
Get science-backed answers as you write with Paperpal's Research feature

How to Write a Research Paper Introduction (with Examples)

The research paper introduction section, along with the Title and Abstract, can be considered the face of any research paper. The following article is intended to guide you in organizing and writing the research paper introduction for a quality academic article or dissertation.
The research paper introduction aims to present the topic to the reader. A study will only be accepted for publishing if you can ascertain that the available literature cannot answer your research question. So it is important to ensure that you have read important studies on that particular topic, especially those within the last five to ten years, and that they are properly referenced in this section. 1 What should be included in the research paper introduction is decided by what you want to tell readers about the reason behind the research and how you plan to fill the knowledge gap. The best research paper introduction provides a systemic review of existing work and demonstrates additional work that needs to be done. It needs to be brief, captivating, and well-referenced; a well-drafted research paper introduction will help the researcher win half the battle.
The introduction for a research paper is where you set up your topic and approach for the reader. It has several key goals:
- Present your research topic
- Capture reader interest
- Summarize existing research
- Position your own approach
- Define your specific research problem and problem statement
- Highlight the novelty and contributions of the study
- Give an overview of the paper’s structure
The research paper introduction can vary in size and structure depending on whether your paper presents the results of original empirical research or is a review paper. Some research paper introduction examples are only half a page while others are a few pages long. In many cases, the introduction will be shorter than all of the other sections of your paper; its length depends on the size of your paper as a whole.
- Break through writer’s block. Write your research paper introduction with Paperpal Copilot
Table of Contents
What is the introduction for a research paper, why is the introduction important in a research paper, craft a compelling introduction section with paperpal. try now, 1. introduce the research topic:, 2. determine a research niche:, 3. place your research within the research niche:, craft accurate research paper introductions with paperpal. start writing now, frequently asked questions on research paper introduction, key points to remember.
The introduction in a research paper is placed at the beginning to guide the reader from a broad subject area to the specific topic that your research addresses. They present the following information to the reader
- Scope: The topic covered in the research paper
- Context: Background of your topic
- Importance: Why your research matters in that particular area of research and the industry problem that can be targeted
The research paper introduction conveys a lot of information and can be considered an essential roadmap for the rest of your paper. A good introduction for a research paper is important for the following reasons:
- It stimulates your reader’s interest: A good introduction section can make your readers want to read your paper by capturing their interest. It informs the reader what they are going to learn and helps determine if the topic is of interest to them.
- It helps the reader understand the research background: Without a clear introduction, your readers may feel confused and even struggle when reading your paper. A good research paper introduction will prepare them for the in-depth research to come. It provides you the opportunity to engage with the readers and demonstrate your knowledge and authority on the specific topic.
- It explains why your research paper is worth reading: Your introduction can convey a lot of information to your readers. It introduces the topic, why the topic is important, and how you plan to proceed with your research.
- It helps guide the reader through the rest of the paper: The research paper introduction gives the reader a sense of the nature of the information that will support your arguments and the general organization of the paragraphs that will follow. It offers an overview of what to expect when reading the main body of your paper.
What are the parts of introduction in the research?
A good research paper introduction section should comprise three main elements: 2
- What is known: This sets the stage for your research. It informs the readers of what is known on the subject.
- What is lacking: This is aimed at justifying the reason for carrying out your research. This could involve investigating a new concept or method or building upon previous research.
- What you aim to do: This part briefly states the objectives of your research and its major contributions. Your detailed hypothesis will also form a part of this section.
How to write a research paper introduction?
The first step in writing the research paper introduction is to inform the reader what your topic is and why it’s interesting or important. This is generally accomplished with a strong opening statement. The second step involves establishing the kinds of research that have been done and ending with limitations or gaps in the research that you intend to address. Finally, the research paper introduction clarifies how your own research fits in and what problem it addresses. If your research involved testing hypotheses, these should be stated along with your research question. The hypothesis should be presented in the past tense since it will have been tested by the time you are writing the research paper introduction.
The following key points, with examples, can guide you when writing the research paper introduction section:
- Highlight the importance of the research field or topic
- Describe the background of the topic
- Present an overview of current research on the topic
Example: The inclusion of experiential and competency-based learning has benefitted electronics engineering education. Industry partnerships provide an excellent alternative for students wanting to engage in solving real-world challenges. Industry-academia participation has grown in recent years due to the need for skilled engineers with practical training and specialized expertise. However, from the educational perspective, many activities are needed to incorporate sustainable development goals into the university curricula and consolidate learning innovation in universities.
- Reveal a gap in existing research or oppose an existing assumption
- Formulate the research question
Example: There have been plausible efforts to integrate educational activities in higher education electronics engineering programs. However, very few studies have considered using educational research methods for performance evaluation of competency-based higher engineering education, with a focus on technical and or transversal skills. To remedy the current need for evaluating competencies in STEM fields and providing sustainable development goals in engineering education, in this study, a comparison was drawn between study groups without and with industry partners.
- State the purpose of your study
- Highlight the key characteristics of your study
- Describe important results
- Highlight the novelty of the study.
- Offer a brief overview of the structure of the paper.
Example: The study evaluates the main competency needed in the applied electronics course, which is a fundamental core subject for many electronics engineering undergraduate programs. We compared two groups, without and with an industrial partner, that offered real-world projects to solve during the semester. This comparison can help determine significant differences in both groups in terms of developing subject competency and achieving sustainable development goals.
Write a Research Paper Introduction in Minutes with Paperpal
Paperpal Copilot is a generative AI-powered academic writing assistant. It’s trained on millions of published scholarly articles and over 20 years of STM experience. Paperpal Copilot helps authors write better and faster with:
- Real-time writing suggestions
- In-depth checks for language and grammar correction
- Paraphrasing to add variety, ensure academic tone, and trim text to meet journal limits
With Paperpal Copilot, create a research paper introduction effortlessly. In this step-by-step guide, we’ll walk you through how Paperpal transforms your initial ideas into a polished and publication-ready introduction.
How to use Paperpal to write the Introduction section
Step 1: Sign up on Paperpal and click on the Copilot feature, under this choose Outlines > Research Article > Introduction
Step 2: Add your unstructured notes or initial draft, whether in English or another language, to Paperpal, which is to be used as the base for your content.
Step 3: Fill in the specifics, such as your field of study, brief description or details you want to include, which will help the AI generate the outline for your Introduction.
Step 4: Use this outline and sentence suggestions to develop your content, adding citations where needed and modifying it to align with your specific research focus.
Step 5: Turn to Paperpal’s granular language checks to refine your content, tailor it to reflect your personal writing style, and ensure it effectively conveys your message.
You can use the same process to develop each section of your article, and finally your research paper in half the time and without any of the stress.
The purpose of the research paper introduction is to introduce the reader to the problem definition, justify the need for the study, and describe the main theme of the study. The aim is to gain the reader’s attention by providing them with necessary background information and establishing the main purpose and direction of the research.
The length of the research paper introduction can vary across journals and disciplines. While there are no strict word limits for writing the research paper introduction, an ideal length would be one page, with a maximum of 400 words over 1-4 paragraphs. Generally, it is one of the shorter sections of the paper as the reader is assumed to have at least a reasonable knowledge about the topic. 2 For example, for a study evaluating the role of building design in ensuring fire safety, there is no need to discuss definitions and nature of fire in the introduction; you could start by commenting upon the existing practices for fire safety and how your study will add to the existing knowledge and practice.
When deciding what to include in the research paper introduction, the rest of the paper should also be considered. The aim is to introduce the reader smoothly to the topic and facilitate an easy read without much dependency on external sources. 3 Below is a list of elements you can include to prepare a research paper introduction outline and follow it when you are writing the research paper introduction. Topic introduction: This can include key definitions and a brief history of the topic. Research context and background: Offer the readers some general information and then narrow it down to specific aspects. Details of the research you conducted: A brief literature review can be included to support your arguments or line of thought. Rationale for the study: This establishes the relevance of your study and establishes its importance. Importance of your research: The main contributions are highlighted to help establish the novelty of your study Research hypothesis: Introduce your research question and propose an expected outcome. Organization of the paper: Include a short paragraph of 3-4 sentences that highlights your plan for the entire paper
Cite only works that are most relevant to your topic; as a general rule, you can include one to three. Note that readers want to see evidence of original thinking. So it is better to avoid using too many references as it does not leave much room for your personal standpoint to shine through. Citations in your research paper introduction support the key points, and the number of citations depend on the subject matter and the point discussed. If the research paper introduction is too long or overflowing with citations, it is better to cite a few review articles rather than the individual articles summarized in the review. A good point to remember when citing research papers in the introduction section is to include at least one-third of the references in the introduction.
The literature review plays a significant role in the research paper introduction section. A good literature review accomplishes the following: Introduces the topic – Establishes the study’s significance – Provides an overview of the relevant literature – Provides context for the study using literature – Identifies knowledge gaps However, remember to avoid making the following mistakes when writing a research paper introduction: Do not use studies from the literature review to aggressively support your research Avoid direct quoting Do not allow literature review to be the focus of this section. Instead, the literature review should only aid in setting a foundation for the manuscript.
Remember the following key points for writing a good research paper introduction: 4
- Avoid stuffing too much general information: Avoid including what an average reader would know and include only that information related to the problem being addressed in the research paper introduction. For example, when describing a comparative study of non-traditional methods for mechanical design optimization, information related to the traditional methods and differences between traditional and non-traditional methods would not be relevant. In this case, the introduction for the research paper should begin with the state-of-the-art non-traditional methods and methods to evaluate the efficiency of newly developed algorithms.
- Avoid packing too many references: Cite only the required works in your research paper introduction. The other works can be included in the discussion section to strengthen your findings.
- Avoid extensive criticism of previous studies: Avoid being overly critical of earlier studies while setting the rationale for your study. A better place for this would be the Discussion section, where you can highlight the advantages of your method.
- Avoid describing conclusions of the study: When writing a research paper introduction remember not to include the findings of your study. The aim is to let the readers know what question is being answered. The actual answer should only be given in the Results and Discussion section.
To summarize, the research paper introduction section should be brief yet informative. It should convince the reader the need to conduct the study and motivate him to read further. If you’re feeling stuck or unsure, choose trusted AI academic writing assistants like Paperpal to effortlessly craft your research paper introduction and other sections of your research article.
1. Jawaid, S. A., & Jawaid, M. (2019). How to write introduction and discussion. Saudi Journal of Anaesthesia, 13(Suppl 1), S18.
2. Dewan, P., & Gupta, P. (2016). Writing the title, abstract and introduction: Looks matter!. Indian pediatrics, 53, 235-241.
3. Cetin, S., & Hackam, D. J. (2005). An approach to the writing of a scientific Manuscript1. Journal of Surgical Research, 128(2), 165-167.
4. Bavdekar, S. B. (2015). Writing introduction: Laying the foundations of a research paper. Journal of the Association of Physicians of India, 63(7), 44-6.
Paperpal is a comprehensive AI writing toolkit that helps students and researchers achieve 2x the writing in half the time. It leverages 21+ years of STM experience and insights from millions of research articles to provide in-depth academic writing, language editing, and submission readiness support to help you write better, faster.
Get accurate academic translations, rewriting support, grammar checks, vocabulary suggestions, and generative AI assistance that delivers human precision at machine speed. Try for free or upgrade to Paperpal Prime starting at US$19 a month to access premium features, including consistency, plagiarism, and 30+ submission readiness checks to help you succeed.
Experience the future of academic writing – Sign up to Paperpal and start writing for free!
Related Reads:
- Scientific Writing Style Guides Explained
- 5 Reasons for Rejection After Peer Review
- Ethical Research Practices For Research with Human Subjects
- 8 Most Effective Ways to Increase Motivation for Thesis Writing
Practice vs. Practise: Learn the Difference
Academic paraphrasing: why paperpal’s rewrite should be your first choice , you may also like, how to write the first draft of a..., mla works cited page: format, template & examples, how to write a high-quality conference paper, academic editing: how to self-edit academic text with..., measuring academic success: definition & strategies for excellence, phd qualifying exam: tips for success , ai in education: it’s time to change the..., is it ethical to use ai-generated abstracts without..., what are journal guidelines on using generative ai..., quillbot review: features, pricing, and free alternatives.
- Privacy Policy

Home » Research Paper Introduction – Writing Guide and Examples
Research Paper Introduction – Writing Guide and Examples
Table of Contents

Research Paper Introduction
Research paper introduction is the first section of a research paper that provides an overview of the study, its purpose, and the research question (s) or hypothesis (es) being investigated. It typically includes background information about the topic, a review of previous research in the field, and a statement of the research objectives. The introduction is intended to provide the reader with a clear understanding of the research problem, why it is important, and how the study will contribute to existing knowledge in the field. It also sets the tone for the rest of the paper and helps to establish the author’s credibility and expertise on the subject.
How to Write Research Paper Introduction
Writing an introduction for a research paper can be challenging because it sets the tone for the entire paper. Here are some steps to follow to help you write an effective research paper introduction:
- Start with a hook : Begin your introduction with an attention-grabbing statement, a question, or a surprising fact that will make the reader interested in reading further.
- Provide background information: After the hook, provide background information on the topic. This information should give the reader a general idea of what the topic is about and why it is important.
- State the research problem: Clearly state the research problem or question that the paper addresses. This should be done in a concise and straightforward manner.
- State the research objectives: After stating the research problem, clearly state the research objectives. This will give the reader an idea of what the paper aims to achieve.
- Provide a brief overview of the paper: At the end of the introduction, provide a brief overview of the paper. This should include a summary of the main points that will be discussed in the paper.
- Revise and refine: Finally, revise and refine your introduction to ensure that it is clear, concise, and engaging.
Structure of Research Paper Introduction
The following is a typical structure for a research paper introduction:
- Background Information: This section provides an overview of the topic of the research paper, including relevant background information and any previous research that has been done on the topic. It helps to give the reader a sense of the context for the study.
- Problem Statement: This section identifies the specific problem or issue that the research paper is addressing. It should be clear and concise, and it should articulate the gap in knowledge that the study aims to fill.
- Research Question/Hypothesis : This section states the research question or hypothesis that the study aims to answer. It should be specific and focused, and it should clearly connect to the problem statement.
- Significance of the Study: This section explains why the research is important and what the potential implications of the study are. It should highlight the contribution that the research makes to the field.
- Methodology: This section describes the research methods that were used to conduct the study. It should be detailed enough to allow the reader to understand how the study was conducted and to evaluate the validity of the results.
- Organization of the Paper : This section provides a brief overview of the structure of the research paper. It should give the reader a sense of what to expect in each section of the paper.
Research Paper Introduction Examples
Research Paper Introduction Examples could be:
Example 1: In recent years, the use of artificial intelligence (AI) has become increasingly prevalent in various industries, including healthcare. AI algorithms are being developed to assist with medical diagnoses, treatment recommendations, and patient monitoring. However, as the use of AI in healthcare grows, ethical concerns regarding privacy, bias, and accountability have emerged. This paper aims to explore the ethical implications of AI in healthcare and propose recommendations for addressing these concerns.
Example 2: Climate change is one of the most pressing issues facing our planet today. The increasing concentration of greenhouse gases in the atmosphere has resulted in rising temperatures, changing weather patterns, and other environmental impacts. In this paper, we will review the scientific evidence on climate change, discuss the potential consequences of inaction, and propose solutions for mitigating its effects.
Example 3: The rise of social media has transformed the way we communicate and interact with each other. While social media platforms offer many benefits, including increased connectivity and access to information, they also present numerous challenges. In this paper, we will examine the impact of social media on mental health, privacy, and democracy, and propose solutions for addressing these issues.
Example 4: The use of renewable energy sources has become increasingly important in the face of climate change and environmental degradation. While renewable energy technologies offer many benefits, including reduced greenhouse gas emissions and energy independence, they also present numerous challenges. In this paper, we will assess the current state of renewable energy technology, discuss the economic and political barriers to its adoption, and propose solutions for promoting the widespread use of renewable energy.
Purpose of Research Paper Introduction
The introduction section of a research paper serves several important purposes, including:
- Providing context: The introduction should give readers a general understanding of the topic, including its background, significance, and relevance to the field.
- Presenting the research question or problem: The introduction should clearly state the research question or problem that the paper aims to address. This helps readers understand the purpose of the study and what the author hopes to accomplish.
- Reviewing the literature: The introduction should summarize the current state of knowledge on the topic, highlighting the gaps and limitations in existing research. This shows readers why the study is important and necessary.
- Outlining the scope and objectives of the study: The introduction should describe the scope and objectives of the study, including what aspects of the topic will be covered, what data will be collected, and what methods will be used.
- Previewing the main findings and conclusions : The introduction should provide a brief overview of the main findings and conclusions that the study will present. This helps readers anticipate what they can expect to learn from the paper.
When to Write Research Paper Introduction
The introduction of a research paper is typically written after the research has been conducted and the data has been analyzed. This is because the introduction should provide an overview of the research problem, the purpose of the study, and the research questions or hypotheses that will be investigated.
Once you have a clear understanding of the research problem and the questions that you want to explore, you can begin to write the introduction. It’s important to keep in mind that the introduction should be written in a way that engages the reader and provides a clear rationale for the study. It should also provide context for the research by reviewing relevant literature and explaining how the study fits into the larger field of research.
Advantages of Research Paper Introduction
The introduction of a research paper has several advantages, including:
- Establishing the purpose of the research: The introduction provides an overview of the research problem, question, or hypothesis, and the objectives of the study. This helps to clarify the purpose of the research and provide a roadmap for the reader to follow.
- Providing background information: The introduction also provides background information on the topic, including a review of relevant literature and research. This helps the reader understand the context of the study and how it fits into the broader field of research.
- Demonstrating the significance of the research: The introduction also explains why the research is important and relevant. This helps the reader understand the value of the study and why it is worth reading.
- Setting expectations: The introduction sets the tone for the rest of the paper and prepares the reader for what is to come. This helps the reader understand what to expect and how to approach the paper.
- Grabbing the reader’s attention: A well-written introduction can grab the reader’s attention and make them interested in reading further. This is important because it can help to keep the reader engaged and motivated to read the rest of the paper.
- Creating a strong first impression: The introduction is the first part of the research paper that the reader will see, and it can create a strong first impression. A well-written introduction can make the reader more likely to take the research seriously and view it as credible.
- Establishing the author’s credibility: The introduction can also establish the author’s credibility as a researcher. By providing a clear and thorough overview of the research problem and relevant literature, the author can demonstrate their expertise and knowledge in the field.
- Providing a structure for the paper: The introduction can also provide a structure for the rest of the paper. By outlining the main sections and sub-sections of the paper, the introduction can help the reader navigate the paper and find the information they are looking for.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

Informed Consent in Research – Types, Templates...

APA Table of Contents – Format and Example

Ethical Considerations – Types, Examples and...

Chapter Summary & Overview – Writing Guide...

Research Objectives – Types, Examples and...

Figures in Research Paper – Examples and Guide
Writing a Research Paper Introduction (with 3 Examples)
Nail your research paper's introduction! Learn to captivate and inform readers from the start—our guide shows how!

Ertugrul Portakal
Apr 12, 2024
%20(3).png)
TABLE OF CONTENTS
A catchy and informative introduction is essential in academic writing, especially if you want your readers to have background information about your paper. However, writing an interesting and informative introduction can sometimes be a time-consuming and tiring process. If you don't know where to start when crafting an introduction, no need to worry - we've got you covered!
In this article, we will explain step by step what an introduction is in academic writing and how to write it!
Ready? Let's start!
- An introduction is a paragraph that provides information about your entire paper and aims to attract and inform the reader.
- Before writing an introduction or even starting your paper, you need to research academic sources.
- The first one or two sentences of an introduction paragraph should be a hook to attract the reader's attention.
- Afterwards, you need to prepare the reader for your argument by giving background information about your topic.
- Finally, you should state your argument about your topic with a thesis statement.
- If you are writing a longer paper, you can inform your readers about the map of your paper.
- If you are looking for an AI assistant to support you throughout your writing process, TextCortex is designed for you with its advanced features.
What is an Introduction in a research paper?
In any academic writing, including essays and research papers, an introduction is the first paragraph that the reader will encounter. This paragraph should both attract the reader's attention and give them the necessary information about the paper. In any academic paper, the introduction paragraph constitutes 10% of the paper's total word count. For example, if you are preparing a 3,000-word paper, your introduction paragraph should consist of approximately 300 words. You should also write sentences within these 300 words that will attract the reader's attention and provide them with information about the paper.
Importance of an Introduction Paragraph
The biggest function of an introduction paragraph is to prepare the reader for the author's thesis statement. A traditional introduction paragraph begins with a few sentences or questions that will catch the reader's attention. After attracting the reader's attention, necessary background information on the subject is given. Finally, the author explains to the readers what the whole paper is about by stating the thesis. A thesis statement is the final sentence that summarizes the main points of your paper and conveys your claim.
First Things First: Preliminary Research
When working on any academic writing type, it is essential to start by researching your topic thoroughly before beginning to type. What sets academic writing apart from other writing types is the requirement for it to be written using accurate information from reliable sources.
Researching academic sources can be a time-consuming and unnecessary process. One has to read through hundreds of pages, review dozens of articles and verify the accuracy of each source. However, if you're looking to reduce your workload and maximize efficiency by automating repetitive tasks such as literature review, ZenoChat is the perfect solution for you. With its web search feature, ZenoChat can use the entire internet as a data source. Additionally, by activating the "scholar" option of the ZenoChat web search feature, you can ensure that it only uses academic sources when generating output.
How to Create an Introduction for Academic Writing?
Creating an introduction paragraph that is interesting, informative, and conveys your thesis is an easier process than it seems. As long as you have sufficient information about your topic and an outline , you can write engaging introductions by following a few simple steps. Let's take a closer look at how to write an introduction for academic writing.
1-) Start with a Catchy Hook
Your first sentence is one of the factors that most influence a reader's decision to read your paper. This sentence determines the tone of your paper and attracts the reader's attention. For this reason, we recommend that you start your introduction paragraph with a strong and catchy hook sentence.
- Avoid long and complex sentences
- Use clear and concise sentences
- Write a sentence that will spark the reader's curiosity
- You can ask questions that will encourage the reader to read the remaining paragraph
- Avoid fact or overly broad sentences
- Avoid using dictionary definitions as your hook
2-) Give Background Information
After writing a strong hook sentence, you need to provide basic information about your topic so that the reader can understand what they will learn about when they read your paper. In this section, you can benefit from opinions that support or oppose your argument. Additionally, this section should refer to the body paragraphs of your writing.
- You can write a background information sentence for each body paragraph.
- The information here should be concise and compact
- Avoid talking about your evidence and results unless necessary.
3-) State Your Thesis
After attracting the reader's attention and providing background information, it is time to present your approach and argument towards the topic with a thesis statement. A thesis statement usually comprises one or two sentences and communicates the paper's argument to the reader. A well-written thesis statement should express your stance on the topic.
- Avoid merely stating a fact
- Claim your argument
4-) Tell Reader About Your Paper
Although you need to move on to body paragraphs after the thesis statement in short papers, it will be useful to add a few sentences that will guide the reader in your longer papers. This way, your readers can better understand which arguments they will encounter on which pages and the course of your paper. That leads the reader to clearly understand and follow your content.
Let’s Wrap it Up
Writing an interesting and informative introduction is usually a long process that requires a lot of rewriting. You may need to rewrite a sentence dozens of times so that your words and sentences clearly describe your paper and argument. Fortunately, you can generate state-of-the-art introductions using AI tools and use them with a little editing.
When it comes to text generation, paraphrasing, and grammar & spelling checking, TextCortex is the way to go with its advanced LLMs and customization options. With TextCortex, you can generate all writing types, including introduction, from scratch, rewrite your existing texts, change their tone of voice, or fix their grammar. TextCortex is available as a web application and browser extension. The TextCortex browser extension is integrated with 30,000+ websites and apps. So, you can complete your AI-driven writing tasks anywhere and anytime.
Let's examine a few sample introductions generated by TextCortex.
Example Introduction #1
“Should social media platforms be banned from collecting their users' data?”

Example Introduction #2
“Do electric vehicles decrease overall emissions?”

Example Introduction #3
“Is graffiti an act of vandalism or the creation of art?”

One AI copilot that truly gets you.
Connect multiple data sources, define the voice for your AI and taste what it feels like to have a fully-personalized AI copilot on 50,000+ platforms.
Did you like this article? Explore a few more related posts.
%20(6).png)
How to Create a Strong Thesis?
%20(5).png)
Top 3 AI Tools That Write Essays (Free & Paid)
%20(4).png)
5 Main Essay Types & Guide with Examples
Questions answers..
TextCortex is a powerful AI-powered writing tool that can help you reduce your writing time, handle big tasks, and create high-quality content without errors. With its customizable platform, personalized intelligence experience, advanced writing and research capabilities, and error-free content, TextCortex is the perfect tool for creative professionals who want to be a creative force in their industry.
Our AI copilot learned how to write from more than 3 billion sentences and has the ability to create unique content. However, fact-checking is something which still requires a human approval.
TextCortex supports more than 25 languages including English, Dutch, German, Ukranian, Romanian, Spanish, Portuguese, French, Italian.
Yes, TextCortex is completely free to use with all of its features. When you sign up, you receive 100 free creations. Then you will receive 20 recurring creations every day on the free plan.
Yes, we have a Text Generation API, please talk to us directly to implement it. You can reach out to us at [email protected]
Account sharing is not allowed. If you have a need for more than 5 seats for an account, you can directly contact us at [email protected]
Yes, TextCortex offers 14-day free trial for users to try out all features extensively with higher number of generations. But keep in mind that you can already try everything with the free plan. There is no feature that is locked behind a premium plan.
Overall, TextCortex AI has over 1000 five-star reviews on reputable review sites such as G2, Trustpilot and Capterra.
TextCortex learns and adapts to your unique writing style and knowledge, making it easier for you to write high-quality & personalized content.
Your premium features will be available until the end of your subscription date, then your account plan will be set to Free plan.
General Questions
Your ai copilot is ready to collaborate with you..
Connect your knowledge, customize the style and start collaborating with your AI copilot.
Writing an Introduction for a Scientific Paper
Dr. michelle harris, dr. janet batzli, biocore.
This section provides guidelines on how to construct a solid introduction to a scientific paper including background information, study question , biological rationale, hypothesis , and general approach . If the Introduction is done well, there should be no question in the reader’s mind why and on what basis you have posed a specific hypothesis.
Broad Question : based on an initial observation (e.g., “I see a lot of guppies close to the shore. Do guppies like living in shallow water?”). This observation of the natural world may inspire you to investigate background literature or your observation could be based on previous research by others or your own pilot study. Broad questions are not always included in your written text, but are essential for establishing the direction of your research.
Background Information : key issues, concepts, terminology, and definitions needed to understand the biological rationale for the experiment. It often includes a summary of findings from previous, relevant studies. Remember to cite references, be concise, and only include relevant information given your audience and your experimental design. Concisely summarized background information leads to the identification of specific scientific knowledge gaps that still exist. (e.g., “No studies to date have examined whether guppies do indeed spend more time in shallow water.”)
Testable Question : these questions are much more focused than the initial broad question, are specific to the knowledge gap identified, and can be addressed with data. (e.g., “Do guppies spend different amounts of time in water <1 meter deep as compared to their time in water that is >1 meter deep?”)
Biological Rationale : describes the purpose of your experiment distilling what is known and what is not known that defines the knowledge gap that you are addressing. The “BR” provides the logic for your hypothesis and experimental approach, describing the biological mechanism and assumptions that explain why your hypothesis should be true.
The biological rationale is based on your interpretation of the scientific literature, your personal observations, and the underlying assumptions you are making about how you think the system works. If you have written your biological rationale, your reader should see your hypothesis in your introduction section and say to themselves, “Of course, this hypothesis seems very logical based on the rationale presented.”
- A thorough rationale defines your assumptions about the system that have not been revealed in scientific literature or from previous systematic observation. These assumptions drive the direction of your specific hypothesis or general predictions.
- Defining the rationale is probably the most critical task for a writer, as it tells your reader why your research is biologically meaningful. It may help to think about the rationale as an answer to the questions— how is this investigation related to what we know, what assumptions am I making about what we don’t yet know, AND how will this experiment add to our knowledge? *There may or may not be broader implications for your study; be careful not to overstate these (see note on social justifications below).
- Expect to spend time and mental effort on this. You may have to do considerable digging into the scientific literature to define how your experiment fits into what is already known and why it is relevant to pursue.
- Be open to the possibility that as you work with and think about your data, you may develop a deeper, more accurate understanding of the experimental system. You may find the original rationale needs to be revised to reflect your new, more sophisticated understanding.
- As you progress through Biocore and upper level biology courses, your rationale should become more focused and matched with the level of study e ., cellular, biochemical, or physiological mechanisms that underlie the rationale. Achieving this type of understanding takes effort, but it will lead to better communication of your science.
***Special note on avoiding social justifications: You should not overemphasize the relevance of your experiment and the possible connections to large-scale processes. Be realistic and logical —do not overgeneralize or state grand implications that are not sensible given the structure of your experimental system. Not all science is easily applied to improving the human condition. Performing an investigation just for the sake of adding to our scientific knowledge (“pure or basic science”) is just as important as applied science. In fact, basic science often provides the foundation for applied studies.
Hypothesis / Predictions : specific prediction(s) that you will test during your experiment. For manipulative experiments, the hypothesis should include the independent variable (what you manipulate), the dependent variable(s) (what you measure), the organism or system , the direction of your results, and comparison to be made.
|
|
We hypothesized that reared in warm water will have a greater sexual mating response. (The dependent variable “sexual response” has not been defined enough to be able to make this hypothesis testable or falsifiable. In addition, no comparison has been specified— greater sexual mating response as compared to what?) | We hypothesized that ) reared in warm water temperatures ranging from 25-28 °C ( ) would produce greater ( ) numbers of male offspring and females carrying haploid egg sacs ( ) than reared in cooler water temperatures of 18-22°C. |
If you are doing a systematic observation , your hypothesis presents a variable or set of variables that you predict are important for helping you characterize the system as a whole, or predict differences between components/areas of the system that help you explain how the system functions or changes over time.
|
|
We hypothesize that the frequency and extent of algal blooms in Lake Mendota over the last 10 years causes fish kills and imposes a human health risk. (The variables “frequency and extent of algal blooms,” “fish kills” and “human health risk” have not been defined enough to be able to make this hypothesis testable or falsifiable. How do you measure algal blooms? Although implied, hypothesis should express predicted direction of expected results [ , higher frequency associated with greater kills]. Note that cause and effect cannot be implied without a controlled, manipulative experiment.) | We hypothesize that increasing ( ) cell densities of algae ( ) in Lake Mendota over the last 10 years is correlated with 1. increased numbers of dead fish ( ) washed up on Madison beaches and 2. increased numbers of reported hospital/clinical visits ( .) following full-body exposure to lake water. |
Experimental Approach : Briefly gives the reader a general sense of the experiment, the type of data it will yield, and the kind of conclusions you expect to obtain from the data. Do not confuse the experimental approach with the experimental protocol . The experimental protocol consists of the detailed step-by-step procedures and techniques used during the experiment that are to be reported in the Methods and Materials section.
Some Final Tips on Writing an Introduction
- As you progress through the Biocore sequence, for instance, from organismal level of Biocore 301/302 to the cellular level in Biocore 303/304, we expect the contents of your “Introduction” paragraphs to reflect the level of your coursework and previous writing experience. For example, in Biocore 304 (Cell Biology Lab) biological rationale should draw upon assumptions we are making about cellular and biochemical processes.
- Be Concise yet Specific: Remember to be concise and only include relevant information given your audience and your experimental design. As you write, keep asking, “Is this necessary information or is this irrelevant detail?” For example, if you are writing a paper claiming that a certain compound is a competitive inhibitor to the enzyme alkaline phosphatase and acts by binding to the active site, you need to explain (briefly) Michaelis-Menton kinetics and the meaning and significance of Km and Vmax. This explanation is not necessary if you are reporting the dependence of enzyme activity on pH because you do not need to measure Km and Vmax to get an estimate of enzyme activity.
- Another example: if you are writing a paper reporting an increase in Daphnia magna heart rate upon exposure to caffeine you need not describe the reproductive cycle of magna unless it is germane to your results and discussion. Be specific and concrete, especially when making introductory or summary statements.
Where Do You Discuss Pilot Studies? Many times it is important to do pilot studies to help you get familiar with your experimental system or to improve your experimental design. If your pilot study influences your biological rationale or hypothesis, you need to describe it in your Introduction. If your pilot study simply informs the logistics or techniques, but does not influence your rationale, then the description of your pilot study belongs in the Materials and Methods section.
from an Intro Ecology Lab: Researchers studying global warming predict an increase in average global temperature of 1.3°C in the next 10 years (Seetwo 2003). are small zooplankton that live in freshwater inland lakes. They are filter-feeding crustaceans with a transparent exoskeleton that allows easy observation of heart rate and digestive function. Thomas et al (2001) found that heart rate increases significantly in higher water temperatures are also thought to switch their mode of reproduction from asexual to sexual in response to extreme temperatures. Gender is not mediated by genetics, but by the environment. Therefore, reproduction may be sensitive to increased temperatures resulting from global warming (maybe a question?) and may serve as a good environmental indicator for global climate change. In this experiment we hypothesized that reared in warm water will switch from an asexual to a sexual mode of reproduction. In order to prove this hypothesis correct we observed grown in warm and cold water and counted the number of males observed after 10 days. Comments: Background information · Good to recognize as a model organism from which some general conclusions can be made about the quality of the environment; however no attempt is made to connect increased lake temperatures and gender. Link early on to increase focus. · Connection to global warming is too far-reaching. First sentence gives impression that Global Warming is topic for this paper. Changes associated with global warming are not well known and therefore little can be concluded about use of as indicator species. · Information about heart rate is unnecessary because heart rate in not being tested in this experiment. Rationale · Rationale is missing; how is this study related to what we know about D. magna survivorship and reproduction as related to water temperature, and how will this experiment contribute to our knowledge of the system? · Think about the ecosystem in which this organism lives and the context. Under what conditions would D. magna be in a body of water with elevated temperatures? Hypothesis · Not falsifiable; variables need to be better defined (state temperatures or range tested rather than “warm” or “cold”) and predict direction and magnitude of change in number of males after 10 days. · It is unclear what comparison will be made or what the control is · What dependent variable will be measured to determine “switch” in mode of reproduction (what criteria are definitive for switch?) Approach · Hypotheses cannot be “proven” correct. They are either supported or rejected. | Introduction are small zooplankton found in freshwater inland lakes and are thought to switch their mode of reproduction from asexual to sexual in response to extreme temperatures (Mitchell 1999). Lakes containing have an average summer surface temperature of 20°C (Harper 1995) but may increase by more than 15% when expose to warm water effluent from power plants, paper mills, and chemical industry (Baker et al. 2000). Could an increase in lake temperature caused by industrial thermal pollution affect the survivorship and reproduction of ? The sex of is mediated by the environment rather than genetics. Under optimal environmental conditions, populations consist of asexually reproducing females. When the environment shifts may be queued to reproduce sexually resulting in the production of male offspring and females carrying haploid eggs in sacs called ephippia (Mitchell 1999). The purpose of this laboratory study is to examine the effects of increased water temperature on survivorship and reproduction. This study will help us characterize the magnitude of environmental change required to induce the onset of the sexual life cycle in . Because are known to be a sensitive environmental indicator species (Baker et al. 2000) and share similar structural and physiological features with many aquatic species, they serve as a good model for examining the effects of increasing water temperature on reproduction in a variety of aquatic invertebrates. We hypothesized that populations reared in water temperatures ranging from 24-26 °C would have lower survivorship, higher male/female ratio among the offspring, and more female offspring carrying ephippia as compared with grown in water temperatures of 20-22°C. To test this hypothesis we reared populations in tanks containing water at either 24 +/- 2°C or 20 +/- 2°C. Over 10 days, we monitored survivorship, determined the sex of the offspring, and counted the number of female offspring containing ephippia. Comments: Background information · Opening paragraph provides good focus immediately. The study organism, gender switching response, and temperature influence are mentioned in the first sentence. Although it does a good job documenting average lake water temperature and changes due to industrial run-off, it fails to make an argument that the 15% increase in lake temperature could be considered “extreme” temperature change. · The study question is nicely embedded within relevant, well-cited background information. Alternatively, it could be stated as the first sentence in the introduction, or after all background information has been discussed before the hypothesis. Rationale · Good. Well-defined purpose for study; to examine the degree of environmental change necessary to induce the Daphnia sexual life |
How will introductions be evaluated? The following is part of the rubric we will be using to evaluate your papers.
0 = inadequate (C, D or F) | 1 = adequate (BC) | 2 = good (B) | 3 = very good (AB) | 4 = excellent (A) | |
Introduction BIG PICTURE: Did the Intro convey why experiment was performed and what it was designed to test?
| Introduction provides little to no relevant information. (This often results in a hypothesis that “comes out of nowhere.”) | Many key components are very weak or missing; those stated are unclear and/or are not stated concisely. Weak/missing components make it difficult to follow the rest of the paper. e.g., background information is not focused on a specific question and minimal biological rationale is presented such that hypothesis isn’t entirely logical
| Covers most key components but could be done much more logically, clearly, and/or concisely. e.g., biological rationale not fully developed but still supports hypothesis. Remaining components are done reasonably well, though there is still room for improvement. | Concisely & clearly covers all but one key component (w/ exception of rationale; see left) clearly covers all key components but could be a little more concise and/or clear. e.g., has done a reasonably nice job with the Intro but fails to state the approach OR has done a nice job with Intro but has also included some irrelevant background information
| Clearly, concisely, & logically presents all key components: relevant & correctly cited background information, question, biological rationale, hypothesis, approach. |
- USC Libraries
- Research Guides
Organizing Your Social Sciences Research Paper
- 4. The Introduction
- Purpose of Guide
- Design Flaws to Avoid
- Independent and Dependent Variables
- Glossary of Research Terms
- Reading Research Effectively
- Narrowing a Topic Idea
- Broadening a Topic Idea
- Extending the Timeliness of a Topic Idea
- Academic Writing Style
- Applying Critical Thinking
- Choosing a Title
- Making an Outline
- Paragraph Development
- Research Process Video Series
- Executive Summary
- The C.A.R.S. Model
- Background Information
- The Research Problem/Question
- Theoretical Framework
- Citation Tracking
- Content Alert Services
- Evaluating Sources
- Primary Sources
- Secondary Sources
- Tiertiary Sources
- Scholarly vs. Popular Publications
- Qualitative Methods
- Quantitative Methods
- Insiderness
- Using Non-Textual Elements
- Limitations of the Study
- Common Grammar Mistakes
- Writing Concisely
- Avoiding Plagiarism
- Footnotes or Endnotes?
- Further Readings
- Generative AI and Writing
- USC Libraries Tutorials and Other Guides
- Bibliography
The introduction leads the reader from a general subject area to a particular topic of inquiry. It establishes the scope, context, and significance of the research being conducted by summarizing current understanding and background information about the topic, stating the purpose of the work in the form of the research problem supported by a hypothesis or a set of questions, explaining briefly the methodological approach used to examine the research problem, highlighting the potential outcomes your study can reveal, and outlining the remaining structure and organization of the paper.
Key Elements of the Research Proposal. Prepared under the direction of the Superintendent and by the 2010 Curriculum Design and Writing Team. Baltimore County Public Schools.
Importance of a Good Introduction
Think of the introduction as a mental road map that must answer for the reader these four questions:
- What was I studying?
- Why was this topic important to investigate?
- What did we know about this topic before I did this study?
- How will this study advance new knowledge or new ways of understanding?
According to Reyes, there are three overarching goals of a good introduction: 1) ensure that you summarize prior studies about the topic in a manner that lays a foundation for understanding the research problem; 2) explain how your study specifically addresses gaps in the literature, insufficient consideration of the topic, or other deficiency in the literature; and, 3) note the broader theoretical, empirical, and/or policy contributions and implications of your research.
A well-written introduction is important because, quite simply, you never get a second chance to make a good first impression. The opening paragraphs of your paper will provide your readers with their initial impressions about the logic of your argument, your writing style, the overall quality of your research, and, ultimately, the validity of your findings and conclusions. A vague, disorganized, or error-filled introduction will create a negative impression, whereas, a concise, engaging, and well-written introduction will lead your readers to think highly of your analytical skills, your writing style, and your research approach. All introductions should conclude with a brief paragraph that describes the organization of the rest of the paper.
Hirano, Eliana. “Research Article Introductions in English for Specific Purposes: A Comparison between Brazilian, Portuguese, and English.” English for Specific Purposes 28 (October 2009): 240-250; Samraj, B. “Introductions in Research Articles: Variations Across Disciplines.” English for Specific Purposes 21 (2002): 1–17; Introductions. The Writing Center. University of North Carolina; “Writing Introductions.” In Good Essay Writing: A Social Sciences Guide. Peter Redman. 4th edition. (London: Sage, 2011), pp. 63-70; Reyes, Victoria. Demystifying the Journal Article. Inside Higher Education.
Structure and Writing Style
I. Structure and Approach
The introduction is the broad beginning of the paper that answers three important questions for the reader:
- What is this?
- Why should I read it?
- What do you want me to think about / consider doing / react to?
Think of the structure of the introduction as an inverted triangle of information that lays a foundation for understanding the research problem. Organize the information so as to present the more general aspects of the topic early in the introduction, then narrow your analysis to more specific topical information that provides context, finally arriving at your research problem and the rationale for studying it [often written as a series of key questions to be addressed or framed as a hypothesis or set of assumptions to be tested] and, whenever possible, a description of the potential outcomes your study can reveal.
These are general phases associated with writing an introduction: 1. Establish an area to research by:
- Highlighting the importance of the topic, and/or
- Making general statements about the topic, and/or
- Presenting an overview on current research on the subject.
2. Identify a research niche by:
- Opposing an existing assumption, and/or
- Revealing a gap in existing research, and/or
- Formulating a research question or problem, and/or
- Continuing a disciplinary tradition.
3. Place your research within the research niche by:
- Stating the intent of your study,
- Outlining the key characteristics of your study,
- Describing important results, and
- Giving a brief overview of the structure of the paper.
NOTE: It is often useful to review the introduction late in the writing process. This is appropriate because outcomes are unknown until you've completed the study. After you complete writing the body of the paper, go back and review introductory descriptions of the structure of the paper, the method of data gathering, the reporting and analysis of results, and the conclusion. Reviewing and, if necessary, rewriting the introduction ensures that it correctly matches the overall structure of your final paper.
II. Delimitations of the Study
Delimitations refer to those characteristics that limit the scope and define the conceptual boundaries of your research . This is determined by the conscious exclusionary and inclusionary decisions you make about how to investigate the research problem. In other words, not only should you tell the reader what it is you are studying and why, but you must also acknowledge why you rejected alternative approaches that could have been used to examine the topic.
Obviously, the first limiting step was the choice of research problem itself. However, implicit are other, related problems that could have been chosen but were rejected. These should be noted in the conclusion of your introduction. For example, a delimitating statement could read, "Although many factors can be understood to impact the likelihood young people will vote, this study will focus on socioeconomic factors related to the need to work full-time while in school." The point is not to document every possible delimiting factor, but to highlight why previously researched issues related to the topic were not addressed.
Examples of delimitating choices would be:
- The key aims and objectives of your study,
- The research questions that you address,
- The variables of interest [i.e., the various factors and features of the phenomenon being studied],
- The method(s) of investigation,
- The time period your study covers, and
- Any relevant alternative theoretical frameworks that could have been adopted.
Review each of these decisions. Not only do you clearly establish what you intend to accomplish in your research, but you should also include a declaration of what the study does not intend to cover. In the latter case, your exclusionary decisions should be based upon criteria understood as, "not interesting"; "not directly relevant"; “too problematic because..."; "not feasible," and the like. Make this reasoning explicit!
NOTE: Delimitations refer to the initial choices made about the broader, overall design of your study and should not be confused with documenting the limitations of your study discovered after the research has been completed.
ANOTHER NOTE: Do not view delimitating statements as admitting to an inherent failing or shortcoming in your research. They are an accepted element of academic writing intended to keep the reader focused on the research problem by explicitly defining the conceptual boundaries and scope of your study. It addresses any critical questions in the reader's mind of, "Why the hell didn't the author examine this?"
III. The Narrative Flow
Issues to keep in mind that will help the narrative flow in your introduction :
- Your introduction should clearly identify the subject area of interest . A simple strategy to follow is to use key words from your title in the first few sentences of the introduction. This will help focus the introduction on the topic at the appropriate level and ensures that you get to the subject matter quickly without losing focus, or discussing information that is too general.
- Establish context by providing a brief and balanced review of the pertinent published literature that is available on the subject. The key is to summarize for the reader what is known about the specific research problem before you did your analysis. This part of your introduction should not represent a comprehensive literature review--that comes next. It consists of a general review of the important, foundational research literature [with citations] that establishes a foundation for understanding key elements of the research problem. See the drop-down menu under this tab for " Background Information " regarding types of contexts.
- Clearly state the hypothesis that you investigated . When you are first learning to write in this format it is okay, and actually preferable, to use a past statement like, "The purpose of this study was to...." or "We investigated three possible mechanisms to explain the...."
- Why did you choose this kind of research study or design? Provide a clear statement of the rationale for your approach to the problem studied. This will usually follow your statement of purpose in the last paragraph of the introduction.
IV. Engaging the Reader
A research problem in the social sciences can come across as dry and uninteresting to anyone unfamiliar with the topic . Therefore, one of the goals of your introduction is to make readers want to read your paper. Here are several strategies you can use to grab the reader's attention:
- Open with a compelling story . Almost all research problems in the social sciences, no matter how obscure or esoteric , are really about the lives of people. Telling a story that humanizes an issue can help illuminate the significance of the problem and help the reader empathize with those affected by the condition being studied.
- Include a strong quotation or a vivid, perhaps unexpected, anecdote . During your review of the literature, make note of any quotes or anecdotes that grab your attention because they can used in your introduction to highlight the research problem in a captivating way.
- Pose a provocative or thought-provoking question . Your research problem should be framed by a set of questions to be addressed or hypotheses to be tested. However, a provocative question can be presented in the beginning of your introduction that challenges an existing assumption or compels the reader to consider an alternative viewpoint that helps establish the significance of your study.
- Describe a puzzling scenario or incongruity . This involves highlighting an interesting quandary concerning the research problem or describing contradictory findings from prior studies about a topic. Posing what is essentially an unresolved intellectual riddle about the problem can engage the reader's interest in the study.
- Cite a stirring example or case study that illustrates why the research problem is important . Draw upon the findings of others to demonstrate the significance of the problem and to describe how your study builds upon or offers alternatives ways of investigating this prior research.
NOTE: It is important that you choose only one of the suggested strategies for engaging your readers. This avoids giving an impression that your paper is more flash than substance and does not distract from the substance of your study.
Freedman, Leora and Jerry Plotnick. Introductions and Conclusions. University College Writing Centre. University of Toronto; Introduction. The Structure, Format, Content, and Style of a Journal-Style Scientific Paper. Department of Biology. Bates College; Introductions. The Writing Center. University of North Carolina; Introductions. The Writer’s Handbook. Writing Center. University of Wisconsin, Madison; Introductions, Body Paragraphs, and Conclusions for an Argument Paper. The Writing Lab and The OWL. Purdue University; “Writing Introductions.” In Good Essay Writing: A Social Sciences Guide . Peter Redman. 4th edition. (London: Sage, 2011), pp. 63-70; Resources for Writers: Introduction Strategies. Program in Writing and Humanistic Studies. Massachusetts Institute of Technology; Sharpling, Gerald. Writing an Introduction. Centre for Applied Linguistics, University of Warwick; Samraj, B. “Introductions in Research Articles: Variations Across Disciplines.” English for Specific Purposes 21 (2002): 1–17; Swales, John and Christine B. Feak. Academic Writing for Graduate Students: Essential Skills and Tasks . 2nd edition. Ann Arbor, MI: University of Michigan Press, 2004 ; Writing Your Introduction. Department of English Writing Guide. George Mason University.
Writing Tip
Avoid the "Dictionary" Introduction
Giving the dictionary definition of words related to the research problem may appear appropriate because it is important to define specific terminology that readers may be unfamiliar with. However, anyone can look a word up in the dictionary and a general dictionary is not a particularly authoritative source because it doesn't take into account the context of your topic and doesn't offer particularly detailed information. Also, placed in the context of a particular discipline, a term or concept may have a different meaning than what is found in a general dictionary. If you feel that you must seek out an authoritative definition, use a subject specific dictionary or encyclopedia [e.g., if you are a sociology student, search for dictionaries of sociology]. A good database for obtaining definitive definitions of concepts or terms is Credo Reference .
Saba, Robert. The College Research Paper. Florida International University; Introductions. The Writing Center. University of North Carolina.
Another Writing Tip
When Do I Begin?
A common question asked at the start of any paper is, "Where should I begin?" An equally important question to ask yourself is, "When do I begin?" Research problems in the social sciences rarely rest in isolation from history. Therefore, it is important to lay a foundation for understanding the historical context underpinning the research problem. However, this information should be brief and succinct and begin at a point in time that illustrates the study's overall importance. For example, a study that investigates coffee cultivation and export in West Africa as a key stimulus for local economic growth needs to describe the beginning of exporting coffee in the region and establishing why economic growth is important. You do not need to give a long historical explanation about coffee exports in Africa. If a research problem requires a substantial exploration of the historical context, do this in the literature review section. In your introduction, make note of this as part of the "roadmap" [see below] that you use to describe the organization of your paper.
Introductions. The Writing Center. University of North Carolina; “Writing Introductions.” In Good Essay Writing: A Social Sciences Guide . Peter Redman. 4th edition. (London: Sage, 2011), pp. 63-70.
Yet Another Writing Tip
Always End with a Roadmap
The final paragraph or sentences of your introduction should forecast your main arguments and conclusions and provide a brief description of the rest of the paper [the "roadmap"] that let's the reader know where you are going and what to expect. A roadmap is important because it helps the reader place the research problem within the context of their own perspectives about the topic. In addition, concluding your introduction with an explicit roadmap tells the reader that you have a clear understanding of the structural purpose of your paper. In this way, the roadmap acts as a type of promise to yourself and to your readers that you will follow a consistent and coherent approach to addressing the topic of inquiry. Refer to it often to help keep your writing focused and organized.
Cassuto, Leonard. “On the Dissertation: How to Write the Introduction.” The Chronicle of Higher Education , May 28, 2018; Radich, Michael. A Student's Guide to Writing in East Asian Studies . (Cambridge, MA: Harvard University Writing n. d.), pp. 35-37.
- << Previous: Executive Summary
- Next: The C.A.R.S. Model >>
- Last Updated: May 30, 2024 9:38 AM
- URL: https://libguides.usc.edu/writingguide
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, automatically generate references for free.
- Knowledge Base
- Dissertation
How to Write a Thesis or Dissertation Introduction
Published on 9 September 2022 by Tegan George and Shona McCombes.
The introduction is the first section of your thesis or dissertation , appearing right after the table of contents . Your introduction draws your reader in, setting the stage for your research with a clear focus, purpose, and direction.
Your introduction should include:
- Your topic, in context: what does your reader need to know to understand your thesis dissertation?
- Your focus and scope: what specific aspect of the topic will you address?
- The relevance of your research: how does your work fit into existing studies on your topic?
- Your questions and objectives: what does your research aim to find out, and how?
- An overview of your structure: what does each section contribute to the overall aim?
Instantly correct all language mistakes in your text
Be assured that you'll submit flawless writing. Upload your document to correct all your mistakes.
Table of contents
How to start your introduction, topic and context, focus and scope, relevance and importance, questions and objectives, overview of the structure, thesis introduction example, introduction checklist, frequently asked questions about introductions.
Although your introduction kicks off your dissertation, it doesn’t have to be the first thing you write – in fact, it’s often one of the very last parts to be completed (just before your abstract ).
It’s a good idea to write a rough draft of your introduction as you begin your research, to help guide you. If you wrote a research proposal , consider using this as a template, as it contains many of the same elements. However, be sure to revise your introduction throughout the writing process, making sure it matches the content of your ensuing sections.
The only proofreading tool specialized in correcting academic writing
The academic proofreading tool has been trained on 1000s of academic texts and by native English editors. Making it the most accurate and reliable proofreading tool for students.
Correct my document today
Begin by introducing your research topic and giving any necessary background information. It’s important to contextualise your research and generate interest. Aim to show why your topic is timely or important. You may want to mention a relevant news item, academic debate, or practical problem.
After a brief introduction to your general area of interest, narrow your focus and define the scope of your research.
You can narrow this down in many ways, such as by:
- Geographical area
- Time period
- Demographics or communities
- Themes or aspects of the topic
It’s essential to share your motivation for doing this research, as well as how it relates to existing work on your topic. Further, you should also mention what new insights you expect it will contribute.
Start by giving a brief overview of the current state of research. You should definitely cite the most relevant literature, but remember that you will conduct a more in-depth survey of relevant sources in the literature review section, so there’s no need to go too in-depth in the introduction.
Depending on your field, the importance of your research might focus on its practical application (e.g., in policy or management) or on advancing scholarly understanding of the topic (e.g., by developing theories or adding new empirical data). In many cases, it will do both.
Ultimately, your introduction should explain how your thesis or dissertation:
- Helps solve a practical or theoretical problem
- Addresses a gap in the literature
- Builds on existing research
- Proposes a new understanding of your topic
Prevent plagiarism, run a free check.
Perhaps the most important part of your introduction is your questions and objectives, as it sets up the expectations for the rest of your thesis or dissertation. How you formulate your research questions and research objectives will depend on your discipline, topic, and focus, but you should always clearly state the central aim of your research.
If your research aims to test hypotheses , you can formulate them here. Your introduction is also a good place for a conceptual framework that suggests relationships between variables .
- Conduct surveys to collect data on students’ levels of knowledge, understanding, and positive/negative perceptions of government policy.
- Determine whether attitudes to climate policy are associated with variables such as age, gender, region, and social class.
- Conduct interviews to gain qualitative insights into students’ perspectives and actions in relation to climate policy.
To help guide your reader, end your introduction with an outline of the structure of the thesis or dissertation to follow. Share a brief summary of each chapter, clearly showing how each contributes to your central aims. However, be careful to keep this overview concise: 1-2 sentences should be enough.
I. Introduction
Human language consists of a set of vowels and consonants which are combined to form words. During the speech production process, thoughts are converted into spoken utterances to convey a message. The appropriate words and their meanings are selected in the mental lexicon (Dell & Burger, 1997). This pre-verbal message is then grammatically coded, during which a syntactic representation of the utterance is built.
Speech, language, and voice disorders affect the vocal cords, nerves, muscles, and brain structures, which result in a distorted language reception or speech production (Sataloff & Hawkshaw, 2014). The symptoms vary from adding superfluous words and taking pauses to hoarseness of the voice, depending on the type of disorder (Dodd, 2005). However, distortions of the speech may also occur as a result of a disease that seems unrelated to speech, such as multiple sclerosis or chronic obstructive pulmonary disease.
This study aims to determine which acoustic parameters are suitable for the automatic detection of exacerbations in patients suffering from chronic obstructive pulmonary disease (COPD) by investigating which aspects of speech differ between COPD patients and healthy speakers and which aspects differ between COPD patients in exacerbation and stable COPD patients.
Checklist: Introduction
I have introduced my research topic in an engaging way.
I have provided necessary context to help the reader understand my topic.
I have clearly specified the focus of my research.
I have shown the relevance and importance of the dissertation topic .
I have clearly stated the problem or question that my research addresses.
I have outlined the specific objectives of the research .
I have provided an overview of the dissertation’s structure .
You've written a strong introduction for your thesis or dissertation. Use the other checklists to continue improving your dissertation.
The introduction of a research paper includes several key elements:
- A hook to catch the reader’s interest
- Relevant background on the topic
- Details of your research problem
- A thesis statement or research question
- Sometimes an outline of the paper
Don’t feel that you have to write the introduction first. The introduction is often one of the last parts of the research paper you’ll write, along with the conclusion.
This is because it can be easier to introduce your paper once you’ve already written the body ; you may not have the clearest idea of your arguments until you’ve written them, and things can change during the writing process .
Research objectives describe what you intend your research project to accomplish.
They summarise the approach and purpose of the project and help to focus your research.
Your objectives should appear in the introduction of your research paper , at the end of your problem statement .
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the ‘Cite this Scribbr article’ button to automatically add the citation to our free Reference Generator.
George, T. & McCombes, S. (2022, September 09). How to Write a Thesis or Dissertation Introduction. Scribbr. Retrieved 10 June 2024, from https://www.scribbr.co.uk/thesis-dissertation/introduction/
Is this article helpful?
Tegan George
Other students also liked, what is a dissertation | 5 essential questions to get started, how to write an abstract | steps & examples, how to write a thesis or dissertation conclusion.
How to Write an Introduction For a Research Paper
Learn how to write a strong and efficient research paper introduction by following the suitable structure and avoiding typical errors.
An introduction to any type of paper is sometimes misunderstood as the beginning; yet, an introduction is actually intended to present your chosen subject to the audience in a way that makes it more appealing and leaves your readers thirsty for more information. After the title and abstract, your audience will read the introduction, thus it’s critical to get off to a solid start.
This article includes instructions on how to write an introduction for a research paper that engages the reader in your research. You can produce a strong opening for your research paper if you stick to the format and a few basic principles.
What is An Introduction To a Research Paper?
An introduction is the opening section of a research paper and the section that a reader is likely to read first, in which the objective and goals of the subsequent writing are stated.
The introduction serves numerous purposes. It provides context for your research, explains your topic and objectives, and provides an outline of the work. A solid introduction will establish the tone for the remainder of your paper, enticing readers to continue reading through the methodology, findings, and discussion.
Even though introductions are generally presented at the beginning of a document, we must distinguish an introduction from the beginning of your research. An introduction, as the name implies, is supposed to introduce your subject without extending it. All relevant information and facts should be placed in the body and conclusion, not the introduction.
Structure Of An Introduction
Before explaining how to write an introduction for a research paper , it’s necessary to comprehend a structure that will make your introduction stronger and more straightforward.
A Good Hook
A hook is one of the most effective research introduction openers. A hook’s objective is to stimulate the reader’s interest to read the research paper. There are various approaches you may take to generate a strong hook: startling facts, a question, a brief overview, or even a quotation.
Broad Overview
Following an excellent hook, you should present a wide overview of your major issue and some background information on your research. If you’re unsure about how to begin an essay introduction, the best approach is to offer a basic explanation of your topic before delving into specific issues. Simply said, you should begin with general information and then narrow it down to your relevant topics.
After offering some background information regarding your research’s main topic, go on to give readers a better understanding of what you’ll be covering throughout your research. In this section of your introduction, you should swiftly clarify your important topics in the sequence in which they will be addressed later, gradually introducing your thesis statement. You can use some The following are some critical questions to address in this section of your introduction: Who? What? Where? When? How? And why is that?
Thesis Statement
The thesis statement, which must be stated in the beginning clause of your research since your entire research revolves around it, is the most important component of your research.
A thesis statement presents your audience with a quick overview of the research’s main assertion. In the body section of your work, your key argument is what you will expose or debate about it. An excellent thesis statement is usually very succinct, accurate, explicit, clear, and focused. Typically, your thesis should be at the conclusion of your introductory paragraph/section.
Tips for Writing a Strong Introduction
Aside from the good structure, here are a few tips to make your introduction strong and accurate:
- Keep in mind the aim of your research and make sure your introduction supports it.
- Use an appealing and relevant hook that catches the reader’s attention right away.
- Make it obvious to your readers what your stance is.
- Demonstrate your knowledge of your subject.
- Provide your readers with a road map to help them understand what you will address throughout the research.
- Be succinct – it is advised that your opening introduction consists of around 8-9 percent of the overall amount of words in your article (for example, 160 words for a 2000 words essay).
- Make a strong and unambiguous thesis statement.
- Explain why the article is significant in 1-2 sentences.
- Remember to keep it interesting.
Mistakes to Avoid in Your Introduction
Check out what not to do and what to avoid now that you know the structure and how to write an introduction for a research paper .
- Lacking a feeling of direction or purpose.
- Giving out too much.
- Creating lengthy paragraphs.
- Excessive or insufficient background, literature, and theory.
- Including material that should be placed in the body and conclusion.
- Not writing enough or writing excessively.
- Using too many quotes.
Unleash the Power of Infographics with Mind the Graph
Do you believe your research is not efficient in communicating precisely or is not aesthetically appealing? Use the Mind The Graph tool to create great infographics and add more value to your research.

Subscribe to our newsletter
Exclusive high quality content about effective visual communication in science.
Unlock Your Creativity
Create infographics, presentations and other scientifically-accurate designs without hassle — absolutely free for 7 days!
About Jessica Abbadia
Jessica Abbadia is a lawyer that has been working in Digital Marketing since 2020, improving organic performance for apps and websites in various regions through ASO and SEO. Currently developing scientific and intellectual knowledge for the community's benefit. Jessica is an animal rights activist who enjoys reading and drinking strong coffee.
Content tags
- PRO Courses Guides New Tech Help Pro Expert Videos About wikiHow Pro Upgrade Sign In
- EDIT Edit this Article
- EXPLORE Tech Help Pro About Us Random Article Quizzes Request a New Article Community Dashboard This Or That Game Popular Categories Arts and Entertainment Artwork Books Movies Computers and Electronics Computers Phone Skills Technology Hacks Health Men's Health Mental Health Women's Health Relationships Dating Love Relationship Issues Hobbies and Crafts Crafts Drawing Games Education & Communication Communication Skills Personal Development Studying Personal Care and Style Fashion Hair Care Personal Hygiene Youth Personal Care School Stuff Dating All Categories Arts and Entertainment Finance and Business Home and Garden Relationship Quizzes Cars & Other Vehicles Food and Entertaining Personal Care and Style Sports and Fitness Computers and Electronics Health Pets and Animals Travel Education & Communication Hobbies and Crafts Philosophy and Religion Work World Family Life Holidays and Traditions Relationships Youth
- Browse Articles
- Learn Something New
- Quizzes Hot
- This Or That Game
- Train Your Brain
- Explore More
- Support wikiHow
- About wikiHow
- Log in / Sign up
- Education and Communications
- College University and Postgraduate
- Academic Writing
- Research Papers
How to Write a Research Introduction
Last Updated: December 6, 2023 Fact Checked
This article was co-authored by Megan Morgan, PhD . Megan Morgan is a Graduate Program Academic Advisor in the School of Public & International Affairs at the University of Georgia. She earned her PhD in English from the University of Georgia in 2015. There are 7 references cited in this article, which can be found at the bottom of the page. This article has been fact-checked, ensuring the accuracy of any cited facts and confirming the authority of its sources. This article has been viewed 2,654,071 times.
The introduction to a research paper can be the most challenging part of the paper to write. The length of the introduction will vary depending on the type of research paper you are writing. An introduction should announce your topic, provide context and a rationale for your work, before stating your research questions and hypothesis. Well-written introductions set the tone for the paper, catch the reader's interest, and communicate the hypothesis or thesis statement.
Introducing the Topic of the Paper

- In scientific papers this is sometimes known as an "inverted triangle", where you start with the broadest material at the start, before zooming in on the specifics. [2] X Research source
- The sentence "Throughout the 20th century, our views of life on other planets have drastically changed" introduces a topic, but does so in broad terms.
- It provides the reader with an indication of the content of the essay and encourages them to read on.

- For example, if you were writing a paper about the behaviour of mice when exposed to a particular substance, you would include the word "mice", and the scientific name of the relevant compound in the first sentences.
- If you were writing a history paper about the impact of the First World War on gender relations in Britain, you should mention those key words in your first few lines.

- This is especially important if you are attempting to develop a new conceptualization that uses language and terminology your readers may be unfamiliar with.

- If you use an anecdote ensure that is short and highly relevant for your research. It has to function in the same way as an alternative opening, namely to announce the topic of your research paper to your reader.
- For example, if you were writing a sociology paper about re-offending rates among young offenders, you could include a brief story of one person whose story reflects and introduces your topic.
- This kind of approach is generally not appropriate for the introduction to a natural or physical sciences research paper where the writing conventions are different.
Establishing the Context for Your Paper

- It is important to be concise in the introduction, so provide an overview on recent developments in the primary research rather than a lengthy discussion.
- You can follow the "inverted triangle" principle to focus in from the broader themes to those to which you are making a direct contribution with your paper.
- A strong literature review presents important background information to your own research and indicates the importance of the field.

- By making clear reference to existing work you can demonstrate explicitly the specific contribution you are making to move the field forward.
- You can identify a gap in the existing scholarship and explain how you are addressing it and moving understanding forward.

- For example, if you are writing a scientific paper you could stress the merits of the experimental approach or models you have used.
- Stress what is novel in your research and the significance of your new approach, but don't give too much detail in the introduction.
- A stated rationale could be something like: "the study evaluates the previously unknown anti-inflammatory effects of a topical compound in order to evaluate its potential clinical uses".
Specifying Your Research Questions and Hypothesis

- The research question or questions generally come towards the end of the introduction, and should be concise and closely focused.
- The research question might recall some of the key words established in the first few sentences and the title of your paper.
- An example of a research question could be "what were the consequences of the North American Free Trade Agreement on the Mexican export economy?"
- This could be honed further to be specific by referring to a particular element of the Free Trade Agreement and the impact on a particular industry in Mexico, such as clothing manufacture.
- A good research question should shape a problem into a testable hypothesis.

- If possible try to avoid using the word "hypothesis" and rather make this implicit in your writing. This can make your writing appear less formulaic.
- In a scientific paper, giving a clear one-sentence overview of your results and their relation to your hypothesis makes the information clear and accessible. [10] X Trustworthy Source PubMed Central Journal archive from the U.S. National Institutes of Health Go to source
- An example of a hypothesis could be "mice deprived of food for the duration of the study were expected to become more lethargic than those fed normally".

- This is not always necessary and you should pay attention to the writing conventions in your discipline.
- In a natural sciences paper, for example, there is a fairly rigid structure which you will be following.
- A humanities or social science paper will most likely present more opportunities to deviate in how you structure your paper.
Research Introduction Help

Community Q&A
- Use your research papers' outline to help you decide what information to include when writing an introduction. Thanks Helpful 0 Not Helpful 1
- Consider drafting your introduction after you have already completed the rest of your research paper. Writing introductions last can help ensure that you don't leave out any major points. Thanks Helpful 0 Not Helpful 0

- Avoid emotional or sensational introductions; these can create distrust in the reader. Thanks Helpful 50 Not Helpful 12
- Generally avoid using personal pronouns in your introduction, such as "I," "me," "we," "us," "my," "mine," or "our." Thanks Helpful 31 Not Helpful 7
- Don't overwhelm the reader with an over-abundance of information. Keep the introduction as concise as possible by saving specific details for the body of your paper. Thanks Helpful 24 Not Helpful 14
You Might Also Like

- ↑ https://library.sacredheart.edu/c.php?g=29803&p=185916
- ↑ https://www.aresearchguide.com/inverted-pyramid-structure-in-writing.html
- ↑ https://libguides.usc.edu/writingguide/introduction
- ↑ https://writing.wisc.edu/Handbook/PlanResearchPaper.html
- ↑ https://dept.writing.wisc.edu/wac/writing-an-introduction-for-a-scientific-paper/
- ↑ https://writing.wisc.edu/handbook/assignments/planresearchpaper/
- ↑ http://www.ncbi.nlm.nih.gov/pmc/articles/PMC3178846/
About This Article

To introduce your research paper, use the first 1-2 sentences to describe your general topic, such as “women in World War I.” Include and define keywords, such as “gender relations,” to show your reader where you’re going. Mention previous research into the topic with a phrase like, “Others have studied…”, then transition into what your contribution will be and why it’s necessary. Finally, state the questions that your paper will address and propose your “answer” to them as your thesis statement. For more information from our English Ph.D. co-author about how to craft a strong hypothesis and thesis, keep reading! Did this summary help you? Yes No
- Send fan mail to authors
Reader Success Stories
Abdulrahman Omar
Oct 5, 2018
Did this article help you?

May 9, 2021
Lavanya Gopakumar
Oct 1, 2016
Dengkai Zhang
May 14, 2018
Leslie Mae Cansana
Sep 22, 2016

Featured Articles

Trending Articles

Watch Articles

- Terms of Use
- Privacy Policy
- Do Not Sell or Share My Info
- Not Selling Info
Don’t miss out! Sign up for
wikiHow’s newsletter
Writing an Introduction
Ask these questions:
What is it?
It has two parts:
1. A general introduction to the topic you will be discussing 2. Your Thesis Statement
When do I do it?
How do I do it?
Some Examples:
Example 1 Teenagers in many American cities have been involved in more gangs in the last five years than ever before. These gangs of teens have been committing a lot of violent crimes. The victims of these crimes are both gang members and people outside of gangs. Many people do not want to travel to areas in our cities because of the danger from this problem. For this terrible situation to stop, it is going to take a combined effort on the part of many people. Excellent, supervised after-school programs, more jobs available for teens, and healthy family relationships will go a long way towards ending this crisis in our society. Example 2 During the Middle Ages in Europe and the Middle East there was much armed conflict between Christians and Muslims. Christians called these conflicts the Crusades because they were fighting under the sign of the cross to save the holy lands of the Bible from being desecrated by non-Christians. However, the true reason for fighting for these lands was less than holy. It was mainly a desire for economic gain that prompted the Christian leaders to send soldiers to fight in the Holy Land.

How to write Introduction for a Project
Why write introduction for a project, tips for writing an introduction , keep it brief but impactful, use factual information, start with a punchline, mention the details, inspiration for the project, it should be in sync with the description, it should be different from the conclusion, language of the project introduction, 1. creative project, 2. business project, 3. research project, 4. college project.

A project is a task done by an individual or a group to achieve a specific aim within a stipulated time . A project includes many interrelated sub-tasks to reach the final objective. A project may have particular rules to follow for individuals or groups. It also outlines the use of resources to complete the project. Any project needs an introduction as it mentions the entire details about the project, including the resources used and the timeline in which it was executed.
Like any mail, composition, or letter, a project also needs an introduction, as it introduces the team, the topic, and all other details. With an introduction, the project will retain identity, interest, and professionalism. Hence, a well-thought-out project introduction is imperative.
With an effective introduction, all your hard work can go to good use. As that’s the first para, a person reads, and it needs to be outlined well, or your project may look flat despite all the hours that went into it. A project intro is generally counted as one heading, but there may be cases when subheadings are required. While we are at this point, below are some tips for writing a goof introduction for a project.
An introduction should be brief, as more details can follow in subsequent paragraphs. The work of opening is to provide inputs that will be discussed later. It should also be noted that the brief here is relative to the entire project’s length. On average, the length of the introduction should be at most twenty per cent of the entire project and not less than ten per cent of the total count of words in the project. E.g. a project of 3000 words, will have an introduction between 300(10%) and 600(20%) words.
An introduction for a project should contain factual information. Factual information means information in numbers and figures. This will make the introduction brief and to the point. Numbers in the start mean significant information will be passed on, but it will require details in the description part to explain the source of those numbers. Using graphs or pictures will also make the introduction colourful or exciting.
Starting the project, an introduction with quotes or figures will give it a good punchline and generate reader interest. But it depends upon the type of project. Quoting a number would be a better option if the topic is related to business. In contrast, a creative project can have a quote from a famous person as the first line. E.g. “A deal of $5 million between company X and Y” will arouse sufficient interest and be impactful for a business project.
A gist of all the details that will follow suit can entice a reader to read further. Many times, if you submit a project that may be insignificant, but even if the superior reads all the relevant points covered in the introduction, half your battle is won.
It is a good idea to write about the inspiration for the project. Some ventures, when starting, have to make a project report, and they can briefly write about how they (the individual or group of people behind the project) got the idea. It could be an event that makes for an exciting read. This can also serve as a reminder for other people about how thoughts turn into projects due to inspiration.
The introduction for a project provides specific pointers for the description, and the details of the project should remain in that outline so that they do not look like elements added as an afterthought. The sync of the introduction should be with the description. Since the introduction of a project is written first, the report will have to follow the lead to be relevant.
The conclusion is written at the end and summarizes the whole project. To summarize does not mean repeating the introduction of the project. The introduction should be different from the conclusion. However, the length of the conclusion can be the same as the introduction. Again as in the case of description, the conclusion should follow the lead of the opening but have ending remarks that shapes the completion of project writing.
The language of the introduction of a project should be relevant to the topic of the project. There are many types of projects like projects done in college, projects done for professional courses or work, and creative projects. For example, a Business project will have a formal tone, while creative projects will have an informal style.
Examples of introduction for a project
There are different types of projects, and the examples given here can help you with more clarity and help you with introduction writing. To understand the difference better, we will take the same sample and present it differently as per the project type. Here are some examples of writing a project introduction according to the kind of project.
In the below examples, emphasis is given according to the topic. For instance, a creative project gives more importance to the video, while a medicinal research project gives more weightage to the medicinal properties.
Let us take an example of a creative project about making videos on types of medicinal plants . The creative part of this project is making a video. The Project introduction will contain how videos will be taken, where and the project’s duration. It can start with a quote like “healing comes from nature” and then describe the process of taking videos of medicinal plants. The camera used, and the type of mode used for shooting, the narration part, and light (natural or use of lights) will take a front seat.
If the same example is taken for a business project introduction, then it will contain lots of factual data. The starting line can be “profit of millions from medicinal plants.” Introducing a business project can be making medicines out of plants and selling them for a profit or on sales projection with projections of numbers and figures. Graphs or charts can be used to portray numerical and statistical information better.
If the same example is for a research project, then the start of the introduction can be “50 types of medicinal plants that can help mankind live a healthy life.” The opening should emphasize what kind of plants can be termed medicinal plants. It will further categorize the plants according to usage or the area they flourish. The introduction can use some pictures related to the healing properties of plants.
The introduction of a college project will again depend on the type of course selected. If the course of the college project is related to biosciences, then the opening will be similar to the above. If the college project is a photo management course, the introduction can be similar to the creative project. Write your college project introduction based on your course and its weightage on your overall marks.
Remember any project; the base remains the same – make it brief and impactful, be it with a quote, facts, or numbers. Ultimately, the motive is to impress a reader or your professor or employer and entice them to read through the entire thing.
Get in touch with us for professional content writing for your requirements. Learn More
Share with your friends
Related Posts:

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
APA Sample Paper

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
Note: This page reflects the latest version of the APA Publication Manual (i.e., APA 7), which released in October 2019. The equivalent resource for the older APA 6 style can be found here .
Media Files: APA Sample Student Paper , APA Sample Professional Paper
This resource is enhanced by Acrobat PDF files. Download the free Acrobat Reader
Note: The APA Publication Manual, 7 th Edition specifies different formatting conventions for student and professional papers (i.e., papers written for credit in a course and papers intended for scholarly publication). These differences mostly extend to the title page and running head. Crucially, citation practices do not differ between the two styles of paper.
However, for your convenience, we have provided two versions of our APA 7 sample paper below: one in student style and one in professional style.
Note: For accessibility purposes, we have used "Track Changes" to make comments along the margins of these samples. Those authored by [AF] denote explanations of formatting and [AWC] denote directions for writing and citing in APA 7.
APA 7 Student Paper:
Apa 7 professional paper:.
How to Write a Letter of Introduction (With Examples)
By Priya Jain
Published: January 22, 2024
Writer & Career Coach
Writing a letter of introduction serves as a tool for individuals and businesses to establish new connections, explore opportunities, or introduce services and products. An effectively written letter of introduction can open doors to job opportunities, business collaborations, and networking.
Whether you’re a freelancer seeking new clients, a business looking to forge new partnerships, or an individual exploring job opportunities, a compelling introduction letter can set the stage for fruitful interactions.
In this article, we explain what a letter of introduction is, explore what to include, and give examples you can use while creating your letter.
What Is a Letter of Introduction?
A letter of introduction is a document that introduces one party to another. It can serve various purposes in different contexts, including professional, academic, or personal settings.
This letter can be used to introduce oneself or by someone else to introduce a third party. The key purpose is establishing a connection or a rapport with the recipient, usually with a specific goal, such as exploring job opportunities, proposing business collaborations, or extending networks.
Individuals can use letters of introduction in social settings, like joining a new club or group, where you want to introduce yourself to the members. These letters often introduce a third party, like a colleague or a friend, to your contacts. This can be particularly helpful in professional networking or recommending someone for a job or project .

The Difference Between a Letter of Introduction and a Cover Letter
A letter of introduction and a cover letter are very different. Letters of introduction are generally used when you want to establish a new relationship that may or may not be job-related. It could be an introduction to a potential business partner, a networking contact, or a new community or group.
On the other hand, a cover letter is job-related. It’s sent alongside a resume when applying for a job. The cover letter focuses on why the applicant is suitable for a specific job, highlighting skills and experiences directly relevant to the job description. It’s more tailored to a particular role or company.
Letter of Introduction Examples
Here are some examples you can take inspiration from:
Job Application Letter of Introduction
This letter aims to introduce yourself to a potential employer, highlight relevant skills and experiences, express interest in the position, and provide a glimpse of your personality.
You can use this example to write a job application introduction letter:
Dear [Hiring Manager’s Name],
I am writing to express my keen interest in the [Job Title] position at [Company Name]. With [X years] of experience in [relevant field/industry], I have developed a comprehensive skill set that aligns with your team’s requirements.
My experience at [Previous Company] involved [mention key responsibilities or projects related to the new job]. I am particularly excited about the opportunity at [Company Name] because of [reasons specific to the company or role].
Enclosed is my resume, which further outlines my achievements. I would appreciate the opportunity to discuss how my experience and skills can contribute to the continued success of [Company Name].
Thank you for considering my application. I look forward to the possibility of contributing to your esteemed team.
[Your Name] [Your Contact Information]
Networking Introduction Letter
A networking introduction letter is a valuable tool for establishing new professional connections . It’s a way of introducing yourself to someone in your industry or field whom you haven’t met but wish to connect with for networking purposes.
Here’s an example:
Dear [Contact’s Name],
I hope this message finds you well. I am [Your Name], currently working as a [Your Job Title] at [Your Company]. I came across your profile on [LinkedIn/Professional Event] and was impressed by your extensive experience in [relevant field/industry].
I am reaching out to expand my professional network in the [specific industry or field] and would value the opportunity to learn from your insights. [Mention any mutual connections or shared interests, if applicable].
If you are open, I would appreciate talking with you briefly. I want to hear about your experiences, particularly regarding [specific topic or question].
Thank you for considering my request. I understand the value of your time and would be flexible to accommodate your schedule.
Best regards,
Cold Outreach Letter of Introduction
A cold outreach letter of introduction is used when contacting someone who does not know you or is not expecting your communication. It’s typically used professionally to introduce yourself, your company, or your products/services to a potential client, partner, or employer.
Here’s an example:
Dear [Recipient’s Name],
My name is [Your Name], and I am the [Your Position] at [Your Company]. I am reaching out to introduce our company and the innovative solutions we offer in [specific service or product area].
I believe that [Recipient’s Company] could significantly benefit from our [services/products], especially in [specific area of improvement or opportunity you’ve identified in their business]. We have partnered successfully with companies like yours, such as [mention any relevant clients or case studies], and achieved [mention specific results or improvements].
I would love the opportunity to discuss this further with you. Would you be available for a brief call next week? I am also attaching a brief overview of our services for your reference.
Thank you for your time, and I look forward to working together.
Warm regards,
Letter of Introduction Template
Creating a letter of introduction involves a structured approach to presenting your information effectively.
Here’s a template that you can adapt based on your specific needs:
[Your Name] [Your Address] [City, State, Zip Code] [Email Address] [Phone Number]
[Recipient’s Name] [Recipient’s Title] [Company/Organization Name] [Company Address] [City, State, Zip Code]
Dear [Recipient’s Name],
[Introductory Paragraph: Briefly introduce yourself, stating your name and current position or role. Explain how you came across the recipient, their work, or their organization.]
[Second Paragraph: State the purpose of your letter. Are you seeking a job opportunity, looking to network, or proposing a collaboration? Be specific about your intentions and why you are contacting this particular individual or company.]
[Third Paragraph: Concisely overview your relevant background and experience. Focus on key aspects of your career or education that align with the purpose of your letter.]
[Fourth Paragraph: Highlight one or two significant accomplishments or skills. Use specific examples demonstrating your capabilities and how they relate to the recipient’s needs or interests.]
[Fifth Paragraph: Mention any personal qualities or soft skills that set you apart and are relevant to the context of your introduction. Relate these traits to how they can be beneficial in achieving the goals outlined in your letter.]
[Call to Action: Clearly state what you hope to achieve with this letter. Whether it’s a follow-up meeting, a phone call, or further discussions, provide a clear action you’d like the recipient to take.]
Thank you for taking the time to read my letter. I am very interested in [discussing further, learning more about, etc.] and look forward to the possibility of [working together, meeting you, etc.]. Please contact me at [your email address] or [phone number].
[Your Name] [Attachments: Mention attachments such as your resume, portfolio, or other relevant documents.]
What You Need to Include in a Letter of Introduction
Incorporating specific elements in your letter of introduction can significantly enhance its effectiveness.
Here’s a breakdown of what to include following your provided structure:
Begin with a formal greeting. This is the initial greeting and sets the tone for the letter. Use a formal tone like “Dear [Recipient’s Name]”. If the recipient’s name is unknown, “Dear Hiring Manager” or “To Whom It May Concern” are alternatives. Personalizing the salutation, however, is preferable if you know the recipient’s name.
Introduction
Introduce yourself by stating your name and your current position or role in a professional context. This section should be brief, offering a snapshot of who you are. For instance, “My name is Jane Doe, and I am a Marketing Manager at XYZ Corporation.”
Purpose of the Letter
Clearly articulate why you are writing this letter. This might be to introduce yourself in a job search context, to propose a business collaboration, or to establish a new professional relationship. Be specific about why you’re contacting this particular individual or organization.
Background Information
Provide a concise overview of your professional background relevant to the purpose of your letter. This could include your current job, professional journey, or key areas of expertise. The aim is to give the reader context about your professional standing.
Relevant Accomplishments
Highlight significant achievements that are pertinent to the recipient. These could be successful projects you’ve led, awards you’ve won, or specific contributions you’ve made in previous roles. The objective is to showcase your competence and success in areas relevant to the letter’s purpose.
Personal Qualities
Share personal attributes that make you well-suited for the intended purpose of your letter. For instance, you might emphasize qualities like leadership, innovation, or collaborative skills if you are applying for a job. This part is about showing your personality and fit.
Call to Action
This is a crucial component where you suggest the next steps. It could be a request for a follow-up meeting, a phone call, or an invitation to review your application. Make it clear what you want the recipient to do next.
Conclude your letter with a formal and professional closing. Common closings include “Sincerely”, “Best regards”, or “Kind regards”, followed by your full name. This part signifies the end of your letter respectfully.
Attachments
If you include additional documents, such as a resume or portfolio, mention them here. For example, “Enclosed, please find my resume, which provides further details about my professional experience.”
What Not to Include in a Letter of Introduction
When writing a letter of introduction, it’s important to be aware of certain elements that should be avoided.
Here are what not to include:
Unsubstantiated Claims
Your letter should avoid making broad statements about your abilities or achievements without providing specific examples or evidence to support them. For instance, rather than simply stating that you’re an excellent communicator, provide a brief example or mention a relevant accomplishment demonstrating this skill. The goal is to be as concrete and specific as possible to build credibility.
Clichés and Overused Phrases
Avoid overused phrases and clichés that don’t add substantive information to your introduction. Phrases like “team player,” “hard worker,” or “go-getter” are commonly used and don’t distinguish you from other candidates. Instead, use unique descriptions specifically tailored to your experiences and qualifications.
Unrealistic Promises
Be cautious about making promises or commitments that you might not be able to fulfill. Overpromising to impress can backfire if you cannot deliver on those promises later. It’s important to be honest and realistic about what you can offer to the potential employer or contact.
Best Practices for Writing Letters of Introduction
When writing a letter of introduction, following these best practices can greatly enhance the effectiveness and professional impact of your letter:
Tailoring the Letter to the Audience
By researching and familiarizing yourself with the recipient’s work and organization, you can ensure that your letter speaks directly to their needs and interests. Personalization in the letter demonstrates that you have taken the time to understand who they are and what they value, which can significantly increase the effectiveness of your message.
Keeping It Concise and Focused
An effective letter conveys your message in a clear, succinct manner. Long letters can dilute the impact of your key points and lose the reader’s interest.
Structuring your letter with a clear beginning, middle, and end helps maintain this focus. The introduction should grab attention, the body should elaborate on your purpose and relevant qualifications, and the conclusion should reiterate your intent and suggest the next steps.
Showcasing Personality and Authenticity
An impactful letter is about what you say and how you say it. Infusing your letter with genuine personality and authenticity makes your message resonate more with the recipient. It’s about striking the right balance between professional decorum and personal touch.
Sharing your motivations, interests, or perspectives in a way that aligns with the professional context can make your letter memorable and establish a more personal connection with the recipient.
Proofreading for Clarity and Professionalism
The final yet crucial step in drafting your letter is thorough proofreading. This step is imperative for ensuring your letter is free from grammatical errors and typos and communicates your message.
A well-written and professionally presented letter reflects your attention to detail and commitment to quality. Having someone else review your letter is often beneficial, as a fresh pair of eyes can catch errors and provide feedback on your message’s overall clarity and tone.

About the Author
Read more articles by Priya Jain
CS50: Introduction to Computer Science
An introduction to the intellectual enterprises of computer science and the art of programming.
Associated Schools

Harvard School of Engineering and Applied Sciences
What you'll learn.
A broad and robust understanding of computer science and programming
How to think algorithmically and solve programming problems efficiently
Concepts like abstraction, algorithms, data structures, encapsulation, resource management, security, software engineering, and web development
Familiarity with a number of languages, including C, Python, SQL, and JavaScript plus CSS and HTML
How to engage with a vibrant community of like-minded learners from all levels of experience
How to develop and present a final programming project to your peers
Course description
This is CS50x , Harvard University's introduction to the intellectual enterprises of computer science and the art of programming for majors and non-majors alike, with or without prior programming experience. An entry-level course taught by David J. Malan, CS50x teaches students how to think algorithmically and solve problems efficiently. Topics include abstraction, algorithms, data structures, encapsulation, resource management, security, software engineering, and web development. Languages include C, Python, SQL, and JavaScript plus CSS and HTML. Problem sets inspired by real-world domains of biology, cryptography, finance, forensics, and gaming. The on-campus version of CS50x , CS50, is Harvard's largest course.
Students who earn a satisfactory score on 9 problem sets (i.e., programming assignments) and a final project are eligible for a certificate. This is a self-paced course–you may take CS50x on your own schedule.
Instructors

David J. Malan

You may also like

CS50's Understanding Technology
This is CS50’s introduction to technology for students who don’t (yet!) consider themselves computer persons.

CS50 for Lawyers
This course is a variant of Harvard University's introduction to computer science, CS50, designed especially for lawyers (and law students).
Using Python for Research
Take your introductory knowledge of Python programming to the next level and learn how to use Python 3 for your research.
Join our list to learn more
Explore Jobs
- Jobs Near Me
- Remote Jobs
- Full Time Jobs
- Part Time Jobs
- Entry Level Jobs
- Work From Home Jobs
Find Specific Jobs
- $15 Per Hour Jobs
- $20 Per Hour Jobs
- Hiring Immediately Jobs
- High School Jobs
- H1b Visa Jobs
Explore Careers
- Business And Financial
- Architecture And Engineering
- Computer And Mathematical
Explore Professions
- What They Do
- Certifications
- Demographics
Best Companies
- Health Care
- Fortune 500
Explore Companies
- CEO And Executies
- Resume Builder
- Career Advice
- Explore Majors
- Questions And Answers
- Interview Questions
How To Introduce Yourself Professionally (With Examples)
- How To Introduce Yourself Professionally
- Welcome New Employee Announcement
- Welcome Letter
- Thank You Note To Colleague
- 30/60/90 Plan
- Getting To Know You Questions
- Job Satisfaction
- Team Building Activities
- At Will Employment
- Company Culture
- Corporate Culture
- How To Succeed At Your New Remote Job
- How To Prepare For New Job Orientation
- How To Create An Employee Handbook
Find a Job You Really Want In
It’s important to know how to introduce yourself professionally, as a solid introduction leads to further connection. Whether you’re preparing for a career fair, interview, or sales call, it’s important to practice your self-introduction.
In this article, we’ll cover how to introduce yourself professionally, and we’ll give examples of introductions. We’ll also explain why it’s essential to have a professional introduction ready to go.
Key Takeaways:
Whether you’re sitting down for an interview, meeting a new coworker, or giving a presentation, your self-introduction is the first glimpse into the kind of person that you are.
When introducing yourself, you need to consider the context of the meeting.
Make sure you are using positive body language such as eye contact and smiling and are being an active listener.
When introducing yourself, make sure you are confident because confidence draws people into what you have to say.
How to introduce yourself professionally
How to introduce yourself examples, why are professional introductions important, tips for introducing yourself, job interview self-introduction tips, introducing yourself professionally faqs, expert opinion on introducing yourself professionally.
- Sign Up For More Advice and Jobs
To introduce yourself professionally, you need to consider the situation you’re in, use positive body language, and briefly provide information about who you are. If appropriate, ask questions of the person or people you’re introducing yourself to as well.
Consider the context of the introduction. Adapting your self-introduction to the situation you’re in is imperative. An introduction that is professional at a presentation will seem strange at a job interview .
Additionally, speaking as casually as you might on a first date is inappropriate when interviewing for an open position.
Before speaking, the first step is to understand the context of the scenario you’ll be introducing yourself in and adjust your approach accordingly.
Job interviews The first day of a college class Welcoming new co-workers Meeting people at a job fair or conference Giving a presentation to a large group Conducting a sales call
Use positive body language. People are strongly influenced by body language , even if they don’t realize it consciously. Using positive body language draws the other party into what you have to say and who you are.
Eye contact Shaking hands Smiling Nodding Standing upright Arms uncrossed
Give a little information about who you are. The thing about an effective introduction is that it’s a push-and-pull in exchange for information. Spend equal time speaking and listening .
In the case of a job interview, this means briefly explaining your professional background while highlighting your responsibilities and achievements . Explain what jobs you’ve worked in previously and what the responsibilities in those roles entailed.
When you’re introducing yourself in a social situation, it’s okay to include some career-related information, but try to extend the description past that to give a more well-rounded depiction of who you are.
Ask questions. It’s not an attractive quality to be self-absorbed, whether in a professional or social setting. One way to avoid this perception is by asking the other person questions about themselves, the position you’re applying for, or the company you hope to work for.
Questions demonstrate a genuine interest in the other person or professional role, and that makes them respond more positively.
Asking questions also helps the interaction flow naturally from an introduction to a relaxed conversation .
What do you like about working here? What are the biggest challenges I’d be facing in this position? What are you most looking forward to about this conference? What do you do?
Presenting yourself professionally and politely is important no matter the context. Here are some examples of how to do this in a wide variety of situations:
How to introduce yourself in an interview for a job
“Hello, it’s nice to finally meet you in person. Even though we spoke over email, I wanted to formally introduce myself. My name is Sally Jones, and I’m a passionate social media manager . “I’ve been a professional social media manager for the past five years after graduating with my bachelor’s degree in communications from New York University. I’ve led teams that handled high-profile clients and improved their sales margins by upwards of 4%. “I’ve always admired your organization’s mission, and I’d love to be able to use my leadership skills and industry knowledge to further it.”
How to introduce yourself to a new employee
“Hi, my name is Connor. What’s your name? Nice to meet you, _____. I understand that you’ve recently been hired for the job of administrative assistant , which means that we’ll be working together a lot. “I just wanted to introduce myself and extend a warm welcome to the team. “Please let me know if there’s anything I can help you with while you’re getting adjusted to the new role.”
How to introduce yourself in an email
Dear Mrs. Adams, How are you doing? I hope this email finds you well. My name is Jackson King, and I’m a school librarian . I have ten years of experience working as a librarian in the public schooling system, which has awarded me strengths in collaboration and patience. I’m emailing you today because I know that you are the hiring manager for Woodbridge City School District, and I wanted to pass my resume along in case any positions open up that fit my experience and skills. I’d love to have a further discussion about the education philosophies at Woodbridge City School District. I can be reached via [email protected] or (923-742-6336). Thank you for reading my email in full, and I hope to hear back soon. Sincerely, Jackson King [email protected]
How to introduce yourself at a hiring event
“Hi there, how are you? My name is Matthew Shelton. I’m a recent graduate from the University of Texas with a degree in engineering. While I haven’t had much paid professional experience, I participated in a competitive internship with Cisco Systems for six months. “I wanted to come over and introduce myself to you because I saw that you’re representing Flash Energy Solutions. I’ve heard incredible things about this company’s innovation, and I’m curious to find out more about their open positions. Are you available now to talk more about opportunities at Flash Energy Solutions?”
How to introduce yourself to a university professor
“Good afternoon, Professor Johnson. My name is Abigal Morris, and I’m a sophomore here at The University of Washington. I just wanted to formally introduce myself and say I’m looking forward to learning more in your course this semester.”
How to introduce yourself to your network
Hi, Samantha. How are you? I hope all is well. My name is Jessica Lane, and I’m a gallery director for Elegance Art Studios. I’m reaching out to you today because I recently came across some of your artwork online. Specifically, I saw a painting titled “Oblivion” that I thought was immaculate. I’d like to see your other work and speak further about the possibility of building a working relationship with Elegance Art Studios. If you’re interested, please email me at [email protected] or call me at (558)-292-6868. Thank you. Sincerely, Jessica Lane
How to introduce yourself on social media
Hello, Catherine, my name is Sadie Michaels, and I represent a clothing company called Free Air Designs as a marketing coordinator . I came across your Instagram profile while I was searching through my Top Posts page . I think you have a keen eye for social media development, and I enjoy your style. I was wondering if you’d be interested in collaborating on a few targeted posts involving Free Air Designs. Let me know if you’d be interested in talking more. Thanks! -Sadie
How to introduce yourself to a stranger on a plane
“Hello, I don’t mean to bother you, but since we’re going to be on this 12-hour flight, I figured I’d introduce myself. I’m Tom. What’s your name? It’s a pleasure, ____. What brings you on a flight to Milan?”
How to introduce yourself at an office party
“I don’t think we’ve met before. My name is Eric. I work in accounting. What’s your name? Awesome, it’s great to meet you, ____. How long have you been working here? Eight years? Wow, I’ve only been here for two. Have you been at this location all along?”
How to introduce yourself in class
“Hi everyone, my name’s Madeline Johnson. I’m a sophomore English major in the NEAG education program. I was interested in this class as a way of broadening my knowledge of teaching techniques for toddlers. When I’m not stuck in a book, I like to spend my time fishing at the Housatonic River.”
How to introduce yourself in a letter
Dear Mrs. Sels, “My name is John Buck and I’m a freelance writer with a background in e-commerce and the technical space. Naturally, I thought I’d be a good fit for XYZ Technica, an industry leader in technical e-commerce.”
How to introduce yourself to a group
“Hello everyone, my name’s Tim Thompson. I’ve been working in finance for 10 years, and what I specialize in is client support and education. Being able to bring some of this esoteric, but important, information from our field to more people is the most rewarding part of my job.”
How to introduce yourself in a meeting or presentation
“Hi everyone, my name is Riley Cooper and I’m the head of our content marketing team. What we excel at is making bespoke content calendars that match your brand’s voice, as well as monitoring the success of those campaigns.”
How to introduce yourself to a potential new client
Hello, my name is Chris Trager, and I’m a representative for Campbell Paper. I wanted to introduce myself and let you know about our 30% off sale happening throughout the month of August. We provide high-quality paper products and custom-printed materials to many schools like yours, and I’d love to discuss how we can meet your paper and printing needs. Is there anything in particular you’re looking for for an upcoming project? I really enjoy working with education-based clients like you, and I’d love to send you a sample book and help you find solutions at a price point that works for you. Please feel free to respond to this email or call or text me at 333-444-5555. I look forward to talking with you. Chris Traeger Sales Representative Campbell Paper
How to introduce yourself in a new company
Good morning, Ashley, We haven’t met yet, but I’m the new graphic designer working in the marketing department, and I was assigned your ESL class poster. Would you mind sending me the class times whenever you get the chance? Once I have those, I’ll be ready to send the poster to you to look over. I’m looking forward to working with you, and I hope to be able to meet you in person soon! Thanks, Caleb Olson Graphic Designer 222-333-4455
Professional introductions are important because how you demonstrate your character in the first moments of meeting another person dictates their perception of you moving forward, even if that doesn’t accurately describe who you are .
In situations where there is limited time to interact, such as a job interview, making a positive and professional first impression is crucial in achieving a desirable outcome. The confines of a 30-minute interview are all a candidate has to demonstrate themselves as the perfect choice for a job.
This is truly a test of first impressions as job-seekers are asked to perform well in a brief introduction before being hired.
Making a strong self-introduction is more complicated than simply stating your name and shaking hands. Consider the following tips for introducing yourself to leave a lasting positive impression on people you meet:
Dress well . Clothing is the first impression that a job interviewer or colleague has of you before you speak. Dressing well for a professional event ensures that you’re portraying yourself in a professional light.
Be confident. Refined confidence draws people into what you have to say. While sounding conceited repeals most people, a healthy dose of security in your ability to do a job establishes you as a dependable candidate.
Look for opportunities to further the conversation. An introduction that goes back and forth between two people only lasts a few minutes at most before it gets boring. To avoid a boring discussion, be on the lookout for opportunities to further the conversation.
Understand the culture. Before an interview or meeting, you should do research on the company to understand its culture. This will give you a better understanding of whether they are more straightforward or more casual.
If they are more casual, you can include some light humor in your introduction, just make sure it’s appropriate. If they are more straightforward and formal, keep a professional demeanor.
Prepare what you want to say. Practicing how you want to say something can help with stumbling over words and possibly saying something wrong. Try writing down what you want to say beforehand and practicing what you want to say. It may seem silly to be doing so at the time, but it could be helpful if you are nervous and have new meeting anxiety.
Introducing yourself at a job interview is a bit different than in most social contexts. You’ll want to pay special attention to the following in order to ensure the hiring manager likes you from the get-go:
Research the company. Before the interview, check out how the company presents itself to the public via social media. Are they casual and hip, or formal and serious? That’s your first clue for what sort of tone to strike.
Research the interviewer. Figure out whether the interviewer is an HR representative or someone who you’d be working under directly. You can also learn about their background to see what sort of information they’re most likely to appreciate in an introduction.
Plus, you might find an interesting connection that can be a nice segue out of your self-introduction into a shared, natural conversation.
Be hyper-relevant and brief. The job description is your ultimate cheat sheet for which qualifications to hype up as you introduce yourself at your job interview. Don’t go crazy trying to stuff the whole list into your intro, though.
Talk contributions. Introducing yourself shouldn’t be a laundry list of where you worked, when you graduated, etc. — that’s what your resume is for . Instead, get animated and share why you’re passionate about the field, interesting stories from your background, major milestones from your professional career, etc.
Don’t stop at your job title. When you simply give your name and job title, you’re basically saying, “There’s nothing more interesting about me than the function I can possibly fulfill” — not exactly a thrilling candidate.
Don’t try too hard to be funny. Humor is a great thing, but unless you’re a stand-up, you should wait until you’ve developed a bit of rapport before diving into too many jokes. No matter how much research you’ve done on your interviewer, you won’t know what they find funny or inappropriate, so it’s best to play it safe.
How do I introduce myself professionally?
Introduce yourself professionally with positive body language and relevant information about yourself. This relevant information about yourself should be related to the context of the situation. For example, if you are introducing yourself to someone once you have been referred, you may bring up your reference.
What is a unique way to introduce yourself?
To be unique, talk about your values in your introduction. Your values, even if they are common, define your personality. This helps you set the stage to talk about your goals and accomplishments, which should be tied to your values. Just make sure to keep them relevant and appropriate.
How do you introduce yourself in 3 lines?
To introduce yourself in 3 lines: state your name, why you are there, and ask an open-ended question about the other person. It is especially important to explain your purpose in a natural way, so tie it back to the context of the situation. Then, by using an open-ended question, you provide an opportunity for the other person to contribute to the conversation in a meaningful way.
What is a good introduction?
A good introduction should gain attention and interest in a positive manner. You will have introduced yourself successfully because people will be curious to learn more about you. This creates a flow to whatever topic is at hand while keeping your presence relevant.
How do you start an introduction to introduce yourself?
To start an introduction when introducing yourself, greet the person, give your name, and share a little bit about yourself. This information will change depending on the context. In a job interview, for example, you’ll give a quick overview of your experience or skills, while at a professional conference, you’ll share your job title.
How To Introduce Yourself Professionally?

Amanda Halkiotis Owner and Chief Resume Writer
If you have a hard time thinking of ways to break the ice over email, you can always ask those close to you how you come across to others. Are you funny? Charming? Outgoing? Sincere? Good-natured and kind? Find a characteristic that resonates with you and use it to brand yourself. If you are looking for a financial services job at a fintech firm, for example, a great opening line might be something like, “I have been a math geek my whole life and I started building computers when I was in high school.”. The first line is key to getting the reader interested, so I cannot stress enough the importance of having a “hook” that makes you stand out as an individual.
When introducing yourself personally, manners and confidence matter. Make eye contact and stand up straight, but try to be relaxed and not too stiff. I also recommend being complimentary but a bit subtle about it, for example, saying, “Thank you so much for meeting with me today” followed by, “Your office is such a lovely building” or “I knew we would have a lot in common when we talked based on our email exchange”. A little flattery goes a long way! I like to have three to five points about myself memorized when meeting someone for the first time in an interview setting. Something biographical, something personal, and something professional. So, for me, if someone says, “ Tell me about yourself “, I can reply with, “I grew up in Connecticut and have been in New York City for 14 years, I’m a middle child, I love to travel, cooking, and hiking, I am not afraid of a challenge and I find that I do my best work when I get to work with clients and build relationships”. To sum it up, have an elevator pitch to go along with the brand you promoted over email!
For anyone who gets nervous meeting new people, I suggest practicing in front of a mirror or doing mock interviews with a friend or relative. For virtual interviews (so many are being done on Zoom these days), you can do a mock version by doing a video recording on your phone and looking it over. A few minutes before the actual interview, try a technique called box breathing to calm your nerves.
Lastly, one of my personal heroes who is a true master when it comes to this type of advice is Vanessa Van Edwards. She is a well-known human behaviorist who has been featured on the Today Show, has done a Ted Talk, and has a great YouTube channel. Trust me, you’ll love her.
Harvard Business Review – A Simple Way To Introduce Yourself
Western Michigan University – Introduce Yourself With A Personal Commercial
Yale University – Office of Career Strategy
How useful was this post?
Click on a star to rate it!
Average rating / 5. Vote count:
No votes so far! Be the first to rate this post.

Chris Kolmar is a co-founder of Zippia and the editor-in-chief of the Zippia career advice blog. He has hired over 50 people in his career, been hired five times, and wants to help you land your next job. His research has been featured on the New York Times, Thrillist, VOX, The Atlantic, and a host of local news. More recently, he's been quoted on USA Today, BusinessInsider, and CNBC.
Recent Job Searches
- Registered Nurse Jobs Resume Location
- Truck Driver Jobs Resume Location
- Call Center Representative Jobs Resume Location
- Customer Service Representative Jobs Resume
- Delivery Driver Jobs Resume Location
- Warehouse Worker Jobs Resume Location
- Account Executive Jobs Resume Location
- Sales Associate Jobs Resume Location
- Licensed Practical Nurse Jobs Resume Location
- Company Driver Jobs Resume
Related posts
How To Find A Mentor (With Examples)

The Best April Fools Pranks & Practical Jokes to Use at Work

Why You Should Take A Mental Health Day

Compressed Work Week: What Is It? (With Examples)
- Career Advice >
- Life At Work >
- Introduce Yourself Professionally
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
Methodology
- How to Write a Literature Review | Guide, Examples, & Templates
How to Write a Literature Review | Guide, Examples, & Templates
Published on January 2, 2023 by Shona McCombes . Revised on September 11, 2023.
What is a literature review? A literature review is a survey of scholarly sources on a specific topic. It provides an overview of current knowledge, allowing you to identify relevant theories, methods, and gaps in the existing research that you can later apply to your paper, thesis, or dissertation topic .
There are five key steps to writing a literature review:
- Search for relevant literature
- Evaluate sources
- Identify themes, debates, and gaps
- Outline the structure
- Write your literature review
A good literature review doesn’t just summarize sources—it analyzes, synthesizes , and critically evaluates to give a clear picture of the state of knowledge on the subject.
Instantly correct all language mistakes in your text
Upload your document to correct all your mistakes in minutes

Table of contents
What is the purpose of a literature review, examples of literature reviews, step 1 – search for relevant literature, step 2 – evaluate and select sources, step 3 – identify themes, debates, and gaps, step 4 – outline your literature review’s structure, step 5 – write your literature review, free lecture slides, other interesting articles, frequently asked questions, introduction.
- Quick Run-through
- Step 1 & 2
When you write a thesis , dissertation , or research paper , you will likely have to conduct a literature review to situate your research within existing knowledge. The literature review gives you a chance to:
- Demonstrate your familiarity with the topic and its scholarly context
- Develop a theoretical framework and methodology for your research
- Position your work in relation to other researchers and theorists
- Show how your research addresses a gap or contributes to a debate
- Evaluate the current state of research and demonstrate your knowledge of the scholarly debates around your topic.
Writing literature reviews is a particularly important skill if you want to apply for graduate school or pursue a career in research. We’ve written a step-by-step guide that you can follow below.
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
Writing literature reviews can be quite challenging! A good starting point could be to look at some examples, depending on what kind of literature review you’d like to write.
- Example literature review #1: “Why Do People Migrate? A Review of the Theoretical Literature” ( Theoretical literature review about the development of economic migration theory from the 1950s to today.)
- Example literature review #2: “Literature review as a research methodology: An overview and guidelines” ( Methodological literature review about interdisciplinary knowledge acquisition and production.)
- Example literature review #3: “The Use of Technology in English Language Learning: A Literature Review” ( Thematic literature review about the effects of technology on language acquisition.)
- Example literature review #4: “Learners’ Listening Comprehension Difficulties in English Language Learning: A Literature Review” ( Chronological literature review about how the concept of listening skills has changed over time.)
You can also check out our templates with literature review examples and sample outlines at the links below.
Download Word doc Download Google doc
Before you begin searching for literature, you need a clearly defined topic .
If you are writing the literature review section of a dissertation or research paper, you will search for literature related to your research problem and questions .
Make a list of keywords
Start by creating a list of keywords related to your research question. Include each of the key concepts or variables you’re interested in, and list any synonyms and related terms. You can add to this list as you discover new keywords in the process of your literature search.
- Social media, Facebook, Instagram, Twitter, Snapchat, TikTok
- Body image, self-perception, self-esteem, mental health
- Generation Z, teenagers, adolescents, youth
Search for relevant sources
Use your keywords to begin searching for sources. Some useful databases to search for journals and articles include:
- Your university’s library catalogue
- Google Scholar
- Project Muse (humanities and social sciences)
- Medline (life sciences and biomedicine)
- EconLit (economics)
- Inspec (physics, engineering and computer science)
You can also use boolean operators to help narrow down your search.
Make sure to read the abstract to find out whether an article is relevant to your question. When you find a useful book or article, you can check the bibliography to find other relevant sources.
You likely won’t be able to read absolutely everything that has been written on your topic, so it will be necessary to evaluate which sources are most relevant to your research question.
For each publication, ask yourself:
- What question or problem is the author addressing?
- What are the key concepts and how are they defined?
- What are the key theories, models, and methods?
- Does the research use established frameworks or take an innovative approach?
- What are the results and conclusions of the study?
- How does the publication relate to other literature in the field? Does it confirm, add to, or challenge established knowledge?
- What are the strengths and weaknesses of the research?
Make sure the sources you use are credible , and make sure you read any landmark studies and major theories in your field of research.
You can use our template to summarize and evaluate sources you’re thinking about using. Click on either button below to download.
Take notes and cite your sources
As you read, you should also begin the writing process. Take notes that you can later incorporate into the text of your literature review.
It is important to keep track of your sources with citations to avoid plagiarism . It can be helpful to make an annotated bibliography , where you compile full citation information and write a paragraph of summary and analysis for each source. This helps you remember what you read and saves time later in the process.
Prevent plagiarism. Run a free check.
To begin organizing your literature review’s argument and structure, be sure you understand the connections and relationships between the sources you’ve read. Based on your reading and notes, you can look for:
- Trends and patterns (in theory, method or results): do certain approaches become more or less popular over time?
- Themes: what questions or concepts recur across the literature?
- Debates, conflicts and contradictions: where do sources disagree?
- Pivotal publications: are there any influential theories or studies that changed the direction of the field?
- Gaps: what is missing from the literature? Are there weaknesses that need to be addressed?
This step will help you work out the structure of your literature review and (if applicable) show how your own research will contribute to existing knowledge.
- Most research has focused on young women.
- There is an increasing interest in the visual aspects of social media.
- But there is still a lack of robust research on highly visual platforms like Instagram and Snapchat—this is a gap that you could address in your own research.
There are various approaches to organizing the body of a literature review. Depending on the length of your literature review, you can combine several of these strategies (for example, your overall structure might be thematic, but each theme is discussed chronologically).
Chronological
The simplest approach is to trace the development of the topic over time. However, if you choose this strategy, be careful to avoid simply listing and summarizing sources in order.
Try to analyze patterns, turning points and key debates that have shaped the direction of the field. Give your interpretation of how and why certain developments occurred.
If you have found some recurring central themes, you can organize your literature review into subsections that address different aspects of the topic.
For example, if you are reviewing literature about inequalities in migrant health outcomes, key themes might include healthcare policy, language barriers, cultural attitudes, legal status, and economic access.
Methodological
If you draw your sources from different disciplines or fields that use a variety of research methods , you might want to compare the results and conclusions that emerge from different approaches. For example:
- Look at what results have emerged in qualitative versus quantitative research
- Discuss how the topic has been approached by empirical versus theoretical scholarship
- Divide the literature into sociological, historical, and cultural sources
Theoretical
A literature review is often the foundation for a theoretical framework . You can use it to discuss various theories, models, and definitions of key concepts.
You might argue for the relevance of a specific theoretical approach, or combine various theoretical concepts to create a framework for your research.
Like any other academic text , your literature review should have an introduction , a main body, and a conclusion . What you include in each depends on the objective of your literature review.
The introduction should clearly establish the focus and purpose of the literature review.
Depending on the length of your literature review, you might want to divide the body into subsections. You can use a subheading for each theme, time period, or methodological approach.
As you write, you can follow these tips:
- Summarize and synthesize: give an overview of the main points of each source and combine them into a coherent whole
- Analyze and interpret: don’t just paraphrase other researchers — add your own interpretations where possible, discussing the significance of findings in relation to the literature as a whole
- Critically evaluate: mention the strengths and weaknesses of your sources
- Write in well-structured paragraphs: use transition words and topic sentences to draw connections, comparisons and contrasts
In the conclusion, you should summarize the key findings you have taken from the literature and emphasize their significance.
When you’ve finished writing and revising your literature review, don’t forget to proofread thoroughly before submitting. Not a language expert? Check out Scribbr’s professional proofreading services !
This article has been adapted into lecture slides that you can use to teach your students about writing a literature review.
Scribbr slides are free to use, customize, and distribute for educational purposes.
Open Google Slides Download PowerPoint
If you want to know more about the research process , methodology , research bias , or statistics , make sure to check out some of our other articles with explanations and examples.
- Sampling methods
- Simple random sampling
- Stratified sampling
- Cluster sampling
- Likert scales
- Reproducibility
Statistics
- Null hypothesis
- Statistical power
- Probability distribution
- Effect size
- Poisson distribution
Research bias
- Optimism bias
- Cognitive bias
- Implicit bias
- Hawthorne effect
- Anchoring bias
- Explicit bias
A literature review is a survey of scholarly sources (such as books, journal articles, and theses) related to a specific topic or research question .
It is often written as part of a thesis, dissertation , or research paper , in order to situate your work in relation to existing knowledge.
There are several reasons to conduct a literature review at the beginning of a research project:
- To familiarize yourself with the current state of knowledge on your topic
- To ensure that you’re not just repeating what others have already done
- To identify gaps in knowledge and unresolved problems that your research can address
- To develop your theoretical framework and methodology
- To provide an overview of the key findings and debates on the topic
Writing the literature review shows your reader how your work relates to existing research and what new insights it will contribute.
The literature review usually comes near the beginning of your thesis or dissertation . After the introduction , it grounds your research in a scholarly field and leads directly to your theoretical framework or methodology .
A literature review is a survey of credible sources on a topic, often used in dissertations , theses, and research papers . Literature reviews give an overview of knowledge on a subject, helping you identify relevant theories and methods, as well as gaps in existing research. Literature reviews are set up similarly to other academic texts , with an introduction , a main body, and a conclusion .
An annotated bibliography is a list of source references that has a short description (called an annotation ) for each of the sources. It is often assigned as part of the research process for a paper .
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
McCombes, S. (2023, September 11). How to Write a Literature Review | Guide, Examples, & Templates. Scribbr. Retrieved June 10, 2024, from https://www.scribbr.com/dissertation/literature-review/
Is this article helpful?
Shona McCombes
Other students also liked, what is a theoretical framework | guide to organizing, what is a research methodology | steps & tips, how to write a research proposal | examples & templates, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”
- Data center hardware and strategy
The worlds of IT and OT are converging. Advances in technologies, such as the internet of things and big data analytics, are systematically enabling the digital information world to see, understand and influence the physical operational world. When implemented properly, IT/OT convergence can merge business processes, insights and controls into a single uniform environment. Use this guide to learn more about IT/OT convergence, its benefits and challenges, plus industry examples, use cases and more.
Information technology (it).

- Kinza Yasar, Technical Writer
What is information technology?
Information technology (IT) is the use of computers, storage, networking and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data. Typically, IT is used in the context of business operations, as opposed to the technology used for personal or entertainment purposes. The commercial use of IT encompasses both computer technology and telecommunications .
Harvard Business Review coined the term information technology in 1958 to distinguish between purpose-built machines designed to perform a limited scope of functions and general-purpose computing machines that could be programmed for various tasks. As the IT industry evolved from the mid-20th century, computing capability increased, while device cost and energy consumption decreased, a cycle that continues today when new technologies emerge.
Types of information technology
Information technology encompasses a wide range of technologies and systems that are used to store, retrieve, process and transmit data for specific use cases.
Common information technology types include the following:
- Internet and web technologies. This includes the tools and protocols used to access, navigate and interact with information on the internet. Examples include web browsers, websites, web servers, Hypertext Markup Language , cascading style sheets , JavaScript , HTTP and other internet-related technologies.
- Cloud computing. This involves the delivery of computing resources and services over the internet on a pay-per-use basis. This can include infrastructure as a service , platform as a service, software as a service and cloud storage options.
- Databases. This includes IT systems and software used to store, organize and retrieve data. Examples include MySQL , NoSQL , relational database management systems and MongoDB .
- Artificial intelligence and machine learning. AI and ML-based IT technologies use algorithms and statistical models to enable computers to perform tasks that typically require human intelligence. Examples include speech recognition, image recognition and natural language processing .
- Cybersecurity. This type of IT includes technologies and best practices designed to protect IT systems , networks and data from unauthorized access, cyber attacks and other security threats. Cybersecurity can be enforced through firewalls, antivirus software, encryption , intrusion detection systems and security policies.
- Internet of things. This includes the network of interconnected devices and sensors that collect, exchange and analyze data. IoT technologies enable the integration of physical objects into computer systems, providing automation, monitoring and control in various domains.
- IT governance. This involves making policies and rules for the organization to ensure effective operation.
- Data analytics and business intelligence. BI focuses on tools and techniques for extracting insights from large data sets to support decision-making and business operations. This can include data mining , statistical analysis, data visualization and predictive modeling .
What does information technology encompass?
The IT department ensures that the organization's systems, networks, applications, data and information all connect and function properly. The IT team handles the following three major areas:
This article is part of
What is IT/OT convergence? Everything you need to know
- Which also includes:
- Benefits and challenges of IT/OT convergence
- Understand the best IT/OT convergence strategies
- 5 ways to facilitate the convergence of IT and OT in IoT
- Deploying and maintaining business applications, services and infrastructure -- including servers, networks and storage.
- Monitoring, optimizing and troubleshooting the performance of applications , services and infrastructure.
- Overseeing the security and governance of applications, services and infrastructure.
Most IT staff have different responsibilities within the team that can be broken into the following key areas:
- Administration. Administrators handle the day-to-day deployment, operation and monitoring of an IT environment, including systems, networks and applications. Admins often perform a range of other duties such as software upgrades, user training, software license management, procurement, security, data management and observing adherence to business process and compliance requirements. Effective delegation is also part of IT administration and is crucial for a team's productivity.
- Support. Help desk staff specialize in answering questions, gathering information and directing troubleshooting efforts for hardware and software. IT support often includes IT asset and change management, helping admins with procurement, handling backup and recovery of data and applications, monitoring and analyzing logs and other performance monitoring tools and following established support workflows and processes.
- Applications. Businesses rely on software to perform work. Some applications, such as email server applications, are procured and deployed by third parties. But many organizations retain a staff of skilled developers that create the applications and interfaces -- such as application programming interfaces -- needed to deliver critical business capabilities and services. Applications might be coded in a wide array of popular programming languages and integrated with other applications to create smooth and seamless interactions between different applications. Developers might also be tasked with creating interactive business websites and building mobile applications. The trend toward agile or continuous development paradigms requires developers to be increasingly involved with IT operations, such as deploying and monitoring applications.
- Compliance. Businesses are obligated to observe varied government and industry-driven regulatory requirements. IT staff play a major role in securing and monitoring access to business data and applications to ensure that such resources are used according to established business governance policy that meets regulatory requirements. Such staff are deeply involved with security tasks and routinely interact with legal and business teams to prevent, detect, investigate and report possible breaches.
Why is information technology important?
It's been said that data is what powers industries worldwide. That might be hyperbole, but few businesses -- large or small -- can remain competitive without the ability to collect data and turn it into useful information. IT provides the means to develop, process, analyze, exchange, store and secure information.
Data processing plays a significant role in the following core business practices:
- Product development and design.
- Marketing and market research.
- Sales and invoicing.
- Data analysis and decision-making.
- Customer development and retention.
- Accounting and taxes.
- Human resources and payroll.
- Regulatory compliance.
Information technology plays a vital role for businesses in the following ways:
- Facilitates communication and collaboration. IT enables seamless communication and collaboration across different locations and time zones. For example, global corporations that are spread across continents can use video conferencing, instant messaging and content collaboration tools to bridge geographical distances and communicate effectively.
- Advances pervasive computing. Computing has penetrated practically every part of business and much of our personal lives. The ubiquity of computing -- also referred to as pervasive computing -- is another reason why IT is critical. Computing devices have evolved well beyond PCs and servers. Today, all businesses and most people have and use multiple computing devices, including phones, tablets, laptops, game consoles and even doorbells, thermostats, vacuums and many kitchen appliances.
- Enhances efficiency and productivity. IT systems and tools streamline processes, automate repetitive tasks and provide access to real-time data, thereby improving the overall efficiency and productivity of businesses. For example, a retail company with an integrated IT system can use an automated inventory management tool to track stock levels in real time and replenish them through automatic reordering.
- Enables access to information. IT provides access to vast amounts of information and knowledge in databases and online libraries, empowering individuals and organizations to make informed decisions and stay updated with the latest developments.
- Supports innovation and creativity. IT fosters innovation by providing platforms for creative expression, experimentation and problem-solving. For example, consider a software development company utilizing IT platforms for innovation. Its developers can collaborate in virtual environments, experiment with new coding techniques and technologies and create groundbreaking software through iterative testing, feedback loops and problem-solving.
- Supports critical business operations. IT is essential for the smooth functioning of modern businesses, from managing operations and finances to marketing and customer service. For example, most customer service teams use IT systems for efficient communication, issue resolution and feedback collection to ensure a positive user experience.
- Helps with education and research. IT plays a vital role in education, providing access to educational resources, facilitating distance learning and supporting research endeavors. Remote learning technologies enable access to education from anywhere, bridging geographical barriers and providing opportunities for lifelong learning.
- Provides cost savings. IT reduces costs associated with paper-based processes, manual labor and physical infrastructure, leading to significant savings for both businesses and individuals.
- Provides connectivity to the internet. Virtually all IT devices, many of which are part of the IoT, tap into the internet, which interconnects billions of devices worldwide.
Examples of information technology
So how is IT involved in day-to-day business? Consider the following six common examples of IT and teams at work:
- Server upgrade. One or more data center servers are near the end of their operational and maintenance lifecycle. IT staff will perform the following:
- Select and procure replacement servers.
- Configure and deploy the new servers.
- Back up applications and data on existing servers.
- Transfer that data and applications to the new servers.
- Validate that the new servers are working properly.
- Repurpose or decommission and dispose of the old servers.
- Security monitoring. Businesses routinely use tools to monitor and log activity in applications, networks and systems. IT staff receive alerts of potential threats or noncompliant behavior, such as a user attempting to access a restricted file; check logs and other reporting tools to investigate and determine the root cause of the alert; take prompt action to address and remediate the threat, often driving changes and improvements to security posture that can prevent similar events in the future.
- New software. The business determines a need for a new mobile application that can enable customers to log in and access account information or conduct other transactions from smartphones and tablets. Developers work to create and refine a suitable application according to a planned roadmap. Operations staff post each iteration of the new mobile application for download and deploy the back-end components of the app to the organization's infrastructure.
- Business improvement. A business requires more availability from a critical application to help with revenue or business continuance strategies. The IT staff might be called upon to architect a high-availability cluster to provide greater performance and resilience for the application to ensure that it can continue to function in the face of single outages. This can be paired with enhancements to data storage protection and recovery.
- User support. Developers are building a major upgrade for a vital business application. Developers and admins collaborate to create new documentation for the upgrade. IT staff might deploy the upgrade for limited beta testing -- enabling a select group of users to try the new version -- while also developing and delivering comprehensive training that prepares all users for the new version's eventual release.
- Digital workplace organization. Employees in a bustling office are wasting too much time trying to locate paper documents, files and office supplies that are scattered throughout the workspace. The office has decided to incorporate a digital filing and inventory management system. Each document in the office is scanned and stored electronically and tagged with relevant keywords. Additionally, office supplies are also tracked in a digital inventory database. Now, whenever an employee needs to access a document or find a tool, they promptly open the digital inventory system. With just a quick search, they pinpoint the precise file or item along with its current physical location in the workspace. This enhances the efficiency and productivity of the employees.
Software vs. hardware
When it comes to IT systems, both software and hardware are integral and interdependent components of computer systems. The following are some main differences between the two:
Software refers to a set of instructions that enable the hardware to perform specific tasks. It includes system software, application software and other programs that run on the computer.
There are two categories of software: system software and applications. System software encompasses the computer programs that manage the basic computing functions. They include the following:
- Operating systems (OSes).
- Boot programs.
- Assemblers.
- Device drivers.
Examples of business applications include the following:
- Databases, such as Microsoft SQL Server.
- Transactional systems, such as real-time order entry.
- Email servers, such as Microsoft Exchange.
- Web servers, such as Apache and Microsoft's Internet Information Services.
- Customer relationship management, such as Oracle NetSuite and HubSpot.
- Enterprise resource planning systems, including SAP S/4HANA.
These applications use programmed instructions to manipulate, consolidate, disperse and otherwise work with data for a business purpose.
Mobile applications that run on smartphones, tablets and other portable devices typically connect with cloud or data center applications over the internet. These applications have expanded the scope of computing and created a new category of software and telecommunications that requires special expertise to maintain.
Hardware refers to the physical components of a computer that come in many different forms, including the monitor, servers, central processing unit, keyboard and mouse. Computer servers run business applications. Servers interact with client devices in the client-server model. They also communicate with other servers across computer networks, which typically link to the internet.
Storage is another type of hardware. It's any technology that holds information as data. Storage can be local on a specific server or shared among many servers, and it could be installed on-premises or accessed via a cloud service. Information that is stored can take many forms, including file, multimedia, telephony, and web and sensor data. Storage hardware includes volatile RAM (random-access memory) as well as non-volatile tape, hard disk drives and solid-state drives.
Telecom equipment -- comprising network interface cards , cabling, wireless communications and switching devices -- connects the hardware elements together and to external networks.
Abstracting hardware and software
Abstraction simplifies resource provisioning, management and scalability. By hiding the complexities of hardware, abstraction streamlines resource allocation, ensuring optimal utilization of available resources.
IT architectures have evolved to include virtualization and cloud computing, where physical resources are abstracted and pooled in different configurations to meet application requirements. Clouds can be distributed across locations and shared with other IT users, or they can be contained within a corporate data center or some combination of both deployments.
Volatility is a characteristic of virtualized resources, enabling them to expand and contract as needed. Subscription-based cloud or locally installed resources, such as storage or composable architectures, can spin up resources, such as servers, OSes and application software, as needed and then release them when processing is complete. Top of Form
Information technology vs. computer science
When researching careers in IT, one is likely to come across the term computer science . While there's an overlap between IT and computer science, the two disciplines are distinct and require different courses of study to prepare for careers.
IT is generally associated with the application of technology to deal with business issues. As such, the IT workforce is oriented toward developed technologies such as hardware systems, OSes and application software. Proficiency in IT is required to identify the hardware and software components that should be used to enhance a specific business process. IT pros work with a variety of technologies, such as server OSes, communications devices and software and applications. Career examples typically include roles such as database administrator , cybersecurity specialist and network administrator.
Preparation for an IT career requires basic courses in hardware and software systems. A bachelor's degree in IT and other programs might include the following subjects:
- Business analysis.
- Project management.
- Telecommunications.
- Network administration.
- Database design.
- Database management.
Computer science focuses on the logic and design of the underpinnings of the components that IT experts use to assemble business systems. A strong mathematics background is required to pursue a computer science career. Much of the work in computer science involves developing the algorithms and logic and writing low-level code that enables computer systems to address business problems.
Computer scientists might participate in the hardware and software engineering work required to develop products. They're also likely to delve into more abstract technologies, such as AI and ML. Roles in computer science include software developer, computer systems analyst, computer programmer and computer information research scientist.
A course of study in computer science requires a foundation in computer concepts and advanced mathematics. It could be complemented with the following subjects:
- Neural networks.
- Security systems.
- Data analytics.
- User experience.
Careers in information technology
A team of administrators and other technical staffers deploy and manage a company's IT infrastructure and assets. IT teams depend on a range of specialized information and technology skills and knowledge to support equipment, applications and activities. Third-party contractors and IT vendor support personnel augment the IT team.
The information technology profession is extremely diverse. IT workers can specialize in fields, including software development; application management; hardware components; server, storage or network administration and network architecture. Many businesses seek IT professionals with mixed or overlapping skill sets.
There's a wide array of IT careers, each with varying technological and managerial requisites. Among the most common IT job titles are the following:
- Chief information officer. A CIO is responsible for IT and computer systems that support the goals of the business.
- Chief technology officer. A CTO sets the technology goals and policies within an organization.
- IT director. An IT director is responsible for the functioning of the business's technology tools and processes. This role might also be called IT manager or IT leader.
- System administrator. A sys admin configures, manages, supports and troubleshoots a multiuser computing environment. Within a business, this role can be divided up by technology, requiring an administrator or team dedicated to server, desktop, network administration, virtualization or other components and technologies.
- Application manager. An application manager's role centers on the provisioning and management of a high-demand business application, such as Microsoft Exchange.
- Developer or software engineer. A software engineer or team writes, updates and tests code for computer programs to meet internal or customer-facing business objectives.
- Chief IT architect or IT architect. An IT architect examines and changes IT functions to best support the business.
- Information security analyst. An information security analyst protects organizations from threats and data breaches.
- Cloud engineer. A cloud engineer is responsible for managing and designing cloud-based systems for organizations.
IT skills and certifications
The U.S. Bureau of Labor Statistics projects a 15% growth in employment within the computer and information technology sector between now and 2032. A successful IT career will involve developing several technical skills. For the current IT job market, the following 10 skills are among those most in demand:
- Cybersecurity.
- Cloud computing.
- Edge computing and IoT.
- IT automation.
- Software development.
- Big data management and data analytics.
- Mobile application development.
In the pursuit of these fundamental IT disciplines, it's advantageous to earn certifications to demonstrate proficiency in specific technologies and areas of expertise. Some of the most highly regarded certifications offered by various technology vendors include the following:
- AWS Certified Solutions Architect -- Professional.
- CompTIA A+.
- Certified Ethical Hacker.
- Certified in Risk and Information Systems Control.
- Certified Information Security Manager.
- Certified Information Systems Security Professional.
- Cisco Certified Network Associate.
- Google Certified Professional Cloud Architect.
- Microsoft role-based certifications.
- Project Management Professional.
- VMware Certified Professional.
As reliance on cloud computing continues to grow, there's a significant demand for skilled cloud professionals. Delve into the top 10 cloud computing career paths and discover how to get started in this thriving field of information technology.
Continue Reading About information technology (IT)
- AI engineers: What they do and how to become one
- Best free DevOps certifications and training courses
- Cybersecurity market trends, from AI to post-quantum crypto
- How to conduct a cloud security assessment
- The best cloud security certifications for IT pros
Related Terms
Dig deeper on data center hardware and strategy.

web services

Server hardware guide: Architecture, products and management

cloud computing

blade server
Admins need all the help they can get, and this Microsoft utility shows IT how to correct security issues and optimize ...
Learn how to simplify user provisioning in the cloud collaboration platform with faster results by seeing examples of scripts ...
Automation is a good way for admins to handle all the tasks associated with removing a user from the organization's tenant in ...
Is it better to be 'first' or 'smart' in cloud? Compare the two strategies to determine which will help achieve your ...
Consistency and standardization are critical to a successful AWS tagging strategy. Consider these best practices to organize and ...
Serverless computing continues to grow in popularity to build modern applications. Evaluate the risks and rewards, as well as ...
As the focus for enterprise AI spreads beyond compute, Western Digital introduces a new SSD and HDD. It also released an AI ...
This HPE Discover 2024 conference guide will cover event news from June 17 to 20. There will be three new programs: edge and ...
Explore this updating guide on Dell Technologies World 2024. The show will shine a major spotlight on AI, but also cover topics ...
Dell Technologies World 2024 showcased hardware advancements to support AI and served as a launch for Apex AIOps, a rebranded ...
The best ESG and sustainability certification, workshop or course is the one that is right for you. Here are seven that work for ...
With so many carbon accounting software choices, buying teams may be overwhelmed. Start with this simplified guide to the ...
Page last updated : March 14, 2024
Ethereum Whitepaper
While several years old, we maintain this paper because it continues to serve as a useful reference and an accurate representation of Ethereum and its vision. To learn about the latest developments of Ethereum, and how changes to the protocol are made, we recommend this guide .
Researchers and academics seeking a historical or canonical version of the whitepaper [from December 2014] should use this PDF.
.css-1qbzvaj{transition-property:var(--eth-transition-property-common);transition-duration:var(--eth-transition-duration-fast);transition-timing-function:var(--eth-transition-easing-ease-out);cursor:pointer;-webkit-text-decoration:underline;text-decoration:underline;outline:2px solid transparent;outline-offset:2px;color:var(--eth-colors-primary-base);text-underline-offset:3px;position:absolute;right:100%;opacity:0;-webkit-transition:opacity 0.1s ease-in-out;transition:opacity 0.1s ease-in-out;}.css-1qbzvaj:hover,.css-1qbzvaj[data-hover]{-webkit-text-decoration:underline;text-decoration:underline;color:var(--eth-colors-primary-hover);}.css-1qbzvaj:focus-visible,.css-1qbzvaj[data-focus-visible]{box-shadow:var(--eth-shadows-none);outline:2px solid;outline-color:var(--eth-colors-primary-hover);outline-offset:2px;border-radius:var(--eth-radii-sm);}.css-1qbzvaj[data-inline-link]:visited{color:var(--eth-colors-primary-visited);}[role=group]:hover .css-1qbzvaj,[role=group][data-hover] .css-1qbzvaj,[data-group]:hover .css-1qbzvaj,[data-group][data-hover] .css-1qbzvaj,.group:hover .css-1qbzvaj,.group[data-hover] .css-1qbzvaj{opacity:1;}.css-1qbzvaj:focus,.css-1qbzvaj[data-focus]{opacity:1;} .css-1ff30mc{width:1em;height:1em;display:inline-block;line-height:1em;-webkit-flex-shrink:0;-ms-flex-negative:0;flex-shrink:0;color:currentColor;font-size:var(--eth-fontSizes-xl);-webkit-margin-end:var(--eth-space-1);margin-inline-end:var(--eth-space-1);} A Next-Generation Smart Contract and Decentralized Application Platform
Introduction to bitcoin and existing concepts.
The concept of decentralized digital currency, as well as alternative applications like property registries, has been around for decades. The anonymous e-cash protocols of the 1980s and the 1990s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. In 1998, Wei Dai's b-money (opens in a new tab) became the first proposal to introduce the idea of creating money through solving computational puzzles as well as decentralized consensus, but the proposal was scant on details as to how decentralized consensus could actually be implemented. In 2005, Hal Finney introduced a concept of " reusable proofs of work (opens in a new tab) ", a system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once again fell short of the ideal by relying on trusted computing as a backend. In 2009, a decentralized currency was for the first time implemented in practice by Satoshi Nakamoto, combining established primitives for managing ownership through public key cryptography with a consensus algorithm for keeping track of who owns coins, known as "proof-of-work".
The mechanism behind proof-of-work was a breakthrough in the space because it simultaneously solved two problems. First, it provided a simple and moderately effective consensus algorithm, allowing nodes in the network to collectively agree on a set of canonical updates to the state of the Bitcoin ledger. Second, it provided a mechanism for allowing free entry into the consensus process, solving the political problem of deciding who gets to influence the consensus, while simultaneously preventing sybil attacks. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Since then, an alternative approach has been proposed called proof-of-stake , calculating the weight of a node as being proportional to its currency holdings and not computational resources; the discussion of the relative merits of the two approaches is beyond the scope of this paper but it should be noted that both approaches can be used to serve as the backbone of a cryptocurrency.
Bitcoin As A State Transition System
From a technical standpoint, the ledger of a cryptocurrency such as Bitcoin can be thought of as a state transition system, where there is a "state" consisting of the ownership status of all existing bitcoins and a "state transition function" that takes a state and a transaction and outputs a new state which is the result. In a standard banking system, for example, the state is a balance sheet, a transaction is a request to move $X from A to B, and the state transition function reduces the value in A's account by $X and increases the value in B's account by $X. If A's account has less than $X in the first place, the state transition function returns an error. Hence, one can formally define:
In the banking system defined above:
The "state" in Bitcoin is the collection of all coins (technically, "unspent transaction outputs" or UTXO) that have been minted and not yet spent, with each UTXO having a denomination and an owner (defined by a 20-byte address which is essentially a cryptographic public key fn1 ). A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature produced by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be added to the state.
The state transition function APPLY(S,TX) -> S' can be defined roughly as follows:
- If the referenced UTXO is not in S , return an error.
- If the provided signature does not match the owner of the UTXO, return an error.
- If the sum of the denominations of all input UTXO is less than the sum of the denominations of all output UTXO, return an error.
- Return S with all input UTXO removed and all output UTXO added.
The first half of the first step prevents transaction senders from spending coins that do not exist, the second half of the first step prevents transaction senders from spending other people's coins, and the second step enforces conservation of value. In order to use this for payment, the protocol is as follows. Suppose Alice wants to send 11.7 BTC to Bob. First, Alice will look for a set of available UTXO that she owns that totals up to at least 11.7 BTC. Realistically, Alice will not be able to get exactly 11.7 BTC; say that the smallest she can get is 6+4+2=12. She then creates a transaction with those three inputs and two outputs. The first output will be 11.7 BTC with Bob's address as its owner, and the second output will be the remaining 0.3 BTC "change", with the owner being Alice herself.
If we had access to a trustworthy centralized service, this system would be trivial to implement; it could simply be coded exactly as described, using a centralized server's hard drive to keep track of the state. However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transaction system with a consensus system in order to ensure that everyone agrees on the order of transactions. Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks". The network is intended to produce roughly one block every ten minutes, with each block containing a timestamp, a nonce, a reference to (ie. hash of) the previous block and a list of all of the transactions that have taken place since the previous block. Over time, this creates a persistent, ever-growing, "blockchain" that constantly updates to represent the latest state of the Bitcoin ledger.
The algorithm for checking if a block is valid, expressed in this paradigm, is as follows:
- Check if the previous block referenced by the block exists and is valid.
- Check that the timestamp of the block is greater than that of the previous block fn2 and less than 2 hours into the future
- Check that the proof-of-work on the block is valid.
- Let S[0] be the state at the end of the previous block.
- Suppose TX is the block's transaction list with n transactions. For all i in 0...n-1 , set S[i+1] = APPLY(S[i],TX[i]) If any application returns an error, exit and return false.
- Return true, and register S[n] as the state at the end of this block.
Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. Note that the state is not encoded in the block in any way; it is purely an abstraction to be remembered by the validating node and can only be (securely) computed for any block by starting from the genesis state and sequentially applying every transaction in every block. Additionally, note that the order in which the miner includes transactions into the block matters; if there are two transactions A and B in a block such that B spends a UTXO created by A, then the block will be valid if A comes before B but not otherwise.
The one validity condition present in the above list that is not found in other systems is the requirement for "proof-of-work". The precise condition is that the double-SHA256 hash of every block, treated as a 256-bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 187 . The purpose of this is to make block creation computationally "hard", thereby preventing sybil attackers from remaking the entire blockchain in their favor. Because SHA256 is designed to be a completely unpredictable pseudorandom function, the only way to create a valid block is simply trial and error, repeatedly incrementing the nonce and seeing if the new hash matches.
At the current target of ~2 187 , the network must make an average of ~2 69 tries before a valid block is found; in general, the target is recalibrated by the network every 2016 blocks so that on average a new block is produced by some node in the network every ten minutes. In order to compensate miners for this computational work, the miner of every block is entitled to include a transaction giving themselves 25 BTC out of nowhere. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee". Incidentally, this is also the only mechanism by which BTC are issued; the genesis state contained no coins at all.
In order to better understand the purpose of mining, let us examine what happens in the event of a malicious attacker. Since Bitcoin's underlying cryptography is known to be secure, the attacker will target the one part of the Bitcoin system that is not protected by cryptography directly: the order of transactions. The attacker's strategy is simple:
- Send 100 BTC to a merchant in exchange for some product (preferably a rapid-delivery digital good)
- Wait for the delivery of the product
- Produce another transaction sending the same 100 BTC to himself
- Try to convince the network that his transaction to himself was the one that came first.
Once step (1) has taken place, after a few minutes some miner will include the transaction in a block, say block number 270000. After about one hour, five more blocks will have been added to the chain after that block, with each of those blocks indirectly pointing to the transaction and thus "confirming" it. At this point, the merchant will accept the payment as finalized and deliver the product; since we are assuming this is a digital good, delivery is instant. Now, the attacker creates another transaction sending the 100 BTC to himself. If the attacker simply releases it into the wild, the transaction will not be processed; miners will attempt to run APPLY(S,TX) and notice that TX consumes a UTXO which is no longer in the state. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block 270000 pointing to the same block 269999 as a parent but with the new transaction in place of the old one. Because the block data is different, this requires redoing the proof-of-work. Furthermore, the attacker's new version of block 270000 has a different hash, so the original blocks 270001 to 270005 do not "point" to it; thus, the original chain and the attacker's new chain are completely separate. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the 270005 chain while the attacker alone is working on the 270000 chain. In order for the attacker to make his blockchain the longest, he would need to have more computational power than the rest of the network combined in order to catch up (hence, "51% attack").
Merkle Trees
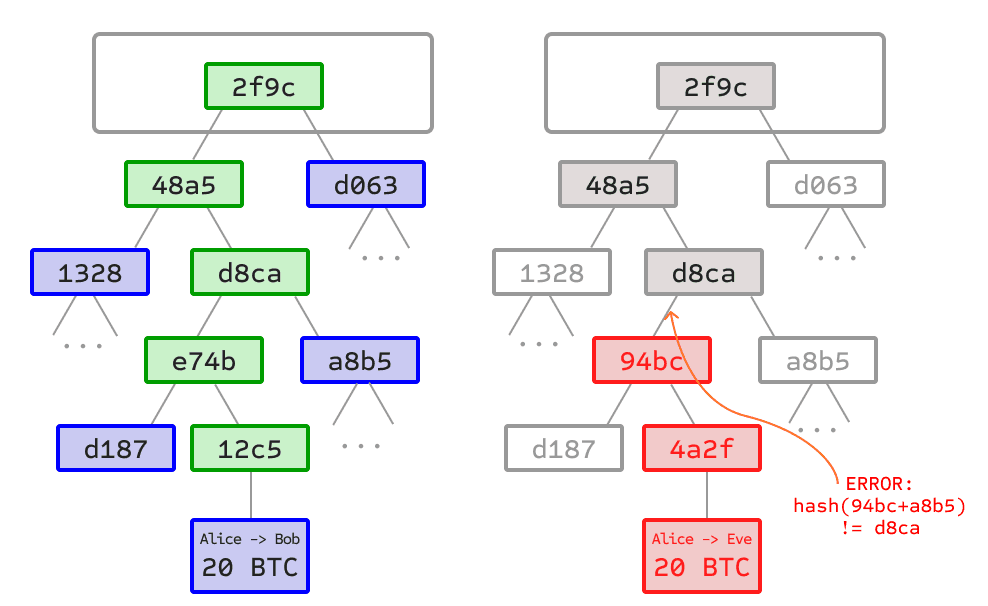
Left: it suffices to present only a small number of nodes in a Merkle tree to give a proof of the validity of a branch.
Right: any attempt to change any part of the Merkle tree will eventually lead to an inconsistency somewhere up the chain.
An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. The "hash" of a block is actually only the hash of the block header, a roughly 200-byte piece of data that contains the timestamp, nonce, previous block hash and the root hash of a data structure called the Merkle tree storing all transactions in the block. A Merkle tree is a type of binary tree, composed of a set of nodes with a large number of leaf nodes at the bottom of the tree containing the underlying data, a set of intermediate nodes where each node is the hash of its two children, and finally a single root node, also formed from the hash of its two children, representing the "top" of the tree. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: a node can download only the header of a block from one source, the small part of the tree relevant to them from another source, and still be assured that all of the data is correct. The reason why this works is that hashes propagate upward: if a malicious user attempts to swap in a fake transaction into the bottom of a Merkle tree, this change will cause a change in the node above, and then a change in the node above that, finally changing the root of the tree and therefore the hash of the block, causing the protocol to register it as a completely different block (almost certainly with an invalid proof-of-work).
The Merkle tree protocol is arguably essential to long-term sustainability. A "full node" in the Bitcoin network, one that stores and processes the entirety of every block, takes up about 15 GB of disk space in the Bitcoin network as of April 2014, and is growing by over a gigabyte per month. Currently, this is viable for some desktop computers and not phones, and later on in the future only businesses and hobbyists will be able to participate. A protocol known as "simplified payment verification" (SPV) allows for another class of nodes to exist, called "light nodes", which download the block headers, verify the proof-of-work on the block headers, and then download only the "branches" associated with transactions that are relevant to them. This allows light nodes to determine with a strong guarantee of security what the status of any Bitcoin transaction, and their current balance, is while downloading only a very small portion of the entire blockchain.
Alternative Blockchain Applications
The idea of taking the underlying blockchain idea and applying it to other concepts also has a long history. In 2005, Nick Szabo came out with the concept of " secure property titles with owner authority (opens in a new tab) ", a document describing how "new advances in replicated database technology" will allow for a blockchain-based system for storing a registry of who owns what land, creating an elaborate framework including concepts such as homesteading, adverse possession and Georgian land tax. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. After 2009, however, once Bitcoin's decentralized consensus was developed a number of alternative applications rapidly began to emerge.
- Namecoin - created in 2010, Namecoin (opens in a new tab) is best described as a decentralized name registration database. In decentralized protocols like Tor, Bitcoin and BitMessage, there needs to be some way of identifying accounts so that other people can interact with them, but in all existing solutions the only kind of identifier available is a pseudorandom hash like 1LW79wp5ZBqaHW1jL5TCiBCrhQYtHagUWy . Ideally, one would like to be able to have an account with a name like "george". However, the problem is that if one person can create an account named "george" then someone else can use the same process to register "george" for themselves as well and impersonate them. The only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a problem perfectly suited for the Bitcoin consensus protocol. Namecoin is the oldest, and most successful, implementation of a name registration system using such an idea.
- Colored coins - the purpose of colored coins (opens in a new tab) is to serve as a protocol to allow people to create their own digital currencies - or, in the important trivial case of a currency with one unit, digital tokens, on the Bitcoin blockchain. In the colored coins protocol, one "issues" a new currency by publicly assigning a color to a specific Bitcoin UTXO, and the protocol recursively defines the color of other UTXO to be the same as the color of the inputs that the transaction creating them spent (some special rules apply in the case of mixed-color inputs). This allows users to maintain wallets containing only UTXO of a specific color and send them around much like regular bitcoins, backtracking through the blockchain to determine the color of any UTXO that they receive.
- Metacoins - the idea behind a metacoin is to have a protocol that lives on top of Bitcoin, using Bitcoin transactions to store metacoin transactions but having a different state transition function, APPLY' . Because the metacoin protocol cannot prevent invalid metacoin transactions from appearing in the Bitcoin blockchain, a rule is added that if APPLY'(S,TX) returns an error, the protocol defaults to APPLY'(S,TX) = S . This provides an easy mechanism for creating an arbitrary cryptocurrency protocol, potentially with advanced features that cannot be implemented inside of Bitcoin itself, but with a very low development cost since the complexities of mining and networking are already handled by the Bitcoin protocol. Metacoins have been used to implement some classes of financial contracts, name registration and decentralized exchange.
Thus, in general, there are two approaches toward building a consensus protocol: building an independent network, and building a protocol on top of Bitcoin. The former approach, while reasonably successful in the case of applications like Namecoin, is difficult to implement; each individual implementation needs to bootstrap an independent blockchain, as well as building and testing all of the necessary state transition and networking code. Additionally, we predict that the set of applications for decentralized consensus technology will follow a power law distribution where the vast majority of applications would be too small to warrant their own blockchain, and we note that there exist large classes of decentralized applications, particularly decentralized autonomous organizations, that need to interact with each other.
The Bitcoin-based approach, on the other hand, has the flaw that it does not inherit the simplified payment verification features of Bitcoin. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols. Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way to the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. Currently, all "light" implementations of Bitcoin-based meta-protocols rely on a trusted server to provide the data, arguably a highly suboptimal result especially when one of the primary purposes of a cryptocurrency is to eliminate the need for trust.
Even without any extensions, the Bitcoin protocol actually does facilitate a weak version of a concept of "smart contracts". UTXO in Bitcoin can be owned not just by a public key, but also by a more complicated script expressed in a simple stack-based programming language. In this paradigm, a transaction spending that UTXO must provide data that satisfies the script. Indeed, even the basic public key ownership mechanism is implemented via a script: the script takes an elliptic curve signature as input, verifies it against the transaction and the address that owns the UTXO, and returns 1 if the verification is successful and 0 otherwise. Other, more complicated, scripts exist for various additional use cases. For example, one can construct a script that requires signatures from two out of a given three private keys to validate ("multisig"), a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. Scripts can also be used to pay bounties for solutions to computational problems, and one can even construct a script that says something like "this Bitcoin UTXO is yours if you can provide an SPV proof that you sent a Dogecoin transaction of this denomination to me", essentially allowing decentralized cross-cryptocurrency exchange.
However, the scripting language as implemented in Bitcoin has several important limitations:
- Lack of Turing-completeness - that is to say, while there is a large subset of computation that the Bitcoin scripting language supports, it does not nearly support everything. The main category that is missing is loops. This is done to avoid infinite loops during transaction verification; theoretically it is a surmountable obstacle for script programmers, since any loop can be simulated by simply repeating the underlying code many times with an if statement, but it does lead to scripts that are very space-inefficient. For example, implementing an alternative elliptic curve signature algorithm would likely require 256 repeated multiplication rounds all individually included in the code.
- Value-blindness - there is no way for a UTXO script to provide fine-grained control over the amount that can be withdrawn. For example, one powerful use case of an oracle contract would be a hedging contract, where A and B put in $1000 worth of BTC and after 30 days the script sends $1000 worth of BTC to A and the rest to B. This would require an oracle to determine the value of 1 BTC in USD, but even then it is a massive improvement in terms of trust and infrastructure requirement over the fully centralized solutions that are available now. However, because UTXO are all-or-nothing, the only way to achieve this is through the very inefficient hack of having many UTXO of varying denominations (eg. one UTXO of 2 k for every k up to 30) and having the oracle pick which UTXO to send to A and which to B.
- Lack of state - UTXO can either be spent or unspent; there is no opportunity for multi-stage contracts or scripts which keep any other internal state beyond that. This makes it hard to make multi-stage options contracts, decentralized exchange offers or two-stage cryptographic commitment protocols (necessary for secure computational bounties). It also means that UTXO can only be used to build simple, one-off contracts and not more complex "stateful" contracts such as decentralized organizations, and makes meta-protocols difficult to implement. Binary state combined with value-blindness also mean that another important application, withdrawal limits, is impossible.
- Blockchain-blindness - UTXO are blind to blockchain data such as the nonce, the timestamp and previous block hash. This severely limits applications in gambling, and several other categories, by depriving the scripting language of a potentially valuable source of randomness.
Thus, we see three approaches to building advanced applications on top of cryptocurrency: building a new blockchain, using scripting on top of Bitcoin, and building a meta-protocol on top of Bitcoin. Building a new blockchain allows for unlimited freedom in building a feature set, but at the cost of development time, bootstrapping effort and security. Using scripting is easy to implement and standardize, but is very limited in its capabilities, and meta-protocols, while easy, suffer from faults in scalability. With Ethereum, we intend to build an alternative framework that provides even larger gains in ease of development as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security.
The intent of Ethereum is to create an alternative protocol for building decentralized applications, providing a different set of tradeoffs that we believe will be very useful for a large class of decentralized applications, with particular emphasis on situations where rapid development time, security for small and rarely used applications, and the ability of different applications to very efficiently interact, are important. Ethereum does this by building what is essentially the ultimate abstract foundational layer: a blockchain with a built-in Turing-complete programming language, allowing anyone to write smart contracts and decentralized applications where they can create their own arbitrary rules for ownership, transaction formats and state transition functions. A bare-bones version of Namecoin can be written in two lines of code, and other protocols like currencies and reputation systems can be built in under twenty. Smart contracts, cryptographic "boxes" that contain value and only unlock it if certain conditions are met, can also be built on top of the platform, with vastly more power than that offered by Bitcoin scripting because of the added powers of Turing-completeness, value-awareness, blockchain-awareness and state.
Ethereum Accounts
In Ethereum, the state is made up of objects called "accounts", with each account having a 20-byte address and state transitions being direct transfers of value and information between accounts. An Ethereum account contains four fields:
- The nonce , a counter used to make sure each transaction can only be processed once
- The account's current ether balance
- The account's contract code , if present
- The account's storage (empty by default)
"Ether" is the main internal crypto-fuel of Ethereum, and is used to pay transaction fees. In general, there are two types of accounts: externally owned accounts , controlled by private keys, and contract accounts , controlled by their contract code. An externally owned account has no code, and one can send messages from an externally owned account by creating and signing a transaction; in a contract account, every time the contract account receives a message its code activates, allowing it to read and write to internal storage and send other messages or create contracts in turn.
Note that "contracts" in Ethereum should not be seen as something that should be "fulfilled" or "complied with"; rather, they are more like "autonomous agents" that live inside of the Ethereum execution environment, always executing a specific piece of code when "poked" by a message or transaction, and having direct control over their own ether balance and their own key/value store to keep track of persistent variables.
Messages and Transactions
The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. Transactions contain:
- The recipient of the message
- A signature identifying the sender
- The amount of ether to transfer from the sender to the recipient
- An optional data field
- A STARTGAS value, representing the maximum number of computational steps the transaction execution is allowed to take
- A GASPRICE value, representing the fee the sender pays per computational step
The first three are standard fields expected in any cryptocurrency. The data field has no function by default, but the virtual machine has an opcode using which a contract can access the data; as an example use case, if a contract is functioning as an on-blockchain domain registration service, then it may wish to interpret the data being passed to it as containing two "fields", the first field being a domain to register and the second field being the IP address to register it to. The contract would read these values from the message data and appropriately place them in storage.
The STARTGAS and GASPRICE fields are crucial for Ethereum's anti-denial of service model. In order to prevent accidental or hostile infinite loops or other computational wastage in code, each transaction is required to set a limit to how many computational steps of code execution it can use. The fundamental unit of computation is "gas"; usually, a computational step costs 1 gas, but some operations cost higher amounts of gas because they are more computationally expensive, or increase the amount of data that must be stored as part of the state. There is also a fee of 5 gas for every byte in the transaction data. The intent of the fee system is to require an attacker to pay proportionately for every resource that they consume, including computation, bandwidth and storage; hence, any transaction that leads to the network consuming a greater amount of any of these resources must have a gas fee roughly proportional to the increment.
Contracts have the ability to send "messages" to other contracts. Messages are virtual objects that are never serialized and exist only in the Ethereum execution environment. A message contains:
- The sender of the message (implicit)
- The amount of ether to transfer alongside the message
- A STARTGAS value
Essentially, a message is like a transaction, except it is produced by a contract and not an external actor. A message is produced when a contract currently executing code executes the CALL opcode, which produces and executes a message. Like a transaction, a message leads to the recipient account running its code. Thus, contracts can have relationships with other contracts in exactly the same way that external actors can.
Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed by that transaction and all sub-executions. For example, if an external actor A sends a transaction to B with 1000 gas, and B consumes 600 gas before sending a message to C, and the internal execution of C consumes 300 gas before returning, then B can spend another 100 gas before running out of gas.
Ethereum State Transition Function
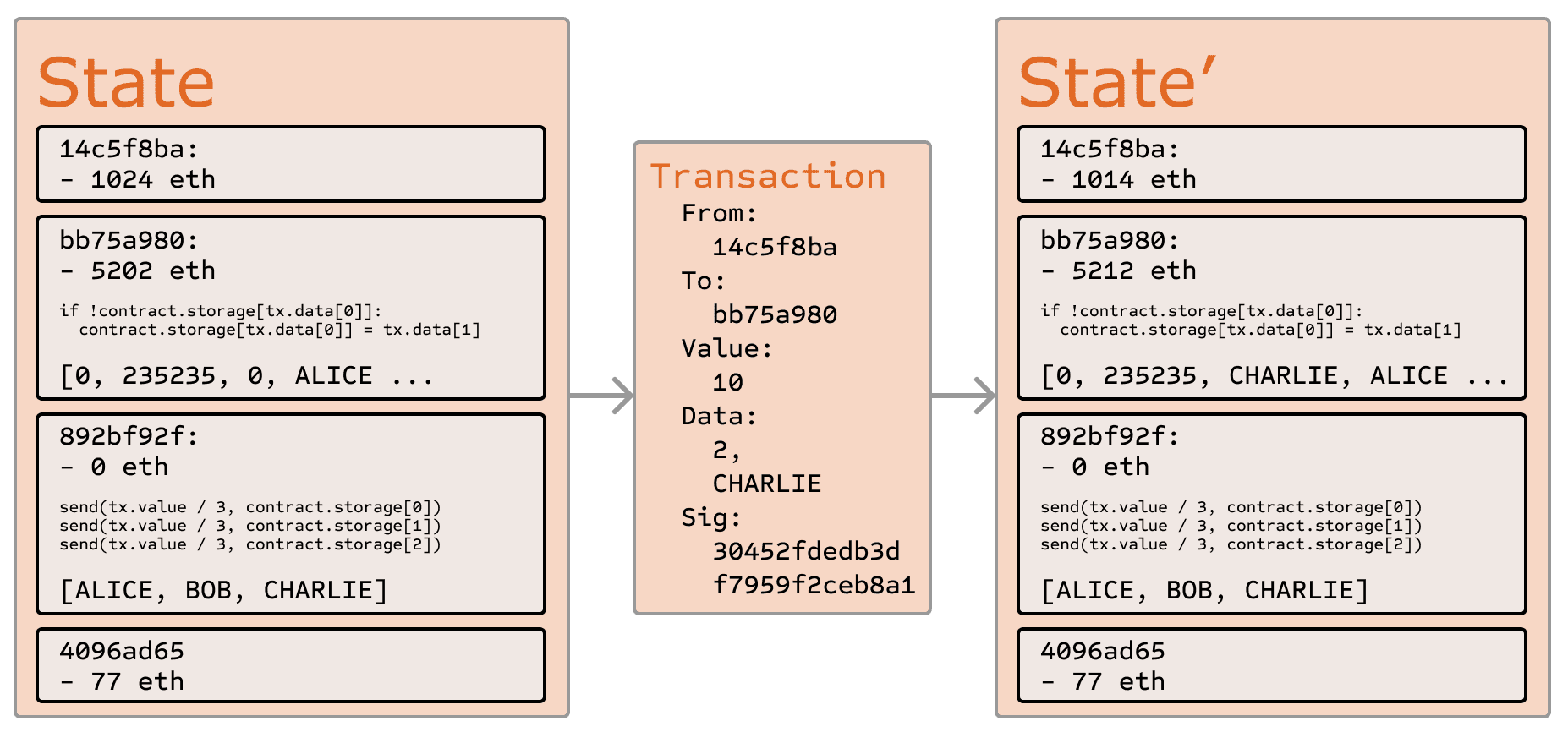
The Ethereum state transition function, APPLY(S,TX) -> S' can be defined as follows:
- Check if the transaction is well-formed (ie. has the right number of values), the signature is valid, and the nonce matches the nonce in the sender's account. If not, return an error.
- Calculate the transaction fee as STARTGAS * GASPRICE , and determine the sending address from the signature. Subtract the fee from the sender's account balance and increment the sender's nonce. If there is not enough balance to spend, return an error.
- Initialize GAS = STARTGAS , and take off a certain quantity of gas per byte to pay for the bytes in the transaction.
- Transfer the transaction value from the sender's account to the receiving account. If the receiving account does not yet exist, create it. If the receiving account is a contract, run the contract's code either to completion or until the execution runs out of gas.
- If the value transfer failed because the sender did not have enough money, or the code execution ran out of gas, revert all state changes except the payment of the fees, and add the fees to the miner's account.
- Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner.
For example, suppose that the contract's code is:
Note that in reality the contract code is written in the low-level EVM code; this example is written in Serpent, one of our high-level languages, for clarity, and can be compiled down to EVM code. Suppose that the contract's storage starts off empty, and a transaction is sent with 10 ether value, 2000 gas, 0.001 ether gasprice, and 64 bytes of data, with bytes 0-31 representing the number 2 and bytes 32-63 representing the string CHARLIE . The process for the state transition function in this case is as follows:
- Check that the transaction is valid and well formed.
- Check that the transaction sender has at least 2000 * 0.001 = 2 ether. If it is, then subtract 2 ether from the sender's account.
- Initialize gas = 2000; assuming the transaction is 170 bytes long and the byte-fee is 5, subtract 850 so that there is 1150 gas left.
- Subtract 10 more ether from the sender's account, and add it to the contract's account.
- Run the code. In this case, this is simple: it checks if the contract's storage at index 2 is used, notices that it is not, and so it sets the storage at index 2 to the value CHARLIE . Suppose this takes 187 gas, so the remaining amount of gas is 1150 - 187 = 963
- Add 963 * 0.001 = 0.963 ether back to the sender's account, and return the resulting state.
If there was no contract at the receiving end of the transaction, then the total transaction fee would simply be equal to the provided GASPRICE multiplied by the length of the transaction in bytes, and the data sent alongside the transaction would be irrelevant.
Note that messages work equivalently to transactions in terms of reverts: if a message execution runs out of gas, then that message's execution, and all other executions triggered by that execution, revert, but parent executions do not need to revert. This means that it is "safe" for a contract to call another contract, as if A calls B with G gas then A's execution is guaranteed to lose at most G gas. Finally, note that there is an opcode, CREATE , that creates a contract; its execution mechanics are generally similar to CALL , with the exception that the output of the execution determines the code of a newly created contract.
Code Execution
The code in Ethereum contracts is written in a low-level, stack-based bytecode language, referred to as "Ethereum virtual machine code" or "EVM code". The code consists of a series of bytes, where each byte represents an operation. In general, code execution is an infinite loop that consists of repeatedly carrying out the operation at the current program counter (which begins at zero) and then incrementing the program counter by one, until the end of the code is reached or an error or STOP or RETURN instruction is detected. The operations have access to three types of space in which to store data:
- The stack , a last-in-first-out container to which values can be pushed and popped
- Memory , an infinitely expandable byte array
- The contract's long-term storage , a key/value store. Unlike stack and memory, which reset after computation ends, storage persists for the long term.
The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output.
The formal execution model of EVM code is surprisingly simple. While the Ethereum virtual machine is running, its full computational state can be defined by the tuple (block_state, transaction, message, code, memory, stack, pc, gas) , where block_state is the global state containing all accounts and includes balances and storage. At the start of every round of execution, the current instruction is found by taking the pc th byte of code (or 0 if pc >= len(code) ), and each instruction has its own definition in terms of how it affects the tuple. For example, ADD pops two items off the stack and pushes their sum, reduces gas by 1 and increments pc by 1, and SSTORE pops the top two items off the stack and inserts the second item into the contract's storage at the index specified by the first item. Although there are many ways to optimize Ethereum virtual machine execution via just-in-time compilation, a basic implementation of Ethereum can be done in a few hundred lines of code.
Blockchain and Mining
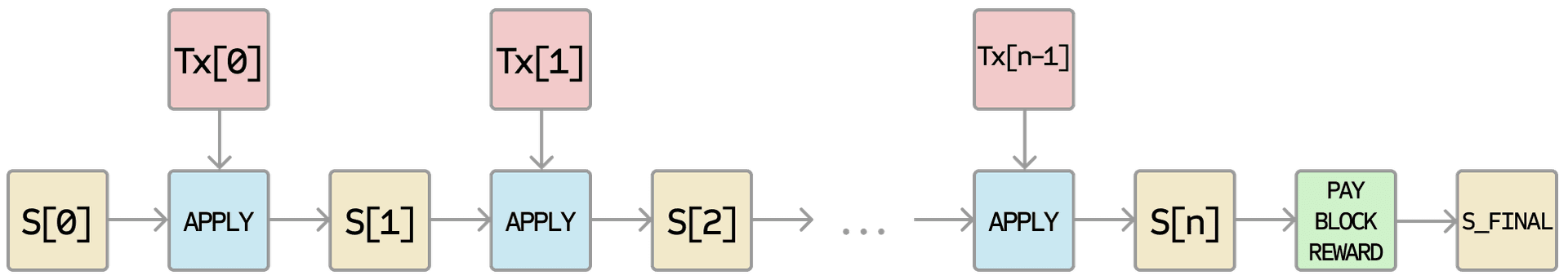
The Ethereum blockchain is in many ways similar to the Bitcoin blockchain, although it does have some differences. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin, Ethereum blocks contain a copy of both the transaction list and the most recent state. Aside from that, two other values, the block number and the difficulty, are also stored in the block. The basic block validation algorithm in Ethereum is as follows:
- Check if the previous block referenced exists and is valid.
- Check that the timestamp of the block is greater than that of the referenced previous block and less than 15 minutes into the future
- Check that the block number, difficulty, transaction root, uncle root and gas limit (various low-level Ethereum-specific concepts) are valid.
- Let TX be the block's transaction list, with n transactions. For all i in 0...n-1 , set S[i+1] = APPLY(S[i],TX[i]) . If any applications returns an error, or if the total gas consumed in the block up until this point exceeds the GASLIMIT , return an error.
- Let S_FINAL be S[n] , but adding the block reward paid to the miner.
- Check if the Merkle tree root of the state S_FINAL is equal to the final state root provided in the block header. If it is, the block is valid; otherwise, it is not valid.
The approach may seem highly inefficient at first glance, because it needs to store the entire state with each block, but in reality efficiency should be comparable to that of Bitcoin. The reason is that the state is stored in the tree structure, and after every block only a small part of the tree needs to be changed. Thus, in general, between two adjacent blocks the vast majority of the tree should be the same, and therefore the data can be stored once and referenced twice using pointers (ie. hashes of subtrees). A special kind of tree known as a "Patricia tree" is used to accomplish this, including a modification to the Merkle tree concept that allows for nodes to be inserted and deleted, and not just changed, efficiently. Additionally, because all of the state information is part of the last block, there is no need to store the entire blockchain history - a strategy which, if it could be applied to Bitcoin, can be calculated to provide 5-20x savings in space.
A commonly asked question is "where" contract code is executed, in terms of physical hardware. This has a simple answer: the process of executing contract code is part of the definition of the state transition function, which is part of the block validation algorithm, so if a transaction is added into block B the code execution spawned by that transaction will be executed by all nodes, now and in the future, that download and validate block B .
Applications
In general, there are three types of applications on top of Ethereum. The first category is financial applications, providing users with more powerful ways of managing and entering into contracts using their money. This includes sub-currencies, financial derivatives, hedging contracts, savings wallets, wills, and ultimately even some classes of full-scale employment contracts. The second category is semi-financial applications, where money is involved but there is also a heavy non-monetary side to what is being done; a perfect example is self-enforcing bounties for solutions to computational problems. Finally, there are applications such as online voting and decentralized governance that are not financial at all.
Token Systems
On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company stocks, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. Token systems are surprisingly easy to implement in Ethereum. The key point to understand is that all a currency, or token system, fundamentally is, is a database with one operation: subtract X units from A and give X units to B, with the proviso that (i) A had at least X units before the transaction and (2) the transaction is approved by A. All that it takes to implement a token system is to implement this logic into a contract.
The basic code for implementing a token system in Serpent looks as follows:
This is essentially a literal implementation of the "banking system" state transition function described further above in this document. A few extra lines of code need to be added to provide for the initial step of distributing the currency units in the first place and a few other edge cases, and ideally a function would be added to let other contracts query for the balance of an address. But that's all there is to it. Theoretically, Ethereum-based token systems acting as sub-currencies can potentially include another important feature that on-chain Bitcoin-based meta-currencies lack: the ability to pay transaction fees directly in that currency. The way this would be implemented is that the contract would maintain an ether balance with which it would refund ether used to pay fees to the sender, and it would refill this balance by collecting the internal currency units that it takes in fees and reselling them in a constant running auction. Users would thus need to "activate" their accounts with ether, but once the ether is there it would be reusable because the contract would refund it each time.
Financial derivatives and Stable-Value Currencies
Financial derivatives are the most common application of a "smart contract", and one of the simplest to implement in code. The main challenge in implementing financial contracts is that the majority of them require reference to an external price ticker; for example, a very desirable application is a smart contract that hedges against the volatility of ether (or another cryptocurrency) with respect to the US dollar, but doing this requires the contract to know what the value of ETH/USD is. The simplest way to do this is through a "data feed" contract maintained by a specific party (eg. NASDAQ) designed so that that party has the ability to update the contract as needed, and providing an interface that allows other contracts to send a message to that contract and get back a response that provides the price.
Given that critical ingredient, the hedging contract would look as follows:
- Wait for party A to input 1000 ether.
- Wait for party B to input 1000 ether.
- Record the USD value of 1000 ether, calculated by querying the data feed contract, in storage, say this is $x.
- After 30 days, allow A or B to "reactivate" the contract in order to send $x worth of ether (calculated by querying the data feed contract again to get the new price) to A and the rest to B.
Such a contract would have significant potential in crypto-commerce. One of the main problems cited about cryptocurrency is the fact that it's volatile; although many users and merchants may want the security and convenience of dealing with cryptographic assets, they many not wish to face that prospect of losing 23% of the value of their funds in a single day. Up until now, the most commonly proposed solution has been issuer-backed assets; the idea is that an issuer creates a sub-currency in which they have the right to issue and revoke units, and provide one unit of the currency to anyone who provides them (offline) with one unit of a specified underlying asset (eg. gold, USD). The issuer then promises to provide one unit of the underlying asset to anyone who sends back one unit of the crypto-asset. This mechanism allows any non-cryptographic asset to be "uplifted" into a cryptographic asset, provided that the issuer can be trusted.
In practice, however, issuers are not always trustworthy, and in some cases the banking infrastructure is too weak, or too hostile, for such services to exist. Financial derivatives provide an alternative. Here, instead of a single issuer providing the funds to back up an asset, a decentralized market of speculators, betting that the price of a cryptographic reference asset (eg. ETH) will go up, plays that role. Unlike issuers, speculators have no option to default on their side of the bargain because the hedging contract holds their funds in escrow. Note that this approach is not fully decentralized, because a trusted source is still needed to provide the price ticker, although arguably even still this is a massive improvement in terms of reducing infrastructure requirements (unlike being an issuer, issuing a price feed requires no licenses and can likely be categorized as free speech) and reducing the potential for fraud.
Identity and Reputation Systems
The earliest alternative cryptocurrency of all, Namecoin (opens in a new tab) , attempted to use a Bitcoin-like blockchain to provide a name registration system, where users can register their names in a public database alongside other data. The major cited use case is for a DNS (opens in a new tab) system, mapping domain names like "bitcoin.org" (or, in Namecoin's case, "bitcoin.bit") to an IP address. Other use cases include email authentication and potentially more advanced reputation systems. Here is the basic contract to provide a Namecoin-like name registration system on Ethereum:
The contract is very simple; all it is a database inside the Ethereum network that can be added to, but not modified or removed from. Anyone can register a name with some value, and that registration then sticks forever. A more sophisticated name registration contract will also have a "function clause" allowing other contracts to query it, as well as a mechanism for the "owner" (ie. the first registerer) of a name to change the data or transfer ownership. One can even add reputation and web-of-trust functionality on top.
Decentralized File Storage
Over the past few years, there have emerged a number of popular online file storage startups, the most prominent being Dropbox, seeking to allow users to upload a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. However, at this point the file storage market is at times relatively inefficient; a cursory look at various existing solutions shows that, particularly at the "uncanny valley" 20-200 GB level at which neither free quotas nor enterprise-level discounts kick in, monthly prices for mainstream file storage costs are such that you are paying for more than the cost of the entire hard drive in a single month. Ethereum contracts can allow for the development of a decentralized file storage ecosystem, where individual users can earn small quantities of money by renting out their own hard drives and unused space can be used to further drive down the costs of file storage.
The key underpinning piece of such a device would be what we have termed the "decentralized Dropbox contract". This contract works as follows. First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. One then makes a contract with the rule that, every N blocks, the contract would pick a random index in the Merkle tree (using the previous block hash, accessible from contract code, as a source of randomness), and give X ether to the first entity to supply a transaction with a simplified payment verification-like proof of ownership of the block at that particular index in the tree. When a user wants to re-download their file, they can use a micropayment channel protocol (eg. pay 1 szabo per 32 kilobytes) to recover the file; the most fee-efficient approach is for the payer not to publish the transaction until the end, instead replacing the transaction with a slightly more lucrative one with the same nonce after every 32 kilobytes.
An important feature of the protocol is that, although it may seem like one is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces via secret sharing, and watching the contracts to see each piece is still in some node's possession. If a contract is still paying out money, that provides a cryptographic proof that someone out there is still storing the file.
Decentralized Autonomous Organizations
The general concept of a "decentralized autonomous organization" is that of a virtual entity that has a certain set of members or shareholders which, perhaps with a 67% majority, have the right to spend the entity's funds and modify its code. The members would collectively decide on how the organization should allocate its funds. Methods for allocating a DAO's funds could range from bounties, salaries to even more exotic mechanisms such as an internal currency to reward work. This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. So far much of the talk around DAOs has been around the "capitalist" model of a "decentralized autonomous corporation" (DAC) with dividend-receiving shareholders and tradable shares; an alternative, perhaps described as a "decentralized autonomous community", would have all members have an equal share in the decision making and require 67% of existing members to agree to add or remove a member. The requirement that one person can only have one membership would then need to be enforced collectively by the group.
A general outline for how to code a DAO is as follows. The simplest design is simply a piece of self-modifying code that changes if two thirds of members agree on a change. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. In a simple implementation of such a DAO contract, there would be three transaction types, distinguished by the data provided in the transaction:
- [0,i,K,V] to register a proposal with index i to change the address at storage index K to value V
- [1,i] to register a vote in favor of proposal i
- [2,i] to finalize proposal i if enough votes have been made
The contract would then have clauses for each of these. It would maintain a record of all open storage changes, along with a list of who voted for them. It would also have a list of all members. When any storage change gets to two thirds of members voting for it, a finalizing transaction could execute the change. A more sophisticated skeleton would also have built-in voting ability for features like sending a transaction, adding members and removing members, and may even provide for Liquid Democracy (opens in a new tab) -style vote delegation (ie. anyone can assign someone to vote for them, and assignment is transitive so if A assigns B and B assigns C then C determines A's vote). This design would allow the DAO to grow organically as a decentralized community, allowing people to eventually delegate the task of filtering out who is a member to specialists, although unlike in the "current system" specialists can easily pop in and out of existence over time as individual community members change their alignments.
An alternative model is for a decentralized corporation, where any account can have zero or more shares, and two thirds of the shares are required to make a decision. A complete skeleton would involve asset management functionality, the ability to make an offer to buy or sell shares, and the ability to accept offers (preferably with an order-matching mechanism inside the contract). Delegation would also exist Liquid Democracy-style, generalizing the concept of a "board of directors".
Further Applications
1. Savings wallets . Suppose that Alice wants to keep her funds safe, but is worried that she will lose or someone will hack her private key. She puts ether into a contract with Bob, a bank, as follows:
- Alice alone can withdraw a maximum of 1% of the funds per day.
- Bob alone can withdraw a maximum of 1% of the funds per day, but Alice has the ability to make a transaction with her key shutting off this ability.
- Alice and Bob together can withdraw anything.
Normally, 1% per day is enough for Alice, and if Alice wants to withdraw more she can contact Bob for help. If Alice's key gets hacked, she runs to Bob to move the funds to a new contract. If she loses her key, Bob will get the funds out eventually. If Bob turns out to be malicious, then she can turn off his ability to withdraw.
2. Crop insurance . One can easily make a financial derivatives contract but using a data feed of the weather instead of any price index. If a farmer in Iowa purchases a derivative that pays out inversely based on the precipitation in Iowa, then if there is a drought, the farmer will automatically receive money and if there is enough rain the farmer will be happy because their crops would do well. This can be expanded to natural disaster insurance generally.
3. A decentralized data feed . For financial contracts for difference, it may actually be possible to decentralize the data feed via a protocol called " SchellingCoin (opens in a new tab) ". SchellingCoin basically works as follows: N parties all put into the system the value of a given datum (eg. the ETH/USD price), the values are sorted, and everyone between the 25th and 75th percentile gets one token as a reward. Everyone has the incentive to provide the answer that everyone else will provide, and the only value that a large number of players can realistically agree on is the obvious default: the truth. This creates a decentralized protocol that can theoretically provide any number of values, including the ETH/USD price, the temperature in Berlin or even the result of a particular hard computation.
4. Smart multisignature escrow . Bitcoin allows multisignature transaction contracts where, for example, three out of a given five keys can spend the funds. Ethereum allows for more granularity; for example, four out of five can spend everything, three out of five can spend up to 10% per day, and two out of five can spend up to 0.5% per day. Additionally, Ethereum multisig is asynchronous - two parties can register their signatures on the blockchain at different times and the last signature will automatically send the transaction.
5. Cloud computing . The EVM technology can also be used to create a verifiable computing environment, allowing users to ask others to carry out computations and then optionally ask for proofs that computations at certain randomly selected checkpoints were done correctly. This allows for the creation of a cloud computing market where any user can participate with their desktop, laptop or specialized server, and spot-checking together with security deposits can be used to ensure that the system is trustworthy (ie. nodes cannot profitably cheat). Although such a system may not be suitable for all tasks; tasks that require a high level of inter-process communication, for example, cannot easily be done on a large cloud of nodes. Other tasks, however, are much easier to parallelize; projects like SETI@home, folding@home and genetic algorithms can easily be implemented on top of such a platform.
6. Peer-to-peer gambling . Any number of peer-to-peer gambling protocols, such as Frank Stajano and Richard Clayton's Cyberdice (opens in a new tab) , can be implemented on the Ethereum blockchain. The simplest gambling protocol is actually simply a contract for difference on the next block hash, and more advanced protocols can be built up from there, creating gambling services with near-zero fees that have no ability to cheat.
7. Prediction markets . Provided an oracle or SchellingCoin, prediction markets are also easy to implement, and prediction markets together with SchellingCoin may prove to be the first mainstream application of futarchy (opens in a new tab) as a governance protocol for decentralized organizations.
8. On-chain decentralized marketplaces , using the identity and reputation system as a base.
Miscellanea And Concerns
Modified ghost implementation.
The "Greedy Heaviest Observed Subtree" (GHOST) protocol is an innovation first introduced by Yonatan Sompolinsky and Aviv Zohar in December 2013 (opens in a new tab) . The motivation behind GHOST is that blockchains with fast confirmation times currently suffer from reduced security due to a high stale rate - because blocks take a certain time to propagate through the network, if miner A mines a block and then miner B happens to mine another block before miner A's block propagates to B, miner B's block will end up wasted and will not contribute to network security. Furthermore, there is a centralization issue: if miner A is a mining pool with 30% hashpower and B has 10% hashpower, A will have a risk of producing a stale block 70% of the time (since the other 30% of the time A produced the last block and so will get mining data immediately) whereas B will have a risk of producing a stale block 90% of the time. Thus, if the block interval is short enough for the stale rate to be high, A will be substantially more efficient simply by virtue of its size. With these two effects combined, blockchains which produce blocks quickly are very likely to lead to one mining pool having a large enough percentage of the network hashpower to have de facto control over the mining process.
As described by Sompolinsky and Zohar, GHOST solves the first issue of network security loss by including stale blocks in the calculation of which chain is the "longest"; that is to say, not just the parent and further ancestors of a block, but also the stale descendants of the block's ancestor (in Ethereum jargon, "uncles") are added to the calculation of which block has the largest total proof-of-work backing it. To solve the second issue of centralization bias, we go beyond the protocol described by Sompolinsky and Zohar, and also provide block rewards to stales: a stale block receives 87.5% of its base reward, and the nephew that includes the stale block receives the remaining 12.5%. Transaction fees, however, are not awarded to uncles.
Ethereum implements a simplified version of GHOST which only goes down seven levels. Specifically, it is defined as follows:
- A block must specify a parent, and it must specify 0 or more uncles
- It must be a direct child of the kth generation ancestor of B, where 2 <= k <= 7 .
- It cannot be an ancestor of B
- An uncle must be a valid block header, but does not need to be a previously verified or even valid block
- An uncle must be different from all uncles included in previous blocks and all other uncles included in the same block (non-double-inclusion)
- For every uncle U in block B, the miner of B gets an additional 3.125% added to its coinbase reward and the miner of U gets 93.75% of a standard coinbase reward.
This limited version of GHOST, with uncles includable only up to 7 generations, was used for two reasons. First, unlimited GHOST would include too many complications into the calculation of which uncles for a given block are valid. Second, unlimited GHOST with compensation as used in Ethereum removes the incentive for a miner to mine on the main chain and not the chain of a public attacker.
Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. The default approach, used in Bitcoin, is to have purely voluntary fees, relying on miners to act as the gatekeepers and set dynamic minimums. This approach has been received very favorably in the Bitcoin community particularly because it is "market-based", allowing supply and demand between miners and transaction senders determine the price. The problem with this line of reasoning is, however, that transaction processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the miner is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of whether or not to include it. Hence, tragedy-of-the-commons problems are very likely to occur.
However, as it turns out this flaw in the market-based mechanism, when given a particular inaccurate simplifying assumption, magically cancels itself out. The argument is as follows. Suppose that:
- A transaction leads to k operations, offering the reward kR to any miner that includes it where R is set by the sender and k and R are (roughly) visible to the miner beforehand.
- An operation has a processing cost of C to any node (ie. all nodes have equal efficiency)
- There are N mining nodes, each with exactly equal processing power (ie. 1/N of total)
- No non-mining full nodes exist.
A miner would be willing to process a transaction if the expected reward is greater than the cost. Thus, the expected reward is kR/N since the miner has a 1/N chance of processing the next block, and the processing cost for the miner is simply kC . Hence, miners will include transactions where kR/N > kC , or R > NC . Note that R is the per-operation fee provided by the sender, and is thus a lower bound on the benefit that the sender derives from the transaction, and NC is the cost to the entire network together of processing an operation. Hence, miners have the incentive to include only those transactions for which the total utilitarian benefit exceeds the cost.
However, there are several important deviations from those assumptions in reality:
- The miner does pay a higher cost to process the transaction than the other verifying nodes, since the extra verification time delays block propagation and thus increases the chance the block will become a stale.
- There do exist nonmining full nodes.
- The mining power distribution may end up radically inegalitarian in practice.
- Speculators, political enemies and crazies whose utility function includes causing harm to the network do exist, and they can cleverly set up contracts where their cost is much lower than the cost paid by other verifying nodes.
(1) provides a tendency for the miner to include fewer transactions, and (2) increases NC ; hence, these two effects at least partially cancel each other out. How? (opens in a new tab) (3) and (4) are the major issue; to solve them we simply institute a floating cap: no block can have more operations than BLK_LIMIT_FACTOR times the long-term exponential moving average. Specifically:
BLK_LIMIT_FACTOR and EMA_FACTOR are constants that will be set to 65536 and 1.5 for the time being, but will likely be changed after further analysis.
There is another factor disincentivizing large block sizes in Bitcoin: blocks that are large will take longer to propagate, and thus have a higher probability of becoming stales. In Ethereum, highly gas-consuming blocks can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate. This delay disincentive is a significant consideration in Bitcoin, but less so in Ethereum because of the GHOST protocol; hence, relying on regulated block limits provides a more stable baseline.
Computation And Turing-Completeness
An important note is that the Ethereum virtual machine is Turing-complete; this means that EVM code can encode any computation that can be conceivably carried out, including infinite loops. EVM code allows looping in two ways. First, there is a JUMP instruction that allows the program to jump back to a previous spot in the code, and a JUMPI instruction to do conditional jumping, allowing for statements like while x < 27: x = x * 2 . Second, contracts can call other contracts, potentially allowing for looping through recursion. This naturally leads to a problem: can malicious users essentially shut miners and full nodes down by forcing them to enter into an infinite loop? The issue arises because of a problem in computer science known as the halting problem: there is no way to tell, in the general case, whether or not a given program will ever halt.
As described in the state transition section, our solution works by requiring a transaction to set a maximum number of computational steps that it is allowed to take, and if execution takes longer computation is reverted but fees are still paid. Messages work in the same way. To show the motivation behind our solution, consider the following examples:
- An attacker creates a contract which runs an infinite loop, and then sends a transaction activating that loop to the miner. The miner will process the transaction, running the infinite loop, and wait for it to run out of gas. Even though the execution runs out of gas and stops halfway through, the transaction is still valid and the miner still claims the fee from the attacker for each computational step.
- An attacker creates a very long infinite loop with the intent of forcing the miner to keep computing for such a long time that by the time computation finishes a few more blocks will have come out and it will not be possible for the miner to include the transaction to claim the fee. However, the attacker will be required to submit a value for STARTGAS limiting the number of computational steps that execution can take, so the miner will know ahead of time that the computation will take an excessively large number of steps.
- An attacker sees a contract with code of some form like send(A,contract.storage[A]); contract.storage[A] = 0 , and sends a transaction with just enough gas to run the first step but not the second (ie. making a withdrawal but not letting the balance go down). The contract author does not need to worry about protecting against such attacks, because if execution stops halfway through the changes get reverted.
- A financial contract works by taking the median of nine proprietary data feeds in order to minimize risk. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. However, the financial contract can set a gas limit on the message to prevent this problem.
The alternative to Turing-completeness is Turing-incompleteness, where JUMP and JUMPI do not exist and only one copy of each contract is allowed to exist in the call stack at any given time. With this system, the fee system described and the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. Additionally, Turing-incompleteness is not even that big a limitation; out of all the contract examples we have conceived internally, so far only one required a loop, and even that loop could be removed by making 26 repetitions of a one-line piece of code. Given the serious implications of Turing-completeness, and the limited benefit, why not simply have a Turing-incomplete language? In reality, however, Turing-incompleteness is far from a neat solution to the problem. To see why, consider the following contracts:
Now, send a transaction to A. Thus, in 51 transactions, we have a contract that takes up 2 50 computational steps. Miners could try to detect such logic bombs ahead of time by maintaining a value alongside each contract specifying the maximum number of computational steps that it can take, and calculating this for contracts calling other contracts recursively, but that would require miners to forbid contracts that create other contracts (since the creation and execution of all 26 contracts above could easily be rolled into a single contract). Another problematic point is that the address field of a message is a variable, so in general it may not even be possible to tell which other contracts a given contract will call ahead of time. Hence, all in all, we have a surprising conclusion: Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete?
Currency And Issuance
The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. For convenience and to avoid future argument (see the current mBTC/uBTC/satoshi debate in Bitcoin), the denominations will be pre-labelled:
- 10 12 : szabo
- 10 15 : finney
- 10 18 : ether
This should be taken as an expanded version of the concept of "dollars" and "cents" or "BTC" and "satoshi". In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point.
The issuance model will be as follows:
- Ether will be released in a currency sale at the price of 1000-2000 ether per BTC, a mechanism intended to fund the Ethereum organization and pay for development that has been used with success by other platforms such as Mastercoin and NXT. Earlier buyers will benefit from larger discounts. The BTC received from the sale will be used entirely to pay salaries and bounties to developers and invested into various for-profit and non-profit projects in the Ethereum and cryptocurrency ecosystem.
- 0.099x the total amount sold (60102216 ETH) will be allocated to the organization to compensate early contributors and pay ETH-denominated expenses before the genesis block.
- 0.099x the total amount sold will be maintained as a long-term reserve.
- 0.26x the total amount sold will be allocated to miners per year forever after that point.
| Group | At launch | After 1 year | After 5 years |
|---|---|---|---|
| Currency units | 1.198X | 1.458X | 2.498X |
| Purchasers | 83.5% | 68.6% | 40.0% |
| Reserve spent pre-sale | 8.26% | 6.79% | 3.96% |
| Reserve used post-sale | 8.26% | 6.79% | 3.96% |
| Miners | 0% | 17.8% | 52.0% |
Long-Term Supply Growth Rate (percent)
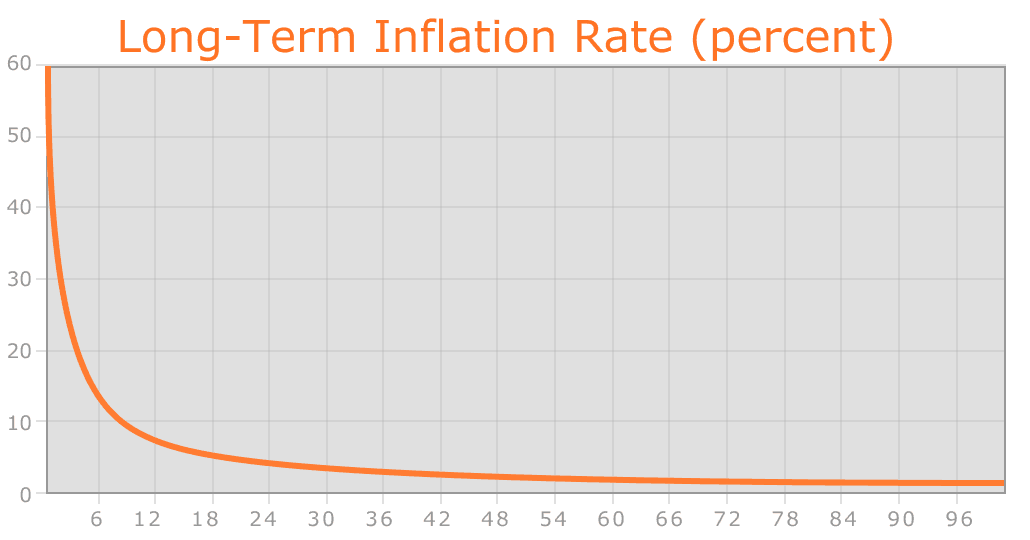
Despite the linear currency issuance, just like with Bitcoin over time the supply growth rate nevertheless tends to zero.
The two main choices in the above model are (1) the existence and size of an endowment pool, and (2) the existence of a permanently growing linear supply, as opposed to a capped supply as in Bitcoin. The justification of the endowment pool is as follows. If the endowment pool did not exist, and the linear issuance reduced to 0.217x to provide the same inflation rate, then the total quantity of ether would be 16.5% less and so each unit would be 19.8% more valuable. Hence, in the equilibrium 19.8% more ether would be purchased in the sale, so each unit would once again be exactly as valuable as before. The organization would also then have 1.198x as much BTC, which can be considered to be split into two slices: the original BTC, and the additional 0.198x. Hence, this situation is exactly equivalent to the endowment, but with one important difference: the organization holds purely BTC, and so is not incentivized to support the value of the ether unit.
The permanent linear supply growth model reduces the risk of what some see as excessive wealth concentration in Bitcoin, and gives individuals living in present and future eras a fair chance to acquire currency units, while at the same time retaining a strong incentive to obtain and hold ether because the "supply growth rate" as a percentage still tends to zero over time. We also theorize that because coins are always lost over time due to carelessness, death, etc, and coin loss can be modeled as a percentage of the total supply per year, that the total currency supply in circulation will in fact eventually stabilize at a value equal to the annual issuance divided by the loss rate (eg. at a loss rate of 1%, once the supply reaches 26X then 0.26X will be mined and 0.26X lost every year, creating an equilibrium).
Note that in the future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and 0.05X per year. In the event that the Ethereum organization loses funding or for any other reason disappears, we leave open a "social contract": anyone has the right to create a future candidate version of Ethereum, with the only condition being that the quantity of ether must be at most equal to 60102216 * (1.198 + 0.26 * n) where n is the number of years after the genesis block. Creators are free to crowd-sell or otherwise assign some or all of the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions.
Mining Centralization
The Bitcoin mining algorithm works by having miners compute SHA256 on slightly modified versions of the block header millions of times over and over again, until eventually one node comes up with a version whose hash is less than the target (currently around 2 192 ). However, this mining algorithm is vulnerable to two forms of centralization. First, the mining ecosystem has come to be dominated by ASICs (application-specific integrated circuits), computer chips designed for, and therefore thousands of times more efficient at, the specific task of Bitcoin mining. This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. Second, most Bitcoin miners do not actually perform block validation locally; instead, they rely on a centralized mining pool to provide the block headers. This problem is arguably worse: as of the time of this writing, the top three mining pools indirectly control roughly 50% of processing power in the Bitcoin network, although this is mitigated by the fact that miners can switch to other mining pools if a pool or coalition attempts a 51% attack.
The current intent at Ethereum is to use a mining algorithm where miners are required to fetch random data from the state, compute some randomly selected transactions from the last N blocks in the blockchain, and return the hash of the result. This has two important benefits. First, Ethereum contracts can include any kind of computation, so an Ethereum ASIC would essentially be an ASIC for general computation - ie. a better CPU. Second, mining requires access to the entire blockchain, forcing miners to store the entire blockchain and at least be capable of verifying every transaction. This removes the need for centralized mining pools; although mining pools can still serve the legitimate role of evening out the randomness of reward distribution, this function can be served equally well by peer-to-peer pools with no central control.
This model is untested, and there may be difficulties along the way in avoiding certain clever optimizations when using contract execution as a mining algorithm. However, one notably interesting feature of this algorithm is that it allows anyone to "poison the well", by introducing a large number of contracts into the blockchain specifically designed to stymie certain ASICs. The economic incentives exist for ASIC manufacturers to use such a trick to attack each other. Thus, the solution that we are developing is ultimately an adaptive economic human solution rather than purely a technical one.
Scalability
One common concern about Ethereum is the issue of scalability. Like Bitcoin, Ethereum suffers from the flaw that every transaction needs to be processed by every node in the network. With Bitcoin, the size of the current blockchain rests at about 15 GB, growing by about 1 MB per hour. If the Bitcoin network were to process Visa's 2000 transactions per second, it would grow by 1 MB per three seconds (1 GB per hour, 8 TB per year). Ethereum is likely to suffer a similar growth pattern, worsened by the fact that there will be many applications on top of the Ethereum blockchain instead of just a currency as is the case with Bitcoin, but ameliorated by the fact that Ethereum full nodes need to store just the state instead of the entire blockchain history.
The problem with such a large blockchain size is centralization risk. If the blockchain size increases to, say, 100 TB, then the likely scenario would be that only a very small number of large businesses would run full nodes, with all regular users using light SPV nodes. In such a situation, there arises the potential concern that the full nodes could band together and all agree to cheat in some profitable fashion (eg. change the block reward, give themselves BTC). Light nodes would have no way of detecting this immediately. Of course, at least one honest full node would likely exist, and after a few hours information about the fraud would trickle out through channels like Reddit, but at that point it would be too late: it would be up to the ordinary users to organize an effort to blacklist the given blocks, a massive and likely infeasible coordination problem on a similar scale as that of pulling off a successful 51% attack. In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification suggested by Peter Todd (opens in a new tab) which will alleviate this issue.
In the near term, Ethereum will use two additional strategies to cope with this problem. First, because of the blockchain-based mining algorithms, at least every miner will be forced to be a full node, creating a lower bound on the number of full nodes. Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. Even if block validation is centralized, as long as one honest verifying node exists, the centralization problem can be circumvented via a verification protocol. If a miner publishes an invalid block, that block must either be badly formatted, or the state S[n] is incorrect. Since S[0] is known to be correct, there must be some first state S[i] that is incorrect where S[i-1] is correct. The verifying node would provide the index i , along with a "proof of invalidity" consisting of the subset of Patricia tree nodes needing to process APPLY(S[i-1],TX[i]) -> S[i] . Nodes would be able to use those nodes to run that part of the computation, and see that the S[i] generated does not match the S[i] provided.
Another, more sophisticated, attack would involve the malicious miners publishing incomplete blocks, so the full information does not even exist to determine whether or not blocks are valid. The solution to this is a challenge-response protocol: verification nodes issue "challenges" in the form of target transaction indices, and upon receiving a node a light node treats the block as untrusted until another node, whether the miner or another verifier, provides a subset of Patricia nodes as a proof of validity.
The Ethereum protocol was originally conceived as an upgraded version of a cryptocurrency, providing advanced features such as on-blockchain escrow, withdrawal limits, financial contracts, gambling markets and the like via a highly generalized programming language. The Ethereum protocol would not "support" any of the applications directly, but the existence of a Turing-complete programming language means that arbitrary contracts can theoretically be created for any transaction type or application. What is more interesting about Ethereum, however, is that the Ethereum protocol moves far beyond just currency. Protocols around decentralized file storage, decentralized computation and decentralized prediction markets, among dozens of other such concepts, have the potential to substantially increase the efficiency of the computational industry, and provide a massive boost to other peer-to-peer protocols by adding for the first time an economic layer. Finally, there is also a substantial array of applications that have nothing to do with money at all.
The concept of an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique potential; rather than being a closed-ended, single-purpose protocol intended for a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer for a very large number of both financial and non-financial protocols in the years to come.
Notes and Further Reading
- A sophisticated reader may notice that in fact a Bitcoin address is the hash of the elliptic curve public key, and not the public key itself. However, it is in fact perfectly legitimate cryptographic terminology to refer to the pubkey hash as a public key itself. This is because Bitcoin's cryptography can be considered to be a custom digital signature algorithm, where the public key consists of the hash of the ECC pubkey, the signature consists of the ECC pubkey concatenated with the ECC signature, and the verification algorithm involves checking the ECC pubkey in the signature against the ECC pubkey hash provided as a public key and then verifying the ECC signature against the ECC pubkey.
- Technically, the median of the 11 previous blocks.
- Internally, 2 and "CHARLIE" are both numbers fn3 , with the latter being in big-endian base 256 representation. Numbers can be at least 0 and at most 2 256 -1.
Further Reading
- Intrinsic value (opens in a new tab)
- Smart property (opens in a new tab)
- Smart contracts (opens in a new tab)
- B-money (opens in a new tab)
- Reusable proofs of work (opens in a new tab)
- Secure property titles with owner authority (opens in a new tab)
- Bitcoin whitepaper (opens in a new tab)
- Namecoin (opens in a new tab)
- Zooko's triangle (opens in a new tab)
- Colored coins whitepaper (opens in a new tab)
- Mastercoin whitepaper (opens in a new tab)
- Decentralized autonomous corporations, Bitcoin Magazine (opens in a new tab)
- Simplified payment verification (opens in a new tab)
- Merkle trees (opens in a new tab)
- Patricia trees (opens in a new tab)
- GHOST (opens in a new tab)
- StorJ and Autonomous Agents, Jeff Garzik (opens in a new tab)
- Mike Hearn on Smart Property at Turing Festival (opens in a new tab)
- Ethereum RLP (opens in a new tab)
- Ethereum Merkle Patricia trees (opens in a new tab)
- Peter Todd on Merkle sum trees (opens in a new tab)
For history of the whitepaper, see this wiki (opens in a new tab) .
Ethereum, like many community-driven, open-source software projects, has evolved since its initial inception. To learn about the latest developments of Ethereum, and how changes to the protocol are made, we recommend this guide .
Was this article helpful?

Introducing Microsoft 365 Copilot – your copilot for work
Mar 16, 2023 | Jared Spataro - CVP, AI at Work
- Share on Facebook (opens new window)
- Share on Twitter (opens new window)
- Share on LinkedIn (opens new window)
Humans are hard-wired to dream, to create, to innovate. Each of us seeks to do work that gives us purpose — to write a great novel, to make a discovery, to build strong communities, to care for the sick. The urge to connect to the core of our work lives in all of us. But today, we spend too much time consumed by the drudgery of work on tasks that zap our time, creativity and energy. To reconnect to the soul of our work, we don’t just need a better way of doing the same things. We need a whole new way to work.
Today, we are bringing the power of next-generation AI to work. Introducing Microsoft 365 Copilot — your copilot for work . It combines the power of large language models (LLMs) with your data in the Microsoft Graph and the Microsoft 365 apps to turn your words into the most powerful productivity tool on the planet.
“Today marks the next major step in the evolution of how we interact with computing, which will fundamentally change the way we work and unlock a new wave of productivity growth,” said Satya Nadella, Chairman and CEO, Microsoft. “With our new copilot for work, we’re giving people more agency and making technology more accessible through the most universal interface — natural language.”
Copilot is integrated into Microsoft 365 in two ways. It works alongside you, embedded in the Microsoft 365 apps you use every day — Word, Excel, PowerPoint, Outlook, Teams and more — to unleash creativity, unlock productivity and uplevel skills. Today we’re also announcing an entirely new experience: Business Chat . Business Chat works across the LLM, the Microsoft 365 apps, and your data — your calendar, emails, chats, documents, meetings and contacts — to do things you’ve never been able to do before. You can give it natural language prompts like “Tell my team how we updated the product strategy,” and it will generate a status update based on the morning’s meetings, emails and chat threads.
With Copilot, you’re always in control. You decide what to keep, modify or discard. Now, you can be more creative in Word, more analytical in Excel, more expressive in PowerPoint, more productive in Outlook and more collaborative in Teams.
Microsoft 365 Copilot transforms work in three ways:
Unleash creativity. With Copilot in Word, you can jump-start the creative process so you never start with a blank slate again. Copilot gives you a first draft to edit and iterate on — saving hours in writing, sourcing, and editing time. Sometimes Copilot will be right, other times usefully wrong — but it will always put you further ahead. You’re always in control as the author, driving your unique ideas forward, prompting Copilot to shorten, rewrite or give feedback. Copilot in PowerPoint helps you create beautiful presentations with a simple prompt, adding relevant content from a document you made last week or last year. And with Copilot in Excel, you can analyze trends and create professional-looking data visualizations in seconds.
Unlock productivity. We all want to focus on the 20% of our work that really matters, but 80% of our time is consumed with busywork that bogs us down. Copilot lightens the load. From summarizing long email threads to quickly drafting suggested replies, Copilot in Outlook helps you clear your inbox in minutes, not hours. And every meeting is a productive meeting with Copilot in Teams. It can summarize key discussion points — including who said what and where people are aligned and where they disagree — and suggest action items, all in real time during a meeting. And with Copilot in Power Platform, anyone can automate repetitive tasks, create chatbots and go from idea to working app in minutes.
GitHub data shows that Copilot promises to unlock productivity for everyone. Among developers who use GitHub Copilot, 88% say they are more productive, 74% say that they can focus on more satisfying work, and 77% say it helps them spend less time searching for information or examples.
But Copilot doesn’t just supercharge individual productivity. It creates a new knowledge model for every organization — harnessing the massive reservoir of data and insights that lies largely inaccessible and untapped today. Business Chat works across all your business data and apps to surface the information and insights you need from a sea of data — so knowledge flows freely across the organization, saving you valuable time searching for answers. You will be able to access Business Chat from Microsoft 365.com, from Bing when you’re signed in with your work account, or from Teams.
Uplevel skills. Copilot makes you better at what you’re good at and lets you quickly master what you’ve yet to learn. The average person uses only a handful of commands — such as “animate a slide” or “insert a table” — from the thousands available across Microsoft 365. Now, all that rich functionality is unlocked using just natural language. And this is only the beginning.
Copilot will fundamentally change how people work with AI and how AI works with people. As with any new pattern of work, there’s a learning curve — but those who embrace this new way of working will quickly gain an edge.
The Copilot System: Enterprise-ready AI
Microsoft is uniquely positioned to deliver enterprise-ready AI with the Copilot System . Copilot is more than OpenAI’s ChatGPT embedded into Microsoft 365. It’s a sophisticated processing and orchestration engine working behind the scenes to combine the power of LLMs, including GPT-4, with the Microsoft 365 apps and your business data in the Microsoft Graph — now accessible to everyone through natural language.
Grounded in your business data. AI-powered LLMs are trained on a large but limited corpus of data. The key to unlocking productivity in business lies in connecting LLMs to your business data — in a secure, compliant, privacy-preserving way. Microsoft 365 Copilot has real-time access to both your content and context in the Microsoft Graph. This means it generates answers anchored in your business content — your documents, emails, calendar, chats, meetings, contacts and other business data — and combines them with your working context — the meeting you’re in now, the email exchanges you’ve had on a topic, the chat conversations you had last week — to deliver accurate, relevant, contextual responses.
Built on Microsoft’s comprehensive approach to security, compliance and privacy. Copilot is integrated into Microsoft 365 and automatically inherits all your company’s valuable security, compliance, and privacy policies and processes. Two-factor authentication, compliance boundaries, privacy protections, and more make Copilot the AI solution you can trust.
Architected to protect tenant, group and individual data. We know data leakage is a concern for customers. Copilot LLMs are not trained on your tenant data or your prompts. Within your tenant, our time-tested permissioning model ensures that data won’t leak across user groups. And on an individual level, Copilot presents only data you can access using the same technology that we’ve been using for years to secure customer data.
Integrated into the apps millions use every day. Microsoft 365 Copilot is integrated in the productivity apps millions of people use and rely on every day for work and life — Word, Excel, PowerPoint, Outlook, Teams and more. An intuitive and consistent user experience ensures it looks, feels and behaves the same way in Teams as it does in Outlook, with a shared design language for prompts, refinements and commands.
Designed to learn new skills. Microsoft 365 Copilot’s foundational skills are a game changer for productivity: It can already create, summarize, analyze, collaborate and automate using your specific business content and context. But it doesn’t stop there. Copilot knows how to command apps (e.g., “animate this slide”) and work across apps, translating a Word document into a PowerPoint presentation. And Copilot is designed to learn new skills. For example, with Viva Sales, Copilot can learn how to connect to CRM systems of record to pull customer data — like interaction and order histories — into communications. As Copilot learns about new domains and processes, it will be able to perform even more sophisticated tasks and queries.
Committed to building responsibly
At Microsoft, we are guided by our AI principles and Responsible AI Standard and decades of research on AI, grounding and privacy-preserving machine learning. A multidisciplinary team of researchers, engineers and policy experts reviews our AI systems for potential harms and mitigations — refining training data, filtering to limit harmful content, query- and result-blocking sensitive topics, and applying Microsoft technologies like InterpretML and Fairlearn to help detect and correct data bias. We make it clear how the system makes decisions by noting limitations, linking to sources, and prompting users to review, fact-check and adjust content based on subject-matter expertise.
Moving boldly as we learn
In the months ahead, we’re bringing Copilot to all our productivity apps—Word, Excel, PowerPoint, Outlook, Teams, Viva, Power Platform, and more. We’ll share more on pricing and licensing soon. Earlier this month we announced Dynamics 365 Copilot as the world’s first AI Copilot in both CRM and ERP to bring the next-generation AI to every line of business.
Everyone deserves to find purpose and meaning in their work — and Microsoft 365 Copilot can help. To serve the unmet needs of our customers, we must move quickly and responsibly, learning as we go. We’re testing Copilot with a small group of customers to get feedback and improve our models as we scale, and we will expand to more soon.
Learn more on the Microsoft 365 blog and visit WorkLab to get expert insights on how AI will create a brighter future of work for everyone.
And for all the blogs, videos and assets related to today’s announcements, please visit our microsite .
Tags: AI , Microsoft 365 , Microsoft 365 Copilot
- Check us out on RSS

COMMENTS
Define your specific research problem and problem statement. Highlight the novelty and contributions of the study. Give an overview of the paper's structure. The research paper introduction can vary in size and structure depending on whether your paper presents the results of original empirical research or is a review paper.
Research paper introduction is the first section of a research paper that provides an overview of the study, its purpose, and the research question (s) or hypothesis (es) being investigated. It typically includes background information about the topic, a review of previous research in the field, and a statement of the research objectives.
Research paper introduction examples. Full examples of research paper introductions are shown in the tabs below: one for an argumentative paper, the other for an empirical paper. ... Criteria & Examples Research questions give your project a clear focus. They should be specific and feasible, but complex enough to merit a detailed answer. 2613.
1-) Start with a Catchy Hook. Your first sentence is one of the factors that most influence a reader's decision to read your paper. This sentence determines the tone of your paper and attracts the reader's attention. For this reason, we recommend that you start your introduction paragraph with a strong and catchy hook sentence.
The second part of an introduction sums up the most important findings regarding the problem of the article. This part presents the current controversies around the studied issue. The literature review has three main purposes. On the one hand, it positions the research project within a certain scientific tradition.
Dr. Michelle Harris, Dr. Janet Batzli,Biocore. This section provides guidelines on how to construct a solid introduction to a scientific paper including background information, study question, biological rationale, hypothesis, and general approach. If the Introduction is done well, there should be no question in the reader's mind why and on ...
The introduction leads the reader from a general subject area to a particular topic of inquiry. It establishes the scope, context, and significance of the research being conducted by summarizing current understanding and background information about the topic, stating the purpose of the work in the form of the research problem supported by a hypothesis or a set of questions, explaining briefly ...
Overview of the structure. To help guide your reader, end your introduction with an outline of the structure of the thesis or dissertation to follow. Share a brief summary of each chapter, clearly showing how each contributes to your central aims. However, be careful to keep this overview concise: 1-2 sentences should be enough.
Overview of the structure. To help guide your reader, end your introduction with an outline of the structure of the thesis or dissertation to follow. Share a brief summary of each chapter, clearly showing how each contributes to your central aims. However, be careful to keep this overview concise: 1-2 sentences should be enough.
In general, your introductions should contain the following elements: When you're writing an essay, it's helpful to think about what your reader needs to know in order to follow your argument. Your introduction should include enough information so that readers can understand the context for your thesis. For example, if you are analyzing ...
Provide your readers with a road map to help them understand what you will address throughout the research. Be succinct - it is advised that your opening introduction consists of around 8-9 percent of the overall amount of words in your article (for example, 160 words for a 2000 words essay). Make a strong and unambiguous thesis statement.
Research paper introduction example. The following introduction is taken from a research paper exploring the potential uses of the peach palm. We've highlighted each step we mentioned above. Note that some of the steps may overlap a bit; the goal is to include all four components. In this example, the thesis statement appears in Step 4 rather ...
The key thing is. to guide the reader into your topic and situate your ideas. Step 2: Describe the background. This part of the introduction differs depending on what approach your paper is ...
Download Article. 1. Announce your research topic. You can start your introduction with a few sentences which announce the topic of your paper and give an indication of the kind of research questions you will be asking. This is a good way to introduce your readers to your topic and pique their interest.
An introduction is the first paragraph of a written research paper, or the first thing you say in an oral presentation, or the first thing people see, hear, or experience about your project. It has two parts: 1. A general introduction to the topic you will be discussing. 2.
Research proposal examples. Writing a research proposal can be quite challenging, but a good starting point could be to look at some examples. We've included a few for you below. Example research proposal #1: "A Conceptual Framework for Scheduling Constraint Management".
A well written introduction will help make a compelling case for your research proposal. To begin with, the introduction must set context for your research by mentioning what is known about the topic and what needs to be explored further. In the introduction, you can highlight how your research will contribute to the existing knowledge in your ...
Here are the steps you can follow to write an effective project introduction: 1. Write the project introduction last. Because a project introduction discusses the main points from your research or proposal, you should write it once your project is complete. This way, the introduction contains accurate, relevant information.
3. Research project. If the same example is for a research project, then the start of the introduction can be "50 types of medicinal plants that can help mankind live a healthy life." The opening should emphasize what kind of plants can be termed medicinal plants. It will further categorize the plants according to usage or the area they ...
Crucially, citation practices do not differ between the two styles of paper. However, for your convenience, we have provided two versions of our APA 7 sample paper below: one in student style and one in professional style. Note: For accessibility purposes, we have used "Track Changes" to make comments along the margins of these samples.
A letter of introduction and a cover letter are very different. Letters of introduction are generally used when you want to establish a new relationship that may or may not be job-related. It could be an introduction to a potential business partner, a networking contact, or a new community or group. On the other hand, a cover letter is job ...
This is CS50x , Harvard University's introduction to the intellectual enterprises of computer science and the art of programming for majors and non-majors alike, with or without prior programming experience. An entry-level course taught by David J. Malan, CS50x teaches students how to think algorithmically and solve problems efficiently.
aspect of the essay. For example, while it may be acceptable to write a two-paragraph (or longer) introduction for your papers in some courses, instructors in other disciplines, such as those in some Government courses, may expect a shorter introduction that includes a preview of the argument that will follow.
To introduce yourself professionally, you need to consider the situation you're in, use positive body language, and briefly provide information about who you are. If appropriate, ask questions of the person or people you're introducing yourself to as well. Consider the context of the introduction. Adapting your self-introduction to the ...
Examples of literature reviews. Step 1 - Search for relevant literature. Step 2 - Evaluate and select sources. Step 3 - Identify themes, debates, and gaps. Step 4 - Outline your literature review's structure. Step 5 - Write your literature review.
Bachelor of Arts in Communications. University of Washington, Seattle WA. August 20XX - May 20XX. Resident Advisor, August 20XX - May 20XX. 3. Make a section for your major accomplishments. Create an additional section that's relevant to the internship you want and highlights your greatest accomplishments as a student.
Information technology (IT) is the use of any computers, storage, networking and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data.
Ethereum Whitepaper. This introductory paper was originally published in 2014 by Vitalik Buterin, the founder of Ethereum, before the project's launch in 2015. It's worth noting that Ethereum, like many community-driven, open-source software projects, has evolved since its initial inception. While several years old, we maintain this paper ...
And Copilot is designed to learn new skills. For example, with Viva Sales, Copilot can learn how to connect to CRM systems of record to pull customer data — like interaction and order histories — into communications. As Copilot learns about new domains and processes, it will be able to perform even more sophisticated tasks and queries.