- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights

Our Network
- Computerworld
- Network World

Computer viruses explained: Definition, types, and examples
This malicious software tries to do its damage in the background while your computer still limps along..

Computer virus definition
A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself.
Like other types of malware , a virus is deployed by attackers to damage or take control of a computer. Its name comes from the method by which it infects its targets. A biological virus like HIV or the flu cannot reproduce on its own; it needs to hijack a cell to do that work for it, wreaking havoc on the infected organism in the process. Similarly, a computer virus isn’t itself a standalone program. It’s a code snippet that inserts itself into some other application. When that application runs, it executes the virus code, with results that range from the irritating to the disastrous.
Virus vs. malware vs. trojan vs. worm
Before we continue a brief note on terminology. Malware is a general term for malicious computer code. A virus, as noted, is specifically a kind of malware that infects other applications and can only run when they run. A worm is a malware program that can run, reproduce, and spread on its own , and a Trojan is malware that tricks people into launching it by disguising itself as a useful program or document. You’ll sometimes see virus used indiscriminately to refer to all types of malware, but we’ll be using the more restricted sense in this article.
What do computer viruses do?
Imagine an application on your computer has been infected by a virus. (We’ll discuss the various ways that might happen in a moment, but for now, let’s just take infection as a given.) How does the virus do its dirty work? Bleeping Computer provides a good high-level overview of how the process works. The general course goes something like this: the infected application executes (usually at the request of the user), and the virus code is loaded into the CPU memory before any of the legitimate code executes.
At this point, the virus propagates itself by infecting other applications on the host computer, inserting its malicious code wherever it can. (A resident virus does this to programs as they open, whereas a non-resident virus can infect executable files even if they aren’t running.) Boot sector viruses use a particularly pernicious technique at this stage: they place their code in the boot sector of the computer’s system disk, ensuring that it will be executed even before the operating system fully loads, making it impossible to run the computer in a “clean” way. (We’ll get into more detail on the different types of computer virus a bit later on.)
Once the virus has its hooks into your computer, it can start executing its payload , which is the term for the part of the virus code that does the dirty work its creators built it for. These can include all sorts of nasty things: Viruses can scan your computer hard drive for banking credentials, log your keystrokes to steal passwords, turn your computer into a zombie that launches a DDoS attack against the hacker’s enemies, or even encrypt your data and demand a bitcoin ransom to restore access . (Other types of malware can have similar payloads.)
How do computer viruses spread?
In the early, pre-internet days, viruses often spread from computer to computer via infected floppy disks. The SCA virus, for instance, spread amongst Amiga users on disks with pirated software . It was mostly harmless, but at one point as many as 40% of Amiga users were infected.
Today, viruses spread via the internet. In most cases, applications that have been infected by virus code are transferred from computer to computer just like any other application. Because many viruses include a logic bomb — code that ensures that the virus’s payload only executes at a specific time or under certain conditions—users or admins may be unaware that their applications are infected and will transfer or install them with impunity. Infected applications might be emailed (inadvertently or deliberately—some viruses actually hijack a computer’s mail software to email out copies of themselves); they could also be downloaded from an infected code repository or compromised app store.
One thing you’ll notice all of these infection vectors have in common is that they require the victim to execute the infected application or code. Remember, a virus can only execute and reproduce if its host application is running! Still, with email such a common malware dispersal method, a question that causes many people anxiety is: Can I get a virus from opening an email? The answer is that you almost certainly can’t simply by opening a message; you have to download and execute an attachment that’s been infected with virus code. That’s why most security pros are so insistent that you be very careful about opening email attachments, and why most email clients and webmail services include virus scanning features by default.
A particularly sneaky way that a virus can infect a computer is if the infected code runs as JavaScript inside a web browser and manages to exploit security holes to infect programs installed locally. Some email clients will execute HTML and JavaScript code embedded in email messages, so strictly speaking, opening such messages could infect your computer with a virus . But most email clients and webmail services have built-in security features that would prevent this from happening, so this isn’t an infection vector that should be one of your primary fears.
Can all devices get viruses?
Virus creators focus their attention on Windows machines because they have a large attack surface and wide installed base. But that doesn’t mean other users should let their guard down. Viruses can afflict Macs, iOS and Android devices, Linux machines, and even IoT gadgets. If it can run code, that code can be infected with a virus.
Types of computer virus
Symantec has a good breakdown on the various types of viruses you might encounter , categorized in different ways. The most important types to know about are:
- Resident viruses infect programs that are currently executing.
- Non-resident viruses , by contrast, can infect any executable code, even if it isn’t currently running
- Boot sector viruses infect the sector of a computer’s startup disk that is read first , so it executes before anything else and is hard to get rid of
- A macro virus infects macro applications embedded in Microsoft Office or PDF files. Many people who are careful about never opening strange applications forget that these sorts of documents can themselves contain executable code. Don’t let your guard down!
- A polymorphic virus slightly changes its own source code each time it copies itself to avoid detection from antivirus software.
- Web scripting viruses execute in JavaScript in the browser and try to infect the computer that way.
Keep in mind that these category schemes are based on different aspects of a virus’s behavior, and so a virus can fall into more than one category. A resident virus could also be polymorphic, for instance.
How to prevent and protect against computer viruses
Antivirus software is the most widely known product in the category of malware protection products. CSO has compiled a list of the top antivirus software for Windows , Android , Linux and macOS , though keep in mind that antivirus isn’t a be-all end-all solution . When it comes to more advanced corporate networks, endpoint security offerings provide defense in depth against malware . They provide not only the signature-based malware detection that you expect from antivirus, but antispyware, personal firewall, application control and other styles of host intrusion prevention. Gartner offers a list of its top picks in this space , which include products from Cylance, CrowdStrike, and Carbon Black.
One thing to keep in mind about viruses is that they generally exploit vulnerabilities in your operating system or application code in order to infect your systems and operate freely; if there are no holes to exploit, you can avoid infection even if you execute virus code. To that end, you’ll want to keep all your systems patched and updated, keeping an inventory of hardware so you know what you need to protect, and performing continuous vulnerability assessments on your infrastructure.
Computer virus symptoms
How can you tell if a virus has slipped past your defenses? With some exceptions, like ransomware, viruses are not keen to alert you that they’ve compromised your computer. Just as a biological virus wants to keep its host alive so it can continue to use it as a vehicle to reproduce and spread, so too does a computer virus attempt to do its damage in the background while your computer still limps along. But there are ways to tell that you’ve been infected. Norton has a good list ; symptoms include:
- Unusually slow performance
- Frequent crashes
- Unknown or unfamiliar programs that start up when you turn on your computer
- Mass emails being sent from your email account
- Changes to your homepage or passwords
If you suspect your computer has been infected, a computer virus scan is in order. There are plenty of free services to start you on your exploration: The Safety Detective has a rundown of the best.
Remove computer virus
Once a virus is installed on your computer, the process of removing it is similar to that of removing any other kind of malware—but that isn’t easy. CSO has information on how to remove or otherwise recover from rootkits , ransomware , and cryptojacking . We also have a guide to auditing your Windows registry to figure out how to move forward.
If you’re looking for tools for cleansing your system, Tech Radar has a good roundup of free offerings , which contains some familiar names from the antivirus world along with newcomers like Malwarebytes. And it’s a smart move to always make backups of your files , so that if need be you can recover from a known safe state rather than attempting to extricate virus code from your boot record or pay a ransom to cybercriminals.
Computer virus history
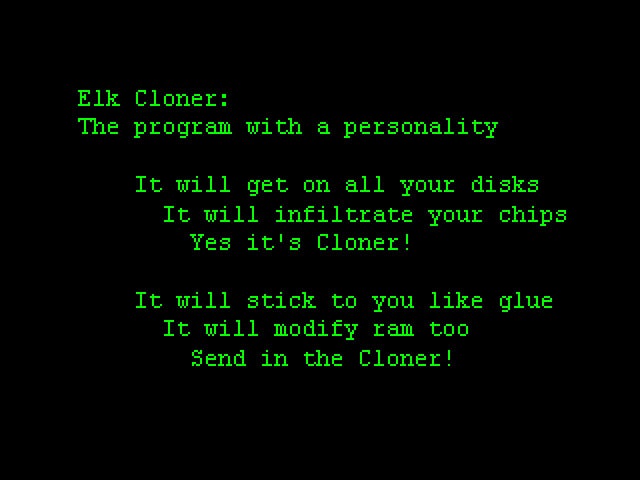
The first true computer virus was Elk Cloner , developed in 1982 by fifteen-year-old Richard Skrenta as a prank. Elk Cloner was an Apple II boot sector virus that could jump from floppy to floppy on computers that had two floppy drives (as many did). Every 50th time an infected game was started, it would display a poem announcing the infection.
Other major viruses in history include:
- Jerusalem : A DOS virus that lurked on computers, launched on any Friday the 13th, and deleted applications.
- Melissa : A mass-mailing macro virus that brought the underground virus scene to the mainstream in 1999. It earned its creator 20 months in prison.
But most of the big-name malware you’ve heard of in the 21st century has, strictly speaking, been worms or Trojans, not viruses. That doesn’t mean viruses aren’t out there, however—so be careful what code you execute.
Related content
Employee discontent: insider threat no. 1, download the hybrid cloud data protection enterprise buyer’s guide, global stability issues alter cyber threat landscape, eset reports, the inside story of cyber command’s creation, from our editors straight to your inbox.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
Ddos attacks: definition, examples, and techniques, social engineering: definition, examples, and techniques, download the zero trust network access (ztna) enterprise buyer’s guide, malware explained: how to prevent, detect and recover from it, most popular authors.

- Microsoft Security
Show me more
Sec rule for finance firms boosts disclosure requirements.

FCC proposes BGP security measures

US AI experts targeted in cyberespionage using SugarGh0st RAT

CSO Executive Sessions: The personality of cybersecurity leaders

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
Advertisement
Introduction: Computer Viruses
By Will Knight
4 September 2006

Any computer connected to the internet faces a daunting range of electronic threats. Perhaps the biggest single threat to any computer is the humble software bug . Seemingly innocuous programming errors can be exploited to force entry into a computer and also provide the weak spots that allow computer worms and viruses to proliferate.
Many software bugs will simply cause a computer to crash . But an expert programmer can sometimes figure out how to make a computer malfunction in a creative way, so that it provides access to secure parts of a system, or shares protected data.
When a software vulnerability is revealed, it is often a race against the clock to apply the correct software patch before an attacker can convert the bug into an “exploit” that can be used to cause major damage.
Viruses and worms
A computer virus is a program that spreads between computers by hiding itself within a – seemingly innocent – document or application. A worm , on the other hand, is a program that replicates and travels without “infecting” anything else on a system.
Many modern specimens of malevolent code, however, use a mixture of tricks to cheat their way onto computer systems, blurring the line between worms and viruses. The terms are now often used interchangeably.
The first worms appeared in the 1970s and spread slowly between computers connected to the same network. They simply displayed an annoying message on the screen of each infected machine. The first computer virus, called Elk Cloner, was written in 1982 and infected computers via floppy disks.
Trojans and zombies
But viruses and worms no longer just provide a way for malevolent hackers to gain notoriety. Today’s viral code can contaminate computers at lightning speed, spreading via email , peer-to-peer file-sharing networks and even instant messaging programs. The most successful ones cause serious damage , forcing companies around the globe to close down while infected computers are cleaned up .
A string of recent specimens have been designed to snatch passwords or credit card information and install programs that can be used to remotely control infected machines. These programs are known as trojan horses .
There is evidence that virus writers can earn large amounts of money by leasing access to networks of compromised computers – often referred to as “botnets” . These groups of remote-controlled “zombies” have been used to extort money from websites, by threatening to crash them with a denial-of-service (DoS) attack. This involves overloading a server with bogus page requests , so that real messages cannot get through.
Spam, Spam, Spam
Spammers have also begun using botnets to forward unsolicited bulk email advertising , or spam, through scores of zombie PCs. This makes it far more difficult for spam hunters to block the messages at source and catch the culprits.
Once considered a fairly minor problem, spam is rapidly spiralling out of control, and much more than half of all email messages are now thought to consist of unwanted advertising messages.
To combat computer scientists’ best efforts to stem the tide of junk email, the spammers have had to become more cunning and sophisticated. More recently, spim ( spam by instant messenger ) and spit ( spam by internet telephony ) have joined the fray.
Spam’s more sinister cousin is the phishing email. This is a con trick that arrives as an email and tries to trick a recipient into handing over money or sensitive personal information like their bank account details or a username and password.
The simplest phishing tricks try to dupe a target into sending money as part of a get-rich-quick scheme. But phishing tricksters are also getting more devious and recent scams pose as customer service emails and send users to bogus banking or commercial websites where they are invited to “re-enter” their account information.
Some genuine sites have even proven vulnerable to software glitches that can be exploited to capture information from regular users. Phishing is especially threatening because it can be used to steal a person’s digital identity .
Along with spam and phishing, spyware represents the third of an unhappy trinity of internet pests. These insidious and clandestine programs typically find their way onto a computer system alongside another, often free, software application, although some can also exploit software bugs to get onto a machine. The programs are used to serve up unwanted adverts, change system settings and gather information on a user’s online behaviour for marketing purposes.
The term “computer hacker” was first coined in the 1960s and originally meant someone capable of developing an ingenious solution to a programming problem. But the phrase has since fallen into disrepute, entering the popular vocabulary as a term for a programmer with criminal intent .
The earliest “criminal” hackers were in fact relatively harmless, interested in testing the boundaries of their knowledge and their ability to get around security measures. They mainly performed innocuous pranks, for example employing low-tech tricks to get free calls through the US phone networks.
There are many tools in the modern hacking kit, including network scanners, packet sniffers, rootkits and decompilers. But “social engineering” – for example, putting a particularly enticing message in an email header to encourage people to open it – and even search engines can also be useful weapons for the hacker.
Computer crime
As the number of computers networks has grown, so have the possibilities for more serious misuse. And, as money increasingly becomes a digital commodity, the world has seen the emergence of serious computer criminals .
Criminal gangs have also started to get in on the action , attracted by the huge quantities of money now spent online every day. There is evidence that unscrupulous experts can also earn serious money from crime syndicates by breaking into computer systems, writing viruses and creating phishing scams.
And it is not just ordinary desktop computers that are under threat. Governments, banks and critical infrastructure can also be brought to a standstill by an expert armed only with a laptop computer and a net connection .
Mobile menace
The biggest new target for computer hackers is the mobile device . Virus writers are already experimenting with code designed for smartphones and experts predict more may be on the way , while hackers are also looking at ways to crack handheld devices .
While the internet has transformed global communication beyond recognition, the arms race between those intent on harnessing its power for criminal purposes and those tasked with preventing them has only just begun.
- computer crime
Sign up to our weekly newsletter
Receive a weekly dose of discovery in your inbox! We'll also keep you up to date with New Scientist events and special offers.
More from New Scientist
Explore the latest news, articles and features
Tricks for making AI chatbots break rules are freely available online
Subscriber-only
Hackers can turn computer cables into antenna to steal sensitive data
Us chooses encryption tools to protect us from quantum computers, what is the hertzbleed computer chip hack and should you be worried, popular articles.
Trending New Scientist articles
Computer Viruses, Their Types and Prevention Research Paper
Introduction, types of virus, standard practices to prevent infection.
Computer viruses are somewhat similar to their organic counterparts since they function under the same principles of infecting a system they are introduced to and focus on replication. However, computer viruses are not a natural aspect of software programs; rather, they are purposefully created to carry out various functions, some of which are malicious in nature. Actions such as compromising the integrity of a computer’s security system, introducing flaws in the programming architecture to cause errors, or even cause the hardware to malfunction resulting in its destruction. These are only a few of the possible actions that a computer virus could be responsible for and, as such, show why it is necessary to know about the different types of viruses out there, how they can infect systems and what measures can a user take to either prevent infection or get rid of one.
Macro Virus
The infection vector of a macro virus is through programs that utilize macros such as.doc,.xls, or.ppp. While the extensions may not be familiar, they consist of Microsoft Word, Excel, and Powerpoint. A macro virus infects these files and spreads when it is shared across various emails and USB drives.
Memory Resident Virus
A memory-resident virus is one of the most resilient types of viruses out there since it resides in the RAM of the computer and comes out of stasis every time the computer’s OS is activated. As a result, it infects other open files leading to the spread of the virus.
A worm is a self-replicating virus that focuses on creating adverse effects on your computer. This can consist of deleting critical system files, overwriting program protocols, and taking up valuable CPU processing space. Worm infections are identifiable based on process errors happening all of a sudden as well as a noticeable decline in the performance of your computer.
Trojan viruses are aptly named since they stay hidden in a computer’s system subtly gathering information. Unlike works, the impact of trojans is rarely felt since their primary purpose is to collect information and transmit it to a predetermined location. Banking information, passwords, and personal details are what Trojans are usually after since this enables malicious hackers to use the information in identity theft as well as to illegally access online accounts and transfer funds.
Direct Action Viruses
This type of virus takes action once certain conditions have been met such as when they are executed by the user (i.e. opened or clicked). They are typically found in the system directory and infect the various therein; however, some varieties of direct action viruses tend to change location depending on how they were initially programmed.
While these are only a few examples, they do represent the various types of computer viruses out there and show why it is necessary to devise different methods of combating them.
Why is it Hard to Prevent the Creation of Computer Viruses?
The problem with computer viruses is that they are often created by people that are looking for exploits in computer systems. Since they are intentionally looking for “holes” in the security to use, it is not surprising that it is hard to create a truly impregnable system that can withstand all manner of computer viruses. The problem lies in the fact that computer viruses are not static entities; rather, they continue to evolve based on new programming architecture. This “evolution” is not the viruses itself evolving. Instead, it is the programmers themselves who create new viruses based on additional principles they learn as technology and in turn software development continues to improve. It is due to this that attempts at creating more efficient anti-virus prevention solutions are met with new types of viruses that try to circumvent them. The only way this practice were to stop altogether would be if all virus creation were to stop, an event that is highly unlikely to occur.
Install an Anti-Virus Software Program
One of the best ways of stopping infection is to install an anti-virus program (ex: McAffee, Symantec, Avast). They specialize in scanning programs, identifying a virus based on information from a database, isolating the file, and deleting it if possible. Do note that anti-virus programs are not infallible since new viruses are created almost every day and, as such, the battle between anti-virus companies and virus creators is never-ending.
Do Not Visit Suspicious Websites
Suspicious websites fall under the category of sites that have questionable content or lack the necessary SSL certificates or verifications. These sites often try to draw visitors via advertisements that indicate that free games can be downloaded from the site, or it has other types of content that a person would usually need to pay for to obtain. Torrent websites are often the most visited of these sites since they offer a wide variety of free content that has been illegally obtained by hackers. However, while it may be tempting to download different movies and games, some of these torrent files are often mixed with viruses that can compromise your system’s security. This can lead to instances of identity theft which can cost you several thousand dollars more than the original price of a movie or game that you illegally downloaded. Utilizing anti-virus programs and following the various instructions in this paper should result in a relatively low chance of your computer.
Be Wary of Foreign USB Drives
USB drives are a ubiquitous method for sharing information around campus; however, since people tend to share these drives among their friends, there are instances where an infection in one computer can rapidly spread to others from that single USB. It is due to circumstances such as these that computer owners need to be cautious with any USB drive that they accept. If you know that the drive has been continuously shared, you need to perform an anti-virus scan on it.
Complete System Reformating
In cases where a computer system has become unavoidably infected and has slowed CPU processes to a crawl due to junk data, it is often necessary to perform a complete system reformat. A system reformats consists of the OS and BIOS of the computer being erased and reinstalled. This helps to get rid of any viruses that remain and enables the computer to work properly again, though this is at the cost of all the files on the computer unless they have backups.
All in all, computer viruses can cause considerable damage if the proper precautions are not taken. Utilizing anti-virus programs and following the various instructions in this paper should result in a relatively low chance of your computer.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2020, September 29). Computer Viruses, Their Types and Prevention. https://ivypanda.com/essays/computer-viruses-their-types-and-prevention/
"Computer Viruses, Their Types and Prevention." IvyPanda , 29 Sept. 2020, ivypanda.com/essays/computer-viruses-their-types-and-prevention/.
IvyPanda . (2020) 'Computer Viruses, Their Types and Prevention'. 29 September.
IvyPanda . 2020. "Computer Viruses, Their Types and Prevention." September 29, 2020. https://ivypanda.com/essays/computer-viruses-their-types-and-prevention/.
1. IvyPanda . "Computer Viruses, Their Types and Prevention." September 29, 2020. https://ivypanda.com/essays/computer-viruses-their-types-and-prevention/.
Bibliography
IvyPanda . "Computer Viruses, Their Types and Prevention." September 29, 2020. https://ivypanda.com/essays/computer-viruses-their-types-and-prevention/.
- Malware: Code Red Computer Worm
- The Quick Scan USB Flash Drives for Different Audiences
- Using Free Antivirus Programs: Pros and Cons
- SQL Injection Attacks and Database Architecture
- Bring Your Device Policy and Security in Business
- Information Technology Department Security Measures
- Information Security Implementation in Healthcare
- Open Source Security Testing Methodology
- Security Tips
- Social Media
- Privacy Tips
- Performance Tips
What Is a Computer Virus?
One of the oldest types of computer threats, viruses are nasty bits of malware that hijack your computer’s resources to replicate, spread, and cause all sorts of chaos. Keep reading to learn how viruses work and how you can protect your computer from viruses with common-sense tips and a dedicated cybersecurity tool.
Get it for Mac , PC , Android
Get it for Android , iOS , Mac
Get it for iOS , Android , PC
Get it for PC , Mac , iOS
Computer viruses are just like that. If you’re unlucky enough to catch one (but don’t beat yourself too much if you do, because they are incredibly common), expect havoc to be wrecked on your hard disk — slower PC performance , damaged or destroyed files, and everything in between.
A computer virus definition, Wikipedia-style
Looking for an essay-friendly definition? Here it goes:
A computer virus is a program or piece of code designed to damage your computer by corrupting system files, wasting resources, destroying data or otherwise being a nuisance.
Viruses are unique from other forms of malware in that they are self-replicating — capable of copying themselves across files or other computers without a user's consent.
Basically, they are really contagious.
Virus, malware, Trojan... what's the difference?
Not every piece of software that attacks your PC is a virus. Computer viruses are just one kind of malware (mal-icious soft- ware ). Here are some of the other, most common kinds:
Trojans : like the ancient wooden horse full of attackers it takes its name from, this malware pretends to be harmless legitimate software, or comes embedded in it, in order to trick the user and open up the gates for other malware to infect a PC.
Spyware : with examples such as keyloggers , this kind of malware is designed to spy on users, save their passwords, credit card details, other personal data and online behavior patterns, and send them off to whoever programmed it.
Worms : this malware type targets entire networks of devices, hopping from PC to PC.
Ransomware : this malware variety hijacks files (and sometimes an entire hard drive), encrypts them, and demands money from its victim in exchange for a decryption key (which may or may not work, but it probably won’t).
Adware : this exceedingly irritating kind of malware floods victims with unwanted ads, and opens up vulnerable security spots for other malware to wiggle its way in.
To recap, viruses are just one of several kinds of malware out there. Strictly speaking, Trojans, ransomware , etc, are not computer viruses, though many people use the shorthand “virus” to refer to malware in a general sense. Altough some devices like phones and iPads are not likely to get a virus , they are not immune to other threats.
Why do people make viruses, and what do they do?
Unlike the bio variety, computer viruses don’t just “happen”. They are manufactured, often with great care, intentionally targeting computers, systems and networks.
But what are these viruses used for?
Well, “fun”. Trolling by software, computer code graffiti… The earliest computer viruses were essentially programmers playing around, like the (maybe, probably) first one, known as the Creeper virus back in 1971, which displayed the message “I’m the creeper, catch me if you can!”.
Not quite Sylvia Plath

Or the Stoned virus , which randomly displayed the words “Your computer is stoned. Legalize marihuana!” on your screen (and stayed in stoner character throughout by doing absolutely nothing else).
Or a personal favorite: the virus that pretends to be a message from a well-known software company, offering you a free cup holder if you download and install it, at which point it opens your PC’s CD tray (remember CD trays?).
Sadly, not all viruses are so cuddly. Take it from Batman’s butler: some people just want to watch the world burn — and computer viruses are a very effective way to spread chaos far and wide.
Like the ILOVEYOU virus , which destroyed the files of more than 50 million internet users worldwide, rendered PCs unbootable, copied people’s passwords and sent them to its creators, and caused up to US$9 billion in damages in the year 2000.
Even that amount pales in comparison to the US$37 billion in damages caused by the Sobig.F virus , which stopped computer traffic in Washington DC and grounded Air Canada for a while.
And then there’s the Mydoom virus , which caused such cyber bloating that it’s believed to have slowed worldwide internet traffic by 10% the day of its release.
Yes, there is a tiny, tiny subset of “good” computer viruses — such as the Cruncher virus, which compresses every file that it infects and theoretically tries to help by saving precious hard disk space.
For example, there’s a virus out there labelled Linux. Wifatch which appears to do nothing other than keeping other viruses out of your router . Linux.Wifatch is itself a virus — it infects a device without its user’s consent and coordinates its actions through a peer-to-peer network — but instead of hurting you, it acts as a sort of security guard.
(But still, there are far better ways to secure your router — and even the creators of Linux.Wifatch tell you not to trust it).
Other “well-intentioned” viruses want to act like a vaccine in that they force people, corporations and governments to strengthen their safety measures and therefore become able to repel genuine threats.
Some virus creators argue they make the world safer by pointing out security gaps and flaws that can be exploited by other viruses with truly malicious intentions.
“What could possibly go wrong?”, asked the first ten minutes of every pandemic disaster movie ever made. The truth is that viruses quickly overwhelm the defenses they’re supposed to put to the test — take the Code Red virus , which in true disaster film fashion attacked the White House (OK the White House’s web server but still OMG) and caused 2.6 billion dollars in damage worldwide.
Some vaccine.
How do computer viruses spread?
Here are some common ways in which you can get infected with a computer virus:
Email viruses
Email is one of the favorite means of transportation for computer viruses everywhere. You can get computer viruses through email by:
Opening an attachment . Often named as something harmless (such as “ Your flight itinerary ”), an executable program file (.com, .exe, .zip, .dll, .pif, .vbs, .js, .scr) or macro file type (.doc, .dot, .xls, .xlt, xlsm, .xsltm…).
Opening an email with an infected body. In these days of rich graphics and colors and bells and whistles, some viruses are being transported in the HTML body of the email itself. Many email services disable HTML by default until you confirm you trust the sender.
Instant messaging viruses
Instant messaging (IM) is another means for viruses to spread. Skype, Facebook Messenger, Windows Live Messenger and other IM services are inadvertently used to spread viruses to your contacts with infected links sent through chat messages.
These instant messaging and social media viruses spread wide and fast because it’s far easier to get people to click on a link when it’s delivered in a message coming from someone they trust, as opposed to a an email from a stranger.
File sharing viruses
Peer-to-peer file sharing services like Dropbox, SharePoint or ShareFile can be used to propagate viruses too. These services sync files and folders to any computer linked to a specific account, so when someone (inadvertently or otherwise) uploads a virus-infected file to a file-sharing account, that virus gets downloaded to everyone else with access to that shared folder.
Some file sharing services, such as Google Drive , scan uploaded files for viruses (although it only scans files smaller than 25MB, giving virus spreaders an easy out — they just have to make sure their virus-infected files are larger than that).
But most other services do not scan for viruses at all, so it’s your responsibility to make sure that you’re protected against any potential threats contained in the file they’re downloading.
Software download viruses
Fake antivirus infections are one of the most common types of virus-loaded software downloads. Scammers and cyber criminals use aggressive pop-ups and ads to scare users into believing that a non-existent virus has been detected in their PC, and compels them to download their “antivirus” software in order to clear the threat.
Instead of ridding the computer of viruses, this fake antivirus proceeds to infect the PC with malware, often with devastating consequences for the victim’s files, hard drive, and personal information.
Unpatched vulnerable software
Last but not least, one of the most common (yet most often overlooked) means for viruses to spread is unpatched software.
Unpatched software refers to software and apps which have not been updated with the latest security updates from the developer, in order to plug up security holes in the software itself.
Unpatched software is a major cybersecurity headache for businesses and organizations, but with criminals exploiting vulnerabilities in outdated versions of such popular programs as Adobe Reader, Java, Microsoft Windows or Microsoft Office , us civilians are very much at risk of infection too.
Types of computer virus
Here’s a list of different types of computer viruses currently out there:
Boot Sector Virus
The boot sector is the part of your PC’s hard drive that loads your computer’s operating system — such as Microsoft Windows. A boot sector virus infects the master boot record (MBR), so the virus loads onto the computer memory during startup.
Boot sector viruses used to be propagated mainly via pluggable devices, like USB keys, floppy disks and CD-ROMS. As technology moves on, boot sector viruses have become much rarer, and these days they mostly live on as email attachments.
Examples of boot sector viruses:
Elk Cloner: this early 1980s virus was attached to a game. At the 50th time the game was started, the virus displayed a poem on-screen.
Stoned: the initial variety displayed on-screen messages in favor of the legalization of marihuana. Its signature (though not the virus itself) crept up into the bitcoin blockchain in 2014.
Parity Boot: another “vintage” virus, this one was the most prevalent virus in Germany up to 1996.
Brain: considered to be the first computer virus for MS-DOS, it was created by the Pakistani Alvi brothers as an attempt to protect their medical software from copyright infringement — an attempt that quickly got out of hand, much to their chagrin.
Michelangelo: every year on March 6 (the birthday of artist Michelangelo), this virus would come alive and overwrite the first 100 sectors of a hard drive with nulls, making it impossible for everyday users to retrieve their files.
Direct Action Virus
These viruses are designed to “pass through” your computer: they get in, generally spread around files of a specific type (COM or EXE files, generally), and when they are done, they delete themselves. They are the most common type of virus out there and the easiest to create — which also makes them the simplest to get rid of.
Examples of direct action viruses:
Win64.Rugrat: also known as the Rugrat virus, this early example of direct action virus could would infect all 64-bit executables it could find in the directory and subdirectories in which it was launched.
Vienna virus: the Vienna virus has the distinction of being the first virus to be destroyed by an antivirus. It searches for .com files and destroys some of them while attempting to infect them.
Resident Virus
Unlike the direct action viruses we mentioned before, memory resident viruses actually set up camp in your computer’s primary memory (RAM). This is bad news, because they can keep working even after you’ve rid yourself of the original infector. Some act fast, some do their damage slowly — and are therefore harder to detect.
Examples of memory resident viruses:
Jerusalem virus (a.k.a. Friday 13th virus): after finding its way into your RAM and hiding inside it, this virus would delete programs from your computer on Friday 13, or increase the size of infected programs until they were too big to run.
Onehalf virus: sometimes known as the Freelove virus, or the Slovak Bomber, this virus slowly encrypts its way through your hard disk. Once it’s done with half (and on the 4th, 8th, 10th, 14th, 18th, 20th, 24th, 28th and 30th day of any month), it displays the message “Dis is one half. Press any key to continue…”
Magistr virus: this very destructive virus emails itself to your contact list, deletes every other file, wrecks your CMOS and BIOS — and leaves you insulting messages to boot.
Multipartite Virus
These ultra-versatile viruses double their spreading power by targeting both your files and your boot space. That way, even after you’ve succeeded in removing all the infected files in your computer, the virus still lingers hidden in the boot sector, ready to strike again — and if you clean the boot sector, the virus will re-infect it by jumping from one of the infected files.
Examples of multipartite viruses:
Junkie virus: this multipartite virus was transmitted in a file called HV-PSPTC.ZIP., supposedly a Pacific Strike computer game. Which it wasn’t.
Tequila virus: this one avoids files which contain the letters “v” and “sc” in their name, and likes to display the message “BEER and TEQUILA forever!”

- Shhhh, don't argue with the virus
Invader virus: this one starts off nicely by playing a Mozart tune, but the moment you hit CTRL+ALT+DEL to reboot, it overwrites the first line of your hard disk with a copy of the virus.
Polymorphic Virus
The mutants of the computer virus world, these viruses shape-shift in order to avoid detection, while holding onto their basic threat capabilities. After infecting your files, these viruses replicate themselves in a slightly different way — which makes them very difficult to fully detect and remove.
Examples of polymorphic viruses:
Satanbug virus: despite its let’s face it quite badass name, this polymorphic virus doesn’t intentionally damage your files — but with its up to nine levels of encryption, virus scanners have a hard time removing it from your PC.
VirLock virus: part ransomware, part polymorphic virus, the Win32/VirLock virus encrypts your files and asks you for ransom — but it also changes shape every time it spreads.
Macro Virus
Macro viruses are written in macro language, with the intention of embedding them within software that allows macro mini-programs such as Microsoft Word. That means your PC can be infected by Word Document viruses.
Examples of macro viruses:
Melissa: distributed through email attachments, once this virus infects your PC it makes its way to your Microsoft Outlook mail client and mails itself to the first 50 contacts in your address book, potentially slowing down or even completely disabling servers in a chain reaction of suck.
How do I protect myself against viruses?
By now we have established you definitely don’t want any of these viruses anywhere near your files, your hard drive or your network. Now, let’s look at how you can avoid computer viruses in the first place.

Use antivirus protection
You have to, have to, have to have some form of antivirus software installed in your PC and your smartphone.
An antivirus is your first line of defense against viruses and a whole bunch of other malware that you seriously don’t want to have to deal with. If you think viruses are bad (and they are), there’s stuff out there that’s even worse.
No excuses. Don’t want to fork out money? There are a few exceptionally good free antivirus software choices out there (ahem). Worried the software will slow down your PC? Ours is so light, you won’t even notice it’s there.
If you’re looking for something extra, premium antivirus programs can offer all kinds of added security features - like our Ransomware Protection shield, which stops anyone from hijacking your files and extorting money from you. For instance, we help you find your phone if you lose it, which is pretty neat.
But hey, you don’t have to get our antivirus (even though it’s free and awesome). Just get some antivirus.*
*although (AND THIS IS THE LAST THING WE’LL SAY ABOUT THIS WE PROMISE) you really shouldn’t get just any free antivirus you find laying around out there, because some of them are actually malware carriers in disguise, and some others are just really blah. So for your own good, always go with an antivirus from a cyber security company whose reputation is at least as good as ours.
Use that pretty head of yours
Apart from letting your antivirus detect and remove viruses, you’ll be doing yourself a huge favor by using proper cyber hygiene in the first place and following some basic internet safety tips:
Don’t just click on any link your friends send you on social media — especially if the message is just a link with no context, or if the words in the message don’t quite sound like them. People’s Facebook accounts get hacked and used to spread out viruses and malware. When in doubt, message your friend directly and ask if they really meant to send you that link. Often, the answer will be “What!? No!”
Don’t open any email attachment unless you 100% know what it is. Cyber criminals often rely on your natural curiosity to spread viruses - they tell you you’ve won something, but you haven’t entered any contests; or they send you a “flight itinerary”, but you aren’t planning on going anywhere. So you open the attachment to see what it’s all about, and bam, you’re infected. So, don’t.
Don’t fall for “Your PC is infected!” hysteric messages and pop-ups that aren’t coming directly from your antivirus. There is a very good chance they’re trying to lure you into downloading a fake antivirus and take your money, infect you computer with malware, or both. When our antivirus catches something, we let you know with a satisfying little message, and that’s it. We don’t ask you to download anything else, or pay any money.
Don’t enable macros in Microsoft Office . A few years ago we would have recommend you to disable macros, but Microsoft already does that by default. Which means cyber criminals try to trick you into enabling them with all sorts of dark mind tricks and fake warnings when you receive an infected email. Don’t fall for them.
But seriously. Antivirus. Now.
How do I remove a virus from my computer?
Stopping a virus from getting into your PC is a lot easier than deleting a virus that’s already in your computer, but if you suspect your PC is already infected with a virus, do not fret. We’ve got you covered.
Is your computer infected?
If your computer has become very slow all of a sudden for no particular reason; if you’re being flooded with pop-up messages out of the blue; if programs and apps start by themselves, and you can hear the hum-hum of your hard drive constantly working in the background…
… it may be.
Here’s how you delete a virus
We have a step-by-step guide that tells you how to get rid of computer viruses the safe and easy way. Give it a read. Or, if your phone has been acting oddly lately, check out our detailed guide to learn how to tell if your phone has a virus or other form of nasty malware — and how to get rid of it.
Get Free Virus Protection
Install free AVG AntiVirus for Android to block viruses and prevent threats. Enjoy 24/7 malware protection.
Get Free Threat Protection
Install free AVG Mobile Security for iOS to prevent security threats. Enjoy 24/7 protection for your iPhone or iPad.
Download AVG AntiVirus FREE for PC to block viruses and prevent threats. Enjoy 24/7 malware protection.
Download AVG AntiVirus FREE for Mac to block viruses and prevent threats. Enjoy 24/7 malware protection.
More helpful tips...
The latest security articles.
- What Is Spyware?
- What Is Adware and How to Get Rid of It?
- What Is a Smurf Attack and How to Prevent It
- What’s the Difference Between Malware and Viruses
- What Is Malware? The Ultimate Guide to Malware
- Microsoft Defender vs. Full-Scale Antivirus
- What Is Scareware? Telltale Signs & How to Remove It
- What Is a Logic Bomb Virus and How to Prevent It
- How to Detect and Remove Spyware from Your iPhone
- How to Remove Spyware from a Mac
- How to Remove Spyware From Android
- What Is Malvertising and How to Prevent It
- How to Scan and Remove Malware From Your Router
- What is a Trojan Horse? Is it Malware or Virus?
- How to Check if an Android App Is Safe to Install
- The Ultimate Guide to Mac Security
- Santa: The Greatest Malware of all Time
- Safest and Most Dangerous US States for PCs and Laptops
- Analysis of Banking Trojan Vawtrak
- iPhone Calendar Virus: What Is It and How Do You Get Rid of It?
- How to Get Rid of a Virus & Other Malware on Your Computer
- How to Find and Clean Viruses on Android Phones or iPhones
- Fake Virus Warnings: How to Spot and Avoid Them
- Can iPads Get Viruses? What You Need to Know
- What Is a Macro Virus and How Do I Remove it?
- The Best Free Antivirus Software for 2024
- Can Macs Get Viruses?
- Worm vs. Virus: What's the Difference?
- What Is a Miner Virus and How Can You Remove It?
- A Brief History of Computer Viruses
- Cobalt Strike Ransomware: What Is It and How to Remove It
- The Ultimate Guide to Ransomware
- The Complete Guide to Mac Ransomware and How to Prevent it
- WannaCry Ransomware: What You Need to Know
- What All Android Users Need to Know About Ransomware
- 2017 Petya Ransomware Outbreak — Your Quick Safety Guide
- The Cost of Ransomware
- EternalBlue Exploit: What Is It and Is It Still a Threat?
- How to Tell If Your Phone Is Tapped: 10 Warning Signs
- What Is a Sniffer and How Can You Prevent Sniffing?
- Reporting Identity Theft — What to Do If Your Identity Is Stolen
- Sextortion and Blackmail — What You Need to Know
- Keyloggers: What They Are, Where They Come From, and How to Remove Them
- What Is SQL Injection?
- What Is a Browser Hijacker and How to Remove One
- Zero-Day Attacks: What You Need to Know
- What Is an Exploit in Computer Security?
- How Secure Is My Phone?
- Identity Theft: What It Is & How It Works
- Everything You Need to Know About Rootkits and How to Protect Yourself
- What Is Pharming and How to Protect Against Attacks
- The NSA is Begging You to Update Windows — Here’s Why
- Your Large-Scale Cyberattack Survival Guide
- Man-in-the-Middle Attacks: What They Are and How to Prevent Them
- The Ultimate Guide to Denial of Service (DoS) Attacks
- What Is a Botnet Attack, How Do They Work, and How Can You Protect Yourself?
- Megabugs! A Quick 'n Easy Guide to Meltdown and Spectre
- 7 Essential iPhone Security Tips
- What is DNS Hijacking?
- Analyzing an Android WebView Exploit
- Threat Report Reveals Pre-teen Children Developing Malicious Code
- How to Block Spam Calls on Your iPhone, Android, or Landline
- What Is a Honeypot? Cybersecurity Traps Explained
- What to Do If You Lose Your Phone With Google Authenticator on It
- How To Open, Create, and Convert RAR Files
- What Is a Security Breach and How to Protect Against It
- What Is Venmo? Is It Safe and How Does It Work?
- What Is Rooting on Android?
- Email Spam Guide: How to Stop Getting Spam and Other Junk Email
- Is PayPal Safe and Secure? 10 Tips for Buyers and Sellers
- What Is a CVV Number and How to Keep It Safe
- What Is Blockchain & How Does It Work?
- What to Do If Your Phone Is Lost or Stolen
- Google Dorks: What Are They and How Are Google Hacks Used?
- What Is a Jailbroken iPhone?
- What Is UPnP (Universal Plug and Play) and Is It Safe?
- How to Delete iPhone Calendar Spam
- How to Browse Safely on Public Wi-Fi
- Best Security Apps for Android Phones
- How to Choose a Secure Cryptocurrency Wallet
- What Is the Best Cryptocurrency Exchange?
- How Safe Is Bitcoin, Really?
- The Best iPhone Security Apps
- 5 Ways to Enhance Your Cybersecurity
- The Ultimate Guide to Keeping Your Email Secure
- What Is a Digital Identity and How Can You Protect Yours?
- 5 Tips to Make Working From Home Work for You
- How to Avoid Coronavirus Malware & Misinformation
- The Dirty Truth About USBs
- 5 Common Security & Privacy Misconceptions Busted
- 20:20 Vision — 5 Threats to Watch Out for This
- 5 Feel-Good Charities for the Digital Age
- Cybersecurity Basics
- 5 Cybersecurity To-Dos Before You Travel
- Malware Is Still Spying on You Even When Your Mobile Is Off
- Everything You Need to Know About the First Dark Web Market: the Silk Road Website
- Best Onion Sites to Discover on the Dark Web in 2024
- Why Is My Ping so High? Helpful Tips for Reducing Lag
- What Is Wi-Fi 6 and Do You Need to Upgrade?
- What Is Streaming and How Does It Work?
- What Is a Router and How Does It Work?
- What Is a Cloud Access Security Broker?
- What Is WPA2 (Wireless Protected Access 2)?
- What Is APKPure and Is It Safe to Use on Android?
- What Is the Dark Web and How to Get on It?
- WEP, WPA, or WPA2 — Which Wi-Fi Security Protocol Is Best?
- Fake Website Check: How to Check If a Website Is Safe or Trying to Scam You
- What Is Fake News and How Can You Spot It?
- Is 2020 the Year We Save the Internet?
- Don’t Get Robbed – 7 Tips for Safer Online Shopping
- 5 Fun Ways to Pointlessly Gamble Your Data
- What Kids Do Online May Surprise You. Internet Safety Tips for You and Your Child
- Who is Tracking You Online?
- Avoid These Mistakes When Using Free Wi-Fi
- What's an Ad Blocker (and Should You Get One)?
- Email Security Checklist – 9+1 Tips for Staying Safe
- Sugar Daddy & Sugar Baby Scams: How to Spot a Fake One
- Avoid USPS Text Scams: Beware of Fake Tracking Numbers and Messages
- 6 Ways to Identify a Fake Text Message
- Pretexting: Definition, Examples, and How to Prevent It
- Common Venmo Scams: How to Avoid Them and Stay Protected
- How To Stop and Report Spam Texts on iPhone or Android
- How to Recognize and Report an Internet Scammer
- What Is Spoofing and How to Protect Against It
- What Is Caller ID Spoofing and How to Stop It
- How to Identify a Tech Support Scammer
- What Is Social Engineering and Are You at Risk?
- Deepfake Videos: Is There Anything You Can Do to Protect Yourself?
- ATM and Card Fraud: Protect Your Money at Home or Abroad
- How to Make Travel Plans, the Secure Way
- Check Out These Real-Life Airline Scams
- Why Is The FBI Asking You To Restart Your Router? (hint: hackers)
- Scammers Trying to Steal Netflix Passwords, and More
- What Is a Vishing Attack?
- What Is Spear Phishing and How to Avoid It
- What Is Smishing and How to Avoid It
- What Is Catfishing & How to Spot Warning Signs
- What is Phishing? The Ultimate Guide to Phishing Emails and Scams
- Is Alexa Always Listening To Us?
- Drones: How Do They Work and Are They Safe?
- Is Your TV Watching You?
- Five Types of Risky Smart Devices to Avoid
- Which Is the Most Secure Android Smart Lock?
- The Birds, Bees, and Bots: Why Parents Are Having The Talk Sooner
- 5 Feel-Good Technology Stories From 2020
- AVG Still Supports Windows 7
- AVG Survey Finds that Parents Don’t Know Enough About Their Children’s Online Habits — Do You?
- AVG Evolved: The Future of Antivirus
- AVG Reveals Invisibility Glasses at Pepcom Barcelona
- Endpoint Security: A Guide for Businesses
- Cybersecurity for Small Businesses: Top Tips and Why It Matters
- What Is a Network Security Key and How Do I Find It?
- Best Small Business Antivirus Solutions for 2024
- Security Suite: What Is It and How Can It Protect Your Business?
iPhone Calendar Virus: What Is It and How Do You Get Rid of It? iPhone Calendar Virus: What Is It and How Do You Get Rid of It?

How to Get Rid of a Virus & Other Malware on Your Computer How to Get Rid of a Virus & Other Malware on Your Computer

How to Find and Clean Viruses on Android Phones or iPhones How to Find and Clean Viruses on Android Phones or iPhones
You Might Also Like...

Fake Virus Warnings: How to Spot and Avoid Them Fake Virus Warnings: How to Spot and Avoid Them
Protect your Android against threats with AVG AntiVirus
Protect your iPhone against threats with AVG Mobile Security
- Media Center
Home Products
- Free Antivirus Download
- Internet Security
- Android Antivirus
- Free Mac Antivirus
- Virus Scanning & Malware Removal
- Installation Files
- Beta Downloads
- Driver Updater
Customer Area
- Register Your License
- Anti-Theft Login
- Home Product Support
- Security & Performance Tips
- Online Research
Partners & Business
- Business Antivirus Software
- Partner Support
- Business Support
Privacy | Report vulnerability | Contact security | License agreements | Modern Slavery Statement | Cookies | Accessibility Statement | Do not sell my info | | All third party trademarks are the property of their respective owners.
We use cookies and similar technologies to recognize your repeat visits and preferences, to measure the effectiveness of campaigns, and improve our websites. For settings and more information about cookies, view our Cookie Policy . By clicking “I accept” on this banner or using our site, you consent to the use of cookies.
To read this content please select one of the options below:
Please note you do not have access to teaching notes, an introduction to computer viruses: problems and solutions.
Library Hi Tech News
ISSN : 0741-9058
Article publication date: 14 September 2012
The purpose of this paper is to discuss various types of computer viruses, along with their characteristics, working, effects on the computer systems and to suggest measures for detecting the virus infection in a computer system and to elaborate means of prevention.
Design/methodology/approach
The author undertook an extensive study and review of the literature available online and on relevant web sites on the present topic.
A large number of viruses were found during the study, which are causing serious damages to computer systems. The author suggests ways to detect and prevent the different computer viruses.
Research limitations/implications
The research is based on and limited to the study of the relevant literature available on different relevant web sites.
Practical implications
The research will benefit business organizations, business houses, educational institutions and libraries working in fully computerized environments, in detection of viruses and preventing infection of their computer systems.
Social implications
The society will also benefit by attaining knowledge about the different types of computer viruses and the measures of prevention of infection.
Originality/value
There are a number of studies and articles available on the topic but almost all of them appear to be incomplete in the sense that either they discuss only a limited number of known viruses or suggest only limited ways of prevention. The paper has made an attempt to discuss almost all the computer viruses and every possible way of prevention of infection from them.
- Computer viruses
- Data security
- Computer security
- Information security
- Security measures
Khan, I. (2012), "An introduction to computer viruses: problems and solutions", Library Hi Tech News , Vol. 29 No. 7, pp. 8-12. https://doi.org/10.1108/07419051211280036
Emerald Group Publishing Limited
Copyright © 2012, Emerald Group Publishing Limited
Related articles
We’re listening — tell us what you think, something didn’t work….
Report bugs here
All feedback is valuable
Please share your general feedback
Join us on our journey
Platform update page.
Visit emeraldpublishing.com/platformupdate to discover the latest news and updates
Questions & More Information
Answers to the most commonly asked questions here
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

An introduction to computer viruses: problems and solutions

Related Papers
Springer Series in Wireless Technology
VANDANA ROHOKALE
International Journal of Engineering Sciences & Research Technology
Ijesrt Journal
Madjid Benfriha
International Journal of Computer Science and Information Security (IJCSIS), Vol. 19, No. 11, November 2021
Journal of Computer Science IJCSIS , Ilori Abolaji , Abimbola Afolayan
Malware is a malevolent code, program, or software. It refers to a program that is introduced into a system, often in a hidden (covert) manner, with the aim of compromising the secrecy, probity, or accessibility of the victim's information, data, applications, software, or operating system(OS) or as well as hinder the proper function of the victim's system as well as hinder good user experience. They are usually created to carry out various delictuous and crimeful functions in such a way that their existence is of total negligence, at a minimum initially when they were introduced into the victim's system. Malware infestations and inhibition before year 2000 centered on system attack, denial of service, and so on. However, beyond year 2000 till date, individuals, corporate bodies, and government of nations have been involved with malicious code design and propagation for distributed network breakdown, as well as, cyberwars. Shared ignorance about the nature of malware's development and propagation has resulted in colossal loss for both individuals and corporate organizations. With new malwares emerging daily to join the thousands in existence, it is evident that the virus issue will not go away any time soon. This paper details the history of malwares and their categories, obfuscation techniques, identification and recommendations for preventing malware incidents to all computer users.
Eugene H Spafford
Abstract There has been considerable interest of late in computer viruses. Much of the information available is either of a highly theoretical nature, or describes a specific set of viruses. Neither is useful for providing an overview of how computer viruses work or how to protect against them. This report is a condensed explanation of viruses-their history, structure, and some information on how to deal with their threat. It should provide a general introduction to the topic without requiring the understanding of excessive detail.
joey maravillas
International Journal of Advances in Engineering and Management (IJAEM)
Justin O N Y A R I N Ogala
Malware is a malicious code, program, or piece of software. It refers to a program that is introduced into a system, often invisibly (covertly), to jeopardize the secrecy, integrity, or accessibility of the victim's information, data, applications, software, or operating system (OS), as well as obstruct the victim's system's proper function and obstructing a good user experience. They are frequently constructed to carry out numerous delicious and criminal activities in such a way that their very existence at least when first introduced into the victim's system, is an act of utter neglect. Before 2000, malware infestations and prevention concentrated on system attacks, denial of service, and other methods. Individuals, corporations, and governments have been involved in malicious code design and spread for distributed network collapse and cyberwars since the year 2000. Individuals and businesses have suffered massive losses due to widespread ignorance regarding the nature of malware generation and spreading. With new Malware appearing daily to add to the hundreds already in existence, it is clear that the virus problem is not going away anytime soon. This document covers the history of Malware and its various classifications and obfuscation tactics, detection, and prevention tips for all computer users.
Ramakrishna Govindu
International Journal for Research in Applied Science & Engineering Technology (IJRASET)
IJRASET Publication
Malicious entities utilize malware as a tool to carry out their nefarious plans. Malicious software, sometimes known as malware or mal-ware, is a type of program with malicious intents. Malware and spam both pose severe hazards to the security of systems, raising complex system issues. Malware that compromises computers through a coordinated attack includes worms, trojan horses, botnets, and rootkits. It is challenging to compile convincing evidence because inadequate tools are available, and the system is still in its infancy. This study examined the challenges faced by investigators in their search for a missing person. The author emphasized the need for a novel approach to malware detection that focuses on a robust framework and offered a solution based on a thorough literature evaluation and market research analysis. While market research was carried out to ascertain the precise nature of the current problem, the literature review concentrated on various malware detection tests and methodologies to establish the parameters for developing a solution design.
Nguyen Duy Y
RELATED PAPERS
Digital Game Research Association Japan Proceedings of the 8th conference
Frédéric J N Seraphine
Clases y notas de Concursos y Quiebras - Derecho Argentino
Lucas Fernandez
Supatra Porasuphatana
International Journal of Financial Studies
Marwan Gad-Elkarim
Elektronik Sosyal Bilimler Dergisi
ceren atmaca
Gideon Wekesa
3rd International Conference on Biological, Chemical and Environmental Sciences (BCES-2015) Sept. 21-22, 2015 Kuala Lumpur (Malaysia)
Journal of Chemical & Engineering Data
GEETA SINGH
Nucleic acids symposium series (2004)
Milos Budesinsky
Chemical Communications
Carlos Gustavo Vazquez
Communications in Computer and Information Science
Akila Sarirete
Journal of Labelled Compounds and Radiopharmaceuticals
Francisco Silva
Acta pediátrica española
Alfonso Solar Boga
Alejandra Rodríguez-Estrada
Revista de la Facultad de Medicina Humana
JHONY DE LA CRUZ-VARGAS
John Aquino
International Journal of Molecular Sciences
Derrick Rancourt
Felice Giani (1758 - 1823). Pittore e decoratore nell'età neoclassica
Antonella Mampieri
Administrative Science Quarterly
Kim Cameron
The American Journal of Cardiology
Elena Biagini
investigacion.izt.uam.mx
Raul Garcia
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Optogenetics, the Big Revolution in Brain Study
Intellectual abilities of artificial intelligence, openmind books, scientific anniversaries, edward o. wilson and island biodiversity, featured author, latest book, the history of computer viruses.
On November 10, 1983, a handful of seminar attendees at Lehigh University, Pennsylvania, USA, heard for the first time the term “virus” applied to computing. The use of the word was strange. The virus that was then on everyone’s mind was the one isolated a few months earlier at the Pasteur Institute in Paris that could be the cause of a new disease called AIDS. In the digital world, talking about viruses was almost nonsense. The first PC had been launched on the market just two years earlier and only the most technologically informed were running an Apple II computer or one of its early competitors.

However, when on that day the graduate student from the University of Southern California Fred Cohen inserted a diskette into a VAX11/750 mainframe computer, the attendees noted how code hidden in a Unix program installed itself and took control in a few minutes , replicating and spreading to other connected machines, similar to a biological virus.
Cohen tells OpenMind that it was on November 3 when a conversation with his supervisor, Leonard Adleman, led to the idea of giving the name of virus to that code capable of infecting a network of connected computers. The Cohen virus was simple: “The code for reproduction was perhaps a few lines and took a few minutes to write,” says the author. “The instrumentation and controls took almost a day.”
Cohen published his creation in 1984, in an article that began: “This paper defines a major computer security problem called a virus.” But though the extensive research of Cohen and Adleman in the specialized literature would draw attention to their existence, the truth is that before that first virus defined as such appeared, there had already been earlier cases.
Interactive timeline: A malware history
[+] Full screen
Catch me if you can
In 1971, Robert Thomas, from the company BBN, created Creeper , a program that moved between computers connected to ARPANET and that displayed the message “I’m the creeper: catch me if you can.” According to David Harley, IT security consultant and researcher for the ESET company, “in the research community, we usually consider the experimental program Creeper to be the first virus and/or worm.”
Moreover, a year before Cohen’s seminar, 15-year-old Rich Skrenta developed Elk Cloner, the first computer virus—not named that yet—that spread outside a laboratory. Skrenta created it as a joke for his friends, whose Apple II computers became infected by inserting a diskette with a game that hid the virus.
So, Cohen was not really the first one. But according what computer security expert Robert Slade explains to OpenMind, the special thing in Cohen’s case was not so much his programming as his method. “He was doing the original academic research on the concept; his structure of antiviral software is still comprehensive despite all the developments since.” Cohen also introduced an informal definition of virus: “a program that can infect other programs by modifying them to include a, possibly evolved, version of itself.”
Those first viruses were technological demonstrations. The motivation of their creators was research and their codes were not malicious. Cohen points out that the objective of his program was “to measure spread time, not to attack.” In the case of Creeper , it was about designing a mobile application that could move to the machine where the data resided, instead of going the other way. As the professor of Computer Science at the University of Calgary (Canada) John Aycock points out to OpenMind, computer viruses were born as “a natural product of human curiosity.” And as such, “their invention was inevitable.”
The first malicious codes
It was also inevitable that the first malicious codes would soon emerge. In 1986, Brain appeared, a virus created by two Pakistani brothers whose purpose was to punish the users of IBM computers who installed a pirated copy of software developed by them. However, the effects of Brain were slight and the virus included the contact information of its authors so that those affected could contact them and request a cure. Spread by means of diskettes, Brain reached international diffusion, giving rise to the birth of the first antivirus companies.

At the end of the 1980s, codes began to proliferate that erased data or disabled systems. In 1988, the worm created by Robert Morris infected many of the computers connected to the then nascent Internet, especially in research institutions, causing a drop in email services. Its effects were more damaging than anticipated by Morris himself, who became the first person to be prosecuted in the US under the Computer Fraud and Abuse Act of 1986.
In this way, so-called malware began to diversify into different families: worms are programs that move from one computer to another without hiding in another application, while Trojans are harmful programs with an innocent appearance. In 1995, WM/Concept appeared, which infected Word documents. “It opened the door for a plague of document-borne malware that dominated the threat landscape for several years after,” says Harley. The expert lists other typologies that have emerged over time, such as bots that manipulate other people’s systems to launch spam campaigns, send malware or denial of service attacks; or ransomware , codes that hijack a system and force the payment of a ransom, such as the recent case of WannaCry , which in May 2017 infected hundreds of thousands of computers in more than 150 countries.

To this threat landscape we must add the current media, such as social networks, which facilitate the expansion of malware. As explained to OpenMind by Jussi Parikka, expert in technological culture at the Winchester School of Art of the University of Southampton (United Kingdom) and author of Digital Contagions: A Media Archeology of Computer Viruses (2nd ed., Peter Lang Publishing, 2016), “the online platforms for communication and interaction are themselves part of the problem due to their various security issues.”
But despite the many headaches caused by the malware, experts point out that these developments can benefit other technologies. Cohen argues that “benevolent” viruses can, for example, be useful in maintaining and updating systems. “I think artificial life (reproducing programs) still have enormous potential, largely unrealized as of today,” he reflects. “History will tell, but I still hold hope that viral computation will be a benefit to humanity in the future.”
Javier Yanes
More publications related to this article, more about technology, artificial intelligence, digital world, visionaries, more publications about ventana al conocimiento (knowledge window), comments on this publication.
Morbi facilisis elit non mi lacinia lacinia. Nunc eleifend aliquet ipsum, nec blandit augue tincidunt nec. Donec scelerisque feugiat lectus nec congue. Quisque tristique tortor vitae turpis euismod, vitae aliquam dolor pretium. Donec luctus posuere ex sit amet scelerisque. Etiam sed neque magna. Mauris non scelerisque lectus. Ut rutrum ex porta, tristique mi vitae, volutpat urna.
Sed in semper tellus, eu efficitur ante. Quisque felis orci, fermentum quis arcu nec, elementum malesuada magna. Nulla vitae finibus ipsum. Aenean vel sapien a magna faucibus tristique ac et ligula. Sed auctor orci metus, vitae egestas libero lacinia quis. Nulla lacus sapien, efficitur mollis nisi tempor, gravida tincidunt sapien. In massa dui, varius vitae iaculis a, dignissim non felis. Ut sagittis pulvinar nisi, at tincidunt metus venenatis a. Ut aliquam scelerisque interdum. Mauris iaculis purus in nulla consequat, sed fermentum sapien condimentum. Aliquam rutrum erat lectus, nec placerat nisl mollis id. Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Nam nisl nisi, efficitur et sem in, molestie vulputate libero. Quisque quis mattis lorem. Nunc quis convallis diam, id tincidunt risus. Donec nisl odio, convallis vel porttitor sit amet, lobortis a ante. Cras dapibus porta nulla, at laoreet quam euismod vitae. Fusce sollicitudin massa magna, eu dignissim magna cursus id. Quisque vel nisl tempus, lobortis nisl a, ornare lacus. Donec ac interdum massa. Curabitur id diam luctus, mollis augue vel, interdum risus. Nam vitae tortor erat. Proin quis tincidunt lorem.
Echolocation: The Sixth Sense of Humans?
Do you want to stay up to date with our new publications.
Receive the OpenMind newsletter with all the latest contents published on our website
OpenMind Books
- The Search for Alternatives to Fossil Fuels
- View all books
About OpenMind
Connect with us.
- Keep up to date with our newsletter
- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
- Ethical Hacking Tutorial
Introduction to Ethical Hacking
- What is Hacktivism ?
- Methodology followed by the Hackers
- Remote Access in Ethical Hacking
- Kali Linux - Information Gathering Tools
- ARIN in Ethical Hacking
- Basic characteristics of Computer Networks
Foot Printing and Reconnaissance
- What is DNS Footprinting?
- Footprinting Through Search Engines
- What is Whois Footprinting?
- Footprinting Using Social Engineering Method
Scanning Networks
- What is Credentialed Vulnerability Scan?
- What are Scanning Attacks?
- Malware Scan in Ethical Hacking
- What is Running of a Malware Scan?
- WAScan - web application security scanner in Kali Linux
- What is TCP-ACK Scanning?
- Port Scanning Techniques By Using Nmap
- What is SYN Scanning?
- What is UDP Scanning?
Enumeration
- Cyber Security - Types of Enumeration
- What is DNS Enumeration?
- SMTP Enumeration
- LDAP Enumeration
- What is NTP Enumeration?
- What is IPsec Enumeration?
- What is NetBIOS Enumeration?
- SNMP Enumeration
- What is Security Testing in Enumeration?
System Hacking
- What is System Hacking in Ethical Hacking?
- What is Windows Hacking ?
- Importance of Physical Security in Ethical Hacking
- What is Non-Electronic Password Attack on a System?
- What is Password Guessing Attack?
- Credential Stuffing in Ethical Hacking
- Reverse Brute Force Attack in System Hacking
- Brute Force Attack
- What is a Default Password Attack Threat?
- USB Drop Attack in System Hacking
- What is Sniffing Attack in System Hacking?
- How to Prevent Man In the Middle Attack?
- How To Generate Rainbow Table Using WinRTGen?
- What is Elcomsoft Distributed Password Recovery?
- pwdump7 in System Hacking
- FGDUMP in System Hacking
- Password Auditing With L0phtcrack 7 Tool
- What is Salted Password Hashing?
- How to Hack Wifi Using Aircrack-ng in Termux Without Root?
- How to Defend Against Password Cracking of Systems?
- How to Defend Against Wi-Fi Pineapple?
- What is DLL Hijacking?
- How to Prevent Privilege Escalation?
Malware Analysis
- Most Popular Methods Used By Hackers to Spread Ransomware
- What is Malvertising?
- How to Find Trojan on Computers?
- Malwares - Malicious Software
- What is WannaCry? How does WannaCry ransomware work?
- Working of Stuxnet Virus
- CryptoLocker Ransomware Attack
- What is Zeus Malware?
- What is SQL Slammer Virus?
- How to Install Trojan Virus on Any Computer?
- Different Ways to Remove Trojan Horse Malware
- How to Defend Against Botnets ?
- What is Proxy Trojan?
- What are Banking Trojans?
What is a Computer Virus?
- Difference between Worms and Virus
- Port Scanning Attack
- What is System Integrity Check?
- Code Emulation Technique For Computer Virus Detection
- Heuristic Virus
- How to Prevent Backdoor Attacks?
- What are Active Sniffing Attacks?
- What is Protocol Analyzer?
- What is MAC Spoofing Attack?
- How to Prevent MAC Flooding?
- What is Port Stealing?
- Dynamic Host Configuration Protocol (DHCP)
- DHCP Starvation Attack
- What is Rogue DHCP Server Attack?
- What is ARP Spoofing Attack?
- How to Prevent DNS Poisoning and Spoofing?
- DNS Spoofing or DNS Cache poisoning
- How to Detect Sniffer in Your Network?
- Mitigation of DHCP Starvation Attack
Social Engineering
- Social Engineering - The Art of Virtual Exploitation
- What is Insider Attack?
- What is an Impersonation Attack?
- What are Tailgating?
- How Hackers Use Social Engineering to Get Passwords on Facebook?
- Pretexting in Social Engineering
- Credit Card Frauds
- Active Social Engineering Defense (ASED)
- Cyber Crime - Identity Theft
- Penetration Testing - Software Engineering
Denial-of-Service
- Distributed Denial of Service DDoS attack
- What are Bandwidth Attacks?
- HTTP Flood Attack
- ICMP Flood DDoS Attack
- Ping Flood Attack
- What is a Permanent DoS (PDoS) Attack?
- What is Phlashing?
- Session Hijacking
- TCP/IP Hijacking
- UDP Session Hijacking
- What are Types of Session Hijacking ?
- Difference Between Spoofing and Hijacking
- Application Level Hijacking Using Proxy Hacking
- Man-in-the-Browser Attack
- DOM-Based Cookie Manipulation
- What are Session Replay Attacks?
- What is Cookie Hijacking?
- Session Prediction Software Attack
- Types of Client-Side Attacks
- Difference Between XSS and SQL Injection
- How SYN cookies are used to preventing SYN Flood attack
- IPSec Architecture
Evading IDS,Firewalls,and Honeypots
- Bypass Firewalls Using SSH
- What is Bitvise SSH Client?
- How to Prevent Port Scan Attacks?
- What is Source Port Randomization For Caching DNS ?
- Types of Evasion Technique For IDS
Hacking Web Servers
- Web Threat Shield
- Web Reputation
- What is Recursive DNS?
- Path Traversal Attack and Prevention
- What is Server Misconfiguration?
- Web Cache Poisoning
- How to Brute-Force SSH in Kali Linux?
- How to Hack a Web Server?
- Testing For IMAP SMTP Injection
- Web Parameter Tampering Attack on Web Servers
- How To Crack Online Web Form Passwords?
- How to Crack FTP Passwords?
- Cookie Tampering Techniques
- What is Input Validation Attack?
- Ethical Hacking | Footprinting
- Parsero - Tool for reading the Robots.txt file in Kali Linux
- What is Credential Harvester Attack ?
- Script Http-Userdir-Enumeration Method
- Linux - Metasploit Command
- Working with Payload Metasploit in Kali Linux
- What is Code Access Security?
- CRLF Injection Attack
- What is Patch Management?
Hacking Web Applications
- What is Cookie Poisoning?
- What are Injection Flaws?
- How to Prevent Broken Access Control?
- What is Improper Error Handling?
- What is Log Tampering?
- OWASP Top 10 Vulnerabilities And Preventions
- Insecure Cryptographic Storage Vulnerability
- Web Server and its Types of Attacks
- Insufficient Transport Layer Protection
- What is Failure to Restrict URL Access?
- Session Fixation Attack
- What is Malicious File Execution?
- What is CSV Injection?
- Converting a CVE list to Patch Vulnerabilities
- What is Arbitrary Code Execution?
- Malicious Script
- What is User Privileges in Ethical Hacking ?
- What is CAPTCHA Attack?
- What is Banner Grabbing?
- WhatWaf - Detect And Bypass Web Application Firewalls And Protection Systems
- User Directed Spidering with Burp
- What is Attack Surface?
- What is Authentication Attack?
- User Enumeration in Ethical Hacking
- What is SMTP Header Injection?
- What is Canonicalization Attack?
- How a Connection String Injection Attack is Performed?
- What is Connection String Parameter Pollution?
- Pass-the-Hash (PtH) Attack
- What is WSDL Attack?
- Types of SQL Injection (SQLi)
Hacking Wireless Networks
- Orthogonal Frequency-Division Multiplexing (OFDM)
- Direct Sequence Spread Spectrum in Wireless Networks
- Frequency-Hopping Spread Spectrum in Wireless Networks
- Warchalking in Wireless Networks
- Types of WiFi Antenna in Wireless Networks
- Types of Wireless Security Encryption
- WEP Crack Method in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- BlueSmack Attack in Wireless Networks
- How To Install Super Bluetooth Hack on Android?
- Bluebugging in Wireless Networks
Cloud Computing
- Net-Centric Computing in Cloud Computing
- Security Issues in Cloud Computing
- Packet Switched Network (PSN) in Networking
- What is Parallel File System in Cloud Computing?
- How To Install AWS CLI - Amazon Simple Notification Service (SNS)?
- How to Authorize Inbound Traffic For Your Linux Instances?
- How To Multiple IP Addresses Work in Ethical Hacking?
Cryptography
- What is Heartbleed Bug in Ethical Hacking ?
- Email Hijacking
- What is Hybrid Cryptosystem in Ethical Hacking?
A computer virus is a type of malicious software program (“ malware “) that, when executed, replicates itself by modifying other computer programs and inserting its code. When this replication succeeds , the affected areas are then said to be “ infected “. Viruses can spread to other computers and files when the software or documents they are attached to are transferred from one computer to another using a network , a disk , file-sharing methods , or through infected email attachments.
A computer virus is a type of harmful program . When it runs, it makes copies of itself and adds its code to other programs and files on your computer. These viruses come in different types , and each type can affect your device differently . Simply put, a computer virus changes how your computer works and aims to spread to other computers. It does this by attaching itself to normal programs or documents that can run code, known as macros .
What Does a Computer Virus Do?
A virus can harm or destroy data , slow down system resources , and log keystrokes , among other things. A virus can have unexpected or harmful outcomes during this procedure, such as destroying system software by corrupting data. Some viruses are made to mess things up by deleting files , messing up programs , or even wiping out your hard drive completely. Even if they’re not super harmful, viruses can still slow down your computer a lot, using up memory and making it crash often . Others might just make copies of themselves or send so much stuff over the internet that it’s hard to do anything online.
Virus vs. Malware – What is the difference?
Viruses and malware are often used interchangeably, but they’re not quite the same. Here’s how they differ:
History of Computer Virus
Viruses have been attacking various devices for a long time, spreading through the Internet or other means. They are often created to steal information or completely ruin devices. The first computer virus, called the “ Creeper system ,” appeared in 1971 as an experimental virus that could copy itself. Following that, in the mid-1970s , the “ Rabbit ” virus emerged , which replicated very quickly and caused significant damage at the same pace. The virus known as “ Elk Cloner ” was created in 1982 by Rich Skrenta . It spread through a floppy disk containing a game and attached itself to the Apple II operating system.
The first virus for MS-DOS , called “ Brain ,” appeared in 1986 . It was designed by two Pakistani brothers and overwrote the boot sector of floppy disks , making it impossible for the computer to start. It was originally meant to be a copy protection system. In 1988 , more destructive viruses began to surface. Until then, most viruses were considered pranks with funny names and messages. However, in 1988, “ The Morris ” became the first widely spreading virus.
How To Prevent Your Computer From Viruses?
Keeping your computer safe from viruses is a lot like keeping yourself from catching a cold. Just as you might wash your hands regularly or avoid sick friends, there are simple steps you can take to protect your computer. Here are some easy tips:
1. Install Antivirus Software: Think of antivirus software as your computer’s doctor. It works around the clock to detect and block viruses before they can infect your system. Make sure to keep it updated!
2. Update Regularly: Keep your operating system , software , and apps up to date . Updates often include fixes for security vulnerabilities that viruses could exploit.
3. Be Cautious with Emails and Downloads: Don’t open emails or download attachments from unknown sources. If an email looks suspicious , even if you know the sender, it’s best to delete it.
4. Use Strong Passwords: Protect your accounts with strong , unique passwords . Consider using a password manager to keep track of them all.
5. Backup Your Data: Regularly back up your data to an external drive or cloud storage . If a virus does slip through , you won’t lose everything.
By following these steps, you can help keep your computer virus-free and running smoothly.
How To Remove Computer Viruses?
To remove a computer infection, you can choose from two options:
Do-it-yourself manual approach: This means you try to fix the problem on your own. Usually, you start by searching online for solutions. Then, you might have to do a lot of tasks to clean up your computer . It can take time and might need some experience to finish everything.
Get help from a reliable antivirus product: Another option is to use antivirus software . This software is designed to find and remove viruses from your computer. You just need to install it and let it do its job.
What is Antivirus?
Antivirus software is a program that searches for, detects , prevents , and removes software infections that can harm your computer. Antivirus can also detect and remove other dangerous software such as worms , adware , and other dangers . This software is intended to be used as a preventative measure against cyber dangers , keeping them from entering your computer and causing problems . Antivirus is available for free as well. Anti-virus software that is available for free only provides limited virus protection, whereas premium anti-virus software offers more effective security. For example Avast , Kaspersky , etc.
Also Check :
Anti-Virus | Its Benefits and Drawbacks How an Antivirus Works?
Different Types of Computer Virus
Each type has a unique way of infecting and damaging computers. Here are a few examples:
How do computer viruses spread?
Through the following activities you may get your device infected by the virus :
1. Sharing the data like music , files , and images with each other.
2. If you open a spam email or an attachment in an email that is sent by an unknown person.
3. Downloading the free game s, toolbars , media players, etc.
4. Visiting a malicious website .
5. Installing pirated software (s) etc.
Examples of Computer Viruses
A computer virus is a type of software designed to spread from one computer to another, similar to how a cold spreads between people. Just like a cold virus can make us sick, a computer virus can harm a computer’s performance and security . Here are some common examples of computer viruses:
These examples show how diverse computer viruses can be in their methods of infection and damage. Knowing about them can help you understand the importance of having reliable antivirus software and practicing safe browsing habits.
In conclusion, understanding what a computer virus is and recognizing the dangers it poses is crucial for keeping your data safe. These viruses are designed to infect , replicate , and damage the functioning of computers. Protecting your computer with antivirus software , being cautious with email attachments , and avoiding suspicious websites are essential steps to prevent virus infections. By staying informed and attentive , you can help safeguard your computer from the potential destruction caused by computer viruses.
What is a Computer Virus? – FAQs
How can you protect your computer system from viruses.
We can use antivirus software to keep your computer safe from viruses. Antivirus software works by comparing the files and programs on your computer to a database of known malware types. It will also monitor computers for the presence of new or undiscovered malware threats , as hackers are constantly generating and propagating new viruses.
What are computer virus infection sources.
The sources via which you can infect your system with viruses are : 1. Downloading programs/software from the internet. 2. Emails 3. External devices like pen-drives 4. Using an unknown CD to Boot data 5. Bluetooth / infrared
Computer viruses are typically propagated by email, file sharing, or CDs or by downloading file(s) from unauthenticated sources.
What is an Anti-Virus?
An anti-virus is a piece of software that consists of programs or a collection of programs that can detect and remove all unsafe and malicious software from your system. This anti-virus software is created in such a way that it can look through a computer’s files and d etect which files are heavily or moderately infected by a virus.
Please Login to comment...
Similar reads.
- School Learning
- School Programming
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

IMAGES
VIDEO
COMMENTS
computer virus, a portion of a computer program code that has been designed to furtively copy itself into other such codes or computer files. It is usually created by a prankster or vandal to effect a nonutilitarian result or to destroy data and program code or, in the case of ransomware, to extort payment. A virus consists of a set of ...
The hackers who design most common computer viruses usually come up with the names (US-CERT, 2012). Some of these viruses include Melissa, the Anna Kournikova, MyDoom, Sasser & Netsky, the ILOVEYOU virus, The Klez Virus, Code Red and Code Red II, Nimda virus, SQL Slammer/Sapphire virus, Leap-A/Oompa-A virus, and Storm Worm (US-CERT, 2012).
Hex dump of the Brain virus, generally regarded as the first computer virus for the IBM Personal Computer (IBM PC) and compatibles. A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus ...
Computer virus definition. A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself. Like other types of malware, a ...
or copy data from computer to computer. viruses can be transmitted via computer. syste ms, an inte rnal network or the. internet. Once a computer system gets. infected with a virus, the data ...
Computer Viruses: an Introduction - University of Wollongong
A computer virus is a program that spreads between computers by hiding itself within a - seemingly innocent - document or application. A worm, on the other hand, is a program that replicates ...
A worm is a self-replicating virus that focuses on creating adverse effects on your computer. This can consist of deleting critical system files, overwriting program protocols, and taking up valuable CPU processing space. Worm infections are identifiable based on process errors happening all of a sudden as well as a noticeable decline in the ...
R. Brown. This thesis is entitled An Analysis of Computer Virus Construction, Proliferation, and Control and is available through the University of Tennessee Library. This paper contains an overview of the computer virus arena that can help the reader to evaluate the threat that computer viruses pose. The extent of this threat can only be
A computer virus is a program or piece of code designed to damage your computer by corrupting system files, wasting resources, destroying data or otherwise being a nuisance. Viruses are unique from other forms of malware in that they are self-replicating — capable of copying themselves across files or other computers without a user's consent.
An introduction to computer viruses: problems and solutions - Author: Imran Khan - The purpose of this paper is to discuss various types of computer viruses, along with their characteristics, working, effects on the computer systems and to suggest measures for detecting the virus infection in a computer system and to elaborate means of ...
Introduction of Computer Virus. Computer Virus is a program that copies itself, Computer virus can infect your computer and slowing down your computer. And virus also can spreads computer to computer. The person who sends out the computer virus may use networking of the internet. The computer virus also can be spread by via disk, CD, thauDVD or ...
An introduction to computer viruses: problems and solutions Imran Khan Introduction The development of large-scale complex campus networks needs to be concerned with network security so that the campus network remains stable. In today's information age, the pool of information available continues to expand logarithmically. ...
An introduction to computer viruses. D. Brown. Published 1 March 1992. Computer Science. TLDR. An overview of the computer virus arena is contained that can help the reader to evaluate the threat that computer viruses pose and support solid general computer security practices as a means of combating computer viruses. Expand.
Cohen tells OpenMind that it was on November 3 when a conversation with his supervisor, Leonard Adleman, led to the idea of giving the name of virus to that code capable of infecting a network of connected computers. The Cohen virus was simple: "The code for reproduction was perhaps a few lines and took a few minutes to write," says the author.
Inf. Manag. Comput. Secur. 2002. TLDR. The purpose of this paper is to apply the analytic hierarchy process (AHP), a well‐known multiple criteria decision making method, which is designed for decisions that require integration of quantitative and qualitative data, to evaluate and select an antivirus and content filtering software. Expand.
1 Introduction: 1.1 Definition of computer virus A computer virus is Program or a portion of the codes that enter into the computer to target vandalism and characterized by their ability to copy itself to many copies and their ability to move from place to place and from computer to computer, disappearances and contents cover. 1.2 History: Many types of computer virus has been spreading in ...
A computer virus is a type of malicious software program ("malware") that, when executed, replicates itself by modifying other computer programs and inserting its code. When this replication succeeds, the affected areas are then said to be "infected". Viruses can spread to other computers and files when the software or documents they ...
Abstract. The computer virus is a problem to computer users at all levels including students, home users, corporate users, system administrators, corporate managers and even the anti-virus manufacturers. The viruses are written by people with malefic intentions to trouble the innocent users. There are many types of viruses are boot sector ...
An introduction to computer viruses. ... This report on computer viruses is based upon a thesis written for the Master of Science degree in Computer Science from the University of Tennessee in December 1989 by David R. Brown. This thesis is entitled An Analysis of Computer Virus Construction, Proliferation, and Control and is available through ...
5- To keep multiple backup copies of all your files before installing any new programs. 6- Processing computer with an anti-virus and always updated to ensure that detect new viruses. 7- Always updated operating system and support it by the windows defender .
Introduction of Computer Virus. Computer Virus is a program that copies itself, Computer virus can infect your computer and slowing down your computer. And virus also can spreads computer to computer. The person who sends out the computer virus may use networking of the internet. The computer virus also can be spread by via disk, CD, thauDVD or ...
Computer Virus Essay Introduction Computer Virus Essay Introduction 2. The Importance Of Fanatic Discipline In Nursing As look to the future, I become excited about the possibilities that lay ahead. I was captured by Collins with these words, We cannot predict the future. But we can create it (p.1).