embedded systems Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords

A Modular End-to-End Framework for Secure Firmware Updates on Embedded Systems
Firmware refers to device read-only resident code which includes microcode and macro-instruction-level routines. For Internet-of-Things (IoT) devices without an operating system, firmware includes all the necessary instructions on how such embedded systems operate and communicate. Thus, firmware updates are essential parts of device functionality. They provide the ability to patch vulnerabilities, address operational issues, and improve device reliability and performance during the lifetime of the system. This process, however, is often exploited by attackers in order to inject malicious firmware code into the embedded device. In this article, we present a framework for secure firmware updates on embedded systems. This approach is based on hardware primitives and cryptographic modules, and it can be deployed in environments where communication channels might be insecure. The implementation of the framework is flexible, as it can be adapted in regards to the IoT device’s available hardware resources and constraints. Our security analysis shows that our framework is resilient to a variety of attack vectors. The experimental setup demonstrates the feasibility of the approach. By implementing a variety of test cases on FPGA, we demonstrate the adaptability and performance of the framework. Experiments indicate that the update procedure for a 1183-kB firmware image could be achieved, in a secure manner, under 1.73 seconds.
Computer development based embedded systems in precision agriculture: tools and application
Low-power on-chip implementation of enhanced svm algorithm for sensors fusion-based activity classification in lightweighted edge devices.
Smart homes assist users by providing convenient services from activity classification with the help of machine learning (ML) technology. However, most of the conventional high-performance ML algorithms require relatively high power consumption and memory usage due to their complex structure. Moreover, previous studies on lightweight ML/DL models for human activity classification still require relatively high resources for extremely resource-limited embedded systems; thus, they are inapplicable for smart homes’ embedded system environments. Therefore, in this study, we propose a low-power, memory-efficient, high-speed ML algorithm for smart home activity data classification suitable for an extremely resource-constrained environment. We propose a method for comprehending smart home activity data as image data, hence using the MNIST dataset as a substitute for real-world activity data. The proposed ML algorithm consists of three parts: data preprocessing, training, and classification. In data preprocessing, training data of the same label are grouped into further detailed clusters. The training process generates hyperplanes by accumulating and thresholding from each cluster of preprocessed data. Finally, the classification process classifies input data by calculating the similarity between the input data and each hyperplane using the bitwise-operation-based error function. We verified our algorithm on `Raspberry Pi 3’ and `STM32 Discovery board’ embedded systems by loading trained hyperplanes and performing classification on 1000 training data. Compared to a linear support vector machine implemented from Tensorflow Lite, the proposed algorithm improved memory usage to 15.41%, power consumption to 41.7%, performance up to 50.4%, and power per accuracy to 39.2%. Moreover, compared to a convolutional neural network model, the proposed model improved memory usage to 15.41%, power consumption to 61.17%, performance to 57.6%, and power per accuracy to 55.4%.
Getting Started with Secure Embedded Systems
Design principles for embedded systems, cyense: cyclic energy-aware scheduling for energy-harvested embedded systems, embedded systems software development, esqumo an embedded software quality model.
Embedded systems are increasingly used in our daily life due to their importance. They are computer platforms consisting of hardware and software. They run specific tasks to realize functional and non functional requirements. Several specific quality attributes were identified as relevant to the embedded system domain. However, the existent general quality models do not address clearly these specific quality attributes. Hence, the proposition of quality models which address the relevant quality attributes of embedded systems needs more attention and investigation. The major goal of this paper is to propose a new quality model (called ESQuMo for Embedded Software Quality Model) which provides a better understanding of quality in the context of embedded software. Besides, it focuses the light on the relevant attributes of the embedded software and addresses clearly the importance of these attributes. In fact, ESQuMo is based on the well-established ISO/IEC 25010 standard quality model.
Embedded Systems and Architectures
Embedded systems and application areas in engineering, export citation format, share document.


- Advanced Search
Jacdac: Service-Based Prototyping of Embedded Systems
New citation alert added.
This alert has been successfully added and will be sent to:
You will be notified whenever a record that you have chosen has been cited.
To manage your alert preferences, click on the button below.
New Citation Alert!
Please log in to your account
Information & Contributors
Bibliometrics & citations, view options, index terms.
Computer systems organization
Embedded and cyber-physical systems
Embedded systems
Embedded software
Software and its engineering
Software organization and properties
Software system structures
Abstraction, modeling and modularity
Recommendations
A framework for flexible and dependable service-oriented embedded systems.
The continued development and deployment of distributed, real-time embedded systems technologies in recent years has resulted in a multitude of ecosystems in which service-oriented embedded systems can now be realised. Such ecosystems are often exposed ...
Interface decomposition for service compositions
Service-based applications can be realized by composing existing services into new, added-value composite services. The external services with which a service composition interacts are usually known by means of their syntactical interface. However, an ...
Towards Mobile Data Streaming in Service Oriented Architecture
Service Oriented Architecture (SOA) is an architectural pattern providing agility to align technical solutions to modular business services that are decoupled from service consumers. Service capabilities such as interface options, quality of service (...
Information
Published in.

Amazon, USA
Association for Computing Machinery
New York, NY, United States
Publication History
Permissions, check for updates.
Author Tags
- embedded systems
- microcontrollers
- plug-and-play
- Research-article
Contributors
Other metrics, bibliometrics, article metrics.
- 0 Total Citations
- 36 Total Downloads
- Downloads (Last 12 months) 36
- Downloads (Last 6 weeks) 36
View options
View or Download as a PDF file.
View online with eReader .
Login options
Check if you have access through your login credentials or your institution to get full access on this article.
Full Access
Share this publication link.
Copying failed.
Share on social media
Affiliations, export citations.
- Please download or close your previous search result export first before starting a new bulk export. Preview is not available. By clicking download, a status dialog will open to start the export process. The process may take a few minutes but once it finishes a file will be downloadable from your browser. You may continue to browse the DL while the export process is in progress. Download
- Download citation
- Copy citation
We are preparing your search results for download ...
We will inform you here when the file is ready.
Your file of search results citations is now ready.
Your search export query has expired. Please try again.
Help | Advanced Search
Computer Science > Computers and Society
Title: embedded systems education in the 2020s: challenges, reflections, and future directions.
Abstract: Embedded computing systems are pervasive in our everyday lives, imparting digital intelligence to a variety of electronic platforms used in our vehicles, smart appliances, wearables, mobile devices, and computers. The need to train the next generation of embedded systems designers and engineers with relevant skills across hardware, software, and their co-design remains pressing today. This paper describes the evolution of embedded systems education over the past two decades and challenges facing the designers and instructors of embedded systems curricula in the 2020s. Reflections from over a decade of teaching the design of embedded computing systems are presented, with insights on strategies that show promise to address these challenges. Lastly, some important future directions in embedded systems education are highlighted.
| Subjects: | Computers and Society (cs.CY) |
| Cite as: | [cs.CY] |
| (or [cs.CY] for this version) | |
| Focus to learn more arXiv-issued DOI via DataCite |
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .

Embedded Systems and Artificial Intelligence
Proceedings of ESAI 2019, Fez, Morocco
- Conference proceedings
- © 2020
- Vikrant Bhateja 0 ,
- Suresh Chandra Satapathy 1 ,
- Hassan Satori 2
Department of Electronics and Communication Engineering, Shri Ramswaroop Memorial Group of Professional Colleges (SRMGPC), Lucknow, India
You can also search for this editor in PubMed Google Scholar
School of Computer Engineering, Kalinga Institute of Industrial Technology (KIIT), Bhubaneswar, India
Department of computer sciences, faculty of sciences dhar mahraz, sidi mohammed ben abbdallah university, fez, morocco.
- Gathers outstanding research papers presented at the ESAI 2019
- Discusses new findings in embedded systems and artificial intelligence
- Serves as a reference guide for researchers and practitioners in academia and industry
Part of the book series: Advances in Intelligent Systems and Computing (AISC, volume 1076)
131k Accesses
290 Citations
2 Altmetric
This is a preview of subscription content, log in via an institution to check access.
Access this book
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Other ways to access
Licence this eBook for your library
Institutional subscriptions
About this book
Similar content being viewed by others.

Computational Intelligence in Embedded System Design: A Review

Intelligence in Embedded Systems: Overview and Applications

Smart Electronic Systems: An Overview
- Conference Proceedings
- Artificial Intelligence
- Embedded Systems
- Fuzzy and Expert Systems
- Networked Embedded Systems
- Mobile Embedded Systems
Table of contents (85 papers)
Front matter, embedded computing and applications, real-time implementation of artificial neural network in fpga platform.
- Mohamed Atibi, Mohamed Boussaa, Abdellatif Bennis, Issam Atouf
Design of a 0.18 μm CMOS Inductor-Based Bandpass Microwave Active Filter
- Mariem Jarjar, Nabih Pr. El Ouazzani
Improvement of the Authentication on In-Vehicle Controller Area Networks
- Asmae Zniti, Nabih El Ouazzani
Comparative Evaluation of Speech Recognition Systems Based on Different Toolkits
- Fatima Barkani, Hassan Satori, Mohamed Hamidi, Ouissam Zealouk, Naouar Laaidi
Stability Analysis and \(H_\infty \) Performance for Nonlinear Fuzzy Networked Control Systems with Time-Varying Delay
- Ahmed Ech-charqy, Said Idrissi, Mohamed Ouahi, El Houssaine Tissir, Ghali Naami
Driver Behavior Assistance in Road Intersections
- Safaa Dafrallah, Aouatif Amine, Stéphane Mousset, Abdelaziz Bensrhair
BER Performance of CE-OFDM System: Over AWGN Channel and Frequency-Selective Channel Using MMSE Equalization
- J. Mestoui, M. El Ghzaoui, K. El Yassini
Towards a Dynamical Adaptive Core for Urban Flows Simulations
- Hind Talbi, El Miloud Chaabelasri, Najim Salhi, Imad Elmahi
An Efficiency Study of Adaptive Median Filtering for Image Denoising, Based on a Hardware Implementation
- Hasnae El Khoukhi, Faiz Mohammed Idriss, Ali Yahyaouy, My Abdelouahed Sabri
Processing Time and Computing Resources Optimization in a Mobile Edge Computing Node
- Mohamed El Ghmary, Tarik Chanyour, Youssef Hmimz, Mohammed Ouçamah Cherkaoui Malki
Viscous Dissipation and Heat Source/Sink Effects on Convection Heat Transfer in a Saturated Porous Medium
- Elyazid Flilihi, Mohammed Sriti, Driss Achemlal
Fast and Efficient Decoding Algorithm Developed from Concatenation Between a Symbol-by-Symbol Decoder and a Decoder Based on Syndrome Computing and Hash Techniques
- M. Seddiq El Kasmi Alaoui, Saïd Nouh, Abdelaziz Marzak
SWIMAC: An Ultra-Low Power Consumption MAC Protocol for IR-UWB-Based WSN
- Anouar Darif
An Optimal Design of a Short-Channel RF Low Noise Amplifier Using a Swarm Intelligence Technique
- Soufiane Abi, Hamid Bouyghf, Bachir Benhala, Abdelhadi Raihani
Study and Design of a See Through Wall Imaging Radar System
- M. Abdellaoui, M. Fattah, S. Mazer, M. El bekkali, M. El ghazi, Y. Balboul et al.
Analog Active Filter Component Selection Using Genetic Algorithm
- Asmae El Beqal, Bachir Benhala, Izeddine Zorkani
Preliminary Study of Roots by Georadar System
- Ahmed Faize, Gamil Alsharahi

Predictive Agents for the Forecast of CO2 Emissions Issued from Electrical Energy Production and Gas Consumption
- Seif Eddine Bouziane, Mohamed Tarek Khadir
Editors and Affiliations
Vikrant Bhateja
Suresh Chandra Satapathy
Hassan Satori
About the editors
Bibliographic information.
Book Title : Embedded Systems and Artificial Intelligence
Book Subtitle : Proceedings of ESAI 2019, Fez, Morocco
Editors : Vikrant Bhateja, Suresh Chandra Satapathy, Hassan Satori
Series Title : Advances in Intelligent Systems and Computing
DOI : https://doi.org/10.1007/978-981-15-0947-6
Publisher : Springer Singapore
eBook Packages : Intelligent Technologies and Robotics , Intelligent Technologies and Robotics (R0)
Copyright Information : Springer Nature Singapore Pte Ltd. 2020
Softcover ISBN : 978-981-15-0946-9 Published: 08 April 2020
eBook ISBN : 978-981-15-0947-6 Published: 07 April 2020
Series ISSN : 2194-5357
Series E-ISSN : 2194-5365
Edition Number : 1
Number of Pages : XXII, 910
Number of Illustrations : 174 b/w illustrations, 277 illustrations in colour
Topics : Computational Intelligence , Artificial Intelligence , Information Systems Applications (incl. Internet) , Systems and Data Security
- Publish with us
Policies and ethics
- Find a journal
- Track your research

Research Topics in Embedded Systems for PhD
The amalgamation of software and hardware in a computer system is called an embedded system. The signal processors, microprocessors, and ...
- matlabprojects.org
- [email protected]
- +91 9790238391

The amalgamation of software and hardware in a computer system is called an embedded system. The signal processors, microprocessors, and digital signal processors are functioning through the embedded systems. In addition, flexibility, scalability, energy, dependability, efficiency, and precision are some of the notable features of embedded systems. Let’s start this article with the significant research areas of embedded systems to derive the recent research topics in embedded systems for PhD.
Research Areas in Embedded Systems
- Intelligent and solar-operated robot
- Metal detector
- Pc-based bomb detector
- Heat controller
- Rain detector
- LCD thermometer
- Voice dialer for phone
- The speed limit of the vehicle
- Driverless car
- Gas leak detection
- Train accident alert
- Gesture control
- Anti-sleep alarm
- Auto door open
- Fridge door alarm
- Digital calendar
- Biomedical monitoring system
- Embedded-based auto lift
- Fingerprint car ignition system
At this moment, let us take a look at the list of research algorithms in this field of embedded systems. In addition to that, the research scholars have to go through and finalize the research fields before getting into the selection of research topics in embedded systems for PhD because the algorithms also have to place the research topic in a short note.
Algorithms in Embedded Systems
- The tasks in RMS are scheduled through the static priority which is determined using the duration. In addition, it guarantees time restraints capable of 70% CPU load
- In this process LLF, the tasks are scheduled through the order of laxity and it is not functioning in the soft real-time applications, it has to compete with the applications that are in higher priority
- It is denoted as the dynamic scheduling algorithm which is used in real-time operating systems. Along with that, it is accomplished to assign priority to the process which has the earliest deadline. The process of EDF is functioning over the tasks which are scheduled by the order of the deadline
For your quick reference, our technical experts in the embedded system have highlighted the list of substantial research ideas in the embedded system for your PhD topic selection. More than that, our research experts are ready to implement the scholar’s research ideas. So, discover the innovations with our better guidance.
Latest Interesting Research Ideas in Embedded Systems
- Communication propagation and antenna
- Embedded systems and secure applications
- Cognitive science
- Signal processing applications
- Water level controller
- PLC-based intruder information sharing
- Land rover robot
- Traffic signal auto stop
- Ultrasonic and voice-based walking for blind
- Multi-channel fire alarm
- GPRS-based industrial monitoring
- GSM-based ECG tele-alert system
- Data acquisition system
- Power failure indicator
Are you guys requiring the research topics in embedded systems for PhD with the discussion and to shape your research knowledge? Then you can approach our research experts at any time. The following is about the list of significant research topics that occurred in the contemporary research platform and it is used to select the project titles based on an embedded system.
Research Topics in Embedded Systems for PhD Scholars
- Representation of embedded system with the Petri synthesis property preservation
- Controlling the time nonlinear systems through the embedded systems
- Analysis, application, and modeling
- Nonvolatile data memory with a real-time embedded system
- PCP water injection system design
- Parallel heterogeneous system applications
- Deep neural networks and voice recognition
- Distinct stair recognition system and ultrasonic device frequency
- LPWAN is used while monitoring the coastal waves
- Power harvesting for smart sensor networks in monitoring water distribution system
- Accelerometer-based gesture recognition for wheelchair direction control
- Bedside patient monitoring with wireless sensor networks
- 4-GHz energy-efficient transmitter for wireless medical applications
- Automatic docking system for recharging home surveillance robots
- Hybrid RFID-GPS-based terminal system in vehicular communications
- RF fingerprinting physical objects for anti-counterfeiting applications
- Authenticated and access control system for the device using smart card technology
- Hazardous gas detecting method applied in coal mine detection robot
- Posture allocations and activities by a shoe-based wearable sensor
- Development of an ES for secure wireless data communication
- A microcontroller-based intelligent traffic controller system
- Monitoring and controlling of requirements for cultivation
The following is about the list of research applications based on the embedded system research field it is beneficial for research scholars to find the finest PhD research work through the provided list and these are highlighted by our experienced research professionals in embedded systems.

Applications in Embedded Systems
- Artificial intelligence and robotics
- Telephones, satellite, and radio communications
- Text interfaces
- Military control bases
- Firing of missiles
- Patient monitoring
- Heart treatments
- Radiation therapy
- Space station control
- Spaceship launch and monitoring
- Automobiles
We provide complete research assistance in the research field based on embedded systems for research scholars. On that note, the research scholars have to know about the components that are used in their selected research area. Thus, we have enlisted the components based on the embedded system for your quick reference to implement research topics in embedded systems for PhD.
Components in Embedded Systems
- The power supply is considered the significant component to provide power to the embedded system circuit. In addition, the embedded system requires a 5 V supply that ranges from 1.8 to 3.3. V
- 32-bit processor
- 16-bit processor
- 8-bit processor
- Several microcontrollers are utilized in the embedded system and the memory is the representation of the microcontroller itself. It includes two significant types as
- RAM is denoted as the volatile type of memory and it is used to store the data for a temporary period in the memory while switching off the system, the data will be lost from the memory
- It is denoted as the code memory and it is deployed to store the program when the system is switched on the embedded system fetch code from ROM memory
- The input is used in the embedded system where it is needed to interact with the system. The processors are used in the embedded system based on input and output. In addition, the proper configuration is required for using the input and output ports. In the embedded system there are fixed input and output ports to connect the devices only with the specified ports and P0, P1, P2, and more are examples of input and output ports
- The type of interface which is deployed to communicate with other types of embedded systems is called a communication port. When the small-scale application includes the embedded system and communication ports can be deployed in the form of a microcontroller and it includes the serial protocols used to send data from one system board to another system board
- The timer and counter are utilized in the embedded system and the programming is done in such a way that delay can be generating the embedded system. The delay period can be decided through the functions of the crystal oscillator and system frequency
- The application is used for embedded systems with the competition of hardware components. For instance, temperature sensor applications are requiring the temperature sensors to measure the temperature
Up to now, we have discussed some forceful research components that are used in an embedded system which every research scholar prerequisites to be aware of while selecting their research topics in an embedded system for PhD. Without any delay, let’s discuss research problems in the research field based on the embedded system in the following.
Research Challenges in Embedded Systems
- Performance
- DRM vs usability
- Creating the required latent process
- Moore’s law
- Globalization
- Future vs legacy
- Emerging behavior
- Heterogeneous vendors
- Heterogeneity
Below, our research professionals have enlisted the research questions that are asked by the research scholars to develop their research projects in the embedded system along with the appropriate answers.
People Asked Questions
What are the top research fields in embedded systems.
- Cyber security embedded system
- Embedded IoT application
- Embedded network design
- Embedded applications
- Embedded Linux system
- Microcontroller firmware
What are the different types of embedded systems?
- Mobile phones
- Digital camera
- Home security systems
- ATM machine
- Card swipe machine
- MP3 players
- Microwave ovens
- Traffic control system
- Military usage in the defense sector
- Medical usage in the health sector
What is a new technology in embedded systems?
- Cloud connectivity
- Embedded security
- Augmented reality and virtual reality
- Artificial intelligence
- Deep learning
What is the simulation tools used in embedded system?
What is the programming languages used in embedded system, what are the topics in embedded systems.
- Wireless meter for consumer utility
- An ultrasonic parking guidance system
- Iris-based door opening and closing
- Fault location in underground power networks
- Embedded-based calibration of the proximity sensor
- Accident prevention using eye blink
- Earthquake analyzer and reporter
- AC motor speed monitoring and control through telephone
- Bus information alert for the blind using Zigbee
What are the real-time examples in embedded systems?
- Medical Equipment
- Electronic Calculators
- Industrial machines
- Laser Printer
- Digital phones
- Televisions
- Washing Machine
- Digital watches
To this end, the research scholars can trust us for your PhD work and we shape your innovative research thoughts with proper research implementation by using the required simulation tools, protocols, algorithms, etc. Our research experts have years of experience in this research platform and also from research topics in embedded systems for PhD to paper publication too. We are strong in all the research fields in embedded systems and we are being learned through the fundamentals till the growth and now. Finally, the research scholars will acquire the finest result when you join hands with us. As well as, we teach you an easy way to acquire the finest research knowledge to shine in your research career.
Similar Pages
- 275 words per page
- Free revisions1
- Topic/subject mastery
- Perfect citations
- Editorial review
- Money back guarantee2
- 1-on-1 writer chat
- 24/7 support
- A top writer
- Satisfaction guarantee
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Watch The Results

Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you.
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.

Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Ontime Delivery
- Best Prices
- Unique Work
Simulation Projects Workflow
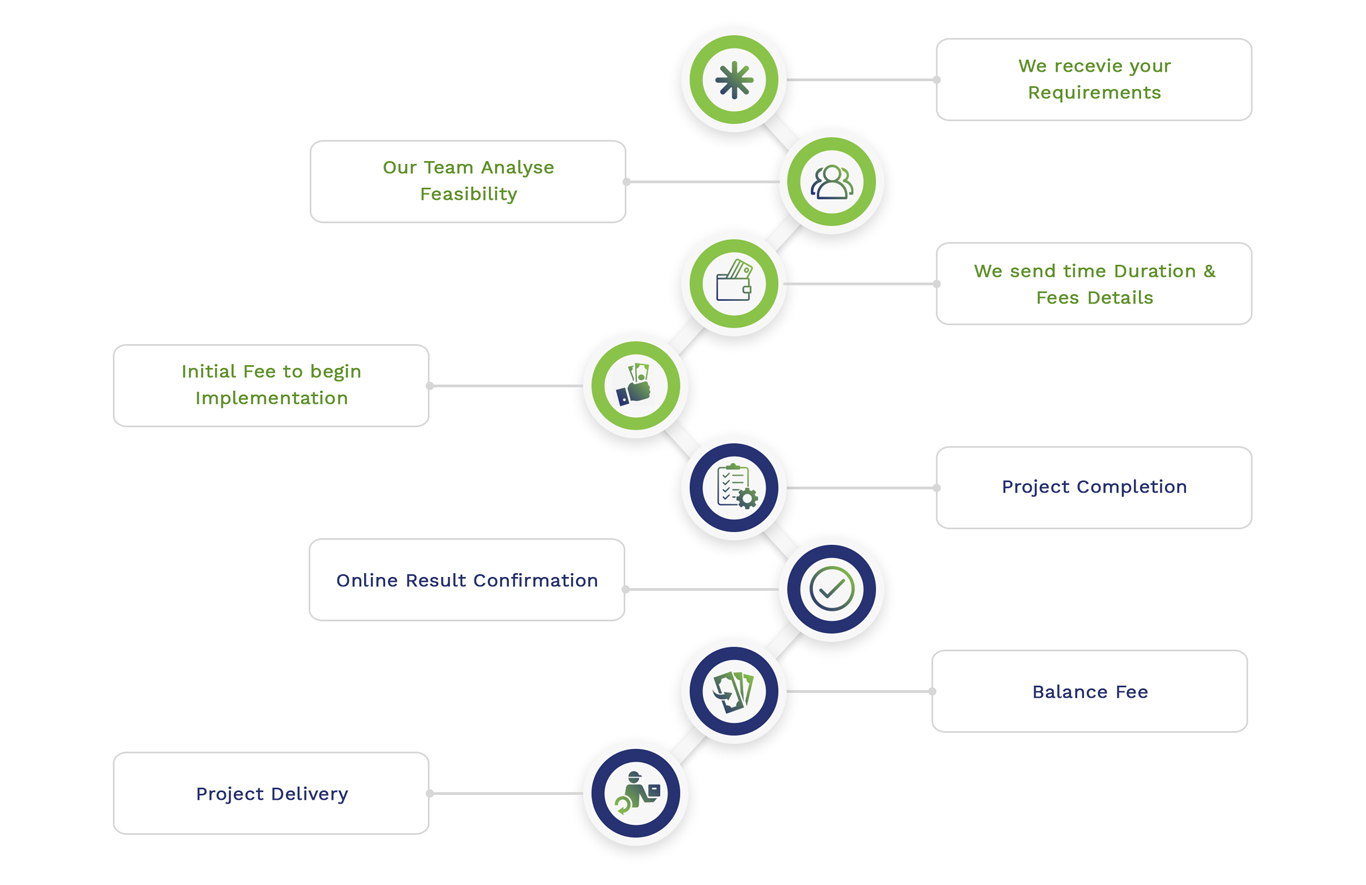
Embedded Projects Workflow
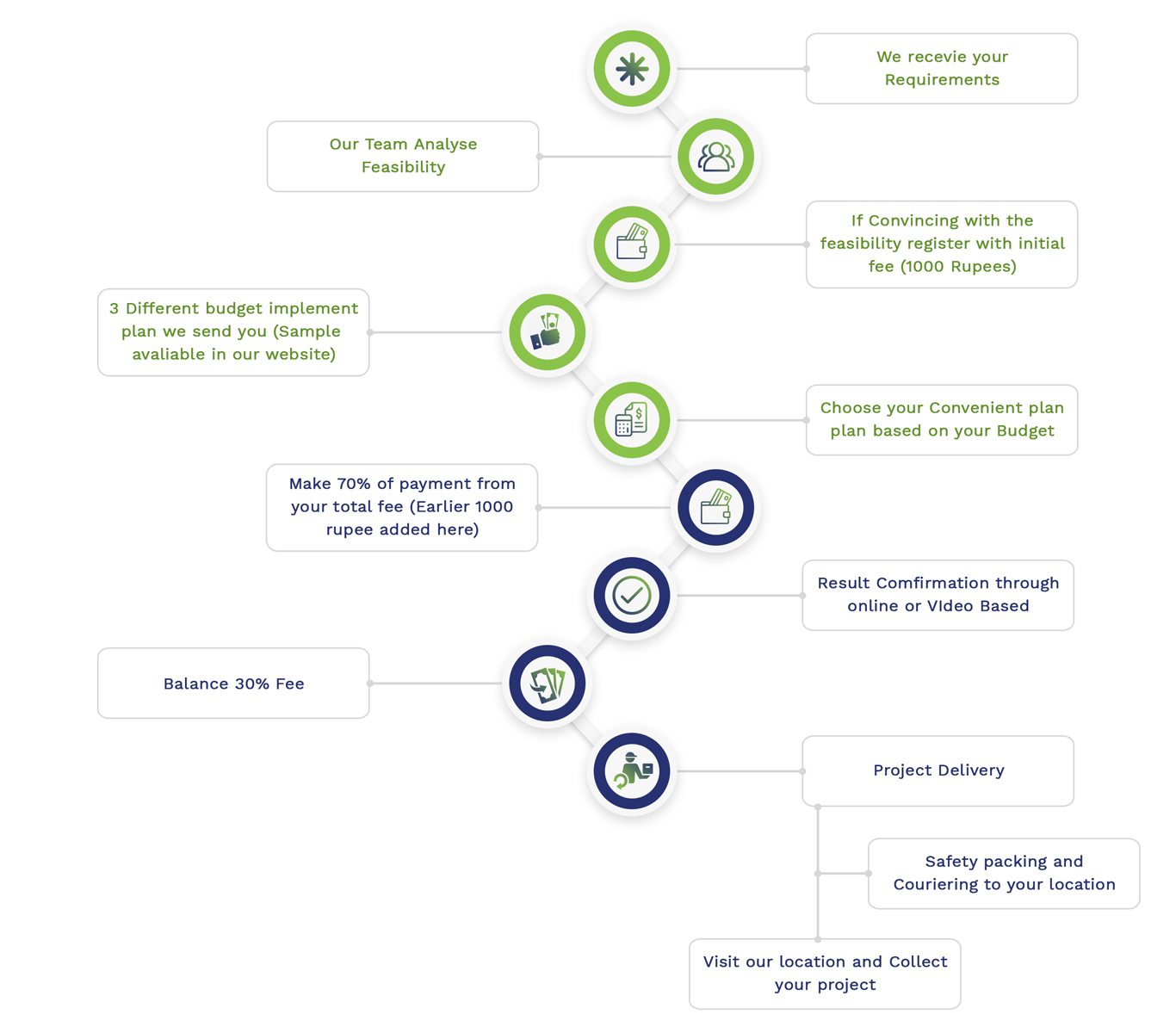
This Service will be usefull for
Share us your Matlab needs our technical team will get it done Ontime with Detailed Explanations .All Matlab assignments , routine matlab homeworks and Matlab academic Tasks completed at affordable prices. You get Top Grade without any Tension .Upload your Matlab requirements and see your Marks improving.Our Matlab Tutors are from US, UK, CANADA, Australia, UAE , china and India.If you need guidance in MATLAB ,assignments or Thesis and want to chat with experts or any related queries and Research issues feel free contact us.

- OnTime Delivery
- Customized Works
- Plagiarism Free
- Unique works
- Detailed Explanations
- Multiple Revisions
- MATLAB Simulink
- 90, Pretham Street, Duraisamy Nagar Madurai – 625001 Tamilnadu, India


Military Embedded Systems
DARPA introduces XRQ-73 as new hybrid-electric X-plane
June 25, 2024

Technology Editor

ARLINGTON, Virginia. The Defense Advanced Research Projects Agency (DARPA) officially designated the hybrid-electric uncrewed aircraft system (UAS) developed under its Series Hybrid Electric Propulsion AiRcraft Demonstration (SHEPARD) program as the XRQ-73, the agency announced in a statement.
The SHEPARD program, an "X-prime" initiative, incorporates series hybrid electric architecture and various technologies from the earlier AFRL/IARPA Great Horned Owl project. This approach is designed to mitigate system-level integration risks and accelerate the maturation of long-endurance aircraft designs suitable for rapid field deployment, the agency says.
The XRQ-73, a Group 3 UAS weighing about 1,250 pounds, is set for its inaugural flight by the end of 2024. The program involves key contributions from multiple defense research and industry partners, including Northrop Grumman Corporation's Aeronautics Systems sector, which serves as the prime contractor, the statement readas.
This designation and the anticipated first flight could be precursors to developing mission-ready, resilient uncrewed systems for the Department of Defense. The collaborative effort spans several organizations including the Air Force Research Laboratory, the Office of Naval Research, and various technology suppliers.
Featured Companies

U.S. Defense Advanced Research Projects Agency (DARPA)
Unmanned - test, unmanned - payloads, unmanned - sensors.

Third GlobalEye aircraft to be delivered to Swedish FMV by Saab
June 28, 2024

DoD unveils IT integration, interoperability strategy
June 26, 2024

AI and the OODA loop: How AI enhances strategic decisions for today’s warfighters
June 21, 2024
Case study: LiDAR system provides helicopter pilots a clear line of sight in brownouts
June 24, 2008
March 30, 2010
September 23, 2009
October 12, 2011
The U.S. Army's ability to "see first, shoot second" rolls on with UGVs
October 06, 2010
June 20, 2011

DARPA surveillance system uses EEG for image filtering
September 20, 2012
May 23, 2013
June 01, 2015
July 23, 2015
September 10, 2015
Hermetic power packaging vs. PEMs for mil electronics: No power issues here
July 27, 2011
June 16, 2011
February 18, 2009
April 29, 2011
February 10, 2009
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Journal Menu
- Electronics Home
- Aims & Scope
- Editorial Board
- Reviewer Board
- Topical Advisory Panel
- Instructions for Authors
- Special Issues
- Sections & Collections
- Article Processing Charge
- Indexing & Archiving
- Editor’s Choice Articles
- Most Cited & Viewed
- Journal Statistics
- Journal History
- Journal Awards
- Society Collaborations
- Conferences
- Editorial Office
Journal Browser
- arrow_forward_ios Forthcoming issue arrow_forward_ios Current issue
- Vol. 13 (2024)
- Vol. 12 (2023)
- Vol. 11 (2022)
- Vol. 10 (2021)
- Vol. 9 (2020)
- Vol. 8 (2019)
- Vol. 7 (2018)
- Vol. 6 (2017)
- Vol. 5 (2016)
- Vol. 4 (2015)
- Vol. 3 (2014)
- Vol. 2 (2013)
- Vol. 1 (2012)
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
Embedded Systems: Fundamentals, Design and Practical Applications
- Print Special Issue Flyer
Special Issue Editors
Special issue information.
- Published Papers
A special issue of Electronics (ISSN 2079-9292). This special issue belongs to the section " Circuit and Signal Processing ".
Deadline for manuscript submissions: 15 September 2024 | Viewed by 35428
Share This Special Issue

Dear Colleagues,
Recent years have witnessed the ever-more widespread use of embedded systems in increasingly diverse areas of human activity. Suffice to say, about 99% of all manufactured microprocessors are used in embedded systems. With the development of the Internet of Things, the automation of production, and the increasing utilization of various robots, enhancing the intelligence of the material world around us would be unthinkable without the use of embedded systems. Modern embedded systems are implemented both on the basis of fairly simple microcontrollers, and on the basis of complex integrated circuits consisting of billions of transistors. In many cases, embedded systems are real-time cyber–physical systems that monitor and control complex physical objects. Such systems should be sufficiently reliable and secure. Failures in the operation of such systems should not lead to fatal consequences associated with a threat to life and/or the environment. In response to increasingly frequent hacking attacks, such systems should have strong protection against unauthorized access. The solution to this problem requires the development of implemented cryptographic protection methods, for example, in embedded systems. In the case of distributed embedded systems, effective methods of interaction of their components are of paramount importance. The incredible complexity of modern embedded systems requires the development of effective methods for specification and automation of the design process. This is only a small part of one of the existing problems associated with the development and implementation of embedded systems. These problems provide a wide field for the theoretical research and practical implementations of embedded systems.
The aim of this Special Issue is to collate scientific manuscripts on the practical and theoretical aspects associated with theoretical and practical aspects of implementing efficient embedded systems. The key focus is to present theoretical advances, as well as new specification, design and verification methods, in order to improve the main characteristics of embedded systems.
Topics may include, but are not limited to, the following:
- Theoretical foundations of embedded systems;
- Sensors and actuators for embedded systems;
- Real-time embedded systems and real-time operating systems (RTOS);
- Scheduling algorithms in embedded systems;
- Techniques of low-power design in embedded systems;
- Improving security and dependability of embedded systems;
- Development of efficient analog-to-digital and digital-to-analog converters for embedded systems;
- Hardware-software co-design: methods and CAD tools;
- Design of embedded systems based on microcontrollers;
- User interfaces in embedded systems;
- Improving communication channels and communication protocols;
- Using embedded systems in Internet of Things and Internet of Battle Things applications;
- Methods of specification and development of distributed embedded systems;
- Methods of the implementation of mobile and autonomous embedded systems;
- Development of standard hardware platforms for implementing embedded systems (including reprogrammable devices, e.g., FPGAs);
- Methodology of platform-based design (PBD) for embedded systems;
- Design methodology based on models (model-driven design);
- Soft and hard IP cores in embedded system design;
- Dynamic voltage and frequency scaling, HW and SW dynamic power management;
- Approximate computing, low-power arithmetic;
- Algorithm-level optimization, low-complexity algorithm for low-power digital systems;
- Parallel/high-throughput processing techniques for low-power digital systems;
- Design space exploration techniques, with special emphasis on power/energy estimations and power minimization methodologies;
- Design of self-energy aware systems;
- High-level synthesis and HW/SW co-design techniques for low-power digital systems;
- Cybersecurity aspects in embedded systems;
- Graphical modelling of embedded systems (including Petri nets, UML, etc.);
- Verification and analysis methods of embedded systems (including formal methods);
- Validation techniques of embedded systems.
Prof. Dr. Alexander Barkalov Prof. Dr. Larysa Titarenko Prof. Dr. Dariusz Kania Prof. Dr. Remigiusz Wiśniewski Guest Editors
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website . Once you are registered, click here to go to the submission form . Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the special issue website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Electronics is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript. The Article Processing Charge (APC) for publication in this open access journal is 2400 CHF (Swiss Francs). Submitted papers should be well formatted and use good English. Authors may use MDPI's English editing service prior to publication or during author revisions.
- embedded systems
- hardware-software co-design
- microcontrollers
- dependability
- security and cybersecurity
- distributed embedded systems
- ASIC-based design of embedded systems
- FPGA-based design of embedded systems
- mobile and autonomous embedded systems
- optimization of power consumption
- communication channels
Published Papers (20 papers)

Further Information
Mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

COMMENTS
Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore. Contact Us. Help.
Electronics, Embedded Systems, and Microcontrollers, Hardware in the Loop | Explore the latest full-text research PDFs, articles, conference papers, preprints and more on EMBEDDED SYSTEMS. Find ...
Embedded systems are increasingly used in our daily life due to their importance. They are computer platforms consisting of hardware and software. They run specific tasks to realize functional and non functional requirements. Several specific quality attributes were identified as relevant to the embedded system domain.
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on EMBEDDED SYSTEMS PROGRAMMING. Find methods information, sources, references or conduct a literature ...
1. Introduction. Real-time and networked embedded systems are important bidirectional bridges between the physical and the information worlds. Embedded intelligence increasingly pervades industry, infrastructure, and public and private spaces, being identified as a society and economy emerging "neural system" that supports both societal ...
Abstract: Embedded system design is crucial for the development of industry, technology, and science, and it is an area that has significantly grown in recent years throughout Latin America, both in academia and in industry. Embedded System (ES) refers to electronic equipment with a computing core which, unlike a personal computer, is designed to meet a specific function and is usually ...
This paper describes the evolution of embedded systems education ... In [12], guiding principles were presented for the embedded systems teaching and research agenda at UC Berkeley. The authors ... Embedded systems have evolved in recent years to include increasingly autonomous decision-making,
Embedded systems are increasingly becoming a key technological component of all kinds of complex technical systems, ranging from vehicles, telephones, audio-video equipment, aircraft, toys, security systems, medical diagnostics, to weapons, pacemakers, climate control systems, manufacturing systems, intelligent power systems etc. IJES addresses the state of the art of all aspects of embedded ...
The Journal of Supercomputing announces a new section dedicated to Advanced Embedded Systems, bringing together embedded hardware, novel embedded software solutions, and advancements related to solving critical issues in embedded security, energy efficiency, or emerging applications. We aim to foster collaboration among researchers spanning ...
Design Automation for Embedded Systems is a multidisciplinary journal that focuses on the systematic design of embedded systems. Offers a forum for scientists and engineers to report their latest work on algorithms, tools, architectures, case studies, and actual design examples. Focuses on tools, methodologies and architectures, including HW/SW ...
Dear Colleagues, This Special Issue (SI) invites papers on research achievements in emerging and new technologies in embedded systems. Embedded systems have matured as a discriminating technology for a wide variety of applications in our daily life. However, this immense impact is unfortunately confined by the power and cost constraints of ...
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... embedded-system design ...
The remainder of this article is organised as follows. Section 2 presents the background of the Internet of Things, approached from the perspective of the evolution of embedded devices and wireless communication technologies that have enabled the development of IoT applications that are already present in our daily lives. In Section 3, the evolution of the Machine Learning area is presented ...
The continued development and deployment of distributed, real-time embedded systems technologies in recent years has resulted in a multitude of ecosystems in which service-oriented embedded systems can now be realised. Such ecosystems are often exposed ...
Embedded Systems Education in the 2020s: Challenges, Reflections, and Future Directions. Embedded computing systems are pervasive in our everyday lives, imparting digital intelligence to a variety of electronic platforms used in our vehicles, smart appliances, wearables, mobile devices, and computers. The need to train the next generation of ...
This paper proposed an Actor-oriented modeling and designing methodology for complex real time embedded system. Embedded system can be divided into multiple single computing model subsystems according to different computation model and different abstract hierarchy by this method. Then, specialist can construct this subsystem according to their previous experiences and knowledge, and the ...
Embedded Systems Engineering has grown in recent years to become an integral part of our daily living as it finds striking applications in various spheres of our lives.
This book gathers selected research papers presented at the First International Conference on Embedded Systems and Artificial Intelligence (ESAI 2019), held at Sidi Mohamed Ben Abdellah University, Fez, Morocco, on 2-3 May 2019. Highlighting the latest innovations in Computer Science, Artificial Intelligence, Information Technologies, and ...
NS2. The amalgamation of software and hardware in a computer system is called an embedded system. The signal processors, microprocessors, and digital signal processors are functioning through the embedded systems. In addition, flexibility, scalability, energy, dependability, efficiency, and precision are some of the notable features of embedded ...
Special Issue Information. Dear Colleagues, The objective of this Special Issue is to invite original and high-quality papers that describe research, technical aspects, or developments in real-time embedded systems architecture, software, and applications. The research on real-time embedded systems has gained great interest in the last years as ...
The XRQ-73, a Group 3 UAS weighing about 1,250 pounds, is set for its inaugural flight by the end of 2024. The program involves key contributions from multiple defense research and industry partners, including Northrop Grumman Corporation's Aeronautics Systems sector, which serves as the prime contractor, the statement readas.
Electronics and embedded systems have become an increasingly integral part of modern automobiles. Automotive embedded systems are a class of embedded systems which are based on the concept of generic embedded systems but vary widely in terms of design constrains, operating environments, performance goals and many other factors. This paper serves as a review of the recent trends of automotive ...
Total new vehicle retail sales in the United States reached 1.1 million units in June last year, according to data from industry consultants J.D. Power and GlobalData.
Top authors and change over time. The top authors publishing at National Power Systems Conference (based on the number of publications) are: Bhim Singh (23 papers) published 4 papers at the last edition, 1 more than at the previous edition,; Naran M. Pindoriya (12 papers) published 10 papers at the last edition,; K V S Baba (12 papers) published 4 papers at the last edition, 1 less than at the ...
Abstract. Large Language Models (LLMs) have demonstrated remarkable capabilities across a variety of software engineering and coding tasks. However, their application in the domain of code and compiler optimization remains underexplored.
This paper provides a decent intuition into most of the prominent technological innovations of embedded systems in the automotive field. Discover the world's research 25+ million members
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... Modern embedded systems are ...
Save & Close Corporate Research & Development Report 2022. Deloitte's ongoing focus on research and development (R&D) is what has inspired us to carry out this survey - our first research project of this kind since the outbreak of COVID-19 in 2020. ... Deloitte's global network of alliances can support you in meeting new market needs and ...
This paper also designs and implements an embedded security protection system based on trusted computing technology, containing a measurement and control component in the kernel and a remote graphical management interface for administrators. The kernel layer enforces the integrity measurement and control of the embedded application on the device.
those of the authors alone. This research was conducted while some of the authors were employees at the U.S. Department of the Treasury. The findings, interpretations, and conclusions expressed in this paper are entirely those of the authors and do not necessarily reflect the views or the official positions of the U.S. Department of the Treasury.