
- Onsite training
3,000,000+ delegates
15,000+ clients
1,000+ locations
- KnowledgePass
- Log a ticket
01344203999 Available 24/7

What is Web Jacking In Cyber Security?
This blog on Web Jacking in Cyber Security explains the threats Web Jacking poses to organisations and the measures that can used to stay safe from them.

Exclusive 40% OFF
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Share this Resource
- Microsoft Cybersecurity Architect SC100
- Cyber Security Awareness
- CISSP-ISSAP Training & Certification
- CISSP Certification
- Introduction to System and Network Security

Nowadays, terms like Cybercrime and cyber security attack are gaining popularity. Cyber-attacks occur so frequently that both individuals and organisations are at risk of falling prey to it. Implementing effective Cyber Security Risk Management strategies are crucial in safeguarding against such threats. The Cyber Threat Defense Report of 2021 stated a 5% increase in the foundational IT security budget. In recent years, the number of Cyber Security professionals has increased considerably.
Know about Web Jacking, a type of phishing attack frequently used to obtain user information, such as credit card numbers and login information, in Cyber Security.
Table of contents
1) What is Web Jacking?
2) Understanding how Web Jacking works
3) Web Threats for Organisations In Cyber Security
4) How to stay safe from Web Jacking?
5) Conclusion
Learn everything you need to know about cyber threats and Cyber Security. Sig n up for our Cyber Security Awarenes s course now!
What is Web Jacking?
There are still millions of people who do not understand the significance of Cyber Security , let alone web threats like Web Jacking. The safety of your web must be a priority. This is why it is important to understand how Web Jacking works and learn how to prevent it.

Understanding how Web Jacking works
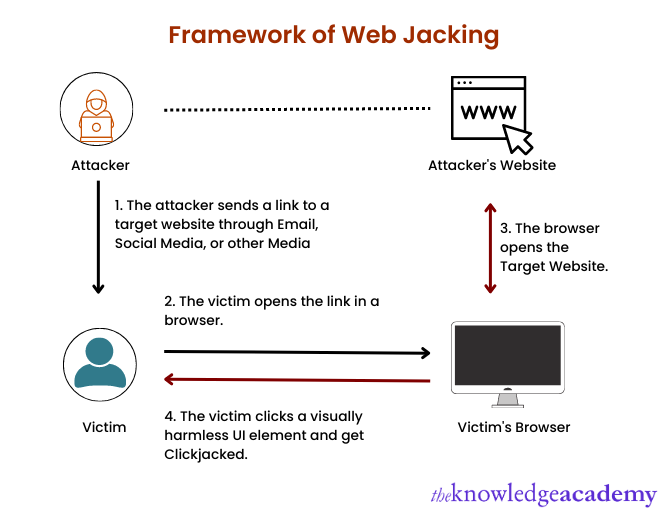
Web Jacking is a phishing attack intended to extract confidential data from users. It follows a basic skeleton, from creating a fake website to freezing it to steal the users' login information. Following are the steps generally followed by attackers in Web Jacking.
a) Compromising the Domain Name System (DNS): Firstly, the hacker creates a fake web page using the same domain name as the targeted web application.
b) Hosting: The second step is to host it on your computer or shared hosting.
c) Sending link: This step involves the hacker sending the fake website’s link to the victim. The success of the hacker’s mission depends entirely on whether the victim falls for it.
d) Entering details: If the victim clicks on the link, it directs them to the malicious website. As the victim enters sensitive information like their login credentials or credit card details, the hacker gets all of it. The attacker can use these freshly retrieved details for nefarious reasons.
Learn to deal with advanced cyber threats and respond with efficient solutions. Sign up for our CCNA Cybersecurity Operation Training course now!

How do you initiate a Web Jacking attack?
Seven steps need to be followed to launch a Web Jacking attack:
a) T he first step to applying the Web Jacking method is to make use of the ‘ setoolkit ’ in Kali Linux.
b) Next, open the K ali Linux system, followed by the Termi nal window .
c) Type setoolkit on the terminal .
d) This will pave the way for various options for attacking methods. From the provided list , you must choose the Social-engineering attack option .
e) You are required to type 1 to select your preferred s ocial-engineering attack. This gives you numerous options of attack types to choose from. If you type 2, it shows the list of ways that you can use to attack the website, as you require a vector it.
The steps mentioned above will help create a fake website (the same as the victim's website page) and host it on your computer.
f) The next step is copying the fake website link and sending it to the victim. Make sure that the link is changed to the domain name if it was present as your local computer IP address.
g) For converting, open the link, type your computer ID ad dres s , a nd wait for the link to be created. Once it ’ s ready, send it to the victim and wait until they enter their details.
Once the victim opens the link, their browser will display a message – the site www.xyz.com has moved to another address, click here to go to the new location - that asks them to move to a new page . The victim gets redirected to the fake webpage upon clicking this link.

Web Threats For Organisations In Cyber Security
The fatality of being a victim of cybercrime can vary on the degree of attack and the hacker’s target group. While aiming at organisations, hackers intend to extract cardinal data that can pave the way to more sensitive information or money. Alongside knowing about cyber–attacks, it is also important to understand the results of being conned on the Web.
Protect your business by examining the potential threats it faces and delving into concepts of hacking. Sign up for our Certified Cyber Security Professional (CCS - PRO) cour se now!
Consequences of Web Jacking in Organisations
Web Jacking can affect an organisation in various ways. If at all an employee’s login credentials get leaked, the hacker has access to all the files on that person’s system, which might hold company-sensitive data. When an organisation gets hit with this type of cyber-attack, they are prone to vast amounts of financial loss. Losing funds can lead to losing business partners, a gradual dip in market shares, and a tainted reputation.
How to stay safe from Web Jacking?

a) The first tip to keep in mind is to avoid clicking on suspicious links that make their way to you via emails or messages.
b) Always check the legitimacy of the link by pasting the URL on the address bar. Your first hint at a fraudulent link could be the difference between the URL and the intended website.
c) Make use of browsers with anti -phishing detection.
d) If your links include company or institution names, confirm the original spelling.
e) Another tip to keep in mind is that if or when you come across a shady website that is asking for your details, do not give your original credentials. Instead, put in a fake username and password. This way, you protect your information and can confirm the website’s legitimacy.

Web Jacking is merely one of the multiple types of cyber threats present today. Since it is difficult to keep up with all of them, understanding them one by one is taking one step in the right direction. We hope this blog has helped familiarise you with Web Jacking in Cyber Security.
Improve your understanding of virtual risks and different ways to manage and prevent them Sign up for our Cyber Security Risk Management course now!
Frequently Asked Questions
Upcoming it security & data protection resources batches & dates.
Fri 26th Apr 2024
Fri 9th Aug 2024
Fri 6th Dec 2024
Get A Quote
WHO WILL BE FUNDING THE COURSE?
My employer
By submitting your details you agree to be contacted in order to respond to your enquiry
- Business Analysis
- Lean Six Sigma Certification
Share this course
Our biggest spring sale.

We cannot process your enquiry without contacting you, please tick to confirm your consent to us for contacting you about your enquiry.
By submitting your details you agree to be contacted in order to respond to your enquiry.
We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Or select from our popular topics
- ITIL® Certification
- Scrum Certification
- Change Management Certification
- Business Analysis Courses
- Microsoft Azure Certification
- Microsoft Excel & Certification Course
- Microsoft Project
- Explore more courses
Press esc to close
Fill out your contact details below and our training experts will be in touch.
Fill out your contact details below
Thank you for your enquiry!
One of our training experts will be in touch shortly to go over your training requirements.
Back to Course Information
Fill out your contact details below so we can get in touch with you regarding your training requirements.
* WHO WILL BE FUNDING THE COURSE?
Preferred Contact Method
No preference
Back to course information
Fill out your training details below
Fill out your training details below so we have a better idea of what your training requirements are.
HOW MANY DELEGATES NEED TRAINING?
HOW DO YOU WANT THE COURSE DELIVERED?
Online Instructor-led
Online Self-paced
WHEN WOULD YOU LIKE TO TAKE THIS COURSE?
Next 2 - 4 months
WHAT IS YOUR REASON FOR ENQUIRING?
Looking for some information
Looking for a discount
I want to book but have questions
One of our training experts will be in touch shortly to go overy your training requirements.
Your privacy & cookies!
Like many websites we use cookies. We care about your data and experience, so to give you the best possible experience using our site, we store a very limited amount of your data. Continuing to use this site or clicking “Accept & close” means that you agree to our use of cookies. Learn more about our privacy policy and cookie policy cookie policy .
We use cookies that are essential for our site to work. Please visit our cookie policy for more information. To accept all cookies click 'Accept & close'.
Clickjacking: Beware of Clicking
- Published: 01 September 2021
- Volume 121 , pages 2845–2855, ( 2021 )
Cite this article
- Rishabh Sahani 1 &
- Sukhchandan Randhawa ORCID: orcid.org/0000-0002-4330-9732 1
316 Accesses
4 Citations
3 Altmetric
Explore all metrics
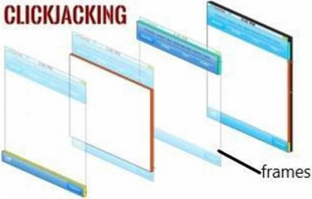
Clickjacking is a newly discovered breach in network security. It is based on the functionality of web-designing in which two or more web frames are overlapped over each other. The analysis shows that there is a need for in-depth study on click-jacking attacks (client-side vulnerability) and preventive measures so that early prevention and detection of such kinds of attacks can be implemented in a timely manner. In this research work, most of the client-side attacks are studied and an overview of the clickjacking techniques is presented to provide insights into the area of network security to the researchers. The overview of tools and techniques used by attackers are also investigated along with the prevention measures.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Code Availability
No code is used for the research article.
Availability of data and material
Data and material used in the article are available.
Sinha, R., Uppal, D., Singh, D., & Rathi, R. (2014). Clickjacking: Existing defenses and some novel approaches. In 2014 International Conference on Signal Propagation and Computer Technology (ICSPCT 2014) , (pp. 396–401).
Pawade, D., Reja, D., Lahigude, A., & Johri, E. (2016). Implementation of extension for browser to detect vulnerable elements on web pages and avoid Clickjacking. In 2016 6th International Conference - Cloud System and Big Data Engineering (Confluence) (pp. 226–230). https://doi.org/10.1109/CONFLUENCE.2016.7508118
Shamsi, J. A., Hameed, S., Rahman, W., Zuberi, F., Altaf, K., & Amjad, A. (2014). Clicksafe: Providing Security against Clickjacking Attacks. In 2014 IEEE 15th International Symposium on High-Assurance Systems Engineering (pp. 206–210). https://doi.org/10.1109/HASE.2014.36
Lundeen, B., & Alves-Foss, J. (2012). Practical clickjacking with BeEF. In 2012 IEEE Conference on Technologies for Homeland Security (HST) (pp. 614–619). https://doi.org/10.1109/THS.2012.6459919
Qianqian, W., & Xiangjun, L. (2014). Research and design on Web application vulnerability scanning service. In 2014 IEEE 5th International Conference on Software Engineering and Service Science (pp. 671–674). https://doi.org/10.1109/ICSESS.2014.6933657
Faghani, M. R., & Nguyen, U. T. (2014). A study of clickjacking worm propagation in online social networks. In Proceedings of the 2014 IEEE 15th International Conference on Information Reuse and Integration (IEEE IRI 2014) (pp. 68–73). https://doi.org/10.1109/IRI.2014.7051873
Kim, D., & Kim, H. (2015). Performing Clickjacking Attacks in the Wild: 99% are Still Vulnerable! In 2015 1st International Conference on Software Security and Assurance (ICSSA) (pp. 25–29). https://doi.org/10.1109/ICSSA.2015.015
Takamatsu, Y., & Kono, K. (2014). Clickjuggler: Checking for incomplete defenses against clickjacking (pp. 224–231). https://doi.org/10.1109/PST.2014.6890943
Rehman, U. U., Khan, W. A., Saqib, N. A., & Kaleem, M. (2013). On Detection and Prevention of Clickjacking Attack for OSNs. In 2013 11th International Conference on Frontiers of Information Technology (pp. 160–165). https://doi.org/10.1109/FIT.2013.37
Krishna Chaitanya, T., Ponnapalli, H., Herts, D., & Pablo, J. (2012). Analysis and Detection of Modern Spam Techniques on Social Networking Sites. In 2012 Third International Conference on Services in Emerging Markets (pp. 147–152). https://doi.org/10.1109/ICSEM.2012.28
Wu, L., Brandt, B., Du, X., & Ji, B. (2017). Analysis of clickjacking attacks and an effective defense scheme for Android devices. In 2016 IEEE Conference on Communications and Network Security, CNS 2016 , (pp. 55–63). https://doi.org/10.1109/CNS.2016.7860470
Rydstedt, G., Bursztein, E., Boneh, D., & Jackson, C. (2010). Busting Frame Busting : a Study of Clickjacking Vulnerabilities on Popular Sites A Survey of Frame busting. Web 20 Security and Privacy 2010 , pp. 1–13. Retrieved from http://www.mendeley.com/research/busting-frame-busting-study-clickjacking-vulnerabilities-popular-sites-survey-frame-busting-2/
Starov, O., Zhou, Y., & Wang, J. (2019). Detecting malicious campaigns in obfuscated JavaScript with scalable behavioral analysis. In Proceedings - 2019 IEEE Symposium on Security and Privacy Workshops, SPW 2019 , (pp. 218–223). https://doi.org/10.1109/SPW.2019.00048
Kalim, A., Jha, C. K., Tomar, D. S., & Sahu, D. R. (2021). Novel Detection Technique For Framejacking Vulnerabilities In Web Applications. In 2021 2nd International Conference on Computation, Automation and Knowledge Management (ICCAKM) (pp. 265–270). https://doi.org/10.1109/ICCAKM50778.2021.9357764
Narayanan, A. S. (2012). Clickjacking vulnerability and countermeasures. International Journal of Applied Information Systems, 4 (7), 7–10. https://doi.org/10.5120/ijais12-450793
Article Google Scholar
Rehman, U. U., Khan, W. A., Saqib, N. A., & Kaleem, M. (2013). On detection and prevention of clickjacking attack for OSNs. In Proceedings - 11th International Conference on Frontiers of Information Technology, FIT 2013 , (December), (pp. 160–165). https://doi.org/10.1109/FIT.2013.37
Patil, Y. (2020). Detection of Clickjacking Attacks using the Extreme Learning Machine algorithm MSc Cyber Security 2019–2020 Yashodha Patil.
Kavitha, D., & Ravikumar, S. (2016). Click jacking Vulnerability Analysis and Providing Security against WEB Attacks Using White listing URL analyzer. International Journal of Computer Techniques , 2 (3). Retrieved from http://www.ijctjournal.org
Shital, P., & R., Chavan. . (2017). Web browser security: Different attacks detection and prevention techniques. International Journal of Computer Applications, 170 (9), 35–41. https://doi.org/10.5120/ijca2017914938
Possemato, A., Lanzi, A., Chung, S. P. H., Lee, W., & Fratantonio, Y. (2018). Clickshield: Are you hiding something? Towards eradicating clickjacking on android. In Proceedings of the ACM Conference on Computer and Communications Security , (pp. 1120–1136). https://doi.org/10.1145/3243734.3243785
Download references
No funding availed. So, this is not applicable.
Author information
Authors and affiliations.
Computer Science and Engineering Department, Thapar University, Patiala, Punjab, India
Rishabh Sahani & Sukhchandan Randhawa
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Sukhchandan Randhawa .
Ethics declarations
Conflict of interest.
The author declares there is no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Sahani, R., Randhawa, S. Clickjacking: Beware of Clicking. Wireless Pers Commun 121 , 2845–2855 (2021). https://doi.org/10.1007/s11277-021-08852-y
Download citation
Accepted : 06 August 2021
Published : 01 September 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s11277-021-08852-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Click-Jacking
- Like-Jacking
- Frame-Busting
- Find a journal
- Publish with us
- Track your research
Web Jacking: A Basic Overview In 3 Points
INTRODUCTION
When a Web application improperly redirects a user’s browser from a page on a trusted domain to a bogus domain without the user’s consent, it’s called Web Jacking. Web Jacking attack method is another type of social engineering attack method called Phishing attack, often used to steal user data, including login credentials and credit card numbers. When an attacker impersonating an object, cheats the victim by opening an email, instant message, or text message. The recipient is then tricked into clicking on a malicious link, leading to a malware installation, program freezing as part of a ransomware attack, or exposure to sensitive information.
Attacks can have serious consequences. For individuals, this includes unauthorized purchases, money laundering, or identity theft. Also, identity theft is often used to gain corporate or government networks as part of a larger attack, such as an Advanced Persistent Threat (APT). In the latter case, employees are compromised to go through security perimeters, distribute malware within a closed area, or gain access to secure data. An organization defeated by these attacks often supports greater financial losses in addition to declining market share, reputation, and consumer confidence. Broadly speaking, a criminal attempt to steal sensitive information can escalate into a security incident where the business will have a difficult time recovering.
- Web jacking attack method
- How to apply Web jacking attack method
- How to be safe from the Web jacking attack method?
1. Web jacking attack method
The setup for the attack is simple:
1. A hacker registers a free domain name that is the same as the domain of a web application. Using a generic attack vector, the attacker sets up the real site to be malicious and lies about the domain name of the real site.
2. The attacker sends a request to the legitimate web application using the domain of the malicious site. The request for authentic information from the victim (e.g., a user account) causes the web application to sign the user out. The attacker uses the user’s user name and password to log in as the victim.
3. The attacker can now use the victim’s user name and password to log in as the victim. If the attacker uses the name and password for the victim’s account, they can access any information from the victim’s account on the legitimate website. The attacker can now send an authentication request with the victim’s real name and password to its legitimate website. The victim’s account will only accept this request if the user name and password match the attackers.
4. The attacker signs up for a free domain name that contains one or more numbers or special characters. Using the official domain name of the site as the source of the registration, the attacker registers an account at a hosting service or cloud storage site. Using this account, the attacker posts a malicious script to the host site that contains the malicious user name and/or password. The script performs a malicious action on behalf of the victim.
5. The attackers often use malicious scripts that work with popular cloud storage sites such as DropBox or Google Drive. After the malicious script is uploaded to the hosting service or cloud storage site, the malicious user name and/or password are displayed on the account page.
6. The user is directed to a login page hosted on the hosting service or cloud storage site. The user is then asked to enter his or her own user name and/or password. The user is then shown a fake login form that uses the user name and password for the malicious site. If the user is tricked into entering the fake login form, the host site or the cloud storage site is logged out of the account. This means that the user’s legitimate account is logged out of his or her account as well.
7. The attacker is now able to log into the victim’s account. This is because the victim’s account was logged out when the user visited the login page. The attacker can now use the victim’s legitimate account to download any file the victim has on the host server or cloud storage site. The attacker can also delete any files stored on the cloud storage site, and users are never alerted to the incident.
2. How to apply Web jacking attack method
Step 1: To use the web jacking attack method, we will use a tool in kali Linux called setoolkit.
Step 2: Open your kali Linux system, then open the Terminal window.
Step 3: Type a deadly setoolkit.
Step 4: It will show many ways to attack, but you will have to choose a Social-engineering attack.
Step 5: Type 1 to choose a Social-engineering attack. It will show multiple methods of engineering attack. Here, you have to select a vector to attack the website, so type 2 will show different ways to attack it.
The above methods will create a fake webpage similar to the victim’s web page and host it on your computer.
Step 6: Copy the link (IP of your computer that you previously installed) to the fake website and send it to the victim. If the link is your home IP address, then change it to a domain name. To convert your IP address to a domain name, open the link and type your computer’s IP address here. It will create a link. Now, your link is ready to copy and send to the victim, then wait until they enter their details.
Step 7: When the victim opens a link in their browser, the browser displays the message “help www.abc.com move to another address, click here to go to a new location,” and click this link, they will find it redirected to a fake webpage.
3. How to be safe from the Web jacking attack method?
Users who receive emails with phishing links should always check the URL first by typing the URL in the address bar rather than clicking the link. If the URL does not match the expected website, the user should not click on the link and should also not click on any suspicious links in emails. Users should also avoid clicking on links sent in emails with an embedded image or if the sender starts with a link that looks like a typical URL.
The purpose of this Web Jacking is to damage someone’s reputation or to take away a ransom from the real owner. It is a very interesting method that tries to deceive the user that the web page is real, but in reality, it is a fake page, and then by clicking on the victim, they get all the information of the victim.
So, have you made up your mind to make a career in Cyber Security? Visit our Master Certificate in Cyber Security (Red Team) for further help. It is the first program in offensive technologies in India and allows learners to practice in a real-time simulated ecosystem, that will give them an edge in this competitive world.
- Data Degaussing: A Comprehensive Guide In 2021
- SOC Analyst: A Basic Guide In 4 Points
Fill in the details to know more
PEOPLE ALSO READ

Related Articles

What Is Asset Classification?
March 20, 2023
Masquerade Attack – Everything You Need To Know!
February 27, 2023

Best Infosys Information Security Engineer Interview Questions and Answers
What Are SOC and NOC In Cyber Security? What’s the Difference?

A Brief Introduction to Cyber Security Analytics
February 26, 2023

Cyber Safe Behaviour In Banking Systems
February 17, 2023
Are you ready to build your own career?
Query? Ask Us
Enter Your Details ×
Burp Scanner
Burp Suite's web vulnerability scanner

Product comparison
What's the difference between Pro and Enterprise Edition?

Download the latest version of Burp Suite.

Top 10 web hacking techniques of 2021

James Kettle
Director of Research
Published: 09 February 2022 at 13:59 UTC
Updated: 10 February 2022 at 15:20 UTC

Welcome to the Top 10 (new) Web Hacking Techniques of 2021, the latest iteration of our annual community-powered effort to identify the most significant web security research released in the last year.
Since kicking off the selection process in January, the infosec community has nominated 40 research papers, then voted on their favourites to whittle the list down to 15 final-round candidates. Finally, an expert panel consisting of myself and noted researchers Nicolas Grégoire , Soroush Dalili , and Filedescriptor have voted on the 15 finalists to create the official top 10. As usual, we haven't excluded PortSwigger research, but panellists can't vote for anything they're affiliated with.
The research quality this year was frankly exceptional - it's the strongest year I've seen since getting involved back in 2015. This has led to fierce competition for the top 10, and numerous high-standard research papers missing out. I usually name a few of my favourite runners up but this year there's so many it would be unfair - instead I recommend anyone with time explores the full nomination list . Massive thanks to everyone who contributed to this wave of research!
One particular theme dominated this year. In both the nominations and the final top ten, we saw heavy focus on HTTP Request Smuggling , and attacks on parser inconsistency in general. As systems get more complex and more connected, these threats bloom. It'll be interesting to see where the parser battleground shifts when HTTP/1.1 use eventually starts to dwindle in a few decade's time.
Let's begin the countdown!
10 - Fuzzing for XSS via nested parsers
With an age-old topic like XSS, it's all too easy to think you know it all already and glibly dismiss new research. Gems like Fuzzing for XSS via nested parsers prove just how risky this is. In this fluff-free post, Psych0tr1a shows how to turn stacked HTML sanitization rules against each other with specular results. Impressive case-studies and a clear, practical methodology cement this as a piece of top-tier research.
9 - HTTP Smuggling via Higher HTTP Versions
At the start of 2021, HTTP/2 was thought to be largely free of security concerns beyond timing attacks and minor DoS concerns. Emil Lerner 's HTTP Smuggling via Higher HTTP Versions destroyed this myth, using custom tooling and innovative techniques to reveal numerous holes in HTTP/2 to HTTP/1.1 conversion. The slide deck is crammed with novel attacks and if you're fluent in Russian, be sure to check out the presentation too. Emil's also written up some terrifying new findings on HTTP/3 since.
8 - Practical HTTP Header Smuggling
A vulnerability can be prevalent, well-understood and high-impact, but if nobody knows how to detect it, it can be tempting to just... refocus your thoughts on something more profitable. CL.CL request smuggling had been quietly lurking in this niche for quite a while.
In Practical HTTP Header Smuggling , Daniel Thatcher isolates a core component of HTTP Request Smuggling, and elegantly restiches it into a strategy that makes it possible to identify both CL.CL vulnerabilities, and generic hidden-header attacks, all integrated into Param Miner . In case you have any doubts about just how valuable this methodology is, he illustrates it with multiple case-studies targeting AWS. You'll hear more about this technique in future.
7 - JSON Interoperability Vulnerabilities
JSON has long been known for being a bit quirky, but largely dodged the barrage of exploits affecting XML parsing. However, whatever the format, if you're going to parse something twice, things are going to go wrong.
JSON Interoperability Vulnerabilities by Jake Miller takes an in-depth look at how to trigger JSON parser inconsistencies, and where these usually-harmless quirks can become exploitable. Bundled Docker-based labs make these easy to replicate and practise.
6 - Cache Poisoning at Scale
Case studies make or break research, and Cache Poisoning at Scale has them in droves. Youstin proves web cache poisoning is still endemic, and still widely overlooked. DoS vulnerabilities are often spurned by researchers, but the persistent, single-request takedowns offered by web cache poisoning are clearly taken seriously by many companies. This is also a solid demonstration of the art of chaining tiny inconsistencies with secret headers and misconfigurations to concoct a severe vulnerability.

5 - Hidden OAuth attack vectors
Hackers typically focus on endpoints that are either directly visible, or discovered during recon. In Hidden OAuth attack vectors , our own Michael Stepankin takes an alternative approach and dives deep into the OAuth and OpenID specifications to uncover hidden endpoints and design flaws that lay the stage for enumeration, session poisoning and SSRF . Michael has also updated both ActiveScan++ and Burp's discovery wordlists to keep an automated eye out and make sure this attack surface doesn't slip by unnoticed.
4 - Exploiting Client-Side Prototype Pollution in the wild
Described by filedescriptor as "arguably an underdog bug class as it's only occasionally exploited", Prototype Pollution was strictly a technique for enthusiasts until A tale of making internet pollution free - Exploiting Client-Side Prototype Pollution in the wild landed.
This phenomenal research defines a clear, insightful methodology for practical identification and exploitation. It's also notable for the all-star cast, headed by s1r1us - in Soroush's words "It feels like watching Avengers!"
3 - A New Attack Surface on MS Exchange
Orange Tsai is back in the Top 10 for the 5th year running, with the 3-part series A New Attack Surface on MS Exchange . While most research focuses on uncovering classes of vulnerability common across numerous websites, this work instead delves astoundingly deep into a single target, with catastrophic results.
The entire panel loved this entry, describing it as a "flawless intro to Exchange's architecture and attack surface, with reliable exploits and huge impact" , an "inspiring read if you want to start serious research" , and a "can of worms" that "changed the way many looked at this popular mailing solution and reminded us even the most secure looking apps can be broken easily if you are persistent and pay attention to all the details" .
2 - HTTP/2: The Sequel is Always Worse
Nine months in the making, my own HTTP/2: The Sequel is Always Worse had a topic-collision with Emil's work above which made this more 'interesting' than it should have been, but some last-minute breakthroughs saved the day. Here's what the other panellists had to say: "Ever wondered what could go wrong when converting between binary and ASCII protocols?" "This research has everything a reader needs. Besides the actual research and result, the quality write up, tooling, and the presentation make this very special." "This is a nice research on how HTTP2 tremendously increases the complexity of the whole situation. As HTTP2 usage is still being adopted, request smuggling will be even more relevant with the help of the never-ending HTTP (down)upgrade."
If you enjoy this presentation, I highly recommend checking out the other high quality research papers on HTTP Request Smuggling in the full nomination list - just CTRL+F smuggling!
1 - Dependency Confusion
Some of the best research has an elegant simplicity that makes it seem deceptively obvious in hindsight. In Dependency Confusion , Alex Birsan exposes critical design and configuration flaws affecting major package managers, exploiting package name ambiguity to achieve RCE on numerous major companies and earn well over $100k in bounties. Beyond the crazy impact, it's also exceptionally well-explained, taking the reader through the entire research journey.
Discussions and mitigations are still underway for this attack, and we're really curious to see where this avenue of research goes next. Is the attack so elegant it can't be improved? Or is this just the humble beginning of a persistent new attack class? What we do know is if you're only going to read one piece of research this year, you should make it Dependency Confusion. Congratulations to Alex on a well deserved win!
2021 was a seriously good year for web security research.
More than ever this year, the top 10 list just scratches the surface and we recommend web security enthusiasts read the entire nomination list . Past year's top 10s are well worth a look too! You can also get the drop on this year's top research the moment it's released by following r/websecurityresearch and @PortSwiggerRes . Also, if you're interested in doing this kind of research yourself, I've written up some advice for you . Also, before we wrap up, I should give an honorary mention to the repeatedly nominated, hot new hacking technique known only as 'F12'. Sadly it didn't make the cut.
Thanks again to everyone who took part! Without your nominations, votes, and most-importantly research, this wouldn't be possible.
Till next time!
Back to all articles
Related Research
This website uses cookies to analyze our traffic and only share that information with our analytics partners.
Clickjacking
Clickjacking, also known as a “UI redress attack”, is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. Thus, the attacker is “hijacking” clicks meant for their page and routing them to another page, most likely owned by another application, domain, or both.
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of stylesheets, iframes, and text boxes, a user can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attacker.
For example, imagine an attacker who builds a web site that has a button on it that says “click here for a free iPod”. However, on top of that web page, the attacker has loaded an iframe with your mail account, and lined up exactly the “delete all messages” button directly on top of the “free iPod” button. The victim tries to click on the “free iPod” button but instead actually clicked on the invisible “delete all messages” button. In essence, the attacker has “hijacked” the user’s click, hence the name “Clickjacking”.
One of the most notorious examples of Clickjacking was an attack against the Adobe Flash plugin settings page . By loading this page into an invisible iframe, an attacker could trick a user into altering the security settings of Flash, giving permission for any Flash animation to utilize the computer’s microphone and camera.
Clickjacking also made the news in the form of a Twitter worm . This clickjacking attack convinced users to click on a button which caused them to re-tweet the location of the malicious page, and propagated massively.
There have also been clickjacking attacks abusing Facebook’s “Like” functionality. Attackers can trick logged-in Facebook users to arbitrarily like fan pages, links, groups, etc
Defending against Clickjacking
There are three main ways to prevent clickjacking:
- Sending the proper Content Security Policy (CSP) frame-ancestors directive response headers that instruct the browser to not allow framing from other domains. The older X-Frame-Options HTTP headers is used for graceful degradation and older browser compatibility.
- Properly setting authentication cookies with SameSite=Strict (or Lax ), unless they explicitly need None (which is rare).
- Employing defensive code in the UI to ensure that the current frame is the most top level window.
For more information on Clickjacking defense, please see the the Clickjacking Defense Cheat Sheet .
- Why am I anxious about Clickjacking?
- A Basic understanding of Clickjacking Attack
- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/frame-ancestors
- Mozilla developer resource on Content-Security-Policy frame-ancestors response header.
- https://developer.mozilla.org/en-US/docs/The_X-FRAME-OPTIONS_response_header
- Mozilla developer resource on the X-Frame-Options response header.
- Busting Frame Busting: A study of clickjacking vulnerabilities on top sites
- A study by the Stanford Web Security Group outlining problems with deployed frame busting code.
- Clickjacking, Sec Theory
- A paper by Robert Hansen defining the term, its implications against Flash at the time of writing, and a disclosure timeline.
- https://www.codemagi.com/blog/post/194
- Framebreaking defense for legacy browsers that do not support X-Frame-Option headers.
- A simple J2EE servlet filter that sends anti-framing headers to the browser.
- CSP frame-ancestors vs. X-Frame-Options for Clickjacking prevention
Important Community Links
- Attacks (You are here)
- Vulnerabilities
Upcoming OWASP Global Events
Owasp news & opinions.
+ Clients Back
- Get Free Legal Answers
- Get Fee Estimates
- Deeds & Drafts
- Find Lawyers
- Get A Dedicated Legal Assistant
- Office Manager
- Display Boards
- Petitions & Pleadings Templates
- Case Diary & Office Manager
- Post News & Artilces
- Post Jobs & Internships
- Get A Dedicated Legal Secretary
+ Law Students
- Campus Ambassadors
- Find Jobs & Internships
- Post News & Articles
- Resource Sharing
+ Law Schools
- Post Admissions
- Post Opportunities
- Get Law School Rating
DETAILED OVERVIEW: WEB JACKING
Latest news.
Web Jacking is done at the places where the attackers create a fake website and when the website opens it will direct it to another website and harm the user’s system. It is basically done to steal the sensitive data of the victim and use it. As there are many types of cyber-crime that are growing with a fast pace in society it becomes very important to stop it and for that everyone should have a full knowledge of the cyber- security. Every person who makes the website is having their own domain and no one can have the same domain but when it is highjacked then the other person takes that domain and then ask for the ransom from the real owner. He may also conduct illegal activities on the website. Customers and the subscribers everyone can be fooled because it looks so similar to the real website and it becomes difficult to know that it’s not the real website.
TOPIC- WEB JACKING
Web Jacking is one of types of Cyber Crime. There are different tactics and strategies adopted by cyber people to carry out nefarious activity on the web. Web Jacking is used in social media where the creators makes a fake website and when the website open it will direct it to another malicious website then it harms the user’s system. In simple terms when the website or the web is hijacked then its terms as Web Jacking. Recently, the site Ministry of Information Technology was hacked by Pakistan hackers and also by the Bombay crime branch site was also been hacked. It is done to take out all the sensitive and confidential information of the users.
Web jacking attack method is one kind of trap which is spread by the attacker to steal the sensitive data of any people, and those people got trapped who are not aware about cyber security.
METHODS OF WEB JACKING
- The first thing that is done in Web Jacking is to create a fake page of victim website for example www.anywebsite.com/login.php .
- The second step is to host it either on your local computer or shared hosting.
- Then third comes to send the link of the fake page to the victim.
- Further comes the fourth step in which the victim thinks that it is a valid link and click on it and enter all his details and submit it.
- Last step, comes accused will get all the details submitted by the victim.
WHAT ARE THE THREATS?
As the fraudster taken over the domain, he may tell the real owner of the website to pay the ransom for restoring control over him. He may also conduct illegal activities on the website and then the customers and subscribers all can be fooled by thinking that they are working and entering the details in the real website but in reality, it’s a fake one.
WEB JACKING RISKS
Web jacking creates many losses to the real owner that it destroys the reputation of the real owner, his website, brand image, financial losses.
LEGISLATION RELATED TO WEB JACKING
There are following sections that will be used during the case of Web Jacking which are as follows-
- Sending defamatory messages by email - Sec 499 IPC
- Sending threatening messages by email - Sec 503 IPC
- Forgery of electronic records - Sec 463 IPC
- Bogus websites, cyber frauds - Sec 420 IPC
- Email spoofing - Sec 463 IPC
- Web-Jacking - Sec. 383 IPC
- E-Mail Abuse - Sec.500 IPC
Mainly section 383 deals with Extortion which also includes about Web Jacking:
Whoever intentionally puts any person in fear of any injury to that person, or to any other, and thereby dishonestly induces the person so put in fear to deliver to any person any property or valuable security, or anything signed or sealed which may be converted into a valuable security, commits “extortion”.
CASE RELATED TO WEB JACKING
In a recent incident reported in the USA the owner of a hobby website for children received an e-mail informing her that a group of hackers had gained control over her website. They demanded a ransom of 1 million dollars from her. The owner, a schoolteacher, did not take the threat seriously. She felt that it was just a scare tactic and ignored the e-mail. It was three days later that she came to know, following many telephone calls from all over the country, that the hackers had web jacked her website. Subsequently, they had altered a portion of the website which was entitled ‘How to have fun with goldfish’. In all the places where it had been mentioned, they had replaced the word ‘goldfish’ with the word ‘piranhas’. Piranhas are tiny but extremely dangerous flesh-eating fish. Many children had visited the popular website and had believed what the contents of the website suggested. These unfortunate children followed the instructions, tried to play with piranhas, which they bought from pet shops, and were very seriously injured!
HOW TO BE SAFE FROM WEB JACKING METHOD
- Don’t enter sensitive data in any link sent to you.
- Check the URL.
- If the address seem so that it is true that doesn’t means that it is.
- Read company name carefully and identify it is right or wrong.
- Check it carefully that there is https protocol or http protocol and then if you find that there is http protocol then don’t fill your data.
- If you are not sure site is real or fake enter a wrong name and user and password.
- Use a browser with anti-phasing detection.
- It’s advisable to install No script addon if you’re using Firefox. They provide protection against frame-based attack, by preventing scripts from loading.
- Frame burst is a method implemented by developers using JavaScript to restrict frame usage.
The purpose [vi] of this Web Jacking is to destroy someone reputation or it can also be done to take ransom from the real owner. It is a quite interesting technique that tries to trick the user that the web page is real but in reality, it’s a fake web page and then by clicking on it by the victim they access all the information of the victim.
News Updates

Allow Cookies!
By using our website, you agree to the use of cookies
Lawyers Network
Cities Serving
Law Schools Network
Law Students Network
THE 2024 STATE OF PHISHING REPORT IS PUBLISHED! READ THE REPORT HERE

Read the company overview to learn more about how Perception Point provides unparalleled prevention of advanced cyber threats across all attack vectors.
- Advanced Email Security
- Internal Emails
- Outbound Email Security
- Security Awareness Training

Download this complimentary Gartner report .
- Risky Access
- Sensitive Access

Download the Advanced Browser Security solution paper .
- Cloud Collaboration Apps
- Business Communication
- Cloud Storage

Read the brochure to learn more about Advanced Cloud Collaboration Security.

Check out the solution paper on Advanced Threat Protection for Web Apps.
- Microsoft 365
- Google Workspace

Read this case study to see how we helped a high-tech enterprise secure 3 collaboration channels: MS Teams, OneDrive, and SharePoint.
- Phishing Prevention
- Quishing Prevention
- BEC Prevention
- Account Takeover Prevention
- Malware Detection
- Zero-days & N-days Detection

Read the company overview to learn more about how Perception point provides unparalleled prevention of all attacks across email, web browsers and cloud collaboration apps.
- AI Threat Prevention
- HAP – Next-Gen Sandbox
- Anti-Evasion Technology

- Incident Response
- End User Reporting
- More Services

Learn more about Perception Point’s Managed Service .
- Channel Partners
- MSP/MSSP Partners
- SentinelOne
- Crowdstrike

Learn more about the Perception Point Partner Program . Protect your customers from all threats across top attack vectors with one platform.
- Browser Security
- Cloud Storage Security
- Cybersecurity
- Email Security
- Endpoint Security

Keep up with Perception Point’s updates and new offerings on our blog, here .

Learn how Red Bull augmented Microsoft EOP to prevent attacks in the case study, here .

Access the datasheet to learn about the use cases, technical specifications, and the key features of our Security Browser Extension

Download this whitepaper to learn how today’s digital-first enterprises can protect themselves against advanced threats.

Download the 2023 Gartner Market Guide for Email Security .

Check out our webinar in cooperation with Forrester — “Rethinking Email Security: Why Traditional Approaches Fail and Why You Can’t Afford to Ignore it”

Download this ebook to get a thorough overview of the most current email security challenges and how to mitigate them through best practices.

Reach this brochure to learn how Advanced Email Security combines cutting edge threat prevention with the speed, scale and flexibility of the cloud.

Use this calculator to assess the potential benefit of deploying Perception Point with just 3 variables. We will do the rest for you.

Are you managing a remote team? Download this IT Checklist to make sure you’re organization is secure.
Read the company overview to learn how Perception Point provides unparalleled prevention of all attacks across email, web browsers and cloud collaboration apps.
- Book a Demo
Perception Point » Guides » What Is Clickjacking? How Does It Work?
What Is Clickjacking? How Does It Work?

Clickjacking is a serious threat to web security that can compromise user privacy, data integrity, and system functionality. The term “clickjacking” was coined by security researchers Robert Hansen and Jeremiah Grossman in 2008, but the technique has been known since at least 2002.
Clickjacking is also known as UI redress attack or UI redressing, because it involves manipulating the user interface (UI) of a web page to trick users into performing actions they did not intend to.

Clickjacking can have serious consequences for both users and web applications. For example, it can be used to:
– Steal user credentials or sensitive information
– Download malware or unwanted software
– Transfer money or purchase products online
– Like or share content on social media platforms
– Change user settings or preferences
– Grant access to device features such as camera or microphone
Clickjacking is a serious threat to web security that can compromise user privacy, data integrity, and system functionality. The term “clickjacking” was coined by security researchers Robert Hansen and Jeremiah Grossman in 2008, but the technique has been known since at least 2002. Clickjacking is also known as UI redress attack or UI redressing, because it involves manipulating the user interface (UI) of a web page to trick users into performing actions they did not intend to.
Clickjacking is an attack that tricks a user into clicking on a webpage element which is invisible or disguised as another element. This can cause users to unwittingly perform actions on another web page or application, most likely owned by another domain or attacker.
There are many variations of clickjacking attacks that target different aspects of user interaction and web functionality. Here are some common types: – Likejacking – Cursorjacking – Download hijacking – Form hijacking
In this article, we will explore how clickjacking works, what types of attacks are possible, some real-world examples of clickjacking incidents, and how to prevent or mitigate clickjacking attacks.
This is part of a series of articles about Cybersecurity .
In this article
How Does Clickjacking Work?
Clickjacking exploits the fact that web browsers allow web pages to be embedded inside other web pages using HTML elements such as <iframe>, <frame>, <object>, <embed>, etc. These elements can display content from different sources within the same browser window.
However, if an attacker can control the content of one of these elements (e.g., by hosting it on their own server), they can overlay it on top of another web page (e.g., by using CSS properties such as position , opacity , z-index , etc.), making it invisible or partially visible to the user.
The attacker can then align the clickable elements of their embedded page (e.g., buttons, links, forms, etc.) with the visible elements of the underlying page (e.g., images, text boxes , headlines , etc.), creating a false impression for the user.
When the user interacts with the visible elements of the underlying page (e.g., by clicking on them), they are actually interacting with the invisible elements of the embedded page. Thus, the attacker hijacks their clicks and redirects them to perform actions on their behalf.
Types of Clickjacking
There are many variations of clickjacking attacks that target different aspects of user interaction and web functionality. Here are some common types:
– Likejacking : This type of attack manipulates the Facebook “Like” button to make users like pages or posts they did not intend to like. For example, an attacker could create a fake video player with an invisible “Like” button over the play button. When users try to play the video, they actually like the attacker’s page or post.
– Cursorjacking : This type of attack changes the position of the cursor for what the user perceives to another position. For example, an attacker could use Flash or JavaScript to move the cursor image away from its actual location and make it appear somewhere else on the screen. When users try to click on something with their mouse pointer (which is actually not where they think it is), they end up clicking on something else controlled by the attacker.
– Download hijacking : This type of attack tricks users into downloading malicious files by disguising them as legitimate ones. For example, an attacker could create a fake download link with an invisible iframe that loads another website with a real download link over it. When users try to download something from the fake link (which looks like it belongs to a trusted source), they actually download something from the other website (which could be malware).
– Form hijacking : This type of attack steals user input data by overlaying an invisible form over another visible form. For example, an attacker could create a fake login form with an invisible iframe that loads another website’s login form over it. When users try to log in using
The fake form (which looks like it belongs to their intended website), they actually send their credentials to the other website (which could be phishing).
A Real-World Case Study
In December 2022, a clickjacking scam was discovered by researchers . It was an advertising fraud scheme that utilized Google Ads and “pop-unders” on adult websites that generated millions of ad impressions on stolen content. The campaign was reported by Malwarebytes and the scam raked in an estimated $275,000 per month for the perpetrators.
How did it work?
- The scammer created fake blogs and news portals with scraped content from other websites and used them as pop-under advertisements.
- Instead of displaying the content of the fake page, they overlaid an iframe promoting an adult site.
- To collect revenue from these pop-unders, the perpetrators used a Google Ad scheme.
- A click anywhere on the iframe page triggers a real click on a Google Ad embedded in the fake news page.
How to Prevent Clickjacking Scams with Perception Point
To prevent clickjacking attacks, there are several methods that can be applied at both the server side, the app side, and the browser side.
At the server side, one of the most effective methods is to send proper Content Security Policy (CSP) frame-ancestors directive response headers that instruct the browser to not allow framing from other domains.
Alternatively, older browsers can use X-Frame-Options HTTP headers for graceful degradation. Another server-side method is to set authentication cookies with SameSite=Strict (or Lax) attribute, unless they explicitly need None (which is rare).
At the app frontend side, developers can employ defensive code in the UI to ensure that the current frame is the most top level window. This can be done by using JavaScript code that checks if window.top === window.self and redirects or alerts the user if not.
At the browser side, one of the best methods is to use browser add-ons that can detect and prevent clickjacking attempts – ensuring users don’t click on invisible or “redressed” web page elements.
Perception Point Advanced Browser Security adds enterprise-grade security to standard browsers like Chrome, Edge, and Safari. The solution fuses advanced threat detection with browser-level governance and DLP controls providing organizations of all sizes with unprecedented ability to detect, prevent and remediate web threats including sophisticated phishing attacks, ransomware, exploits, Zero-Days, and more.
By transforming the organizational browser into a protected work environment, the access to sensitive corporate infrastructure and SaaS applications is secure from data loss and insider threats. The solution is seamlessly deployed on the endpoints via a browser extension and is managed centrally from a cloud-based console. There is no need to tunnel/proxy traffic through Perception Point.
An all-included managed Incident Response service is available for all customers 24/7. Perception Point’s team of cybersecurity experts will manage incidents, provide analysis and reporting, and optimize detection on-the-fly. The service drastically minimizes the need for internal IT or SOC team resources, reducing the time required to react and mitigate web-borne attacks by up to 75%.
Customers deploying the solution will experience fewer breaches, while providing their users with a better experience as they have the freedom to browse the web, use SaaS applications that they require, and access privileged corporate data, confidently, securely, and without added latency.
Contact us for a demo of the Advanced Browser Security solution.

Rate this article
Average rating 5 / 5. Ratings: 2
Be the first to rate this post.
- Cybersecurity in 2024: Threats, Technologies, and Best Practices
- Workspace Security: Challenges, Threats, and Security Solutions
- Understanding Shadow IT: Risks, Benefits, and Effective Management
- Domain Spoofing: How Does It Work?
- What Is Malvertising? How to Prevent Malvertising Attacks
- APT Security: Understanding, Detecting, and Mitigating the Threat
- Advanced Persistent Threats: Warning Signs and 6 Prevention Tips
PMB 98147 6 Liberty Sq Boston, MA 02109 +1 (857) 278 4184
3 Rothschild St, Floor 6 Tel Aviv, Israel 6688106 +972 (3) 979 7011
- Privacy Policy
- Service Levels and Support Description
- Cybersecurity Glossary
© 2024 Perception Point Inc. All rights reserved.

To revisit this article, visit My Profile, then View saved stories .
- Backchannel
- Newsletters
- WIRED Insider
- WIRED Consulting
Lily Hay Newman
Hack Brief: Hackers Enlisted Tesla's Public Cloud to Mine Cryptocurrency

Cryptojacking only really coalesced as a class of attack about six months ago, but already the approach has evolved and matured into a ubiquitous threat. Hacks that co-opt computing power for illicit cryptocurrency mining now target a diverse array of victims, from individual consumers to massive institutions— even industrial control systems . But the latest victim isn't some faceless internet denizen or a Starbucks in Buenos Aires. It's Tesla .
Researchers at the cloud monitoring and defense firm RedLock published findings on Tuesday that some of Tesla's Amazon Web Services cloud infrastructure was running mining malware in a far-reaching and well-hidden cryptojacking campaign. The researchers disclosed the infection to Tesla last month, and the company quickly moved to decontaminate and lock down its cloud platform within a day. The carmaker's initial investigation indicates that data exposure was minimal, but the incident underscores the ways in which cryptojacking can pose a broad security threat—in addition to racking up a huge electric bill.
RedLock discovered the intrusion while scanning the public internet for misconfigured and unsecured cloud servers, a practice that more and more defenders depend on as exposures from database misconfigurations skyrocket.
"We got alerted that this is an open server and when we investigated it further that’s when we saw that it was actually running a Kubernetes, which was doing cryptomining," says Gaurav Kumar, chief technology officer of RedLock, referring to the popular open-source administrative console for cloud application management. "And then we found that, oh, it actually belongs to Tesla." You know, casual.
The attackers had apparently discovered that this particular Kubernetes console—an administrative portal for cloud application management—wasn't password protected and could therefore be accessed by anyone. From there they would have found, as the RedLock researchers did, that one of the console's "pods," or storage containers, included login credentials for a broader Tesla Amazon Web Services cloud environment. This allowed them to burrow deeper, deploying scripts to establish their cryptojacking operation, which was built on the popular Stratum bitcoin mining protocol.
RedLock says it's difficult to gauge exactly how much mining the attackers accomplished before being discovered. But they note that enterprise networks, and particularly public cloud platforms, are increasingly popular targets for cryptojackers, because they offer a huge amount of processing power in an environment where attackers can mine under the radar since CPU and electricity use is already expected to be relatively high. By riding on a corporate account as large as Tesla's, the attackers could have mined indefinitely without a noticeable impact.
From a consumer perspective, Tesla's compromised cloud platform also contained an S3 bucket that seemed to house sensitive proprietary data, like vehicle and mapping information and other instrument telemetry. The researchers say that they didn't investigate what information could have been exposed to the attackers, as part of their commitment to ethical hacking.
A Tesla spokesperson said in a statement that the risk was minimal: “We addressed this vulnerability within hours of learning about it. The impact seems to be limited to internally-used engineering test cars only, and our initial investigation found no indication that customer privacy or vehicle safety or security was compromised in any way.”
Still, data about test cars alone could be extremely valuable coming from a company like Tesla, which works on next-generation products like driverless automation.

Lauren Goode

Karen Williams
William Turton
The RedLock researchers submitted their findings through Tesla's bug bounty program. Elon Musk's company awarded them more than $3,000 for the discovery, which RedLock donated to charity.
This incident itself is just one example in an ever-growing list of high-profile cryptojacking compromises. Just last week, researchers from the security firm Check Point said that attackers made more than $3 million by mining Monero on the servers of the popular web development application Jenkins. The Tesla infection is particularly noteworthy, though, because it shows not only the brazenness of cryptojackers, but also how their attacks have become more subtle and sophisticated.
RedLock's Kumar notes that the Tesla attackers were running their own mining server, making it less likely that it would land on malware-scanner black lists. The mining malware also communicated with the attacker's server on an unusual IP port, making it less likely that a port scanner would detect it as malicious. And the obfuscation techniques didn't stop there. The attack communications all happened over SSL web encryption to hide their content from security-monitoring tools, and the mining server also used a proxy server as an intermediary to mask it and make it less traceable.
RedLock says the attackers obtained free proxying services and the SSL certificate from the internet infrastructure firm Cloudflare, which offers these free services to make web security and privacy tools accessible to anyone, but grapples with the ways they can be abused by bad actors.
The good news about attackers investing time and energy to conceal their operations is that it means that first-line defensive efforts are working. But it also means that the payoff for executing the hacks makes it worth deploying those advanced maneuvers. Within months, cryptojacking has decidedly reached this phase. "The big thing to note here is the fact that public cloud is quickly becoming a target, specifically because it’s an easy target," says RedLock vice president Upa Campbell. "The benefit of the cloud is agility, but the downside is that the chance of user error is higher. Organizations are really struggling."
- We've come a long way since the early days of cryptojacking , way back in the heady days of 2017
- As bad as the Tesla incident was, cryptojacking attacks on critical infrastructure are an even bigger cause for alarm
- Tesla probably already had enough of a headache trying to ramp up its Model 3 production

Andrew Couts

Andy Greenberg

Dan Goodin, Ars Technica

Matt Burgess

Kate O'Flaherty

Dell Cameron
- +91 9810155766
- [email protected]
- B-10, Sector 40, NOIDA (India)
- Online Query
KarnikaSeth.com
What is web-jacking.
This term is derived from the term hi jacking. In these kinds of offences the hacker gains access and control over the web site of another. He may even change the information on the site. This may be done for fulfilling political objectives or for money. E.g. recently the site of MIT (Ministry of Information Technology) was hacked by the Pakistani hackers and some obscene matter was placed therein. Further the site of Bombay crime branch was also web jacked. Another case of web jacking is that of the ‘gold fish’ case. In this case the site was hacked and the information pertaining to gold fish was changed.

We apologize for the inconvenience...
To ensure we keep this website safe, please can you confirm you are a human by ticking the box below.
If you are unable to complete the above request please contact us using the below link, providing a screenshot of your experience.
https://ioppublishing.org/contacts/
- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
- What is Digital Privacy & Online Safety?
- Prefetch Files in Windows
- What is Amazon Alexa?
- Working with E-Commerce & BITNET
- What are the Security Risks of USB drives?
- Cross Domain Referrer Header Leakage
- Introduction To Classic Security Models
- How to Password Protect an Excel File
- XML External Entity (XXE) and Billion Laughs attack
- EDRM - Electronic Discovery Reference Model
- GraphQL - Attacks and Security
- What is Bluejacking?
- White Collar Crimes - Cyber Security
- Futuristic Solution to Privacy and Security in online social media
- Write Blockers- An Introduction
- Raspberry-Pi a computer for Geeks
- How to Connect Between Devices Via Network Wire on Cisco Packet Tracer(Virtual Program)?
- Validating and Testing Forensics Software
- Biometric System Architecture
What is Juice Jacking?
A security vulnerability in which an infected USB charging station is used to compromise linked devices is known as juice jacking . The flaw takes advantage of the fact that a mobile device’s power is delivered over the same USB cable that is used to transfer data. But people are probably unaware of this that when they are also charging it from the charging port, at the same time it also copies the data from the phone or installs malware. This technique of data theft is called a “ juice jacking ” fraud.
Through this, data is copied from smartphones, tablets, or computer devices in such a way that it is not even noticed. People frequently charge their devices through charging ports located in areas such as cafes, metro stations, railway stations, and airports. But this method of charging can be harmful. Cybercrooks can use ‘Juice Jacking’ to not only transfer data from your phone but also to wipe your bank account. The number of cases of juice jacking fraud is steadily increasing.
How does Juice Jacking work ?
The USB port is frequently utilized as a data transfer medium. When users charge their devices with a USB cable, they may be able to transfer files across devices. For this hackers often use off-the-shelf hardware which is easily installed in the charging port of public charging board. It was created with the sole intention of breaching security and gaining access to information about linked devices. You are completely unaware that your data has been stolen using this method. The data includes all the files from the phone’s contact list, photo gallery to WhatsApp chat, etc.
What could be the harm?
SBI has issued a Twitter warning to the public about this dangerous smartphone malware. Before you connect your phone to a charging station, think carefully. Malware can enter your phone in a variety of ways. After then, hackers can export the data as well as steal the phone’s password. Not only this, but the Los Angeles County District Office of the US also issued a video warning about the USB charging scam. In the video, the Deputy District Attorney had said that a free charger can destroy your bank account.
Types of Juice Jacking Attacks
1. data theft.
Juice jacking can lead to data theft of connected devices. Hackers can search your phone for personally identifiable information i.e. personally identifiable information, account credentials, banking-related data, credit card data, etc. These hackers have the ability to copy all the information on their devices. Nowadays there are many such apps that clone all the data from your phone to another phone.
2. Malware installation
Once the connection is established, the malware is automatically installed on the connected device. Malware remains on the device until it is detected and removed by the users. There are several categories of malware that cybercriminals can install through juice jacking including adware, crypto miner, ransomware, spyware, or even Trojans.
3. Multi-device attack
A multi-device attack is a method of attacking multiple devices at the same time. A device charged by infected cables may infect additional cables and ports with the same malware as an unwitting carrier of the virus, in addition to hurting the device plugged into a corrupted charger.
An attack that renders you helpless. Some virus that is downloaded via a charging device might lock the user out of their gadget, giving the hacker complete control.
This can be avoided
- The best way to avoid juice jacking fraud is to avoid charging your device from the charging port available in public places. If the phone needs to be charged immediately, do not use the USB cable of the charging kiosk to make your charger happy electronically.
- When you are traveling, you can carry a power bank. This prevents the need to charge at public ports. Note that even high-security areas like airports aren’t always secure.
- Everywhere should be alert. Although hacked USB ports are less possible in high-security places, there’s no guarantee that airport charging kiosks haven’t been tampered with, as juice jacked chargers are common can be rapidly installed which is difficult to detect later.
- Most of the juice jacking fraud is done using phone cables. As a result, avoid purchasing low-cost cables, as they may prove to be costly in the future.
- Do not jailbreak your operating system, as it can make your device vulnerable. Avoid installing pirated software or media as there is a possibility of a virus coming from it.
Remember that antivirus can provide extra protection but it won’t be useful when it comes to juice jacking however if cybercriminals try to install malware then antivirus can block apps. So next time when you travel definitely take your power bank and charger with you.
Please Login to comment...
Similar reads.

- Information-Security
- Computer Subject
- 10 Best Slack Integrations to Enhance Your Team's Productivity
- 10 Best Zendesk Alternatives and Competitors
- 10 Best Trello Power-Ups for Maximizing Project Management
- Google Rolls Out Gemini In Android Studio For Coding Assistance
- 30 OOPs Interview Questions and Answers (2024)
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

IRJET- Case Study on Elevating Structures by Jacking Technology

2020, IRJET
This project study gives us an idea to adopt a particular method to uplift the structure based on workability, practicability, cost-effective, and time. In this process, the house is temporarily lifted to a certain height with the help of jacking technology and a new elevated foundation is constructed below. In case your house lies below the road level and sewage water routinely streams in, Demolition and then new construction is not the best option. With the present technology you can undoubtedly raise the level of your house without any structural damage. Now here's an opportunity to save money and live in a similar house which you are accustomed to living in. Being more explicit, houses that are set up in low-lying regions frequently face a major issue. This issue is endless during the rainy seasons when there is significant precipitation and a substantial inflow of water into the low-lying lands. As an outcome, there's an answer for this issue which is house lifting.
Related Papers
ASHISH H . MAKWANA
International Journal of Latest Technology in Engineering, Management & Applied Science -IJLTEMAS (www.ijltemas.in)
Demolition of a house needs a strict attention and supervision to carry out the demolition and hen new construction is done. The project study includes the process of house lifting and new construction of building. Estimation, drawings are prepared for both house lifting and new construction of building. Drawings are prepared in accordance with the site visited for the house lifting. From the drawings estimation of house lifting method and new construction are done, which gives the total cost of both methods.The project study will give us the idea to adopt a particular method on the basis of feasibility, economy in cost & time and practicability.
International Journal of GEOMATE
Juan Sebastián Echeverry Fernández
IOP Conference Series: Materials Science and Engineering
Krzysztof Gromysz
IRJET Journal , Jayesh Magar , Jayant Pachpohe
Lower base of a structure is a very supreme part as it links the main body superstructure to the earth. That lower base is known as Foundation. In this paper we are going to discuss about the types of foundations used in construction industry, there design and also which alternative materials we can utilize as foundation material which can make it more firm, durable and ecofriendly. When it comes to built a structure it is very crucial to construct a firm base which holds the superstructure in all climatic conditions without collapsing or decaying. It is very important to know which type of foundation is essential to use in a particular superstructure, which materials are more suitable, which designs should be used. If any inappropriate material is used for foundation of structure then high risk is involved of collapsing of the structure. Different types of foundation base are utilized in different types of structures, each one of them has a unique design and specific configuration which makes a particular structure more durable and firm. A different foundation type is used in bungalows and in high rise buildings. In short this study presents the foundation types, which type is used for which superstructure, which design is suitable and more precisely we will be discussing about how we can make the foundation base ecofriendly, cost efficient and more durable and strong to withstand the natural calamities.
IRJET Journal
Although the RCC structures are designed as per codes not always constructed properly using correct techniques and methods. As a result, the structures start showing signs of distress which requires repair and rehabilitation work. In this project, a case study of (G+7) multistoried building whose ground floor was damaged due to the flood of 2006 has been represented. The repair strategy was to assess the quality of structural members of the ground floor of the building with the help of Non-Destructive and Semi Destructive Tests such as Rebound Hammer, UPV and Concrete Core Test. All the flood-affected members were tested and proper treatment to each of them was applied such as anticorrosion coating, injection grouting, micro concreting and also jacketing of columns at ground level. Strict quality control in materials and workmanship was adopted. All the rehabilitation work was done to increase the durability and service life of the building. After the engagement of all the professionals and cooperation of the residents for rehabilitation work was carried out. Some of the recommendations and conclusion have also been given to prevent further damage and to increase the service life of the building.
The construction of a building involves various processes such as site selection, survey, soil testing, locating ground water table, excavation of soil, structural design, material availability, feasibility etc. There is different methodology used for building construction. According to infrastructural requirements and limited space constraints buildings with more basement floors are constructed now a days. Top-Down construction method can be adopted in such cases. Bottom-up method is the convectional construction method where substructure and superstructure floors are constructed sequentially from the bottom of substructure to the top of superstructure. Top-down construction method, is a method which builds the permanent structure member of basement along with the excavation from top to bottom and the substructure and superstructure can be constructed subsequently. In this case study all the construction process involved in the construction of a building is analyzed based on an ongoing bottom-up construction project and comparing its implementation (phase of work) and time of execution of the work in both Top-down construction method and bottom-up construction method using PRIMAVERA software.
The buildings are one of the biggest energy consumers. In India the construction methodology practiced is a conventional one. In the current construction methodology, the natural resources are being used at faster rate than estimated. Hence, it has become essential to think about a construction methodology of an ideal building to reduce the demand and consumption of natural resources. This concept will allow reducing the use of natural resources in the construction practices and pushing towards using renewable resources. This study is aimed at the use of construction methodology with ideal building as compared to conventional method. The main purpose of present study is about the various construction materials, technologies and techniques to minimize the use of natural resources and maximize the use of renewable resources such as solar panel, biogas plants etc. The use of eco-friendly construction materials such as green concrete, pervious concrete may prove very effective for greater energy efficiency and when green concrete used for road surfaces etc., helping to increase in infiltration causing the recharge of groundwater and thereby rise in water table.
Marylee MacDonald
RELATED PAPERS
Adil S. ZINEELABDIN
Renata Relja
Yosselyn Mamani
British Journal of Anaesthesia
Allan Doctor
Husnain Abid
Anuario De Estudios Atlanticos
Jesus Martinez
sadegh kalantari
Pedro Hubertus Vivas Aguero
Hydrology and Earth System Sciences Discussions
Meine van Noordwijk
Open Engineering
rana shabbar
George N. Triantaphyllou
RSC Advances
Yi-June Huang
Raymond Josephsson
Arch Med Interna
Jose Diego Pardo Villegas
Revista Clínica Española
ANDRES FELIPE AGUDELO GARCIA
Marek Swierczynski
Combustion and Flame
Per Petersson
Jurnal Sekretaris & Administrasi Bisnis (JSAB)
Anny Nurbasari Roekmana
Applied Radiation and Isotopes
JESUS BOLIVAR
sayeh omidvari
Giulio F Tarro
Psychology of Sport and Exercise
Yvonne Forsell
Afrooz Ravanfar
Publications of the Astronomical Society of the Pacific
Rudolf Albrecht
tyghfg hjgfdfd
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

IMAGES
VIDEO
COMMENTS
Step-1: So to apply web jacking attack method we will use a tool in kali linux called setoolkit. Step-2: Open your kali linux operating system, and then open Terminal window. Step-3: Type setoolkit on the terminal. Step-4: It will display lots of attacking method but you have to select Social-engineering attack.
Following are the steps generally followed by attackers in Web Jacking. a) Compromising the Domain Name System (DNS): Firstly, the hacker creates a fake web page using the same domain name as the targeted web application. b) Hosting: The second step is to host it on your computer or shared hosting.
one scenario, the often-assumed web-surfing-anonymity can be compromised. In another, a user's private data and emails can be stolen. Lastly, an attacker can spy on a user through her webcam. We have conducted the first click-jacking effectiveness study through Amazon Mechanical Turk and find that the aforementioned attacks have suc-
Clickjacking is a newly discovered breach in network security. It is based on the functionality of web-designing in which two or more web frames are overlapped over each other. The analysis shows that there is a need for in-depth study on click-jacking attacks (client-side vulnerability) and preventive measures so that early prevention and detection of such kinds of attacks can be implemented ...
1 Introduction. A clickjacking attack is an attack against users of the web application in which an attacker creates a malicious page. The infected web application is designed in such a way that it tricks a user into clicking on a page element. This click targets an action against victim page that is hidden from the.
Web security has become a major area of concern as most of the users go online to get their needs fullled. Web security involves various attacks like Cross-Site Scripting (CSS) phishing, Click-jacking, SQL injection, and many more. Click-jacking is one of them and has emerged nowadays. Click-jacking has made browsing on the Internet
Step 1: To use the web jacking attack method, we will use a tool in kali Linux called setoolkit. Step 2: Open your kali Linux system, then open the Terminal window. Step 3: Type a deadly setoolkit. Step 4: It will show many ways to attack, but you will have to choose a Social-engineering attack.
Case studies make or break research, and Cache Poisoning at Scale has them in droves. Youstin proves web cache poisoning is still endemic, and still widely overlooked. DoS vulnerabilities are often spurned by researchers, but the persistent, single-request takedowns offered by web cache poisoning are clearly taken seriously by many companies.
jacking and its damage, infrastructure, and evasion techniques. Our work complements past measurement studies on malicious web pages [37], and provides useful recommendations to browser-based security enhancements [6]. Contributions. In summary, we make the following contributions in this paper: •We design and implement a detector, named ...
Clickjacking. Clickjacking, also known as a "UI redress attack", is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. Thus, the attacker is "hijacking" clicks meant for their page and routing them to ...
CASE RELATED TO WEB JACKING. In a recent incident reported in the USA the owner of a hobby website for children received an e-mail informing her that a group of hackers had gained control over her website. They demanded a ransom of 1 million dollars from her. The owner, a schoolteacher, did not take the threat seriously.
Cryptojacking is officially the scourge of the internet. Cybersecurity can feel like a chaotic free-for-all sometimes, but it's not every day that a whole new conceptual type of attack crops up ...
Clickjacking is an attack that tricks a user into clicking on a webpage element which is invisible or disguised as another element. This can cause users to unwittingly perform actions on another web page or application, most likely owned by another domain or attacker. Clickjacking exploits the fact that web browsers allow web pages to be ...
For a reliable and convenient system, it is essential to build a secure system that will be protected from outer attacks and also serve the purpose of keeping the inner data safe from intruders. A juice jacking is a popular and spreading cyber-attack that allows intruders to get inside the system through the web and theive potential data from the system. For peripheral communications ...
Click-jacking protection on the modern Web is commonly enforced via client-side security mechanisms for framing control, like the X-Frame-Options header (XFO) and Content Security Policy (CSP ...
It's Tesla. Researchers at the cloud monitoring and defense firm RedLock published findings on Tuesday that some of Tesla's Amazon Web Services cloud infrastructure was running mining malware in a ...
A Case Study on Clickjacking Attack and Location Leakage. L. Nei, Loo Yow Cherng, M. Singh. Published 2014. Computer Science. TLDR. In this research, a review on the type of social media ad what are the current threat in social media is provided, and a solution for each as well as the evaluation of the solution is proposed. Expand.
What is web-jacking? This term is derived from the term hi jacking. In these kinds of offences the hacker gains access and control over the web site of another. He may even change the information on the site. This may be done for fulfilling political objectives or for money. E.g. recently the site of MIT (Ministry of Information Technology) was ...
This study investigates the influencing factors affecting jacking loads during slurry pipe-jacking works at four drives in the Shulin district sewer network in Taipei County, Taiwan, with lengths between 73 and 126 m. The main factors affecting jacking loads during tunnelling may include: (a) overcut annulus and volume of injected lubricant; (b) work stoppages; (c) geology; and (d) misalignment.
The statistic in year 2018 shown that the range of age below 20 - 20's had spent their time average duration within 6 - 8 hours daily in using internet [33]. This paper therefore imperative to see the awareness of cyber defamation and the main Social Networking Sites (SNSs) among adolescent. 2. Purpose of the Study.
A security vulnerability in which an infected USB charging station is used to compromise linked devices is known as juice jacking. The flaw takes advantage of the fact that a mobile device's power is delivered over the same USB cable that is used to transfer data. But people are probably unaware of this that when they are also charging it ...
Abstract - This project study gives us an idea to adopt a particular method to uplift the structure based on workability, practicability, cost-effective, and time. In this process, the house is temporarily lifted to a certain height with the help of jacking technology and a new elevated foundation is constructed below.
@article{Yu2023AJF, title={A Jacking Force Study Based on Interpretation of Box Jacking Records: A Case Study of Curved Rectangular Box Jacking in Soft Soil in Saitama, Japan}, author={Bosong Yu and Hideki Shimada and Takashi Sasaoka and Akihiro Hamanaka and Fumikiho Matsumoto and Tomo Morita}, journal={SSRN Electronic Journal}, year={2023 ...