- Talk to Expert
- Machine Identity Management
- October 20, 2023
- 9 minute read

7 Data Breach Examples Involving Human Error: Did Encryption Play a Role?

Despite an overall increase in security investment over the past decade, organizations are still plagued by data breaches. What’s more, we’re learning that many of the attacks that result in breaches misuse encryption in some way. (By comparison, just four percent of data breaches tracked by Gemalto’s Breach Level Index were “secure breaches” in that the use of encryption rendered stolen data useless). Sadly, it’s often human error that allows attackers access to encrypted channels and sensitive information. Sure, an attacker can leverage “gifts” such as zero-day vulnerabilities to break into a system, but in most cases, their success involves provoking or capitalizing on human error.
Human error has a well-documented history of causing data breaches. The 2022 Global Risks Report released by the World Economic Forum, found that 95% of cybersecurity threats were in some way caused by human error. Meanwhile, the 2022 Data Breach Investigations Report (DBIR) found that 82% of breaches involved the human element, including social attacks, errors and misuse.
I think it’s interesting to look at case studies on how human error has contributed to a variety of data breaches, some more notorious than others. I’ll share the publicly known causes and impacts of these breaches. But I’d also like to highlight how the misuse of encryption often compounds the effects of human error in each type of breach.

SolarWinds: Anatomy of a Supersonic Supply Chain Attack
Data breach examples.
Here is a brief review of seven well-known data breaches caused by human error.
1. Equifax data breach—Expired certificates delayed breach detection
In the spring of 2017, the U.S. Department of Homeland Security's Computer Emergency Readiness Team (CERT) sent consumer credit reporting agency Equifax a notice about a vulnerability affecting certain versions of Apache Struts. According to former CEO Richard Smith, Equifax sent out a mass internal email about the flaw. The company’s IT security team should have used this email to fix the vulnerability, according to Smith’s testimony before the House Energy and Commerce Committee. But that didn’t happen. An automatic scan several days later also failed to identify the vulnerable version of Apache Struts. Plus, the device inspecting encrypted traffic was misconfigured because of a digital certificate that had expired ten months previously. Together, these oversights enabled a digital attacker to crack into Equifax’s system in mid-May and maintain their access until the end of July.
How encryption may become a factor in scenarios like this: Once attackers have access to a network, they can install rogue or stolen certificates that allow them to hide exfiltration in encrypted traffic. Unless HTTPS inspection solutions are available and have full access to all keys and certificates, rogue certificates will remain undetected.
Impact: The bad actor is thought to have exposed the personal information of 145 million people in the United States and more than 10 million UK citizens. In September 2018, the Information Commissioner’s Office issued Equifax a fine of £500,000, the maximum penalty amount allowed under the Data Protection Act 1998, for failing to protect the personal information of up to 15 million UK citizens during the data breach.
2. Ericsson data breach—Mobile services go dark when the certificate expires
At the beginning of December 2018, a digital certificate used by Swedish multinational networking and telecommunications company Ericsson for its SGSN–MME (Serving GPRS Support Node—Mobility Management Entity) software expired. This incident caused outages for customers of various UK mobile carriers including O2, GiffGaff, and Lyca Mobile. As a result, a total of 32 million people in the United Kingdom alone lost access to 4G and SMS on 6 December. Beyond the United Kingdom, the outage reached 11 countries including Japan.
How encryption may become a factor in scenarios like this: Expired certificates do not only cause high-impact downtime; they can also leave critical systems without protection. If a security system experiences a certificate outage , cybercriminals can take advantage of the temporary lack of availability to bypass the safeguards.
Impact: Ericsson restored the most affected customer services over the course of 6 December. The company also noted in a blog post that “The faulty software [for two versions of SGSN–MME] that has caused these issues is being decommissioned.”
3. LinkedIn data breach—Millions miss connections when the certificate expires
On 30 November, a certificate used by business social networking giant LinkedIn for its country subdomains expired. As reported by The Register , the incident did not affect www.linkedin.com, as LinkedIn uses a separate certificate for that particular domain. But the event, which involved a certificate issued by DigiCert SHA2 Secure Server CA, did invalidate us.linkedin.com along with the social media giant’s other subdomains. As a result, millions of users were unable to log into LinkedIn for several hours.
How encryption may become a factor in scenarios like this: Whenever certificates expire, it may indicate that overall protection for machine identities is not up to par. Uncontrolled certificates are a prime target for cybercriminals who can use them to impersonate the company or gain illicit access.
Impact: Later in the afternoon on 30 November, LinkedIn deployed a new certificate that helped bring its subdomains back online, thereby restoring all users’ access to the site.
4. Strathmore College data breach—Student records not adequately protected
In August 2018, it appears that an employee at Strathmore secondary college accidentally published more than 300 students’ records on the school’s intranet. These records included students' medical and mental health conditions such as Asperger’s, autism and ADHD. According to The Guardian , they also listed the exposed students’ medications along with any learning and behavioral difficulties. Overall, the records remained on Strathmore’s intranet for about a day. During that time, students and parents could have viewed and/or downloaded the information.
How encryption may become a factor in scenarios like this: Encrypting access to student records makes it difficult for anyone who doesn’t have the proper credentials to access them. Any information left unprotected by encryption can be accessed by any cybercriminals who penetrate your perimeter.
Impact: Strathmore’s principal said he had arranged professional development training for his staff to ensure they’re following best security practices. Meanwhile, Australia’s Department of Education announced that it would investigate what had caused the breach.
5. Veeam data breach—Customer records compromised by unprotected database
Near the end of August 2018, the Shodan search engine indexed an Amazon-hosted IP. Bob Diachenko, director of cyber risk research at Hacken.io, came across the IP on 5 September and quickly determined that the IP resolved to a database left unprotected by the lack of a password. The exposed database contained 200 gigabytes worth of data belonging to Veeam, a backup and data recovery company. Among that data were customer records including names, email addresses and some IP addresses.
How encryption may become a factor in scenarios like this: Usernames and passwords are a relatively weak way of securing private access. Plus, if an organization does not maintain complete control of the private keys that govern access for internal systems, attackers have a better chance of gaining access.
Impact: Within three hours of learning about the exposure, Veeam took the server offline. The company also reassured TechCrunch that it would “conduct a deeper investigation and… take appropriate actions based on our findings.”
6. Marine Corps data breach—Unencrypted email misfires
At the beginning of 2018, the Defense Travel System (DTS) of the United States Department of Defense (DOD) sent out an unencrypted email with an attachment to the wrong distribution list. The email, which the DTS sent within the usmc.mil official unclassified Marine domain but also to some civilian accounts, exposed the personal information of approximately 21,500 Marines, sailors and civilians. Per Marine Corp Times , the data included victims’ bank account numbers, truncated Social Security Numbers and emergency contact information.
How encryption may become a factor in scenarios like this: If organizations are not using proper encryption, cybercriminals can insert themselves between two email servers to intercept and read the email. Sending private personal identity information over unencrypted channels essentially becomes an open invitation to cybercriminals.
Impact: Upon learning of the breach, the Marines implemented email recall procedures to limit the number of email accounts that would receive the email. They also expressed their intention to implement additional security measures going forward.
7. Pennsylvania Department of Education data breach—Misassigned permissions
In February 2018, an employee in Pennsylvania’s Office of Administration committed an error that subsequently affected the state’s Teacher Information Management System (TIMS). As reported by PennLive , the incident temporarily enabled individuals who logged into TIMS to access personal information belonging to other users including teachers, school districts and Department of Education staff. In all, the security event is believed to have affected as many as 360,000 current and retired teachers.
How encryption may become a factor in scenarios like this: I f you do not know who’s accessing your organization’s information, then you’ll never know if it’s being accessed by cybercriminals. Encrypting access to vital information and carefully managing the identities of the machines that house it will help you control access.
Impact: Pennsylvania’s Department of Education subsequently sent out notice letters informing victims that the incident might have exposed their personal information including their Social Security Numbers. It also offered a free one-year subscription for credit monitoring and identity protection services to affected individuals.
How machine identities are misused in a data breach
Human error can impact the success of even the strongest security strategies. As the above attacks illustrate, this can compromise the security of machine identities in numerous ways. Here are just a few:
- SSH keys grant privileged access to many internal systems. Often, these keys do not have expiration dates. And they are difficult to monitor. So, if SSH keys are revealed or compromised, attackers can use them to pivot freely within the network.
- Many phishing attacks leverage wildcard or rogue certificates to create fake sites that appear to be authentic. Such increased sophistication is often required to target higher-level executives.
- Using public-key encryption and authentication in the two-step verification makes it harder to gain malicious access. Easy access to SSH keys stored on computers or servers makes it easier for attackers to pivot laterally within the organization.
- An organization’s encryption is only as good as that of its entire vendor community. If organizations don’t control the keys and certificates that authenticate partner interactions, then they lose control of the encrypted tunnels that carry confidential information between companies.
- If organizations are not monitoring the use of all the keys and certificates that are used in encryption, then attackers can use rogue or stolen keys to create illegitimate encrypted tunnels. Organizations will not be able to detect these malicious tunnels because they appear to be the same as other legitimate tunnels into and out of the organization.
How to avoid data breaches
The best way to avoid a data breach to make sure your organization is using the most effective, up-to-date security tools and technologies. But even the best cybersecurity strategy is not complete unless it is accompanied by security awareness training for all who access and interact with sensitive corporate data.
Because data breaches take many different forms and can happen in a multitude of ways, you need to be ever vigilant and employ a variety of strategies to protect your organization. These should include regular patching and updating of software, encrypting sensitive data, upgrading obsolete machines and enforcing strong credentials and multi-factor authentication.
In particular, a zero-trust architecture will give control and visibility over your users and machines using strategies such as least privileged access, policy enforcement, and strong encryption. Protecting your machine identities as part of your zero trust architecture will take you a long way toward breach prevention. Here are some machine identity management best practices that you should consider:
- Locate all your machine identities. Having a complete list of your machine identities and knowing where they’re all installed, who owns them, and how they’re used will give you the visibility you need to ensure that they are not being misused in an attack.
- Set up and enforce security policies. To keep your machine identities safe, you need security policies that help you control every aspect of machine identities — issuance, use, ownership, management, security, and decommissioning.
- Continuously gather machine identity intelligence. Because the number of machines on your network is constantly changing, you need to maintain intelligence their identities, including the conditions of their use and their environment.
- Automate the machine identity life cycle. Automating he management of certificate requests, issuance, installation, renewals, and replacements helps you avoid error-prone manual actions that may leave your machine identities vulnerable to outage or breach.
- Monitor for anomalous use. After you’ve established a baseline of normal machine identity usage, you can start monitoring and flagging anomalous behavior, which can indicate a machine identity compromise.
- Set up notifications and alerts. Finding and evaluating potential machine identity issues before they exposures is critical. This will help you take immediate action before attackers can take advantage of weak or unprotected machine identities.
- Remediate machine identities that don’t conform to policy. When you discover machine identities that are noncompliant, you must quickly respond to any security incident that requires bulk remediation.
Training your users about the importance of machine identities will help reduce user errors. And advances in AI and RPA will also play a factor in the future. But for now, your best bet in preventing encryption from being misused in an attack on your organization is an automated machine identity management solution that allows you to maintain full visibility and control of your machine identities. Automation will help you reduce the inherent risks of human error as well as maintain greater control over how you enforce security policies for all encrypted communications.
( This post has been updated. It was originally published Posted on October 15, 2020. )
Related posts
- Marriott Data Breach: 500 Million Reasons Why It’s Critical to Protect Machine Identities
- Breaches Are Like Spilled Milk: It Doesn’t Help to Cry
- The Major Data Breaches of 2017: Did Machine Identities Play a Factor?

2024 Machine Identity Management Summit
Help us forge a new era in cybersecurity
TICKETS ON SALE | Let's get fired up! 🔥 Grab your ticket today and save up to $200 with limited-time Early Bird deals.
- Data Breach
Advancing database security: a comprehensive systematic mapping study of potential challenges
- Original Paper
- Open access
- Published: 17 July 2023
Cite this article
You have full access to this open access article
- Asif Iqbal 1 ,
- Siffat Ullah Khan 1 ,
- Mahmood Niazi 2 , 3 ,
- Mamoona Humayun 4 ,
- Najm Us Sama 5 ,
- Arif Ali Khan 6 &
- Aakash Ahmad 7
2705 Accesses
2 Citations
Explore all metrics
The value of data to a company means that it must be protected. When it comes to safeguarding their local and worldwide databases, businesses face a number of challenges. To systematically review the literature to highlight the difficulties in establishing, implementing, and maintaining secure databases. In order to better understand database system problems, we did a systematic mapping study (SMS). We’ve analyzed 100 research publications from different digital libraries and found 20 issues after adopting inclusion and exclusion criteria. This SMS study aimed to identify the most up-to-date research in database security and the different challenges faced by users/clients using various databases from a software engineering perspective. In total, 20 challenges were identified related to database security. Our results show that “weak authorization system”, “weak access control”, “privacy issues/data leakage”, “lack of NOP security”, and “database attacks” as the most frequently cited critical challenges. Further analyses were performed to show different challenges with respect to different phases of the software development lifecycle, venue of publications, types of database attacks, and active research institutes/universities researching database security. The organizations should implement adequate mitigation strategies to address the identified database challenges. This research will also provide a direction for new research in this area.
Similar content being viewed by others

Database Security: Attacks and Solutions

Reverse Engineering of Database Security Policies

Automated Generation of Multi-tenant Database Systems Based upon System Design Diagrams
Avoid common mistakes on your manuscript.
1 Introduction
Companies’ databases (DBs) are repositories of their most significant and high-value data. As DB utilization has surged, so has the frequency of attacks on these databases. A DB attack is characterized as an event that jeopardizes a resource by altering or destroying vital data [ 1 , 2 ]. The common goal of DB attacks is to access critical information. Illicitly acquiring sensitive data such as credit card details, banking data, and personal identifiers is another prevalent motive behind DB hacks. In our interconnected global society, several technologies provide avenues for DB attacks to exploit vulnerabilities in DB architecture, as per common understanding [ 1 , 3 , 4 ].
Many enterprises confront challenges like data piracy, data replication, and denial of service attacks. To infiltrate a company’s DBs, cybercriminals scout for system vulnerabilities and exploit them using specialized tools [ 5 , 6 ].
The aspect of security should be prioritized during the development of information systems, particularly DBs. In terms of software development, security concerns must be addressed at every stage of the development cycle [ 7 ]. As illustrated in Fig. 1 , security breaches, including the loss of critical data, have become commonplace in recent years. Given the importance of data security to numerous businesses, a range of measures and methodologies are required to safeguard the DB [ 8 , 9 , 10 ]. A secure DB is designed to react appropriately in the event of a potential DB attack [ 11 ].
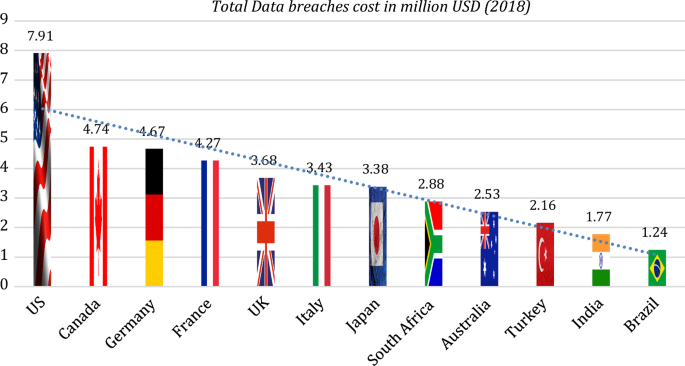
Total data breaches cost in different countries [ 5 ]
In the current world, the impact of cyber-attacks on the commercial landscape must be addressed. To succeed in the globalized environment, businesses must ensure the protection of their vital data. DBs can be safeguarded from unauthorized access [ 12 , 13 , 14 ]. When a DB is outsourced to the cloud, cloud platforms introduce security challenges such as unreliable service providers, malicious cloud employees, data protection, consistency, and scalability. With cloud DBs becoming increasingly susceptible to both external and internal threats, traditional and conventional security measures are insufficient for their protection [ 15 , 16 ].
While extensive work has been done in this field, much of it focuses on a few specific DB platforms or problems, typically explored through standard literature reviews. We aim to provide a more holistic view by conducting a systematic mapping study (SMS) to identify security concerns in DB architecture, development, and maintenance from a software engineering perspective. This SMS will help us identify the ongoing research challenges and priorities.
The following research questions (RQs) will guide our SMS to achieve our study objectives:
RQ1 What is the current state of the art in the development and implementation of secure DBs?
RQ2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
1.1 Paper contribution
The contributions of the intended work are as follows:
The proposed research undertakes a systematic mapping study (SMS) to identify and emphasize the challenges associated with developing and maintaining secure databases.
In addition to showing the difficulties experienced by users using various databases from a software engineering standpoint, our SMS survey sheds light on some of the most current database security studies.
It also highlights the importance of maintaining careful attention to database security and suggests a direction for future research in this field.
1.2 Motivation for the paper
Several research in the literature seeks to give a solution for database security. However, before moving forward with new solutions, it is necessary to synthesize current knowledge to offer security practitioners the most up-to-date information. We must identify the cutting-edge in constructing, implementing, and maintaining dependable databases, as well as security challenges, so BD’s design, development, and maintenance may be secure. The motivation behind this research is to provide in-depth solutions to these problems.
1.3 Paper organization
The remainder of the article is arranged in the following manner.
In Sect. 2 , we discussed the background of DB security, and Sect. 3 , illustrated the research methodology in detail. The results of our conducted SMS are given in Sect. 4 . In Sect. 5 , the Implication of our findings is discussed. Finally, the conclusion and future work are discussed in Sect. 6 . Other supportive information is provided in the rest of the sections at the bottom of this paper.
2 Background
There are a number of studies that look at database security from different angles. In their study [ 17 ], Mai et al. suggest using cloud-based security measures to safeguard power system databases. Using an RSA encryption method, public and private keys are generated for database encryption; a huge prime integer is chosen randomly from the cloud platform’s Simple Storage Service and used as the client key. When the database receives a verification key, it compares it to the public key and private key established by the RSA encryption method. If the database determines that the access is legitimate, it provides feedback on the access. According to the findings of the tests, the database can be protected against threats as the threat situation value is always less than 0.50 once the design technique has been implemented.
A data encryption algorithm was developed by Ibrahim et al., which provides an encryption-based solution for DB security. In this system, information is encrypted using standard ASCII characters. They encrypted all of the data in the database and used three keys to access the primary formula. Numbers and text both work for the data. The suggested formula may restore the data’s original format by combining another coordinator with the aforementioned three keys. In order to achieve a comparable data size to when the data is encrypted at a decent pace, the algorithm prioritizes data size and recording speed [ 18 ].
The article offers a lightweight cryptosystem based on the Rivest Cypher 4 (RC4) algorithm [ 19 ] as a solution to the widespread problem of insecure database transfer between sender and recipient. This cryptosystem safeguards sensitive information by encrypting it before sending it through a network and then decrypting it upon its safe return. Database tables have an encapsulating system that ciphers symbolize hens.
The continual improvements in digitizing have enhanced the prominence of online services. Enterprises must store essential data in corporate DB systems, including bank records, activities, the history of patient paperwork, personal data, agreements, etc. The institutions also must maintain the data’s authenticity, privacy, and availability. Any intrusion in security procedures or data may cause severe economic loss and damage the company’s reputation [ 20 ]. The remarkable development in the deployment of DB’s is the required architecture to cope with information that can be attributed to the rising big data. Every 1.2 years, according to research, the entire quantity of institutional information doubles [ 21 ].
Most of the latest studies provide encryption-based solutions for DB security. However, before proceeding towards these solutions, there is a need to find out the flaws that lead to security breaches.
One or more of the following sources can lead to a security flaw:
Interior Internal origins of attack originate from inside the corporation. Human resources—organization supervisors, admins, workers, and interns—all fall within this category of insiders. Almost all insiders are recognized in a particular way, and just a few IT professionals have significant access levels.
Exterior Exterior attacks originate from entities outside the organization instance, cybercriminals, illegal parties of established ways, and government agencies. Usually, no confidence and trust, or benefit is offered for external sources.
Collaborator Any third party involved in a business connection with the organization, firm, or group is considered a partner in many companies. This significant collection of partners, distributors, vendors, contractual labor, and customers is known as the entire enterprise. There must be some level of confidence and privilege of accessibility or record among colleagues in the entire enterprise; therefore, this is often advised.
2.1 Secure databases
With incredibly high secure data and an expanded online presence, the worries concerning DB security are high at all-time. As more systems are connected and brought online to improve access, the sensitivity towards attacks is also increased, estimated to be about $1.3 million in massive financial losses; these mischievous attacks are also liable for public reputation and client relations with the association [ 21 , 22 ]. All users can boundlessly get information from the DB server in an un-secure DB system. All hosts are allowed to associate with the server from any IP address and link with the DB server, making everyone’s information accessible in the storage engine [ 23 , 24 ].
Hence, the DB system is retained with numerous security mechanisms which contain anticipation of unauthorized access to data from an insider or outsider of an organization. Proper encryption techniques should be applied to secure the DB’s [ 25 ]. The most comprehensive secure DB model is the multilevel model, which allows the arrangement of information according to its privacy and deals with mandatory access control MAC [ 7 ]. DB services are intended to ensure that client DB’s are secure by implementing backup and recovery techniques [ 26 ].
The DB can be protected from the third party, which is not authorized by the procedure called cryptography and utilizing other related techniques. The primary motivation behind DB security is ensuring data privacy from unauthorized outsiders. The essential techniques in DB security are authentication, confidentiality, and integrity, which are utilized to secure the DB’s [ 27 ]. DB construction, in particular, must consider security as the main goal while developing a data system. In this respect, security should be addressed at all stages of the software development process [ 7 , 28 , 29 , 30 ].
2.2 Related work
Various articles examine the importance of security controls from the perspective of software engineering [ 31 ]. For instance, MÁRQUEZ et al. [ 32 ] conducted a systematic survey concentrating on the telemedicine platform’s safety from the software engineering viewpoint. The key focus of this article is investigating how Software development assists in designing a reliable telehealth platform. However, the proposed work is just restricted to, particularly telehealth systems.
Al-Sayid et al. [ 1 ] notably studied the challenges of data stores and proposed DB security issues. To prevent unauthorized access to or alteration of the DB’s critical material, they observed a wide variety of DB security issues. Another research by Zeb focuses on identifying potential attacks on the DB system using a standard research study. Mousa et al. [ 33 ] discover the various risks to DB safety in their analysis through the unstructured research study. Moghadam et al. [ 15 ] did an investigation on cloud servers to figure out all conceivable threats.
Nevertheless, this analysis is solely restricted to the cloud DB environment. The researchers Segundo Toapanta et al. [ 5 ] uncovered real-world examples of cybercrime. Apart from that, their research is restricted to cyberattacks.
The authors in [ 21 ] have suggested an innovative technique for spotting distinct threats to DB systems by assessing the risk for incoming new activities. Their research discovered various harmful attacks that could harm the DB system. The emphasis of their research is only confined to security assessment involving DB’s. Experts in [ 32 ] present a comprehensive mapping analysis, and their observations are only limited to the Telehealth system’s privacy from the software engineering point of view. They did not define the security problems in creating, implementing, and managing safe DB’s. Furthermore, with the rapid development of ICTs, it is essential to be up to date on the most recent developments in this field.
The primary goal of this research is to gain a greater understanding of this topic by conducting a Systematic Mapping Survey to identify the problems in building, managing, and sustaining reliable DB’s.
3 Research methodology
The goal of this study was accomplished by evaluating the current state of DB privacy and suggesting areas that needed further research work. With the SMS, researchers may better connect the data from literary research to a series of questions [ 34 , 35 ]. SMS is a descriptive investigation that involves picking and putting combine all published research articles associated with a particular challenge and gives a broad summery of existing materials relating to the particular questions. In the near future, software engineers will benefit significantly from SMS because it provides a comprehensive overview of the research in the field. Figure 2 outlines the process that was followed to conduct the mapping study.
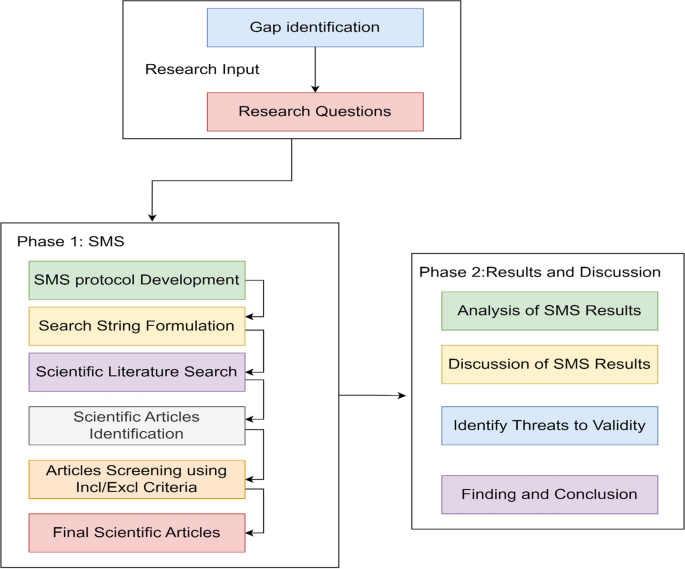
SMS process
3.1 Research questions
Our primary objective is to find the obstacles in planning, creating, and managing data protection. To achieve this objective, relevant study questions have been devised.
RQ 1 What is the current state of the art in the development and implementation of secure DBs?
To address RQ1, we have studied the material depending on the sub-questions mentioned above:
RQ 1.1 n terms of reliable data modeling, development, and maintenance, which stage has received the most attention in the research?
RQ 1.2 What are the primary sites for robust DB design?
RQ 1.3 What are the ongoing research organizations working in robust data modeling?
RQ 1.4 What kinds of DB attacks have been described in the research?
RQ 1.5 According to the research, what are the various categories of DB's?
RQ 1.6 What kinds of DBMS platforms are often employed, as stated in the literature.
RQ 2 What are the security issues in building, implementing, and maintaining secure DBs, as reported in the literature?
3.2 Search strategy
The scholars in [ 36 , 37 , 38 ] employed the PICO (Population, Intervention, Comparison, and Outcomes) framework to develop a list of terms and then drew search terms from research questions.
Population DB’s and software development in general.
Intervention Security Strategies.
Comparison No assessments proceed for the ongoing investigation.
Outcomes Reliable DB’s.
3.3 Search strings
After several tries, the following two search terms were selected to link the PICO aspects by utilizing Boolean connector (AND):
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database intrusion” OR “Database prevention”) AND (“Security Mechanisms” OR “Security Models” OR “Security methods” OR “Security policies” OR “Security techniques” OR “Security Guidelines”)).
For Science Direct online repository, we compressed the above search term due to space limits. As a result, the accompanying keywords were entered into the ScienceDirect database:
((“Database security” OR “Secure Databases” OR “Database protection” OR “Guarding Database” OR “Database prevention”) AND (“Security Mechanisms” OR “Security methods” OR “Security techniques” OR “Security guidelines”)).
3.4 Literature resources
We choose below digital repositories (A to F) to do our SMS and execute the search stings for acquiring publications.
IEEE xplore–B
Springer link–C
AIS electronic library (AiSel)–D
Science direct–E
Wiley online library–F
3.5 Research evaluation criteria
Titles, abstracts, entire readings, and quality assessments were all factors in our selection of research publications. The primary goal of the selection process is to compile an appropriate collection of papers by imposing inclusion and exclusion standards on submissions. We have set the accompanying inclusion and exclusion criteria to perform our SMS effectively. The same inclusion and exclusion criteria have been used in other studies [ 39 , 40 , 41 ]
3.5.1 Inclusion criteria
Only articles that meet one or more of the below criteria were considered for inclusion in our collection.
I1 Research involving the design and implementation of database security measures.
I2 Research that explains how to protect DB’s.
I3 Research the difficulties and dangers of creating, implementing, and maintaining safe DB’s.
I4 Research on the planning, development, and management of reliable DB's included in this category.
3.5.2 Exclusion criteria
The preceding exclusion criteria were considered to find relevant articles.
E1 Publications that are not published in the English language.
E2 No consideration will be given to materials that haven’t been published in any journal, magazine, or conference proceedings, such as unpublished books and grey material.
E3 Books as well as non-peer-reviewed articles, including briefs, proposals, keynotes, evaluations, tutorials, and forum discussions.
E4 Articles that aren’t published in their whole digital.
E5 Publications that don’t meet the inclusion requirements.
E6 Research is only provided as abstracts or PowerPoint slides.
We used the snowballing approach [ 42 , 43 , 44 ] in addition to the previous inclusion/exclusion criteria for our concluding decision. The snowball method was used to choose seven articles from various research repositories. Appendix 1 contains the papers selected using the snowballing approach, from 94 to 100. In the latest research, scholars have employed the same method [ 45 , 46 ].
3.6 Quality evaluation
All articles chosen in the selection have been evaluated for quality. Criteria for quality evaluation include:
To evaluate the papers, we used a three-point Likert scale (yes, partially, no) for every element of the quality evaluation criteria. We awarded each element of quality assessment criteria a score of 2 (yes), 1 (partially), or 0 (no) to achieve notable findings. Including an article in the SMS is permitted if it gained an average standard score of > or = 0.5. Many other scholars [ 45 , 47 , 48 , 49 ] have employed a similar approach. A list of all of the questions from Table 1 is included in the quality ranking.
3.7 Article selection
Employing Afzal et al. tollgate’s technique, we adjusted the key publication selection in our SMS analysis upon executing the search terms (Sect. 3.3 ) and online DB’s (Sect. 3.4 ) [ 50 ]. The five stages of this method are as follows: (Table 2 ).
Stage1 (St-1) Conducting literature searches in digital repositories/DB’s for most relevant articles.
Stage 2 (St-2) A article’s inclusion or removal is based on its title and abstract readings.
Stage 3 (St-3) To determine if an item should be included or not, the introduction and findings must be reviewed.
Stage 4 (St-4) the inclusion and exclusion of data analysis research are based on a full-text review of the research's findings.
In Stage 5 (St-5) most of the original studies that will be included in the SMS study have been vetted and selected for inclusion.
There were 4827 documents collected from the chosen web-based libraries/DB’s by imposing inclusion and exclusion criteria following the initial search string iteration (see Sect. 3.3 ). (Sects. 3.5.1 and 3.5.2 , respectively). The tollgate strategy led to a shortlist of 100 publications that were eventually selected for the research. Quality evaluation criteria were used to evaluate the selected articles (Sect. 3.6 ). Appendix 1 includes a collection of the publications that were ultimately chosen.
3.8 Extracting and synthesizing content
A survey of the articles reviewed is used to obtain the data. In order to address the questions stated in Sect. 3.1 , the entire content of every article has been reviewed, and pertinent data extracted. You can find a precise technique for extracting data in the SMS Protocol.
4 Description of key findings
A comprehensive mapping analysis was used throughout this study to determine current state-of-the-art and privacy issues in data modeling, development, and maintenance. Sections 4.1 , 4.2 , 4.3 , 4.4 , 4.5 and 4.6 contain the facts of our observations.
4.1 The current state of the art
RQ1 has been addressed using the below sub-questions as a reference (Sects. 4.1.1 , 4.1.2 , 4.1.3 , 4.1.4 , 4.1.5 and 4.1.6 ).
4.1.1 Stages in the building of a protected database
RQ 1.1 focuses on a reliable DB’s most frequently studied stages (design, development, and maintenance). As seen in Table 3 , the “design” step was mentioned in most publications at a rate of 27%. There is a 25 percent chance that you’ll hear about the “developing” stage. The “maintenance” stage was only mentioned in 5 of our SMS research findings.
4.1.2 Well-known sources for the building of reliable DB’s
RQ 1.2 is addressed in the second part of this SMS, which concentrates on the location of the papers chosen for this SMS. For venue and provider type analyses, we looked at five repositories, including A, B, C, D, and E. Tables 4 and 5 exhibit the snowballing method, which we refer to as “others.” Several of the papers from these collections were presented at conferences, journals, and workshops/symposia, among other venues. As shown in Table 4 , 45 out of 100 articles were published through the conference venue. Secondly, we found that, with a rate of 37 out of 100, a large percentage of the publications came from the journal channel. Workshops and symposiums accounted for 18% of the articles presented.
Table 4 lists a total of 100 articles spanning a wide range of topics related to DB privacy. This indicates that scholars have devoted a great deal of attention to this topic. “International Journal of Information Security(IJIS)”, “The International Journal on Very Large Data Bases (VLDB)”, “Computers and Security (C&S)”, “Digital Investigation (DI)”, “Journal of Natural Sciences (JNS)” and “Journal of Zhejiang University SCIENCE A (JZUS-A)” were found to be the most popular publications for privacy mechanisms in secure DB designing, as mentioned in Table 5 . We also discovered that the “Annual Computer Security Applications Conference(ACSAC)” and the “International Workshop on Digital Watermarking(IWDW)” are the most often referred articles on the issue of our research. Software engineering and other related domains can benefit greatly from DB privacy studies.
4.1.3 Research institutions participating in the construction of a reliable DB
The institution of the first researcher was utilized to determine and evaluate the highly ongoing researching institutes in the field of protected DB’s. Table 6 shows the findings for RQ 1.3, which reveal that “University of Florida, USA (UOF)” and “CISUC, University of Coimbra, Portugal (UOC)” produced the most research publications on protected DB’s (3 percent, each, out of 100). Ben-Gurion University of the Negev (BGU); RMIT University in Melbourne, Australia; YONSEI University in Seoul; TELECOM Bretagne in Brest, France(ENST); Anna University in Chennai, India (AUC); Huazhong University of Science and Technology in Wuhan (HUST); and George Mason University in Fairfax, Virgin Islands(GMU). BGU has presented two publications for each of the selected research.
4.1.4 The most common kind of DB attacks, according to academic research
RQ 1.4 is concerned with identifying the many kinds of DB attacks that have been recorded. Table 7 shows the three types of incidents: internal, external, and both (internal and external). To effectively understand intrusions, we must combine cyber-attacks with breaches by collaborators. Because both internal and external attacks are mentioned in one article, we refer to this as both (internal and external). Our SMS study’s “Both (Internal & External)” attacks had a rate of 52, according to the assessment in Table 7 . The bulk of the articles in our SMS survey highlighted “External” attacks with a frequency of 35%. In total, 13 papers in our SMS addressed the topic of “internal” attacks.
4.1.5 Database types that have been identified in the literature
To answer RQ 1.5, we must recognize the various DB’s discussed in the literature. Seventeen different DB’s have been documented in the research based on the data we gathered from the articles we included in our SMS. Table 8 shows that of the 100 articles in our SMS survey, 24 papers mentioned the term “Web DB.” Secondly, we found that “Commercial DB” appeared in 11 of the 100 articles in our SMS analysis. According to SMS, “multilevel DB and distributed DB” was mentioned in ten publications.
4.1.6 Kinds of database management systems (DBMS) presented in the research
Data management systems (DBMS) are examined in RQ 1.6. In this research, 11 distinct DBMS types have been documented based on our SMS data, which was gathered from a selection of studies. Most of the articles in our SMS survey mentioned an “Oracle DB system” with a 31 out of 100 rate, as shown in Table 9 . Secondly, “MySQL DB system” was mentioned in most of the publications in our SMS analysis (23 out of 100). Our SMS research found 21 publications that mentioned the term “SQL Server DB system.”
4.2 Issues in databases
As demonstrated in Table 10 and Fig. 3 our existing research into DB privacy has uncovered 20 issues from a pool of 100 studies (see Appendix 1 ).
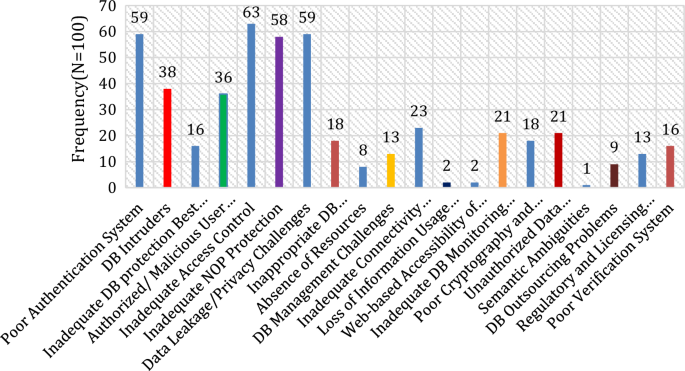
Issues in DB security
CC #1 Poor authentication system An unauthorized individual gains access to a DB, harvests vital information, and allows the hostile attacker to violate the safety of certified DB’s [ 1 , 51 ].
CC #2 Database intruders We are talking about when we say “threat database attacks” Anonymous queries (anomalous query attack), Harmful queries (query flood attack), and Inferential Attacks (polyinstantiation issue, aggregate problem).
CC #3: Inadequate database protection Best Strategies Specifications Engineering, Architectural, Planning, and Development all suffer from the absence of proper security procedures.
CC #4 Authorized/Malicious User Threats An authorized individual, employee, or administrator may collect or disclose critical data [ 52 ].
CC #5 Inadequate access contro Whenever many persons need access to the information, the risk of data fraud and leakage increases. The access should be restricted and regulated [ 1 ]
CC #6 Inadequate NOP protection Inadequate NOP Protection is a shortage of network privacy, operating system privacy, and physical safety.
CC #7 Data leakage/privacy challenges Clients of database systems are increasingly concerned about information security. Attacks on disclosed confidential information, including passwords, emails, and private photographs, triggered this issue. Individuals and database systems cannot stop the propagation of data exploitation and destruction once the content has been leaked [ 53 ].
CC #8 Inappropriate database implementation/configuration/maintenance Numerous DB’s are improperly setup, formatted, and maintained, among the main reasons for database privacy issues [ 54 ].
CC #9 Absence of resources When we talk about a shortage of resources, we are talking about a need of trained employees, a lack of time and budget, a shortage of reliable resources, and an insufficient storage capacity, to name a few things.
CC #10 Database management challenges There are aspects of effectively handling database systems, connectivity, and information at different levels [ 53 ].
CC #11 Inadequate connectivity platforms Presently, the majority of customer, user, and third-party conversations are conducted online. The inclusion of an insecure transmission medium was driven by the Internet’s opportunity to link DB’s [ 1 ].
CC #12 Loss of information usage monitoring Several users are unconcerned regarding their communications but may inadvertently send important information to an unauthorized person or untrustworthy servers. Because of a shortage of supervision of data consumption, they are also lost and destroyed [ 1 ].
CC #13 Web-based accessibility of tools for database attacks Several tools being used for intrusions are accessible in this globally networked domain, allowing intruders to expose weak spots with minimal expertise of the victim DB architecture [ 1 ].
CC #14 Inadequate database monitoring strategy Regulatory risk, discovery, mitigation, and restoration risk are just a few of the dangers posed by a lack of DB auditing [ 1 ].
CC #15 Poor cryptography and anonymization No DB privacy plan, regulation, or technology would be sufficient without cryptography, whether the information is traveling over a network or being kept in the DB system [ 1 ].
CC #16 Unauthorized data alteration/deletion Any type of unauthorized information alteration or deletion can result in substantial economic losses for an organization or corporation [ 55 ].
CC #17 Semantic ambiguities DB issues, including semantic uncertainty, which arises from an absence of semantics or inadequate semantic descriptions, dissemination issues, updating scope constraints, and tuple mistrust, are addressed [ 56 , 57 ].
CC #18: DB outsourcing problems : Because so many DB’s are now being outsourced, there are serious concerns about the data’s accuracy and safety. Clients will have to relinquish management of the information they have outsourced [ 58 , 59 ] .
CC #19 Regulatory and licensing challenges DB’s have many security issues, including policy and licensing concerns. Would the corporation have a consistent and approved policy and licensing from the authorities or organization [ 1 , 60 ]?
#20 Poor verification system A poor verification system allows an attacker to assume the credentials of a legitimate DB and access its data. The invader has a wide range of options for determining the identification of data. Assuming passwords are easy to remember [ 1 ] or using a preset username and password.
4.3 An assessment of database protection issues based on continents
There is much research on various continents in our SMS findings. A comparative analysis of only three continents, i.e., Europe, North America, and Asia, is discussed in this work (See Appendix 2 for more details). We want to find out if these issues are different across continents. We believe that by examining the similarities and distinctions among these problems, we may better prepare ourselves to deal with them on the continent in question. We employed the sequential correlation chi-square test to determine whether there were notable variations among the issues in the three continents listed previously (Martin, 2000). There are many more similarities than distinctions among the issues in the three continents. Poor authentication systems, DB intruders, inadequate DB protection best strategies, and authorized/ malicious user threats are the only major differences found in Table 11 . According to our findings, the most prevalent risks in the three continents are “Inadequate Access Control” (65%, 57%, and 64%), “Inadequate NOP Protection” (59%, 57%, and 60%), “Data Leakage/Privacy Challenges” (49%, 60%, 64%), and “Authorized/Malicious Individuals Threats” (40%, 20%, and 52%). It is not uncommon to see “Authorized/Malicious User Threats,” “Inadequate Access Control,” and “Inadequate NOP Security” across Europe and Asia. Inadequate Connectivity Platforms, Poor Verification Systems, Data Leakage/Privacy Challenges, and Regulatory and Licensing Challenges are some of the problems North American and European clients/users face while creating safe DB’s, as shown in Table 11 . According to our research, the “Poor Verification System” problem affects the most significant number of customers and users in Asia (78 percent). “Data Leakage/Privacy Challenges” is the most common issue faced by European customers and individuals (60 percent). Many customers in North America face “Inadequate Access Control” and “Data Leakage/Privacy Challenges” concerns, respectively (i.e., 64 percent) (Fig. 4 ).
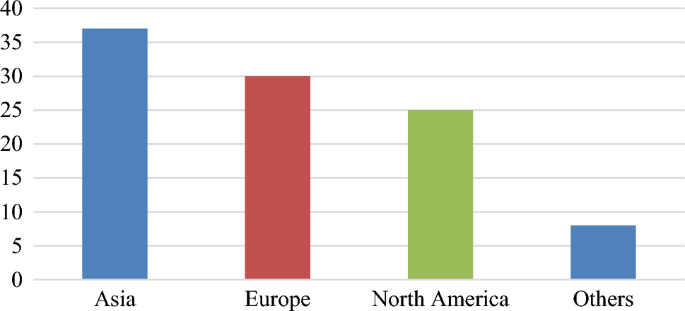
Distribution depending on continents
4.4 Methodological assessment of database privacy issues
Table 12 shows how we divided the different types of difficulties into three distinct approaches. Table 12 shows the three approaches used: tests, Ordinary literature review OLR, and Other/Mixed Approaches as shown in Fig. 5 . Other techniques include writing an experience report, conducting a case study, conducting a survey, and utilizing fuzzy methodologies. When we talk about “many methodologies,” we mean that more than one is employed in a single work. Testing is commonly utilized (39 out of 100 times, according to Table 12 ). The second notable finding in our SMS research is that 31 of the 100 participants used a standard literature review approach. Appendix 2 has further information. Many issues have been revealed by studying the distribution of publications among the three methodologies. Seventeen issues have been detected in relation to OLR, as shown in Table 12 . Two of the Seventeen issues have been mentioned in over 50% of the publications. Inadequate Access Control (74%), and Data Leakage/Privacy Challenges (52%), are two of the most often stated problems. Tests face a total of 18 difficulties. Four of these 18 issues have been quoted more than 50% of the time in at least one of the publications. “Data Leakage/Privacy Challenges—64 percent”, “Inadequate NOP Protection—62 percent”, “Poor Authentication System—56 percent”, and “Inadequate Access Control—56 percent” are among the most often stated difficulties. Other/Mixed Approaches publications have highlighted twenty difficulties. Moreover, half of the publications cited 4 of the 20 issues listed. “Poor Authentication System—73%”, “Inadequate NOP Protection—63%”, “Inadequate Access Control—60%”, and “Data Leakage/Privacy Challenges—60%” are among the most frequently stated problems.
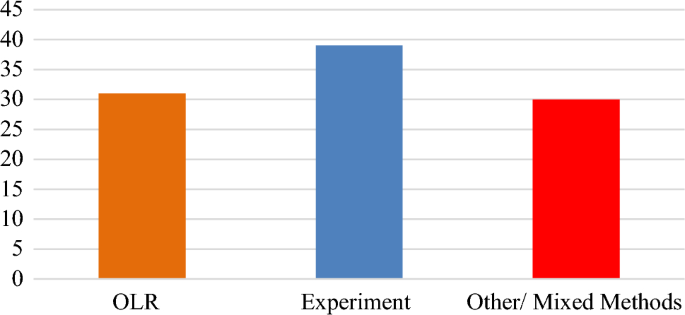
Methodological-based distribution of papers
Table 12 shows that no SMS approach was employed in any studies (n = 0). These findings prove that our study methodology is innovative in this particular field. We performed the Linear-by-Linear Chi-Square test for the earlier research-mentioned techniques and methodologies to establish whether there was a substantial difference between the challenges. “Poor Authentication System” and “Inappropriate DB implementation/configuration/maintenance” are the only notable variances.
4.5 Years-based study of database privacy issues
A comparison of issues over two time periods, 1990–2010 and 2011–2021, is shown in Table 13 and presented in Fig. 6 . More information can be found in Appendix 2 . Within the first phase; we found that 18 issues had been highlighted in the research. Four of the 18 issues have been quoted more than 50% in the publications. Inadequate Access Control (70 percent), Poor Authentication System (65 percent), Inadequate NOP Protection (62 percent), and Data Leakage/Privacy Challenges (52 percent) are the most commonly stated vulnerabilities. Between 1990 and 2010, 70 percent of DB’s had Inadequate Access Control, indicating that designers failed to effectively control access permission throughout implementationcontrol access permission throughout implementation.
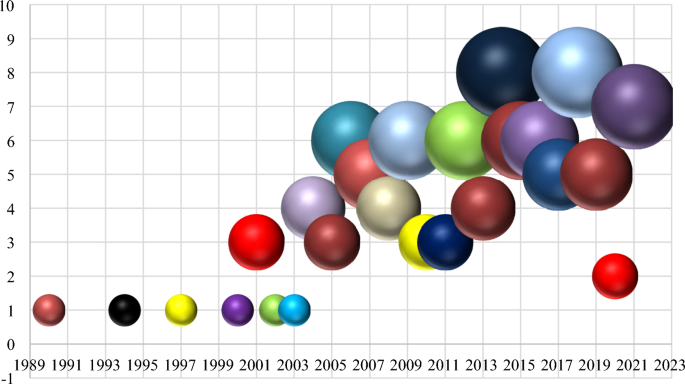
Year-based distribution of publications
Furthermore, admins in an organization are liable for ensuring that data is adequately protected via access permissions. The “Inadequate Access Control” difficulty has dropped to 58 percent in the second period. The literature has revealed 19 problems for the second time period. Four of the 19 obstacles have been referenced in at least half of the publications. “Data Leakage/Privacy Challenges” accounts for 63% of the faults, “Inadequate Access Control” for 58%, “Poor Authentication System” for 55%, and “Inadequate NOP Protection” for 55% of the issues, respectively. We used the Linear-by-Linear Chi-Square analysis and only identified a substantial variation for one problem, “DB Management Challenges, “with a p -value of less than.05.
4.6 Evaluation of articles based on their venue
Table 14 displays a breakdown of the various distribution methods. In addition to Journals, Symposiums, Conferences, and Workshops, we have presented our final articles on extracting data via SMS in various other publications venues as well. Journals, Workshops/Symposiums, and conferences have been classified into three categories for easy study. We found that 45 percent of our comprehensive study of articles was presented at conferences, according to Table 14 and Fig. 7 . Additionally, 37% of the publications in Table 14 were presented in new journals. For further information, please see Appendix 2 at the ending of the study. Many issues have been discovered as a result of distributing papers via these three channels. According to our findings, 18 issues with journals need to be addressed. Four of the 18 challenges have been referenced in at least half of the publications. “Privacy Issues/Data Leakage—84 percent,” “Inadequate Access Control”—59 percent, “Inadequate NOP Protection”—59 percent,” and “Poor Authentication System—54 percent” are the most often stated difficulties. Conferences face a total of 20 obstacles. Three of these 20 difficulties have been quoted more than 50% of the time in at least one publication. “Poor Authentication System—71 percent,” “Inadequate Access Control—69 percent,” and “Inadequate NOP Protection—62 percent” are the most often stated issues. Workshops/Symposiums face a total of 16 difficulties. Two issues have been mentioned in over half of the publications out of the 16 total. “Data Leakage/Privacy Challenges—61 percent” and “Inadequate Access Control—56 percent” are the most commonly reported hurdles. Linear-by-Linear Chi-Squared test has been used to find substantial differences throughout the difficulties. We have found just one big variation between the hurdles “Data Leakage/Privacy Challenges”.
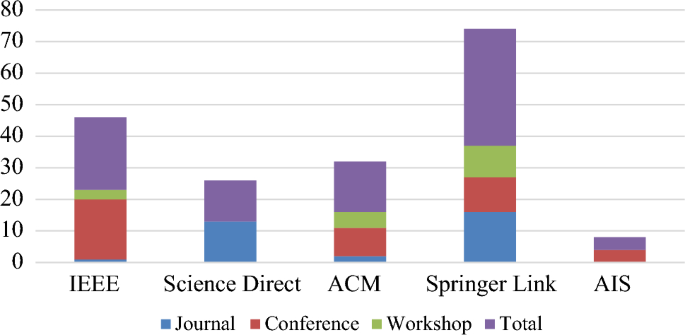
Venue-based distribution of articles
4.7 Comparison with existing studies
A wealth of studies have delved into various aspects of database security. Some of these have centered their attention on securing data transmission from server to client, while others have prioritized the construction of secure databases through secure coding practices. The increasing dependence on geographically dispersed information systems for daily operations might augment productivity and efficiency but simultaneously heightens the risk of security violations. Current security measures ensure data transmission protection, yet a comprehensive security strategy must also encompass mechanisms to enforce diverse access control policies. These policies should consider the content sensitivity, data attributes and traits, and other contextual data such as timing.
The consensus in the field is that effective access control systems should integrate data semantics. Moreover, strategies ensuring data integrity and availability must be customized for databases. Consequently, the database security community has developed an array of strategies and procedures over time to safeguard the privacy, integrity, and accessibility of stored data.
Nonetheless, despite these advancements, fresh challenges persist in the database security landscape. Evolving threats, data access “disintermediation,” and emerging computing paradigms and applications like grid-based computing and on-demand business have all introduced new security demands and innovative contexts where existing methodologies can be employed or extended. Despite a multitude of available solutions, raising awareness about existing security breaches is critical for bolstering database security.
In response, we decided to conduct a Systematic Mapping Study (SMS) on secure databases to offer an up-to-date perspective for both database users and developers. We did not find any comprehensive systematic literature review (SLR) or mapping study on this topic to draw comparisons with. However, we believe this research will offer a strategic roadmap for all database stakeholders.
5 Practical implications of research
The practical implications of this research are manifold and impactful. Initially, the results of this SMS will serve as an invaluable resource for DB privacy professionals and users. By leveraging the insights from this study, experts gain an enhanced understanding of DB privacy issues that need addressing. Consequently, they can prioritize their focus on the most significant security challenges. This, in turn, equips DB users with an awareness of their potential privacy risks. Thus, this study benefits consumers by assisting organizations in developing secure DB systems, mindful of the challenges they face (Table 10 ).
Furthermore, professionals such as DB designers, project managers, and scholars specializing in secure DB design are keen to keep abreast of the latest developments. This research provides DB developers with insights into novel strategies for DB security and the latest advancements in DB technology. Journals such as “VLDB,” “Computers & Security,” “DI,” and “JNS” should be of particular interest to them. Consequently, they would find it beneficial to scrutinize papers available from the “ACSAC” and “IWDW” Conferences and Workshops. The aforementioned venues present optimal resources for studying reliable DB development.
These venues, recognized for their focus on secure DB design, encourage scholars to contribute high-quality academic articles. The outcomes of this study will inform experts’ decision-making processes, providing guidance on where to invest when developing tools and methodologies for safeguarding DB systems. Lastly, it underscores the need for organizations to provide appropriate training for their customers to tackle critical challenges.
Acknowledgements
The authors would like to acknowledge the support provided by the Deanship of Scientific Research via project number DF201007 at King Fahd University of Petroleum and Minerals, Saudi Arabia.
Open Access funding provided by University of Oulu including Oulu University Hospital.
Author information
Authors and affiliations.
Department of Computer Science and IT, Software-Engineering-Research-Group (SERG-UOM), University of Malakand, Chakdara, Pakistan
Asif Iqbal & Siffat Ullah Khan
Information and Computer Science Department, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Mahmood Niazi
Interdisciplinary Research Center for Intelligent Secure Systems, King Fahd University of Petroleum and Minerals, Dhahran, 31261, Saudi Arabia
Department of Information Systems, College of Computer and Information Sciences, Jouf University, Sakaka, 72311, Saudi Arabia
Mamoona Humayun
Faculty of Computer Science and Information Technology, Universiti Malaysia Sarawak, Kota Samarahan, Sarawak, Malaysia
Najm Us Sama
M3S Empirical Software Engineering Research Unit, University of Oulu, Oulu, Finland
Arif Ali Khan
Lancaster University Leipzig, Leipzig, Germany
Aakash Ahmad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Arif Ali Khan .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
See Table 15 .
See Table 16 .
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Iqbal, A., Khan, S.U., Niazi, M. et al. Advancing database security: a comprehensive systematic mapping study of potential challenges. Wireless Netw (2023). https://doi.org/10.1007/s11276-023-03436-z
Download citation
Published : 17 July 2023
DOI : https://doi.org/10.1007/s11276-023-03436-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Database security
- Systematic mapping study
- Secure databases
- Modeling and maintenance of protected databases
- Issues in the development
- Find a journal
- Publish with us
- Track your research

Building a culture of cyber security
- Call for Change
- When Tech Meets Human Ingenuity
- A Valuable Difference
- Meet the Team
- Related Capabilities
Call for change
Before 2010, threats of ransomware and malicious malware seldom, if ever, made the news headlines. But as more and more information moved to the cloud and digital technologies expanded, so did the frequency and sophistication of such cyber attacks. This shift prompted organizations and individuals to do more to protect the information they stored and transferred within these infrastructures.
Within Accenture, a small team was tasked with formulating a response, strengthening and expanding our security defenses beyond technical systems, tools and controls by restructuring our security approach to meet Information Security Management System (ISMS) standards. Such standards looked to manage cyber security with a focus on people, processes and technologies, and served to establish the framework to protect Accenture’s global and increasingly mobile workforce.
Further, the team also undertook a formal assessment process in 2011, designed to create a comprehensive Information Security Risk Profile for the company. This move helped identify and prioritize security risks, as well as the actions necessary to prevent and protect against them. These transformative steps led Accenture to formally create the company’s information security organization.
Now with over 50,000 physical and virtual servers operating our business and supporting our clients, the Information Security organization is more than 800 people strong across the globe. The team’s expertise spans technical architecture and security operations, governance and risk management, acquisition integration, threat response and intelligence, compliance and behavior change.
“To protect the data we are entrusted with, our Information Security organization continues to adapt and optimize its risk resilience, addressing current cyber threats while preparing for new issues tomorrow might bring.” — KRIS BURKHARDT , Accenture Chief Information Security Officer
When tech meets human ingenuity
Our Information Security organization was developed around a strategy focused on building a resilient buffer against evolving threats and risks facing Accenture and our clients. This strategy also fosters a mindset within Accenture where everyone takes accountability for putting security first. A further aspect of the strategy is the establishment of several distinct areas and an extensive governance network led by the Chief Information Security Officer.
This network of accountability plays a critical and necessary role in maintaining Accenture’s security posture. The Information Security organization, which operates 24/7/365, can quickly respond to and address attacks, threat intelligence, system patching, vulnerabilities and workstation remediation. With Accenture’s increasing organic and inorganic growth, the areas of assessing acquisition security environments, employee security training and protecting our client data have become even more significant in the day to day activity of our organization.
As our Information Security organization has matured, cross-functional teams have been put in place to monitor and provide oversight to the security practices across a wider swath of Accenture’s business. Now, cross-collaborative groups like the Policy & Advisory Committee, Security Steering Committee and Accenture Information Security Leads meet and communicate regularly to ensure good security standings company-wide, or that concerns are raised and escalated promptly.

A valuable difference
Given an environment of aggressively growing cyber threats, Accenture’s risk tolerance has changed. In response, the industrialized processes of our Information Security organization continue to prove value, most visibly through the overall culture of shared accountability that has developed across the company. Through our team’s fine-tuned programs and processes, every Accenture employee understands they each play a role in keeping Accenture and its clients secure.
One tangible way this understanding has manifested is in employee participation in the award-winning Information Security Advocates program. This program engages each person in bite-sized, “gamified” security training exercises each quarter. Learning experiences on topics like social engineering , credential theft and working remotely are modified and refreshed regularly as new threat realities are identified. This training—a lot of which is voluntary—has shown that with each completion employees are much less likely to be involved in a security incident. And, on average, 99% of all employees become Information Security Advocates each year.
Another valuable capability from the evolution of Information Security is the I SO-certified Client Data Protection (CDP) program . This program provides Accenture client engagement teams with a standardized approach to managing risk through a set of security processes, controls and metrics. A CDP plan is developed for each client project and provides end-to-end security risk management measures covering physical, application, infrastructure and data security.
A further valuable outcome is detailed reporting. Key security performance indicators (KPIs) from across the business are captured and fed into a comprehensive Security Posture Scorecard (SPS). The contents are used to report out to the highest levels of Accenture leadership weekly, and to the Board of Directors twice a year. The dozen-plus KPIs include measures such as vulnerabilities, out-of-compliance servers, and misconfigured networked devices. In reviewing the SPS, Information Security teams have a very near real-time view of the global security posture. This view gives them the ability to take corrective actions more proactively and plan strategically.
Our Information Security organization’s continuous flexibility through a constant state of change and our ability to reinforce a security mindset across a global workforce, demonstrates one Accenture that protects client and Accenture information.
“Protecting our services and data are an absolute top priority and a cornerstone of our client relationships.” — JO DEBLAERE , Accenture Chief Operating Officer
Employee commitment
99% of all Accenture people are Information Security Advocates.
Secure devices
~1M workstations, servers, wireless access points and mobile devices secured.
Protecting client data
+2K client projects with active CDP plans.
Maintains certification for data-privacy standards.
CSA Security, Trust & Assurance Registry (STAR)
Awarded, and maintains, the highest Gold-level certification for Accenture-managed cloud infrastructure.
Accenture ranks top among its peers in maintaining a strong defense against threats, as reported by the leading cyber security rating vendors in each risk category.
Meet the team

Kris Burkhardt

Steve Zutovsky
Related capabilities, how accenture does it, information security at accenture.
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

Security Case Studies
Selected case studies on security challenges and solutions.
Security case studies: Selected in-depth explorations of how leading organizations have approached critical security challenges.
These case studies provide the chance to learn from your peers, whether you are creating an overall strategy or working to solve a specific tactical security problem. (Note: None of these articles were written or sponsored by product and service providers.)
Case study collection updated 10/16/2012.
Leadership and Organizational Issues
Governance, risk and compliance
Fiserv’s GRC process and software implementation (2012)
GRC is a process, not a technology. Fiserv identifies the benefits and challenges of its GRC work.
Alignment with corporate mission and profitability
Dunkin’ Brands security focuses on making dough (2010)
Aligning corporate security with corporate priorities makes everyone’s fortunes rise. A look behind the counter at Dunkin’ Donuts’ parent company. [Full article requires
E-discovery
NBC Universal takes e-discovery inhouse (2010)
NBC Universal saw requests for e-discovery services soar in just a few years. The company’s CISO, Jonathan Chow, knew there had to be a more efficient and cost-effective way to handle it.
Digital and Physical Security Convergence:
Constellation Energy (2005)
What does it take to make security convergence happen? One secret is to sneak up on it, the way Constellation Energy did, by seeming to be doing something else entirely.
Enterprise Risk Management:
All systems go at Georgetown University (2010)
ERM might seem a lofty concept, but Georgetown University provides an example of turning that concept into specific systems and projects that reduce risk.
Information Risk Management:
Harland-Clarke Rechecks Risk Management (2007)
New security program adds more systematic processes for evaluating, prioritizing and mitigating risk.
Departmental Organization:
Reinventing T-Mobile’s Security Function (2006)
T-Mobile needed to reinvent its security function, so it recruited a veteran team to shape a new asset protection division. The goal: Inject risk calculations into every business decision.
Safety and Community Relations:
Boston’s Infectious Disease Research Lab (2006)
When controversy hit, Kevin Tuohey became the public face of a high-profile plan to study deadly diseases in Boston. To succeed, the security director would have to become part diplomat, part great communicator.
Security Metrics, Budgets and ROI
Cost management:
IT security on a shoestring budget (2011)
Michael Dent, CISO of Fairfax County Government in Virginia, created an enterprise-wide IT security program with a fraction of the budget he wanted.
Budgeting, Metrics and Security Value:
American Water (2006)
How American Water’s Bruce Larson uses a simple metric to build bridges with business partners and justify security spending at the same time.
Project ROI:
Digital Video Surveillance at Intel (2005)
Allen Rude, security manager at Intel, invested more than four years in an ROI study to justify the cost of digital video surveillance.
Threats and Defenses
Advanced Persistent Threats:
APT in action: The Heartland breach
Heartland Payment Systems CTO Kris Herrin talks about the attack that changed his views on data security.
What’s the business case for GRC? (2012)
Governance, risk and compliance (GRC) can be a dauntingly complex undertaking. But for Fiserv, the alternative was even more complicated.
Situational Awareness:
Inside the new World Trade Center (2011)
Louis Barani leads the construction of an integrated system to help identify security and safety issues by connecting the dots faster.
Cloud security:
More tales from the cloud (2011)
Challenges and solutions at three companies moving into cloud-based IT services:
- Mohawk Fine Papers
Identity management:
How DTCC took on ID management (2011)
A look at why DTCC deployed identity and access management software from Hitachi ID Systems to automate its password management processes.
Access control:
Policy-based access control at a university (2010)
One school’s approach to maintaining security in an open environment.
Virtualization Security:
Virtual Server Security at Schwan Foods (2010)
When it comes to sampling innovative technology, Schwan Foods, a multibillion-dollar frozen food producer, digs right in.
DDOS and Online Extortion:
How a Bookmaker and a Whiz Kid Took On a DDOS-based Online Extortion Attack (2005)
What it’s like to get hit with a DDoS attack (2010)]
Facing an online extortion threat, bookmaker Mickey Richardson bet his Web-based business on a networking whiz from Sacramento who first beat back the bad guys, then helped the cops nab them.
Anatomy of a Fraud (2004)
Most fraud victims clam up. In this check-tampering case, the victim-a small-business owner-decided to speak out. The resulting cautionary tale offers a rare, detailed look into the mechanics and psychology of fraud. And its aftermath.
Phishing and Incident Response:
Midsize Bank (2005)
What happens after a phishing attack? Here’s one midsize bank’s phishing incident response plan.
Product Counterfeiting:
Drug Busters: Novartis (2005)
Novartis deploys a global team to track down counterfeit drugs and help authorities prosecute counterfeiters.
Video Surveillance:
Surveillance Cameras at Secaucus Junction (2005)
New Jersey Transit’s new station finds additional benefits in its security cameras.
School Security:
Securing the Suburban High School (2007)
Privacy, safety, security and budgeting considerations collide.
Crisis Communication:
Gale Global Facilities Services (2006)
With good planning, Web and mobile technologies can help find and inform employees in the event of a disaster. A global company shows how.
Simulations and exercises:
USAA’s Disaster Drill: Practice Makes Perfect (2003)
As one of the nation’s largest insurance companies, USAA is in the business of managing risk. So it makes sense that the company uses exercises, simulations and drills to learn how to respond in the event of a disaster.
Related content
Improved incident response planning is a business necessity, windows path conversion weirdness enables unprivileged rootkit behavior, rethinking work dynamics: why consumer browsers are no longer enough, ransomware feared in octapharma plasma’s us-wide shutdown, from our editors straight to your inbox.

Derek helped create and launch CSO in 2002, and served as Editor in Chief of the magazine and website from 2006 through 2013.
More from this author
33 questions to ask about your company’s security, sample erm organizational charts, 2011 state of the cso, getting the board on board, most popular authors.

Show me more
Top cybersecurity product news of the week.

Cisco fixes vulnerabilities in Integrated Management Controller

UK law enforcement busts online phishing marketplace

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

CSO Executive Sessions: Former convicted hacker Hieu Minh Ngo on blindspots in data protection

LockBit feud with law enforcement feels like a TV drama

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that’s compromised in most data breaches.
Database security must address and protect the following:
- The data in the database.
- The database management system (DBMS).
- Any associated applications.
- The physical database server or the virtual database server and the underlying hardware.
- The computing or network infrastructure that is used to access the database.
Database security is a complex and challenging endeavor that involves all aspects of information security technologies and practices. It’s also naturally at odds with database usability. The more accessible and usable the database, the more vulnerable it is to security threats; the more invulnerable the database is to threats, the more difficult it is to access and use. This paradox is sometimes referred to as Anderson’s Rule (link resides outside ibm.com).
Get insights to better manage the risk of a data breach with the latest Cost of a Data Breach report.
Register for the X-Force Threat Intelligence Index
By definition, a data breach is a failure to maintain the confidentiality of data in a database. How much harm a data breach inflicts on your enterprise depends on various consequences or factors:
- Compromised intellectual property: Your intellectual property—trade secrets, inventions, proprietary practices—can be critical to your ability to maintain a competitive advantage in your market. If that intellectual property is stolen or exposed, your competitive advantage can be difficult or impossible to maintain or recover.
- Damage to brand reputation: Customers or partners might be unwilling to buy your products or services (or do business with your company) if they don’t feel they can trust you to protect your data or theirs.
- Business continuity ( or lack thereof): Some businesses cannot continue to operate until a breach is resolved.
- Fines or penalties for non-compliance: The financial impact for failing to comply with global regulations such as the Sarbannes-Oxley Act (SAO) or Payment Card Industry Data Security Standard (PCI DSS), industry-specific data privacy regulations such as HIPAA, or regional data privacy regulations, such as Europe’s General Data Protection Regulation (GDPR) can be devastating, with fines in the worst cases exceeding several million dollars per violation .
- Costs of repairing breaches and notifying customers: In addition to the cost of communicating a breach to customer, a breached organization must pay for forensic and investigative activities, crisis management, triage, repair of the affected systems and more.
Many software misconfigurations, vulnerabilities or patterns of carelessness or misuse can result in breaches. The following are among the most common types or causes of database security attacks.
Insider threats
An insider threat is a security threat from any one of three sources with privileged access to the database:
- A malicious insider who intends to do harm.
- A negligent insider who makes errors that make the database vulnerable to attack.
- An infiltrator, an outsider who somehow obtains credentials via a scheme, such as phishing or by gaining access to the credential database itself.
Insider threats are among the most common causes of database security breaches and are often the result of allowing too many employees to hold privileged user access credentials.
Human error
Accidents, weak passwords, password sharing and other unwise or uninformed user behaviors continue to be the cause of nearly half (49%) of all reported data breaches .
Exploitation of database software vulnerabilities
Hackers make their living by finding and targeting vulnerabilities in all kinds of software, including database management software. All major commercial database software vendors and open source database management platforms issue regular security patches to address these vulnerabilities, but failure to apply these patches in a timely fashion can increase your exposure.

SQL or NoSQL injection attacks
A database-specific threat, these involve the insertion of arbitrary SQL or non-SQL attack strings into database queries that are served by web applications or HTTP headers. Organizations that don’t follow secure web application coding practices and perform regular vulnerability testing are open to these attacks.
Buffer overflow exploitation
Buffer overflow occurs when a process attempts to write more data to a fixed-length block of memory than it is allowed to hold. Attackers can use the excess data, which is stored in adjacent memory addresses, as a foundation from which to start attacks.
Malware is software that is written specifically to take advantage of vulnerabilities or otherwise cause damage to the database. Malware can arrive via any endpoint device connecting to the database’s network.
Attacks on backups
Organizations that fail to protect backup data with the same stringent controls that are used to protect the database itself can be vulnerable to attacks on backups.
These threats are exacerbated by the following:
- Growing data volumes: Data capture, storage and processing continues to grow exponentially across nearly all organizations. Any data security tools or practices need to be highly scalable to meet near and distant future needs.
- Infrastructure sprawl : Network environments are becoming increasingly complex, particularly as businesses move workloads to multicloud or hybrid cloud architectures, making the choice, deployment and management of security solutions ever more challenging.
- Increasingly stringent regulatory requirements: The worldwide regulatory compliance landscape continues to grow in complexity, making adhering to all mandates more difficult.
- Cybersecurity skills shortage: Experts predict there might be as many as 8 million unfilled cybersecurity positions by 2022 .
Denial of service (DoS and DDoS) attacks
In a denial of service (DoS) attack, the attacker deluges the target server—in this case the database server—with so many requests that the server can no longer fulfill legitimate requests from actual users, and, often, the server becomes unstable or crashes.
In a distributed denial of service attack (DDoS), the deluge comes from multiple servers, making it more difficult to stop the attack.
Because databases are network-accessible, any security threat to any component within or portion of the network infrastructure is also a threat to the database, and any attack impacting a user’s device or workstation can threaten the database. Thus, database security must extend far beyond the confines of the database alone.
When evaluating database security in your environment to decide on your team’s top priorities, consider each of the following areas:
- Physical security: Whether your database server is on-premises or in a cloud data center, it must be located within a secure, climate-controlled environment. If your database server is in a cloud data center, your cloud provider takes care of this for you.
- Administrative and network access controls: The practical minimum number of users should have access to the database, and their permissions should be restricted to the minimum levels necessary for them to do their jobs. Likewise, network access should be limited to the minimum level of permissions necessary.
- User account and device security: Always be aware of who is accessing the database and when and how the data is being used. Data monitoring solutions can alert you if data activities are unusual or appear risky. All user devices connecting to the network housing the database should be physically secure (in the hands of the right user only) and subject to security controls at all times.
- Encryption: All data, including data in the database and credential data, should be protected with best-in-class encryption while at rest and in transit. All encryption keys should be handled in accordance with best practice guidelines.
- Database software security: Always use the latest version of your database management software, and apply all patches when they are issued.
- Application and web server security: Any application or web server that interacts with the database can be a channel for attack and should be subject to ongoing security testing and best practice management.
- Backup security: All backups, copies or images of the database must be subject to the same (or equally stringent) security controls as the database itself.
- Auditing: Record all logins to the database server and operating system, and log all operations that are performed on sensitive data as well. Database security standard audits should be performed regularly.
In addition to implementing layered security controls across your entire network environment, database security requires you to establish the correct controls and policies for access to the database itself. These include:
- Administrative controls to govern installation, change and configuration management for the database.
- Preventive controls to govern access, encryption, tokenization and masking.
- Detective controls to monitor database activity monitoring and data loss prevention tools. These solutions make it possible to identify and alert on anomalous or suspicious activities.
Database security policies should be integrated with and support your overall business goals, such as protection of critical intellectual property and your cybersecurity policies and cloud security policies . Ensure that you have designated responsibility for maintaining and auditing security controls within your organization and that your policies complement those of your cloud provider in shared responsibility agreements. Security controls, security awareness training and education programs, and penetration testing and vulnerability assessment strategies should all be established in support of your formal security policies.
Today, a wide array of vendors offer data protection tools and platforms. A full-scale solution should include all of the following capabilities:
- Discovery: Look for a tool that can scan for and classify vulnerabilities across all your databases—whether they’re hosted in the cloud or on-premises—and offer recommendations for remediating any vulnerabilities that are identified. Discovery capabilities are often required to conform to regulatory compliance mandates.
- Data activity monitoring: The solution should be able to monitor and audit all data activities across all databases, regardless of whether your deployment is on-premises, in the cloud, or in a container . It should alert you to suspicious activities in real-time so that you can respond to threats more quickly. You’ll also want a solution that can enforce rules, policies and separation of duties and that offers visibility into the status of your data through a comprehensive and unified user interface. Make sure that any solution you choose can generate the reports you need to meet compliance requirements.
- Encryption and tokenization capabilities: Upon a breach, encryption offers a final line of defense against compromise. Any tool that you choose should include flexible encryption capabilities that can safeguard data in on-premises, cloud, hybrid or multicloud environments. Look for a tool with file, volume and application encryption capabilities that conform to your industry’s compliance requirements, which might demand tokenization (data masking) or advanced security key management capabilities.
- Data security optimization and risk analysis: A tool that can generate contextual insights by combining data security information with advanced analytics will enable you to accomplish optimization, risk analysis and reporting with ease. Choose a solution that can retain and synthesize large quantities of historical and recent data about the status and security of your databases, and look for one that offers data exploration, auditing and reporting capabilities through a comprehensive but user-friendly self-service dashboard.
Continuous edge-to-edge cloud protection for your data and applications with regulatory compliance.
Wide visibility, compliance and protection throughout the data security lifecycle.
Comprehensive data protection for the most critical enterprise data.
Learn more about data organization in the cloud.
Now in its 17th year, the 2022 Cost of a Data Breach report shares the latest insights into the expanding threat landscape and offers recommendations for how to save time and limit losses.
In this introduction to networking, learn how computer networks work, the architecture used to design networks, and how to keep them secure.
Learn how the IBM Security Guardium family of products can help your organization meet the changing threat landscape with advanced analytics, real-time alerts, streamlined compliance, automated data discovery classification and posture management.
Home > Learning Center > Database Security
Article's content
Database security, what is database security.
Database security includes a variety of measures used to secure database management systems from malicious cyber-attacks and illegitimate use. Database security programs are designed to protect not only the data within the database, but also the data management system itself, and every application that accesses it, from misuse, damage, and intrusion.
Database security encompasses tools, processes, and methodologies which establish security inside a database environment.
Database Security Threats
Many software vulnerabilities , misconfigurations, or patterns of misuse or carelessness could result in breaches. Here are a number of the most known causes and types of database security cyber threats.
Insider Threats
An insider threat is a security risk from one of the following three sources, each of which has privileged means of entry to the database:
- A malicious insider with ill-intent
- A negligent person within the organization who exposes the database to attack through careless actions
- An outsider who obtains credentials through social engineering or other methods, or gains access to the database’s credentials
An insider threat is one of the most typical causes of database security breaches and it often occurs because a lot of employees have been granted privileged user access.
Blog: How Insider Threats Drive Better Data Protection Strategies.
Human Error
Weak passwords, password sharing, accidental erasure or corruption of data, and other undesirable user behaviors are still the cause of almost half of data breaches reported.
Exploitation of Database Software Vulnerabilities
Attackers constantly attempt to isolate and target vulnerabilities in software, and database management software is a highly valuable target. New vulnerabilities are discovered daily, and all open source database management platforms and commercial database software vendors issue security patches regularly. However, if you don’t use these patches quickly, your database might be exposed to attack.
Even if you do apply patches on time, there is always the risk of zero-day attacks , when attackers discover a vulnerability, but it has not yet been discovered and patched by the database vendor.
Blog: Imperva Protects from New Spring Framework Zero-Day Vulnerabilities.
SQL/NoSQL Injection Attacks
A database-specific threat involves the use of arbitrary non-SQL and SQL attack strings into database queries. Typically, these are queries created as an extension of web application forms, or received via HTTP requests. Any database system is vulnerable to these attacks, if developers do not adhere to secure coding practices, and if the organization does not carry out regular vulnerability testing.
Buffer Overflow Attacks
Buffer overflow takes place when a process tries to write a large amount of data to a fixed-length block of memory, more than it is permitted to hold. Attackers might use the excess data, kept in adjacent memory addresses, as the starting point from which to launch attacks.
Denial of Service (DoS/DDoS) Attacks
In a denial of service (DoS) attack, the cybercriminal overwhelms the target service—in this instance the database server—using a large amount of fake requests. The result is that the server cannot carry out genuine requests from actual users, and often crashes or becomes unstable.
In a distributed denial of service attack (DDoS), fake traffic is generated by a large number of computers, participating in a botnet controlled by the attacker. This generates very large traffic volumes, which are difficult to stop without a highly scalable defensive architecture. Cloud-based DDoS protection services can scale up dynamically to address very large DDoS attacks .
Malware is software written to take advantage of vulnerabilities or to cause harm to a database. Malware could arrive through any endpoint device connected to the database’s network. Malware protection is important on any endpoint, but especially so on database servers, because of their high value and sensitivity.
An Evolving IT Environment
The evolving IT environment is making databases more susceptible to threats. Here are trends that can lead to new types of attacks on databases, or may require new defensive measures:
- Growing data volumes —storage, data capture, and processing is growing exponentially across almost all organizations. Any data security practices or tools must be highly scalable to address distant and near-future requirements.
- Distributed infrastructure— network environments are increasing in complexity, especially as businesses transfer workloads to hybrid cloud or multi-cloud architectures, making the deployment, management, and choice of security solutions more difficult.
- Increasingly tight regulatory requirements —the worldwide regulatory compliance landscape is growing in complexity, so following all mandates are becoming more challenging.
- Cybersecurity skills shortage —there is a global shortage of skilled cybersecurity professionals, and organizations are finding it difficult to fill security roles. This can make it more difficult to defend critical infrastructure, including databases.

Thales + Imperva: Trusted End-to-end Data Security
Register Now
How Can You Secure Your Database Server?
A database server is a physical or virtual machine running the database. Securing a database server, also known as “hardening”, is a process that includes physical security, network security, and secure operating system configuration.
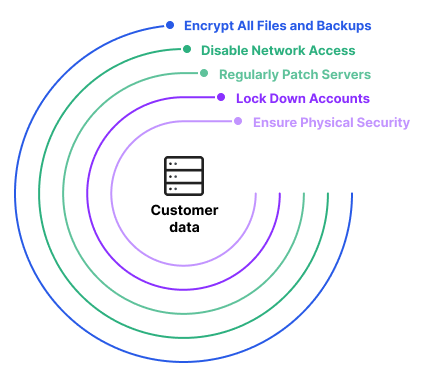
Ensure Physical Database Security
Refrain from sharing a server for web applications and database applications, if your database contains sensitive data. Although it could be cheaper, and easier, to host your site and database together on a hosting provider, you are placing the security of your data in someone else’s hands.
If you do rely on a web hosting service to manage your database, you should ensure that it is a company with a strong security track record. It is best to stay clear of free hosting services due to the possible lack of security.
If you manage your database in an on-premise data center, keep in mind that your data center is also prone to attacks from outsiders or insider threats. Ensure you have physical security measures, including locks, cameras, and security personnel in your physical facility. Any access to physical servers must be logged and only granted to authorized individuals.
In addition, do not leave database backups in locations that are publicly accessible, such as temporary partitions, web folders, or unsecured cloud storage buckets.
Lock Down Accounts and Privileges
Let’s consider the Oracle database server. After the database is installed, the Oracle database configuration assistant (DBCA) automatically expires and locks most of the default database user accounts.
If you install an Oracle database manually, this doesn’t happen and default privileged accounts won’t be expired or locked. Their password stays the same as their username, by default. An attacker will try to use these credentials first to connect to the database.
It is critical to ensure that every privileged account on a database server is configured with a strong, unique password. If accounts are not needed, they should be expired and locked.
For the remaining accounts, access has to be limited to the absolute minimum required. Each account should only have access to the tables and operations (for example, SELECT or INSERT) required by the user. Avoid creating user accounts with access to every table in the database.
Regularly Patch Database servers
Ensure that patches remain current. Effective database patch management is a crucial security practice because attackers are actively seeking out new security flaws in databases, and new viruses and malware appear on a daily basis.
A timely deployment of up-to-date versions of database service packs, critical security hotfixes, and cumulative updates will improve the stability of database performance.
Disable Public Network Access
Organizations store their applications in databases. In most real-world scenarios, the end-user doesn’t require direct access to the database. Thus, you should block all public network access to database servers unless you are a hosting provider. Ideally, an organization should set up gateway servers (VPN or SSH tunnels) for remote administrators.
Encrypt All Files and Backups
Irrespective of how solid your defenses are, there is always a possibility that a hacker may infiltrate your system. Yet, attackers are not the only threat to the security of your database. Your employees may also pose a risk to your business. There is always the possibility that a malicious or careless insider will gain access to a file they don’t have permission to access.
Encrypting your data makes it unreadable to both attackers and employees. Without an encryption key, they cannot access it, this provides a last line of defense against unwelcome intrusions. Encrypt all-important application files, data files, and backups so that unauthorized users cannot read your critical data.
Database Security Best Practices
Here are several best practices you can use to improve the security of sensitive databases.
Actively Manage Passwords and User Access
If you have a large organization, you must think about automating access management via password management or access management software. This will provide permitted users with a short-term password with the rights they need every time they need to gain access to a database.
It also keeps track of the activities completed during that time frame and stops administrators from sharing passwords. While administrators may feel that sharing passwords is convenient, however, doing so makes effective database accountability and security almost impossible.
In addition, the following security measures are recommended:
- Strong passwords must be enforced
- Password hashes must be salted and stored encrypted
- Accounts must be locked following multiple login attempts
- Accounts must be regularly reviewed and deactivated if staff move to different roles, leave the company, or no longer require the same level of access
Test Your Database Security
Once you have put in place your database security infrastructure, you must test it against a real threat. Auditing or performing penetration tests against your own database will help you get into the mindset of a cybercriminal and isolate any vulnerabilities you may have overlooked.
To make sure the test is comprehensive, involve ethical hackers or recognized penetration testing services in your security testing. Penetration testers provide extensive reports listing database vulnerabilities, and it is important to quickly investigate and remediate these vulnerabilities. Run a penetration test on a critical database system at least once per year.
Use Real-Time Database Monitoring
Continually scanning your database for breach attempts increases your security and lets you rapidly react to possible attacks.
In particular, File Integrity Monitoring (FIM) can help you log all actions carried out on the database’s server and to alert you of potential breaches. When FIM detects a change to important database files, ensure security teams are alerted and able to investigate and respond to the threat.
Use Web Application and Database Firewalls
You should use a firewall to protect your database server from database security threats. By default, a firewall does not permit access to traffic. It needs to also stop your database from starting outbound connections unless there is a particular reason for doing so.
As well as safeguarding the database with a firewall, you must deploy a web application firewall (WAF). This is because attacks aimed at web applications, including SQL injection , can be used to gain illicit access to your databases.
A database firewall will not stop most web application attacks, because traditional firewalls operate at the network layer, while web application layers operate at the application layer (layer 7 of the OSI model ). A WAF operates at layer 7 and is able to detect malicious web application traffic, such as SQL injection attacks, and block it before it can harm your database.
Imperva Database Security
Imperva provides an industry-leading Web Application Firewall , which can prevent web application attacks that affect databases, including SQL injection. We also provide file integrity protection (FIM) and file security technology, defending sensitive files from cybercriminals and malicious insiders.
In addition, Imperva protects all cloud-based data stores to ensure compliance and preserve the agility and cost benefits you get from your cloud investments:
Cloud Data Security – Simplify securing your cloud databases to catch up and keep up with DevOps. Imperva’s solution enables cloud-managed services users to rapidly gain visibility and control of cloud data.
Database Security – Imperva delivers analytics, protection, and response across your data assets, on-premise and in the cloud – giving you the risk visibility to prevent data breaches and avoid compliance incidents. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value.
Data Risk Analysis – Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation.
Latest Blogs

Brian Robertson
Apr 19, 2024 3 min read
- Industry Perspective

Lynne Murray
Apr 2, 2024 3 min read

Mar 11, 2024 4 min read

Feb 28, 2024 5 min read

, Paul Steen
Feb 26, 2024 5 min read

, Shiri Margel
Dec 1, 2023 5 min read
Latest Articles
- Data Security
174.9k Views
126.7k Views
114.5k Views
80.6k Views
78.9k Views
72.8k Views
2024 Bad Bot Report
Bad bots now represent almost one-third of all internet traffic
The State of API Security in 2024
Learn about the current API threat landscape and the key security insights for 2024
Protect Against Business Logic Abuse
Identify key capabilities to prevent attacks targeting your business logic
The State of Security Within eCommerce in 2022
Learn how automated threats and API attacks on retailers are increasing
Prevoty is now part of the Imperva Runtime Protection
Protection against zero-day attacks
No tuning, highly-accurate out-of-the-box
Effective against OWASP top 10 vulnerabilities
An Imperva security specialist will contact you shortly.
Top 3 US Retailer

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/cybersecurity-basics/case-study-series
Small Business Cybersecurity Corner
Small business cybersecurity case study series.
Ransomware, phishing, and ATM skimming are just a few very common and very damaging cybersecurity threats that Small Businesses need to watch out for. The following Case Studies were created by the National Cyber Security Alliance , with a grant from NIST, and should prove useful in stimulating ongoing learning for all business owners and their employees.
- Case 1: A Business Trip to South America Goes South Topic: ATM Skimming and Bank Fraud
- Case 2: A Construction Company Gets Hammered by a Keylogger Topic: Keylogging, Malware and Bank Fraud
- Case 3: Stolen Hospital Laptop Causes Heartburn Topic: Encryption and Business Security Standards
- Case 4: Hotel CEO Finds Unwanted Guests in Email Account Topic: Social Engineering and Phishing
- Case 5: A Dark Web of Issues for a Small Government Contractor Topic: Data Breach
Database security threats: A survey study
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

A Court of Auditors in Brazil Ensures Confidential Data Protection, Compliance, and Agility with Thales Technology - Case Study
The Court of Auditors of the State of Mato Grosso (TCE-MT) is the external public auditor responsible for looking after public property and supervising the use of resources. Any person or organization who uses public money, assets or securities originating from the State or from the 141 Municipalities must answer to the Court.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Case study of Database security in Campus ERP System

Related Papers
International Journal of Computer Applications
Mohd Muntjir
Frimpong Twum , Safianu Omar
Ulf Mattsson
Marijke Coetzee
Abstract The rapid growth of the Internet and the deployment of intranets and extranets increase the importance of connecting to existing databases. More than ever before, it is possible to deliver information instantly to thousands of internal and external users via XML and client interfaces.
Chanchala Joshi
Network vulnerability is the weaknesses in the network configuration that inadvertently allows dangerous operations and poses serious security threats. An attacker can exploit these vulnerabilities to gain unauthorized access to the system. Hence, detection and remediation of network vulnerabilities is critical for network security. This paper proposed method for effective risk level estimation by using a new introduced metric, the Hazard Metric (HM) which identifies the probability of attacks in user environments. As in network environment the number of attacks scenario increases, there is higher probability of compromising a target and thus the overall security of the network reduces. Thus, there is a need for quantification of security level of a specific network. The HM measures the probability of successful exploits by estimation of impact and likelihood of the attacks, which is to quantify the degree of security strength against vulnerability exploit in a network system. The proposed method prioritizes the mitigation of discovered vulnerabilities according to their risk levels. The methodology is tested in Vikram University Ujjain, India's network environment. The results represent the system trustworthiness.
International Journal of Information Sciences and Techniques (IJIST) , Emil Burtescu
In today's world, data is generated at a very rapid speed and final destination of such data is database. Data is stored in database for easy and efficient way to manage these data. All the operations of data manipulation and maintenance are done using Database Management System. Considering the importance of data in organization, it is absolutely essential to secure the data present in the database. A secure database is the one which is reciprocated from different possible database attacks. Security models are required to develop for databases. These models are different in many aspects as they are dealing with different issues of the database security. They may different also because of they are taking different assumptions about what constitutes a secure database. So, it becomes very difficult for database security seekers to select appropriate model for securing their database. In this paper, we have discussed some of the attacks that can be possible with its counter measures and its control methods that can be possible. Securing database is important approach for the planning of explicit and directive based database security requirements. Ensuring security for database is very critical issues for the companies. As complexity of database increases, we may tend to have more complex security issues of database.
Journal of Computer Science IJCSIS
Recently, due to economical escalation & with the need of advancements in national strategy based on scientific technologies, maximum institutions have been adopting their own campus network. That is why setting up campus network is being realized as important part of school education information. The utilization of campus network shares opportunity for teaching, scientific research and management to work together by using resources and exchange maximum information in minimum time. Hence, campus network security positively influences school teaching activities.
ijcaonline.org
Mozammel Bin Motalab
A Cloud Computing system is intended to improve and automate the controlling single point operations. By using a single point of control, this goal is accomplished through the elimination of duplicate entry and the contribution of data integrity, detailed drilldown, simple training, manageable support, minimal IT maintenance, easy upgrades and reduced costs. Overall, the advantages of cloud computing usage fulfill the original intentions of business as it allows process manufacturers to manage their business as simply and efficiently as possible. Enterprise Resource Planning (ERP) software is designed to improve and auto-mate business processes operations. However, there are many unnecessary administrative, procedural costs and delays often associated with this practice. Examples include duplicate data entry, data corruption, increased training, complicated supplier relations, greater IT support and software incompatibilities. Purpose of this system is Single Point of Control, Duplicate Entry Elimination, Data Integrity, Detail Drill Down, Basic Training, Manage Support, Security, Minimal IT Maintenance, Easy Upgrades, and Reduce Costs etc.
RELATED PAPERS
International Journal of Intellectual Advancements and Research in Engineering Computations
IJIAREC Journal
Reproductive Health of Woman
REPRODUCTIVE HEALTH OF WOMAN
Nisrina Qoriroh
R. S Harmon
Keryn Davis
Revista de Medicina
Marcelo L A Torres
Tonos Digital Revista Electronica De Estudios Filologicos
Mónica Olivares Leyva
Martha Yepez
Mediterranean Journal of Social Sciences
International Journal of Operational Research
Panos Pardalos
Proceedings of the 2015 ITiCSE on Working Group Reports
Margaret Hamilton
Journal of Neuroscience
S N Schiffmann
Don Garrett
Miriam Aceves
Peter Tozer
Cadernos EBAPE.BR
Marcia Borges
Journal of Economics and Sustainable Development
Suriyani Muhamad
pitrasacha adytia
American Journal of Analytical Chemistry
Rama Joga Eranki
Jean-Pierre Delahaye
American Journal of Physiology-endocrinology and Metabolism
Archives of Otolaryngology-head & Neck Surgery
Eric Holbrook
Civil Rights Project Proyecto Derechos Civiles
erica frankenberg
Paul Heisey
Frontiers in Psychology
Sabrina Grondhuis
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Maine City Enhances Data Security and Productivity With Modern Software
-- resource type , success stories , solutions , cybersecurity , erp , products , cybersecurity , enterprise erp --.
Organization Profile
- Industry : Municipal
- Location : Saco, Maine
- Number of Employees : 170
- Population : 20,381
- Tyler Client Since : 2002
- Tyler Products/Solutions : Enterprise ERP, Content Manager
The Challenge
As cities grow and adapt over time, technology also advances, creating new opportunities and challenges. The city of Saco, Maine, sought a modern solution to streamline software upgrades, aiming to enhance productivity and prioritize the safety of their data.
“The challenges that we were facing were mostly to do with ensuring that we could get updates and patches done efficiently,” said Ryan Pinheiro, IT director of Saco, Maine. “We wanted the upgrades to be done on our schedule.”
With the traditional method, Pinheiro and team were consistently monitoring the update process to make sure there were no issues and that upgrades were happening at the appropriate time. Pinheiro notes that when it came to scheduling upgrades, “it was hard to nail down when it was best for us and best for Tyler so that everyone [could be on the same page].” The city needed a solution that was trustworthy and dependable.
The Solution
With the requirement of more management of IT operations, the city adopted Tyler’s Deploy solution, a self-service upgrade tool allowing control over when to deploy and update software with minimal operational impact.
Because the tool was easy to set up and didn’t require additional check-ins with technicians, Deploy started to make a difference immediately. Pinheiro said thanks to Deploy, operations are no longer “affecting people and their ability to do business with the city, like registering their vehicles or applying for permits. I think the biggest thing is ensuring that our people have what they need right away.”
Deploy is such an easy system to use. It’s been beneficial to be able to perform everything on our own time and schedule so that we’re not affecting business hours.”
Ryan Pinheiro
City of Saco, IT Director
Tyler’s Deploy solution has enabled the city to routinely upgrade Tyler products on its own schedule. “I was really blown away at how easy it actually was to get it all done just by myself without intervention,” said Pinheiro.
Deploy has also improved the city’s operations by increasing schedule flexibility among technicians to focus more on management for IT operations. “We don’t have down time anymore,” Pinheiro noted. “Now that we’re able to do this ourselves, everything is done overnight.”
The Results
Because of Deploy, the city of Saco can securely install important software updates independently.
Prior to using Deploy, the city’s IT department relied on Tyler’s teams to complete the updates or would schedule the upgrades through support.
This solution has also made a positive impact on the community overall. “When citizens are able to come in on a Tuesday after an upgrade and do their business [without running into issues], you know it’s a good benefit for them.”
Case Study Highlights
- Thanks to the reliability of Tyler's consistent deployments, the Saco team no longer has to monitor upgrades to make sure they went out on time
- Tyler Deploy enabled employees to become more productive - no more after-hours shifts or unnecessary downtime
- The system was easy to get up and running without extra help or time-consuming troubleshooting
Get all the latest Tyler content you’ll ever want. Sign up for newsletters, webinars, blog updates, and more.
Related Content

- Free Case Studies
- Business Essays
Write My Case Study
Buy Case Study
Case Study Help
- Case Study For Sale
- Case Study Service
- Hire Writer
Case Study on Database Security Issues
Database security case study:.
Database security is the activity which is aimed at the protection of the information stored at the databases from the access of the third people and the illegal source of this information for various purposes. Nowadays information is the most valuable resource for every organization, because business, economics and politics exist due to the quality of information and its secure storage.Every organization, private and public has its own database where the whole valuable information is stored in security for the positive functioning of the institution. It is natural that every businessman and scientist who keeps important information about the further development of his firm or scientific project wants to keep this data in total security.Obviously, numerous third people and rivals want to steal the information and use it for their own benefit, so the problem of database security is probably the most important one for the successful existence of modern business, politics, science, etc.There are many types of threat which can damage the safety of a database.
First of all, there are hacker’s attacks which are aimed at the break of the security system, destruction or stealth of the information kept in the databases. Another threat is virus. There are numerous viral programmes which attack the network and destroy the security of the database having the aim to make it out of order. There are of course, such threats as physical damage of the database, overloading with information, which can damage the work of the system, etc. With the aim to protect databases from the illegal access the experts install up-to-date powerful security programmes, antivirus programmes and create several levels of protection.
We Will Write a Custom Case Study Specifically For You For Only $13.90/page!
Database security is the relevant problem for the research, because nowadays there is hardly an institution which does not have its own database which requires protection and the student is able to observe the issue on the definite example. The young professional is able to observe the issue on database security suggested by the professor ad find out about the cause of the problem and its effect. One should think about the factors which can be called the reason of the damage of the security and brainstorm the effective solution to the problem demonstrating knowledge and skills.The student is able to cope with his case study if he follows the advice of the free example case study on database security written by the real expert in the Internet for the student’s convenience.Everybody can use the tips and ideas of a free sample case study on database security in order to understand the right way of writing, organization of the text and research of the problem which can be accepted by the professor.
Related posts:
- Case Study on Database Management System
- Using the Case Study Provided at the End of the Module Identify and Explain the Client’s Issues and Devise a Course of Treatment for Him, Taking Into Account Any Ethical Issues.
- Essay on Security Plan
- Advantages of Using a Database
- Case study Security Officer
- Case Study on Network Security
- Case Study on Social Security
Quick Links
Privacy Policy
Terms and Conditions
Testimonials
Our Services
Case Study Writing Service
Case Studies For Sale
Our Company
Welcome to the world of case studies that can bring you high grades! Here, at ACaseStudy.com, we deliver professionally written papers, and the best grades for you from your professors are guaranteed!
[email protected] 804-506-0782 350 5th Ave, New York, NY 10118, USA
Acasestudy.com © 2007-2019 All rights reserved.

Hi! I'm Anna
Would you like to get a custom case study? How about receiving a customized one?
Haven't Found The Case Study You Want?
For Only $13.90/page
Asking the better questions that unlock new answers to the working world's most complex issues.
Trending topics
AI insights
EY podcasts
EY webcasts
Operations leaders
Technology leaders
Marketing and growth leaders
Cybersecurity and privacy leaders
Risk leaders
EY Center for Board Matters
EY helps clients create long-term value for all stakeholders. Enabled by data and technology, our services and solutions provide trust through assurance and help clients transform, grow and operate.
Artificial Intelligence (AI)
Strategy, transaction and transformation consulting
Technology transformation
Tax function operations
Climate change and sustainability services
EY Ecosystems
Supply chain and operations
EY Partner Ecosystem
Explore Services
We bring together extraordinary people, like you, to build a better working world.
Experienced professionals
MBA and advanced-degree students
Student and entry level programs
Contract workers
EY-Parthenon careers
Discover how EY insights and services are helping to reframe the future of your industry.
Case studies
Energy and resources
How data analytics can strengthen supply chain performance
13-Jul-2023 Ben Williams
How Takeda harnessed the power of the metaverse for positive human impact
26-Jun-2023 Edwina Fitzmaurice
Banking and Capital Markets
How cutting back infused higher quality in transaction monitoring
11-Jul-2023 Ron V. Giammarco
At EY, our purpose is building a better working world. The insights and services we provide help to create long-term value for clients, people and society, and to build trust in the capital markets.
EY is now carbon negative
19-Sep-2022 Carmine Di Sibio
Our commitment to audit quality
13-Nov-2023 Julie A. Boland
No results have been found
Recent Searches

BEPS 2.0: as policies evolve, engagement is key
It remains to be seen whether the US will align its tax law with the OECD/G20’s global BEPS 2.0 rules. MNEs will feel the impact in 2024. Learn more.

How GenAI strategy can transform innovation
Companies considering or investing in a transformative GenAI strategy should tie generative artificial intelligence use cases to revenue, cost and expense. Learn more

Top five private equity trends for 2024
Read about the five key trends private equity firms will emphasize in 2024 as they create value
Select your location
close expand_more
Consulting at EY is building a better working world by realizing business transformation through the power of people, technology and innovation.
The nature of work is evolving fast, we’re all being asked to adopt new behaviors — to be more innovative, more agile, more collaborative, more everything.
Business today is anything but usual. There is an urgency demanding we look ahead through a new lens, reframe the future and ask new and different questions:
- How do you create customer intimacy without proximity?
- Where does employee centricity meet the future of work?
- How can technology at speed create competitive advantage?
- Where does innovation at scale meet the new "S-curve" of growth?
By placing humans at the center, leveraging technology at speed and enabling innovation at scale, our clients are transforming to realize long-term value for people, business and society as a whole.
How organizations can stop skyrocketing AI use from fueling anxiety</p> "> How organizations can stop skyrocketing AI use from fueling anxiety

Discover c-suite executive agendas
- Technology leaders' agenda
- Operation leaders' agenda
- Marketing leaders' agenda
- Cyber and privacy leaders' agenda
- Risk leaders' agenda
- Finance leaders’ agenda
Explore our case study library

- Our case studies
- Our latest thinking
Explore our case studies

Natural language processing turns search speed into light speed
A managed care company saves hundreds of hours in compliance verification with a new, AI-enabled database. Learn more in this case study.

How strong data management becomes a real game-changer
For one video game company, a data-driven culture meant gigs of innovation. Learn more.

How a major health provider is putting care into patients’ hands
Learn how a leading health care system used digital transformation to enhance its telehealth application and better serve both patients and providers.

How Ownership Works used a digital springboard to launch a movement
EY teams helped create an online presence — providing employees with the opportunity to build wealth at work.

Why cybersecurity should be required reading for higher education
Following a full cybersecurity assessment, a university lands on a solution that can identify, triage and manage data risks.

How EY is delivering an exceptional experience for its workforce
Learn how EY People Advisory Services has helped the global EY organization realize one of the largest end-to-end HR transformations on record.
Explore our latest thinking

Can core platform modernization position a bank for future success?
Case study: how one regional bank used core platform modernization to build a strong foundation for future profitability.

Case study: Intelligent automation shifts a state agency into higher gear
In this case study, learn how a state agency used robotic process automation to serve its customers with speed and convenience.

What strategic ops mean for your business
Many executives think of operations as a cost center. A 180-degree shift in thinking could lead to competitive advantage. Learn more.

How companies are achieving distribution transformation at speed and scale
Read how organizations can improve global supply chain efficiency through an integrated network of distribution centers.

AI Summit NYC: How leaders are tapping the potential of AI
Read session summaries and watch videos from AI Summit NYC where leaders demonstrate how AI in business boosts efficiency and productivity and drives growth.

Six ways CFOs and CSCOs can collectively drive value
Despite the challenges of frequently diverging objectives, the value that these executives can collaboratively unlock is transformative. Learn more.
EY Consulting case studies are a window into how we work alongside our clients to deliver strategic, sustainable growth and success.
How EY can help
Transformation EQ™ services
EY Transformation EQ™ services help your business implement leading practices and harness the power of your people to drive transformation success. Learn more.
Service Leader

EY Global People Advisory Services Tax Deputy Leader
Business reinvention consulting services
EY Business reinvention consulting services can help your business deliver long-term value for customers, employees, businesses and society. Learn more.
Evolving technology and data through cloud services
EY’s Business transformation through cloud services can help your business unlock the agility, efficiency and innovation of composable business services. Learn more.
Commercial excellence services
EY Commercial excellence helps organizations unlock, create and sustain new organic value in a fast-changing world.
Customer experience services
The EY Customer Experience solution can help your business integrate CX programs that help deliver sustainable long-term value. Discover more.
Cybersecurity Transformation
Discover how EY's Cybersecurity Transformation solution can help your organization design, deliver, and maintain cybersecurity programs.
Data and Insight-driven Transformation solution
EY Data and Insight-Driven Transformation teams can help you use technology and data to modernize and innovate your business and prepare for future disruption. Learn more.
</b>Enterprise Resilience" href="https://www.ey.com/en_us/services/consulting/enterprise-resilience"> Enterprise Resilience
Discover how EY can help transform your business to navigate disruption with agility, stay competitive in the market and help generate long-term value.
Internal Audit Transformation Services
EY IA services can help your business define the IA vision to create value from thought leadership, digital insights, and risk management. Learn more.
Organization and Workforce Transformation
Our Organization and Workforce Transformation solution can help build workforce capabilities needed to realize organizational strategy. Read more.
People Experience solution
EY People Experience can help you build insight, develop interventions and scale people experience capabilities. Learn more.
Product and Service Innovation consulting services
EY Product and Service Innovation teams can help your business identify, define and design products and services that deliver long-term value. Discover more.
EY Supply Chain Transformation solution
Discover how EY's Supply Chain Transformation solution can help your business move towards fully autonomous, connected supply chains that drive business growth.
Sustainability governance, risk and compliance solution
EY Sustainability GRC can help you implement a digitally enabled ESG framework that is embedded in your operating model and meets regulatory requirements.
Transformation delivery solution
EY Transformation Delivery solution improves your confidence over time in achieving your transformation outcomes. Find out how.

Transformational leader. Innovator. Technologist. Complex problem solver. Strategist. Husband. Father. Mentor. Volunteer. Auto enthusiast.

Errol Gardner
Helping clients embrace disruption to drive change. Passionate about inclusion and mentoring. Avid Manchester United fan.

Lisa Caldwell
Recognized for building business models, systems and processes that drive profitable growth in highly competitive markets while championing the next generation of leaders.

Focused on driving technology transformation, innovation and strategy. Husband. Father. Volunteer. Golfer. Hockey fan. Supports diversity and inclusion.

Nalika Nanayakkara
Wealth and Asset management industry leader. Passionate about innovative market solutions as well as helping underserved demographic groups get the financial advice they need.

- Connect with us
- Our locations
- Do Not Sell or Share My Personal Information
- Legal and privacy
- Accessibility
- Open Facebook profile
- Open X profile
- Open LinkedIn profile
- Open Youtube profile
EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.
TechRepublic
Account information.

Share with Your Friends
XZ Utils Supply Chain Attack: A Threat Actor Spent Two Years to Implement a Linux Backdoor
Your email has been sent

A threat actor quietly spent the last two years integrating themself in the core team of maintainers of XZ Utils, a free software command-line data compressor widely used in Linux systems. The attacker slowly managed to integrate a backdoor in the software that was designed to interfere with SSHD and allow remote code execution via an SSH login certificate. The backdoor was discovered a few days before being released on several Linux systems worldwide.
The threat actor is suspected to be a developer with or using the name Jian Tan. Several security experts believe this supply chain attack might be state sponsored.
What is XZ Utils, and what is the XZ backdoor?
XZ Utils and its underlying library liblzma is a free software tool that implements both XZ and LZMA, which are two compression/decompression algorithms widely used in Unix-based systems, including Linux systems. XZ Utils is used by many operations on those systems for compressing and decompressing data.
The CVE-2024-3094 backdoor found in XZ Utils was implemented to interfere with authentication in SSHD , the OpenSSH server software that handles SSH connections. The backdoor enabled an attacker to execute remote code via an SSH login certificate. Only XZ Utils versions 5.6.0 and 5.6.1 are impacted.
How the XZ backdoor was implemented cautiously for more than years
On March 29, 2024, Microsoft software engineer Andres Freund reported the discovery of the backdoor . He found it when he became interested in odd behavior of a Debian sid installation, such as SSH logins taking a lot of CPU and Valgrind errors and decided to analyze the symptoms in depth. Freund explained that the discovery of the backdoor in XZ was luck , as it “really required a lot of coincidences.”
Yet it appears that the implementation of the backdoor has been a very quiet process that took about two years. In 2021, a developer named Jian Tan, username JiaT75, appeared out of the blue to start working on the XZ Utils code, which is not unusual because developers of free software often work together on updating code. Tan contributed frequently to the XZ project since late 2021, slowly building trust in the community.
In May 2022, an unknown user using the fake name Dennis Ens complained on the XZ mailing list that the software update was not satisfying. Another unknown user, Jigar Kumar, came into the discussion two times to pressure the main developer of XZ Utils, Lasse Collin, to add a maintainer to the project. “Progress will not happen until there is new maintainer,” Jigar Kumar wrote. “Why wait until 5.4.0 to change maintainer? Why delay what your repo needs?”
Meanwhile, Collin expressed that “Jia Tan has helped me off-list with XZ Utils and he might have a bigger role in the future at least with XZ Utils. It’s clear that my resources are too limited (thus the many emails waiting for replies) so something has to change in the long term.” (Collin wrote Jia in his message while other messages reference Jian. To add to the confusion, Jian’s nickname is JiaT75.)
In the months that followed, Tan became increasingly involved in XZ Utils and became co-maintainer of the project. In February 2024, Tan issued commits for versions 5.6.0 and 5.6.1 of XZ Utils, both of which contained the backdoor.
It is also interesting to note that in July 2023, Tan requested to disable ifunc (GNU indirect function) on oss-fuzz, a public tool made to detect software vulnerabilities. That operation was probably done to allow the backdoor in XZ to stay undetected once it was released, as the backdoor makes use of that function to achieve its goals.
Finally, several persons responsible for different Linux distributions have been contacted by the attacker to include the backdoored versions of XZ Utils in their own distributions. Richard WM Jones from RedHat wrote about it on a forum : “Very annoying – the apparent author of the backdoor was in communication with me over several weeks trying to get xz 5.6.x added to Fedora 40 & 41 because of it’s ‘great new features’. We even worked with him to fix the valgrind issue (which it turns out now was caused by the backdoor he had added). We had to race last night to fix the problem after an inadvertent break of the embargo. He has been part of the xz project for 2 years, adding all sorts of binary test files, and to be honest with this level of sophistication I would be suspicious of even older versions of xz until proven otherwise”. Tan also tried to have it included in Ubuntu .
XZ backdoor: A highly technical attack
In addition to the highly elaborated social engineering covered previously in this article, the backdoor itself is very complex.
Microsoft’s senior threat researcher Thomas Roccia designed and published an infographic to show the whole operation leading to CVE-2024-3094 ( Figure A ).
The backdoor is composed of several parts that have been included over multiple commits on the XZ Utils GitHub, described in depth by Freund .
Gynvael Coldwind, managing director of HexArcana Cybersecurity GmbH,a cybersecurity company providing consulting and courses services, wrote in a detailed analysis of the backdoor that “someone put a lot of effort for this to be pretty innocent looking and decently hidden. From binary test files used to store payload, to file carving, substitution ciphers, and an RC4 variant implemented in AWK all done with just standard command line tools. And all this in 3 stages of execution, and with an ‘extension’ system to future-proof things and not have to change the binary test files again.”
DOWNLOAD: Open source quick glossary from TechRepublic Premium
Martin Zugec, technical solutions director at Bitdefender, said in a statement provided to TechRepublic that “this appears to be a meticulously planned, multi-year attack, possibly backed by a state actor. Considering the massive efforts invested and the low prevalence of vulnerable systems we’re seeing, the threat actors responsible must be extremely unhappy right now that their new weapon was discovered before it could be widely deployed.”
Which operating systems are impacted by the XZ backdoor?
Thanks to Freund’s discovery, the attack was stopped before being spread on a wider scale. The cybersecurity company Tenable exposed the following operating systems known to be affected by the XZ backdoor:
- Fedora Rawhide.
- Fedora 40 Beta.
- Debian testing, unstable and experimental distributions versions 5.5.1alpha-01 to 5.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- Kali Linux.
- Arch Linux.
In a blog post, Red Hat reported that no versions of Red Hat Enterprise Linux are affected by CVE-2024-3094 .
Debian indicated that no stable version of the distribution are affected , and Ubuntu posted that no released versions of Ubuntu were affected .
MacOS homebrew package manager reverted XZ from 5.6.x to 5.4.6, an older yet safe version. Bo Anderson, maintainer and Homebrew technical steering committee member, declared that Homebrew does not “… believe Homebrew’s builds were compromised (the backdoor only applied to deb and rpm builds) but 5.6.x is being treated as no longer trustworthy and as a precaution we are forcing downgrades to 5.4.6.”
How to mitigate and protect from this XZ backdoor threat
More systems might be affected, especially those on which developers compiled the vulnerable versions of XZ. Security company Binarly offers an online detection tool that could be used to test systems to see if they are affected by the XZ backdoor.
The version of XZ should be carefully checked, as versions 5.6.0 and 5.6.1 contain the backdoor. It is advised to revert to a previous known safe version of XZ Utils, such as 5.4.
Software supply chain attacks are increasing
As previously reported on TechRepublic, software supply chain attacks are increasingly being used by threat actors.
Yet usual software supply chain attacks mostly consist of managing to compromise a key account in the process of the development of software, and use the account to push malicious content to legitimate software, which often gets detected quite rapidly. In the XZ Utils case, it is very different because the threat actor carefully managed to gain the trust of legitimate developers and become one of the maintainers of the tool, allowing him to slowly push different vulnerable parts of code into the software without being noticed.
Software supply chain attacks are not the only increasing threats; other supply chain attacks based on IT products are also increasing .
Therefore, companies should ensure that third parties are taken into consideration in their attack surface monitoring.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Subscribe to the Cybersecurity Insider Newsletter
Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. Delivered Tuesdays and Thursdays
- CISA Aims For More Robust Open Source Software Security for Government and Critical Infrastructure
- GitHub Universe: Open Source Trends Report and New AI Security Products
- 6 Best Open Source IAM Tools in 2024
- Hiring Kit: Security Analyst
- Cybersecurity: More must-read coverage

Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
What Suicide Data for Public Safety Officers Tell Us
Police officers are at a greater risk of dying by suicide than the general public, and even more likely to die by suicide than in the line of duty, according to evidence from prior research. But many fundamental questions have remained unanswered for lack of comprehensive data: who, where, how, in what roles, and in what circumstances are public safety personnel dying by suicide?
CNA has begun to address those questions, recently publishing the first examination of a systematic, national, and comprehensive effort to collect data on the extent of public safety deaths by suicide. This new research brief is an analysis of a database compiled by First H.E.L.P. , an organization that voluntarily collects data on suicides of law enforcement, correctional officers, firefighters, emergency medical personnel, and 911 telecommunicators. Our report focuses specifically on law enforcement and corrections personnel, examining the 1,287 deaths by suicide that were recorded from 2016 to 2022.
Suicide Data Findings
Among many other findings, the analysis found that annual public safety personnel deaths by suicide rose from 152 in 2016 to a peak of 234 recorded deaths in 2019 before declining during the pandemic. The number of deaths climbed again in 2022. It is possible that some of these changes are affected by data availability. As families, friends, and colleagues become increasingly willing to confront the stigma surrounding suicide and mental health, they may have become more inclined to provide the kind of voluntary data First H.E.L.P. collects. First H.E.L.P. has also suggested that the pandemic may have provided public safety personnel with a renewed sense of purpose, potentially reducing the incidence of suicide in 2020 and 2021.
Source: CNA analysis of First H.E.L.P. data.
Another important finding showed that 60 percent of officers who died by suicide were known to be experiencing some life challenges. The most prevalent of these challenges was depression, affecting 34 percent of those officers who died by suicide. It was followed by post-traumatic stress disorder, or PTSD, reported among 27 percent of officers. Taken together, mental health issues emerged as the category of life challenge affecting the highest proportion of public safety personnel, with 46 percent experiencing depression, PTSD, another mental illness, childhood trauma, or grief from the recent loss of a loved one. The second highest category was work-related challenges, encountered by 25 percent of these individuals. Another recent CNA report examining the work and life stressors among public safety personnel identified the most prominent stressors to be work/life balance, lack of support, being overworked and experiencing burnout, and challenges with colleagues.
Despite the majority of this group experiencing adversity, only 23 percent were reported to be seeking any kind of help. Approximately 17 percent of officers sought assistance for PTSD, and 7 percent sought any form of mental health treatment. CNA has previously explored deterrents to seeking mental health support, including concerns related to confidentiality, cultural competency, and stigma.
The data also indicate that White individuals account for 80 percent of deaths by suicide in this population, though they make up 69 percent of the public safety workforce. This is not entirely surprising. Studies of the broader U.S. population have found that Black individuals often exhibit lower rates of depression and anxiety than their White counterparts, despite facing greater exposure to stressors that typically undermine mental well-being.
We found that firearms were used in 82 percent of public safety personnel deaths by suicide. Since public safety personnel have greater access to firearms as a result of their profession, they must be afforded stronger protections against their unsafe use, including secure firearm storage. These are just a sampling of the findings contained in our report.
The Law Enforcement Suicide Data Collection Act
The insights afforded by analysis of First H.E.L.P. data hint at the necessity of a truly national dataset on suicides of public safety personnel. In 2020, Congress enacted the Law Enforcement Suicide Data Collection Act, which tasks the FBI with collecting national data on suicides. However, the FBI collects these data directly from law enforcement agencies, with limited success so far. The FBI reports 50 suicides for 2022 , submitted by just 39 law enforcement agencies nationwide. In contrast, First H.E.L.P. data reported 183 deaths by suicide using submissions from friends, family members, or acquaintances, as well as Google Alerts and social media. The work by the FBI is in its early stages, and it's essential to recognize and address any shortcomings in the existing data collection processes. There is a pressing need for further refinement and expansion of federal data collection methodologies to achieve a more comprehensive understanding of this critical issue on a national level.
The prevalence of deaths by suicide among public safety personnel is a public health crisis that affects the safety of all. Not only should we ensure the well-being of public safety personnel for humanitarian reasons, but the current level of stress experienced by public safety personnel is unsustainable—as indicated by waning national staffing levels . CNA analysts work with public safety agencies across the country to improve agency member well-being , and recently partnered with command staff of several public safety organizations to provide a webinar on organizational stress . This webinar provided an opportunity for peer learning about supervisory stress and the importance of the command staff in reducing organizational stressors for their supervisees. Continuing to address these work-related stressors is critical, as each death by suicide in the public safety community is already one too many.
Jessica Dockstader is an expert in officer wellness and Daniel Lawrence is a specialist in law enforcement research with CNA’s Center for Justice Research and Innovation . Special thanks to Karen Solomon, Joe Willis, Lew Solomon, and First H.E.L.P. for collecting and providing these data and collaborating with CNA on the analysis.
Related Articles
MIT Technology Review
- Newsletters
Taking AI to the next level in manufacturing
Reducing data, talent, and organizational barriers to achieve scale.
- MIT Technology Review Insights archive page
In partnership with Microsoft
Few technological advances have generated as much excitement as AI. In particular, generative AI seems to have taken business discourse to a fever pitch. Many manufacturing leaders express optimism: Research conducted by MIT Technology Review Insights found ambitions for AI development to be stronger in manufacturing than in most other sectors.

Manufacturers rightly view AI as integral to the creation of the hyper-automated intelligent factory. They see AI’s utility in enhancing product and process innovation, reducing cycle time, wringing ever more efficiency from operations and assets, improving maintenance, and strengthening security, while reducing carbon emissions. Some manufacturers that have invested to develop AI capabilities are still striving to achieve their objectives.
This study from MIT Technology Review Insights seeks to understand how manufacturers are generating benefits from AI use cases—particularly in engineering and design and in factory operations. The survey included 300 manufacturers that have begun working with AI. Most of these (64%) are currently researching or experimenting with AI. Some 35% have begun to put AI use cases into production. Many executives that responded to the survey indicate they intend to boost AI spending significantly during the next two years. Those who haven’t started AI in production are moving gradually. To facilitate use-case development and scaling, these manufacturers must address challenges with talents, skills, and data. Following are the study’s key findings:
- Talent, skills, and data are the main constraints on AI scaling. In both engineering and design and factory operations, manufacturers cite a deficit of talent and skills as their toughest challenge in scaling AI use cases. The closer use cases get to production, the harder this deficit bites. Many respondents say inadequate data quality and governance also hamper use-case development. Insufficient access to cloud-based compute power is another oft-cited constraint in engineering and design.
- The biggest players do the most spending, and have the highest expectations. In engineering and design, 58% of executives expect their organizations to increase AI spending by more than 10% during the next two years. And 43% say the same when it comes to factory operations. The largest manufacturers are far more likely to make big increases in investment than those in smaller—but still large—size categories.
- Desired AI gains are specific to manufacturing functions. The most common use cases deployed by manufacturers involve product design, conversational AI, and content creation. Knowledge management and quality control are those most frequently cited at pilot stage. In engineering and design, manufacturers chiefly seek AI gains in speed, efficiency, reduced failures, and security. In the factory, desired above all is better innovation, along with improved safety and a reduced carbon footprint.
- Scaling can stall without the right data foundations. Respondents are clear that AI use-case development is hampered by inadequate data quality (57%), weak data integration (54%), and weak governance (47%). Only about one in five manufacturers surveyed have production assets with data ready for use in existing AI models. That figure dwindles as manufacturers put use cases into production. The bigger the manufacturer, the greater the problem of unsuitable data is.
- Fragmentation must be addressed for AI to scale. Most manufacturers find some modernization of data architecture, infrastructure, and processes is needed to support AI, along with other technology and business priorities. A modernization strategy that improves interoperability of data systems between engineering and design and the factory, and between operational technology (OT) and information technology (IT), is a sound priority.
Artificial intelligence
Large language models can do jaw-dropping things. but nobody knows exactly why..
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
- Will Douglas Heaven archive page
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
What’s next for generative video
OpenAI's Sora has raised the bar for AI moviemaking. Here are four things to bear in mind as we wrap our heads around what's coming.
The AI Act is done. Here’s what will (and won’t) change
The hard work starts now.
- Melissa Heikkilä archive page
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.

IMAGES
VIDEO
COMMENTS
The exposed database contained 200 gigabytes worth of data belonging to Veeam, a backup and data recovery company. Among that data were customer records including names, email addresses and some IP addresses. How encryption may become a factor in scenarios like this: Usernames and passwords are a relatively weak way of securing private access ...
A Case Study of the Capital One Data Breach Nelson Novaes Neto, Stuart Madnick, Anchises Moraes G. de Paula, Natasha Malara Borges Working Paper CISL# 2020-07 ... and the legislation related to data security and privacy have been changing frequently in the past few years. For example, the data leak cases compromising a huge amount of data ...
A Famous Data Security Breach & PCI Case Study: Four Years Later. Secureworks. October 25, 2012. Heartland Payment Systems (HPS) became famous in January 2009 for something it didn't want to be famous for: it was the victim of one of the largest data security breaches in U.S. history, with tens of millions of cardholder records possibly lost ...
There are a number of studies that look at database security from different angles. In their study [], Mai et al. suggest using cloud-based security measures to safeguard power system databases.Using an RSA encryption method, public and private keys are generated for database encryption; a huge prime integer is chosen randomly from the cloud platform's Simple Storage Service and used as the ...
These transformative steps led Accenture to formally create the company's information security organization. Now with over 50,000 physical and virtual servers operating our business and supporting our clients, the Information Security organization is more than 800 people strong across the globe. The team's expertise spans technical ...
This case study is based off of CSA's Top Threats to Cloud Computing: Egregious Eleven Deep Dive.The Deep Dive connects the dots between CSA Top Threats through the use of nine real-world attacks and breaches. Pulling from one of the case studies, this article provides a security analysis overview of the Amazon Ring data breach.
Selected case studies on security challenges and solutions. Security case studies: Selected in-depth explorations of how leading organizations have approached critical security challenges. These ...
Database security refers to the range of tools, controls and measures designed to establish and preserve database confidentiality, integrity and availability. Confidentiality is the element that's compromised in most data breaches. Database security must address and protect the following: The data in the database.
Usab ility meets security: a datab ase c ase stud y. Y on g Wang, B harat S. Ra w al *. IST Department, Penn State Abington, PA 19001 USA. *Corresponding author E-mail: [email protected]. Ab stract ...
Case Study: Equifax Equifax was the victim of data hack in 2017 that affected at least 143 million consumers and resulted in the revelation of at least 209,000 consumer credit card details. Equifax was notified in 2016 about a XSS (Cross-site Scripting) vulnerability but failed to address it. (3) XSS is described as a type of injection:
Identification of security features and vulnerabilities that are found to affect the data tier of the web applications were examined. The findings from the study have shown that Microsoft SQL Server is more security feature-rich in terms of Confidentiality, Integrity, and Availability compared to PostgreSQL and Microsoft SQL Server is more ...
See how we can help you secure your web apps and data. Free Trial Schedule Demo. +1 866 926 4678. Learn how Imperva helps industry leaders protect business-critical data and applications, in the cloud, on-premises and in hybrid configurations.
Database security programs are designed to protect not only the data within the database, but also the data management system itself, and every application that accesses it, from misuse, damage, and intrusion. Database security encompasses tools, processes, and methodologies which establish security inside a database environment.
This has made organizations agile in terms of functioning and, at the same time, has posed new challenges. In this direction, the present study aims to explore and examine information security management (ISM) practices of two IT development and services organizations in India. In case study design, the study adopts qualitative research route ...
In this paper, we review security and usability scenarios. We propose security enhancement without losing usability. We apply this approach to popular application systems in the database. Specifically, we analyze database security in access control, auditing, authentication, encryption, integrity control, and backups. Finally, we present our recommendations for system security and usability to ...
The following Case Studies were created by the National Cyber Security Alliance, with a grant from NIST, and should prove useful in stimulating ongoing learning for all business owners and their employees. Case 1: A Business Trip to South America Goes South Topic: ATM Skimming and Bank Fraud; Case 2: A Construction Company Gets Hammered by a ...
Databases are the repositories of the most important and expensive information in the enterprise. With the increase in access to data stored in databases, the frequency of attacks against those databases has also increased. A database threat refers to an object, person or other entity that represents a risk of loss or corruption of sensitive data to an asset. Today, in many business ...
Abstract. This article is a case study about an Enterprise Data Security project including the strategy that addresses key areas of focus for database security encompassing all major RDBMS platforms. It presents the current state of database security tools and processes, the current needs of a typical enterprise, and a plan for evolving the ...
A Court of Auditors in Brazil Ensures Confidential Data Protection, Compliance, and Agility with Thales Technology - Case Study. The Court of Auditors of the State of Mato Grosso (TCE-MT) is the external public auditor responsible for looking after public property and supervising the use of resources. Any person or organization who uses public ...
Otherwise to set automatically logout the system when starts screensaver. 5. Vulnerability Assessment During the case study we have discuss major database security vulnerability for ERP database. All of the security procedures and technologies currently available cannot guarantee that any systems are safe from intrusion.
Encrypted data is the referral to cipher or encoded text. In a database, there are two states for data security. Data is in two statuses: at rest and in motion - data stored in a database, on a backup disk, or a hard drive. Once transiting through the network, it necessitates the use of various encryption solutions.
Organization Profile Industry: Municipal Location: Saco, Maine Number of Employees: 170 Population: 20,381 Tyler Client Since: 2002 Tyler Products/Solutions: Enterprise ERP, Content Manager The Challenge As cities grow and adapt over time, technology also advances, creating new opportunities and challenges. The city of Saco, Maine, sought a modern solution to streamline software upgrades ...
Highly sensitive financial records require stricter controls than general business communications. The aim is a DLP policy that ensures security without unnecessarily hindering agility. 4. Make the business case. Now comes a crucial step: Make a compelling business case to secure DLP program buy-in from leadership and affected departments.
Database Security Case Study: Database security is the activity which is aimed at the protection of the information stored at the databases from the access of the third people and the illegal source of this information for various purposes. Nowadays information is the most valuable resource for every organization, because business, economics and politics exist due to the quality of information ...
A managed care company saves hundreds of hours in compliance verification with a new, AI-enabled database. Learn more in this case study. 13 Sep 2023. How strong data management becomes a real game-changer For one video game company, a data-driven culture meant gigs of innovation. ...
A threat actor quietly spent the last two years integrating themself in the core team of maintainers of XZ Utils, a free software command-line data compressor widely used in Linux systems. The ...
The Law Enforcement Suicide Data Collection Act. The insights afforded by analysis of First H.E.L.P. data hint at the necessity of a truly national dataset on suicides of public safety personnel. In 2020, Congress enacted the Law Enforcement Suicide Data Collection Act, which tasks the FBI with collecting national data on suicides.
Engaging courses covering data structures, streams, search, security & more. ... Products Source available In-memory database for caching and streaming Redis Cloud Fully managed service integrated with Google Cloud, Azure, and AWS for production-ready apps Redis Software ... Customer case studies Read stories. Optimizing Pokémon GO with a ...
4.2 Criteria for Case Study Selection To choose the Case Study, a survey for a target (company or entity) that suffered a data leak incident between January 2018 and December 2019 was performed under the following two criteria: 1. Had enough technical details publicly available about the incident, and; 2.
To facilitate use-case development and scaling, these manufacturers must address challenges with talents, skills, and data. Following are the study's key findings: