- Pharmaceutical Engineering Magazine
- Online Exclusives
- Special Reports
- Facilities & Equipment
- Information Systems
- Product Development
- Production Systems
- Quality Systems
- Regulatory Compliance
- Research + Development
- Supply Chain Management
- White Papers
- iSpeak Blog
- Editorial Calendar
- Article of the Year
- Submit an Article
- Editorial Team

Quality Considerations in Disaster Recovery: A Case Study

Due to the growing digitalization of the industry, we are highly dependent on information technology (IT) systems and data. The basic ability to execute our pharmaceutical business and decision-making processes relies on the permanent availability of these IT systems and data to ensure compliance and efficiency of our business operations. But numerous factors—including criminal activities, political unrest, and environmental hazards—have made disaster recovery (DR) and business continuity planning essential.
A Growing Need for Disaster Recovery Plans
Cybersecurity attacks have been on the rise for many years, with ransomware and phishing being the top threats to our industry. A 2023 survey found that 66% of organizations experienced at least one ransomware attack. 1 How can the life sciences industry become more resilient against those attacks while acknowledging that 100% security cannot be established?
Appendix O10, “Business Continuity Management,” and Appendix O11, “Security Management,” in the ISPE GAMP® 5 Guide: A Risk-Based Approach to Compliant GxP Computerized Systems (Second Edition) provide excellent guidance for requirements and measures to prevent security incidents from happening and keep the business operational during a disaster. 2 Most companies rely on their backup and restore capabilities for their DR strategy; therefore, the backup setup, verification, and monitoring described in Appendix O9, “Backup and Restore,” should be considered. 2
Other standards also provide detailed guidance:
- ISO/IEC Standard 27000:2018 provides an overview of information security management systems, 3 including ISO 27031, A Standard for IT Disaster Recovery.
- ISO/IEC Standard 22301:2012 sets out the requirements for a business continuity management system. 4
DR, business continuity, and backup and restore are closely connected and need to be managed throughout the entire system and data life cycle (see Figure 1).
DR aims to anticipate and assess the impact of disasters and to build strategies and plans for how to recover from such disasters. In this context, a disaster may be related to IT (e.g., cybersecurity incident), staffing (e.g., pandemics), or facilities (e.g., natural disasters). Business continuity addresses how to keep the business processes operational in case of any disaster. In case of an IT-related (including IT facilities) disaster, the backup and restore capabilities are typically key to restoring IT systems, data, and services.
However, cybercriminals are increasingly designing their ransomware code as a time bomb to hinder the company from easily restoring their IT systems and data. Rather than encrypting data immediately after it gets past the corporate firewall, it begins to infect the data over time. Days, weeks, or months later, when the infected data has been backed up, it initiates the encryption of the corporate data. As the backup is also infected, it cannot be restored easily and may encrypt already restored data or systems.
The Human Factor
Humans tend to believe that disasters “only happen to other people.” And even if a disaster did happen to them, they are convinced that they would know how to deal with it. This combination of over-optimism, normalcy bias, and tendency to overvalue known short-term costs and under-value unknown long-term rewards is referred to as the “preparedness paradox” and is reflected in sentences like:
- “ Why would anyone attack us? We are too small/insignificant/etc.!”
- “ We have state-of-the-art IT protection. We are safe.”
- “ If the data center blows up, I’ll just walk over to the next IT store, buy new equipment, and bring it all back in no time.”
- “ If an IT system goes down, we can always restore it from the backup in no time at all. No further planning is required.”
- “ What do you mean when you say, ‘We need to test if we can restore data/systems from the backup?’ We are using a market-leading software, and it has not given us any errors or alarms. It works!”
- “ If the IT goes down, we just go back to paper. It worked in the past, didn’t it?”
This human trait often leads to:
- Lack of time, resources, and willingness to take this seriously and contribute (e.g., “This will never happen, so this is a waste of time.”)
- DR or business continuity plans (BCPs) that are not fit for purpose (e.g., badly designed or not up to date)
- Lack of robust testing of the plans (e.g., scenarios are too simple, assumptions are too positive, everything is simulated and not tested, or tests are always postponed due to “more urgent business”)
- Missing concepts for processing paper records and reintegration of these records into the restored computer systems
This is also reflected in the fact that only 50% of all companies test their DR annually or less frequently, whereas 7% do not test their DR at all. 5 But when a major security incident leads to widespread system issues and data loss strikes, what are the best practices? What are the benefits of appropriate planning? And what are potential challenges from a quality perspective?
In this article, the authors have created, based on several DR scenarios they have been involved in, a hypothetical case study of a successful ransomware attack to highlight potential pitfalls and provide guidance on how to restore regular business and compliance. However, the guidance can easily be adapted to other incidents that lead to significant data loss or system unavailability.
The Importance of Plans
Every regulated organization should have adequate DR and BCPs. These plans should cover a variety of potential disasters and provide detailed guidance on how to operate during a disaster and recover back to normal processes as quickly as possible. Furthermore, required roles and responsibilities should be defined and individuals to fill those roles identified.
- 1 Sophos. “The State of Ransomware 2023.” May 2023. https://assets.sophos.com/X24WTUEQ/at/c949g7693gsnjh9rb9gr8/sophos-state-of-ransomware-2023-wp.pdf
- 2 a b International Society for Pharmaceutical Engineering. ISPE GAMP® 5 Guide: A Risk-Based Approach to Compliant GxP Computerized Systems (Second Edition). North Bethesda, MD: International Society for Pharmaceutical Engineering, 2022.
- 3 ISO/IEC Standard 27000:2018. “Information Technology — Security Techniques — Information Security Management Systems — Overview and Vocabulary.” February 2018. www.iso.org/standard/73906.html
- 4 ISO/IEC Standard 22301:2012. “Societal Security — Business Continuity Management Systems — Requirements.” May 2015. www.iso.org/standard/50038.html#:~:text=ISO%2022301%3A2012%20specifies%20requirements%20to%20plan%2C%20establish%2C%20implement%2C,and%20recover%20from%20disruptive%20incidents%20when%20they%20arise
- 5 Computing Research. “When Plan B Goes Wrong: Avoiding the Pitfalls of DRaaS.” June 2021. https://iland.com/wp-content/uploads/2021/10/Whitepaper-iLand-Zerto-vs3.pdf
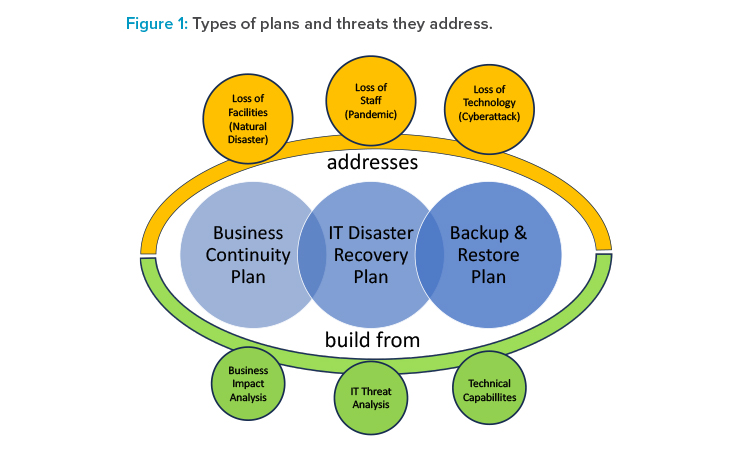
Organizations that do not spend the necessary time and resources on creating and maintaining these plans on an ongoing basis have already fallen for the first pitfall in DR. Without such plans, the significant amount of confusion that invariably happens once a disaster strikes is prolonged unnecessarily.
The organization may be paralyzed at the IT level and communicate through unusual channels, e.g., via social networks. But well-designed plans and robust communication can reduce the duration and intensity of this period significantly. Without a plan, communication channels and roles and responsibilities are unclear. Most organizations may not know what to do, how to communicate, or how to get further information.
DR and BCPs are worthless if they cannot be accessed in a disaster. Separate, secure, and accessible storage should be established for these documents, and supporting documentation (e.g., the business impact analysis or the risk assessment) should also be stored in that location. The value of DR and BCPs can also be diminished if they are not frequently reviewed and adequately tested to ensure they are fit for purpose.
The level of preparedness for such disasters can be assessed through internal audits that focus on DR and/or ransomware readiness. The Information Systems Audit and Control Association (ISACA) provides focused audit programs like the “IT Business Continuity/Disaster Recovery Audit Program” for these areas. 6 These audits may verify that the design of the IT landscape is resilient to widespread ransomware attacks, e.g., via an appropriate network architecture, as well as the existence and quality of plans and procedures.
A Hypothetical Case Study: Setting the Scene
Disasters can strike your organization in many ways, and every disaster is unique and requires unique recovery activities. Common to all IT disasters is that data and systems are either lost, not available, or stolen. This article does not consider natural disasters and similar incidents where the health and safety of the organization’s staff are directly at risk. The case study that we want to use as an example throughout the article is a midsized pharmaceutical company that has been hit by a ransomware attack.
- 6 Information Systems Audit and Control Association. “IT Business Continuity/Disaster Recovery Audit Program.” 2021. https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004KoEfEAK
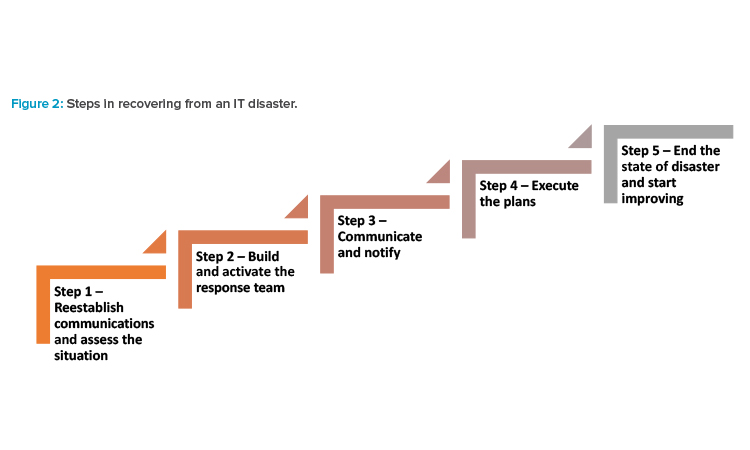
The ransomware encrypted most of the connected endpoint devices, infected system backups over a period of three months, and encrypted most servers in the organization. Also, data that was stored on cloud infrastructure had been encrypted. Electronic communication via email or collaboration platforms was not possible. The company has BCPs and an IT DR plan that is available on every site as a paper printout. A permanent disaster hotline is available for all staff. In our hypothetical case study, the organization followed the following DR steps (see Figure 2).
Step 1: Reestablish Communications and Assess the Situation
As a very first step, the organization needs to evaluate the extent and impact of the IT disaster. To enable any kind of DR activities, staff must identify the affected systems, data, and infrastructure. To achieve this, it is critical that key decision-makers, as outlined in the relevant plans, are informed of a potential disaster as quickly as possible and have the means to establish communications quickly and permanently without having to rely on company resources that may be unavailable in a disaster.
It is critical that the IT, quality, and relevant business, legal, and human resources departments are included in these early communications and assessments, as not only the impact on technology must be determined but also the potential downstream impacts on regulatory compliance, product quality, data integrity, patient safety and privacy, financial stability, and company reputation.
Once the damage has been contained by isolating affected systems to prevent further damage and after the extent of the disaster has been roughly established, the “responsible person” needs to declare the disaster. This may be the CEO, or other leadership, but it should be as outlined in the applicable plan, with backup leaders as needed should someone be unavailable.
Declaring the disaster is important because the company may suspend and/or adapt processes for the duration of the disaster, e.g., falling back on paper documentation and processes for impacted IT or business processes. The initial investigation must identify the technical root causes of the disaster so that any vulnerabilities or weaknesses that contributed to it can be considered when planning and making decisions on what to do next.
The leadership of the organization now needs to determine and balance the following aspects:
- How to enable business and reduce or limit financial loss for the organization (e.g., through short-term workarounds)
- How to restore manufacturing to produce critical products to ensure patient safety
- How to manage potential technology and IT supply chain constraints
- If and how the disaster impacts regulatory compliance
- How to handle data privacy implications (e.g., for data theft)
- How to meet legal/regulatory obligations (e.g., shareholder notification)
In our hypothetical case, communication could quickly be reestablished because the board of directors kept a list of the up-to-date contact information of the key decision-makers and other critical staff in a safe, “break-glass” location. That allowed key communications to be restored via social media, and meetings could be organized and conducted.
The initial assessment showed that affected systems included:
- Manufacturing systems, including the manufacturing execution system (MES)
- Laboratory systems, including the laboratory information management system (LIMS)
- Document management systems, including all standard operating procedures (SOPs)
- Pharmacovigilance system
- Email and collaboration platforms, intranet, and extranet
- IT systems for backup, including the configuration management database (CMDB) and service desk
- Financial systems
The root cause was a ransomware attack that was introduced to the organization by unknown means. Further forensics are initiated to identify the root cause. After careful consideration, it was decided not to pay the ransom and use the services of a prequalified IT security service provider to analyze the attack, determine the exact circumstances that introduced the ransomware to the organization, and help recover the data and systems.
Step 2: Build and Activate the Response Team
As a next step, the organization needs to assemble a team of experts responsible for managing the recovery process and assign roles and responsibilities to team members. With the team, the organization needs to prioritize the systems and data recovery in more detail and identify potential obstacles.
In our hypothetical case, the company made the following high-level decisions for response teams. Dependencies between the workstreams were identified and tasks were worked on in parallel wherever possible. The response team leaders aligned themselves in daily meetings.
Response team: infrastructure
- Priority 1: Establish a secure infrastructure environment, including backup services.
- Priority 2: Reestablish email and collaboration platforms, intranet, and extranet.
- Priority 3: Reestablish the CMDB and service desk.
Response team: applications and systems
- Priority 1: Reestablish the MES.
- Priority 2: Reestablish the LIMS.
- Priority 3: Reestablish the pharmacovigilance system.
- Priority 4: Reestablish the financial systems.
- Priority 5: Reestablish the document management systems, including all SOPs.
Response team: quality
- Priority 1: Assess risk to data integrity, product quality, patient safety, and regulatory compliance.
- Priority 2: Document the disaster, including all decisions and actions.
- Priority 3: Stand up support teams that establish basic processes for recovery activities.
Response team: legal
- Priority 1: Assess legal obligations and restrictions, including data privacy, financial, and other regulations.
Step 3: Communicate and Notify
It is crucial to inform relevant staff of the disaster and the next steps to be taken to reestablish normal operations as soon as possible as well as provide potential instructions for end users. This can, for example, be communicated via established support channels, if still available, or via announcements over a disaster hotline that has been established before the disaster.
Furthermore, the established group of decision-makers must decide on the potential need to communicate the disaster externally (e.g., to regulatory authorities, partners, or customers). All external communication, including to the media, must be tightly controlled and managed (e.g., for shareholder information).
In our hypothetical case, a toll-free disaster hotline number was available and was used to relay information and general instructions to the organization. Through this line of communication, which was supported by social media, town hall meetings could be organized to provide further information to the employees.
Regulatory authorities should be informed that the company will be unable to produce essential products that some patient groups depend on. The board of directors should inform all impacted partners. Communication with the public, including customers, is initiated, and overseen by the board of directors and managed/executed by the public relations department.
Step 4: Execute the Plans
By their very nature, BCPs and IT DR plans must be very flexible because disasters can strike an organization in many ways and can take many different forms. At the same time, the plans need to outline technical dependencies clearly and be based on the business impact analysis and the risk assessment that was done when the plans were created. With support from subject matter experts, the response teams now need to decide which parts of the plans must be implemented and build a strategy for recovering services and systems.
This is not the time for parts of the organization that did not contribute to plan development to question the plan’s basic structure. Any changes to the established plans, e.g., reprioritization of recovery activities, may require an impact and risk assessment to avoid undesired effects on the overall recovery activities and should require approval by the organization’s senior management.
The appropriate quality functions should be involved throughout the entire execution of BCPs and IT DR plans. Even in case of a disaster, quality and regulatory compliance must not be neglected. In such situations, quality functions need to be “enablers” that help establish critical documentation and records during recovery activities. The documentation will not be perfect but should be sufficient to allow justified decision-making on the release of systems and data that could impact product quality, patient safety, or data integrity.
Considering the challenges the organization is facing in such times, flexibility and critical thinking by everyone is absolutely required. In our hypothetical case, the analysis of the attack showed that:
- The attack already happened months ago and infiltrated all backups.
- The attack vector was phishing.
- The preventive technical controls were ineffective and not well maintained.
- The historically grown infrastructure was not designed to contain such an attack to a section of the IT landscape.
- The IT security service provider can decrypt the affected files with special tools and software re-engineering.
The BCP and IT DR plan provided the required order for the recovery of systems and data. The quality organization faced the following challenges that had not been considered in the plans:
Our company produces important (potentially life-saving) products that some patient groups depend on. What is the best way to avoid drug shortages without sacrificing product quality?
1: Drug shortages
“Our company produces important (potentially life-saving) products that some patient groups depend on. What is the best way to avoid drug shortages without sacrificing product quality?”
The BCP for the manufacturing process outlines and documents alternative ways to operate in case IT systems are unavailable. The approach was evaluated (including a risk assessment by quality assurance), adapted based on the nature of the disaster and the recovery planning, and discussed with applicable regulatory authorities as outlined in the European Medicines Agency’s regulatory guidance on drug shortages. 7 Once implemented, additional reviews, verifications, and checks are performed and documented to ensure data integrity, patient safety, and product quality are not at risk.
2: Documentation for audits and inspections
“How do we document the incident, the root cause, and the sequence of the events in such a way that it can be presented and defended in audits and inspections?”
Processes that are especially timebound like pharmacovigilance can be a significant challenge because regulatory timelines must be met during the disaster.
It was decided that a dedicated resource in quality would maintain a chronological issue log containing all activities and decisions. All quality and IT staff (including the IT security service provider) must copy this resource on all relevant communications. All created documentation must consider potential needs for confidentiality.
3: Interim processes
“How do we provide the organization with interim processes until the SOPs from the document management system have been restored?”
Interim processes and supporting templates are created by the quality organization and provided via a cloud storage provider. These processes are abbreviated, focusing on the essentials, and not extensively reviewed but approved by senior quality executives. The following order has been established for the creation of quality processes:
- Infrastructure qualification
- IT change control
- Validation of computerized systems
Training is done virtually, and attendance is recorded manually. In parallel, non-IT-related processes must be reestablished or restored (e.g., for manufacturing and quality control of medical products). The prioritization should be based on patient safety, product quality, and data integrity.
4: Data integrity
“How do we maintain data integrity during and after the disaster?”
Because alternate ways to operate involved the creation and/or processing of paper documentation, a task force was created to ensure appropriate handling of the paper records throughout the entire data life cycle and to develop a strategy to integrate the data once the IT system is available again.
This approach, already documented in the BCP and the business process requirements, was adapted for every system and business process individually, based on the specifics of the disaster (e.g., anticipated time to full system recovery).
Processes that are especially timebound like pharmacovigilance can be a significant challenge because regulatory timelines must be met during the disaster. After the disaster, all data must be integrated into the restored system to allow the processing of follow-up information and the ongoing analysis and evaluation of product safety.
5: Qualification of IT infrastructure
“How do we record the qualification of the IT infrastructure, including potential changes to the architecture and design to prevent such incidents going forward?”
The recovery activities start immediately based on security recommendations by the IT security service provider and are recorded informally, covering:
- Date and time of the activity
- Specification and configuration of the infrastructure
- Required verification activities
- Name of the person performing the activity
The quality department will establish an abbreviated process and templates for infrastructure qualification to be used going forward. When published, the process will be executed retrospectively and based on risk for already established infrastructure at that point in time. All created records must consider potential needs for confidentiality. The usage of tools and automation, where possible, is highly recommended.
6: Decryption tools
“How do we qualify the tools used to decrypt the data and systems? How do we know the data is correct and complete and the systems are fit for the intended use (also considering the changes to the underlying infrastructure)?”
Existing tools of the prequalified IT security service provider are used as is and qualified retrospectively. The qualification will leverage the existing vendor documentation and technical integrity checks to the extent possible. The testing of the tools focuses on:
- Identifying unencrypted files, databases, and servers
- Encrypting these items with the original ransomware in a controlled environment
- Decrypting them with the existing tools of the IT security service provider
- Verifying that the items and data are the same after processing and free from malware
If possible, the qualification of the recovery tools will be completed before the recovered systems and data are used in production again. All created documentation must consider potential needs for confidentiality and IT security. Systems that do not function as intended due to tighter security will be prioritized and investigated. All decrypted systems that are used productively without the qualification of the tools completed will be reviewed and released by the process owner and senior quality management.
7: Ransom situations
“How do we deal with data loss, e.g., data or systems that cannot be restored?”
For every logical group of lost data, a corrective and preventive action will be issued to investigate how the data was lost, the risk or impact of this data being lost, and measures that can be taken to prevent reoccurrence. Examples of data loss risks and impact include regulatory noncompliance (e.g., retention period), inability to recall the product, incomplete drug safety data, and lost business and financial impacts. Again, all created documentation must consider potential needs for confidentiality and IT security.
A similar approach could (and should) be used in scenarios where the ransom is paid and the key for decryption is provided.
To pay or not to pay
On average, 46% of the companies that were hit by a ransomware attack in 2022 paid the ransom, which was, on average, around $1.5 million US. 1 That makes ransomware a lucrative business model for cybercriminals, but law enforcement agencies recommend not paying the ransom. In fact, paying the ransom could even be illegal, because it could be violating the US Office of Foreign Assets Control’s regulations or other similar regulations 9 or interpreted as funding terrorism under the United Kingdom’s Terrorism Act. 10
Still, in many cases, it is easier, faster, and cheaper to pay the ransom than to recover from backup. The basic assumption is that if organizations pay the ransom, the attackers will provide a decryption tool and withdraw the threat to publish any potentially stolen data. However, payment does not guarantee all data will be restored. In reality, on average, only 65% of the data is recovered, and only 8% of organizations manage to recover all data. 8 After all, cybercriminals are not necessarily IT experts or software developers that you can trust.
In fact, encrypted files are often unrecoverable because the attacker-provided decryptors may crash or fail. In such cases, you may need to build a new decryption tool by extracting keys from the tool the attacker provides. This raises significant quality and data integrity concerns, as already outlined previously in step 3. Finally, “there is no honor among thieves”—paying a ransom may increase the likelihood of repeat attacks on an organization. The cybercriminals now know that your system is a good target and that you will pay a ransom.
Step 5: End the State of Disaster and Start Improving
When a predefined recovery level has been reached (e.g., all critical systems recovered), the state of disaster should be formally ended. This can be done for entire organizations or for individual areas of the business (e.g., when systems and/or data have been restored) so that the associated processes can be executed as they were before the disaster.
At that time, a thorough analysis of the incident should be performed to identify further areas of improvement. By this time, your organization will have a good estimate of the losses the company has suffered due to the incident. Based on the analysis, losses, and risk assessment, an improvement plan should be developed that may include:
- A review of processes to create and update BCPs and IT DR plans
- Hardening of infrastructure
- Zoning of networks
- Creating a DR instance of critical systems
- Storing of BCPs and IT DR plans outside of the company network
- Emergency contact information
The plan’s outcome and analysis should be considered in the remaining recovery activities and the implementation of all new systems and infrastructure going forward.
Best- And Worst-Case Disaster Recovery Approaches
What if a company is not as well prepared as the one in our hypothetical case study? Table 1 contains best-case approaches as outlined in the case study and worst-case alternatives and their consequences. This list is not exhaustive and is meant to encourage critical thinking and discussion around DR and business continuity.
As Scottish poet Robert Burns said: “The best-laid schemes of mice and men go oft awry.” However, if plans are created with the necessary care, they can be invaluable in an IT disaster. They reduce the initial state of confusion and allow for the prioritization of activities based on already performed risk assessments. Preselected and prequalified service providers for forensic analysis and data restoration may further reduce downtimes and speed up recovery activities.
The challenges to the quality organization during DR are many. Often activities are done in parallel, processes may be unavailable or not fit for purpose, and documentation may not be as controlled as it was when all systems were available. A pragmatic approach that focuses on product quality, patient safety, and data integrity and that is based on risk and critical thinking is essential.
Depending on the nature of the disaster, the quality organization may need to:
- Support the teams in the creation of required processes to support recovery activities.
- Support infrastructure qualification and computer system validation activities for systems that are restored or rebuilt.
- Assess data integrity of restored systems and data, including data integration activities after the system is restored.
- Support risk-management activities to ensure the effectiveness of workarounds and other short-term measures.
- Document the disaster, the subsequent analysis, the root cause, the corrective actions, and the lessons learned.
Every disaster is unique, and every organization needs to define its strategy and plans. The measures and controls described in this hypothetical case study may not be suitable for every organization. This case study provides a realistic disaster scenario and demonstrates the value of being prepared and having appropriate plans.
The internal audit program ensures regular reviews of business continuity and DR preparedness and compliance with company expectations. In our scenario, this was the case, and these plans were created using critical thinking that accepts that disasters will strike at some point in time.
For our hypothetical company, we can state that they were very well prepared and decisive. They did not simply focus on IT DR but had roles and responsibilities, priorities, and tasks that were planned beyond what was needed. This significantly contributed to getting the situation under control.
- 7 European Medicines Agency. “Guidance on detection and notification of shortages of medicinal products for Marketing Authorisation Holders (MAHs) in the Union (EEA).” July 2019. www.ema.europa.eu/en/documents/regulatory-procedural-guideline/guidance-detection-notification-shortages-medicinal-products-marketing-authorisation-holders-mahs_en.pdf
- 1
- 9 US Department of the Treasury’s Office of Foreign Assets Control. “Advisory on Potential Sanctions Risks for Facilitating Ransomware Payments.” October 2020. https://ofac.treasury.gov/media/48301/download?inline
- 10 Terrorism Act 2000. www.legislation.gov.uk/ukpga/2000/11/section/17
- 8 Gartner. “When it Comes to Ransomware, Should Your Company Pay?” 10 October 2021. www.gartner.com/en/articles/when-it-comes-to-ransomware-should-your-company-pay?
Unlock Access to Member-Only Content
Complete the form below to get exclusive access to Member-only content. Each issue of Pharmaceutical Engineering magazine features thought-provoking content that is available to Members only, but NOW we're giving you exclusive access to see what you've been missing out on.
By completing this form, you consent to have your information provided to the third-party sponsor of this content and may use your information to provide information about relevant products, services, and other opportunities which may be of interest to you . ISPE will store your information in a secure environment and may use your information to provide information about relevant products, services, and other opportunities which may be of interest to you. You may unsubscribe from these ISPE communications at any time. For more information or to unsubscribe, review our Privacy Policy or contact us at [email protected] .
- 'Share on Twitter'
About the Author

Related Articles

The FDA recommended CSA seeks to speed Computer System Validation (CSV) without sacrificing quality, but there’s a lot to know before you get started. This eBook, authored by CSV expert Darren Geaney, will give you a foundation of understanding so you can take the first step in your CSA journey with confidence.
In 2022, the US Food and Drug Administration (FDA) issued their draft guidance “Computer Software Assurance for Production and Quality System Software”
Digital display labels (DDLs) offer an alternative solution to eliminate manual relabeling in the clinical supply chain, optimizing label content updates through a simple, system-controlled approach while providing new, uncharted opportunities. With increased efficiency in making regulatory-compliant changes and enhanced flexibility in the clinical supply chain, DDL technology has the...
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Disaster Recovery Plan For Business Continuity: Case Study Of Business Sector

2016, Elsevier BV
An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned incidents that threaten an IT infrastructure, which includes hardware, software, networks, processes and people. Protecting your organization's investment in its technology infrastructure, and protecting your organization's ability to conduct business are the key reasons for implementing an IT disaster recovery plan.
Related Papers
Ahmed AL Zaidy
Court system plays a central role in the constitution in the United States, as information technology now involving in almost all aspects of the daily life, for businesses, government agencies, and individual’s activities. Courts also dependents on information technology, in computerize case management systems, electronic filing, electronic retrieval, and communications systems. Disasters can strike court systems as all other systems in the United States, as a natural disaster, and / or Human made disasters, therefor, having a plan that can help protect the systems, and data of the courts is an essential. The need of having a correct and affective disaster recovery, and business continuity plans efforts need to be taken serially and essential.
Michael Allen
cesar cobena
unkl 347 , Osama El-Temtamy , Munir Majdalawieh
Purpose – This purpose of this paper is to assess information technology (IT) disaster recovery plans (DRPs) in publicly listed companies on Abu Dhabi securities exchange (ADX) in the United Arab Emirates. The authors assessed, among other things, DRP preparedness, documentation, employees' preparedness and awareness and the most significant physical and logical risks that pose the most threads to drive the development of the DRP, etc. Design/methodology/approach – The authors surveyed publicly listed companies on the ADX using a questionnaire adapted from past research papers as well as from audit programs published by the Information Systems Audit and Control Association. The surveys were completed through interviews with middle and senior management familiar with their firm's IT practices. Findings – The majority of the respondents reported having a DRP, and a significant number of the respondents reported that their top management were extremely committed to their DRP. Employees were generally aware of their role and the existence of the DRP. The greatest risk/threat to their organization's IT system was logical risk followed closely by power and network connectivity loss as the second highest physical risk. The most highly ranked consequence of an IT disaster was loss of confidence in the organization. Research limitations/implications – Because this paper only examined publicly listed companies on ADX, the research results may lack generality. Therefore, further research is needed in this area for determining the extent of the deployment of the DRP in the region. Practical implications – Results of this paper could be used for IT DRP planning bench-marking purposes. Originality/value – This paper adds value to research by investigating the current IT DRP practices by public companies listed on ADX.
Yasin AKILLI
In accordance with the technological developments in today's world many companies implement their vital operations on their data centers and IT services.In connection with the fast development in technology and risimg complexity of business processes, the control of the systems and critical data that companies have, became more and more complicated. Therefore; it became an obligation for most companies to have a well-organized " Disaster Recovery Plan " .
AD-Minister (Journal) , Gustavo Ferreira G F J Jordao
It is safe to say that building disaster resilience by preparing for disasters with a business continuity plan is vital for small business to thrive in the long run. More often than not, small business owners invest large sums of money, time, and resources to make their ventures successful and yet, many of them fail to properly plan and prepare for disaster situations. With this problem in mind, Florida International University (FIU) became the house of the Small Business Development Center (SBDC) and the Extreme Events Institute (EEI). Together, both institutes have collaborated in their mission to spread disaster resilience and business continuity management knowledge and best practices in an accessible way to small businesses in South Florida and Latin America. By developing and disseminating knowledge, processes and best-practices through several activities and channels such as business consulting and business continuity plan elaboration, Pasantías (Practicums), and the Disaster Resilience Toolkit for Small-and-Medium-Sized Enterprises, both institutes truly represent FIU’s experience with SMEs and its commitment with entrepreneurship and South Florida’s community.
IAEME Publication
The business continuity plan describes the steps an organization takes when it cannot operate normally because of natural or manmade disaster. It may be written for a specific business process or may address for mission critical business processes. Business continuity and disaster recovery are critical components used to ensure that the systems essential to the operation of organization are available when needed. This is important to control the MTD (Mean Tolerable Downtime). A distributed disaster detection system that is based on agents. Disaster Recovery Plans is a crucial part of the life of an IT center in an organization; it contains policies and procedures to be applied before, during, and after a disaster of an IT system. However, an important part of the disaster recovery process comes when the disaster occurs up until the disaster recovery plan is activated. This is precious time to detect and declare a disaster especially in critical systems. Here, is a distributed disaster detection system that is based on agents. Agents are to be located on different servers in a data center and the will communicate with a central management unit. The Disaster recovery plan is aimed to complement the work of an existing disaster recovery system, or to run stand-alone if no disaster recovery system exists and act as a warning tool aiding the system administrator.
Rheumatology
Usama Al-Sari
alison brown
RELATED PAPERS
Zulfiqar Gilani
DR. S U N I T A DEVI
Theoretical & Applied Science
Simon M Karume
ASEAN Marketing Journal
rudi gunawan
Journal of Computer and Education Research
Fitopatologia Brasileira
mirian serrano
Physical Review D
Harald Soleng
Paisagem e Ambiente
Eugênio Queiroga
Research, Society and Development
Kewen Santiago da Silva Luz
Jesus Cegarra
BMC Public Health
Turk Kardiyoloji Dernegi Arsivi-Archives of the Turkish Society of Cardiology
Péter Domsik
Surface and Coatings Technology
Matthias Oechsner
Philosophical Transactions of the Royal Society B: Biological Sciences
Michael J Laver
Experiments in Fluids
Grazia Lamanna
Rekh Magazine Papers
Angelo Grossi , Maria Bologna
International Review of Psychiatry
Aleksandar Janca
Saurav Sarkar
Yafteh Lorestan University of Medical Sciences
Mehran Ghahramani
Physical Review Research
Boris Zaltzman
Alzahra university
jera journal
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Get your DRP / BCP on the cloud for the price of Latte
- Live Chat Support

Case Studies
The business scenario of Network-based Enterprises is one of tremendous growth, with organizations securing themselves with advanced technology tools as well as planning, monitoring, and maintenance of the overall IT infrastructure. Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP) are critical elements of organizational management, and involve the workable plan, process, procedures and policies that are effectuated to enable recovery and continuity of operations in the event of a natural or human-induced disaster. While a Disaster Recovery plan is focused on recovery restoration of the IT infrastructure, the Business Continuity Plan also includes in scope the non-IT related aspects that are related to the recovery/continuity process.
The case studies presented in this segment are typical examples of Disaster Recovery and Business Continuity through using proven technology solutions.
- Automotive Case Study – Disaster Recovery
- Bank Case Study – Disaster Recovery
- Electric Company Case Study
- Free Disaster Recovery Plan (DRP) Whitepaper
- Free Business Continuity Plan (BCP) Template
- View a Cloud based Disaster Recovery Solution
Name (required)
Title/Designation (required)
Company (required)
Email (required)
Phone/Mobile (required)
City (required)
State (required)
Country (required)
Please prove you are human by selecting the Plane .
Membership Overview
Membership renewal, frequently asked questions, special offers, knowledge center, knowledge center overview, publications.
- PAS Reports
- PAS QuickNotes
- Zoning Practice
Applied Research
- APA Foresight
- Green Communities
- Hazards Planning
- Planning and Community Health
Research KnowledgeBase
- Contributor's Dashboard
- Featured Collections
- Search All Collections
Topic Based Resources
- Autonomous Vehicles (AV)
- Climate Change
- Disaster Recovery
- Infrastructure
Planning Advisory Service
Conferences and learning, conferences and learning overview, national planning conference, planners' day on capitol hill, upskilling planners.

AICP Overview
One path to aicp, certification maintenance, maximize your credential, aicp fellows, policy and advocacy, policy and advocacy overview, policy issues, planners' advocacy network, state government affairs, amicus curiae, career center, career center overview, job seekers, advance your career, choosing the planning profession, mentoring at apa, in your community, in your community overview, what is planning, great places in america, national community planning month, national planning awards, planning home, consultants, connect with apa, connect with apa overview, students and new planners, member directory, awards and honors, equity diversity inclusion, advertise with apa, apa foundation.

APA Foundation Overview
Ways to give, apa scholarships, foundation donors, pre‐disaster planning for post‐disaster recovery: case studies, by: federal emergency management agency (fema), http://redevelopment.net/wp-content/uploads/2010/09/crs-case-studies_final.pdf, hazard mitigation.
This report surveys communities that have incorporated the Community Ratings System (CRS) into their post-disaster recovery planning. It gives an overview of flooding in the US and the CRS and discusses the role of post-disaster recovery planning. The report examines plan development, elements, and implementation in three case studies from Florida and one case study from Oregon.

Content Search
World + 1 more
Disaster recovery planning: Explanatory note and case study (June 2023)
Attachments.

Author(s): Steven Goldfinch, Anne Orquiza, Roberto Jovel, et al.
This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery. Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication shows how the cost to property, infrastructure, and production can be calculated and built into a PDNA.
This paper illustrates why PDNAs should consider key sectors such as health and energy, and factor the macroeconomic and personal impacts of catastrophic events into the total estimate of post-disaster recovery and reconstruction.
Explanatory Note
1. Introduction
A post-disaster needs assessment (PDNA) aims to assess the full extent of the impact of a disaster on a country and—based on its findings—produce an actionable and sustainable recovery strategy to mobilize financial and technical resources. If necessary, a PDNA will also request additional external cooperation and assistance for implementation, depending on the financial, technical, and institutional capacities of a country.
A PDNA should be designed to estimate the value of financial requirements to achieve recovery and reconstruction after a disaster. Guidelines have been developed, expanded, and refined using the initial methodology developed by the United Nations Economic Commission for Latin America and the Caribbean for the assessment of the value of destroyed physical assets and losses in the production of goods and services, and the formulation of the first PDNA Handbook. This process required quantitative and evidence-based information. However, the procedure to systematically and quantitatively estimate the required financial needs to achieve recovery and reconstruction has lagged. One significant development was a 2015 World Bank proposal for using a recovery framework to guide post-disaster activities for recovery and reconstruction.
Quantitative procedures for the estimation of the value of financial requirements only have been described in the guidance notes of the World Bank´s Global Facility for Disaster Reduction and Recovery. These notes served to estimate recovery and reconstruction needs as of 2010. This note draws from the facility’s guidance notes and from field experience acquired during many post-disaster assessments to provide comprehensive and quantitative procedures for the estimation of recovery and reconstruction financial requirements following disasters of any type, using as inputs the values of damage and losses arising from the PDNA.
Related Content
Philippines
Philippines: Typhoon Rai (Odette) - Emergency Appeal No. MDRPH045 - Final Report
Water and food security: wfp's contribution to the water sector, march 2024, joint statement of the humanitarian country team on the 10th year anniversary of super typhoon haiyan in the philippines, philippines: super typhoon haiyan (yolanda) - in retrospect - humanitarian impact and response achievements of the humanitarian country team (as of 26 october 2023).
20.500.12592/jrnzrp
Disaster Recovery Planning: Explanatory Note and Case Study
$refs.text.clientHeight" x-on:resize.window="isTruncated = $refs.text.scrollHeight > $refs.text.clientHeight" > This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery.Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication shows how the cost to property, infrastructure, and production can be calculated and built into a PDNA. It illustrates why PDNAs should consider key sectors such as health and energy, and factor the macroeconomic and personal impacts of catastrophic events into the total estimate of post-disaster recovery and reconstruction. environment climate change disaster risk management DOI http://dx.doi.org/10.22617/TIM230163-2 Dimensions 8.5x11 ISBN 978-92-9270-143-7(print) 978-92-9270-144-4(electronic) 978-92-9270-145-1(ebook) Published in Philippines SKU TIM230163-2 pages 46
Related Topics
Share artifact.
Or copy link:
If your institution is a member, please log into Policy Commons from a link provided by your institution. This typically involves logging in via a menu managed by your library.
Accessing this content requires a membership
Add to list
You have no lists yet
Create your first list:
1 ? 's' : ''}`" >
Full-page Screenshot
- Service & Support: 952.925.6868
- Client Portal
Search Loffler

Insights from Our Business Continuity & Disaster Recovery Case Study
We received the call late at night. Our client had been notified of an ongoing robbery in their main office and warehouse. The building housed their data center, and they needed to know they could still do business the next day.
With help from Loffler's Professional Services team, everything they needed was up and running by the next morning.
How? They had invested in disaster recovery and business continuity about a year before the robbery. Planning ahead can benefit any organization when disaster strikes.
Disaster Recovery Case Study Insights: How Total Tool Kept Working Despite a Disaster
Rewind to about a year before the robbery. Total Tool Supply had a data backup system to preserve their data on a daily basis.
What they didn’t have was a way to restore data quickly in the event of a disaster. If the worst were to occur, restoring from backup could take weeks, and vital systems they need to do business could be inaccessible.
Total Tool turned to Loffler for disaster recovery and business continuity (DR/BC). With Loffler's solution, if a business interruption caused Total Tool’s data center to become unavailable, they could switch to a secondary data center seamlessly. Everything would be up and running in minutes.
That’s exactly what happened, and exactly what they needed. Read the full case study .
Disaster Recovery vs Business Continuity: What's the Difference?
What is disaster recovery.
Disaster recovery is how you will preserve data when the unexpected occurs. It's how you will restore your systems when they would be otherwise unavailable. In today's world, a disaster could mean a power outage, a robbery or natural disasters like fires, floods or tornados. A disaster could be a cyber-attack, too , where once malicious actors compromise your system with technologies like ransomware, your data could be locked up indefinitely. Total Tool’s solution provided disaster recovery because it allowed them to fail-over to an off-site data center when their main one was in jeopardy.
What Is Business Continuity?
Business continuity is how you will keep doing business in the event that your main systems and/or work locations are inaccessible. If a disaster happens, you need a way to recover your data and you need a way for your business to continue forward. For example, many organizations enacted a business continuity plan in early 2020 when they needed employees to work from home . In the case of Total Tool, they ended up relying on their secondary data center for several weeks before the St. Paul data center was ready again.
Four Reasons to Plan Ahead for Disaster Recovery and Business Continuity
Disaster recovery and business continuity are different concepts, but they work together and are usually part of the same conversation. When you plan ahead and implement a DR/BC solution, you’ll see the following benefits.
1. Always know who to call
When disaster strikes, there is an unavoidable feeling of panic. The building is on fire. You've been hit by ransomware. The roof has caved in. What now?
When you have a DR/BC solution in place, you can answer that feeling of panic with the knowledge of what to do next. Total Tool knew to get on the phone with Loffler while the robbery was taking place. One of our senior engineers worked with them to restore their systems, even while the robbers were still in the building. Total Tool knew what to do because they had prepared for the worst.
2. Recover data in a timely manner
Total Tool was not comfortable with a data recovery time of two weeks. They could afford to be down hours, but not weeks. When talking about recovering from a disaster, we use terms like RPO and RTO to get a better understanding of an organization's risk tolerance:
- RPO, or Recovery Point Objective, is the measure of how far back you need your data to restore from. Do need everything up to one minute ago? One hour? One day?
- RTO, or Recovery Time Objective, is the measure of how soon you need to have all systems back up and running.
We work with clients and design DR/BC systems based on the answers we get from those two measurements. For Total Tool, this meant not missing a beat, despite the robbery and its threat to their data center, they were open for business as usual the next morning.
3. Continue business without interruption
Because a DR/BC solution is designed to fit your RTO and RPO specifications, you can recover from a disaster in a way that fits your business. Total Tool wanted a system that would get them back up and running without interruption, and that’s what they got. By the next morning, employees at their branch locations around the United States couldn’t tell an incident had occurred. Business was uninterrupted despite the robbery.
4. Mitigate the risk of losing everything
A little bit of planning goes a long way. When planning to survive a worst-case scenario, risk must be balanced with cost. Having a DR/BC solution is much like having a homeowner’s insurance policy. You hope that you never have to use it, but you need to have it in place in the event that something does occur.
One of the main questions you should ask when writing a business continuity plan is what’s the cost of being down — all systems down, unable to work — for one minute, versus one hour, versus one day, versus one week?
The question then becomes: How much are you willing to lose? Without a DR/BC solution in place, you may be risking several days of revenue or your business itself.
This was something Total Tool understood, and in the end they were thankful for their foresight. The luxury of only being down overnight kept them from losing money. The price they paid for DR/BC was a fraction of what they would have lost had they been down for weeks.
Most business owners don't think that a business outage can happen to them. They haven't faced a disaster yet.
One thing that Loffler companies does really well is listen to our clients. We help them understand what their risks are. Instead of having a single solution that fits all of our clients, we have a wide variety of options for our customers to choose from to solve their business needs. Disaster recovery and business continuity are part of Loffler's Professional Services offerings.

Read Next: 5 Data Storage Questions to Determine Your Needs

Jeff Gullickson
Jeff Gullickson is an Account Executive who has been part of Loffler's IT Solutions Group since 2005. He serves as a trusted resource for clients to find the best fit for their business IT needs.
Latest News

Managed IT Services Pricing (Cost Guide + Examples)

Navigating the Shift to a New Managed IT Services Provider

7 Cybersecurity Trends SMBs Should Be Aware of in 2024
- Global Assessment Report (GAR)
- PreventionWeb
Special Events
- Global Platform
- International Day for Disaster Reduction
- World Tsunami Awareness Day
- Sendai Framework Monitor
- Voluntary Commitments
Please help us improve PreventionWeb by taking this brief survey. Your input will allow us to better serve the needs of the DRR community.
See the survey
- Documents and publications
Disaster recovery planning: Explanatory note and case study
This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery. Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication shows how the cost to property, infrastructure, and production can be calculated and built into a PDNA.
This paper illustrates why PDNAs should consider key sectors such as health and energy, and factor the macroeconomic and personal impacts of catastrophic events into the total estimate of post-disaster recovery and reconstruction.
Editors' recommendations
- View more about collecting disaster loss data
- Guidance note on recovery: pre-disaster recovery planning
- Pre-disaster Recovery Planning Guide for Tribal Governments
- Results in resilience: Informing resilient recovery policy, planning, and investments in Freetown, Sierra Leone
- Disaster recovery in Spain: a legal and policy survey
Explore further

Please note: Content is displayed as last posted by a PreventionWeb community member or editor. The views expressed therein are not necessarily those of UNDRR, PreventionWeb, or its sponsors. See our terms of use
Is this page useful?
Thank you. If you have 2 minutes, we would benefit from additional feedback (link opens in a new window) .
- PreventionWeb
- Global Assessment Report (GAR)
Special Events
- Global Platform
- International Day for Disaster Reduction
- World Tsunami Awareness Day
- Sendai Framework Monitor
- Voluntary Commitments

Disaster recovery planning: Explanatory note and case study
This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery. Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication shows how the cost to property, infrastructure, and production can be calculated and built into a PDNA.
This paper illustrates why PDNAs should consider key sectors such as health and energy, and factor the macroeconomic and personal impacts of catastrophic events into the total estimate of post-disaster recovery and reconstruction.
Editors' recommendations
- View more about collecting disaster loss data
- Guidance note on recovery: pre-disaster recovery planning
- Pre-disaster Recovery Planning Guide for Tribal Governments
- Results in resilience: Informing resilient recovery policy, planning, and investments in Freetown, Sierra Leone
- Disaster recovery in Spain: a legal and policy survey
Explore further

Also featured on
Is this page useful.
Thank you. If you have 2 minutes, we would benefit from additional feedback (link opens in a new window) .
Housing Programs
Why we care.
- Housing Needs By State
- Become a Member

Projects & Campaigns
- Take Action
Case Study Documents Pre-Disaster Planning Challenges for Public Housing Recovery
The Natural Hazards Center published a new article as part of its “Mitigation Matters” research brief series. “ Pre-Disaster Recovery Planning for Public Housing in Salt Lake County, Utah ,” a case study, examines post-disaster housing plans, planning motivation, challenges, opportunities, and coordination between various entities as they relate to pre-disaster recovery planning for public housing in Salt Lake County, Utah. A lack of pre-disaster assessments, poor coordination and information-sharing, inadequate funding, leadership problems, and issues with trust were all challenges for successful pre-disaster recovery planning and post-disaster rehousing of public housing residents.
The article cites research finding that Salt Lake County has a 57% probability of experiencing 6.75 magnitude earthquake sometime in the next 50 years. One scenario modeling a 7.0 magnitude earthquake in the region predicted almost 263,300 people could be displaced. Public housing residents are particularly vulnerable to negative impacts from such disasters.
The authors, Sayma Khajehei and Divya Chandrasekhar, used a combination qualitative research techniques including archival research and semi-structured key informant interviews with ten local emergency management, city planning, and housing officials to conduct the case study. They found that Salt Lake County and its localities had not developed a stand-alone plan for housing recovery in their disaster preparedness and response plans. The authors also observed:
- Lack of adequate or dedicated funding for pre-disaster planning
- Lack of knowledge among housing authorities about the potential scale of displacement
- Insufficient planning for how to implement post-disaster shelter needs assessments for displaced public housing residents
- Limited opportunities for coordination between public housing agencies and other housing-related entities
- Little motivation among local leaders to plan ahead
The authors concluded Salt Lake County is generally unprepared to house displaced public housing residents after a disaster. They recommended that communities in Salt Lake County better promote pre-disaster recovery planning for public housing through dedicated funding for planning, joint planning, engagement with diverse communities, and public education about the importance of public housing recovery.
“Pre-Disaster Recovery Planning for Public Housing in Salt Lake County, Utah” is at: https://bit.ly/3shlIm0
Related Content
New research sheds light on impact of new construction on mobility of low-income renters.
A study recently published in the Journal of the American Planning Association, “Can New Housing Supply Mitigate Displacement and Exclusion?,” examines the impact of new market rate and subsidized…
FTC and DOJ File Joint Legal Brief on Algorithmic Price Fixing in Housing Market
The Federal Trade Commission (FTC) and the U.S. Department of Justice (DOJ) filed a joint legal brief on March 1 expressing concerns related to algorithmic price fixing in the housing market. In the…
New Study Examines Filtering Dynamics in U.S. Housing Supply
New research published in Housing Policy Debate, “Has Housing Filtering Stalled? Heterogeneous Outcomes in the American Housing Survey, 1985–2021,” examines long-term trends and dynamics in the…

IMAGES
VIDEO
COMMENTS
Browse case study reports and best practice articles from across FEMA's areas of expertise. You can search by title or keywords, select additional content filters, or jump to a collection. Collections. COVID-19 Best Practice Case Studies; Interagency Recovery Coordination Case Studies; Mitigation Best Practices; Preparedness Grants Case Studies
The Bay Park Sewage Treatment Plant was originally built in the 1940s. In 2012, the plant processed sewage for approximately 550,000 people. Hurricane Sandy caused significant damage to approximately 50 structures, including mechanical and electrical systems and essential operating equipment. The plant was completely inoperable for three days ...
Disaster Recovery Plan for Business Continuity: Case Study in a Business Sector. 26 Pages Posted: 27 Aug 2018 Last revised: 13 Mar 2020. ... Freelancer / Independent . Date Written: June 16, 2016. Abstract. An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned incidents that ...
Quality Considerations in Disaster Recovery: A Case Study. Due to the growing digitalization of the industry, we are highly dependent on information technology (IT) systems and data. The basic ability to execute our pharmaceutical business and decision-making processes relies on the permanent availability of these IT systems and data to ensure ...
Disaster Recovery Planning: Explanatory Note and Case Study; ... Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication shows how the cost to property, infrastructure, and production can be calculated and built into a PDNA. It illustrates why PDNAs should consider key sectors such as ...
VMware's rapidly growing global business drove the need for an enterprise IT Disaster Recovery (DR) plan to protect corporate assets and prevent loss in the event that any disaster—fire, flood, cyber attacks, earthquake, plane crashes—were to hit one of its data centers. VMware's IT Disaster Recovery program strategically combines ...
1.1 Objectives. This research aims to establish business continuity and disaster recovery plan to control risks and recover as quickly as possible from any crisis or serve as a foundation for future research on business continuity, disaster recovery, and risk management. 2. Literature Review.
Case Studies in Disaster Recovery, the initial release in the Disaster and Emergency Management: Case Studies in Adaptation and Innovation series, explores recovery from a number of perspectives: household, community and nation. Chapters cover the concept of social vulnerability to explain/predict recovery outcomes, consider broader themes of sustainability, assess community vulnerability and ...
In this paper, we present an implementation of a technology that supports the above three requirements, thus enabling live mobility of virtual machines between clouds, while enforcing clouds' insularity requirements, using a public cloud provider, such as the case Portugal Telecom. 8. Planning Disaster Recovery A Disaster Recovery project is a ...
After that, a group of transportation network disaster recovery planning experts, who previously developed the DRPTN plan of the case study, systematically and critically evaluated attributes against those evaluation factors through three decision regions (for research data see Zamanifar, 2020). Results suggest a ranked list and the selected ...
2016 Disaster Recovery Plan For Business Continuity : Case Study in a Business Sector Author: Jacob Joseph Kassema INFORMATION TECHNOLOGY DISASTER RECOVERY (ITDR) An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned incidents that threaten an IT infrastructure, which includes ...
Case Studies. The business scenario of Network-based Enterprises is one of tremendous growth, with organizations securing themselves with advanced technology tools as well as planning, monitoring, and maintenance of the overall IT infrastructure. Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP) are critical elements of ...
It gives an overview of flooding in the US and the CRS and discusses the role of post-disaster recovery planning. The report examines plan development, elements, and implementation in three case studies from Florida and one case study from Oregon.
other flood protection projects, but points are not allocated for post‐disaster recovery planning. These case studies seek to provide an overview of several post‐disaster recovery plans. In particular, they focus on the plan development process, the plan contents, and implementation strategies.
This Teaching Note is intended to prepare an instructor to use this case study in a classroom (live or virtually). The note expands on the lessons learned in this case study, intended to help disaster management students learn from a real-world disaster recovery experience. Selection of learning objectives, discussion questions, and activities can
Disaster recovery planning: Explanatory note and case study (June 2023) Author (s): Steven Goldfinch, Anne Orquiza, Roberto Jovel, et al. This publication outlines why post-disaster needs ...
Disaster Recovery Planning: Explanatory Note and Case Study. This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery.Using a theoretical case study highlighting the aftermath ...
The concepts of a disaster recovery plan and data replication are described; the assessment, planning, implementation, and testing of the Disaster Recovery solution used by Houston Community College (HCC) are discussed; and the testing procedures of an actual extension of the plan in the face of a real-life disaster are examined. ABSTRACT Computerized data has become critical to the survival ...
Disaster recovery and business continuity are different concepts, but they work together and are usually part of the same conversation. When you plan ahead and implement a DR/BC solution, you'll see the following benefits. 1. Always know who to call. When disaster strikes, there is an unavoidable feeling of panic.
This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery. Using a theoretical case study highlighting the aftermath of an earthquake and subsequent flooding, the publication ...
Disaster recovery planning: Explanatory note and case study. This publication outlines why post-disaster needs assessments (PDNA) should provide comprehensive details of the economic and social impacts of disasters on countries to swiftly mobilize resources and support resilient recovery. Using a theoretical case study highlighting the ...
The Natural Hazards Center published a new article as part of its "Mitigation Matters" research brief series. "Pre-Disaster Recovery Planning for Public Housing in Salt Lake County, Utah," a case study, examines post-disaster housing plans, planning motivation, challenges, opportunities, and coordination between various entities as they relate to pre-disaster recovery planning for ...