Topics in Computer and Network Security
Stanford cs 356, fall 2023.
CS 356 is graduate course that covers foundational work and current topics in computer and network security. The course consists of reading and discussing published research papers, presenting recent security work, and completing an original research project.

Course Information
Discussion: Mon/Wed 3:00–4:20 PM. Gates B12 . This course is largely based on in-person discussion rather than lecture. Attendance and participation is expected.
Instructor: Zakir Durumeric Office Hours: M/W 4:30–5:00 PM, or by appointment.
Course Assistant: Kimberly Ruth . Office hours by appointment.
Prerequisites: CS 356 is open to all graduate students as well as advanced undergraduate students. While the course has no official prerequisites, it requires a mature understanding of software systems and networks. Students are expected to have taken CS 155: Computer and Network Security or equivalent.
Topics and Readings
The tentative schedule and required readings for the class are below:
9/27 Introduction
Against security nihilism.
Blog Post. 2016. Chris Palmer.
Mining Your Ps and Qs: Detection of Widespread Weak Keys...
SEC '12 . N. Heninger, Z. Durumeric, E. Wustrow, J.A. Halderman.
How to Read a Paper
10/2 web privacy and security, the web never forgets: persistent tracking mechanisms in the....
CCS '14 . Gunes Acar, Christian Eubank, Steven Englehardt, Marc Juarez, Arvind Narayanan, Claudia Diaz.
Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice
CCS '15 . D. Adrian, K. Bhargavan, Z. Durumeric, P. Gaudry, M. Green, J.A. Halderman, N. Heninger, A. Springall, E. Thomé, L. Valenta, B. VanderSloot, E. Wustrow, S. Zanella-Beguelin, P. Zimmermann.
10/4 Usability
Alice in warningland: a large-scale field study of browser security.
SEC '13 . Devdatta Akhawe, Adrienne Porter Felt.
...no one can hack my mind”: Comparing Expert and Non-Expert Security Practices
SOUPS '15 . Iulia Ion, Rob Reeder, Sunny Consolvo.
10/9 Authentication and Phishing
The tangled web of password reuse.
NDSS '14 . Anupam Das, Joseph Bonneau, Matthew Caesar, Nikita Borisov, XiaoFeng Wang.
Detecting credential spearphishing in enterprise settings
SEC '17 . Grant Ho, Aashish Sharma, Mobin Javed, Vern Paxson, David Wagner.
10/11 Denial of Service
Inferring internet denial-of-service activity.
SEC '01 . David Moore, Geoffrey Voelker, Stefan Savage.
Understanding the Mirai Botnet
10/16 spam and ecrime, framing dependencies introduced by underground commoditization.
WEIS '15 . Kurt Thomas, Danny Huang, David Wang, Elie Bursztein, Chris Grier, Thomas Holt, Christopher Kruegel, Damon McCoy, Stefan Savage, Giovanni Vigna.
Spamalytics: An Empirical Analysis of Spam Marketing Conversion
CCS '08 . Chris Kanich, Christian Kreibich, Kirill Levchenko, Brandon Enright, Geoffrey Voelker, Vern Paxson, and Stefan Savage.
10/18 Software Attacks
Hacking blind s&p '14 . andrea bittau, adam belay, ali mashtizadeh, david mazieres, dan boneh. sok: eternal war in memory.
S&P '13 . Laszlo Szekeres, Mathias Payer, Tao Wei, Dawn Song.
10/23 Software Defenses
Native client: a sandbox for portable, untrusted x86 native code.
S&P '09 . Bennet Yee, David Sehr, Gregory Dardyk, J. Bradley Chen, Robert Muth, Tavis Ormandy, Shiki Okasaka, Neha Narula, Nicholas Fullagar.
Multiprogramming a 64 kB Computer Safely and Efficiently
SOSP '17 . Amit Levy, Bradford Campbell, Branden Ghena, Daniel B. Giffin, Pat Pannuto, Prabal Dutta, Philip Levis.
10/25 Malware and Supply Chain
Towards measuring supply chain attacks on package managers for interpreted languages.
NDSS '21 . Ruian Duan, Omar Alrawi, Ranjita Pai Kasturi, Ryan Elder, Brendan Saltaformaggio, Wenke Lee.
Before We Knew It: An Empirical Study of Zero-Day Attacks In The Real World
CCS '12 Leyla Bilge and Tudor Dumitraş.
10/30 Side Channels and Information Leakage
Timing analysis of keystrokes and timing attacks on ssh.
SEC '01 . Dawn Song, David Wagner, Xuqing Tia.
Spectre Attacks: Exploiting Speculative Execution
S&P '19 . P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Hamburg, M. Lipp, S. Mangard, T. Prescher, M. Schwarz, Y. Yarom.
11/1 Hardware
Stealthy dopant-level hardware trojans.
CHES '13 . Georg Becker, Francesco Regazzoni, Christof Paar, Wayne Burleson.
Comprehensive Experimental Analyses of Automotive Attack Surfaces
SEC '11 . Stephen Checkoway, Damon McCoy, Brian Kantor, Danny Anderson, Hovav Shacham, Stefan Savage.
W32.Stuxnet Dossier
Symantec Technical Report . Nicolas Falliere, Liam Murchu, Eric Chien.
11/8 Machine Learning
Towards evaluating the robustness of neural networks.
S&P '16 . Nicholas Carlini and David Wagner.
Outside the Closed World: On Using Machine Learning For Network Intrusion Detection
S&P '10 . Robin Sommer and Vern Paxson.
11/13 Vulnerable Populations / Security For Everyone
A stalker’s paradise: how intimate partner abusers exploit technology.
CHI '18 Diana Freed, Jackeline Palmer, Diana Minchala, Karen Levy, Thomas Ristenpart, Nicola Dell.
A11y Attacks: Exploiting Accessibility in Operating Systems
CCS '14 Yeongjin Jang, Chengyu Song, Simon Chung, Tielei Wang, Wenke Lee.
11/15 Privacy and Dark Patterns
Robust de-anonymization of large sparse datasets.
S&P '08 . Arvind Narayanan and Vitaly Shmatikov.
Dark patterns at scale: Findings from a crawl of 11K shopping websites
S&P '08 . Arunesh Mathur, Gunes Acar, Michael Friedman, Eli Lucherini, Jonathon Mayer, Marshini Chetty, Arvind Narayanan.
11/20 Thanksgiving Break
11/22 thanksgiving break, 11/27 surveillance and anonymity, keys under doormats.
MIT Technical Report '15. H. Abelson, R. Anderson, S. Bellovin, J. Benaloh, M. Blaze, W. Diffie, J. Gilmore, M. Green, S. Landau, P. Neumann, R. Rivest, J. Schiller, B. Schneier, M. Specter, D. Weitzner.
Tor: The Second-Generation Onion Router
SEC '04 . Roger Dingledine, Nick Mathewson, Paul Syverson.
11/29 Government Attacks and Disinformation
When governments hack opponents: a look at actors and technology.
SEC '14 . Bill Marczak, John Scott-Railton, Morgan Marquis-Boire, Vern Paxson.
Disinformation as Collaborative Work: Surfacing the Participatory Nature of Strategic Information Operations
CSCW '19 . Kate Starbird, Ahmer Arif, Tom Wilson.
12/4 Ethics and Problem Selection
The moral character of cryptographic work.
Phillip Rogaway.
Science, Security, and the Elusive Goal of Security as a Scientific Pursuit
S&P '17 . Cormac Herley and P.C. van Oorschot.
12/6 Final Presentations
No required reading. attendance mandatory., course structure.
This course is composed of three parts: reading and discussing foundational papers in every class, reading and presenting recent work for one class, and completing a group research project. Grading will be based on:
Readings and Discussion (30%)
We will read and discuss 1–2 papers for each class. Typically, these are formative works in an area of security. Students should come prepared to actively discuss assigned papers and to make substantive intellectual contributions. This means that you need to thoroughly read each paper ahead of time. Before each section, students will submit a short (400 word) summary and reaction for each each paper, as well as a proposal of one discussion question for class.
Students should submit the reading assignments through Gradescope by 2:30 pm on the day of each class . Paper responses should be completed individually without the assistance of LLMs (e.g., ChatGPT).
Grading will be based 20% on these written responses and 10% on in-class participation. We do not allow any late days for paper reactions, but students may skip two paper summaries and two lectures without penalty. We will take class attendance. However, participation grades are based on not only attendence, but active participation during class discussion.
Do not underestimate the amount of time required to properly read and process a research paper. Expect to spend several hours preparing for each section.
Topic Presentation (15%)
While reading formative papers helps to demonstrate how a subfield started, it oftentimes leaves us wondering how the area has evolved. To fill this gap, each student in the class will present one recent paper during the quarter topically relevant to that day's class. At the start of the quarter, students will have the opportunity to sign up for the topic/date that they want to present their paper. Stuents will have 12-15 minutes to present their paper.
Students are expected to do a literature search and to select a paper that was published in the last three years from a top-tier venue in security (e.g., IEEE Security and Privacy, USENIX Security, ACM Computer or Communication Security) or adjacent field (e.g., CHI, NSDI, ASPLOS, PLDI, etc.). Students should submit their papers to approval to the teaching staff a week prior to their presentation.
Course Project (55%)
Students will complete a quarter-long original research project in small groups (1–3 students) on a topic of their own choosing. Groups will present their work during the last two sections as well as submit a 6–10 page report, similar to the papers we read in the course.
- Project Proposal (5%). Project groups will meet with course staff to discuss their project during the third week of class and submit a one page project proposal. Written proposals are due on 10/16.
- Mid-Quarter Progress Report (5%). Submit a short (1–2 pages) progress report part way through the quarter. The report should indicate what has been accomplished, what work is remaining, obstacles the team has encountered, and any preliminary data or insights. Due 11/17.
- Class Presentation (10%). Each group will give a 10 minute class presentation during the last week of the course.
- Final Paper (35%). Groups will submit a final project report similar to the papers we read in the course. Papers should be 6–10 pages and use the USENIX LaTeX template . It may be helpful to read Writing Technical Articles if you haven't previously published any work in computer science. Due 12/8.
Students should submit all reports through Gradescope by 11:59PM on the day of each deadline.
In past offerings, well-executed projects have led to publications at top-tier security conferences and workshops. I'm happy to work with groups to publish their work.
This class has no final exam. Attendance on 12/6 is required.
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics for 2024
Home Blog Security 60+ Latest Cyber Security Research Topics for 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics /ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security research questions, cyber security topics for the project, best cyber security research topics, research titles about cyber security and web security research topics.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics for 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A) Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B) Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C) Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D) Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E) Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F) Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G) Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H) Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I) Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J) Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Network Security Projects
The term ‘ Network security ’ provides the security for the computer services such as software and hardware and the communication devices like network infrastructure, and basic communication protocols of the network. It desires to attain data security on the network in an organization or in between the user individuals. If you are looking to implement interesting network security projects reach our network team specialist to guide your research work.
“Network security is one of the most important cyber security branches. Comparing to the wired systems, the wireless network like Wi-Fi and internet-linked wireless networks or devices having the most probability for attacks.”
The network security particularly protects the data on the flow. Network security preserves a high level of demand in the cyber security field . As the users’ need for fast internet is considered to be one of the main reasons for network security threats and it has become very common. So network security projects are in the order of the day.
“This article mainly focuses on the Network Security concepts and tools that can be implanted by the Network Security models and to stimulate your interests on proposing Network security projects.”
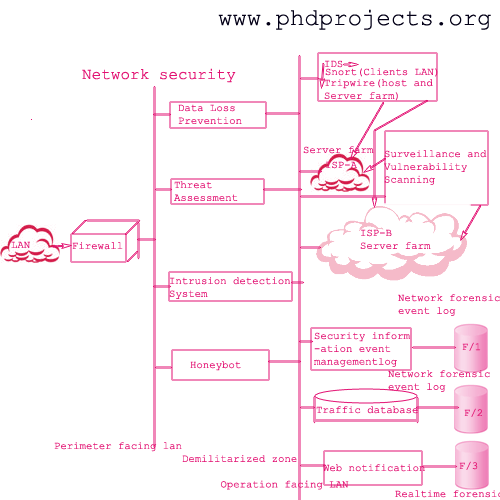
Let’s have a look at the process involved in Network Security that involves the following processes on detecting three leading and common attacks
Process of Network Security
- Detecting phishing threats and harmful URL
- Detecting application attacks
- Detecting spoofing, scanning, and other network intrusions
The network security can be applied into two major ways of endpoint security and use cases authentication of malware, ransomware, and spyware detection and it detects the brute force attacks and unauthorized access as follows
- Detecting affected devices and suspicious entry
- Analyses User activities
- Detecting spyware and ransomware
- Categories malware detection
Network security models are functioning based on detecting malicious software or viruses and patching the affected devices. In the technology world, network security threats are unavoidable and the impact of such threats may extend up to affecting the organization’s monetary assets . The preventing and mitigating actions may vary according to the attacking phases used by the adversary . The attacking steps of the attacker are listed below
List of Attacking Steps
- Tracks erasing
- Control & command
- Exfiltration of data
- Internal recon
- Access expansion
- Data collection
- External recon and
- Manipulation
To mitigate the above malicious attacks performed by an adversary over the network, building security models are one of the best ways to save the network from such threats . To construct an effective security model, you must keep in mind the following features of an effective model.
- Prevention or Mitigation Techniques : the model must prevent the attack’s influence over the business resources in an organization
- Analysis Techniques: the model must use the analysis mechanism of an attack used by the detection method
- Detection Techniques: to detect the anomaly and suspicious activity, and the model must have the current and past historical data.
- Location detection: the model must have the capacity to detect the perimeter and zone of the attacked location.
- Attack Features: the model should have the detecting features for attacks analysis
- Attack Methods: the model has to identify the method of attack per segment.
The security models are used to detect, identify, and counteract the attack by identifying the method of attack and its location for effective patching and it must be updated with new techniques to identify and react according to the level of the threat. Here are the four main network security concepts identified by our engineers that could be performed by the above-mentioned models.
Top 4 Network Security Concepts
- Managing Network Device : due to the displaying of many weak points in the firmware, network device management involves repairing such issues
- Network Monitoring: if any suspicious pattern is sent to manipulate the network, this process involves the action of observation and assessment
- Network Protocol Design : it is used to prevent the attacker from snorting your packet, by sending an encrypted network packet on network interface cards and network devices.
- Designing network security architecture: for in-depth network security measures, this obliging concept is used often.
The above four network security components are considered to be the best in the field of network security . There are other major concepts too, which are professionally used by many research sectors. Scholars who chose to pick the network security projects are set apart to have better scopes in the relevant field and here our research team has come up with the research issues as listed below.
Latest Network Security Projects Research Topics
- Network steganography
- Privacy-friendly communication services and architectures
- Interconnecting system security
- Network interoperability
- Fault-tolerant models
- Distributed computations security
- Techniques of distributed consent
- Security simulation and analysis of distributed systems
- Analyzing network attack propagation
- Mitigation techniques of network layer attacks
- Distributed computing security: protocols and frameworks
- Network security essentials
- Technical aspects, management, and procedures of a secured network
- Vertical Handover Simulation
- Security over distributed systems
- Principles and protocols of network security
- Technologies and algorithms of network security
The above mentioned issues are exposed to research in the field of network security. If you feel those issues would be taken by someone then you, here we help you to find the areas that attract you for research and we guide you by providing innovative network security project topics . Here is the list of major research areas.
- Volunteer Computing in Big Data
- Technical aspects, management, and procedures of a secured network
Latest Network Security Project Topics
- Designing MIMO telecommunication system
- Social media sharing based on blockchain trust
- Using ML and AI to detect fake news in social media
- The technology of new authentication and biometric for access control, identity management, and device authentication
- Cyber-physical-social spaced user privacy protection mainly on online social networks and mobile devices
- Techniques of Intrusion Tolerance in IoT
- Lightweight cryptography for energy efficiency and balance security
Along with our suggestion in the latest research topics in network security that are based on the contemporary mechanism to secure a network, our world-class research developers know to predict the future project trends in network security . As the network threats are on the rise by now, the above-given list is based on securing the network by identifying the threats . But the future network security will be based on the game theory; the evaluating functions of security database and the précised zero-knowledge concurrency.
Future trends in network Security
- Analyzing cryptographic protocols by using Game Theory
- Succeeding enhanced equilibria by Cryptographic protocols
- Analyzing symbolism and concurrency
- Secured theorems for analyzing symbolic security
- Encrypted data evaluating functions
- Recovering private data
- Zero-knowledge sets
- Database privacy definitions
- Zero-knowledge concurrency
- Flexible Cryptography
- Non-Black-box Simulation
- Accurate Zero knowledge
In this article, we mainly focus on network security and there are some measures for analyzing the quality features given by the network security model to provide the fundamental assurance over its capacities in the following.
What are the Quality Attributes for Network Security?
- Ensure privacy
- Interoperability
- Mitigation ability
- Adaptability
- Reliability
- QoS Parameters
- QoE Parameters
- Scalability
The quality based on the basic functions of the model includes the ability of its measure, availability, ease of access, adapting the new mechanisms , etc. they are the characteristic of the network security models . Here are the countermeasures to improve the quality of the models after or before every attack

- QoS Parameters and QoE
The quality based on the basic functions of the model includes the ability of its measure, availability, ease of access, adapting the new mechanisms , etc. they are the characteristic of the network security models . Here are the countermeasures to improve the quality of the models after or before every attack .
How do we secure the network against cyber-attacks?
- Correlation and matching attribution
- Detecting anomaly
- Clustering scenario
- Matching model
- Statistical inference
- Consequences and prerequisites
- Based on structure
- Mixed approaches
In addition to the above methods to secure the network from cyber-attacks the process of detection is the most important step both in identifying the attack and detecting the right counteractions . The IDS are called the Intrusion Detection of a model and its functions are various as we listed below
Detection methods
- Detection based on Flow (Grouping traffic, Deep Learning, Feature Engineering)
- Detection based on Packet (Parsing Packet, Payload analysis)
- Detection based on the session (Statistical, sequence Feature)
- Detection based on log (rule-based system combination, Feature engineering, Text analysis)
- Statistical model
- Machine learning
- Time series
- Machine of finite-state
- Expert system
- Matching the pattern
Before the detection of the attack, a model would function to collect the traffic, selecting the feature of its functions because a network model must have the capacity over its mentioned fundamental working process,
Working process of a network model
- Traffic collection
- Feature Selection
- SVM, ANN, NB, DT, USML
- Evolution Measures
A network security model must meet certain requirements for accurate and precision modeling.
- Advanced Persistent Threats (APT) detection
- Real-time responding
- Large data warehouses Management
- Unstructured Data Analytics
- A large amount of data recollection
The working process of a network model concentrates on its functions over data collection that depends on the various types and functions. While those functions are prone to attack, we could identify the effect of the threat through IDS with our existing data. When we run out of data on the system malfunctions, anomaly detection is used to identify the threats by its following approaches.
Detecting Network Anomaly
- Statistical Approaches
- The flow of statistical data
- Analyzing Wavelet
- Hidden Markov Model
- Analyzing Covariance matrix
- Bayesian networks
- Hybrid clustering
- Reinforcement learning
- Deep learning
As discussed above, the scope of network security projects is on the rise as the network security field has a lot of raising research problems like an attackers’ developed source code of malware . It keeps on developing day by day along with the security codes. To confirm your acceptance to work with us to get an exciting experience in the areas you felt boring. We are here to enrich the quality of your project at a low-cost service . We also introduce you to the various fields related to network security if you are willing to know
Why Work With Us ?
Senior research member, research experience, journal member, book publisher, research ethics, business ethics, valid references, explanations, paper publication, 9 big reasons to select us.
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.
Related Pages
Our benefits, throughout reference, confidential agreement, research no way resale, plagiarism-free, publication guarantee, customize support, fair revisions, business professionalism, domains & tools, we generally use, wireless communication (4g lte, and 5g), ad hoc networks (vanet, manet, etc.), wireless sensor networks, software defined networks, network security, internet of things (mqtt, coap), internet of vehicles, cloud computing, fog computing, edge computing, mobile computing, mobile cloud computing, ubiquitous computing, digital image processing, medical image processing, pattern analysis and machine intelligence, geoscience and remote sensing, big data analytics, data mining, power electronics, web of things, digital forensics, natural language processing, automation systems, artificial intelligence, mininet 2.1.0, matlab (r2018b/r2019a), matlab and simulink, apache hadoop, apache spark mlib, apache mahout, apache flink, apache storm, apache cassandra, pig and hive, rapid miner, support 24/7, call us @ any time, +91 9444829042, [email protected].
Questions ?
Click here to chat with us
NETWORK SECURITY RESEARCH TOPICS
Network security research topics is also one of most accepted area for Research dealing with many protocols. Importance and necessitate of network security makes it admirable area for research. Why is Network Security so important, this question revolve around every one of us. It has also a simple answer which lies in its name i.e. SECURITY. Due to its interdisciplinary nature, we can also develop many security protocols to avoid the current network security violation. To perform an outstanding research, we also need to review recent security violations and also explore related methods and also techniques for it.
We can also work on network forensic and analyze best technique and algorithm for it.
Internet, the word which changed the world depends on Network-security as it is prone to many security attacks, malicious activities, also misleading information and unintelligible communication. Hence, there is also a need for effective security solution which can also be taken as a challenge by young scholars and work on it. Network security research topics which are currently undergoing are cyber-insurance, cumulative Metric for an information network etc. Most commonly also used security mechanisms are Encipherment, Digital signature, also coding-decoding etc. But these are also fundamentals of Network security. It is also fast growing field which needs current update and latest algorithm also for enhance the research. For this, we have a wide collection of Network security research topics with its tool
RESEARCH ISSUES IN NETWORK-SECURITY:
RFID technologies Security in Ad hoc network Security also in telecommunication network Wireless security Collaborative network security Defining network security protocols Network security also in protection measures Network forensics Embedded also in network security IPV6 network security Malware detection etc.
SOFTWARE AND TOOL DETAILS ========================== 1)NeSSi(JAVA) 2)NST(C) 3)JAVASNOOP(JAVA) 4)EXata (C++) 5)NETwork Attacks (also in NETA-omnet++)
Purpose of the every software and tool =======================================.
NeSSi–> novel network simulation tool also used for security research and evaluation purposes due to its varied capability.
NST–> performs routine security, networking diagnostic and also monitoring tasks.
JAVASNOOP–> Security tool also used to test the security of Java applications.
EXata–> network emulator which also provides network security and cyber warfare features
ETwork Attacks (NETA)–>Framework also to simulate attack behaviors in heterogeneous networks using OMNeT++.
Related Search Terms
network security research issues, network security research topics, phd projects in network security, Research issues in network security
Top 161+ Computer Security Research Topics & Ideas – Amazing Guide!
Computer security is a very important field that changes quickly as technology advances. As cyber threats become smarter and the possible damage from security breaches more serious, there is an ongoing need for new research to develop strong defensive strategies and stay one step ahead of bad actors.
Whether you are a student studying cybersecurity, a researcher exploring new techniques, or a professional wanting to learn more, finding interesting computer security research topics can be challenging.
This guide lists over 161 thought-provoking computer security research ideas in different areas, such as network security, cryptography, malware analysis , data privacy , ethical hacking, and more.
Look through these topics to get inspiration for your next big research project or school paper that could potentially shape the future of digital security.
Importance of Choosing the Right Research Topic
Table of Contents
Picking the right topic for your research is super important in computer security. The topic you choose will decide the direction and how much impact your work could have.
A good topic needs to be relevant and interesting, and new solutions or ideas for current computer security issues need to be provided. Here are some key reasons why choosing the perfect topic really matters:
- It keeps you motivated and excited about the project. Working on something you truly find interesting makes the whole research process more enjoyable and productive.
- It makes sure your work tackles real-world problems that people, businesses, or society face. The best research helps solve serious cybersecurity challenges.
- It allows you to bring something totally new to the field. Avoid topics that are way too broad or have already been researched extensively.
- It decides how big or in-depth your research will be. The right topic gives you enough to explore without being too much for your time and resources.
- It affects your chances of getting your findings published or presented. Totally new, well-done research on important current topics is more likely to get accepted by journals, conferences, and computer security experts.
Taking the time upfront to really think about topics and choose the perfect one is so worth it. It sets you up for a meaningful, rewarding research experience.
Recommended Readings: “ Top 119+ Innovative Language Development Research Topics – Innovative Ideas “.
General Guidelines for Selecting Research Topics
Here are some guidelines for selecting research topics that will surely help you select the perfect topic for yourself; please take a look.
Understanding What’s Currently Popular
When picking a research topic, it’s important to look at what computer security areas are really hot and getting a lot of buzz right now. Look for new threats, new technologies, and popular topics that people are talking about. This helps make sure your research is relevant and tackles current issues. Check cybersecurity news sites, research articles, and conference topics to see what trends are happening.
Thinking About Your Interests and Skills
The best research topics are ones that really fascinate you and fit your skills/background. If you pick something you have no interest in, it will be hard to stay motivated. And if it’s too far from what you know, you may struggle. Think about areas of computer security that truly excite your curiosity. Also, consider what technical knowledge and experience you already have that could help.
Considering Real-World Applications
For your research to have maximum impact, it needs real-world uses. Look for topics that solve actual problems faced by individuals, companies, governments, etc., such as protecting systems, securing financial info, or defending against specific attack methods. Considering the potential real-world uses upfront leads to research that delivers concrete solutions rather than just ideas.
Top 161+ Computer Security Research Topics
Here is the list of the top 161+ computer security research topics provided according to different categories; let’s look.
Network Security
- Zero-day vulnerabilities and exploits in network protocols
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
- Network traffic analysis and anomaly detection
- Secure routing protocols for ad-hoc and sensor networks
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attack mitigation
- Wireless network security (e.g., Wi-Fi, Bluetooth, RFID)
- Next-generation firewall technologies
- Secure network design and architecture
- DNS security and DNSSEC implementation
- Threat intelligence sharing mechanisms and platforms
Cryptography
- Post-quantum cryptography algorithms and implementations
- Cryptanalysis of existing cryptographic schemes
- Homomorphic encryption for privacy-preserving computation
- Blockchain and cryptocurrency security
- Secure multiparty computation (MPC)
- Quantum key distribution (QKD) protocols
- Cryptographic protocols for secure communication (e.g., SSL/TLS)
- Side-channel attacks and countermeasures
- Cryptography in IoT devices and embedded systems
- Attribute-based encryption (ABE) for fine-grained access control
Software Security
- Static and dynamic analysis techniques for vulnerability detection
- Secure software development methodologies (e.g., DevSecOps)
- Code obfuscation and anti-reverse engineering techniques
- Secure coding practices and code review methodologies
- Vulnerability management and patching strategies
- Binary exploitation techniques and mitigations
- Software-defined security mechanisms
- Secure software updates and distribution mechanisms
- Software sandboxing and containerization for security
- Secure software testing methodologies (e.g., fuzzing, symbolic execution)
Web Security
- Web application security testing and assessment
- Cross-site scripting (XSS) and Cross-Site Request Forgery (CSRF) prevention
- SQL injection and other injection attack mitigation
- Web security headers and Content Security Policy (CSP)
- Browser security models and vulnerabilities
- Secure authentication mechanisms (e.g., OAuth, OpenID Connect)
- Web server security configurations and best practices
- Web-based malware detection and prevention
- Secure session management techniques
- Website integrity monitoring and protection against defacement
Hardware Security
- Hardware Trojans detection and prevention techniques
- Hardware-based root of trust mechanisms
- Secure boot and firmware integrity verification
- Side-channel attacks on hardware implementations
- Hardware security primitives (e.g., Physically Unclonable Functions)
- Trusted Platform Module (TPM) and its applications
- Hardware security in IoT devices and wearables
- Secure enclave technologies (e.g., Intel SGX, ARM TrustZone)
- Hardware-based secure storage solutions
- Hardware security certification standards (e.g., FIPS, Common Criteria)
Mobile Security
- Mobile application security assessment and testing
- Secure mobile app development frameworks and guidelines
- Mobile malware detection and prevention techniques
- Mobile operating system security (e.g., Android, iOS)
- Secure inter-app communication mechanisms
- Mobile device management (MDM) security
- Biometric authentication on mobile devices
- Secure data storage and transmission on mobile platforms
- Mobile payment security and NFC vulnerabilities
- Location privacy and tracking protection on mobile devices
Cloud Security
- Cloud computing security models and architectures
- Virtualization security and hypervisor vulnerabilities
- Cloud data encryption and key management
- Identity and access management in cloud environments
- Cloud service provider security assurances and certifications
- Cloud-based intrusion detection and incident response
- Data loss prevention (DLP) in cloud storage services
- Secure cloud migration strategies
- Cloud-based disaster recovery and business continuity planning
- Cloud security governance and compliance frameworks
IoT Security
- IoT device authentication and authorization mechanisms
- Secure communication protocols for IoT networks
- IoT firmware update and patch management
- IoT gateway security and edge computing security
- Privacy-preserving techniques for IoT data
- IoT device lifecycle security
- IoT interoperability and security standards
- IoT supply chain security and integrity verification
- IoT botnet detection and mitigation
- IoT security awareness and education for end-users
AI and Machine Learning Security
- Adversarial machine learning and evasion attacks
- Privacy-preserving machine learning techniques
- Secure model training and inference in distributed environments
- AI-driven cyber threat detection and response
- Explainable AI for security applications
- AI-based vulnerability discovery and exploitation
- AI-enabled authentication and access control mechanisms
- Bias and fairness in AI-powered security systems
- AI-based malware detection and classification
- AI-driven security analytics and threat intelligence
Privacy and Data Protection
- Privacy-enhancing technologies (PETs) and their applications
- GDPR compliance and data protection regulations
- Data anonymization and de-identification techniques
- Privacy-preserving data mining and analysis
- Behavioral tracking and online privacy protection mechanisms
- Secure multiparty computation (SMPC) for privacy-preserving data sharing
- Privacy implications of emerging technologies (e.g., IoT, AI)
- Privacy-aware access control models and policies
- Legal and ethical aspects of data privacy and protection
- Privacy-aware risk assessment methodologies
Cyber Threat Intelligence
- Cyber threat hunting and intelligence gathering techniques
- Threat actor profiling and attribution methodologies
- Dark web monitoring and analysis
- Malware analysis and reverse engineering for threat intelligence
- Threat intelligence sharing platforms and standards
- Machine learning for threat intelligence analysis
- Open-source intelligence (OSINT) for cybersecurity
- Cyber threat modeling and risk assessment frameworks
- Automated threat intelligence feeds integration
- Cyber threat intelligence-driven security operations and incident response
Incident Response and Forensics
- Digital forensics methodologies and tools
- Incident response orchestration and automation
- Memory forensics for volatile data acquisition and analysis
- Network forensics techniques and tools
- File system forensics and data recovery
- Live response and volatile data collection in incident response
- Cloud forensics investigation techniques
- Mobile device forensics and data extraction
- Evidence preservation and chain of custody in digital forensics
- Incident response planning and tabletop exercises
Social Engineering and Human Factors
- Psychological techniques used in social engineering attacks
- Security awareness training effectiveness evaluation
- Social engineering countermeasures and awareness programs
- Insider threat detection and mitigation strategies
- Human-centric security policies and procedures
- Influence of organizational culture on security behavior
- Behavioral biometrics for user authentication
- Security education and training for non-technical users
- Neurosecurity: Understanding Human Brain Vulnerabilities
- Usable security design principles for end-user applications
Legal and Policy Issues
- Cybersecurity incident response and coordination frameworks
- Legal challenges in cross-border data transfers
- Intellectual property protection in cyberspace
- Cybersecurity standards and certification programs
- Cybersecurity implications of emerging technologies (e.g., AI, IoT)
- Ethical considerations in cybersecurity research and practice
- Privacy regulations for data sharing and processing
- Cybersecurity implications of remote work and telecommuting
- Cybersecurity and election integrity
- Cybersecurity in critical infrastructure sectors (e.g., energy, transportation)
- International cybersecurity treaties and agreements
Emerging Technologies and Security
- Security challenges in quantum computing and quantum communication
- Security of 5G and beyond-5G networks
- Security implications of augmented reality (AR) and virtual reality (VR)
- Security of biometric authentication systems
- Security and privacy implications of autonomous vehicles
- Blockchain-based secure identity management systems
- Security of smart home devices and ecosystems
- Security implications of edge computing and fog computing
- Secure integration of AI and IoT technologies
- Security considerations in drone technology and autonomous systems
- Securing data in edge computing environments
Cross-cutting Security Topics
- Cybersecurity economics and cost-benefit analysis
- Cyber resilience and disaster recovery planning
- Security implications of global supply chains
- Cybersecurity education and workforce development
- Security implications of quantum internet
- Securing the Internet of Medical Things (IoMT)
- Security of connected vehicles and intelligent transportation systems
- Cybersecurity in the context of social media platforms
- Securing the digital transformation of businesses
- Security of satellite communication systems
These topics cover a broad spectrum of computer security research areas, providing ample opportunities for investigation and innovation in the field.
Closing Up
Computer security is a huge and constantly changing field, providing many opportunities for new and exciting research. With new threats constantly emerging and cyber-attacks becoming more advanced, there is a huge need for fresh, innovative solutions.
This guide has provided a diverse list of over 161 research topic ideas, covering areas like network security, cryptography, malware analysis, data privacy, ethical hacking, and more.
Whether you’re a student looking for a compelling project, a researcher exploring new techniques, or a professional wanting to contribute to the field, these topics offer plenty of possibilities.
By carefully picking a topic that matches current trends, your interests, and real-world applications, you can start a research journey that not only expands your knowledge but could also shape the future of digital security.
The ultimate goal is to develop strong defensive strategies and stay one step ahead of bad actors, protecting our highly connected world from cyber threats.
How do I know if a research topic is relevant to current cybersecurity challenges?
Keeping abreast of industry news, attending conferences, and consulting with experts can help you gauge the relevance of a research topic to current cybersecurity challenges.
Can I conduct interdisciplinary research in computer security?
Absolutely! Many cybersecurity challenges require interdisciplinary approaches, combining insights from computer science, psychology, law, and other fields.
How can I ensure that my research topic is original and not already explored?
Conducting a thorough literature review is essential for identifying gaps in existing research and ensuring the originality of your chosen topic.
Similar Articles

Top 19 Tips & Tricks On How To Improve Grades?
Do you want to improve your grades? If yes, then don’t worry! In this blog, I have provided 19 tips…

How To Study For Final Exam – 12 Proven Tips You Must Know
How To Study For Final Exam? Studying for the final exam is very important for academic success because they test…
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
M.Tech/Ph.D Thesis Help in Chandigarh | Thesis Guidance in Chandigarh

+91-9465330425
Network Security
The network security is the issue which rose due to self-configuring and decentralized nature of the network. The ad-hoc networks are of three type’s mobile ad-hoc networks, wireless sensor networks, and vehicular ad-hoc networks. The malicious nodes may join the network due to which various type of active and passive attacks are possible in the network. The passive type of attack is the type of attack in which malicious nodes do not affect the network performance. The active type of attacks is the attacks in which malicious nodes reduce networks performance in terms of various parameters. There are various topics in network security for thesis and research.

The black hole, wormhole, sinkhole, Sybil etc are the various type of active attacks which reduce network. In recent times, various techniques have been proposed which detect malicious nodes from the network. To improve the security of the network , techniques of the data encryption, intrusion detection systems are proposed in recent times. The area of research in the network security is secure channel establishment algorithms which are Diffie-Helman, RSA etc which increase the security of the network.
Network Security in a computer network is a good topic to choose for the M.Tech thesis. You can get thesis help from a good thesis guidance agencies like Techsparks. Network Security is the means by which any unauthorized access to a computer network is prevented by following certain policies and procedures. Network Security tend to provide certain ways by which only authorized user can get access to the data in the network. Users are provided unique ID and password for access to the network. Network Security is employed in large organizations and institutions for securing the network from any third party access.
A firewall is a system that applies certain protocols for managing and regulating traffic on the network. It acts as the barricade between the internet and the verified internal network. A firewall can be a software or a hardware. Firewalls are commonly used to prevent any threat to the data from an outside source. Hardware firewalls are found on routers while software firewalls are installed on the computers. While working on your M.Tech thesis, you will learn more about how the firewall works. There are three types of firewall:
- Application Gateways
- Packet Filtering
- Hybrid Systems
Types of network attack
Following are the types of attack on the network:
Active Attack
In an active attack, a miscreant tries to attack data while it is being sent to some other location. He can make changes to it or can hack confidential information while data is being transferred.
Passive Attack
In a passive attack, the hacker constantly monitors the system to gain valuable information through open ports. The attacker does not attempt to make changes to data.
CIA Triad in Network Security
It is based on the following principles:
Confidentiality
Protecting the important data from unauthorized access.
Keeping the uniqueness of the data.
Availability
Authorized access to the available data.
Auditing in Network Security
Auditing in network security means checking whether the security policies and procedures are followed by the organization. This helps the organization to find any loophole in the security measures of the organization’s network and hence implement network security.
This was just basics of network security. If you are involved in networking, then this could be a good choice for your M.Tech thesis. There are various thesis topics in network security which you can opt for M.Tech, M.Phil and for Ph.D. degree.
Latest Thesis and research topics in Network Security
There are various hot topics in network security. Following is the list of latest research and thesis topics in network security for masters and other postgraduate students:
- Access Management
Wireless Security
Endpoint security, hole punching, malware detection, information security, access management:.
It is a method of securing the network by granting access to authorized users the right to access the network. This will prevent any authorized attack on the network thereby securing the network. This process makes use of certain policies which are defined under Information Security Management. This process was added to secure the confidential information that is transferred through the network. This is a very good and simple topic for the thesis in the field of network security. There are various sub-processes under it which you can explore while working on your thesis and research paper.
Wireless Security makes use of the wireless network to prevent any unauthorized access and attack to the computers. WEP(Wired Equivalent Privacy) and WPA(Wi-Fi Protected Access) are the common types of wireless security. WEP is comparatively weaker than WPA as its password can be broken easily using some software tools. There are certain security issues in wireless communication. A malicious individual can attack the network through ad hoc networks, non-traditional networks, network injection, caffe latte attack. There are various security measures that can be applied to SSID hiding, static IP addressing, 802.11 security, encryption etc. There are many topics to explore in this and is a very good choice for the master’s thesis.
Firewall has been discussed above. It regulates the traffic on the network and is a security measure for communication on the network. It is an interesting research paper topic in network security.
Endpoint Security is another approach for network security in which remote networks are secured. In this devices follow certain security standards. It manages the user’s access to the corporate network. The main components of this type of security are VPN(Virtual Private Network), operating system and an antivirus software. This security management process operates on the client-server model. Software as a Service is another model used in this case.
Honeypot is another security mechanism for network security. It detects, deflects and counteracts the unauthorized use of information systems. It consists of data which is isolated and monitored but appears as if it is a part of the site. Honeypots are classified into two categories production honeypot and research honeypot. Production honeypots capture only limited information and are easy to use whereas research honeypots collect information about the black hat communities who are trying to attack the network. Based on their design, honeypots can be classified as pure honeypots, low-interaction honeypots, and high-interaction honeypots. Go for this topic for your thesis as it is an innovative topic.
It is a computer networking technique that uses network address translation(NAT) for establishing the direct connection between the two parties. In this one or both the parties may be behind firewalls. For punching a hole, each of the clients connects to a third-party server which is unrestricted for temporarily storing external and internal address and port information. Each client’s information is passed on to the other through a server and using that direct connection is established. As a result, packets are transferred to each side.
A malware is a software code which is designed to intentionally cause damage to the computer network. The malware code can be in the form of viruses, worms, Trojan horses, or spyware. The aim of malware detection is to find and remove any type of malware code from the network. Antivirus software, firewalls, and other such strategies help in detecting malware in the network. It is one of the good topics in network security for project and thesis.
Information security refers to a set of strategies applied to prevent any type of threat to digital and non-digital information. It is also an interesting topic in network security. The strategies applied revolves around the CIA objectives which is expanded as confidentiality, integrity, and availability. These objectives ensure that only authorized users can access the information.
These are some of the latest interesting topics in network security for thesis as well as for research. If you face any difficulty in this area you can get thesis guidance and thesis help in network security from networking experts.
Techsparks offer thesis and research help in network security topics. You can call us at +91-9465330425 or email us at [email protected] for thesis and research help in network security. You can also fill the contact form the website. We will get back to you as soon as possible.
Techsparks provide the following two guidance packages:
Techsparks standard package.
- Problem Definition/Topic Selection
- Latest IEEE Base Paper (Research Paper Selection)
- Synopsis/Proposal (Plagiarism Free)
- Complete Implementation (Base Paper Implementation, Solution Implementation, Result Analysis And Comparison
- All Kind Of Changes And Modifications
- Online Live Video Classes Through Skype

Techsparks Ultimate Package
- Thesis Report (Plagiarism Free)
- Research Paper (With Guaranteed Acceptance In Any International Journal Like IEEE, Scopus, Springer, Science Direct)
Quick Enquiry
Get a quote, share your details to get free.
Present and Future of Network Security Monitoring
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources
Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved

- [email protected]
- +91-97 91 62 64 69
Network Security Project Topics
Network security is the method towards ensuring safety and protection to shield the fundamental system administration from getting affected by unapproved access, data alterations, physical damage, obliteration, and many other potential attacks. Network security project ideas are gaining importance due to the causes arising out of large-scale network usage . Reach our expert panel team for interesting novel network security project topics . Because issues in network security can lead to many problems which include the following
- Loss of data
- Disruptions in the system functioning due to virus and hacking
- Breach in security leading to malfunctioning
Think about a virtual private network. It is one of the important mechanisms that establish a safe connection to secure the data sent and got. Let us first start by understanding the constraints in network security.

WHAT ARE THE LIMITATIONS OF NETWORK SECURITY?
There are a few limitations existing in present-day network security systems which demand in-depth research and analysis to be carried out to get them solved. The following is a detailed description of certain important network security constraints.
- A large number of methods used for the authentication of users are not entirely reasonable for safe system operations.
- The absence of multifaceted validation plans lead to a less protected CPS framework
- As a result, unapproved claims can access the network
- The firewall arrangements are not truly pertinent and appropriate in many work areas of cyber-physical systems
- Dynamic firewall solutions like next-generation application-oriented firewalls can be the best replacement option
- Only the methods that are proposed recently can be explicitly embraced to ensure security frameworks like CPS
- Notwithstanding the recent methods, honeypot approaches in industry 4.0 needed much advancement.
- Assets and latency in overhead is introduced
- Due to the asymmetric nature of cryptography, the constant working of the CPS is in the client to organize some overhead issues and latency in the network because of the encryption and decoding deferral
- The different types of intrusion detection systems based on behavior, signature, and anomaly are available in network security systems
- Even though these systems are present they are not by and large applied inside the internet of things based areas and or not explicitly intended for securing the CPS framework
From the research works that happened recently in network security, our technical team enriched themselves with the possible solutions suggested overcoming the above limitations . It can be quoted here that such efforts of our technical team are retaining us still in the mainstay of cyber security research guidance. Now let us see about the various factors that are prominent in detecting cyber-attacks.
This article will give you a complete picture of network security concepts and implementations that are successful among researchers in different parts of the world.
WHAT ARE THE FACTORS IMPORTANT IN THREAT DETECTION?
Detection of threat is the major part of any network security system to be declared more efficient by network users . The following five factors are common to all threats which should be identified efficiently by any attack detection mechanisms
- Accidental threats are those dangers that were cost and intentionally through some real network organization segments
- Adversarial threats present vindictive expectations of the people, associations, a state, or a nation
- The environmental dangers incorporate the following.
- Events of calamities like floods and seismic tremors
- Destructions caused by humans like blasts and flames
- Failures due to supporting frameworks like the malfunctioning of broadcast communication and power loss
- The objective of the attackers is the motive to any network security threats
- Criminal and terrorist actions
- Political intentions
- Components of the networks
- Network applications
- Interception, intrusion, alteration, and fabrication are the different mechanisms based on which any network security attack rely
- Network integrity
- Confidentiality of information
- Availability and accessibility
So creating the best framework for protecting a network from malicious attacks involves many different types of measures and strategies . Look into the following threats and proper strategies used to overcome such issues in network layer security.
- Hijacking the session
- Collection of data by unauthorized users
- Classifying the security zones
- Maintaining remote security
- Detecting invasions
- Isolation of firewall
It is as a result of our professional online research guidance on network security project topics that many PhD candidates around the world reported higher accuracy and performance of their model . We are always happy to extend you the necessary support for your research work. Get in touch with us to avail one of the top reliable research guidance in the world. Now let us have a detailed outline of network security systems.
OUTLINE OF NETWORK SECURITY
As you might know, there are various technologies involved in cyber security systems . It becomes now important for us to understand such technologies and the various elements involved in ensuring network security along with their benefits.
- Internet of things
- Big data analytics
- Machine learning protocols
- Augmented reality
- Cloud computing applications
- Artificial intelligence
- Theft of intellectual property
- Physical damages in cyber networks
- Production loss
- Spear phishing
- Ransomware attacks
- Threats by malware
- Reliability loss
- Threats to safety and health of the network
- Issues related to the integrity of network and data
- Other common cyber attacks
- Security in application
- Securing the data
- Planning the continuation of business
- Security in operations
- End-user about cyber security mechanisms
- Network security protocols
With these elements, researchers include many new technologies into network security projects for enhancing the system as a whole. Why should one do research in cyber security? The answer to this question lies in its benefits. Let us see the merits of network security systems below.
- Improving the confidence of an organization
- Protecting the end-users from potential attacks on networks
- Enhancing the time of recovery after meeting with a security breach
- Protecting the network and information
- Cyber security mechanism to prevent malware attacks, phishing threats, and ransomware
The advantages of cyber security systems extend well beyond this list and researchers must take the responsibility of exploring and expanding the scope of network security systems existing these days. For this purpose, you need to have access to a high level of research data with multidimensional objectives.
You can reach out to our technical team at any time and get the necessary literature need to carry out your research. We will also provide you with all essential information in formulating network security project topics. Now let us look into the vulnerabilities existing in a network that has to be rectified by network security researchers.
VULNERABILITIES OF NETWORKS
Here we categorize the network vulnerabilities into different heads as listed below.
- Vulnerabilities of devices and networks
- Susceptibility due to flaws in the system security
- Man in the middle attacks
- Threats in manipulating packets
- Network layer
- Application layer
- DoS and DDoS attacks
- Back door attacks
- Eavesdropping
The wired and wireless communications security features are compromised due to cyber security flaws.
- Configuration
- Absence of guidelines due to security
- Procedure lack
- Deficiency of policies of security
Having looked into the above aspects of vulnerabilities present in any network, you should now understand the practical and real-time faults that can become potentially vulnerable zones.
VULNERABILITIES IN REAL-TIME NETWORK APPLICATIONS
The cyber-physical systems and their vulnerabilities are listed below. Have a look into the following aspects of vulnerabilities in which we gained the enormous potential to solve them.
- Protocols for open communication
- Attacks based on web
- Wired and wireless communications
- Insecure protocols
- Interconnected devices (exposed)
- RTOS and OS insecurity
- Insecurity in secondary access points
- Physical sabotage of different network equipment
- Software vulnerabilities
- DoS attacks (software)
- Invasion of privacy of the patients
- Noise issues
- Injection attacks
- Replay issues
- Communication protocols
- Field devices that are interconnected
- Smart meters that are insecure
- Physical sabotage of the equipment
- Insecure algorithms
- Intrusion into privacy
- Tracing GPS
- CAN bus insecurity
- Flaws in communication software
- Components that are not protected (physically)
- Exploitations of the media player
- Flaw due to authentication of Bluetooth
The vulnerabilities are the checkpoints that act as the mode of entry for an attacker to have access to network data. So your network security project topics should be modeled in such a way as to act as a barrier for major attacks. Now let us talk about different kinds of attacks on network security
WHAT ARE NETWORK SECURITY ATTACKS?
A network security attack is nothing but an attempt to compromise the defense system deployed in a network and make alterations to the network and its data.
Prevention of such attacks at the first hand is the major objective of a network security system. An attack can be both active and passive based on the methodologies and techniques used by the attacker. So the scope of any network security model should be to detect and prevent all types of security attacks.
We have successfully modeled plenty of projects with the above-stated objective. To interact with our research experts and get access to the details of our projects . Now let us look into different network security methods.
SECURITY METHODS FOR NETWORKS
Usually, a network is secured by following one or more methods mentioned below.
- The mechanism for data encryption
- Cryptographic protocols and algorithms (lightweight)
- Anti-malware
- Consistent maintenance
- Hashing methods (advanced)
- IPS and IDS
- Spread spectrum
- Multi-factor authentication (by answering too much personal information like your name, occupation, qualification, and possession)
It is not a must that all the above features are included in the same network security system because the demands and objectives of network security vary with the customers. We gained huge credit for our customized research support to craft novel information security project ideas . If you want your queries to be solved by research experts then reach out to us. Now let us have a look into the topmost preferred research network security project topics .
TOP 10 RESEARCH IDEAS IN NETWORK SECURITY
From the experience of rendering project guidance in network security for more than two decades we have come up with the following list of top 10 network security research ideas
- Security solutions based on artificial intelligence
- Protected audit (ensuring security)
- Authentication based on multiple factors (strong entity)
- Cryptographic algorithms (lightweight dynamic key-dependent)
- Definition of privileges
- Classification and prioritizing based network security
- Dynamic hashing process along with strong passwords
- Noncryptographic solutions (enhanced with latest technologies)
You can have a dialogue with us before choosing your network security project topics . The efficiency of your system should not be at the cost compromise on any network security threats. That is we insist that safety protocols in place should be capable of handling network threats in any real-time situation . For this, you should have some idea on simulation methods in network security research. Now let us see about it below,
NETWORK SECURITY ATTACKS SIMULATION
Simulation methods are the advanced techniques that are used to check the efficiency of any network security system to any kind of attack. To achieve this objective the simulation tools take advantage of imitating the possible network security threats from different kinds of hackers and attackers data and check the reaction of our model to them.
In spite of many simulators used by researchers, there are demands for some novel approach in network simulation incorporating the following characteristics.
- Generating automatic attacks based on profile
- Giving proper report on traffic analysis
- Supporting the detection algorithm plugins
- Ability to test the algorithms designed to detect intrusions
- Detailed analysis on security measures included in the network
- Overlay security frameworks development
One of the famous simulators based on OMNET++ that incorporates the above features is NETA or network attack . You might have used this tool earlier. We helped our customers build the research gap by providing them with the technical details on all implementation tools . Now let us look into some of the most important simulation tools used by network security researchers.
NETWORK SECURITY SIMULATION TOOLS
The following is a list of some of the most advanced network security simulation tools that you can use for your project.
- SSL decryption devices
- Forensics boxes (for data capture)
- Proxy servers
- Data collection tools for IDS
- ProVerif 1.93
- NetLogo 3.5
The trend of imputing network security project topics, design to simulation is becoming quite significant. Because from the output of a proper simulation you can get the indication of network performance towards any kind of threat. With that data, you can work towards enhancing your systems’ efficiency . Get in touch with us to have a consideration of the perspectives of research scholars and students from top universities of the world who are our customers too. We encourage the exchange of authentic research data while maintaining professional secrecy. So you can confidently rely on him for entire research guidance.

Opening Hours
- Mon-Sat 09.00 am – 6.30 pm
- Lunch Time 12.30 pm – 01.30 pm
- Break Time 04.00 pm – 04.30 pm
- 18 years service excellence
- 40+ country reach
- 36+ university mou
- 194+ college mou
- 6000+ happy customers
- 100+ employees
- 240+ writers
- 60+ developers
- 45+ researchers
- 540+ Journal tieup
Payment Options

Our Clients

Social Links

- Terms of Use

Opening Time

Closing Time
- We follow Indian time zone

You are using an outdated browser. Please upgrade your browser to improve your experience.
Security at Berkeley
The Security Group in the EECS Department at the University of California, Berkeley studies a wide variety of topics, including cryptography, network security, usable security, and secure machine learning.
To learn more about our research, we encourage you to visit the pages of our faculty and students, linked below.
We've got great people!
Formidable faculty.
- Alessandro Chiesa
- Natacha Crooks
- Anthony Joseph
- Vern Paxson
- Raluca Ada Popa
- David Wagner
Affable affiliates
- Serge Egelman
- Nicholas Weaver
Percipient postdocs & stellar staff
- Ioannis (Yannis) Demertzis
- Evgenios Kornaropoulos
- Katerina Sotiraki
- Sameer Wagh
- Primal Wijesekera
Gracious grad students
- Noura Alomar
- Eleanor Cawthon
- Emma Dauterman
- Vivian Fang
- Conor Gilsenan
- Julien Piet
- Deevashwer Rathee
- Mayank Rathee
- Nikita Samarin
- Chawin Sitawarin
- Eric Wallace
- Jean-Luc Watson
- Tiancheng Xie
Amazing alumni
- Devdatta Akhawe
- Jethro Beekman
- John Bethencourt
- Nikita Borisov
- Nicholas Carlini
- Weikeng Chen
- Xinyun Chen
- Monica Chew
- Chia Yuan Cho
- Arel Cordero
- Weidong Cui
- Thurston Dang
- Rachna Dhamija
- Adrienne Porter Felt
- David Fifield
- Matthew Finifter
- Ian Goldberg
- Dan Hendrycks
- Sakshi Jain
- Steve Hanna
- Mobin Javed
- Noah Johnson
- Rob Johnson
- Alex Kantchelian
- Chris Karlof
- Nathan Malkin
- Bill Marczak
- Michael McCoyd
- Adrian Mettler
- Brad Miller
- Mitar Milutinovic
- Pratyush Mishra
- David Molnar
- Austin Murdock
- Blaine Nelson
- Paul Pearce
- Adrian Perrig
- Rishabh Poddar
- Rebecca Portnoff
- Justin Samuel
- Naveen Sastry
- Prateek Saxena
- Ben Schwarz
- Umesh Shankar
- Richard Shin
- Jeongseok Son
- Emil Stefanov
- Cynthia Sturton
- Kurt Thomas
- Chris Thompson
- Matthias Vallentin
- Jason Waddle
- Joel Weinberger
- Alma Whitten
- Ka-Ping Yee
- Jiaheng Zhang
- Wenting Zheng
- Vijay D'Silva
- Maritza Johnson
- Lorenzo Martignoni
- Ivan Martinovic
- Stephen McCamant
- Bodo Möller
- Prateek Mittal
- Mathias Payer
- William Robertson
Adored admins
- Angie Abbatecola
- Lena Lau Stewart
We have lots of friends!
Security research at Berkeley spans a number of labs, centers, departments, colleges, and schools. You may also want to learn about (in no particular order):
- The cryptography research group
- RISELab (Real-time Intelligent Secure Explainable)
- Center for Evidence-based Security Research
- The Networking and Security Group at ICSI
- Berkeley Laboratory for Usable and Experimental Security (BLUES) and the Usable Security and Privacy Group at ICSI
- The Center for Long-Term Cybersecurity
- The School of Information and its Master's of Information and Cybersecurity
We host events!
- Security Seminar
- Security Reading Group
- The CLTC's seminar series
We teach courses!
Undergraduate.
- CS 161: Computer Security - s21 , f20 , s20 , f19 , s19 , f18 , s18 , f17 , s17 , f16 , s16 , s15 , s14 , s13 , s11 , s10 , f08 , f05
- CS 171: Undergraduate Cryptography - s21 , f19 , s19
- CS 194-138: Penetration Testing ("Cyberwar") - f17
- CS 261: Computer Security - s21 , f18 , f17 , f15 , f12 , s11 , f11 , f09 , f08 , f07 , f04 , f02 , f00 , f98
- CS 261N: Internet/Network Security - s20 , f16 , s15 , s14 , f12 , s12 , f10 , f09 , s09 , s08
- CS 276: Cryptography - f20 , f18 , f17 , f16 , f15 , f14 , s09 , s06 , s04 , s02
- CS 294-163: Decentralized Security: Theory and Systems - f19
- CS 294-155: Law and Cryptography - f19
- CS 294-156: Advanced Topics on Secure Hardware - f18
- CS 294-144/151: Blockchain and Cryptoeconomics - s19 , f18 , s18
- CS 294: Advanced Cryptography - s20 , f18 , s18
- CS 294: Secure Computation - s16
- CS 294-101: Cutting-edge Web Technologies - s15
- CS 294-105: Empirical Analysis - f14
- CS 294-65: Privacy Technologies: From Theory to Practice - s11
- CS 294: Advanced Topics in Computer Security - s10
- CS 294-24: Privacy and Security Enhancing Technologies - f07
- CS 294: Lattices, Learning with Errors and Post-Quantum Cryptography - s20
- INFO 290-001 Cybersecurity in Context - f19
For the most up-to-date list of courses, and to see what's being offered next semester, see the EECS course directory .
We'd love for you to join us!
If you would like to join Berkeley's EECS Department as a graduate student, please apply to our Ph.D. program . Many Berkeley undergraduates assist in our research; if you're interested in doing research, contact our faculty members directly. We also frequently host visiting students and professors.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- Latest Research Topics in Cryptography and Network Security
Network security term itself clearly depicts you that it is designed to protect the entire network from the authorized access in time of digital/analog data communication . The technologies used in network security are guaranteed to provide data confidentiality, authenticity, and availability against security risks throughout the communication.
This article is intended to display to you about latest research topics in Cryptography and Network Security with its current research areas!!!
Generally, the security mechanisms have two constituents to shield the network information . Below, we have listed the working principles of those constituents for your reference.
- Add the security over the information. For instance , implement the encryption method over the transmitting message. So that information will be converted into a new unreadable format where the illegal user cannot access the original message until it is decrypted . Further, it also includes the code information in the header, which depends on the content of the message. Thus, it is used to detect/verify the original sender of the message.
- In the case of sensitive data, it is necessary to share the information between only sender and receive r. The opponent party should not know the information under any conditions. In order to achieve this motive, the encryption key is used to convert the original plain text into scrambled text by the sender. Similarly, the decryption key is used to convert scrambled text into original plain text by the receiver.
For any measure, the main goal is to identify and prevent security attacks with rescue abilities . Most probably, the security measures are based on cryptographic technologies. If you take any security mechanism, then you may find the trace of encryption / some kind of data transformation .
Overview of Cryptography and Network Security
Cryptography is basically classified into two major techniques, and they are cryptography and cryptanalysis. On the one hand, cryptography is the process of protecting or hiding the information through intelligent masking techniques (i.e., code the information). On the other hand, cryptanalysis investigates how the ciphertext is converted into plain text and vice-versa.
Due to its incredible security concern and contribution, it is largely used in many research domains and areas to improve its security aspects. Some of the current research aspects of cryptography are given as below,
- Hashing Techniques
- Public-Key Cryptography
- Key Distribution and Management
- Symmetric-Key Cryptography
- Real-time Cryptography Applications
- Cryptographic Security Protocols / Standards
- Quantum Cryptography
- Biological Cryptography
- And many more
Network Security is intended to develop various levels of shielding measures with an extended security scope. These measures are worked in the principle of identifying/predicting network security threats/risks to take immediate defensive response/actions. As a result, it protects the entire network information. The identification, prediction, and defensive response measures are essential to execute based on specific security policies . Few of the current research directions of the network security are given as below,
- Incident Response System
- Intrusion Detection and Prevention Schemes
- Trusted Heterogeneous Networks
- Network Security Threats, Risks and Vulnerabilities
- Network Protection against Internet Attacks
- Communication Technologies and Protocol Security
We hope you are clear on the fundamentals of cryptography and network security . Now, we can see the recent research areas of cryptography and network security . In truth, our research team is presently creating unbelievable contributions through our latest research topics in cryptography and network security . So, you can confidently hold your hands with us to create amazing research work.
Research Areas in Network Security
- Heterogeneous Communication Networks
- Cognitive Radio based Mobile Communication
- Information Security in Self-Organized Network
- Named data and Data / Human Centric Network
- Ultra-band Wireless Sensor Network (UWSN)
- Wireless Body Area Network (WBAN)
- Cognitive Radio-Wireless Sensor Network (CR-WSN)
- Software Defined-Wireless Sensor Network (SD-WSN)
- Hybrid ad hoc
- Vehicular Ad hoc
- Cognitive Radio Ad hoc
- Underwater Network
- MANET / iMANET / WANET
- Fog / Cloud-Radio Access Network (Fog-RAN / cloud-RAN)
- Advance Cellular Networks (4G, LTEA-Pro, 5G, Beyond 5G and 6G)
Here, we have given you the achievements of cryptography while applying them in network security. For any cryptographic methods , the following are determined as the key objectives for reaching high network security .
What are the objectives of cryptography in network security?
- Detect the attack which definitely create worst impact
- Screen the network to monitor the behavior and activities of intruders
- Detect the attack and analyze their effect on network after execution
- Analyze the origin and root cause of the threats / attacks
- Conduct in-depth inspection on different levels of attacks
Our development team is sophisticated with experienced developers, so we can solve any level of a complex issue. Here, we have given you the widely used cryptographic algorithms, classified as low-cost, lightweight, and ultra-lightweight characteristics .
Major Classifications of Cryptography Algorithms
- Hardware Development – 2000 Gates
- Device Capacity – AT mega 128
- Ciphers – ECC, Grain / 128, MIBS TWINE, PRESENT, etc.
- Software Development – 8kb RAM and 4kb ROM
- Hardware Development – 3000 Gates
- Device Capacity – ATiny 45, AT mega 128 and 8051 micontroller
- Ciphers – ECC, DEXL, SOSEMANUK, CLEFIA, etc.
- Software Development – 8kb RAM and 32kb ROM
- Hardware Development – 1000 Gates
- Device Capacity – ATiny 45 and 8051 microntroller
- Ciphers – KATAN, Hummingbird, Fruitv2, QTL, etc.
- Software Development – 256 B RAM and 4kb ROM
Research Gaps of Cryptography
Though many lightweight ciphers are introduced in cryptography, it lacks performance in any of these aspects, such as high security and low ( resource utilization, delay, internal overhead states , etc.).
Below, we can see the challenges in lightweight cryptographic techniques such as elliptic curve cryptography, stream ciphers, hash methods, and block ciphers . Our developers will pay extra attention to the following for framing lightweight security measures that assure high performance in all aspects.
CRYPTOGRAPHY LATEST ALGORITHMS
- Decrease the usage of energy / power
- Minimize the needs of memory
- Enhance the speed of computation
- Optimize the Group arithmetic and Prime Fields (PF)
- Minimize the length of the key
- Decrease the chip area / size
- Minimize the Key / IV setup rotations
- Reduce the internal state / condition
- Decrease the message and output size
- Make the simpler cycles
- Model the simple key schedules
- Decrease the key and block size for fast execution
Our current study on cryptographic techniques found that ECC is less preferable than AES because of its speed. However, ECC is considered a slow process; it meets the requirement of ultra-lightweight cryptography . Our developers are glad to share the trick to increase the ECC speed for your information. If the memory needs are minimized, then eventually, it also minimizes the ROM and RAM needs. As a result, ECC gains the first priority among others. Below, we have given the list of research fields that offer a sophisticated platform for developing cryptographic techniques enabled network security applications.
Applications of Cryptography based Network Security
- Internet of Things
- Industrial Internet of Things
- Haptic / Tactile Internet of things
- Internet of Bio / Nano-Things
- Vehicle to Infrastructure
- Autonomous Vehicle Driving System
- Deep-Sea Objects Identification and Analysis
- Healthcare and Telemedicine
- Remote Patient Monitoring using Wearable Devices
- 360 Degree and Ultra-High Definition Videos
- Virtual and Augmented Reality
- Space Travel and Satellite Communication
- WBAN based Digital Sensing and Visualization
- Smart Environment Modeling (smart city / home / office, etc.)
Further, we have listed the top-demanding research topics in cryptography and network security . The below-given research ideas are just the samples. More than this, we have a copious amount of novel research notions. If you have your own ideas and are looking for the best guidance to craft network security research topics , we are also ready to support you in your need.
Top 10 Latest Research Topics in Cryptography and Network Security
- Secure Cross-Layer Architecture Design
- Security for Critical Cyber Physical Systems
- Insider Threats Prediction and Detection Systems
- Modeling of Security Assured Smart Grid System
- Data Hiding, Survivability and Watermarking
- SDN-NFV based High Performance Security System
- Security Protocol Performance Assessments
- Design and Development of Ultra-Efficient Security Models
- Security in Cloud Services and Applications
- Identification of Multi-level Security Threats with Preventive Measures
- Improved Privacy and Security Solutions in Wireless Communications
From a development perspective, now we can see how the network security models are designed, tested, and assessed . In order to estimate the efficiency of the network security model, we can use the following for real-time development.
How do we evaluate the performance of network security?
- Analytical Models
- Real-time Tests
Further, we have also listed the important tools used for network security projects developments . All these tools are specialized to meet particular requirements of the network security model. For instance: Wireshark is used to generate and analyze the network packets . Likewise, we have given the other important tools and technologies for your awareness.
- Test the vulnerabilities of the of the network at different angles through continuous scan and access
- Probe the available susceptibilities in the application and take immediate response to that events
- Analyze and troubleshoot the packets, network, applications, communication protocols and more
- Collect whole information of network including OS, computer systems, and network entities
Next, we can see about the secure transmission approaches. Basically, the performance metrics have a key player role in elevating the design of transmission approaches. However, it has high importance, the modeling of physical layer security cause different kinds of technical issues . So, it is critical to select the suitable metrics for improving reliability, resource cost (low power), transmission efficiency, and energy efficiency of the transmission approaches . Our developers will help to attain your goal in the following aspects of transmission approaches.
- Reliability – compute in terms of privacy outage probability and capacity
- Power cost – compute in terms of power usage (low) for promising QoS
- Transmission Efficiency – compute in terms of maximum possible privacy degree and capacity
- Energy Efficiency – compute in terms of amount of energy required for one bit transmission and amount of bits transmitted in one unit of energy
As mentioned earlier, the above-specified metrics are sure to increase the performance of transmission approaches. And, these metrics are adopted in the time of system modelling . Further, we have improved our skills in all security-related strategies based on recent research requirements.
Last but not least, if you want to be familiar with more updates on the latest research topics in cryptography and network security , then communicate with our team. We will surely assist you in fulfilling your needs for a fine-tuning research career.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
This is a potential security issue, you are being redirected to https://csrc.nist.gov .
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Drafts for Public Comment
- All Public Drafts
- NIST Special Publications (SPs)
- NIST interagency/internal reports (NISTIRs)
- ITL Bulletins
- White Papers
- Journal Articles
- Conference Papers
- Security & Privacy
Applications
Technologies.
- Laws & Regulations
- Activities & Products
- News & Updates
- Cryptographic Technology
- Secure Systems and Applications
- Security Components and Mechanisms
- Security Engineering and Risk Management
- Security Testing, Validation, and Measurement
- Cybersecurity and Privacy Applications
- National Cybersecurity Center of Excellence (NCCoE)
- National Initiative for Cybersecurity Education (NICE)
Security and Privacy
- digital signatures
- key management
- lightweight cryptography
- message authentication
- post-quantum cryptography
- random number generation
- secure hashing
- cybersecurity supply chain risk management
- general security & privacy
- access authorization
- access control
- Personal Identity Verification
- public key infrastructure
- personally identifiable information
- privacy engineering
- categorization
- continuous monitoring
- controls assessment
- privacy controls
- security controls
- risk assessment
- roots of trust
- system authorization
- advanced persistent threats
- information sharing
- intrusion detection & prevention
- vulnerability management
- accessibility
- testing & validation
- acquisition
- asset management
- audit & accountability
- awareness training & education
- configuration management
- contingency planning
- incident response
- maintenance
- media protection
- patch management
- personnel security
- physical & environmental protection
- program management
- security automation
- reliability
- artificial intelligence
- cloud & virtualization
- combinatorial testing
- personal computers
- quantum information science
- smart cards
- operating systems
- communications & wireless
- cyber-physical systems
- cybersecurity education
- cybersecurity framework
- cybersecurity workforce
- industrial control systems
- Internet of Things
- mathematics
- positioning navigation & timing
- small & medium business
Laws and Regulations
- Comprehensive National Cybersecurity Initiative
- Cybersecurity Strategy and Implementation Plan
- Cyberspace Policy Review
- Executive Order 13636
- Executive Order 13702
- Executive Order 13718
- Executive Order 13800
- Executive Order 13905
- Executive Order 14028
- Executive Order 14110
- Federal Cybersecurity Research and Development Strategic Plan
- Homeland Security Presidential Directive 7
- Homeland Security Presidential Directive 12
- OMB Circular A-11
- OMB Circular A-130
- Cyber Security R&D Act
- Cybersecurity Enhancement Act
- E-Government Act
- Energy Independence and Security Act
- Federal Information Security Modernization Act
- First Responder Network Authority
- Health Insurance Portability and Accountability Act
- Help America Vote Act
- Internet of Things Cybersecurity Improvement Act
- Federal Acquisition Regulation
Activities and Products
- annual reports
- conferences & workshops
- quick start guides
- reference materials
- standards development
- financial services
- hospitality
- manufacturing
- public safety
- telecommunications
- transportation
e-mail address: [email protected]
Tel 7639361621

Network security is the process that permits the users to regulate the network and manage the operating system and applications in the network. This page deals with the significant research aspects of network security. Let us start with the types of network security.
List of Network Security Research Areas
- Cryptographic Hashing
- Source Location Privacy
- Symmetric Key Cryptography
- IaaS Cloud Forensics
- Anomaly-based IDS
- Lightweight Architecture
- Retraining Massive Data
- Public Key Cryptography
- Software Defined Networking
- Hybrid Signature
- Identity-based Cryptography
- ANN-based Steganography
- Certificateless Cryptography
- Blockchain-based IDS
- Lightweight Cryptography
- Network Intrusion Detection System
- Internet Traffic Transforming
- Fiber Optical Security

Types of Network Security
- It is one of the network security systems which standardize the network traffic the regulated protocols and the firewall which has the part in the barriers among the internet and the internal networks
- It has a device that can scan the networks and that recognize the potential security issues and for example, testing for device penetration
- It is used for the surplus traffic such as the anti-virus scanning device and the content filtering device
- The devices scan and recognize the unnecessary traffic such as the intrusion detection appliances
For add on information, all the research field has its research issues. Similarly, the research problems in network security research areas are highlighted by our research experts with the appropriate solutions.
Network Security Problems and Solutions
- Data Leakage, Illegal Access and Access Illegal IoT
- Privacy Preserving
- Data and Privacy Leakage and Counterfeit
- Authentication, End to End Security and Encryption
- Security and Privacy Problems
- Security Mechanism
- Eavesdropping and Illegal Data Collecting
- Encryption, Data Authentication and etc
- Privacy Leakage and Data Accessing
- Access Control Mechanism, Data Processing
- Data Leakage and wsn simulation
- Access Control, Self Destruction
How to protect the network from attackers?
- It doesn’t use any algorithms or protocols
- If any two files have the same hash functions and it provided the stable authentication
- Evade the circular dependence
- The security dependency among the boundaries is clear
- Definite with the effective control
- The security control should be hinder and reconfigurable
- To protect the impersonation the well build cryptographic mechanisms are used
- The well build cryptographic mechanism has such qualities (updated, revoked and generated)
To conclude, we work by the best effort source and doing projects by all latest lists of updates in the network security research areas . So contact us for your network security research projects & thesis .

IMAGES
VIDEO
COMMENTS
Topics in Computer and Network Security Stanford CS 356, Fall 2023. CS 356 is graduate course that covers foundational work and current topics in computer and network security. The course consists of reading and discussing published research papers, presenting recent security work, and completing an original research project.
Network security threats are patented to cause monetary loss. The data gathered in a network are used to identify the security threats like vulnerabilities and intrusions. Such data are called the data related to network security. Research Scholars can reach us in developing network security thesis topics based on data collection and detection ...
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics/ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The research is conducted based on analysis of threat, risk and vulnerability in an enterprise network along with countermeasures to overcome the security incidents in an enterprise network.
Network Security Research Topic ideas for MS, or Ph.D. Degree. I am sharing with you some of the research topics regarding Network Security that you can choose for your research proposal for the thesis work of MS, or Ph.D. Degree. CompTIA security+ guide to network security fundamentals. A survey of moving target defenses for network security.
Cyber Security Research Topics. Cyber Security Research Topics are as follows: The role of machine learning in detecting cyber threats. The impact of cloud computing on cyber security. Cyber warfare and its effects on national security. The rise of ransomware attacks and their prevention methods.
Wireless Network Security . Wireless Router . Network Security System. The use of computer networks in an agency aims to facilitate communication and data transfer between devices. The network that can be applied can be using wireless media or LAN cable. At SMP XYZ, most of the computers still use wireless networks.
Jan 2024. Dr Santosh Kumar Sahu. Nabahani B. Hamadi. Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse ...
Latest Network Security Project Topics. Designing MIMO telecommunication system. Social media sharing based on blockchain trust. Using ML and AI to detect fake news in social media. The technology of new authentication and biometric for access control, identity management, and device authentication.
In today's increasingly severe network security situation, network security situational awareness provides a more comprehensive and feasible new idea for the inadequacy of various single solutions and is currently a research hotspot in the field of network security. At present, there are still gaps or room for improvement in network security situational awareness in terms of model scheme ...
Network security research topics which are currently undergoing are cyber-insurance, cumulative Metric for an information network etc. Most commonly also used security mechanisms are Encipherment, Digital signature, also coding-decoding etc. But these are also fundamentals of Network security. It is also fast growing field which needs current ...
This guide lists over 161 thought-provoking computer security research ideas in different areas, such as network security, cryptography, malware analysis, data privacy, ethical hacking, and more. Look through these topics to get inspiration for your next big research project or school paper that could potentially shape the future of digital ...
There are various topics in network security for thesis and research. The black hole, wormhole, sinkhole, Sybil etc are the various type of active attacks which reduce network. In recent times, various techniques have been proposed which detect malicious nodes from the network. To improve the security of the network, techniques of the data ...
Network Security Monitoring (NSM) is a popular term to refer to the detection of security incidents by monitoring the network events. An NSM system is central for the security of current networks, given the escalation in sophistication of cyberwarfare. In this paper, we review the state-of-the-art in NSM, and derive a new taxonomy of the functionalities and modules in an NSM system. This ...
A definition of network security is the process of taking concurrent actions for network environment protection from illegal access by attackers.We can see various activities of attackers in the network such as misuse, data loss, modification, improper disclosure, and thereby legitimate user's privacy is leaked.. Our service i.e. network security research topics are your secure environment ...
Description of the topic. Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network.
Classifying the security zones. Maintaining remote security. Detecting invasions. Isolation of firewall. It is as a result of our professional online research guidance on network security project topics that many PhD candidates around the world reported higher accuracy and performance of their model.
The Security Group in the EECS Department at the University of California, Berkeley studies a wide variety of topics, including cryptography, network security, usable security, and secure machine learning. To learn more about our research, we encourage you to visit the pages of our faculty and students, linked below.
22 answers. Asked 4th Feb, 2022. Najim Halloum. Recommended research fields: Applying Machine Learning methods to Network Protocols field in many areas like IoT, Sensor Networks, Network Security ...
Few of the current research directions of the network security are given as below, Incident Response System. Intrusion Detection and Prevention Schemes. Trusted Heterogeneous Networks. Network Security Threats, Risks and Vulnerabilities. Network Protection against Internet Attacks.
Network Security PhD Research Topics Network Security PhD Research Topics offer innovative platform for you to get our dedicated professional's inventive ideas to improve your knowledge.We have 100+ international-level celebrated scientists to provide the best guidance for you in each step of your research.We offer highly confidential ...
Computer Security Resource Center. Projects; Publications Expand or Collapse Topics ... Topics Select a term to learn more about it, and to see CSRC Projects, Publications, News, Events and Presentations on that topic. ... Federal Cybersecurity Research and Development Strategic Plan;
Network security is the process that permits the users to regulate the network and manage the operating system and applications in the network. This page deals with the significant research aspects of network security. Let us start with the types of network security. List of Network Security Research Areas. Cryptographic Hashing; Source ...