In 2020, Chakraborty and Jalal [ 41 ] have put forth a novel image hiding method using local binary pattern (LBP). In this scheme, the cover image is separated into 3 × 3 non-overlapping blocks. The reference pixel of each block is encoded using LBP. The encoded image is XORed with the secret image. The image has been shuffled further to embed secret image bits in the LSB of the cover image. The method has strong statistical features against attacks. The presented method can be further extended to embed data by applying payload-specific hand-crafted descriptors. In 2020, Lin et al. [ 42 ] have proposed a new image hiding method for Dynamic GIF (Graphics Interchange Format) images. The presented scheme is based on the Palette sort. In this method, the cover image is decomposed into frames (static GIF image). A new distortion function is applied to all frames. The data is then embedded into these frames to form the stego frames. In this technique, the data is secured by hiding it into an image but with less payload. In 2018, Parah et al. [ 43 ] have presented computationally efficient and reversible data hiding method for secure electronic health record (EHR) communication. In this method, modular arithmetic has been used for embedding EHR into a medical image. Prior to embedding, the cover medical image is scaled up using the pixel reputation method. The proposed scheme has improved image quality with a better amount of payload but takes a good amount of time for embedding data into an image. The security of the method can be improved by implementing some encryption method. The technique can also be extended to color images to increase EHR embedding capacity.
In 2021, Li et al. [ 44 ] have suggested a high capacity image steganography technique. The method has used retracing extended Sudoku (RE-Sudoku) reference matrix for data embedding. The paper has an enhanced payload with good image quality. The method can be improved in security domain to enhance its superiority. Also, the method can be analyzed on color images to show its generality. In 2020, Saha et al. [ 45 ] have come up with a new image hiding method using a hashed-weightage Array. The method is based on extended exploiting modification direction (EMD) that creates less distortion in an image. The presented method has improved payload and reduces distortion of an image than the existing method. The security of proposed scheme can be enhanced by encrypting the secret data. In 2018, Shen et al. [ 46 ] have proposed a new data hiding method based on improved exploiting modification direction (EMD) and interpolation techniques with consideration of human visual system (HVS). In this scheme, the cover image is separated into various 3 × 3 non-overlapping blocks. The presented method hides data into each block by calculating the neighbor mean value and the difference value. The discussed method has improved embedding efficiency and quality than the traditional EMD technique. The presented method takes more time for processing the task. The scheme can be enriched by applying stegna-analysis resist method to improve security. Moreover, the technique can be improved by applying it to color images as well.
In 2016, Bairagi et al. [ 47 ] have put forth an efficient image steganography method for secure communication in the Internet of Things (IoT) infrastructure. This article has presented three information hiding approaches using RGB image steganography. In this method, data has been embedded in an image using a secret key and carrier information. The technique has improved the security of the data than the traditional steganographic techniques. This work can be enhanced by applying encryption approaches for security improvement. In 2020, Rim et al. [ 48 ] have presented a Beta chaotic map based image hiding method. The method used a Beta chaotic map to sort the embedding positions of an image. The simple least significant bit (LSB) technique has been used to embed data into an image. The technique has provided good security to the data than the traditional steganographic approaches. However, the method can be improved to gain more capacity with good image quality. In 2021, Hassan and Gutub [ 49 ] have introduced an efficient image reversible data hiding (RDH) approach. In this method, interpolation optimization has been used to scale up the original image before embedding. The advantage of this method is a good image quality with a huge payload. However, the cryptographic technique can be applied to the secret data before embedding to enhance security.
2.2 Edge based technique
This subsection discusses different edge-based image steganography methods. Table 2 highlights the pros and cons of these techniques after analyzing the surveyed papers.
In 2021, Atta and Ghanbari [ 50 ] have put forth a new data hiding mechanism based on dual tree complex wavelet transform (DT-CWT). In this method, the cover image has been divided into subbands and neutrosophic edge detector (NSED) has been applied on these subbands to attain edge areas. The secret data is embedded into the detected subband edge regions of an image. The method has been able to get good imperceptivity with a good amount of payload. However, needs to secure data by applying some encryption algorithms. In 2019, Dhargupta et al. [ 51 ] have proposed an image steganography approach using Fuzzy edge detection (FED). In this approach, edges of the cover image are detected by FED to embed data into edge areas of an image. Data to be embedded in an edge region depends upon the Euclidean distance and is determined by the Gaussian function. The technique shows good embedding capacity, but with an increase in payload, its quality gets degraded. The method has been applied only on grayscale images. In 2019, Ahmadian and Amirmazlaghani [ 52 ] have suggested a secret image sharing steganography scheme. This method is dependent on fully exploiting modification direction (FEMD) and edge detection technique to embed data into the cover image. The method has been able to improve image quality than the existing methods, but, has less embedding space. In 2018, Kich et al. [ 53 ] have offered an edge detection method based image steganography method. In this approach, secret information has been dissimulated into edge pixels of an image using modified simple linear iterative clustering (M-SLIC) algorithm. The technique has a good payload, robustness, and imperceptivity. However, the scheme can be also upgraded in the security domain. In 2018, He et al. [ 54 ] have suggested a reversible information hiding method using edge information. The method has been proposed for high dynamic range (HDR) color images. The data has been embedded into HDR color images by using edge information. The approach has achieved less visual distortion after embedding secret data into an image. However, the security of the data by preprocessing has not been considered to increase data security. In 2018, Gaurav and Ghanekar [ 55 ] have introduced an edge region detection based image steganography technique. The secret data has been embedded into the least significant bit (LSB) bits of edge pixels. The approach has good image quality with a better payload. However, can be improved to insert a cryptographic approach along with a steganographic method to ensure better security to the data. In 2020, Prasad and Pal [ 56 ] have introduced a new image steganography algorithm, using edge detector and modulus function. For embedding, the modulus function has been used, whereas, edge detector has been used to find edge locations to embed data into edge areas. The method has been tested only on greyscale images. Further, the technique can be improved by introducing an encryption algorithm to increase security.
In 2019, Mukherjee and Sanyal [ 57 ] have presented an edge based image steganography method with a variable threshold. The edges of an image have been detected by the Sobel edge detector with respect to the threshold key. These detected regions are used to hide secret information. The scheme has gained good image quality with considerable hidden data capacity. The suggested method can be further improved by incorporating encryption schemes to the embedding data before hiding. In 2018, Kadhim et al. [ 58 ] have put forth an adaptive image steganography technique. The technique is based on edge detection over dual-tree complex wavelet transform (DT-CWT). Edge regions of an image have been detected using the canny edge detection method. Even though the method has good embedding capacity and image quality, however, can be extended in the security domain to increase data security against attacks. In 2018, Ghosal et al. [ 59 ] have put forth an image steganography technique based on the Laplacian of Gaussian (LoG) edge detector. In this approach, the data has been embedded into all non-edge pair, edge pair and mixed pair of an image. By this technique, the burden of payload into the traditional method of embedding all data into edge areas only has been reduced. The method no doubt has increased payload and image quality. However, the technique can be further enhanced in the security domain. In 2021, Ghosal et al. [ 60 ] have suggested an image hiding approach based on the Kirsch edge detector. In this method, the data has been embedded into both edge and non-edge regions of an image in such a way that image distortion is minimized. The method has improved payload with less image distortion. The proposed method can be improved by applying a cryptographic method to enhance security. In 2019, Banik et al. [ 61 ] have discussed an image steganography method for embedding capacity improvement. The technique has used Kirsch detector to find the edge regions of an image for data hiding. The threshold value has been used as a key to embed data into edge areas of an image. The technique has good image quality with a good payload. The algorithm has been implemented only on greyscale images. Thus, the method can be extended to color images as well. In 2020, Wang et al. [ 62 ] have presented a high capacity hybrid steganography method based on the least significant bit (LSB) and hamming code (HLAH). In this technique, the color cover image is separated into 9 × 9 blocks and the red (R) plane is extracted. The LSB of the R plane is set to ‘0’ and then the canny edge detection technique is used to find the edges of a plane. The method has used the canny edge detection technique to find edges. The data is embedded into the non-edge and edge regions using LSB and (3,1) hamming code. The method has been able to provide a good payload with better image quality than the existing methods. However, the security of the algorithm can be improved by encrypting the secret data prior to embedding.
In 2020. Tripathy and Srivastava [ 63 ] have proposed an edge based data hiding technique using Modulus-3 strategy and comparative analysis. In this method, the data has been changed into ternary data and has been embedded into edge areas of an image using the Modulus-3 strategy. The edge regions have been detected with Sobel, Prewitt, Canny, and Laplacian edge detectors. The method has been able to hide a vast amount of data into an image with good visual image quality. However, the security of the secret data can be further improved by introducing an encryption method along with the proposed algorithm. In 2019, Tuncer and Sonmez [ 64 ] have introduced the image steganography algorithms based on edge detectors and a 2 k correction scheme. The method has used Sobel, Canny, Laplacian of Gaussian (LoG), block based edge detection (BED), and hybrid edge detectors (HED) to find edge pixels of an image. These detected regions have been used to embed data into it using the least significant method (LSB) and 2 k correction method. The technique has the good capacity with good visual quality, but, has not improved much upon security parameter.
2.3 Frequency domain technique
A thorough summary of the techniques reviewed under the frequency domain is given as follows and their pros and cons are pointed out in Table 3 .
In 2021, Abdel-Aziz et al. [ 65 ] have offered an improved data hiding method for securing color images. In this work, the authors have used a hyper chaotic map and left-most significant bit (LMSB) embedding method to embed data into an image. In this approach, the cover image has been first encrypted using a hyper chaotic map to form the encrypted image and is then converted into the YCbCr channels. Of them, the first channel (Y) has been divided into non-overlapping blocks using the DCT technique. The resulted blocks are quantized and secret data has been embedded into frequency coefficients of these quantized discrete cosine transform (DCT) blocks using Huffman coding. The output stego image is further XORed with the remaining two channels (CbCr) to form the encrypted stego image. The scheme has good security and image quality. However, an encrypted form of stego image can suspect the presence of data. Also, the technique can be extended for embedding any type of data into color images. In 2021, Yao et al. [ 66 ] have presented a reversible data hiding (RDH) approach for dual JPEG images. In this method, the cover image is preprocessed to attain DCT coefficients and to ascribe embedding space. Then, secret data has been embedded into obtained frequency coefficients of image pixels using the dual-JPEG RDH scheme. The technique has gained a considerable embedding space with good visual image quality. However, the secret data to be embedded has not been preprocessed to improve data security. In 2018, Liu and Chang [ 67 ] have suggested a reversible data hiding (RDH) technique for JPEG images for hiding a great amount of data. In this approach, the discrete cosine transform (DCT) technique has been used to gain the coefficient values for non-overlapping 8 × 8 blocks. The quantization method has been applied to each block of an image to attain JPEG quantized block. Then, the AC coefficients are scanned in a zigzag direction to embed secret data into non-zero elements. The proposed method has been able to gain good image quality with considerable payload, but, the enhancement of security to the data with preprocessing has not been taken into consideration. In 2018, Attaby et al. [ 68 ] have put forth a novel data hiding approach using discrete cosine transform (DCT) to embed data into JPEG images. The difference value of two DCT coefficients using modulus 3 has been applied to insert two secret data bits into the values of the coefficients of an image. This significantly reduces the image distortion with improvement in image embedding space. However, the data security of the scheme can be improved by applying a cryptography approach to secret information before embedding. In 2016, El-Rahman [ 69 ] has given a new steganographic tool to hide data into the frequency domain of an image using the discrete cosine transform (DCT) method. The technique has hidden the important information about nuclear reactor in the middle frequency. The scheme is able to protect image quality with a high considerable amount of embedding capacity. However, the confidential information of the nuclear reactor needs to be more secure from any thefts. Therefore, encryption of important information before embedding could be more effective for data security. In 2020, Mohamed et al. [ 70 ] have presented an L*a*b* (luminance channel ‘L*’ and chrominance channels ‘a*and b*’) color space image steganography technique using quad-trees. The method has applied the quad-tree of the gray-scaled cover to the RGB of the cover image. The resultant blocks of the quad-tree are transformed to L*a*b* color space using 2dimentional-discrete cosine transform (2D-DCT) to embed data into the largest zero areas of DCT. The method has considerable embedding capacity, good image quality, and secure than the existing spatial and frequency domain steganography methods. However, the technique is complex. In 2018, Rabie et al. [ 71 ] have suggested increased embedding space and image quality data hiding scheme based on transform domain mechanism. The presented scheme uses the quad tree segmentation method to divide the blocks of the cover image. In each block, quantization step and piecewise linear curve fitting are used to hide secret data in the least significant areas of discrete cosine transform (DCT) coefficient areas. The method has tried to gain a better image payload. However, the data is embedded directly without pre-processing that may lead to security issues. In 2017, Saidi et al. [ 72 ] have put forth a new steganographic approach Based on discrete cosine transform (DCT) and chaotic map. The presented approach is used to find coefficients of the cover image. Piecewise linear chaotic map (PWLCM) has been used to scramble embedding positions to improve security to the embedding data. The algorithm has a good payload, however, the technique has poor image imperceptivity. Also, the technique can be improved further to resist any statistical attacks.
In 2018, Nipanikar et al. [ 73 ] have discussed a sparse representation based image steganography technique using particle swarm optimization (PSO) and discrete wavelet transform (DWT) approaches. These approaches have been used to locate the appropriate pixels for embedding speech signal in the cover image. The method is able to achieve good image imperceptibility and payload. However, the algorithm can be extended in the security domain to enhance data security. In 2018, Nevriyanto et al. [ 74 ] have presented an image steganography method using discrete wavelet transform (DWT) and singular value decomposition (SVD) techniques. In this scheme, a text file has been converted into an image to form a watermark for embedding it into an image. The secret watermark has been embedded into the frequency coefficients of an image using the SVD method. The method can be further made secure enough against attacks by incorporating encryption methods on the data and can be also extended to color images. In 2018, Miri and Faez [ 75 ] have introduced an image steganography technique for hiding important data into frequency coefficients of an image. This method has used the integer wavelet transform (IWT) method to obtain the frequency coefficients of an image. The method has been analyzed on greyscale images that can be extended to color images. The security of the data can be further improved by introducing encryption methods to the secret data before embedding. In 2019, Kalita et al. [ 76 ] have proposed a new steganography method using integer wavelet transform (IWT) and the least significant bit (LSB) substitution method. To estimate the embedding capacity, the coefficient value differencing method has been applied. The scheme has good visual quality of an image and considerable embedding capacity. However, the data can be secured from statistical attacks by introducing encryption algorithms. In 2021, Ghosal et al. [ 77 ] have presented exploiting Laguerre transform (LT) based image hiding method. In this scheme, the cover is separated into m-pixel non-overlapping groups. Each pixel of these groups is then transformed into its equivalent coefficients using LT. The secret data is embedded into these coefficients. The resulted pixels are adjected to minimize distortion and have been recomputed by applying inverse LT (ILT). The presented scheme has been able to increase payload with good image quality but takes more time for completing the process. However, the method can be secured by encrypting the data. In 2019, Ma et al. [ 78 ] have come up with a new reversible data hiding (RDH) approach for medical images. The method is based on block classification and code division multiplexing (CDM). In this scheme, the non-overlapping blocks of the medical image are categorized into smooth and texture groups by calculating mean square error (MSE). The secret information has been embedded into transformed frequency coefficients using the integer-to-integer discrete wavelet transform (IDWT) technique of the texture block. The method has large data hiding capacity with good image imperceptibly. Security to the secret data can be further improved by applying cryptography approaches to the secret data prior to embedding. In 2020, Murugan and Subramaniyam [ 79 ] have proposed an image steganography technique to ensure the data security transaction over an insecure network. The data has been embedded into coefficient values of an image using the alpha factor. The image pixels have been transformed with the 2dimentional-Haar discrete wavelet transform (2D-Haar DWT) to gain four sub-bands. The method has good embedding space while preserving image quality than the existing schemes. Also, the proposed method is secure than already existing frequency domain techniques. However, the proposed method is complex.
2.4 Joint Crypto-stego schemes
This subsection includes the reviewed papers of different dual security image steganography techniques. These techniques have encrypted the secret data/ secret image with either standard encryption method or chaotic method before embedding to provide double layer security to the secret data. The pros and cons of different dual security image steganography methods are shown in Table 4 . The following subsections discuss the different combined image steganography and encryption techniques.
Simple domain crypto-stego schemes
The review of different special domain based image steganography and encryption methods are explained below:
In 2021, Maji et al. [ 80 ] have presented a spatial domain based image steganography method in which higher order pixel bits have been used to embed data. To encrypt data, XOR operation has been used to enhance security. Since the method has been implemented on the greyscale image. Thus, the presented approach can be extended to color images to prove its generality. In 2017, Sharif et al. [ 81 ] have presented an image steganography technique based on a 3-dimensional chaotic map. In this method, the pixel position for embedding changes with the change in the cover image. Thus, makes the system secure against any statistical attacks. However, the method can be improved in terms of complexity. In 2020, Gambhir and Mandal [ 82 ] have proposed chaos based least significant bit (CLSB) steganography method. The technique has used logistic map chaotic function to develop random numbers. The scheme shows good security and image quality results. However, can be improved further to increase embedding space to hide huge data into an image. In 2019, Prasad and Pal [ 83 ] have proposed logistic map based image steganography. This method has used the least significant bit (LSB) and pixel value differencing (PVD) techniques to embed data into the cover image. The embedding data is encrypted using a logistic map to improve security to the data. The proposed algorithm has attained better security. The technique can be modified in a different way to achieve better visual image quality and can be extended to color images also. In 2017, Mohammad et al. [ 84 ] have offered image steganography for visual contents authenticity. The method uses color model transformation, three-level encryption algorithm (TLEA), Morton scanning (MS). The data has been embedded with the direct least significant bit (LSB) substitution method using MS. TLEA has been used to encrypt data. The scheme provides the best algorithm for visual content authenticity in social networks. While the technique is complex and has less payload. In 2019, Alotaibi et al. [ 85 ] have proposed a secure framework for safe data transmission in mobile devices using hash, cryptography, and steganography. The proposed method has used a hash function for storing the secret password, cryptography with AES method for encrypting password, and LSB method for hiding encrypted password into an image. The method is able to provide a considerable amount of payload but has low visual quality of an image. In 2021, Mathivanan and Balaji [ 86 ] have suggested a QR code based color image stego-crypto technique. The method uses dynamic bit replacement and logistic map for embedding and encryption respectively. In this approach, the secret data is converted into 2D binary using base64 encoding method and QR code generator and is then embedded into an image using dynamic bit replacement technique. The image is then scrambled using a logistic map. The method is secure against differential attacks but is able to hide a low amount of secret data. In 2021, Abdelwahab et al. [ 87 ] have put forth an efficient image steganography technique to hide data for safe data transmission. In this scheme, plain text is encrypted using the RSA method and is embedded into the YCbCr components of an image using the LSB approach. The resulted stego image is then compressed using Huffman coding, Run Length coding (RLC), or DWT to form compressed stego image. The method has good amount of payload with considerable image quality. However, the scheme is complex.
Edge based crypto-stego techniques
Few edge detections based image steganography techniques along with data encrypting approaches are discussed as under:
In 2021, Parah et al. [ 88 ] have presented efficient security, high payload, and reversible electronic health record (EHR) data hiding approach. In this method, the cover image is scaled up with the pixel reputation method (PRM) and then the boundary conditions are applied to the image. The resulted image is divided into 2 × 2 blocks to embed data first into counter diagonal pixels and then to the main diagonal pixel after checksum computation. The EHR is secured by adding a watermark and applying the RC4 encryption method. The encrypted data is divided into 3-bit chunks and has been then embedded into the pixels after applying the left data mapping (LDM) method. The scheme has increased security to the data and has authenticated its originality. However, with a high payload, the quality of an image can be enhanced by testing the method to color images also. In 2016, Parah et al. [ 89 ] have proposed a new information hiding technique based on a hybrid edge detection method. In this scheme, the color image is separated into three planes (red, green, blue). The data is embedded into edge regions and non-edge regions of green and blue planes by making use of a hybrid edge detector. Whereas, the red plane is used to hold the bit status of green and blue planes. In order to authenticate and detect tempering the data, a fragile watermark is embedded. Before embedding, the secret information is encrypted using the RC4 algorithm. The algorithm is able to increase capacity with good image quality. Further, the security of the method is provided to the data by encrypting it prior to embedding. However, the time complexity of the method can be reduced by reducing the data extraction time. In 2020, Delmi et al. [ 90 ] have discussed the image hiding approach using the edge adaptive method and chaos cryptography technique. In this technique, the data has been encrypted using the Arnold Cat Map function. Whereas, the data has been embedded into the edge region of an image located by a canny edge detector. The technique although has increased security to the data. However, can be enhanced to increase payload with good image quality. In 2021, Sharma et al. [ 91 ] have suggested crypto-stego approach to prevent data from attacks. In this method, Rabin cryptosystem is used to encrypt the secret data, Arnold transform has been used to scramble the data, and the resulted data has been embedded into the edges of multiple images. The framework is able to provide better image quality with a considerable payload. However, the proposed approach is complex.
Frequency domain crypto-stego techniques
Different frequency domain based image steganography together with data encryption surveyed methods have been discussed in this subsection:
In 2016, Kaushik and Sheokand [ 92 ] have put forth a steganography scheme based on chaotic least significant bit (LSB) and discrete wavelet (DWT) approaches. In this method, the data is encrypted using a logistic map. Whereas, the encrypted data is embedded into frequency coefficients of the cover image using DWT by 3–3-2 LSB insertion scheme. The security of the proposed method has been increased by using the chaotic method. The method has good image quality but has less embedding capacity. In 2020, Panday [ 93 ] has suggested a new medical image steganography approach using a bit mask oriented generic algorithm (BMOGA). BMOGA has been used together with cryptographic features to encrypt data. In this approach, data has been embedded in the frequency coefficients of an image. Discrete wavelet transform (DWT) (1-level & 2-level) has been used to find frequency coefficients. The technique is secure and imperceptible, however, can be enhanced to gain a good payload. However, the scheme can be further modified to reduce the complexity of the algorithm. In 2018, Elhoseny et al. [ 94 ] have presented a secure medical data transmission model for internet of things (IoT) based healthcare systems. The method has used 2-D discrete wavelet transform (2D-DWT) to conceal data into both grayscale and color images. The secret information has been encrypted using a hybrid encryption scheme using advanced encryption standard (AES) and Rivest, Shamir, and Adleman (RSA) algorithms. The technique shows good image quality with good data security. However, the technique is complex.
In 2020, Duan et al. [ 95 ] have proposed a high-capacity image hiding scheme. In this method, the data have used encrypted with elliptic curve cryptography (ECC) approach. Discrete cosine transform (DCT) is applied to the secret image prior to encryption. A deep neural network has been used to increase the payload of the cover image. The method has been applied to both gray images as well as a color images. The method shows better security to the data. However, can be improved to reduce algorithm complexity. In 2018, Subhedar and Mankar [ 96 ] have presented image steganography using curvelet transform (CT) to embed secret information in the selected cover image. In order to obtain curvelet coefficients, level 6 CT has been applied to the cover image. Encryption data has been embedded into appropriate blocks by using standard deviation. Whereas, image block has been replaced with secret data block using spread spectrum when the deviation is higher than a threshold. The resulted stego image is obtained by applying inverse CT. In this technique, security has been heightened by encrypting the data using Arnold transform. However, it can be enhanced in payload and quality domain by testing it on the color image also. Further, the method is complex. In 2020, Eyssa et al. [ 97 ] have introduced an efficient image steganography method. In this approach, the data has been encrypted with the Baker map together with a discrete cosine map (DCT). The secret message in the presented method has been embedded into the values of the coefficients of an image. The security of the system has been increased. However, with a good amount of payload the image quality is less that needs to be enhanced. In 2021, Kaur and Singh [ 98 ] have introduced a new data hiding method based on discrete cosine transform (DCT) and coupled chaotic map. The secret data in this approach has been encrypted using coupled chaotic map of logistic and sine map. In this approach, the data has been embedded into the DCT coefficients of an image. The technique has a good payload, but, has been applied only on greyscale images and is complex.
Medical image crypto-stego techniques
The review of various medical image steganography together with data encryption has been discussed in this subsection:
In 2020, Hureib and Gutub [ 99 ] have proposed a combined cryptography and image steganography approach to enhance security in medical health data. In this method, Elliptic curve cryptography has been used to encrypt text before hiding. Then, the encrypted text is embedded into image pixels to hide its presence from the person who is not authorized. The technique has a good payload and image quality, however, it has not been tested for various attacks, like statistical attacks, etc. In 2020, another image steganography technique using elliptic curve cryptography has been presented [ 100 ]. The method has used 1-LSB and 2-LSB image steganography techniques to hide data into an image. The medical data has been embedded in the medical image after encrypting it with cryptography technique to improve data security. The method provides good image quality but has low embedding capacity. In 2019, Samkari and Gutub [ 101 ] have suggested a protecting mechanism for medical records against cybercrimes within the Hajj period. The method has used a 3-layer security system for medical record protection by encrypting data using hybrid cryptography method and hiding encrypted data into an image to produce stego-image for sending through the internet. The presented approach has good image quality and is safe for data transmission, however, the method is complex. In 2021, Denis and Madhubala [ 102 ] have put forth hybrid data encryption and hiding model for medical data security over cloud-based healthcare systems. In this scheme, a hybrid encryption model using AES and RSA algorithms has been used to convert the original data into an encrypted form. Whereas, the 2D-DWT and Adaptive Genetic Algorithm (AGA) based optimal adjustment method to conceal encrypted medical data into an image for safe data transmission. The proposed technique provides good image quality and is secure. However, the approach is complex and has low hiding space. In 2021, Manikandan et al. [ 103 ] have proposed an image steganography technique to secure e-health. In this approach, the secret image is first encrypted with the XOR cipher encryption and is then embedded into the cove image using LSB method. The framework has considerable image quality but provides low embedding capacity. In 2021, Ogundokum et al. [ 104 ] have presented crypto-stego medical information securing model. This technique uses international data encryption algorithm (IDEA) and Matrix-XOR techniques for enhancing security to the internet of medical things (IoMT) for the medical records protection. In this method, secret data has been encrypted using IDEA and is then embedded into carrier image using XOR. The method provides good visual quality of an image and is secure for medical data transmission. However, space for transmitting data in a concealed manner should be increased. In 2021, Prasanalakshmi et al. [ 105 ] have recommended a secure clinical data transmission technique in the internet of things (IoT) using hyperelliptic curve (HECC) and cryptography techniques. This approach has used AES and Blowfish hybrid cryptography for medical data encryption and HECC for embedding encrypted medical data into a medical image. The generated embedded image is then compressed with the 5-level DWT to attain a good payload and better security. The technique provides good image quality with considerable payload, however, the technique is complex.
From the literature, it has been observed that the use of cryptography and steganography together is able to provide double layer security to the data. Cryptography protects data from hacks, and in particular chaos based cryptography can be the better option for encryption because of its ergodicity and dependence on initial condition properties. And, incorporating a steganography approach with cryptography improves data security by concealing it into digital media. Data hiding using chaotic maps to locate and create a random sequence of pixels enhances data security. Also, concealing secret information in edge regions improves payload, can prevent cover image from noticeable distortion, and thus prevents attacks. Moreover, it has been observed that cryptography and steganography have widened their applications almost in all spheres of life, like in e-health, IoT, mobile devices, system login security, cloud, etc.
3 Evaluation parameters
Evaluation parameters are the tools used to check the efficiency, validity, and superiority of an algorithm. Outcomes of the analyzed scheme with various methods whose values lie between expected ranges prove the strength of the technique. The most common characteristics of image steganography and data encryption analysis are explained below in subsections.
3.1 Visual quality analysis
Steganography method alters the image by storing secret information inside pixels that affects the visual quality of an image. However, changes incorporated in an image should not be perceived by the invaders. There are various standard evaluating methods used to confirm the image quality strength, like, mean square error (MSE), peak signal to noise ratio (PSNR), structural similarity index (SSIM), etc. Table 5 summarizes the MSE, PSNR, NCC, NAE, and SSIM values achieved by different image steganography techniques in this study.
Mean square error (MSE):
MSE is the error measurement of the stego image with respect to its original image. It helps in comparing the difference between the pixel values of an original image and stego image. Lesser MSE value provides better quality of an image [ 106 ]. Therefore, the MSE value should be near ‘0’. MSE can be calculated as follows:
where p i and p i ’ respectively represent the pixel values of the original and stego image. And, n represents the image size.
Peak signal to noise ratio (PSNR):
PSNR is the visual quality measuring tool that measures the image alteration in the stego image compared to its original image. It estimates the difference in pixel values of a stego image in relation to its original image. For better image quality, the PSNR value should be more than 39dB [ 107 ]. PSNR values of different existing methods for different payloads are shown in Graphs 1 , 2 , and 3 below. PSNR can be measured as follows:
where MSE can be measured with Eq. 1 .
Normalized cross correlation (NCC):
NCC is the relation determination method of an image. It investigates the relationship between the original image and its corresponding stego image. A better correlation between images indicates better image visual quality. Hence, NCC near ‘1’ is considered as the good steganography algorithm [ 108 ]. NCC can be analyzed as follows:
where O and S respectively denote the original and stego image pixel values.
Normalized absolute error (NAE):
NAE calculates the error between the original image and stego image to measure image quality after embedding. Error between the images should be less (near ‘0’) to retain the image quality [ 88 ]. NAE can be expressed as follows:
where O is the original image pixel value and S is the stego image pixel value.
Structural similarity index (SSIM):
SSIM is the visual quality measuring tool to checks the similarity between the original and stego image. The value of SSIM close to ‘1’ (means 100%) represents the good image quality [ 109 ]. SSIM can be mathematically represented as follows:
where µ i and µ j are the mean intensity, σ i and σ j are the standard deviations, and σ ij is the cross-covariance of images i and j respectively.
3.2 Embedding capacity analysis
Embedding capacity (EC) is another steganographic analysis parameter that calculates the number of secret data bits embedded into a per pixel of an image. The bits per pixel (bpp) should be more while preserving image imperceptivity. EC can be examined as follows:
Here, size of an image is M × N × D, where M and N represents row and column of an image, and D represents the image pixel depth that can be either 1 or 3 depends upon the image selection (gray or color image). Therefore, maximum bpp for a grayscale image will be 8 and for color image it will be 24 (3 × 8 = 24). Embedding capacity for different image steganography techniques is shown in Table 5 .
3.3 Differential analysis
The strength of an algorithm is tested by checking the sensitivity of an encrypted image with its original image and secret key. The strength of an encryption algorithm should be strong enough to resist attacks. The well-known differential analysis is a number of pixel change rate (NPCR) and unified average change intensity (UACI).
Number of pixel change rate (NPCR):
NPCR is the security evaluating method that analysis the single pixel changes in the original image. It checks the sensitivity of the encrypted image compared to its original image and secret key. The acceptable NPCR value is 99.61% and closer to 100% is considered as the best encryption algorithm [ 110 ]. NPCR can be analyzed by the equation as follows:
where m and n are the image measurements. E T is the total number of unequal units. And, I o and I e are the original image and encrypted image respectively.
Unified average change intensity (UACI):
UACI is the other encrypted image strength checking method. It calculates the average intensity of the difference between the original image and encrypted image. More percentage difference in intensities ensures a good UACI value and the lowest acceptable UACI value is 33.44% [ 110 ]. UACI can be calculated by the equation as follows:
where I o and I e are respectively the original and encrypted images. And, m and n are the image measurements.
3.4 Entropy analysis
Entropy is the average information per bit existing in an image. It checks the pixel randomness of an encrypted image. The average range of entropy is between 0 to 8 and close to 8 for 8 bit is considered as the best entropy value [ 111 ]. Entropy can be computed as follows:
where S represents symbol collections, c i ϵ S , P(c i ) represents probability and n is the symbol number.
3.5 Key analysis
The key analysis is the main tool of an encryption algorithm for checking algorithm strength. The algorithm strength depends on key analysis. It can be checked in two ways: key space and key sensitivity analysis. Key space checks the size of the secret key used for encrypting an image. The larger size of the secret key makes the system secure against attacks, as it will be difficult for the unauthorized user to get the exact same key. Key sensitivity checks the sensitivity of the secret key to the changes made. Even a single bit change in the original key results in an altogether different image or unrecoverable image.
3.6 Statistical analysis
Statistical analysis checks the robustness of an encrypted image against attacks. The commonly used statistical analyses are histogram analysis and correlation coefficient for testing its robustness against attacks.
Histogram analysis represents the image by the number of data points within a definite range. The histogram gives the pixel distribution or uncommon forms of an image. Histogram analysis can be checked on stego image or encrypted image in comparison to the original image. In the steganography approach, the histogram deviations of the stego image with respect to its original image can suspect the presence of data in an image. Therefore, for histogram comparison of stego image, the stego image histogram should resemble the original image histogram to avoid statistical attacks. Whereas, the histogram of an encrypted image should be uniform to show its random behavior. Histogram uniformity among pixels claims the robustness of the encryption method. Thus, the histogram of an encrypted image should be uniform to prevent the data from statistical attacks.
Correlation coefficient (CC):
The correlation coefficient (CC) checks the relationship between the original image and the encrypted image. In the original image, the pixels are interconnected with each other in three different directions: horizontal, vertical, and diagonal. However, for encrypted images, the correlation range between the pixels is [1, 1] and near 0 (lesser correlated) is considered as the good encryption technique [ 112 ]. The correlation coefficient can be expressed as follows:
Here, i and j represent image coordinates and C(i, j) represents the covariance between them. σ(i) and σ(j) are the standard deviations of their respective image coordinates. m is the pixel pairs ( i n, j n ) number. And, x(i) and x(j) are the mean deviations of i n and j n respectively.
3.7 Randomness analysis
Randomness analysis checks the pixel haphazardness of an encrypted image. National Institute of Standards and Technology (NIST) [ 113 ] has developed a statistical test suite to find out the algorithm strength by analyzing several tests on an encrypted image. The NIST statistical test suite consists of almost 15 calculable tests. These tests include frequency test, frequency within block test, run test, longest run of ones in a block test, binary matrix rank test, discrete fourier transform (DCT) test, non-overlapping template matching test, overlapping template matching test, etc. This test is helpful in identifying deviations of a binary sequence of an encrypted image.
3.8 Speed analysis
Scheme efficacy is analyzed by the execution time of an algorithm to complete its task [ 114 ]. The execution time of a method depends upon the system configuration and the algorithm complexity. This analysis can be examined for different processing steps of a program, like, embedding process, encryption process, the extraction process, decryption process, etc. The execution time for any of the program steps should be as small as possible to make the method computationally efficient. The embedding and extraction of some image steganography techniques are shown in Table 6 .
3.9 Steganography effect on medical image accuracy analysis
Medical image accuracy analysis checks the accuracy and precision of resulted medical image after treating with the steganography method. The commonly used methods are accuracy, specificity, sensitivity, and precision, [ 115 ] for analyzing the performance and quality contents of an image after steganography.
Accuracy is the medical image quality content and prediction accuracy measuring tool. It is the ratio between all correct predictions (positive or negative) and the entire test set [ 115 , 116 ]. Accuracy can be measured by the Equation as follows:
where TP is true positive, TN is true negative, FP is false positive, and FN is false negative.
Specificity:
Specificity is also called as true negative rate (TNR). It is the ratio between the number of correctly predicted normal people and the total number of normal people [ 115 ]. Specificity can be calculated by the Equation as follows:
where TN is true negative and FP is false positive.
Sensitivity:
Sensitivity is also called true positive rate (TPR) and recall. It is the ratio between the correctly predicted people with a disease and the total number of actual diseased people [ 115 ]. Sensitivity can be computed as follows:
where TP is true positive and FN is false negative.
Precision is also called a positive prediction value (PPV). It is the ratio between the total number of positive predictions people with a disease and the total number of positive predicted people [ 115 ]. Precision can be expressed as follows:
where TP is true positive and FP is false positive.
4 Discussions and future research directions
For secure information transmission, the image steganographic technique is used to restrict intrusion. It embeds the secret data bits into the image pixels to hide the data from unauthorized extraction. Numerous image steganography techniques have been developed by researchers to ensure data security. New trends in image steganography are discussed in this comprehensive review. From the literature, it can be observed that most of the techniques have been able to provide security and safety to the data. The security of data has been enhanced by some of the crypto-stego techniques discussed to provide double layer security to the data. From the survey of the existing image steganography and crypto-stego techniques, it can be noticed that each algorithm has its advantages and disadvantages. A few of the important issues as future directions are highlighted below:
Using smooth regions for hiding data creates more distortion in an image and thus suspects the presence of data. Hiding data into the edge regions not only provides good image quality but increases the embedding capacity of an image. Therefore, edge based image steganography technique could be used to increase the hiding space and visual quality of an image.
Most of the image steganography methods discussed have taken grayscale images as a cover medium. Therefore, there is a need for developing and applying steganography methods also on color images to prove its versatility and to further increase payload.
Hiding data into the frequency coefficients of an image provides security to the data but provides less capacity and is a complex method. Therefore, robust algorithms should be developed in spatial domain to improve data security with less complexity for which the encryption of data together with steganography can be helpful.
Many of the existing image steganography approaches have tried to either improve payload, image quality, or security of the algorithm. Therefore, a good tradeoff between these parameters should be created to improve the overall performance of the method in all dimensions. For this, edge based image steganography and chaos based encryption methods could be used together. Although, the research in this field has been done by the researchers. Though, it is still an underdeveloped field that needs to be explored in various image steganography schemes and different chaotic maps.
A survey of the literature leads us to conclude that computational complexity is still an open area of research in the area of the image steganography method.
Experimental analysis of different reviewed techniques has not used all the evaluation parameters for analyzing the scheme. It can be observed from the survey that image steganography algorithms that encrypt data before embedding have not tested the technique for basic NPCR, UACI, and other security tools. To ensure strong security to the encrypted data. Therefore, every encryption method should be tested for different security tools.
The steganography approach should resist geometrical attacks, signal processing attacks, and noise attacks to ensure its reliability, so development of robust steganographic systems is an open area of research.
Several methods have been tested only on few image formats. Therefore, an effort should be done to create a benchmark dataset to compile the algorithm for different image formats.
5 Conclusion
Technological advancement is increasing exponentially to ease daily activities and for a fast service delivery system. For todays’ efficient communication system, the internet acts as a central pillar and reduces overconsumption of resources like time and cost. However, the internet is an open environment for data thefts, data modifications, etc. Therefore, to protect data/information from getting into the wrong hands, the image steganography method is used for ensuring data security. The purpose of this review paper is to present a comprehensive review of various image steganography and crypto-stego techniques with their pros and cons to help the reader understand different image crypto-stego techniques. This paper also gives insight into the evaluation parameters being used for steganography and cryptography analysis. This review is significantly highlights the grey areas in the area of the image steganography. Most of the existing image steganography approaches still suffer in terms of less security, low payload, poor image quality, and complexity. Therefore, it is a necessity to develop efficient image steganographic schemes along with data encryption to improve image embedding capacity, image imperceptibility, security with less complexity and should be resistant to different attacks.
Jan A, Parah SA, Malik BA, Rashid M. Secure data transmission in IoTs based on CLoG edge detection. Future Generation Computer system. 2021. https://doi.org/10.1016/j.future.2021.03.005 .
Article Google Scholar
Alsaidi A, lehaibi KA, Alzahrani H, Ghamdi MA, Gutub A. Compression multi-level crypto stego security of texts utilizing colored email forwarding. J Comp Sci Computational Math (JCSCM). 2018;8(3). https://doi.org/10.20967/jcscm.2018.03.002 .
Khan WZ, Aalsalem MY, Khan MK, Arshad Q. Data and Privacy: getting consumers to trust products enabled by the Internet of Things. IEEE Consumer Electronics Magazine. 2019;8:35–8. https://doi.org/10.1109/MCE.2018.2880807 .
Singh AK, Kumar B, Singh SK, Ghrera SP, Mohan A. Multiple watermarking technique for securing online social network contents using back propagation neural network. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.023 .
Alanazi N, Alanizy A, Baghoza N, Ghamdi MA, Gutub A. 3-Layer PC text security via combining compression, aes cryptography 2LSB image steganography. J Res Eng Appl Sci. 2018;3(4):118–124. https://doi.org/10.46565/jreas.2018.v03i04.001 .
Parah SA, Sheikh JA, Assad UI, Bhat GM. Hiding in Encrypted Images: A three tier security data hiding technique. Multidim Syst Sign Process. 2017;28(2):549–72.
Al-Roithy BO, Gutub A. Remodeling randomness prioritization to boost-up security of rgb image encryption. Multimed Tools Appl. 2021;80:28521–81. https://doi.org/10.1007/s11042-021-11051-3 .
Jan A, Parah SA, Malik BA. A novel laplacian of gaussian and chaotic encryption based image steganography technique. 2020 Int Conf Emerg Technol (INCET) Belgaum. 2020;1–4. https://doi.org/10.1109/INCET49848.2020.9154173 .
Luo Y, Yu J, Lai W, Liu L. A novel chaotic image encryption algorithm based on improved baker map and logistic map. Multimed Tools Appl. 2019;78:2023–22043. https://doi.org/10.1007/s11042-019-7453-3 .
Jan A, Parah SA, Malik BA. Logistic map-based image steganography using edge detection. Adv Intell Syst Comput. 2021;1189. https://doi.org/10.1007/978-981-15-6067-5_50 .
Patro KAK, Acharya B. A novel multi-dimensional multiple image encryption technique. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-019-08470-8 .
Li C, Feng B, Li S, Kurths J, Chen G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Transaction on Circuits and Systems-I: Regular Papers. 2019;66(6):2322–35. https://doi.org/10.1109/TCSI.2018.2888688 .
Article MathSciNet MATH Google Scholar
Hua Z, Jin F, Xu B, Huang H. 2D Logistic-Sine-Coupling map for image encryption. Elsevier Signal Process. 2018;149:148–61.
Khan M, Sajjad M, Mehmood I, Rho S, Baik SW. image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.029 .
Kim C, Yang CN, Leng L. High-capacity data hiding for ABTC-EQ based compressed image. Electronics. 2020;9(4):644.
Hussan FS, Gutub A. Improving data hiding within colour images using hue component of HSV colour space, CAAI Transactions on Intelligence Technology. IET (IEE). 2021. https://doi.org/10.1049/cit2.12053 .
Hassan FS, Gutub A. Novel embedding secrecy within images utilizing an improved interpolation-based reversible data hiding scheme. J King Saud University - Comp Information Sci. 2020;ISSN:1319–1578. https://doi.org/10.1016/j.jksuci.2020.07.008 .
Hussan M, Parah SA, Gull S, Qureshi GJ. Temper detection and self-recovery of medical imagery for smart health. Arab J Sci Eng. 2021. https://doi.org/10.1007/s13369-020-05135-9 .
Loan NA, Hurrah NN, Parah SA, Lee JW, Sheikh JA, Bhat GM. Secure and robust digital image watermarking using coefficient differencing and Chaotic encryption. IEEE transection. 2018. https://doi.org/10.1109/ACCESS.2018.2808172 .
Biswas R, Mukherjee I, Bandyopadhyay SK. Image feature based high capacity steganographic algorithm. Multimed Tools Appl. 2019. https://doi.org/10.1007/s11042-019-7369-y .
Hussain M, Wahab AWA, Idris YIB, Ho ATS, Jung KH. Image steganography in special domain: A survey. Signal Process Image Commun. 2018;65:46–66. https://doi.org/10.1016/j.image.2018.03.012 .
Wang J, Yang C, Wang P, Song X, Lu J. Payload location for JPEG image steganography based on co-frequency sub-image filtering. International J Distributed Sensor Networks 2020;16(1).
Ayub N, Selwal A. An improved image steganography technique using edge based data hiding in DCT domain. J Int Math. 2020;23(2):357–66.
Google Scholar
Patel SK, Saravanam C. Performance analysis of hybrid edge detector scheme and magic cube based scheme for steganography application. IEEE transection. 2018.
Jiang S, Ye D, Huang J, Shang Y, Zheng Z. SmartSteganography: Light-weight generative audio steganography model for smart embedding applications. J Netw Comput Appl. 2020;165: 102689. https://doi.org/10.1016/j.jnca.2020.102689 .
Prasad S, Pal AK. An RGB colour image steganography scheme using overlapping block-based pixel-value differencing. Royal Soc Open Sci. 2017;4.
Alkhudaydi M, Gutub A. Securing data via cryptography and Arabic text steganography. SN Computer Sci. 2021;2(46). https://doi.org/10.1007/s42979-020-00438-y .
Alkhudaydi MG, Gutub AA. Integrating light-weight cryptography with diacritics Arabic text steganography improved for practical security applications. J Information Security Cybercrimes Res 2020;3(1), 13–30, https://doi.org/10.26735/FMIT1649 .
Gutub A, Al-Ghamdi M. Image based steganography to facilitate improving counting-based secret sharing, 3D Research. 2019;10(6). https://doi.org/10.1007/s13319-019-0216-0 .
Gutub A, Al-Juaid N. Multi-bits stego-system for hiding text in multimedia images based on user security priority. J Comp Hardware Eng. 2018;1(2):1–9. https://doi.org/10.63019/jche.v1i2.513 .
Al-Juaid N, Gutub A. Combining RSA and audio steganography on personal computers for enhancing security. SN Appl Sci. 2019;1:830. https://doi.org/10.1007/s42452-019-0875-8 .
Atty BAE, Iliyasu AM, Alaskar H, Latif AAAE. A Robust Quasi quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms. Sensors. 2020;20:3108. https://doi.org/10.3390/s20113108 .
Parah SA, Sheikh JA, Assad UI, Bhat GM. Realisation and robustness evaluation of a blind spatial domain watermarking technique. Int J Electron. 2017;104(4):659–72.
Pattanaik B, Chitra P, Lakhmi HR, Selvi T, Nagraj V. Contrasting the performance of discrete transformations on digital image steganography using artificial intelligence. Materials Today: Proceedings. 2021. https://doi.org/10.1016/j.matpr.2020.12.076 .
AbdelRaouf A. A new hiding approach for image steganography based on visual color sensitivity. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-020-10224-w .
Hussain M, Riaz Q, Saleem S, Ghafoor A, Jung KH. Enhanced adaptive data hiding method using LSB and pixel value differencing. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-021-10652-2 .
Sahu AK, Swain G. Reversible image steganography using dual-layer LSB matching. Sens Imaging. 2020;21:1. https://doi.org/10.1007/s11220-019-0262-y .
Hussain M, Wahab AWA, Ho ATS, Javed N, Jung KH. A data hiding scheme using parity-bit pixel value differencing and improved rightmost digit replacement. Signal Process Image Commun. 2017. https://doi.org/10.1016/j.image.2016.10.005 .
Malik A, Sikka G, Verma HK. An AMBTC compression based data hiding scheme using pixel value adjusting strategy. Multidim Syst Sign Process. 2018;29(4):1801–18.
Kumar R, Kim DS, Jung KH. Enhanced AMBTC based data hiding method using hamming distance and pixel value differencing. J Inf Secur Appl. 2019;47:94–103.
Chakraborty S, Jalal AS. A novel local binary pattern based feature image steganography. Multimed Tools Appl. 2020;79:19561–74.
Lin J, Qian Z, Wang Z, Zhang X, Feng G. A new steganography method for dynamic GIF images based on palette sort. Wirel Commun Mobile Comput. 2020;2020:8812087.
Parah SA, Sheikh JA, Akhoon JA, Loan NA. Electronic Health Record Hiding in Images for Smart City Applications: A Computationally Efficient and Reversible Information Hiding Technique for Secure Communication. Future Generation Comp Sys. 2018. https://doi.org/10.1016/j.future.2018.02.023 .
Li X, Luo Y, Bian W. Retracing extended sudoku matrix for high-capacity image steganography. Multimed Tools Appl. 2021 https://doi.org/10.1007/s11042-021-10675-9 .
Saha S, Chakraborty A, Chatterjee A, Dhargupta S, Ghosal SK, Sarkar R. Extended exploiting modification direction based steganography using hashed-weightage array. Multimed Tools Appl. 2020;79:20973–93.
Shen SY, Huang LH, Yu SS. A novel adaptive data hiding based on improved EMD and interpolation. Multimed Tools Appl. 2018;77:131–41.
Bairagi AK, Khondoker R, Islam R. An efficient steganographic approach for protecting communication in the Internet of Things (IoT) critical infrastructures. Information Security J: A Global Perspective Taylor & Francis. 25 2016;4(6):197–212. https://doi.org/10.1080/19393555.2016.1206640 .
Rim Z, Afef A, Ridha E, Mourad Z. Beta chaotic map based image steganography. Springer Nature. 2020. https://doi.org/10.1007/978-3-030-20005-3_10 .
Hassan FS, Gutub A. Efficient image reversible data hiding technique based on interpolation optimization. Arab J Sci Eng. 2021. https://doi.org/10.1007/s13369-021-05529-3 .
Atta R, Ghanbari M. 2021 A high payload data hiding scheme based on dual tree complex wavelet transform. Optik. 2021;226. https://doi.org/10.1016/j.ijleo.2020.165786 .
Dhargupta S, Chakraborty A, Ghosal SK, Saha S, Sarkar R. Fuzzy edge detection based steganography using modified Gaussian distribution. Multimed Tools Appl. 2019. https://doi.org/10.1007/s11042-018-7123-x .
Ahmadian AM, Amirmazlaghani M. A novel secret image sharing with steganography scheme utilizing Optimal Asymmetric Encryption Padding and Information Dispersal Algorithms. Signal Process Image Commun. 2019. https://doi.org/10.1016/j.image.2019.01.006 .
Kich I, Ameur EB, Taouil. Image Steganography Based on Edge Detection Algorithm, IEEE transection. 2018.
He X, Zhang W, Zhang H, Ma L, Li Y. Reversible data hiding for high dynamic range images using edge information. Multimed Tools Appl. 2018. https://doi.org/10.1007/s11042-018-6589-x .
Garav K, Ghanekar U. Image steganography algorithm based on edge region detection and hybrid coding. Comput Model Technol. 2018;22(1):40–56.
Prasad S, Pal AK. Stego-key-based image steganography scheme using edge detector and modulus function. Int J Computational Vision and Robotics. 2020;10(3):223–40.
Mukherjee S, Sanyal G. Edge based image steganography with variable threshold. Multimed Tools Appl. 2019;78:16363–88. https://doi.org/10.1007/s11042-018-6975-4 .
Kadhim IJ, Premaratne P, Vial PJ. Adaptive Image Steganography Based on Edge Detection Over Dual-Tree Complex Wavelet Transform Springer Nature International Publishing. 2018;544–550. https://doi.org/10.1007/978-3-319-95957-3_57 .
Ghosal SK, Mandal JK, Sarkar R. High payload image steganography based on Laplacian of Gaussian (LoG) edge detector. Multimed Tools Appl. 2018;77:30403–18.
Ghosal SK, Chatterjee A, Sarkar R. Image steganography based on Kirsch edge detection. Multimed Syst. 2021;27:73–87.
Banik BG, Poddar MK, Bandyopadhyay SK. Image steganography using edge detection by Kirsch operator and flexible replacement technique. Emerg Technol Data Mining Inf Sec Adv Intel Syst Comput. 2019;814:175–87. https://doi.org/10.1007/978-981-13-1501-5_15 .
Wang Y, Tang M, Wang Z. High-capacity adaptive steganography based on LSB and hamming code. Optik. 2020;213. https://doi.org/10.1016/j.ijleo.2020.164685 https://doi.org/10.1016/j.ijleo.2020.164685 .
Tripathy SK, Srivastava R. An Edge-Based Image Steganography Method Using Modulus-3. Strategy and Comparative Analysis Springer Nature. 2020;485–494. https://doi.org/10.1007/978-981-15-4018-9_43 .
Tuncer T, Sonmez Y. A Novel Data Hiding Method based on Edge Detection and 2k Correction with High Payload and High Visual Quality. Balkan J Electrical & Comp Eng. 2019;7(3):311–318. https://doi.org/10.17694/bajece.573514 .
Abdel-Aziz MM, Hosny KM, Lashin NA. Improved data hiding method for security color images. Multimed Tools Appl. 2021;50:12641–70. https://doi.org/10.1007/s11042-020-10217-9 .
Yao H, Fanyu M, Chuan Q, Tang Z. Dual-JPEG-image reversible data hiding. Inf Sci. 2021;563:130–49. https://doi.org/10.1016/j.ins.2021.02.015 .
Article MathSciNet Google Scholar
Liu Y, Chang CC. Reversible data hiding for JPEG images employing all quantized non-zero AC coefficients. Displays. 2018;51:51–6. https://doi.org/10.1016/j.displa.2018.01.004 .
Attaby AA, Ahmed MFMM, Alsammak AK. Data hiding inside JPEG images with high resistance to Steganalysis using a novel technique: DCT-M3. Ain Shams Engineering Journal. 2018;9:1966–74. https://doi.org/10.1016/j.asej.2017.02.003 .
El-Rahman SA. A comparative analysis of image steganography based on DCT algorithm and steganography tool to hide nuclear reactors confidential information. Comput Electr Eng. 2016;1–20. https://doi.org/10.1016/j.compeleceng.2016.09.001 .
Mohamed N, Baziyad M, Rabie T, Kamel I. L*a*b color space high capacity steganography utilizing quad-trees. Multimed Tools Appl. 2020;79:25089–113. https://doi.org/10.1007/s11042-020-09129-5 .
Rabie T, Kamel I, Baziyad M. Maximizing embedding capacity and stego quality: curve-fitting in the transform domain. Multimed Tools Appl. 2018;77:8295–326. https://doi.org/10.1007/s11042-017-4727-5 .
Saidi M, Hermassi H, Rhouma R, Belghith S. A new adaptive image steganography scheme based on DCT and chaotic map. Multimed Tools Appl. 2017;76(11):13493–510. https://doi.org/10.1007/s11042-016-3722-6 .
Nipanikar SI, Deepthi VH, Kulkarni N. A sparse representation based image steganography using particle swarm optimization and wavelet transform. Alex Eng J. 2018;57:2343–56. https://doi.org/10.1016/j.aej.2017.09.005 .
Navriyanto A, Sutarno S, Erwin E, Siswanti SD. Image steganography using combine of discrete wavelet transform and singular value decomposition for more robustness and higher peak signal noise ratio. IEEE Transection. 2018;147–152.
Miri A, Faez K. An image steganography method based on integer wavelet transform. Multimed Tools Appl. 2018;77:13133–44. https://doi.org/10.1007/s11042-017-4935-z .
Kalita M, Tuithung T, Majumdar S. A new steganography method using integer wavelet transform and least significant bit substitution. Comput J. 2019. https://doi.org/10.1093/comjnl/bxz014 .
Ghosal SK, Mukhopadhyay S, Hossain S, Sarkar R. Exploiting Laguerre transform in image steganography. Comput Electr Eng. 2021;89. https://doi.org/10.1016/j.compeleceng.2020.106964 .
Ma B, Li B, Wang XY, Wang CP, Li J, Shi YQ. A code division multiplexing an block classification-based real-time reversible data-hiding algorithm for medical images. J Real-Time Image Proc. 2019. https://doi.org/10.1007/s11554-019-00884-9 .
Murugan GVK, Subramaniyam RU. Performance analysis of image steganography using wavelet transform for safe and secured transaction. Multimed Tools Appl. 2020;79:9101–15. https://doi.org/10.1007/s11042-019-7507-6 .
Maji G, Mandal S, Sen S. Cover independent image steganography in spatial domain using higher order pixel bits. Multimed Tools Appl. 2021;80:15977–6006. https://doi.org/10.1007/s11042-020-10298-6 .
Sharif A, Mollaeefar M, Nzari M. A novel method for digital image steganography based on a new three-dimensional chaotic map. Multimed Tools Appl. 2017;76:7849–67. https://doi.org/10.1007/s11042-016-3398-y .
Gambhir G, Mandal JK. Multicore implementation and performance analysis of a chaos based LSB steganography technique. Microsyst Technol. 2020. https://doi.org/10.1007/s00542-020-04762-4 .
Prasad S, Pal AK. Logistic map-based image steganography scheme using combined LSB and PVD for security Enhancement. Springer Nature Adv Intel Comput. 2019. https://doi.org/10.1007/978-981-13-1501-5_17 .
Mohammad K, Ahamd j, Rho S, Baik SW. Image steganography for authenticity of visual contents in social networks. Multimed Tools Appl. 2017. https://doi.org/10.1007/s11042-017-4420-8 .
Alotaibi M, Al-Hendi D, Alroithy B, Alghamdi M, Gutub A. Secure mobile computing authentication utilizing hash, cryptography and steganography combination. J Inf Sec Cybercrimes Res (JISCR). 2019;2(1):9–20.
Mathivanan P, Balaji GA. QR code base color image stego-crypto technique using dynamic bit replacement and logistic map. Optik. 2021;225: 165838. https://doi.org/10.1016/j.ijleo.2020.165838 .
Abdelwahab OF, Hussein AI, Hamed HFA, Kelash HM, Khalaf AAM. Efficient combination of RSA cryptography, lossy and lossless compression steganography techniques to hide data. Comput Sci. 2021;183:5–12. https://doi.org/10.1016/j.procs.2021.02.002 .
Parah SA, Kaw JA, Bellavista P, Loan NA, Bhat GM, Muhammad K, Victor A. Efficient security and authentication for edge-based Internet of Medical Things. IEEE Internet Things J. 2021. https://doi.org/10.1109/JIOT.2020.3038009 .
Parah SA, Sheikh JA, Akhoon JA, Loan NA, Bhat GM. Information Hiding in Edges: A high capacity information hiding technique using hybrid edge detection. Springer Multimedia Tools Appl. 2016;77(1):185–207.
Delmi A, Suryadi S, Satria Y. Digital image steganography by using edge adaptive based chaos cryptography. J Phys. 2017;1442. https://doi.org/10.1088/1742-6596/1442/1/012041 .
Sharma H, Mishra DC, Sharma RK, Kumar N. Multi-image steganography and authentication using crypto-stego techniques. Multimed Tools Appl. 2021;80:29067–93. https://doi.org/10.1007/s11042-021-11068-8 .
Kaushik N, Sheokand K. A steganography technique based on chaotic LSB and DWT. International J Innov Res Comp Comm Eng. 2016;4(6):10420–10426. https://doi.org/10.15680/IJIRCCE.2016.0405028 .
Panday HM. Secure medical data transmission using a fusion of bit mask oriented genetic algorithm, encryption and steganography. Futur Gener Comput Syst. 2020;111:213–25. https://doi.org/10.1016/j.future.2020.04.034 .
Elhoseny M, Gonzalez GR, Elnasr OMA, Shawkat SA, Arunkumar A, Farouk A. Secure Medical Data Transmission Model for IoT-Based Healthcare Systems. IEEE Transection, Special Section on Information Security Solutions for Telemedicine Applications. 2018;6(2018):20596–608. https://doi.org/10.1109/ACCESS.2018.2817615 .
Duan X, Guo D, Liu N, Li B, Gou M, Qin C. A new high capacity image steganography method combined with image elliptic curve cryptography and deep neural network. IEEE Transection. 2020;8. https://doi.org/10.1109/ACCESS.2020.2971528 .
Subhedar MS, Mankar VH. Curvelet transform and cover selection for secure steganography. Multimed Tools Appl. 2018;77:8115–38. https://doi.org/10.1007/s11042-017-4706-x .
Eyssa AA, Abdelsamie FE, Abdelnaiem AE. An efficient image steganography approach over wireless communication system. Wireless Pers Commun. 2020;110:321–37. https://doi.org/10.1007/s11277-019-06730-2 .
Kaur R, Singh B. A hybrid algorithm for image steganography. Multidimens Syst Signal Process. 2021;32:1–23. https://doi.org/10.1007/s11045-020-00725-0 .
Hureib ESB, Gutub AA. Enhancing medical data security via combining elliptic curve cryptography and image steganography. International J Comp Sci Network Security (IJCSNS). 2020;20(8):1–8. https://doi.org/10.22937/IJCSNS.2020.20.08.1 .
Hureib ESB, Gutub AA. Enhancing medical data security via combining elliptic curve cryptography with 1-LSB and 2-LSB image steganography. International J Comp Sci Network Security (IJCSNS). 2020;20(12):232–241. https://doi.org/10.22937/IJCSNS.2020.20.12.26 .
Samkari H, Gutub A. Protecting medical records against cybercrimes within hajj period by 3-layer security. Recent Trends Inf Technol Appl. 2019;2(3):1–21. https://doi.org/10.5281/zenodo.3543455 .
Denis R, Madhubala P. Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare system. Multimed Tools Appl. 2021;80:21165–202. https://doi.org/10.1007/s11042-021-10723-4 .
Manikandan T, Muruganandham A, Babuji R, Nandalal V, Iqbal JIM. Secure E-Health using image steganography. J Phys. 2021;1917: 012016. https://doi.org/10.1088/1742-6596/1917/1/012016 .
Ogundokun RO, Awotunde JB, Adeniyi EA, Ayo FE. Crypto-stego based model for securing medical information on IOMT platform. Multimed Tools Appl. 2021. https://doi.org/10.1007/s11042-021-11125-2 .
Prasanalakshmi B, Murugan K, Srinivasan K, Shridevi S, Shamsudheen S, Hu YC. Improved authentication and computation of medical data transmission in the secure IoT using hyperelliptic curve cryptography. J Supercomput. 2021. https://doi.org/10.1007/s11227-021-03861 .
Karakus S, Avci E. A new image steganography method with optimum pixel similarity for data hiding in medical images. Med Hypotheses. 2020;139. https://doi.org/10.1016/j.mehy.2020.109691 .
Sukumar AK, Subramaniyaswamy V, Vijayakumar V, Ravi L. A secure multimedia steganography scheme using hybrid transform and support vector machine for cloud-based storage. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-019-08476-2 .
Gutub A, Al-Shaarani F. Efficient implementation of multi-image secret hiding based on LSB and DWT steganography comparisons. Arab J Sci Eng. 2020. https://doi.org/10.1007/s13369-020-04413-w .
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW. Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst. 2016. https://doi.org/10.1016/j.future.2016.11.029 .
Khan MF, Ahmed A, Saleem K. A novel cryptographic substitution box design using gaussian distribution. IEEE Access. 2019;7:15999–6007.
Sneha PS, Sankar S, Kumar AS. A chaotic colour image encryption scheme combining Walsh-Hadamard transform and Arnold-Tent maps. J Ambient Intell Humaniz Comput. 2020;11:1289–308. https://doi.org/10.1007/s12652-019-01385-0 .
Shah D, Shah T. Anovel discrete image encryption algorithm based o n finite algebraic structures. Multimed Tools Appl. 2020. https://doi.org/10.1007/s11042-020-09182-0 .
Cicek I, Pusane AE, Dundar G. An Integrated Dual Entropy Core True Random Number Generator. IEEE Transaction Circuits-II. 2017;64:329–33.
Njitacke ZT, Isaac SD, Nestor T, Kengne J. Window of Multistability and Control in a Simple 3D Hopfield Neural Network: Application to Biomedical Image Encryption. Springer Neural Comput Appl. 2020. https://doi.org/10.1007/s00521-020-05451-z .
Eze P, Parampalli U, Evans R, Liu D. Evaluation of the effect of steganography on medical image classification accuracy. J Bioinforma Comput Biol. 2020;9(4). https://doi.org/10.1007/s11042-021 .
Eze P, Parampalli U, Evans R, Liu D. A new evaluation method for medical image information hiding techniques. IEEE Transection. 2020;6119–6122. https://doi.org/10.1109/EMBC44109.2020.9176066 .
Download references
This work is not supported by any funding.
Author information
Authors and affiliations.
Department of Electronics and Instrumentation Technology, University of Kashmir, Srinagar, India
Aiman Jan, Shabir A. Parah & Muzamil Hussan
Department of Electronics and Communication Engineering, Institute of Technology, University of Kashmir Zakoora, Srinagar, India
Bilal A. Malik
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Shabir A. Parah .
Ethics declarations
Informed consent, research involving human participants and/or animals., conflicts of interest.
The authors do not have any conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Jan, A., Parah, S.A., Hussan, M. et al. Double layer security using crypto-stego techniques: a comprehensive review. Health Technol. 12 , 9–31 (2022). https://doi.org/10.1007/s12553-021-00602-1
Download citation
Received : 03 August 2021
Accepted : 20 September 2021
Published : 13 October 2021
Issue Date : January 2022
DOI : https://doi.org/10.1007/s12553-021-00602-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Steganography
- Cryptography
- Imperceptivity
- Find a journal
- Publish with us
- Track your research
Welcome to the MIT CISR website!
This site uses cookies. Review our Privacy Statement.

AI Is Everybody’s Business
This briefing presents three principles to guide business leaders when making AI investments: invest in practices that build capabilities required for AI, involve all your people in your AI journey, and focus on realizing value from your AI projects. The principles are supported by the MIT CISR data monetization research, and the briefing illustrates them using examples from the Australia Taxation Office and CarMax. The three principles apply to any kind of AI, defined as technology that performs human-like cognitive tasks; subsequent briefings will present management advice distinct to machine learning and generative tools, respectively.
Access More Research!
Any visitor to the website can read many MIT CISR Research Briefings in the webpage. But site users who have signed up on the site and are logged in can download all available briefings, plus get access to additional content. Even more content is available to members of MIT CISR member organizations .
Author Barb Wixom reads this research briefing as part of our audio edition of the series. Follow the series on SoundCloud.
DOWNLOAD THE TRANSCRIPT
Today, everybody across the organization is hungry to know more about AI. What is it good for? Should I trust it? Will it take my job? Business leaders are investing in massive training programs, partnering with promising vendors and consultants, and collaborating with peers to identify ways to benefit from AI and avoid the risk of AI missteps. They are trying to understand how to manage AI responsibly and at scale.
Our book Data Is Everybody’s Business: The Fundamentals of Data Monetization describes how organizations make money using their data.[foot]Barbara H. Wixom, Cynthia M. Beath, and Leslie Owens, Data Is Everybody's Business: The Fundamentals of Data Monetization , (Cambridge: The MIT Press, 2023), https://mitpress.mit.edu/9780262048217/data-is-everybodys-business/ .[/foot] We wrote the book to clarify what data monetization is (the conversion of data into financial returns) and how to do it (by using data to improve work, wrap products and experiences, and sell informational solutions). AI technology’s role in this is to help data monetization project teams use data in ways that humans cannot, usually because of big complexity or scope or required speed. In our data monetization research, we have regularly seen leaders use AI effectively to realize extraordinary business goals. In this briefing, we explain how such leaders achieve big AI wins and maximize financial returns.
Using AI in Data Monetization
AI refers to the ability of machines to perform human-like cognitive tasks.[foot]See Hind Benbya, Thomas H. Davenport, and Stella Pachidi, “Special Issue Editorial: Artificial Intelligence in Organizations: Current State and Future Opportunities , ” MIS Quarterly Executive 19, no. 4 (December 2020), https://aisel.aisnet.org/misqe/vol19/iss4/4 .[/foot] Since 2019, MIT CISR researchers have been studying deployed data monetization initiatives that rely on machine learning and predictive algorithms, commonly referred to as predictive AI.[foot]This research draws on a Q1 to Q2 2019 asynchronous discussion about AI-related challenges with fifty-three data executives from the MIT CISR Data Research Advisory Board; more than one hundred structured interviews with AI professionals regarding fifty-two AI projects from Q3 2019 to Q2 2020; and ten AI project narratives published by MIT CISR between 2020 and 2023.[/foot] Such initiatives use large data repositories to recognize patterns across time, draw inferences, and predict outcomes and future trends. For example, the Australian Taxation Office (ATO) used machine learning, neural nets, and decision trees to understand citizen tax-filing behaviors and produce respectful nudges that helped citizens abide by Australia’s work-related expense policies. In 2018, the nudging resulted in AUD$113 million in changed claim amounts.[foot]I. A. Someh, B. H. Wixom, and R. W. Gregory, “The Australian Taxation Office: Creating Value with Advanced Analytics,” MIT CISR Working Paper No. 447, November 2020, https://cisr.mit.edu/publication/MIT_CISRwp447_ATOAdvancedAnalytics_SomehWixomGregory .[/foot]
In 2023, we began exploring data monetization initiatives that rely on generative AI.[foot]This research draws on two asynchronous generative AI discussions (Q3 2023, N=35; Q1 2024, N=34) regarding investments and capabilities and roles and skills, respectively, with data executives from the MIT CISR Data Research Advisory Board. It also draws on in-progress case studies with large organizations in the publishing, building materials, and equipment manufacturing industries.[/foot] This type of AI analyzes vast amounts of text or image data to discern patterns in them. Using these patterns, generative AI can create new text, software code, images, or videos, usually in response to user prompts. Organizations are now beginning to openly discuss data monetization initiative deployments that include generative AI technologies. For example, used vehicle retailer CarMax reported using OpenAI’s ChatGPT chatbot to help aggregate customer reviews and other car information from multiple data sets to create helpful, easy-to-read summaries about individual used cars for its online shoppers. At any point in time, CarMax has on average 50,000 cars on its website, so to produce such content without AI the company would require hundreds of content writers and years of time; using ChatGPT, the company’s content team can generate summaries in hours.[foot]Paula Rooney, “CarMax drives business value with GPT-3.5,” CIO , May 5, 2023, https://www.cio.com/article/475487/carmax-drives-business-value-with-gpt-3-5.html ; Hayete Gallot and Shamim Mohammad, “Taking the car-buying experience to the max with AI,” January 2, 2024, in Pivotal with Hayete Gallot, produced by Larj Media, podcast, MP3 audio, https://podcasts.apple.com/us/podcast/taking-the-car-buying-experience-to-the-max-with-ai/id1667013760?i=1000640365455 .[/foot]
Big advancements in machine learning, generative tools, and other AI technologies inspire big investments when leaders believe the technologies can help satisfy pent-up demand for solutions that previously seemed out of reach. However, there is a lot to learn about novel technologies before we can properly manage them. In this year’s MIT CISR research, we are studying predictive and generative AI from several angles. This briefing is the first in a series; in future briefings we will present management advice specific to machine learning and generative tools. For now, we present three principles supported by our data monetization research to guide business leaders when making AI investments of any kind: invest in practices that build capabilities required for AI, involve all your people in your AI journey, and focus on realizing value from your AI projects.
Principle 1: Invest in Practices That Build Capabilities Required for AI
Succeeding with AI depends on having deep data science skills that help teams successfully build and validate effective models. In fact, organizations need deep data science skills even when the models they are using are embedded in tools and partner solutions, including to evaluate their risks; only then can their teams make informed decisions about how to incorporate AI effectively into work practices. We worry that some leaders view buying AI products from providers as an opportunity to use AI without deep data science skills; we do not advise this.
But deep data science skills are not enough. Leaders often hire new talent and offer AI literacy training without making adequate investments in building complementary skills that are just as important. Our research shows that an organization’s progress in AI is dependent on having not only an advanced data science capability, but on having equally advanced capabilities in data management, data platform, acceptable data use, and customer understanding.[foot]In the June 2022 MIT CISR research briefing, we described why and how organizations build the five advanced data monetization capabilities for AI. See B. H. Wixom, I. A. Someh, and C. M. Beath, “Building Advanced Data Monetization Capabilities for the AI-Powered Organization,” MIT CISR Research Briefing, Vol. XXII, No. 6, June 2022, https://cisr.mit.edu/publication/2022_0601_AdvancedAICapabilities_WixomSomehBeath .[/foot] Think about it. Without the ability to curate data (an advanced data management capability), teams cannot effectively incorporate a diverse set of features into their models. Without the ability to oversee the legality and ethics of partners’ data use (an advanced acceptable data use capability), teams cannot responsibly deploy AI solutions into production.
It’s no surprise that ATO’s AI journey evolved in conjunction with the organization’s Smarter Data Program, which ATO established to build world-class data analytics capabilities, and that CarMax emphasizes that its governance, talent, and other data investments have been core to its generative AI progress.
Capabilities come mainly from learning by doing, so they are shaped by new practices in the form of training programs, policies, processes, or tools. As organizations undertake more and more sophisticated practices, their capabilities get more robust. Do invest in AI training—but also invest in practices that will boost the organization’s ability to manage data (such as adopting a data cataloging tool), make data accessible cost effectively (such as adopting cloud policies), improve data governance (such as establishing an ethical oversight committee), and solidify your customer understanding (such as mapping customer journeys). In particular, adopt policies and processes that will improve your data governance, so that data is only used in AI initiatives in ways that are consonant with your organization's values and its regulatory environment.
Principle 2: Involve All Your People in Your AI Journey
Data monetization initiatives require a variety of stakeholders—people doing the work, developing products, and offering solutions—to inform project requirements and to ensure the adoption and confident use of new data tools and behaviors.[foot]Ida Someh, Barbara Wixom, Michael Davern, and Graeme Shanks, “Configuring Relationships between Analytics and Business Domain Groups for Knowledge Integration, ” Journal of the Association for Information Systems 24, no. 2 (2023): 592-618, https://cisr.mit.edu/publication/configuring-relationships-between-analytics-and-business-domain-groups-knowledge .[/foot] With AI, involving a variety of stakeholders in initiatives helps non-data scientists become knowledgeable about what AI can and cannot do, how long it takes to deliver certain kinds of functionality, and what AI solutions cost. This, in turn, helps organizations in building trustworthy models, an important AI capability we call AI explanation (AIX).[foot]Ida Someh, Barbara H. Wixom, Cynthia M. Beath, and Angela Zutavern, “Building an Artificial Intelligence Explanation Capability,” MIS Quarterly Executive 21, no. 2 (2022), https://cisr.mit.edu/publication/building-artificial-intelligence-explanation-capability .[/foot]
For example, at ATO, data scientists educated business colleagues on the mechanics and results of models they created. Business colleagues provided feedback on the logic used in the models and helped to fine-tune them, and this interaction helped everyone understand how the AI made decisions. The data scientists provided their model results to ATO auditors, who also served as a feedback loop to the data scientists for improving the model. The data scientists regularly reported on initiative progress to senior management, regulators, and other stakeholders, which ensured that the AI team was proactively creating positive benefits without neglecting negative external factors that might surface.
Given the consumerization of generative AI tools, we believe that pervasive worker involvement in ideating, building, refining, using, and testing AI models and tools will become even more crucial to deploying fruitful AI projects—and building trust that AI will do the right thing in the right way at the right time.
Principle 3: Focus on Realizing Value From Your AI Projects
AI is costly—just add up your organization’s expenses in tools, talent, and training. AI needs to pay off, yet some organizations become distracted with endless experimentation. Others get caught up in finding the sweet spot of the technology, ignoring the sweet spot of their business model. For example, it is easy to become enamored of using generative AI to improve worker productivity, rolling out tools for employees to write better emails and capture what happened in meetings. But unless those activities materially impact how your organization makes money, there likely are better ways to spend your time and money.
Leaders with data monetization experience will make sure their AI projects realize value in the form of increased revenues or reduced expenses by backing initiatives that are clearly aligned with real challenges and opportunities. That is step one. In our research, the leaders that realize value from their data monetization initiatives measure and track their outcomes, especially their financial outcomes, and they hold someone accountable for achieving the desired financial returns. At CarMax, a cross-functional team owned the mission to provide better website information for used car shoppers, a mission important to the company’s sales goals. Starting with sales goals in mind, the team experimented with and then chose a generative AI solution that would enhance the shopper experience and increase sales.
Figure 1: Three Principles for Getting Value from AI Investments
The three principles are based on the following concepts from MIT CISR data research: 1. Data liquidity: the ease of data asset recombination and reuse 2. Data democracy: an organization that empowers employees in the access and use of data 3. Data monetization: the generation of financial returns from data assets

Managing AI Using a Data Monetization Mindset
AI has and always will play a big role in data monetization. It’s not a matter of whether to incorporate AI, but a matter of how to best use it. To figure this out, quantify the outcomes of some of your organization’s recent AI projects. How much money has the organization realized from them? If the answer disappoints, then make sure the AI technology value proposition is a fit for your organization’s most important goals. Then assign accountability for ensuring that AI technology is applied in use cases that impact your income statements. If the AI technology is not a fit for your organization, then don’t be distracted by media reports of the AI du jour.
Understanding your AI technology investments can be hard if your organization is using AI tools that are bundled in software you purchase or are built for you by a consultant. To set yourself up for success, ask your partners to be transparent with you about the quality of data they used to train their AI models and the data practices they relied on. Do their answers persuade you that their tools are trustworthy? Is it obvious that your partner is using data compliantly and is safeguarding the model from producing bad or undesired outcomes? If so, make sure this good news is shared with the people in your organization and those your organization serves. If not, rethink whether to break with your partner and find another way to incorporate the AI technology into your organization, such as by hiring people to build it in-house.
To paraphrase our book’s conclusion: When people actively engage in data monetization initiatives using AI , they learn, and they help their organization learn. Their engagement creates momentum that initiates a virtuous cycle in which people’s engagement leads to better data and more bottom-line value, which in turn leads to new ideas and more engagement, which further improves data and delivers more value, and so on. Imagine this happening across your organization as all people everywhere make it their business to find ways to use AI to monetize data.
This is why AI, like data, is everybody’s business.
© 2024 MIT Center for Information Systems Research, Wixom and Beath. MIT CISR Research Briefings are published monthly to update the center’s member organizations on current research projects.
Related Publications

Talking Points
Ai, like data, is everybody's business.

Working Paper: Vignette
The australian taxation office: creating value with advanced analytics.

Research Briefing
Building advanced data monetization capabilities for the ai-powered organization.

Building AI Explanation Capability for the AI-Powered Organization
What is Data Monetization?
About the researchers.

Barbara H. Wixom, Principal Research Scientist, MIT Center for Information Systems Research (CISR)

Cynthia M. Beath, Professor Emerita, University of Texas and Academic Research Fellow, MIT CISR
Mit center for information systems research (cisr).
Founded in 1974 and grounded in MIT's tradition of combining academic knowledge and practical purpose, MIT CISR helps executives meet the challenge of leading increasingly digital and data-driven organizations. We work directly with digital leaders, executives, and boards to develop our insights. Our consortium forms a global community that comprises more than seventy-five organizations.
MIT CISR Associate Members
MIT CISR wishes to thank all of our associate members for their support and contributions.
MIT CISR's Mission Expand
MIT CISR helps executives meet the challenge of leading increasingly digital and data-driven organizations. We provide insights on how organizations effectively realize value from approaches such as digital business transformation, data monetization, business ecosystems, and the digital workplace. Founded in 1974 and grounded in MIT’s tradition of combining academic knowledge and practical purpose, we work directly with digital leaders, executives, and boards to develop our insights. Our consortium forms a global community that comprises more than seventy-five organizations.
Quantum Cryptography: A New Generation of Information Technology Security System
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
New treatment could reverse hair loss caused by an autoimmune skin disease
Press contact :, media download.

*Terms of Use:
Images for download on the MIT News office website are made available to non-commercial entities, press and the general public under a Creative Commons Attribution Non-Commercial No Derivatives license . You may not alter the images provided, other than to crop them to size. A credit line must be used when reproducing images; if one is not provided below, credit the images to "MIT."
Previous image Next image
Researchers at MIT, Brigham and Women’s Hospital, and Harvard Medical School have developed a potential new treatment for alopecia areata, an autoimmune disorder that causes hair loss and affects people of all ages, including children.
For most patients with this type of hair loss, there is no effective treatment. The team developed a microneedle patch that can be painlessly applied to the scalp and releases drugs that help to rebalance the immune response at the site, halting the autoimmune attack.
In a study of mice, the researchers found that this treatment allowed hair to regrow and dramatically reduced inflammation at the treatment site, while avoiding systemic immune effects elsewhere in the body. This strategy could also be adapted to treat other autoimmune skin diseases such as vitiligo, atopic dermatitis, and psoriasis, the researchers say.
“This innovative approach marks a paradigm shift. Rather than suppressing the immune system, we’re now focusing on regulating it precisely at the site of antigen encounter to generate immune tolerance,” says Natalie Artzi, a principal research scientist in MIT’s Institute for Medical Engineering and Science, an associate professor of medicine at Harvard Medical School and Brigham and Women’s Hospital, and an associate faculty member at the Wyss Institute of Harvard University.
Artzi and Jamil R. Azzi, an associate professor of medicine at Harvard Medical School and Brigham and Women’s Hospital, are the senior authors of the new study , which appears in the journal Advanced Materials . Nour Younis, a Brigham and Women’s postdoc, and Nuria Puigmal, a Brigham and Women’s postdoc and former MIT research affiliate, are the lead authors of the paper.
The researchers are now working on launching a company to further develop the technology, led by Puigmal, who was recently awarded a Harvard Business School Blavatnik Fellowship.
Direct delivery
Alopecia areata, which affects more than 6 million Americans, occurs when the body’s own T cells attack hair follicles, leading the hair to fall out. The only treatment available to most patients — injections of immunosuppressant steroids into the scalp — is painful and patients often can’t tolerate it.
Some patients with alopecia areata and other autoimmune skin diseases can also be treated with immunosuppressant drugs that are given orally, but these drugs lead to widespread suppression of the immune system, which can have adverse side effects.
“This approach silences the entire immune system, offering relief from inflammation symptoms but leading to frequent recurrences. Moreover, it increases susceptibility to infections, cardiovascular diseases, and cancer,” Artzi says.
A few years ago, at a working group meeting in Washington, Artzi happened to be seated next to Azzi (the seating was alphabetical), an immunologist and transplant physican who was seeking new ways to deliver drugs directly to the skin to treat skin-related diseases.
Their conversation led to a new collaboration, and the two labs joined forces to work on a microneedle patch to deliver drugs to the skin. In 2021, they reported that such a patch can be used to prevent rejection following skin transplant. In the new study, they began applying this approach to autoimmune skin disorders.
“The skin is the only organ in our body that we can see and touch, and yet when it comes to drug delivery to the skin, we revert to systemic administration. We saw great potential in utilizing the microneedle patch to reprogram the immune system locally,” Azzi says.
The microneedle patches used in this study are made from hyaluronic acid crosslinked with polyethylene glycol (PEG), both of which are biocompatible and commonly used in medical applications. With this delivery method, drugs can pass through the tough outer layer of the epidermis, which can’t be penetrated by creams applied to the skin.
“This polymer formulation allows us to create highly durable needles capable of effectively penetrating the skin. Additionally, it gives us the flexibility to incorporate any desired drug,” Artzi says. For this study, the researchers loaded the patches with a combination of the cytokines IL-2 and CCL-22. Together, these immune molecules help to recruit regulatory T cells, which proliferate and help to tamp down inflammation. These cells also help the immune system learn to recognize that hair follicles are not foreign antigens, so that it will stop attacking them.
Hair regrowth
The researchers found that mice treated with this patch every other day for three weeks had many more regulatory T cells present at the site, along with a reduction in inflammation. Hair was able to regrow at those sites, and this growth was maintained for several weeks after the treatment ended. In these mice, there were no changes in the levels of regulatory T cells in the spleen or lymph nodes, suggesting that the treatment affected only the site where the patch was applied.
In another set of experiments, the researchers grafted human skin onto mice with a humanized immune system. In these mice, the microneedle treatment also induced proliferation of regulatory T cells and a reduction in inflammation.
The researchers designed the microneedle patches so that after releasing their drug payload, they can also collect samples that could be used to monitor the progress of the treatment. Hyaluronic acid causes the needles to swell about tenfold after entering the skin, which allows them to absorb interstitial fluid containing biomolecules and immune cells from the skin.
Following patch removal, researchers can analyze samples to measure levels of regulatory T cells and inflammation markers. This could prove valuable for monitoring future patients who may undergo this treatment.
The researchers now plan to further develop this approach for treating alopecia, and to expand into other autoimmune skin diseases.
The research was funded by the Ignite Fund and Shark Tank Fund awards from the Department of Medicine at Brigham and Women’s Hospital.
Share this news article on:
Press mentions, healthday news.
MIT researchers have developed microneedle patches that are capable of restoring hair growth in alopecia areata patients, reports Ernie Mundell for HealthDay . The team’s approach includes a, “patch containing myriad microneedles that is applied to the scalp,” writes Mundell. “It releases drugs to reset the immune system so it stops attacking follicles.”
Previous item Next item
Related Links
- Natalie Artzi
- Institute for Medical Engineering and Science
Related Topics
- Drug delivery
- Health sciences and technology
- Institute for Medical Engineering and Science (IMES)
Related Articles

A sprayable gel could make minimally invasive surgeries simpler and safer

Patch that delivers drug, gene, and light-based therapy to tumor sites shows promising results

MIT researchers design tailored tissue adhesives
More mit news.
Janabel Xia: Algorithms, dance rhythms, and the drive to succeed
Read full story →

Jonathan Byrnes, MIT Center for Transportation and Logistics senior lecturer and visionary in supply chain management, dies at 75
Researchers develop a detector for continuously monitoring toxic gases

The beauty of biology

Navigating longevity with industry leaders at MIT AgeLab PLAN Forum

Jeong Min Park earns 2024 Schmidt Science Fellowship
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
Advertisement
Supported by
Senators Propose $32 Billion in Annual A.I. Spending but Defer Regulation
Their plan is the culmination of a yearlong listening tour on the dangers of the new technology.
- Share full article

By Cecilia Kang and David McCabe
Cecilia Kang and David McCabe cover technology policy.
A bipartisan group of senators released a long-awaited legislative plan for artificial intelligence on Wednesday, calling for billions in funding to propel American leadership in the technology while offering few details on regulations to address its risks.
In a 20-page document titled “Driving U.S. Innovation in Artificial Intelligence,” the Senate leader, Chuck Schumer, and three colleagues called for spending $32 billion annually by 2026 for government and private-sector research and development of the technology.
The lawmakers recommended creating a federal data privacy law and said they supported legislation, planned for introduction on Wednesday, that would prevent the use of realistic misleading technology known as deepfakes in election campaigns. But they said congressional committees and agencies should come up with regulations on A.I., including protections against health and financial discrimination, the elimination of jobs, and copyright violations caused by the technology.
“It’s very hard to do regulations because A.I. is changing too quickly,” Mr. Schumer, a New York Democrat, said in an interview. “We didn’t want to rush this.”
He designed the road map with two Republican senators, Mike Rounds of South Dakota and Todd Young of Indiana, and a fellow Democrat, Senator Martin Heinrich of New Mexico, after their yearlong listening tour to hear concerns about new generative A.I. technologies. Those tools, like OpenAI’s ChatGPT, can generate realistic and convincing images, videos, audio and text. Tech leaders have warned about the potential harms of A.I., including the obliteration of entire job categories, election interference, discrimination in housing and finance, and even the replacement of humankind.
The senators’ decision to delay A.I. regulation widens a gap between the United States and the European Union , which this year adopted a law that prohibits A.I.’s riskiest uses, including some facial recognition applications and tools that can manipulate behavior or discriminate. The European law requires transparency around how systems operate and what data they collect. Dozens of U.S. states have also proposed privacy and A.I. laws that would prohibit certain uses of the technology.
Outside of recent legislation mandating the sale or ban of the social media app TikTok, Congress hasn’t passed major tech legislation in years, despite multiple proposals.
“It’s disappointing because at this point we’ve missed several windows of opportunity to act while the rest of the world has,” said Amba Kak, a co-executive director of the nonprofit AI Now Institute and a former adviser on A.I. to the Federal Trade Commission.
Mr. Schumer’s efforts on A.I. legislation began in June with a series of high-profile forums that brought together tech leaders including Elon Musk of Tesla, Sundar Pichai of Google and Sam Altman of OpenAI.
(The New York Times has sued OpenAI and its partner, Microsoft, over use of the publication’s copyrighted works in A.I. development.)
Mr. Schumer said in the interview that through the forums, lawmakers had begun to understand the complexity of A.I. technologies and how expert agencies and congressional committees were best equipped to create regulations.
The legislative road map encourages greater federal investment in the growth of domestic research and development.
“This is sort of the American way — we are more entrepreneurial,” Mr. Schumer said in the interview, adding that the lawmakers hoped to make “innovation the North Star.”
In a separate briefing with reporters, he said the Senate was more likely to consider A.I. proposals piecemeal instead of in one large legislative package.
“What we’d expect is that we would have some bills that certainly pass the Senate and hopefully pass the House by the end of the year,” Mr. Schumer said. “It won’t cover the whole waterfront. There’s too much waterfront to cover, and things are changing so rapidly.”
He added that his staff had spoken with Speaker Mike Johnson’s office
Maya Wiley, president of the Leadership Conference on Civil and Human Rights, participated in the first forum. She said that the closed-door meetings were “tech industry heavy” and that the report’s focus on promoting innovation overshadowed the real-world harms that could result from A.I. systems, noting that health and financial tools had already shown signs of discrimination against certain ethnic and racial groups.
Ms. Wiley has called for greater focus on the vetting of new products to make sure they are safe and operate without biases that can target certain communities.
“We should not assume that we don’t need additional rights,” she said.
Cecilia Kang reports on technology and regulatory policy and is based in Washington D.C. She has written about technology for over two decades. More about Cecilia Kang
David McCabe covers tech policy. He joined The Times from Axios in 2019. More about David McCabe
Explore Our Coverage of Artificial Intelligence
News and Analysis
Ilya Sutskever, the OpenAI co-founder and chief scientist who in November joined three other board members to force out Sam Altman before saying he regretted the move, is leaving the company .
OpenAI has unveiled a new version of its ChatGPT chatbot that can receive and respond to voice commands, images and videos.
A bipartisan group of senators released a long-awaited legislative plan for A.I. , calling for billions in funding to propel U.S. leadership in the technology while offering few details on regulations.
The Age of A.I.
D’Youville University in Buffalo had an A.I. robot speak at its commencement . Not everyone was happy about it.
A new program, backed by Cornell Tech, M.I.T. and U.C.L.A., helps prepare lower-income, Latina and Black female computing majors for A.I. careers.
Publishers have long worried that A.I.-generated answers on Google would drive readers away from their sites. They’re about to find out if those fears are warranted, our tech columnist writes .
A new category of apps promises to relieve parents of drudgery, with an assist from A.I. But a family’s grunt work is more human, and valuable, than it seems.
MIT Technology Review
- Newsletters
Google DeepMind’s new AlphaFold can model a much larger slice of biological life
AlphaFold 3 can predict how DNA, RNA, and other molecules interact, further cementing its leading role in drug discovery and research. Who will benefit?
- James O'Donnell archive page
Google DeepMind has released an improved version of its biology prediction tool, AlphaFold, that can predict the structures not only of proteins but of nearly all the elements of biological life.
It’s a development that could help accelerate drug discovery and other scientific research. The tool is currently being used to experiment with identifying everything from resilient crops to new vaccines.
While the previous model, released in 2020, amazed the research community with its ability to predict proteins structures, researchers have been clamoring for the tool to handle more than just proteins.
Now, DeepMind says, AlphaFold 3 can predict the structures of DNA, RNA, and molecules like ligands, which are essential to drug discovery. DeepMind says the tool provides a more nuanced and dynamic portrait of molecule interactions than anything previously available.
“Biology is a dynamic system,” DeepMind CEO Demis Hassabis told reporters on a call. “Properties of biology emerge through the interactions between different molecules in the cell, and you can think about AlphaFold 3 as our first big sort of step toward [modeling] that.”
AlphaFold 2 helped us better map the human heart , model antimicrobial resistance , and identify the eggs of extinct birds , but we don’t yet know what advances AlphaFold 3 will bring.
Mohammed AlQuraishi, an assistant professor of systems biology at Columbia University who is unaffiliated with DeepMind, thinks the new version of the model will be even better for drug discovery. “The AlphaFold 2 system only knew about amino acids, so it was of very limited utility for biopharma,” he says. “But now, the system can in principle predict where a drug binds a protein.”
Isomorphic Labs, a drug discovery spinoff of DeepMind, is already using the model for exactly that purpose, collaborating with pharmaceutical companies to try to develop new treatments for diseases, according to DeepMind.
AlQuraishi says the release marks a big leap forward. But there are caveats.
“It makes the system much more general, and in particular for drug discovery purposes (in early-stage research), it’s far more useful now than AlphaFold 2,” he says. But as with most models, the impact of AlphaFold will depend on how accurate its predictions are. For some uses, AlphaFold 3 has double the success rate of similar leading models like RoseTTAFold. But for others, like protein-RNA interactions, AlQuraishi says it’s still very inaccurate.
DeepMind says that depending on the interaction being modeled, accuracy can range from 40% to over 80%, and the model will let researchers know how confident it is in its prediction. With less accurate predictions, researchers have to use AlphaFold merely as a starting point before pursuing other methods. Regardless of these ranges in accuracy, if researchers are trying to take the first steps toward answering a question like which enzymes have the potential to break down the plastic in water bottles, it’s vastly more efficient to use a tool like AlphaFold than experimental techniques such as x-ray crystallography.
A revamped model
AlphaFold 3’s larger library of molecules and higher level of complexity required improvements to the underlying model architecture. So DeepMind turned to diffusion techniques, which AI researchers have been steadily improving in recent years and now power image and video generators like OpenAI’s DALL-E 2 and Sora. It works by training a model to start with a noisy image and then reduce that noise bit by bit until an accurate prediction emerges. That method allows AlphaFold 3 to handle a much larger set of inputs.
That marked “a big evolution from the previous model,” says John Jumper, director at Google DeepMind. “It really simplified the whole process of getting all these different atoms to work together.”
It also presented new risks. As the AlphaFold 3 paper details, the use of diffusion techniques made it possible for the model to hallucinate, or generate structures that look plausible but in reality could not exist. Researchers reduced that risk by adding more training data to the areas most prone to hallucination, though that doesn’t eliminate the problem completely.
Restricted access
Part of AlphaFold 3’s impact will depend on how DeepMind divvies up access to the model. For AlphaFold 2, the company released the open-source code , allowing researchers to look under the hood to gain a better understanding of how it worked. It was also available for all purposes, including commercial use by drugmakers. For AlphaFold 3, Hassabis said, there are no current plans to release the full code. The company is instead releasing a public interface for the model called the AlphaFold Server , which imposes limitations on which molecules can be experimented with and can only be used for noncommercial purposes. DeepMind says the interface will lower the technical barrier and broaden the use of the tool to biologists who are less knowledgeable about this technology.
Artificial intelligence
Sam altman says helpful agents are poised to become ai’s killer function.
Open AI’s CEO says we won’t need new hardware or lots more training data to get there.
Is robotics about to have its own ChatGPT moment?
Researchers are using generative AI and other techniques to teach robots new skills—including tasks they could perform in homes.
- Melissa Heikkilä archive page
What’s next for generative video
OpenAI's Sora has raised the bar for AI moviemaking. Here are four things to bear in mind as we wrap our heads around what's coming.
- Will Douglas Heaven archive page
An AI startup made a hyperrealistic deepfake of me that’s so good it’s scary
Synthesia's new technology is impressive but raises big questions about a world where we increasingly can’t tell what’s real.
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.
Microsoft Research Blog
Research focus: week of may 13, 2024.
Published May 15, 2024
Share this page
- Share on Facebook
- Share on Twitter
- Share on LinkedIn
- Share on Reddit
- Subscribe to our RSS feed
Welcome to Research Focus, a series of blog posts that highlights notable publications, events, code/datasets, new hires and other milestones from across the research community at Microsoft.

NEW RESEARCH
Injecting new knowledge into large language models via supervised fine-tuning .
Large language models (LLMs) have shown remarkable performance in generating text similar to that created by people, proving to be a valuable asset across various applications. However, adapting these models to incorporate new, out-of-domain knowledge remains a challenge, particularly for facts and events that occur after the model’s training knowledge cutoff date.
In a recent paper: Injecting New Knowledge into Large Language Models via Supervised Fine-Tuning , researchers from Microsoft investigate the effectiveness of supervised fine-tuning (SFT) as a method for knowledge injection in LLMs, specifically focusing on recent sporting events. They compare different dataset generation strategies—token-based and fact-based scaling—to create training data that helps the model learn new information. Their experiments on GPT-4 demonstrate that while token-based scaling can lead to improvements in Q&A accuracy, it may not provide uniform coverage of new knowledge. Fact-based scaling, on the other hand, offers a more systematic approach to ensure even coverage across all facts. The researchers present a novel dataset generation process that leads to more effective knowledge ingestion through SFT, and results show considerable performance improvements in Q&A tasks related to out-of-domain knowledge.
A Reflection on Human-Notebook Experiences in the Era of AI
Computational notebooks provide an interactive way to work with data. They have been widely used by data professionals to write code, explore data, and generate visualizations, all in one document. Previous research has revealed unique pain points around the user experience in computational notebooks. However, as AI tools like ChatGPT or Copilot have emerged, it is unclear whether these pain points have been reduced or changed, or whether new pain points have arisen. Due to the fast pace of advances in AI technology, most of the development of new AI tools has been primarily driven by technology and not by user experience.
In a recent paper: A Reflection on Human-Notebook Experiences in the Era of AI , researchers from Microsoft summarize literature on how new AI technology has impacted human-notebook interaction and human-computer interaction (HCI) paradigms, new challenges and user behavior around using AI assistants, and recent research on AI assistants in computational notebook scenarios. They outline gaps in existing literature and suggest a future focus on improving macro human-notebook experiences throughout a user’s workflow, measuring and quantifying the value of AI systems, and establishing a set of standards and best practices for AI tools.
Spotlight: Event Series

Microsoft Research Forum
Join us for a continuous exchange of ideas about research in the era of general AI. Watch Episodes 1 & 2 on-demand.
Jacdac: Service-Based Prototyping of Embedded Systems
The traditional approach to programming embedded systems is monolithic: firmware on a microcontroller contains both application code and the drivers needed to communicate with sensors and actuators, using low-level protocols such as I2C, SPI, and RS232. In comparison, software development for the cloud has moved to a service-based development and operation paradigm: a service provides a discrete unit of functionality that can be accessed remotely by an application, or other service, but is independently managed and updated.
In a recent paper: Jacdac: Service-Based Prototyping of Embedded Systems (opens in new tab) , researchers from Microsoft propose, design, implement, and evaluate a service-based approach to prototyping embedded systems called Jacdac (opens in new tab) . Jacdac defines a service specification language, designed especially for embedded systems, along with a host of specifications for a variety of sensors and actuators. With Jacdac, each sensor/actuator in a system is paired with a low-cost microcontroller that advertises the services that represent the functionality of the underlying hardware over an efficient and low-cost single-wire bus protocol. A separate microcontroller executes the user’s application program, which is a client of the Jacdac services on the bus.
Three Jacdac kits, comprising over twenty modules, have been produced by third-party manufacturers: KittenBot (opens in new tab) and Forward Education (opens in new tab) .
PARIKSHA: A Scalable, Democratic, Transparent Evaluation Platform for Assessing Indic Large Language Models
Evaluation of multilingual LLMs is challenging due to a variety of factors – the lack of benchmarks with sufficient linguistic diversity, contamination of popular benchmarks into LLM pre-training data, and the lack of local, cultural nuances in translated benchmarks. Hence, it is difficult to extensively evaluate LLMs in a multilingual setting, leading to lack of fair comparisons between models and difficulties in replicating the evaluation setup used by some models. Recently, several Indic (Indian language) LLMs have been created to help build more locally and culturally relevant LLMs.
In a recent paper: PARIKSHA: A Scalable, Democratic, Transparent Evaluation Platform for Assessing Indic Large Language Models , researchers from Microsoft present an evaluation framework, which is the first comprehensive evaluation of Indic LLMs using a combination of human and LLM-based evaluation. The researchers conduct a total of 90,000 human evaluations and 50,000 LLM-based evaluations of 29 models to present leaderboards for 10 Indic languages. Pariksha provides inclusive evaluation by engaging a community of workers that represent India’s large and diverse workforce and also serves as a research platform for improving the process of evaluation. For transparency on the process, the evaluation artifacts will be released. Conducting Pariksha at regular intervals, the researchers aim to enable models to improve over time with insights and artifacts from their evaluations.
Tinker, Tailor, Configure, Customize: The Articulation Work of Customizing AI Fairness Checklists
Many responsible AI resources, such as toolkits, playbooks, and checklists, have been developed to support AI practitioners in identifying, measuring, and mitigating potential fairness-related harms. These resources are often designed to be general purpose, in order to address a variety of use cases, domains, and deployment contexts. However, this can lead to decontextualization, where such resources lack the level of relevance or specificity needed to use them.
To understand how AI practitioners might contextualize one such resource, an AI fairness checklist, for their particular use cases, domains, and deployment contexts, researchers from Microsoft conducted a retrospective contextual inquiry with 13 AI practitioners from seven organizations. In a recent paper: Tinker, Tailor, Configure, Customize: The Articulation Work of Customizing AI Fairness Checklists , they identify how contextualizing this checklist introduces new forms of work for AI practitioners and other stakeholders, while opening up new sites for negotiation and contestation of values in AI. The researchers also identify how the contextualization process may help AI practitioners develop a shared language around AI fairness. They also identify dynamics related to ownership over this process that suggest larger issues of accountability in responsible AI work.
MS MARCO Web Search: A Large-scale Information-rich Web Dataset with Millions of Real Click Labels
LLMs are becoming indispensable tools for many creative and information related tasks, but they still come with limitations, including a tendency to fabricate content. State-of-the-art algorithms pair the LLM with an external, dynamically updated knowledge base to ground the LLM’s answers and provide up-to-date information. However, these techniques require large amounts of relevant, labeled training data that have not previously been publicly available.
In a recent paper: MS MARCO Web Search: A Large-scale Information-rich Web Dataset with Millions of Real Click Labels presented at the 2024 ACM Web Conference, researchers from Microsoft introduce a novel dataset that closely mimics real-world web document and query distribution. MS MARCO Web Search contains 10 million unique queries across 93 languages with millions of relevant labeled query-document pairs. It uses ClueWeb22’s 10 billion high-quality web pages as the document corpus and provides rich information for various kinds of downstream tasks.
This dataset unlocks several new research directions that previous datasets cannot well support, including generic end-to-end neural indexer models, generic embedding models, and next generation information access systems with LLMs. MS MARCO Web Search offers a retrieval benchmark with three web scale retrieval challenge tasks, each with automatic evaluation and leaderboard. These tasks demand innovation in both machine learning and information retrieval systems. The researchers intend for MS MARCO Web Search to lay the groundwork for future advancements in AI and systems research.
- AI Case Studies for Natural Science Research with Bonnie Kruft
Among the stunning changes and disruptions driven by AI, one of the most significant is the impact on scientific discovery. In her presentation at EmTech Digital 2024 (opens in new tab) , Bonnie Kruft, partner deputy director at Microsoft Research AI for Science, outlined some examples of how generative AI enables groundbreaking research in the natural sciences. Recent breakthroughs aided by AI include small molecular inhibitors for treating infectious disease, the discovery of new materials for energy storage, and new drug development.
Catch a replay of the presentation , including a follow-up Q&A with the audience, and hear how researchers are reducing discovery times from years to months. The discussion explores safe and responsible AI practices, how large language models can work with science-based models, and what lies ahead for AI in science.
Microsoft Research in the news
The tiny glass blocks that can preserve your data for centuries .
The Times UK | April 27, 2024
Microsoft’s Project Silica is an innovative form of long-term storage – potentially revolutionizing how important data can be preserved for future generations.
These Recyclable Circuit Boards Could Stem E-Waste
IEEE Spectrum | May 2, 2024
New research from the University of Washington and Microsoft show that vitrimer-based PCBs can be broken down into a gel for repeated reuse. The research stems from the Microsoft Research Climate Initiative .
Today’s AI models are impressive. Teams of them will be formidable
The Economist | May 13, 2024
Teams of LLMs are more capable and intelligent than solitary agents because a single job can be split into many smaller, more specialized tasks, says Chi Wang, a principal researcher at Microsoft Research in Redmond, Washington.
You Only Cache Once: Decoder-Decoder Architectures for Language Models
Microsoft Research LinkedIn | May 11, 2024
YOCO is a novel decoder-decoder architecture for LLMs, enhancing memory efficiency by caching key-value pairs only once. It slashes KV cache memory and prefilling time and makes 1M-length LLMs practical.
Peter Lee discusses new technologies that will drive the future of drug discovery
AAPS | May 10, 2024
The president of Microsoft Research explores how new advances in technologies, such as AI and machine learning, are transforming biotechnology, in the closing plenary of the AAPS National Biotechnology Conference (NBC) on Thursday, May 16.
PKSHA develops advanced LLMs in collaboration with Microsoft Japan
Business Wire | April 29, 2024
PKSHA Technology has developed one of the first Japanese-English LLMs in collaboration with Microsoft Japan. This development primarily focuses on boosting productivity within contact centers and corporate help desks.
BRAID fellowships include three collaborations with Microsoft Research
Bridging Responsible AI Divides | May 2024
BRAID fellowships support individual researchers in partnership with public and private organizations to address challenges in the field of responsible AI. Among the latest fellowships are three supported by Microsoft Research.
Related publications
Injecting new knowledge into large language models via supervised fine-tuning, continue reading.

Research Focus: Week of April 15, 2024

Research Focus: Week of April 1, 2024

Research Focus: Week of February 5, 2024

Research Focus: Week of May 22, 2023
Research areas.
Research Groups
- Technology and Empowerment | India
- Research in Software Engineering (RiSE)
- FATE: Fairness, Accountability, Transparency & Ethics in AI
- Research for Industry
Related tools
Related projects.
- GenAI for Industry
- Project VeLLM
- Project FarmVibes
- Jacdac: Connect and code electronics. Instantly.
- AI Fairness Checklist
Related labs
- Microsoft Research Lab - India
- Microsoft Research Lab - Redmond
- Microsoft Research Lab - New York City
- Microsoft Research AI for Science
Related videos
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
Share this page:

COMMENTS
Cryptography has the importa nt purpose of providing reliabl e, strong, and robust network and data security. In this paper, we. demonstrated a review of some of the research that has been ...
Cryptography is the solution to secure data from different security risks. To enhance the security of communication systems better cryptosystems technology is obvious in the area of cryptography. Our research focuses on data encryption and decryption technique for a better cryptosystem; where we have proposed a new approach that ensures better ...
This paper showed that we reviewed a part of the evaluation, which was also organized in cryptography, beginning with how the numbers used for various security purposes in cryptography operate. IT and attractive procedures for guaranteeing particular, cash-related, clinical and web-business data and ensuring the required standard of safety will ...
Quantum key distribution (QKD) 1, 2, 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 ...
Quantum cryptography is one of the emerging topics in the field of computer industry. This paper focus on quantum cryptography and how this technology contributes value to a defense-in-depth strategy pertaining to completely secure key distribution. The scope of this paper covers the weaknesses of modern digital cryptosystems, the fundamental ...
Cryptography is an international, scientific, peer-reviewed, open access journal on cryptography published quarterly online by MDPI. Open Access — free for readers, with article processing charges (APC) paid by authors or their institutions. High Visibility: indexed within Scopus, ESCI (Web of Science), dblp, and other databases. Rapid ...
The aim of this paper is to explore the knowledge related to the Quantum Cryptography, Quantum Key Distribution; and their elements, implementation, and the latest research. Moreover, exploration of the loopholes and the security of Internet of Things (IoT) infrastructure and current used classical cryptographic algorithms are described in the ...
Cryptography is the study of assured communication procedure which allows only the sender and the intended person to review the message and the content shared. The simplest method used is the symmetric algorithm in which once the message is encrypted it is sent to the recipient along with its secret key. 2.
A Review Paper on Cryptography Abstract: With the internet having reached a level that merges with our lives, growing explosively during the last several decades, data security has become a main concern for anyone connected to the web. Data security ensures that our data is only accessible by the intended receiver and prevents any modification ...
NIST-approved cryptography algorithms are chosen based on security criteria such as confidentiality and identity authentication [14]. This paper will focus on the architectural aspects of KMS. The primary contributions of this research paper include: • Conduct a comprehensive literature survey of KMS systems. •
The 18 full papers presented in this volume were carefully reviewed and selected from 46 submissions. The conference presents papers on subjects such as public key cryptography; symmetric cryptography; signatures; homomorphic encryption; identity-based encryption; constructions; and threshold signatures and fault attacks.
During the last few decades, digital communication has played a vital role in various sectors such as healthcare departments, banking, information technology companies, industries, and other fields. Nowadays, all data are transmitted over the Internet, which needs high protection for transmitting the original data from source to destination. In order to secure digital communication ...
Cryptography. , Volume 5, Issue 4 (December 2021) - 13 articles. Cover Story ( view full-size image ): As the demand for wearables and fitness trackers is rising, serious concerns over data privacy and security issues are coming into the spotlight. Individual users' sensitive information, such as heart rate, calories burned, or even sleep ...
Cryptography. , Volume 6, Issue 1 (March 2022) - 13 articles. Cover Story ( view full-size image ): Anonymous authentication systems have received the attention of many fields, as they secure user privacy. Both group signatures and ring signatures preserve user anonymity, allowing users to hide their identity within a group.
Further, a detailed description of commonly using evaluations parameters for both steganography and cryptography, are given in this paper. Overall, this work is an attempt to create a better understanding of image steganography and its coupling with the encryption methods for developing state of art double layer security crypto-stego systems.
Cryptography Research Center, Technology Innovation Institute, Abu Dhabi, UAE. Search about this author, Carlo Sanna. ... In this paper, a new variant of differential cryptanalysis is developed by applying the idea of the boomerang attack on the truncated differential. We call this variant a triangle differential cryptanalysis since it utilizes ...
MIT math major Janabel Xia sorts algorithms and improving traffic control systems for driverless vehicles, is a member of several dance clubs, is active in several social justice organizations, worked on cryptography and web authentication technology, and created a polling app that allows users to vote anonymously.
AI technology's role in this is to help data monetization project teams use data in ways that humans cannot, usually because of big complexity or scope or required speed. In our data monetization research, we have regularly seen leaders use AI effectively to realize extraordinary business goals.
This survey paper introduced an overview of IoT technology, architecture, and applications and a detailed analysis comparing all cryptographic algorithms and their use in day-to-day life activities. ... New technology. ... -constrained ones (RFID tags, sensors, etc.) is another crucial aspect of the technology. In the next section, the research ...
Quantum cryptography is an emerging technology in which two parties can secure network communications by applying the phenomena of quantum physics. The security of these transmissions is based on the inviolability of the laws of quantum mechanics. Quantum cryptography was born in the early seventies when Steven Wiesner wrote "Conjugate Coding", which took more than ten years to end this paper ...
MIT researchers' "consensus game" is a game-theoretic approach for language model decoding. The equilibrium-ranking algorithm harmonizes generative and discriminative querying to enhance prediction accuracy across various tasks, outperforming larger models and demonstrating the potential of game theory in improving language model consistency and truthfulness.
Cryptography. , Volume 7, Issue 1 (March 2023) - 15 articles. Cover Story ( view full-size image ): Traditional password authentication methods have raised many issues in the past, including insecure practices, so it comes as no surprise that the evolution of authentication should arrive in the form of password-less solutions.
Nour Younis, a Brigham and Women's postdoc, and Nuria Puigmal, a Brigham and Women's postdoc and former MIT research affiliate, are the lead authors of the paper. The researchers are now working on launching a company to further develop the technology, led by Puigmal, who was recently awarded a Harvard Business School Blavatnik Fellowship.
A bipartisan group of senators released a long-awaited legislative plan for A.I., calling for billions in funding to propel U.S. leadership in the technology while offering few details on regulations.
Honorable Mentions. B ig or Small, It's All in Your Head: Visuo-Haptic Illusion of Size-Change Using Finger-Repositioning Myung Jin Kim, Eyal Ofek, Michel Pahud, Mike J. Sinclair, Andrea Bianchi This research introduces a fixed-sized VR controller that uses finger repositioning to create a visuo-haptic illusion of dynamic size changes in handheld virtual objects, allowing users to perceive ...
Founded at the Massachusetts Institute of Technology in 1899, MIT Technology Review is a world-renowned, independent media company whose insight, analysis, reviews, interviews and live events ...
In a recent paper: A Reflection on Human-Notebook Experiences in the Era of AI, researchers from Microsoft summarize literature on how new AI technology has impacted human-notebook interaction and human-computer interaction (HCI) paradigms, new challenges and user behavior around using AI assistants, and recent research on AI assistants in ...