
- TRP for UPSC Personality Test
- Interview Mentorship Programme – 2023
- Daily News & Analysis
- Daily Current Affairs Quiz
- Baba’s Explainer
- Dedicated TLP Portal
- 60 Day – Rapid Revision (RaRe) Series – 2024
- English Magazines
- Hindi Magazines
- Yojana & Kurukshetra Gist
- PT20 – Prelims Test Series
- Gurukul Foundation
- Gurukul Advanced – Launching Soon
- Prelims Exclusive Programme (PEP)
- Prelims Test Series (AIPTS)
- S-ILP – English
- S-ILP – हिंदी
- Connect to Conquer(C2C) 2024
- TLP Plus – 2024
- TLP Connect – 2024
- Public Administration FC – 2024
- Anthropology Foundation Course
- Anthropology Optional Test Series
- Sociology Foundation Course – 2024
- Sociology Test Series – 2023
- Geography Optional Foundation Course
- Geography Optional Test Series – Coming Soon!
- PSIR Foundation Course
- PSIR Test Series – Coming Soon
- ‘Mission ಸಂಕಲ್ಪ’ – Prelims Crash Course
- CTI (COMMERCIAL TAX INSPECTOR) Test Series & Video Classes
- Monthly Magazine

Cyberattacks
- February 27, 2023
Security Issues

Context: Ransomwares have emerged as the most predominant of malicious cyberattacks worldwide.
About Cyberattacks:

- Cyberattacks are u nwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer systems.
- Typically such forms of attacks to keep networks from functioning after encrypting data, are carried out by ransomware-seeking entities.
- In ransomware, the perpetrators demand hefty payments for the release of withheld data.
Recent cases of ransomware attacks
- Nearly 40 million health records were compromised and it took over two weeks for the systems to be brought online.
- Cyberattack on Solar Industries Limited: A ransomware gang, BlackCat, breached the parent company of Solar Industries Limited , one of the Ministry of Defence’s ammunition and explosives manufacturers, and extracted over 2 terabytes of data.
- Overall data: Data shows that over 75% of Indian organisations have faced such attacks, with each breach costing an average of Rs.35 crores of damage .
Reasons for increasing Cyberattacks:
- As we grow faster, more and more systems are being shifted to virtual space to promote access and ease of use. However, the downside to this trend is the increased vulnerability of such systems to cyber-attacks.
- Therefore, cyber warfare has increasingly become the chosen space for conflict between nations.
- Despite a number of agencies, policies and initiatives, their implementation has been far from satisfactory.
- Therefore, it is expected to have capabilities to disable or partially interrupt the information technology services in another country.
- Combined with the recent border standoff and violent incidents between the armies of the two countries, the adversity in relations is expected to spill over to attacking each other’s critical information infrastructure.
- Asymmetric and covert warfare : Unlike conventional warfare with loss of lives and eyeball to eyeball situations, cyber warfare is covert warfare with the scope of plausible deniability, i.e. the governments can deny their involvement even when they are caught.
- Lack of International Coordination: International cooperation and consensus is missing in this field.
- Low digital literacy among the general public and digital gaps amongst nations create an unsustainable environment in the cyber domain.
- It is often reported that people are duped easily by click-baiting them into clicking interesting content, which often has malware attached to itself.
Challenges associated with cyberattacks :
- Need of a cyber security policy: With cyber threats capable of undermining our critical infrastructure, industry and security, a comprehensive cyber security policy is the need of the hour.
- India also faces an acute scarcity of cybersecurity professionals.
- Nearly two-thirds would find it challenging to respond to a cybersecurity incident due to the shortage of skills within their team.
- India is projected to have a total workforce of around 3,00,000 people in this sector in contrast to the 1.2 million people in the United States.
- They would be advised to look at the Digital Geneva Convention , where over 30 global companies have signed a declaration to protect users and customers from cyber breaches and collaborate with like-minded intergovernmental and state frameworks.
- Need for a global framework: With most cyberattacks originating from beyond our borders, international cooperation would be critical to keeping our digital space secure.
India’s Preparedness to Ensure Cybersecurity:
- India had banned many apps (mostly of Chinese origin), which were found to be unsafe for usage by Indian citizens.
- Awaited National cybersecurity strategy : Comprehensive plan in preparing & dealing with cyber-attacks (Pre, Post and During the attack).
- Indian Cyber Crime Coordination Centre (I4C): Launched in 2018, It is an apex coordination centre to deal with cybercrimes.
- Evolving Technology : Cyber attackers are continuously working on novel ways to sabotage the systems.
- It is the nodal agency to deal with cyber security threats like hacking and phishing.
- It strengthens security-related defence of the Indian Internet domain .
- National Cyber Security Policy, 2013: The policy provides the vision and strategic direction to protect the national cyberspace.
- Cyber Swachhta Kendra : Launched in 2017, these helps users to analyse and keep their systems free of various viruses, bots/ malware, Trojans, etc.
- Cyber Surakshit Bharat: It was launched by the Ministry of Electronics and Information Technology (MeitY) in 2018 with an aim to spread awareness about cybercrime and building capacity for safety measures for Chief Information Security Officers (CISOs) and frontline IT staff across all government departments.
- The Cyber Warrior Police Force : It was organised on the lines of the Central Armed Police Force in 2018.
- Personal Data Protection Bill: The bill mandates the strengthening of data infrastructure by private companies to safeguard the data of individuals.
- National Critical Information Infrastructure Protection Centre (NCIIPC) was created under Section 70A of IT Act 2000 to protect Cyberinfrastructure.
Way Forward:
- Human resource is crucial and there is an urgent need to create an informal Indian team of Cyber Warriors.
- The critical infrastructure managers should also be well trained in cyber warfare and well equipped with all the technologies for isolating viruses and attacks .
- There should be a reward for white hackers who can highlight their shortcomings.
- The managers and common mass must be made aware.
- There is a need to enhance the general awareness levels of the government installations as well as the general public to counter such threats.
- Separate wing under Army or Navy as Cyber Command on lines of US.
- The need of the hour is to come up with a futuristic National Cyber-Security Policy which allocates adequate resources and addresses the concerns of the stakeholders.
- Similarly, there is a need for quicker up-gradation of the existing infrastructure as information technology is a fast-evolving field and there is a need to stay ahead of the competition.
Cooperation with G20:
- The G-20 summit this year in India, which will see participation by all the stakeholders driving the global levers of power, is a r are opportunity to bring together domestic and international engagement groups across the spectrum, and steer the direction of these consultations.
- India could try to conceptualise a global framework of common minimum acceptance for cybersecurity.
Source: The Hindu
For a dedicated peer group, Motivation & Quick updates, Join our official telegram channel – https://t.me/IASbabaOfficialAccount
Subscribe to our YouTube Channel HERE to watch Explainer Videos, Strategy Sessions, Toppers Talks & many more…

Related Posts :
India’s sticky inflation.

- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam – 11th April 2024
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 11th April 2024
- [DAY 33] 60 DAY RAPID REVISION (RaRe) SERIES for UPSC Prelims 2024 – ECONOMY, CURRENT AFFAIRS & CSAT TEST SERIES!
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 10th April 2024
- [DAY 32] 60 DAY RAPID REVISION (RaRe) SERIES for UPSC Prelims 2024 – GEOGRAPHY, CURRENT AFFAIRS & CSAT TEST SERIES!
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 9th April 2024
- [DAY 31] 60 DAY RAPID REVISION (RaRe) SERIES for UPSC Prelims 2024 – GEOGRAPHY, CURRENT AFFAIRS & CSAT TEST SERIES!
- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam – 8th April 2024
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 8th April 2024
- [DAY 30] 60 DAY RAPID REVISION (RaRe) SERIES for UPSC Prelims 2024 – GEOGRAPHY, CURRENT AFFAIRS & CSAT TEST SERIES!
Don’t lose out on any important Post and Update. Learn everyday with Experts!!
Email Address
Search now.....
Sign up to receive regular updates.
Sign Up Now !

- IAS Preparation
- UPSC Preparation Strategy
- Ransomware Attack UPSC Notes
Ransomware Attack [UPSC Notes]
In November 2022, there was a ransomware attack on the database of the All India Institute of Medical Sciences (AIIMS) affecting its operations significantly leading to the hospital running in manual mode for weeks. This topic becomes important for the cybersecurity segment of the UPSC syllabus . In this article, you can read about ransomware attacks, how they can be prevented, etc.
What is Ransomware?
Ransomware is advanced software used by hackers to block the access of users to crucial databases.
- These cyber criminals demand money in lieu of unblocking data to the respective users.
- In the recent cyberattack on the AIIMS database, the hacker demanded ransom in cryptocurrencies .

Image Source: The Hindu
Some examples of recent ransomware attacks:
- CryptoLocker
Ransomware Attack Implications
According to Interpol’s first-ever Global Crime Trend report, ransomware was the second highest-ranking threat after money laundering, at 66%. It is also expected to increase the most (72%).
- About 70 per cent of organisations in India have been hit by a ransomware attack in the last three years while 81 per cent of organisations feel that they could be the target of ransomware attacks.
- The Indian Computer Emergency Response Team (CERT-IN) in its India Ransomware Report 2022 stated that there is a 51-percent increase in the number of ransomware attacks across multiple sectors including critical infrastructure.

Image source: The Hindu
Agencies to deal with the cyber threat:
- The Indian Computer Emergency Response Team (CERT-In) established in 2004 is the national nodal agency that collects, analyses and circulates inputs on cyber-attacks.
- The National Critical Information Infrastructure Protection Centre has been set up for the protection of national critical information infrastructure.
- The Cyber Swachhta Kendra (Bot-Net Cleaning and Malware Analysis Centre) has been launched for the detection of malicious software programmes and to provide free tools to remove them.
- The National Cyber Coordination Centre works on creating awareness about existing and potential threats.
Ransomware Attack Best Practices
Best practices recommended by the CERT-In for dealing with ransomware:
- Maintain an offline database of the important files in encrypted form .
- All accounts should have strong and unique passwords , an account lockout policy , and multi-factor authentication for all services.
- A host-based firewall should be installed to only allow connections to such shares via server message block from a limited set of administrator machines.
Ransomware Attack:- Download PDF Here
Leave a Comment Cancel reply
Your Mobile number and Email id will not be published. Required fields are marked *
Request OTP on Voice Call
Post My Comment
IAS 2024 - Your dream can come true!
Download the ultimate guide to upsc cse preparation.
- Share Share
Register with BYJU'S & Download Free PDFs
Register with byju's & watch live videos.

Cyberwarfare: Everything you need to know
PYQ Discussion 2024 Batch-1, An opportunity to revise 2011-2023 PYQ’s, Batch Starts 24th April 2024 Click Here for more information
- 1 What is the News?
- 2 What is Cyber Warfare?
- 3 Why are Cyber attacks carried out?
- 4 Which countries are behind state-backed cyber attacks?
- 5 How often is India targeted?
What is the News?
Ukraine has been hit by a wave of cyberattacks targeting critical infrastructure companies. The timing and scale of the attacks point towards hackers working at the behest of Russia.
What is Cyber Warfare?
Cyberwarfare has emerged as a new form of retaliation or passive aggression deployed by nations that do not want to go to actual war but want to send a tough message to their opponents.
In these types of warfare, nation-state actors attack and attempt to damage another nation’s computers or information networks through computer viruses or denial-of-service attacks, especially for strategic or military purposes.
Why are Cyber attacks carried out?
State-backed cyber attacks are usually carried out to steal state secrets, trade deals and weapons blueprints, or target large multinationals to steal their intellectual property (IP) and use it to build local industry.
However, when states launch cyberattacks on other states as a result of worsening of geopolitical relations, the target is usually critical infrastructure firms to disrupt economic activity.
Which countries are behind state-backed cyber attacks?
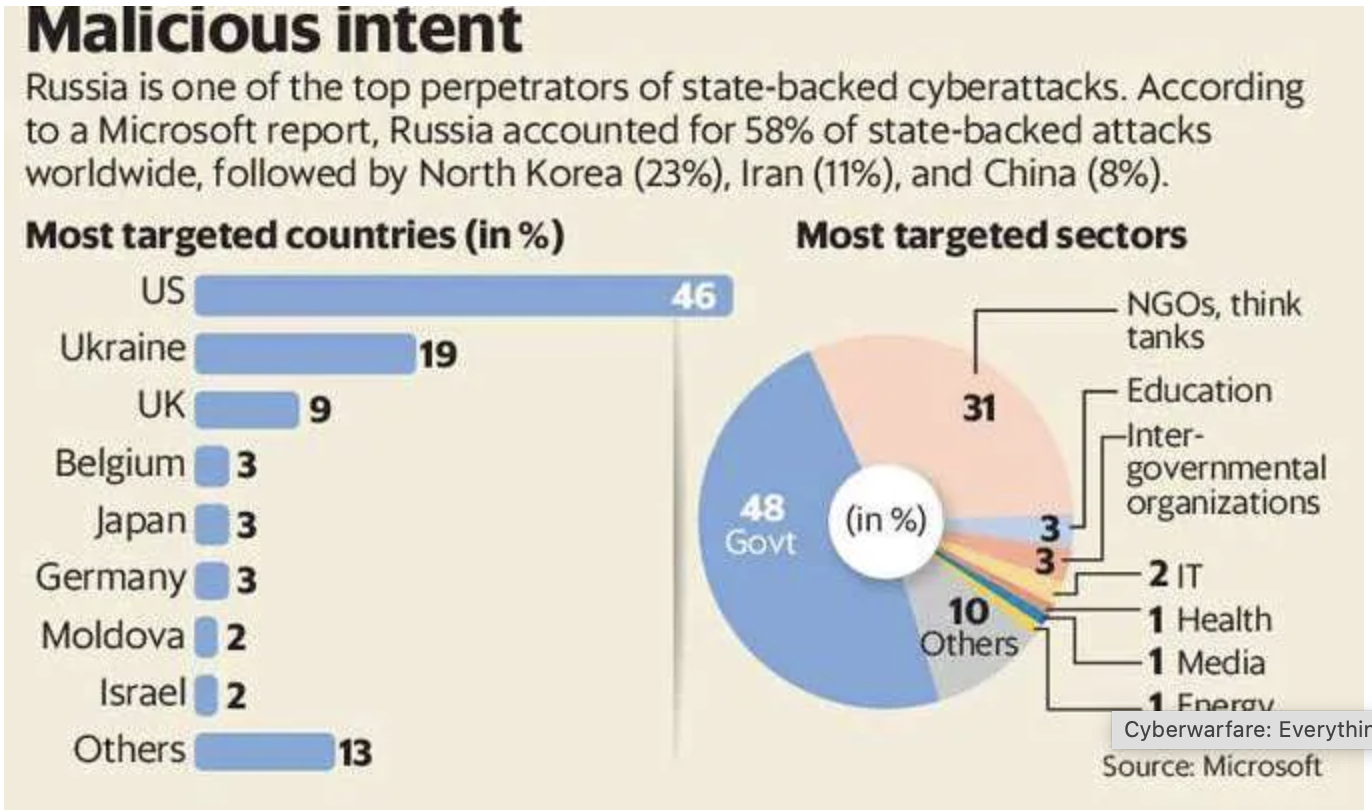
Russia is one of the top perpetrators of state-backed cyberattacks. According to a report by Microsoft, Russia accounted for 58% of state-backed attacks worldwide, followed by North Korea (23%), Iran (11%), and China (8%).
How often is India targeted?
According to a study, cyberattacks rose 100% between 2017 and 2021. For example:
– In 2019. The administrative network of the Kudankulam Nuclear Power Plant was hit by a malware attack by North Korea-backed Lazarus Group.
– China-backed hackers were believed to be behind a power outage in Mumbai in 2020.
– Pakistan-based hackers targeted power firms and one government organization in India in early 2021.
Source : This post is based on the article “Cyberwarfare: Everything you need to know ” published in Livemint on 25th February 2022.

Type your email…
Search Articles
Latest articles.
- UPSC Prelims Marathon 11th April – Climate Change Organizations – 2024
- [Answered] UPSC Mains Answer writing 9 April, 2024 I Mains Marathon
- 10 PM UPSC Current Affairs Quiz 10 April, 2024
- 9 PM UPSC Current Affairs Articles 10 April, 2024
- Globalisation of Indian rupee
- To be a doctor in “India”
- Laws for better climate
- Parental consent before using a child’s personal data: Aadhaar-based age tokens can solve a privacy problem
- India’s struggle with TB drug shortages: Gross mismanagement
- Climate crisis is not gender-neutral
Prelims 2024 Current Affairs
- Art and Culture
- Indian Economy
- Science and Technology
- Environment & Ecology
- International Relations
- Polity & Nation
- Important Bills and Acts
- International Organizations
- Index, Reports and Summits
- Government Schemes and Programs
- Miscellaneous
- Species in news
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
UPSC Coaching, Study Materials, and Mock Exams
Enroll in ClearIAS UPSC Coaching Join Now Log In
Call us: +91-9605741000
Basics of Cyber Security
Last updated on December 25, 2022 by ClearIAS Team

What are the basics of cyber security that everyone should be aware of? What are the various forms of cyber-attacks? Read further to know more.
The accelerating pace of globalization and digitization fuelled a record-breaking cybercrime with ransomware attacks rising 151% in 2021
The World Economic Form’s Global Cybersecurity Outlook 2022 released during its Davos Agenda Summit stated each cyber breach cost the organization $3.6 million past year.
Table of Contents
Cyberattack: Introduction
A cyberattack is an attempt to gain illegal access to a computer system to cause damage. It can occur on any modern digital device.
The vital government and health services can even be blocked and extorted for ransom.
Its impact can range from an inconvenience for an individual to global economic and social disruption.
Join Now: UPSC Prelims cum Mains Course
An attacker uses people, computers, phones, applications, messages, and system processes to carry out an attack. Individuals, organizations, institutions, and governments can be victims of an attack.

Modes of Cyber Attack
- Lock data and processes, and demand a ransom.
- Remove vital information to cause serious harm.
- Steal information.
- Publicly expose private information.
- Halter vital business processes and systems from running, to cause disruption and malfunction.
Cyber Security
Cybersecurity refers to technologies, processes, and training that protect systems, networks, programs, and data from cyberattacks, damage, and unauthorized access.
Cyber Threat Landscape
The digital landscape is usually the entry point for a cyberattack. These can include:
- Social media
- Mobile devices
- The organization’s technology infrastructure
- Cloud services
A ttack vectors
An attack vector is an entry point or route for an attacker to gain access to a system.
Security breaches come in different forms:
Join Now: CSAT Course
Social engineering attacks
Attackers use social engineering to exploit or manipulate users into granting them unauthorized access to a system.
In social engineering, impersonation attacks happen when an unauthorized user (the attacker), aims to gain the trust of an authorized user by posing as a person of authority to access a system.
For example, a cybercriminal pretending to be a support engineer tricks a user into revealing their password to access an organization’s systems.
Browser attacks
Security vulnerabilities in a browser can have a significant impact because of their pervasiveness.
For example, if a user is working on an important project with a looming deadline. They want to figure out how to solve a particular problem for their project and find a website that they believe will provide a solution.
Join Now: UPSC Prelims Test Series
The website asks the user to make some changes to their browser settings so they can install an add-on. The user follows the instructions on the website thus making the browser compromised. The attacker can now use the browser to steal information, monitor user behavior, or compromise a device.
Password attacks
A password attack is when someone attempts to use authentication for a password-protected account to gain unauthorized access to a device or system. Attackers often use software to speed up the process of cracking and guessing passwords.
The brute force attack and is one of many ways in which a cybercriminal can use password attacks.
Data Breach
A data breach is when an attacker successfully gains access or control of data similar to that person getting access to, or stealing, vital documents and information inside the building:
Here, the victim’s data could be abused in many ways. For example, it can be held as ransom or used to cause financial or reputational harm.
Malware comes from the combination of the words malicious and software. It’s a piece of software used by cybercriminals to infect systems and carry out actions that will cause harm. This could include stealing data or disrupting normal usage and processes.
Malware has two main components:
- Propagation mechanism
What is a propagation mechanism?
Propagation is about how the malware spreads itself across one or more systems.
few examples of common propagation techniques:
In biology, a virus enters the human body, and once inside, can spread and cause harm.
Technology-based viruses depend on some means of entry, specifically a user action, to get into a system. Say, a user might download a file or plug in a USB device that contains the virus, and contaminates the system. You now have a security breach.
In contrast to a virus, a worm doesn’t need any user action to spread itself across systems. Instead, a worm causes damage by finding vulnerable systems it can exploit. Once inside, the worm can spread to other connected systems.
For example, a worm might infect a device by exploiting a vulnerability in an application that runs on it. The worm can then spread across other devices in the same network and other connected networks.
A trojan horse attack gets its name from classical history, where soldiers hid inside a wooden horse that was gifted to the Trojans. When the Trojans brought the wooden horse into their city, the soldiers emerged from the wooden horse and attacked.
In the context of cybersecurity, a trojan is a type of malware that pretends to be genuine software. When a user installs the program, it can pretend to be working as mentioned, but the program also secretly performs malicious actions such as stealing information.
The payload is the action that malware performs on an infected device or system.
Some common types of payload:
- It’s a payload that locks systems or data until the victim has paid a ransom.
- A cybercriminal can exploit this to access and then encrypt all files across this network.
- The attacker demands a ransom in return for decrypting the files.
- They threaten to remove all the files if the ransom hasn’t been paid by a set deadline.
- It spies on a device or system.
- The malware may install keyboard scanning software on a user’s device, collect password details, and transmit them back to the attacker, without the user’s knowledge.
- A backdoor is a payload that enables a cybercriminal to exploit a system or device to bypass existing security measures and cause harm.
- It’s a backdoor that the cybercriminal could use to hack into the application, the device in which it’s running on, and even the organization’s and customers’ networks and systems.
- A botnet joins a computer, server, or another device to a network of similarly infected devices that can be controlled remotely to carry out some nefarious action.
- A common application of botnet malware is crypto-mining. In this case, the malware connects a device to a botnet that consumes the device’s computing power to mine or generates cryptocurrencies.
- A user might notice their computer is running slower than normal and getting worse with time.
Mitigation strategy
To defend against cyberattacks, technological and organizational policies and processes can be designed and implemented.
Many different mitigation strategies are available to an organization:
Multifactor authentication
Conventionally, if someone’s password or username is compromised, this allows a cybercriminal to gain control of the account. But multifactor authentication was introduced to combat this.
Multifactor authentication works by requiring a user to provide multiple forms of identification to verify that they are who they claim to be.
The most common form of identification used to verify or authenticate a user is a password which represents something the user knows.
Two other authentication methods provide something to the user such as a fingerprint or retinal scan (a biometric form of authentication), or provide something the user has, such as a phone, hardware key, or other trusted device. Multifactor authentication employs two or more of these forms of proof to verify a valid user.
For example, a bank might require a user to provide security codes sent to their mobile device, in addition to their username and password, to access their online account.
Browser security
We all rely on browsers to access the internet to work and carry out our daily tasks. As the attackers can even compromise poorly secured browsers. Organizations can protect against these types of attacks by implementing security policies that:
- Prevent the installation of unauthorized browser extensions or add-ons.
- Allow only permitted browsers to be installed on devices.
- Block sites using web content filters.
- Keep updating browsers
Social engineering attacks rely on the vulnerabilities of humans to cause harm.
Organizations can defend against social engineering attacks by educating their staff.
Users should learn how to recognize malicious content they receive or encounter, and know what to do when they spot something suspicious. For example, organizations can teach users to:
- Identify suspicious elements in a message.
- Avoid responding to external requests for personal information.
- Lock devices when they’re not in use.
- Store, share, and remove data according to the organization’s policies.
Threat intelligence
The threat landscape can be vast.
Organizations need to take as many measures as possible to monitor, prevent, defend against attacks, and even identify possible vulnerabilities before cybercriminals use them to carry out attacks.
Hence, the users need to use threat intelligence.
- Threat intelligence enables an organization to collect systems information, details about vulnerabilities and information on attacks
- The organization can then implement policies for security, devices, user access, and more, to defend against cyberattacks.
- The collection of information to gain insights, and respond to cyberattacks, is known as threat intelligence.
- Organizations can use technological solutions to implement threat intelligence across their systems.
- The threat intelligent solutions automatically collect information, and even hunt and respond to attacks and vulnerabilities.
These are just some of the mitigation strategies that organizations can take to protect against cyberattacks.
Mitigation strategies enable an organization to take a robust approach to cybersecurity. This will ultimately protect the confidentiality, integrity, and availability of information
Article written by : Sulochana Anu

Take a Test: Analyse Your Progress
Aim IAS, IPS, or IFS?

About ClearIAS Team
ClearIAS is one of the most trusted learning platforms in India for UPSC preparation. Around 1 million aspirants learn from the ClearIAS every month.
Our courses and training methods are different from traditional coaching. We give special emphasis on smart work and personal mentorship. Many UPSC toppers thank ClearIAS for our role in their success.
Download the ClearIAS mobile apps now to supplement your self-study efforts with ClearIAS smart-study training.
Reader Interactions
Leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Don’t lose out without playing the right game!
Follow the ClearIAS Prelims cum Mains (PCM) Integrated Approach.
Join ClearIAS PCM Course Now
UPSC Online Preparation
- Union Public Service Commission (UPSC)
- Indian Administrative Service (IAS)
- Indian Police Service (IPS)
- IAS Exam Eligibility
- UPSC Free Study Materials
- UPSC Exam Guidance
- UPSC Prelims Test Series
- UPSC Syllabus
- UPSC Online
- UPSC Prelims
- UPSC Interview
- UPSC Toppers
- UPSC Previous Year Qns
- UPSC Age Calculator
- UPSC Calendar 2024
- About ClearIAS
- ClearIAS Programs
- ClearIAS Fee Structure
- IAS Coaching
- UPSC Coaching
- UPSC Online Coaching
- ClearIAS Blog
- Important Updates
- Announcements
- Book Review
- ClearIAS App
- Work with us
- Advertise with us
- Privacy Policy
- Terms and Conditions
- Talk to Your Mentor
Featured on

and many more...
Cyber Security
What is cyber space?
- The emergence of the Internet in the late 1980s led to the evolution of cyberspace as a fifth domain of human activity (following land, sea, air and space)
- Cyberspace comprises
- Computer systems - servers, desktops, laptops, Personal Digital Assistants (PDAs), mobile computing platforms etc.
- Computer networks - Local Area Networks (LAN) and Wide Area Networks (WAN)
- A nation’s cyberspace is part of the global cyberspace .
- Unlike physical space, cyber space is anonymous and borderless .
What is cyber security?
- Cybersecurity is the proactive measures and practices implemented to safeguard information, equipment, computer devices, computer resource, communication device and information stored therein from unauthorised access, use, disclosure, disruption, modification or destruction ensuring their confidentiality, integrity, and availability.
- A country’s capability in cyber security is not independent and is embedded in Global Internet.

Various types of Cyber-Threats
- Malware : It includes viruses, worms, Trojans, ransomware, spyware, and adware.
- Ransomware : The attacker then demands a ransom payment, usually in cryptocurrency.
- Phishing Attacks : Phishing attacks involve tricking individuals into revealing sensitive information such as usernames, passwords.
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks : DoS and DDoS attacks overwhelm computer systems, networks, or websites with a flood of traffic.
- SQL Injection : SQL injection attacks exploit vulnerabilities in web applications that interact with databases.
- Social Engineering : Social engineering involves manipulating and deceiving individuals
- Man-in-the-Middle (MitM) Attacks : In a MitM attack, an attacker intercepts and alters communication between two parties without their knowledge. It allows the attacker to eavesdrop, steal information, or modify data.
- Insider Threats : Insider threats occur when individuals with authorized access to systems or data misuse their privileges for malicious purposes.
- Zero-day Exploits: Zero-day exploits target vulnerabilities in software that are unknown to the software vendor.
Significance of Cybersecurity
Cybersecurity plays a crucial role in today's interconnected digital world. Following are some of the key reasons why cybersecurity is significant:
- Protection of Sensitive Data
- Example -The importance of cybersecurity brought into forefront in the recent AIIMS cyberattack, which resulted in the encryption of around 1.3 terabytes of data.
- Prevention of Financial Loss
- Example -Cosmos Bank cyber-attack 2018, stressed on need of cybersecurity in banking system in India.
- Safeguarding National Security
- Example- Operation Shady RAT, a notorious operation as early as 2006 and has hit at least 72 organizations, including defence contractors, businesses worldwide and Government Agencies.
- Protection of Intellectual Property
- Example -Dispute of Tesla and Rivian automotive over trade secret. To avoid such instances, cybersecurity plays a vital role.
- Maintaining Trust and Confidence
- Example -Incidences like AIIMS cyberattack, Pegasus row may erode trust on digital world. In such scenario cybersecurity is important.
- Protection of Critical Infrastructure
- Cybersecurity ensures the protection and resilience of critical infrastructure (power grids, transportation systems, healthcare facilities and systems which rely heavily on interconnected networks.) against cyber threats.
- Example -Attack on Kudankulam nuclear power plant 2019 brought cybersecurity in forefront for critical infrastructure.
- Mitigation of Operational Disruptions
- Example -In May 2022, low-fare airline SpiceJet reported a ransomware attack that delayed several flights by up to six hours.
- Preserving Privacy and Individual Rights
- Cybersecurity safeguards personal privacy and upholds digital rights by protecting sensitive information and preventing unauthorized surveillance, ensuring privacy in the digital age.
- Preserving Democracy and Elections
- Example -The 2016 US presidential election demonstrated the significance of cybersecurity in safeguarding democratic processes.
Challenges to Cybersecurity

Initiatives for Cyber Security
Steps taken by India towards cyber security
- Information technology Act, 2000 - Provides legal recognition to e-documents and a framework to support e-filing & e-commerce along with a legal framework to mitigate, check cybercrimes.
- To create a secure cyber ecosystem, and generate adequate trust & confidence in IT systems
- Creating an assurance framework – testing & certification
- Operating a 24x7 National Critical Information Infrastructure Protection Centre (NCIIPC)
- To develop suitable indigenous security technologies
- To create a workforce of 500,000 professionals skilled in cyber security
- To enable effective prevention, investigation and prosecution of cyber crime
- Enhancement of law enforcement capabilities
- To develop effective public private partnerships and collaborative engagements
- To enhance global cooperation
- National Technical Research Organization (NTRO) – a technical intelligence agency that develops technology capabilities in aviation and remote sensing, data gathering and processing, cyber security, cryptology systems, strategic hardware & software development and strategic monitoring.
- National Critical Information Infrastructure Protection centre (NCIIPC) - Designated as the National Nodal Agency in respect of Critical Information Infrastructure Protection
- Multi-agency National Cyber Coordination Centre (NCCC) - cyber-security and e-surveillance agency mandated to scan internet traffic and communication metadata (of government and private service providers) to detect real-time cyber threats.
- NIC-CERT (National Information Centre-Computer Emergency Response Team) to prevent & predict cyber-attacks on NIC & govt. utilities.
- CERT-In or Computer Emergency Response Team (India) - CERTs are deployed as dedicated bodies for particular tasks E.g. NIC-CERT to counter cyber attacks on NIC, proposed CERTs for financial and power sectors (sectoral CERT-In) etc.
- National Cyber Security Coordinator (created by PMO office in 2014)
- Newly created division of the Ministry of Home Affairs to monitor crimes online, including cyber fraud and hacking and counter cyber-attacks on critical information infrastructure.
- The Indian Cyber Crime Coordination Centre (I4C) and the Cyber Warrior Police Force will be set up under the CIS Division to serve as catalysts for tracking down the online criminals.
- Pradhan Mantri Gramin Digital Saksharta Abhiyan (PMGDISHA) - under Digital India Programme to cover 6 crore households in rural areas to make them digitally literate .
- Cyber Surakshit Bharat (CSB) programme – to train Chief Information Security Officer (CISO) and other IT officers of Central and State Government, Banks, PSU etc.
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for providing detection of malicious programmes and free tools to remove such programmes.
- Proposals for a Digital Payment bill to strengthen legal framework and enhance surveillance to check cyber crimes in the financial sector, including frauds targeting cards and e-wallets.
- Formulation of Crisis Management Plan for countering cyber attacks and cyber terrorism.
- RBI recently issued a deadline for localisation of all sensitive data belonging to Indian users of various digital payment services.
Other International Initiatives
- Budapest Convention on Cybercrime - It is the only binding international instrument on the issue of cybercrime, dealing particularly with infringements of copyright, computer-related fraud, child pornography and violations of network security.
- Global Centre for Cyber security: launched by World Economic Forum to safeguard
Way forward
- Time bound implementation of key recommendations of various committees eg. Rao Inderjit Singh committee (on Cyber Crime, Cyber Security and Right to Privacy), Gulshan Rai Committee etc.
- Periodic revision of domestic laws such as Information Technology Act, 2000 and National Cyber Security Policy, 2013 should be done to meet the changing demands of the time.
- Data Security – Expeditious finalisation and passage of the Draft Personal Data Protection Bill, 2019
- Operationalizing Cyber policy - A more detailed plan of action should be constructed for operation of Cyber security Policy, 2013.
- Cyber crime cells should be constituted in each state, district and block, connected to centralized system. Cyber forensics investigation & labs.
- Capacity building of various stakeholders — such as police, judicial officers, forensic scientists as well as officials in the banking sector.
- Creating National Cyber Registry : Repository of highly skilled IT workforce for strategic use.
- Energise “Make in India” Programme for boosting local IT, Electronics equipment manufacturing
- Regular Audits to ensure compliance. Testing of all the hardware machinery, esp. imported ones.
- Data localisation – Internet servers for critical sectors should be hosted within India .
- Enterprise security - Companies should consider Cyber security as part of their management agenda and build clearly defined security roadmaps – run regular stress tests simulating real-life attacks.
- Digital literacy - Need to create awareness among citizens to help them secure their sensitive data and prevent misuse of the information in future.
- Set up Grievance redressal mechanism – Cyber Appellate Tribunal and Helpline for common public.
- Signing MoU’s and international treaties - to address cross border challenges in cyber security.
- Build offensive cyber capabilities – systems to intrude, intercept and exploit digital networks. It serves as function of strategic “cyber deterrence”.
Conclusion: Cyber security is a crucial aspect of our digital world. It involves protecting systems, networks, and data from unauthorized access and damage. With the increasing complexity of cyber threats, it is imperative to prioritize cyber security, implement robust measures, and foster collaboration to safeguard our digital assets and society.
Answer our survey to get FREE CONTENT

Feel free to get in touch! We will get back to you shortly
- Privacy Policy
- Terms of Service
- Quality Enrichment Program (QEP)
- Total Enrichment Program (TEP)
- Ethics Marks Maximization Prog. 2024
- Interview Mentorship Program (IMP)
- Prelims Crash Course for UPSC 2024
- Science of Answer Writing (SAW)
- Intensive News Analysis (INA)
- Topper's UPSC PYQ Answer
- Essay Marks Maximization Program
- PSIR Optional
- NEEV GS + CSAT Foundation
- News-CRUX-10
- Daily Headlines
- Geo. Optional Monthly Editorials
- Past Papers
- © Copyright 2024 - theIAShub
Talk To Our Counsellor

Call us @ 08069405205

Search Here

- An Introduction to the CSE Exam
- Personality Test
- Annual Calendar by UPSC-2024
- Common Myths about the Exam
- About Insights IAS
- Our Mission, Vision & Values
- Director's Desk
- Meet Our Team
- Our Branches
- Careers at Insights IAS
- Daily Current Affairs+PIB Summary
- Insights into Editorials
- Insta Revision Modules for Prelims
- Current Affairs Quiz
- Static Quiz
- Current Affairs RTM
- Insta-DART(CSAT)
- Insta 75 Days Revision Tests for Prelims 2024
- Secure (Mains Answer writing)
- Secure Synopsis
- Ethics Case Studies
- Insta Ethics
- Weekly Essay Challenge
- Insta Revision Modules-Mains
- Insta 75 Days Revision Tests for Mains
- Secure (Archive)
- Anthropology
- Law Optional
- Kannada Literature
- Public Administration
- English Literature
- Medical Science
- Mathematics
- Commerce & Accountancy
- Monthly Magazine: CURRENT AFFAIRS 30
- Content for Mains Enrichment (CME)
- InstaMaps: Important Places in News
- Weekly CA Magazine
- The PRIME Magazine
- Insta Revision Modules-Prelims
- Insta-DART(CSAT) Quiz
- Insta 75 days Revision Tests for Prelims 2022
- Insights SECURE(Mains Answer Writing)
- Interview Transcripts
- Previous Years' Question Papers-Prelims
- Answer Keys for Prelims PYQs
- Solve Prelims PYQs
- Previous Years' Question Papers-Mains
- UPSC CSE Syllabus
- Toppers from Insights IAS
- Testimonials
- Felicitation
- UPSC Results
- Indian Heritage & Culture
- Ancient Indian History
- Medieval Indian History
- Modern Indian History
- World History
- World Geography
- Indian Geography
- Indian Society
- Social Justice
- International Relations
- Agriculture
- Environment & Ecology
- Disaster Management
- Science & Technology
- Security Issues
- Ethics, Integrity and Aptitude

- Indian Heritage & Culture
- Enivornment & Ecology
- How to Study Art & Culture?
- What is Art and Culture? What is the difference between the two?
- Indus Civilization
- Evolution of rock-cut architecture in India
- Important rock-cut caves
- The contribution of Pallavas to Rock-cut architecture
- Comparision of art form found at Ellora and Mahabalipuram
- Buddhist Architecture
- Early Temples in India
- Basic form of Hindu temple
- Dravida style of temple architecture
- Nagara Style or North India Temple style
- Vesara style of temple architecture
- Characteristic features of Indo-Islamic form of architecture
- Styles of Islamic architecture in the Indian subcontinent
- Types of buildings in Islamic architecture in the Indian subcontinent
- Evolution of this form of architecture during the medieval period
- Modern Architecture
- Post-Independence architecture
- Indus Civilization Sculpture
- Bharhut Sculptures
- Sanchi Sculptures
- Gandhara School of Sculpture
- Mathura School of Sculpture
- Amaravati School of Sculpture
- Gupta Sculpture
- Medieval School of Sculpture
- Modern Indian Sculpture
- Pre Historic Painting
- Mural Paintings & Cave Paintings
- Pala School
- Mughal Paintings
- Bundi School of Painting
- Malwa School
- Mewar School
- Basohli School
- Kangra School
- Decanni School of Painting
- Madhubani Paintings or Mithila paintings
- Pattachitra
- Kalighat Painting
- Modern Indian Paintings
- Personalities Associated to Paintings
- Christianity
- Zoroastrianism
- Six Schools of Philosophy
- Lokayata / Charvaka
- Hindustani Music
- Carnatic Music
- Folk Music Tradition
- Modern Music
- Personalities associated with Music
- Bharatanatyam
- Mohiniattam
- Folk Dances
- Modern Dance in India
- Sanskrit Theatre
- Folk Theatre
- Modern Theatre
- Personalities associated with Theatre
- History of Puppetry
- String Puppetry
- Shadow Puppetry
- Rod Puppetry
- Glove Puppetry
- Indian Cinema and Circus
- Shankaracharya
- Ramanujacharya (1017-1137AD)
- Madhvacharya
- Vallabhacharya
- Kabir (1440-1510 AD)
- Guru Nanak (1469-1538 AD)
- Chaitanya Mahaprabhu
- Shankar Dev
- Purandaradasa
- Samard Ramdas
- Classical Languages
- Scheduled Languages
- Literature in Ancient India
- Buddhist and Jain Literature
- Tamil (Sangam) Literature
- Malayalam Literature
- Telugu Literature
- Medieval Literature
- Modern Literature
- Important characteristics of Fairs and Festivals of India
- Some of the major festivals that are celebrated in India
- Art & Crafts
- Ancient Science & Technology
- Medieval Science & Technology
- Famous Personalities in Science & Technology
- Tangible Cultural Heritage
- Intangible Cultural Heritage
- Cultural Heritage Sites
- Natural Heritage Sites
- Important Institutions
- Important programmes related to promotion and preservation of Indian heritage
- Ochre Colored Pottery (OCP)
- Black and Red Ware (BRW)
- Painted Grey-Ware (PGW)
- Northern Black Polished Ware (NBPW)
- Origin of Martial arts in India
- Various forms of Martial arts in India
- National Security Act (NSA), 1980
- Major shortcomings in India’s national security architecture
- National Security Strategy
- National Security Doctrine
- Meaning of Internal Security
- Review of Internal Security Threats and Vulnerabilities
- Role of external state and non-state actors in creating challenges to internal security
- Unlawful Activities (Prevention) Act
- Insurgency in North East India (NEI)
- Left-wing Extremism
- Maoist insurgent more than just ideological problem
- Women cadres in left-wing extremism
- Illegal immigration in India’s northern and eastern borders
- Reasons that sustain insurgency in north east India
- Recent Developments
- Correlation between development and extremism
- Impact of US withdrawal from Afghanistan
- AFSPA Meaning
- Disturbed Area
- Powers of armed forces under AFSPA
- Origin of AFSPA
- AFSPA in Nagaland
- Constitutionality of AFSPA & Role of Judiciary
- AFSPA, a draconian Act?
- Experts Recommendation on AFSPA
- But, why have AFSPA?
- Terrorism and role of External State and Non-State Actors
- Reasons for rise of Terrorism
- Terror Funding
- Terrorism Measures- Institutional and Legal Framework
- Militancy in Jammu and Kashmir
- Issues of Money Laundering
- Working of Money Laundering
- Evolving threats of Money laundering
- Impacts of globalization on money laundering
- Way forward
- Cryptocurrency and Money Laundering
- Statutory framework
- Institutional framework
- THE VIENNA CONVENTION on Money Laundering
- The FINANCIAL ACTION TASK FORCE (FATF)
- Asia/Pacific Group on Money Laundering (APG)
- Eurasian Group on Combating Money Laundering and Financing of Terrorism (EAG)
- Efforts to Tackle Black Money
- Meaning, Need and Importance of Cyber Security
- Cyber Security Framework in India
- Present Status of Cyber Security
- Cyber Security Index 2020
- Meaning and Types of Cybersecurity Threats
- What’s the Difference Between Malware, Trojan, Virus, and Worm?
Recent Cyberattacks
- Cyber warfare
- “Supply chain” cyber-attack
- Cyber Terrorism
- Growing threat of Cyber Security
- Pegasus Spyware
- Incidences of Cyberattacks in India
- Cybercrime Against Women
- Disinformation
- Cognitive hacking
- Way Forward
- Challenges to Cyber Security
- Steps taken by the Government to spread awareness about Cybercrimes
- Cybercrime volunteer programme
- National Cyber Security Strategy 2020
- National Security Directive on Telecom Sector
- National Cyber Security Policy, 2013
- Concerns / Challenges and Wayforward
- Critical Infrastructure and Critical Information Infrastructure (CII)
- Issues and Measures with respect to Media
- Rise of Social Media in recent decade
- Positive Impact of Social Media
- Negative impact of Social Media
- Campaigns by Social Media Platforms
- Role of Social Media during Pandemic
- Challenges of Social Media in Democracy
- Spread of Fake News
- Threats to Internal Security by Social Media
- Social media in the lives of women
- Countering Deepfakes
- Checking Online Abuse
- Regulations on Social Media
- Social Media- New Rules and Implications
- Information Technology Act, 2000
Home » Security Issues » Cyber Security » Various Cyber Threats » Recent Cyberattacks
- Recently, few “State-sponsored” Chinese hacker groups targeted various Indian power centres . However, these groups have been thwarted after government cyber agencies warned it about their activities.
- Recently, Australia had to stave off its biggest cyber threat with the attack targeting everything from public utilities to education and health infrastructure. India has also been a victim to many such cyber-attacks in the past like WannaCry, Petya ransomware, Mirai botnet etc.
- Towards the end of 2020, a major cyberattacks headlined ‘SolarWinds’ —was believed to have been sponsored from Russia. It involved data breaches across several wings of the U.S. government, including defence, energy and state.
- Thousands of U.S. organisations were hacked in early 2021 in an unusually aggressive cyberattack, by a Chinese group Hafnium, which had exploited serious flaws in Microsoft’s software, thus gaining remote control over affected systems.
- Another Russia-backed group, Nobellium, next launched a phishing attack on 3,000 e-mail accounts, targeting USAID and several other organisations.

- Our Mission, Vision & Values
- Director’s Desk
- Commerce & Accountancy
- Previous Years’ Question Papers-Prelims
- Previous Years’ Question Papers-Mains
- Environment & Ecology
- Science & Technology

IMAGES
VIDEO
COMMENTS
For Prelims: Cyber security, Ransomware, Indian Cyber Crime Coordination Centre (I4C), Budapest Convention on Cybercrime, Indian Computer Emergency Response Team (CERT-In), Cyber Surakshit Bharat, Cyber Swachhta Kendra, National Cyber security Coordination Centre (NCCC), Draft Digital Personal Data Protection Bill 2022, G20 For Mains: Recent Instances of Cyber Attacks in India, Major Types of ...
In February 2022, Air India experienced a major cyberattack that compromised approximately 4.5 million customer records. Passport, ticket, and some credit card information were compromised. In 2020, approximately 82% of Indian companies suffered ransomware attacks. In 2021, A high-profile India-based payment company, Juspay, suffered a data ...
Insights IAS: Simplifying UPSC IAS Exam Preparation. InsightsIAS has redefined, revolutionized and simplified the way aspirants prepare for UPSC IAS Civil Services Exam. Today, it's India's top website and institution when it comes to imparting quality content, guidance and teaching for the IAS Exam.
Context: The Ministry of Electronics and Information Technology is likely to come out with new cyber security regulations, as indicated by Minister of State at a recent cyber security event. The essence of this regulation will be to put the onus on organisations to report any cyber crime that may have happened against them, … Continue reading "Insights into Editorial: Reporting cyber attacks"
Reasons for increasing Cyber Attacks in India. Increasing dependency on technology: As we grow faster, more and more systems are being shifted to virtual space to promote access and ease of use. However, the downside to this trend is the increased vulnerability of such systems to cyber-attacks. For e.g., there is a concern of widespread damage ...
Cyber Security initiatives are taken up by the Ministry of Electronics and Information Technology in India. Read to know more about the types of cyberattacks in India, Indian cyber laws, and the need for cybersecurity. Download cybersecurity notes PDF for UPSC GS-III preparation. For UPSC 2023, follow BYJU'S
Vedic Period: History Notes for UPSC & Govt. Exams; Sangam Age - Political History of South India | UPSC Ancient History Notes; MAURYAN EMPIRE (322-185 BCE): Reign, Ruler & Historical Significance; Jainism and Buddhism: Difference and Similarities| UPSC Notes; Post Mauryan Period (200 BC - 300 AD) - Clashes, Cultures, and Kingdoms in ...
Context: Ransomwares have emerged as the most predominant of malicious cyberattacks worldwide. About Cyberattacks: Cyberattacks are unwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer systems. Typically such forms of attacks to keep networks from functioning after encrypting data, are carried out by ransomware-seeking entities. In ...
For Mains: India's vulnerability to cyber attacks, Challenges posed by cyber attacks, Government Initiatives and Way Forward. As the world is advancing in the realm of digitalisation, the threat of cyber attacks has also grown and India is no exception to it. In October, 2023, Resecurity, a US company, informed the world about the ...
Agencies to deal with the cyber threat: The Indian Computer Emergency Response Team (CERT-In) established in 2004 is the national nodal agency that collects, analyses and circulates inputs on cyber-attacks.; The National Critical Information Infrastructure Protection Centre has been set up for the protection of national critical information infrastructure.
Source: This post is based on the article "Cyberwarfare: Everything you need to know" published in Livemint on 25th February 2022. Ukraine has been hit by a wave of cyberattacks targeting critical infrastructure companies. The timing and scale of the attacks point towards hackers working at the behest of Russia.
An attacker uses people, computers, phones, applications, messages, and system processes to carry out an attack. Individuals, organizations, institutions, and governments can be victims of an attack. Modes of Cyber Attack. Lock data and processes, and demand a ransom. Remove vital information to cause serious harm. Steal information.
Cyber Security is the practice of protecting computers, networks, and data from malicious attacks. The term 'cyber' is related to or involves computers and computer networks. This connection between the internet ecosystems forms cyberspace, leading to various issues that lead to needing Cyber Security. It involves implementing measures and ...
Rethinking India's Cyber Defence. 05 Dec 2022. 11 min read. Tags: GS Paper - 3. Cyber Security. Cyber Warfare. Challenges to Internal Security Through Communication Networks. This editorial is based on "The AIIMS attack shows the importance of a robust cybersecurity framework" which was published in Hindustan Times on 04/12/2022.
Build offensive cyber capabilities - systems to intrude, intercept and exploit digital networks. It serves as function of strategic "cyber deterrence". Conclusion: Cyber security is a crucial aspect of our digital world. It involves protecting systems, networks, and data from unauthorized access and damage.
GS Paper 3 Syllabus: Internal Security: Cyber attacks Source: IE Context: Apple has been sending automated notifications to individuals worldwide, including many politicians and opposition leaders, alerting them to potential state-sponsored attacks. What is State-Sponsored Cyber Attack? A state-sponsored cyber-attack is a hacking or digital intrusion orchestrated or supported by a government ...
Cyber warfare is computer- or network-based conflict involving politically motivated attacks by a nation-state on another nation-state. In these types of attacks, nation-state actors attempt to disrupt the activities of organizations or nation-states, especially for strategic or military purposes and cyber espionage. It involves the actions by a nation-state or international organization to ...
This editorial is based on "Securing India's cyberspace from quantum techniques" which was published in The Indian Express on 17/10/2022. It talks about the issues related to India's cyberspace and rising quantum technology. For Prelims: WannaCry, Cloud computing, 5G, E-Commerce, Quantum technology, Man in Middle Attack, Denial of ...
Cost of cyber-attacks. There are many cyber-attacks that go undetected and unreported as well.; The losses emanate from operational disruptions, loss of sensitive information and designs, customer churn and impact on brand image, as well as increase in legal claims and insurance premium.; Limited awareness. Many companies do not treat importance of cyber security as a strategic agenda, but ...
National Cyber Crime Reporting Portal: A platform where the public can report incidents of cyber-crimes, with a special focus on crimes against women and children. Citizen Financial Cyber Fraud Reporting and Management System: It is a system for immediate reporting of financial frauds and assistance in lodging online cyber complaints through a ...
India has also been a victim to many such cyber-attacks in the past like WannaCry, Petya ransomware, Mirai botnet etc. Towards the end of 2020, a major cyberattacks headlined 'SolarWinds' —was believed to have been sponsored from Russia. It involved data breaches across several wings of the U.S. government, including defence, energy and ...